Wargames.MY CTF 2023 - Writeups
This is a writeup for some forensics challenges from Wargames.MY CTF 2023 organized by Wargames.MY. This was also the last local CTF I’ve participated in 2023 with my friends @Shen and @Blugon. The CTF blew our mind as the challenges were so much more difficult than previous years. I could have done better in this CTF but I was too distracted with my final year project. I will be back stronger and hope to achieve top 10 next year.
Compromised [Forensics]
Question:
Flag: wgmy{d1df8b8811dbe22f3dce67ef2998f21c}
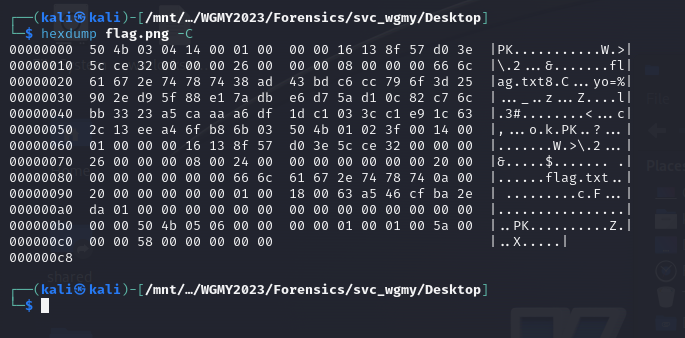
We are given triaged Windows artifacts to investigate. Checking common Windows locations, a flag image can be identified in the user’s Desktop. Checking its magic bytes, the flag image was a ZIP file instead.
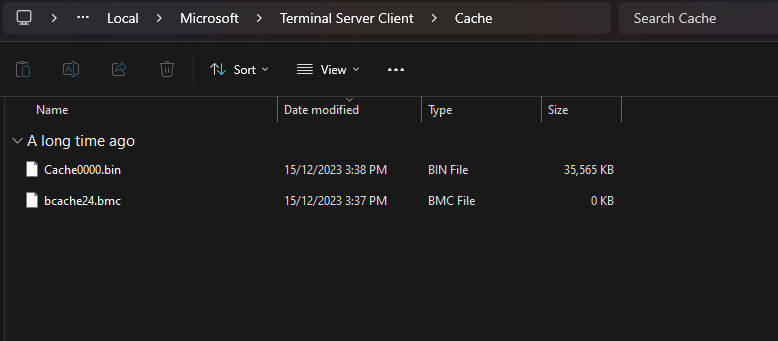
The ZIP file contained the actual flag file, however, the ZIP was password-protected. Looking for ways to obtain the password, I came across the RDP cache files located in \svc_wgmy\AppData\Local\Microsoft\Terminal Server Client\Cache. Doing research on it, this blog mentioned about parsing RDP bitmap cache.
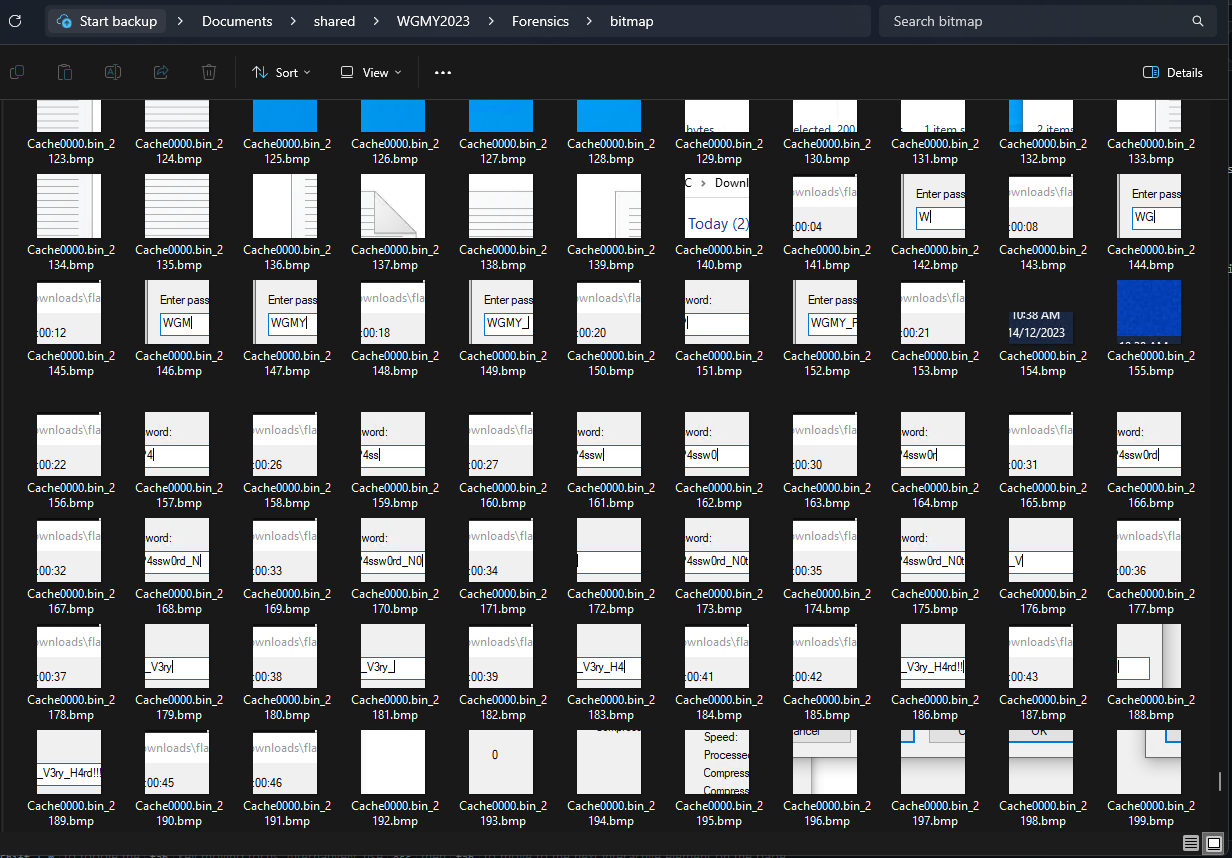
Using bmc-tools, the RDP bitmap cache can be parsed and rebuilt into a RDP snapshot. The ZIP password was identified to be WGMY_P4ssw0rd_N0t_V3ry_H4rd!!! which allows us to obtain the flag file within it.
See You [Forensics]
Question:
Flag: wgmy{c0e22d2434fa188003be61e9fe404ea6}
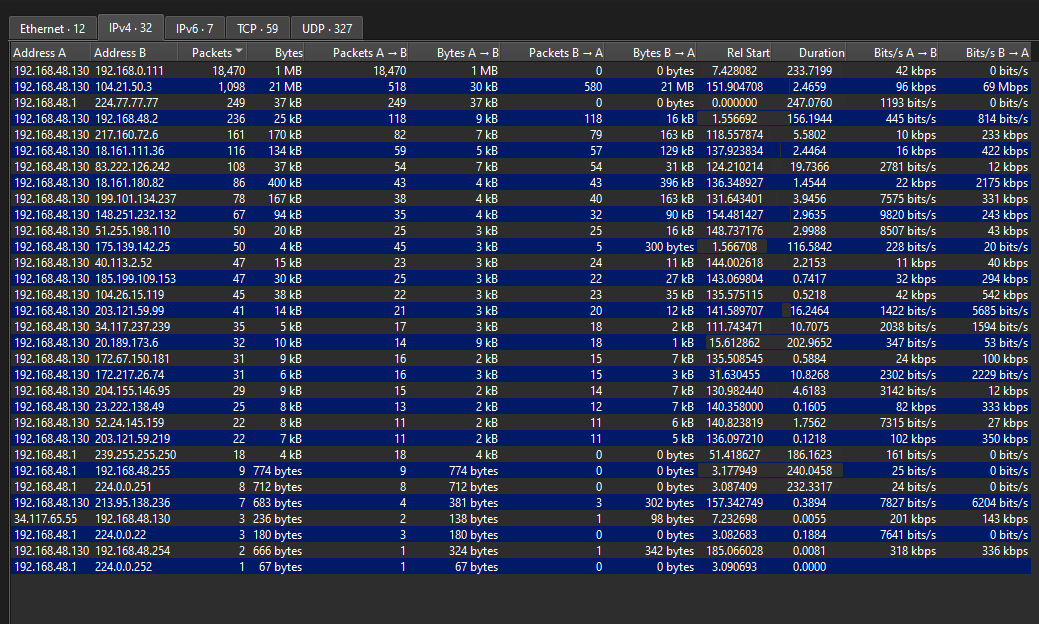
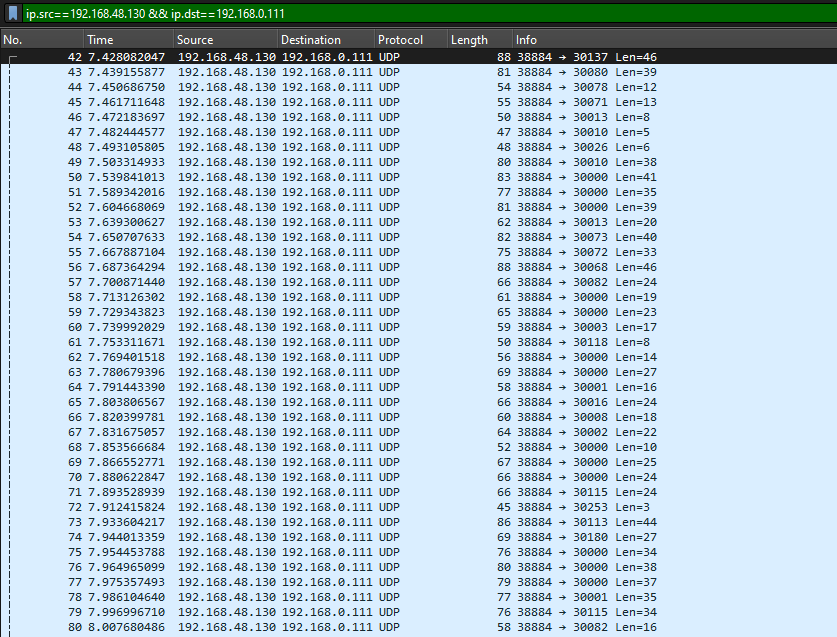
We are given a PCAP file to investigate. Unfortunately I could not solve this before the CTF ended, but I still attempted it with the help from the author. The solution was pretty cool, the challenge already mentioned about some exfiltration of a “file” to another internal computer. So the first thing was to check the IP that was sending the most requests. The IP 192.168.48.130 seem to be sending multiple UDP packets to 192.168.0.111.
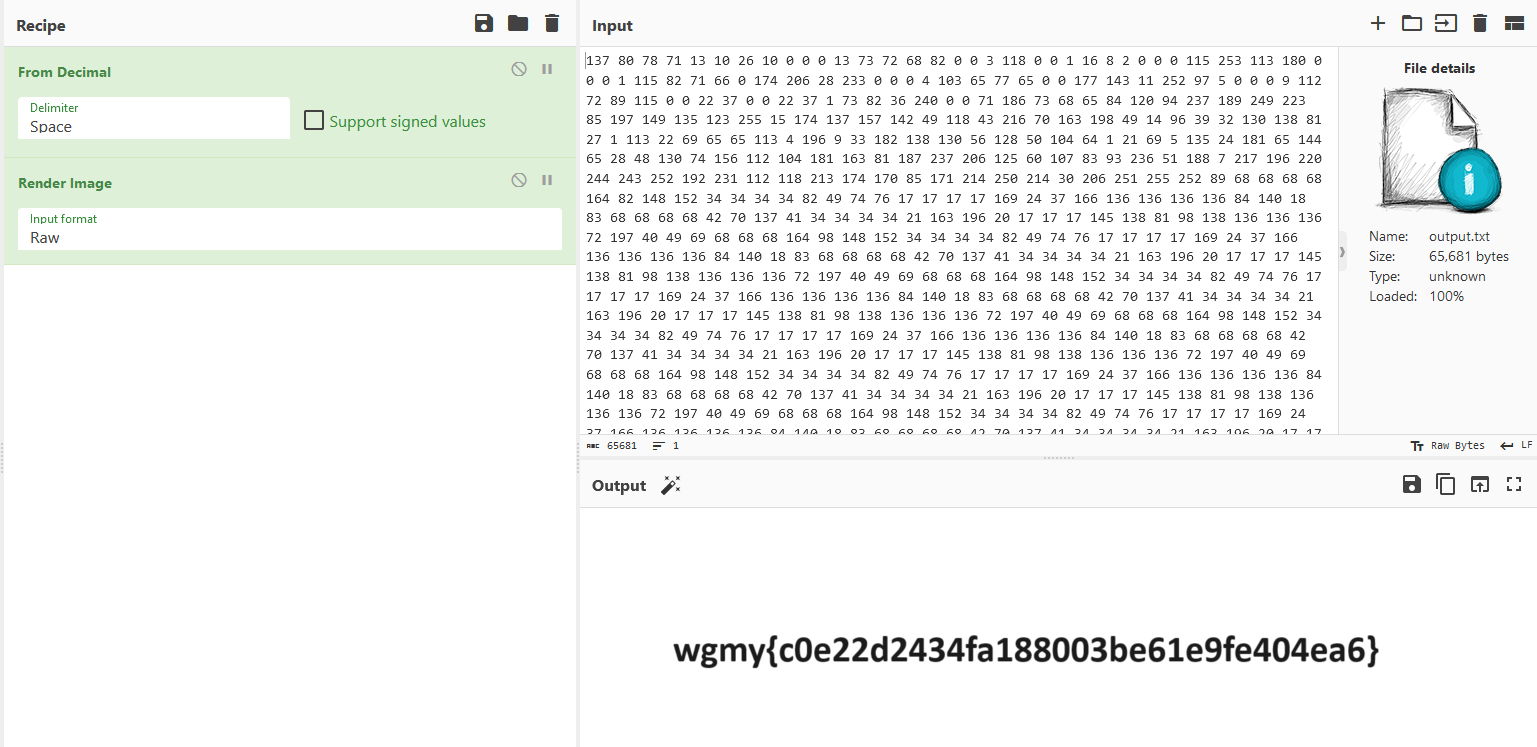
A Python script can be created to automatically extract the ports and minus 30000 from each of them.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
import subprocess
import sys
pcap_file = "artifact.pcapng"
tshark_filter = "udp.srcport == 38884"
output_field = "udp.dstport"
final_output = "output.txt"
try:
tshark_command = [
"tshark", "-r", pcap_file, "-Y", tshark_filter,
"-T", "fields", "-e", output_field
]
tshark_output = subprocess.run(
tshark_command, text=True, capture_output=True, check=True
).stdout
results = []
for line in tshark_output.strip().splitlines():
try:
value = int(line.strip())
result = value - 30000
results.append(str(result))
except ValueError:
print("Error: The tshark output should contain only integers.")
sys.exit(1)
with open(final_output, 'w') as output_file:
output_file.write(' '.join(results))
print(f"Results have been written to {final_output}.")
except subprocess.CalledProcessError as e:
print(f"Error executing tshark: {e}")
sys.exit(1)
except Exception as e:
print(f"An unexpected error occurred: {e}")
sys.exit(1)
Decoding the output, the flag can be obtained.