WolvCTF 2024 - Writeups
This is a writeup for some forensics and OSINT challenges from WolvCTF 2024. Overall, the challenges were super fun and interesting. Shame that the hardest forensics challenge could be done unintentionally with strings.
Eternally Pwned: Infiltration [Forensics]
Question: I recently had my passwords and other sensitive data leaked, but I have no idea how. Can you figure out how the attacker got in to my PC?
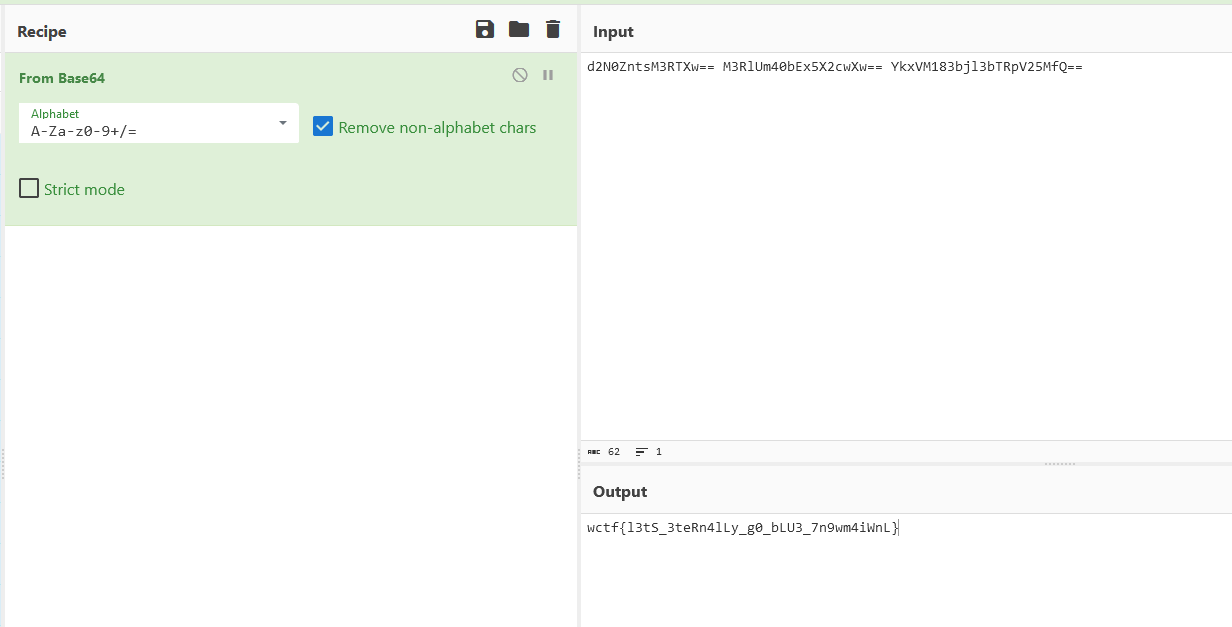
Flag: wctf{l3tS_3teRn4lLy_g0_bLU3_7n9wm4iWnL}
We are given a PCAP file to investigate. Analyzing the PCAP file, several protocols can be identified including HTTP, SMB, Ethernet, etc. Checking the SMB packets, it seems that there were pieces of base64 encoded text at the bottom of the packet data. Decoding the text, we can get the flag.
Eternally Pwned: Persistence [Forensics]
Question: I get that the attackers were in my PC, but how did they achieve persistence?
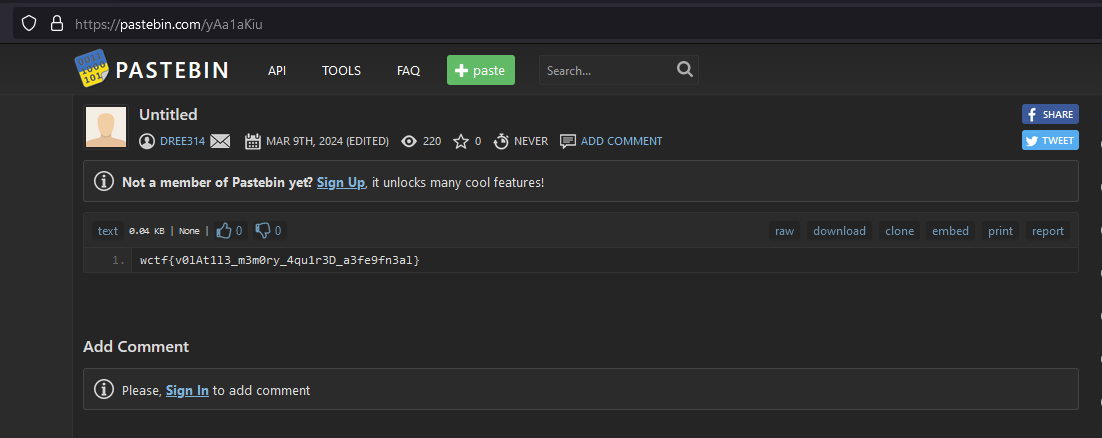
Flag: wctf{v0lAt1l3_m3m0ry_4qu1r3D_a3fe9fn3al}
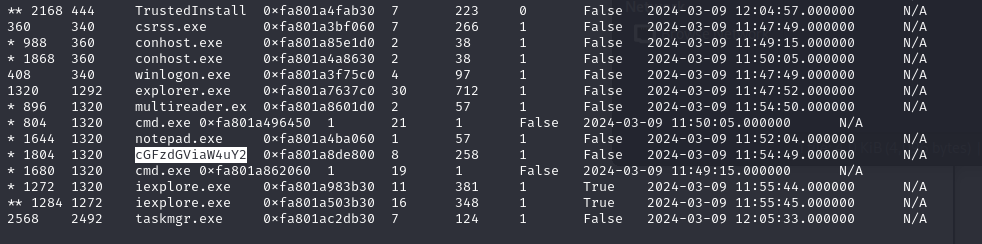
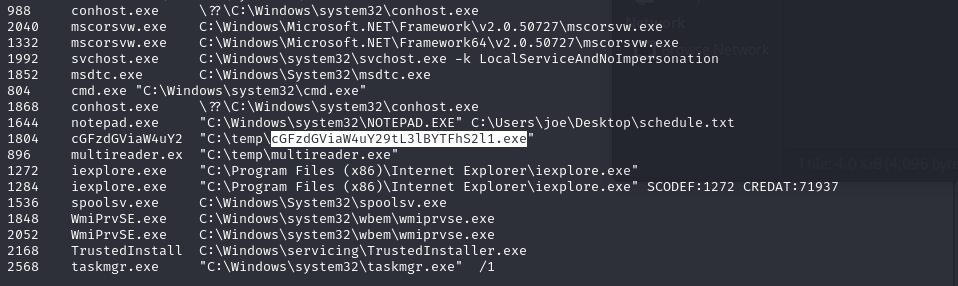
We are given a memory dump to investigate. Checking the processes and CMD arguments, a suspicious process can be identified.
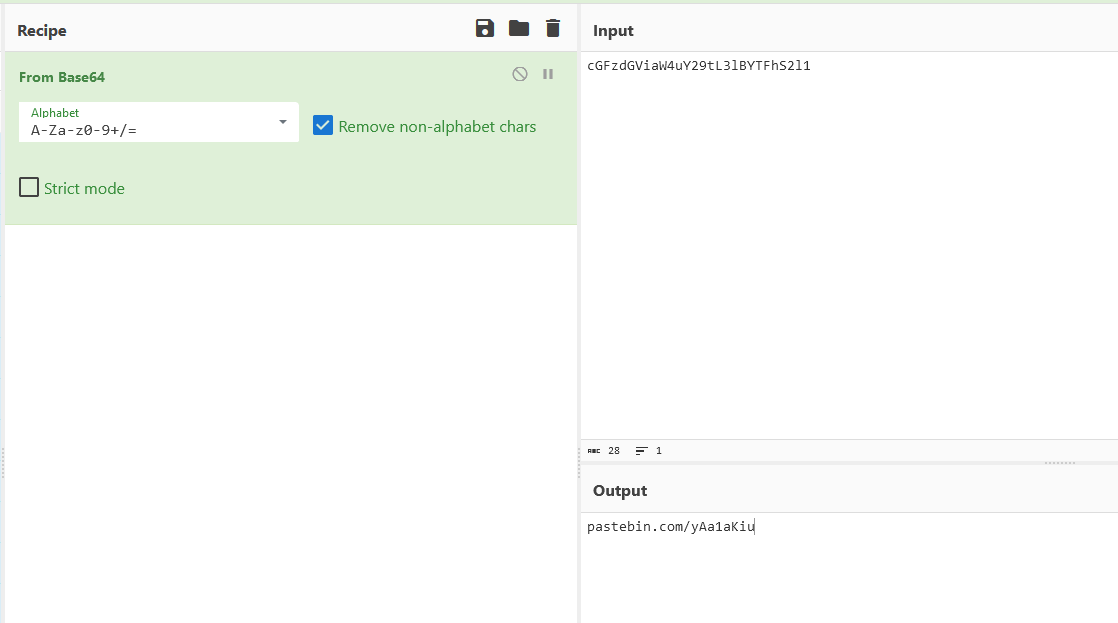
Decoding the name gives a Pastebin URL which redirects to the flag.
Eternally Pwned: Exfiltration [Forensics]
Question: Ok yeah, they are definitely in the machine. But how did they manage to take my data? You will likely find both the packet capture from Eternally Pwned: Infiltration and the memory dump from Eternally Pwned: Persistence to be useful
Flag: wctf{ahk-5cr1pt5-4r3-d4ng3r0u5-dirmgaiwpd}
We are given the same memory dump to investigate. For this challenge, the flag can be obtained via strings which is obviously unintended.
1
2
3
4
5
6
7
└─$ strings -e l MEMORY.DMP| grep wctf{
6mail userr3reewedaweawe@gmail.com password123 wctf{ahk-5cr1pt5-4r3-d4ng3r0u5-dirmgaiwpd}iwonderifa
mail userr3reewedaweawe@gmail.com password123 wctf{ahk-5cr1pt5-4r3-d4ng3r0u5-dirmgaiwpd}iwonderifa
Pmail userr3reewedaweawe@gmail.com password123 wctf{ahk-5cr1pt5-4r3-d4ng3r0u5-dirmgaiwpd}iwonderifa
mail userr3reewedaweawe@gmail.com password123 wctf{ahk-5cr1pt5-4r3-d4ng3r0u5-dirmgaiwpd}iwonderifanyoneislisteningtowhatiamtypinghm;3;3;3;3;3;
mail userr3reewedaweawe@gmail.com password123 wctf{ahk-5cr1pt5-4r3-d4ng3r0u5-dirmgaiwpd}iwonderifanyoneislisteningtowhatiamtypinghm;3;3;3;3;3;
...
The intended way was shown in the author’s writeup.
Log Analysis [Forensics]
Question: Hi there incident responder. So we have this company that was breached sometime last week, but their SOC team only keeps HTTP request logs :( We took down all of our wolvsecsolutions websites as a precaution. Maybe there’s still a way to figure out what happened? Why did they click on a suspicious link? Somebody told me there’s a flag on the link now?
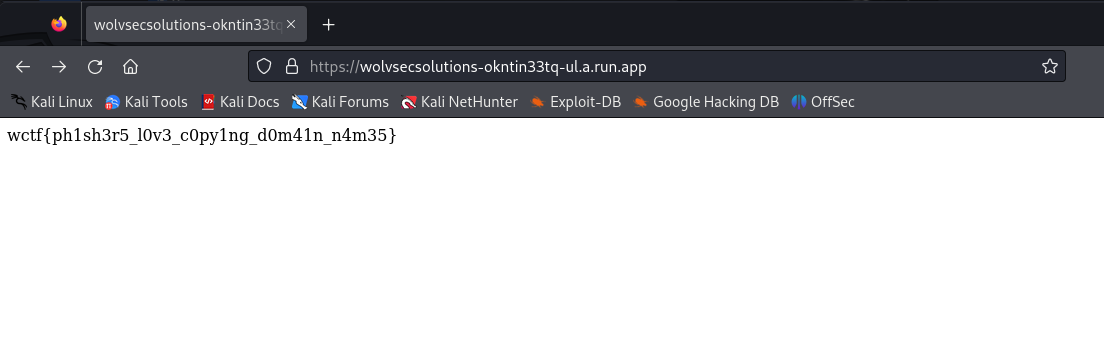
Flag: wctf{ph1sh3r5_l0v3_c0py1ng_d0m41n_n4m35}
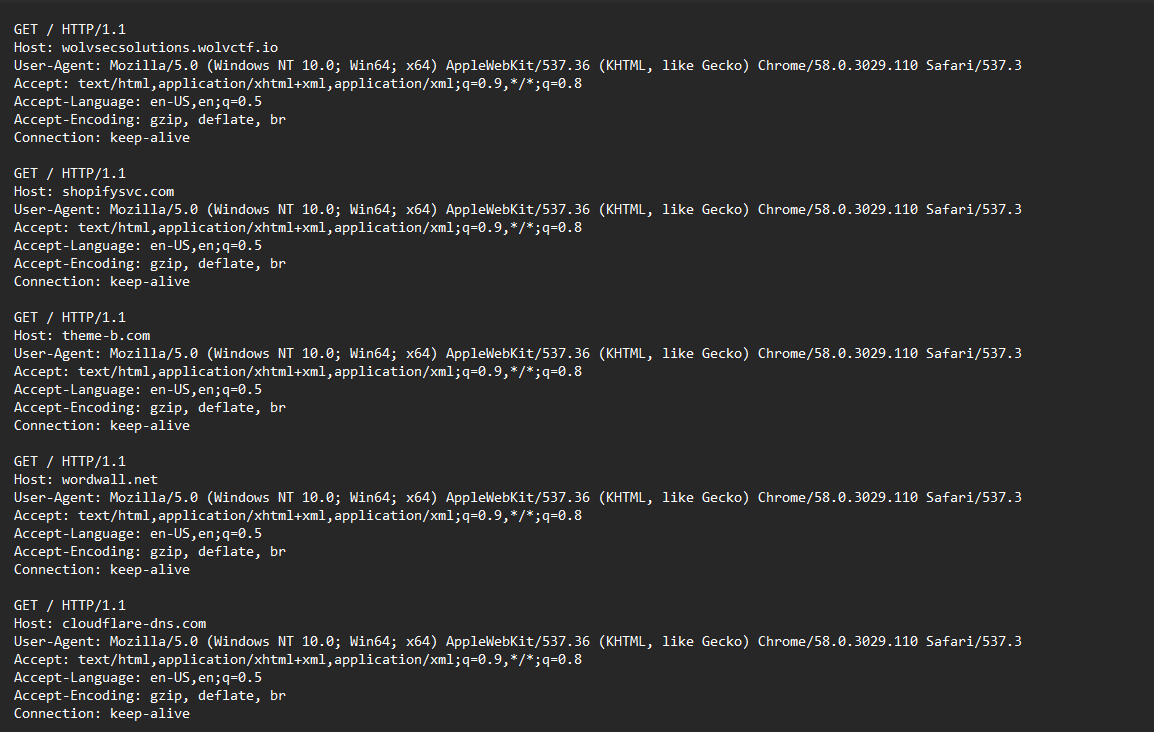
We are given a log file to investigate. Since the question mentioned the website wolvsecsolutions being taken down, it might be related to finding the flag somehow.
Going through the domains for wolvsecsolutions, a suspicious domain can be identified wolvsecsolutions-okntin33tq-ul.a.run.app. The flag can be obtained from the website directly.
Site Secret [Forensics]
Question: There’s been a secret flag on this website the whole time??? That’s an interesting background…
Flag: wctf{t00k_y0u_l0Ng_3n0UgH_h3h3}
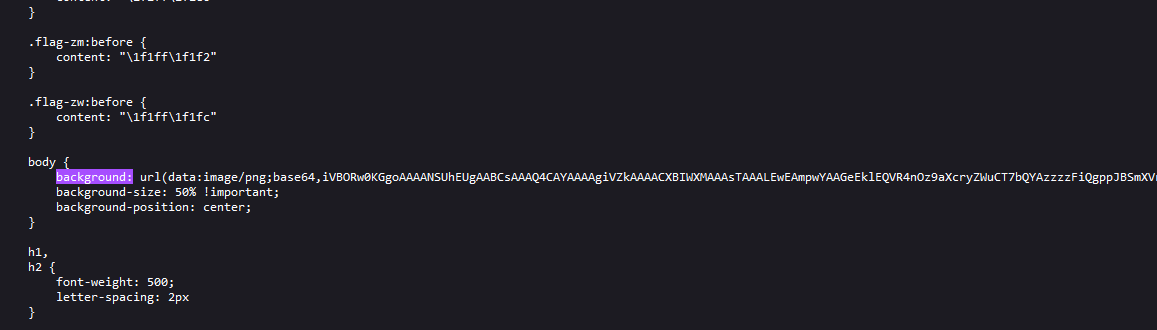
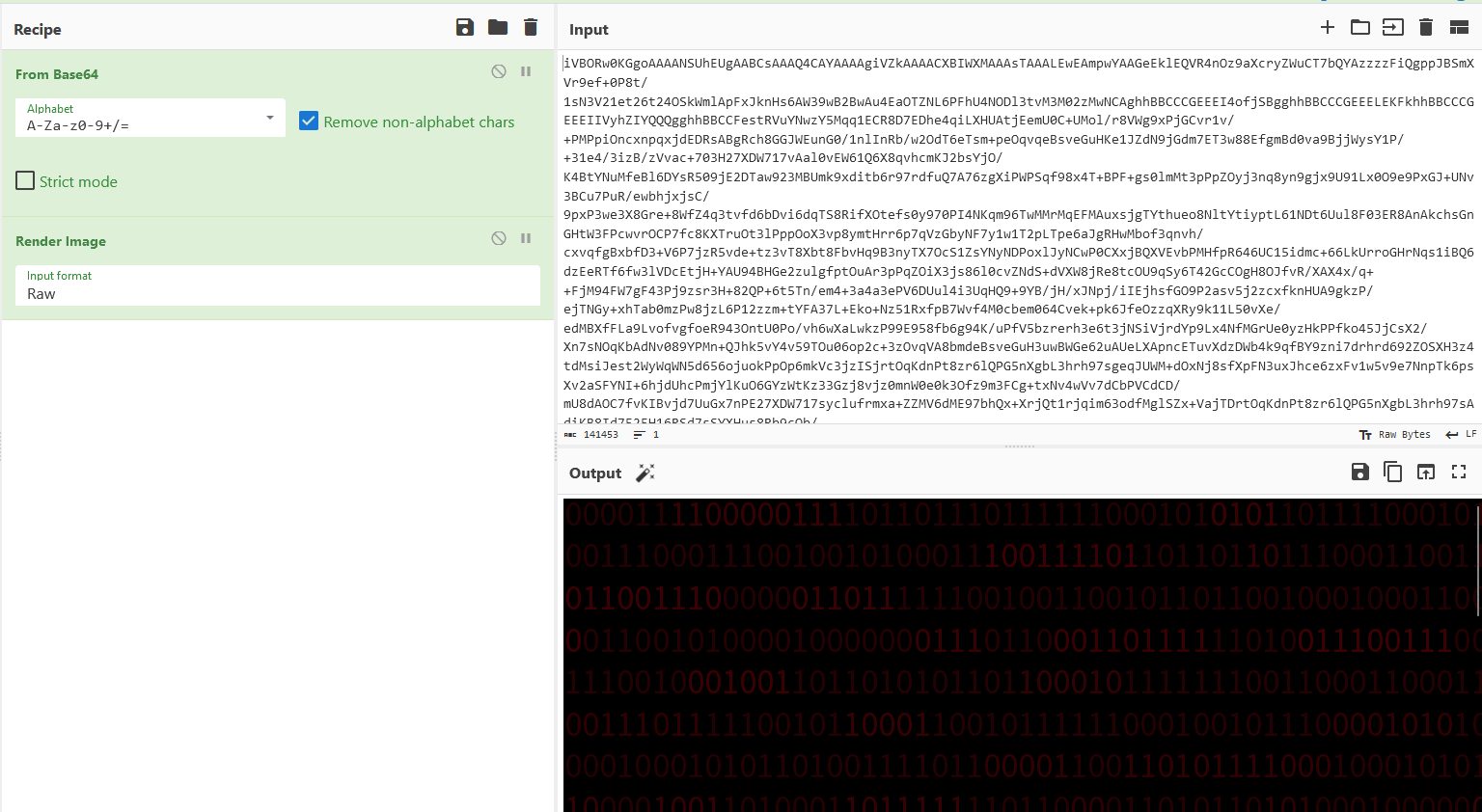
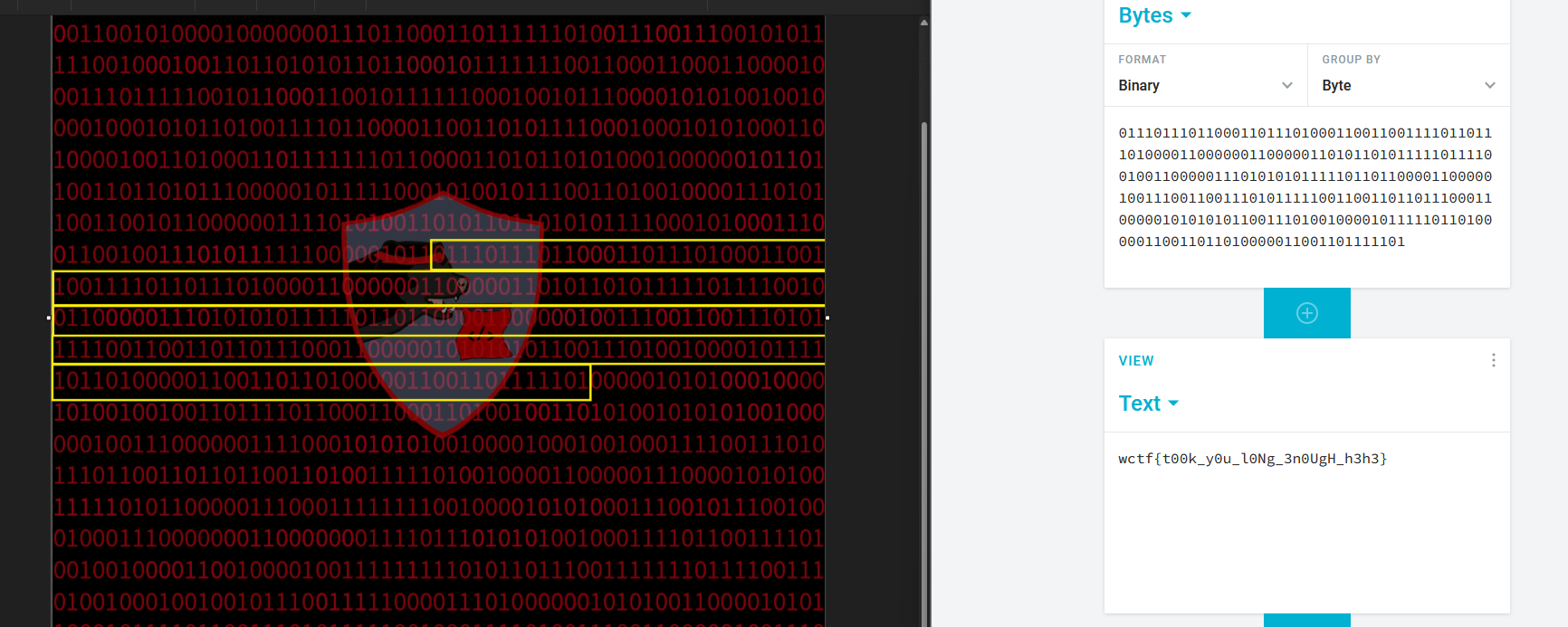
The challenge mentioned the flag being inside the background of the CTF website.
Extracting the website background which was encoded in base64, the background seem to be a long sequence of binary code.
The binary values of wctf{ was 01110111 01100011 01110100 01100110 01111011, so I can start my search with the binary values. Additionally, I increased the brightness and contrast of the background image to ease my eyes. The flag can be obtained after finding the starting point.
WOLPHV I: Reconnaissance [OSINT]
Question: A new ransomware group you may have heard about has emerged: WOLPHV. There’s already been reports of their presence in articles and posts. NOTE: Wolphv’s twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges. This is a start to a 5 part series of challenges. Solving this challenge will unlock WOLPHV II: Infiltrate
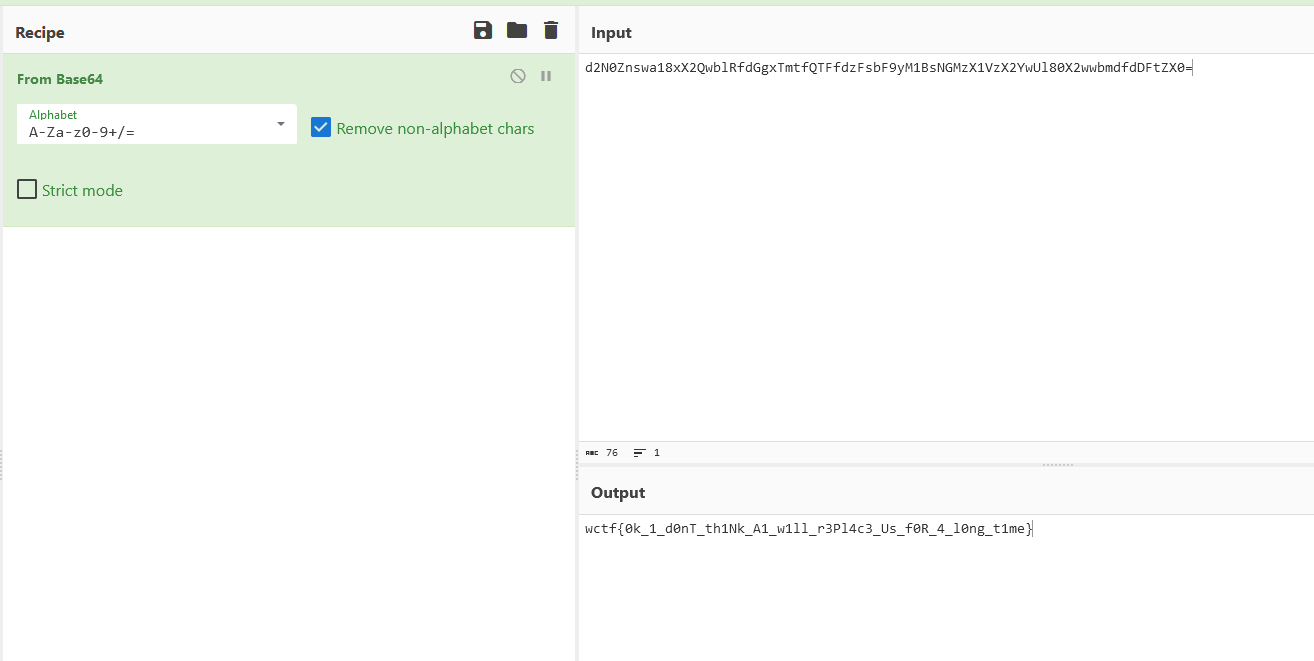
Flag: wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me}
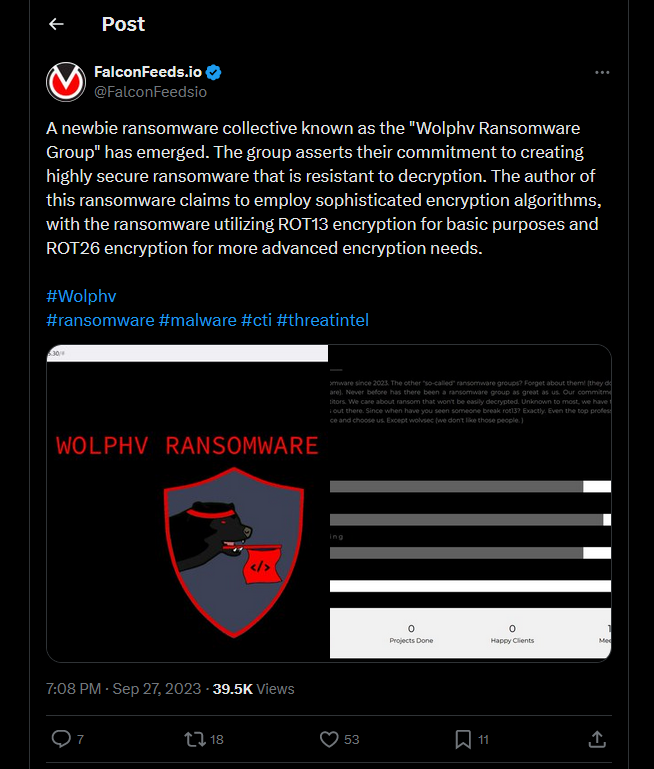
We are tasked to find information on the new ransomware group: WOLPHV. Checking WOLPHV on social media platforms, this article can be identified on Twitter.
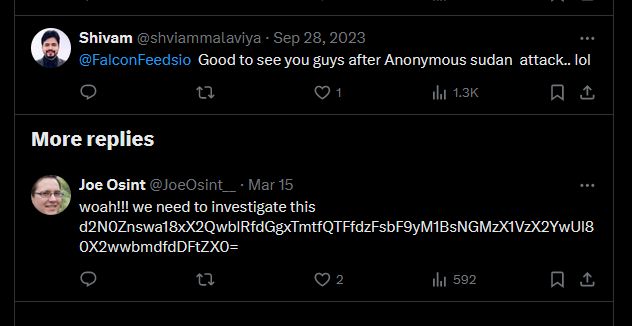
Reading the comments, the flag can be found encoded in base64.
WOLPHV II: Infiltrate [OSINT]
Question: Since the WOLPHV twitter/x is out of comission now, I wonder where else the official WOLPHV group posts on social media. Maybe we can also infiltrate what they use to message each other. NOTE: Wolphv’s twitter/X account and https://wolphv.chal.wolvsec.org/ are out of scope for all these challenges. Any flags found from these are not a part of these challenges. Solving this challege will unlock WOLPHV III, WOLPHV IV, and WOLPHV V
Flag: wctf{0k_1_d0nT_th1Nk_A1_w1ll_r3Pl4c3_Us_f0R_4_l0ng_t1me}
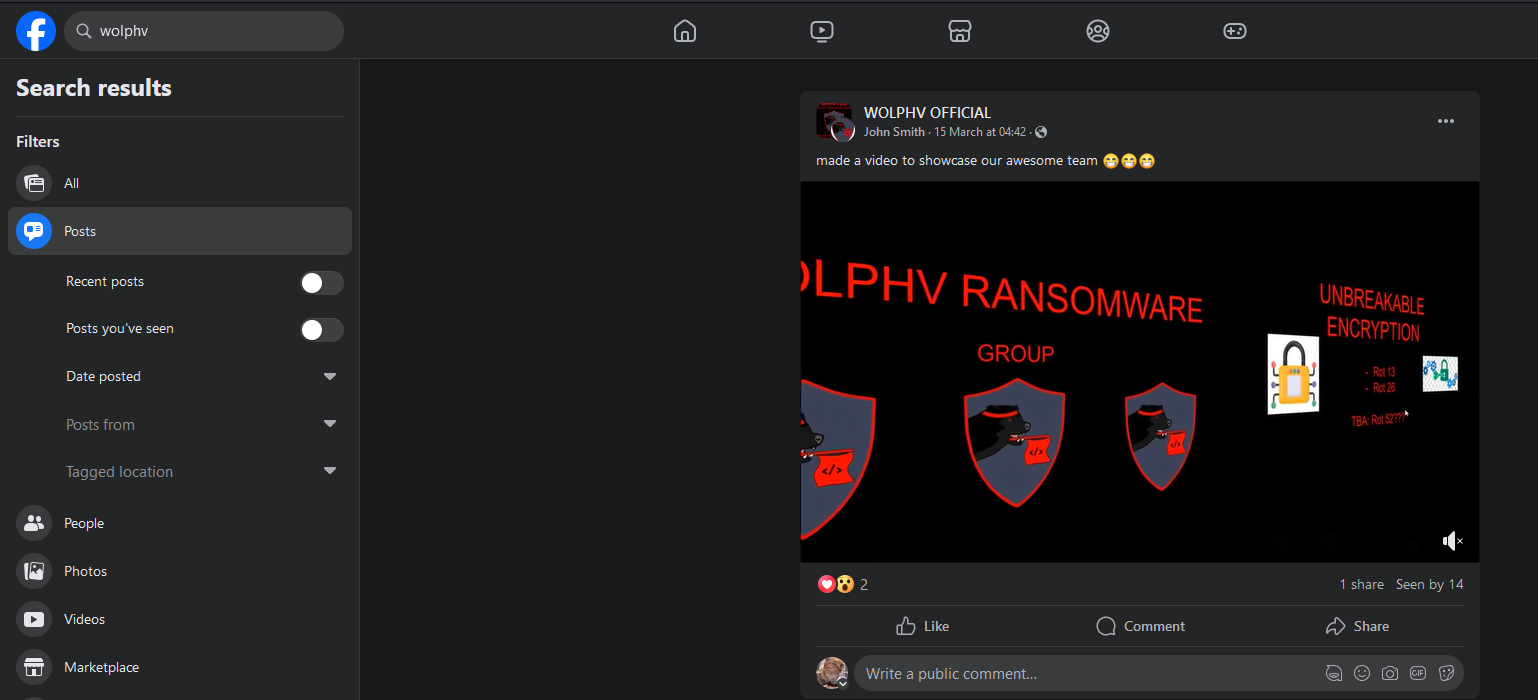
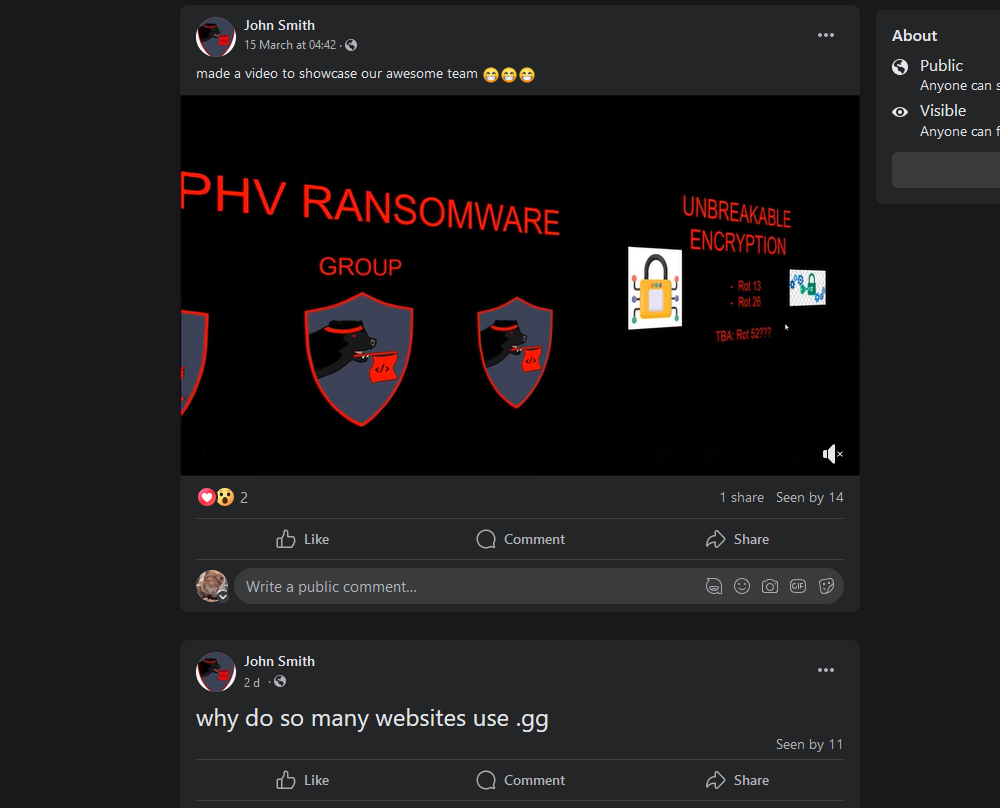
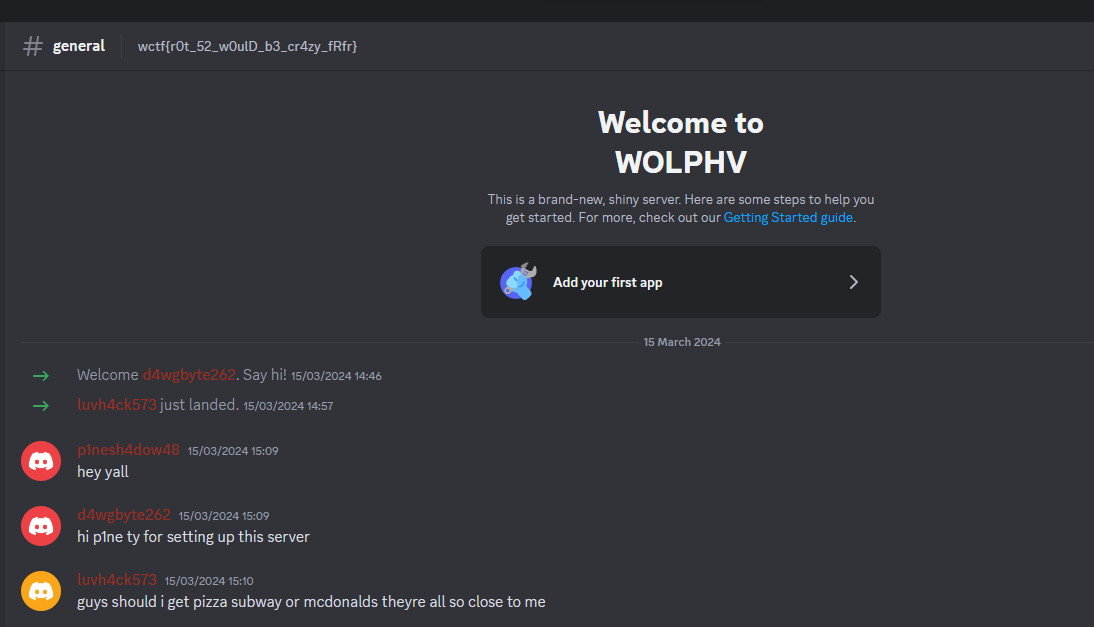
Similarly, checking WOLPHV on social media platforms, a Facebook group that was created four days ago can be identified.
Watching the video, a Discord link was leaked at the end of the video.
However, the discord link leads to an error page. Reading the group posts again, they mentioned something about .gg in URLs. So I tried that and it worked, the URL turned into a server invite link.
The flag can be obtained after joining the server.