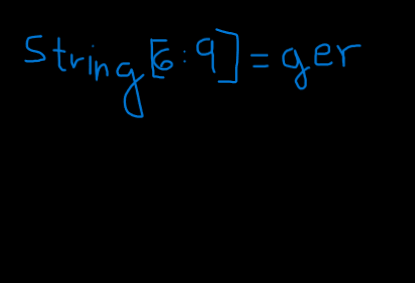VishwaCTF 2024 - Writeups
This is a writeup for some forensics and steganography challenges from VishwaCTF 2024. The CTF was quite enjoyable despite having bad/guessy challenges at the beginning. Fortunately, the second wave of challenges had better quality in them.
Repo Riddles [Forensics]
Question: We got a suspicious Linkedin post which got a description and also a zip file with it. It is suspected that a message is hidden in there. Can you find it?
1
2
3
4
5
6
7
Title: My First Project -The Journey Begins
Hello fellow developers and curious minds!
I'm thrilled to share with you my very first Git project - a labor of love, dedication, and countless late-night commits. 🚀
Explore the code, unearth its nuances, and let me know your thoughts. Your feedback is invaluable and will contribute to the ongoing evolution of this project.
Flag: VishwaCTF{G1tG1gger_2727}
We are given a GitHub repository to investigate. Unfortunately I could not solve this before the CTF ended, but I still attempted it with the help from @rex. Using GitTools, the commits and other repository objects can be extracted for further analysis.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
└─$ sudo bash extractor.sh /vishwa/LearningGit/ /vishwa/Forensics
[sudo] password for kali:
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[+] Found commit: 02adccb9209edc074b17967f062cc60413f64293
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/0-02adccb9209edc074b17967f062cc60413f64293/index.html
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/0-02adccb9209edc074b17967f062cc60413f64293/style.css
[+] Found commit: 41dca9f040deaa65060065ef78523ba44b2c60f1
[+] Found commit: 57f66532b0c6403f95dcfaffa0650f28850d6922
[+] Found commit: 9370bf54bc070fa53c5f2b8b14834db8ed7f3e79
[+] Found commit: aa3306a61a6dc2b4b1fe97ede91c5c843d452c58
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f1.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f2.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f3.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f4.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f5.txt
[+] Found commit: db01ffe29d0ea57655fcd880dea8816cb2d74d9f
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f1.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f2.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f3.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f4.txt
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f5.txt
[+] Found commit: ebf967130d550a180f7e3fda47a5ca96bb442c81
[+] Found file: /mnt/hgfs/sharedfolder/vishwa/Forensics/6-ebf967130d550a180f7e3fda47a5ca96bb442c81/Screenshot 2024-03-01 151511.png
Analyzing each text file manually, the flag seems to be broken up into index strings. So I went ahead to grep the word string and got parts of the flag. However, index 6, 7 and 8 was missing from the results obtained.
1
2
3
4
5
6
7
8
9
10
└─$ grep -rni "string" .
./0-02adccb9209edc074b17967f062cc60413f64293/index.html:116: string[3: 6] = G1g
./2-57f66532b0c6403f95dcfaffa0650f28850d6922/commit-meta.txt:6:string[0] = G string[1] = 1 string[2] = t
./4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f4.txt:6:string -- VishwaCTF{}
./4-aa3306a61a6dc2b4b1fe97ede91c5c843d452c58/f4.txt:8:HERE -- 0th Index of string is V.
./5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f4.txt:5:string[9] = _
./5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f4.txt:6:string[10] = 2
./5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f4.txt:7:string[11] = 7
./5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f4.txt:8:string[12] = 2
./5-db01ffe29d0ea57655fcd880dea8816cb2d74d9f/f4.txt:9:string[13] = 7
Going through the folders again, a PNG file can be found which contains the letters for index 6, 7 and 8.
Router |port| [Forensics]
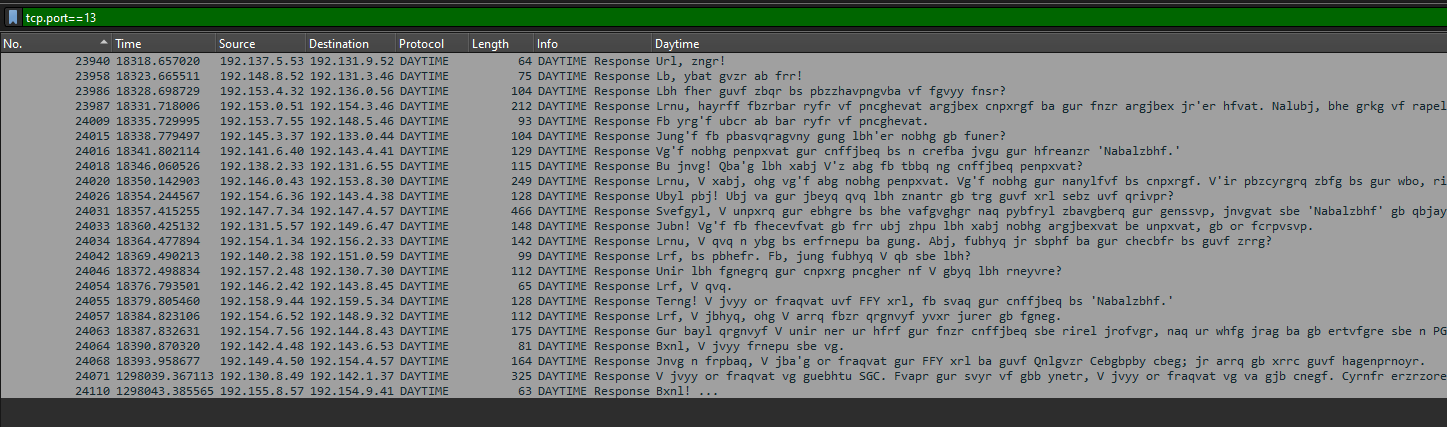
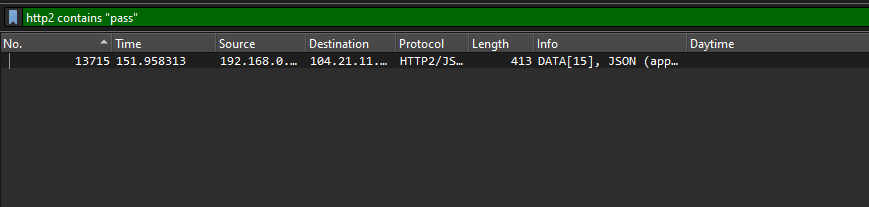
Question: There’s some unusual traffic on the daytime port, but it isn’t related to date or time requests. Analyze the packet capture to retrieve the flag.
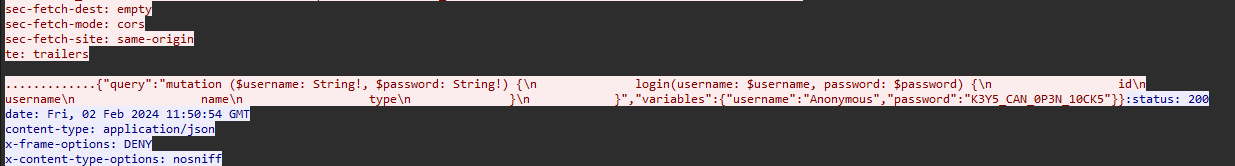
Flag: VishwaCTF{K3Y5_CAN_0P3N_10CK5}
We are given a PCAP file to investigate. Researching online about daytime port, the port for daytime protocol seems to be port 13. Looking at the packets, there seems to be encoded text that holds valuable information. This is pretty guessy but the encoded text was encoded with Vigenère using keyword nnn according to this decoder website.
The decoded text:
1
2
3
4
5
6
7
8
9
10
11
Hey, mate!
Yo, long time no see! You sure this mode of communication is still safe?
Yeah, unless someone else is capturing network packets on the same network we're using. Anyhow, our text is encrypted, and it would be difficult to interpret. So let's hope no one else is capturing. What's so confidential that you're about to share? It's about cracking the password of a person with the username 'Anonymous.'
Oh wait! Don't you know I'm not so good at password cracking?
Yeah, I know, but it's not about cracking. It's about the analysis of packets. I've completed most of the job, even figured out a way to get the session key to decrypt and decompress the packets. Holy cow! How in the world did you manage to get this key from his device? Firstly, I hacked the router of our institute and closely monitored the traffic, waiting for 'Anonymous' to download some software that requires admin privilege to install. Once he started the download, I, with complete control of the router, replaced the incoming packets with the ones I created containing malicious scripts, and thus gained a backdoor access to his device. The further job was a piece of cake.
Whoa! It's so surprising to see how much you know about networking or hacking, to be specific.
Yeah, I did a lot of research on that. Now, should we focus on the purpose of this meet? Yes, of course. So, what should I do for you?
Have you started the packet capture as I told you earlier?
Yes, I did. Great! I will be sending his SSL key, so find the password of 'Anonymous.' Yes, I would, but I need some details like where to start. The only details I have are he uses the same password for every website, and he just went on to register for a CTF event.
Okay, I will search for it. Wait a second, I won't be sending the SSL key on this Daytime Protocol port; we need to keep this untraceable. I will be sending it through FTP. Since the file is too large, I will be sending it in two parts. Please remember to merge them before using it. Additionally, some changes may be made to it during transfer due to the method I'm using. Ensure that you handle these issues.
Okay! ...
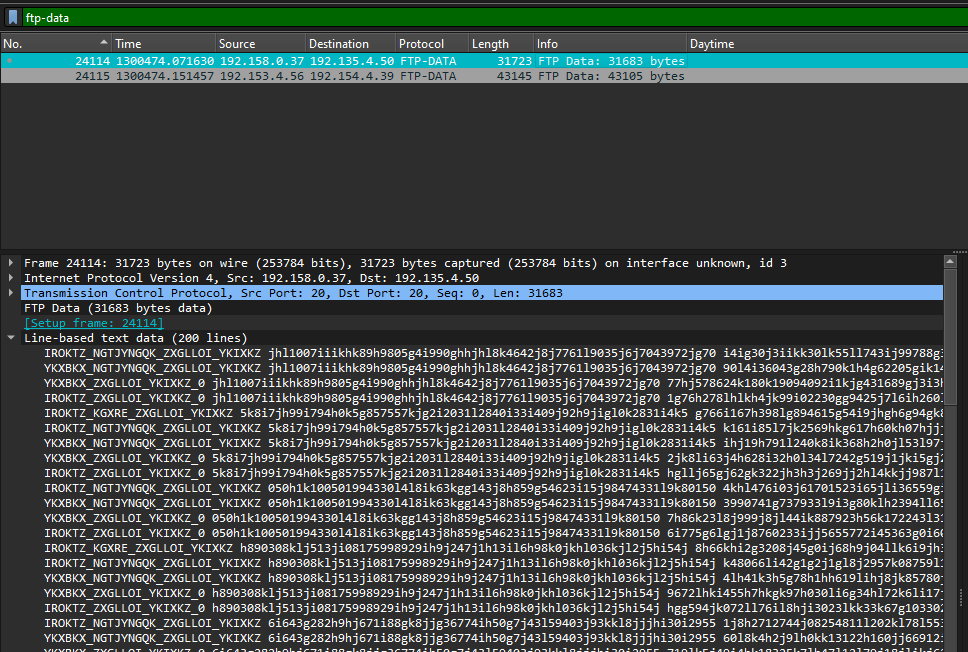
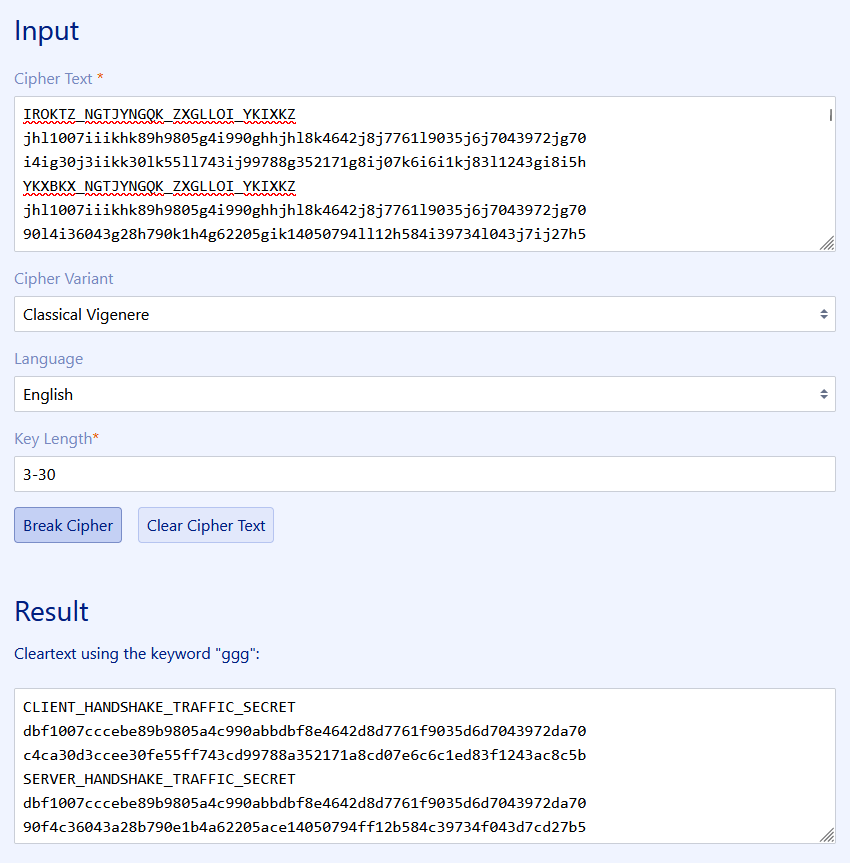
The flag was the password of the user “Anonymous” and the hacker managed to steal a SSL key to encrypt packets. It also mentions that the SSL key is sent to another hacker via FTP. Analyzing FTP packets, the encoded SSL key can be identified.
Again, I randomly guessed Vigenère with the same site and succesfully extracted both PSK log files and imported them to the PCAP file.
After decrypting the TLS packets, the password can be identified from a HTTP2 packet.
Mysterious Old Case [Steganography]
Question: You as a FBI Agent, are working on a old case involving a ransom of $200,000. After some digging you recovered an audio recording.
Flag: VishwaCTF{1_W!LL_3E_B@CK}
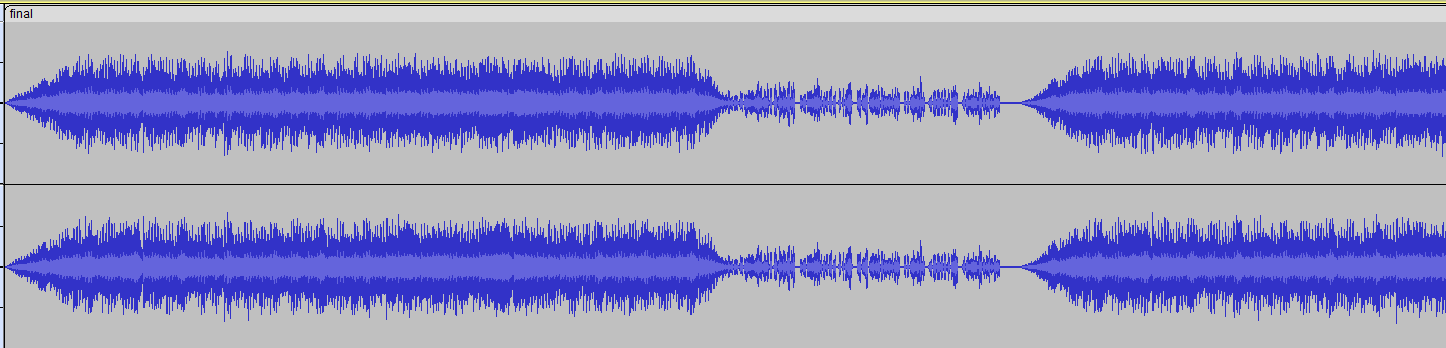
We are given a MP3 audio file to investigate. Analyzing it on Audacity, it seems that there were hidden audio messages in them.
Listening to the hidden audio messages, the audio seems to be reversed, so I reversed the whole audio and used this site to get the transcript of the reversed audio.
The transcript:
1
2
3
4
5
6
7
8
Cooper.
It is 24 November 1971.
Now I have left from Seattle and headed towards Reno.
I have got all my demands fulfilled.
I have done some changes in the flight log and uploaded it to the remote server.
The file is encrypted.
The hint for description is the airline I was flying in.
Most importantly, the secret key is split and hidden in every element of the Fibonacci series, starting from two.
Spending several minutes looking for the encrypted file, I managed to find a suspicious Google Drive link from the metadata of the MP3 audio file which had the encrypted file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
└─$ exiftool final.mp3
ExifTool Version Number : 12.76
File Name : final.mp3
Directory : .
File Size : 2.6 MB
File Modification Date/Time : 2024:03:02 23:19:36-05:00
File Access Date/Time : 2024:03:03 04:14:51-05:00
File Inode Change Date/Time : 2024:03:02 23:19:36-05:00
File Permissions : -rwxrwxrwx
File Type : MP3
File Type Extension : mp3
MIME Type : audio/mpeg
MPEG Audio Version : 1
Audio Layer : 3
Audio Bitrate : 128 kbps
Sample Rate : 44100
Channel Mode : Stereo
MS Stereo : Off
Intensity Stereo : Off
Copyright Flag : False
Original Media : False
Emphasis : None
ID3 Size : 320209
Title : Unknown
Artist : Anonymous
Track : 727/305
Album : Cooper
Recording Time : 1971
Genre : the zip file is 100 MB not 7 GB
Original Release Time : 0001
Band : DB Cooper
Comment : password for the zip is all lowecase with no spaces
User Defined URL : https://drive.google.com/file/d/1bkuZRLKOGWB7tLNBseWL34BoyI379QbF/view?usp=drive_lin
User Defined Text : (purl) https://drive.google.com/file/d/1bkuZRLKOGWB7tLNBseWL34BoyI379QbF/view?usp=drive_lin
Picture MIME Type : image/jpeg
Picture Type : Front Cover
Picture Description : Front Cover
Picture : (Binary data 158421 bytes, use -b option to extract)
Date/Time Original : 1971
Duration : 0:02:22 (approx)
The URL redirects to a ZIP file filled with flight logs. As the question mentioned, the password is the airline Cooper was flying in. Thankfully, I am a huge fan of DB Cooper so I knew the airline name was Northwest Orient Airlines. Extracting the files, many flight logs can be obtained. The flight DB Cooper was in was known to be Flight #305. Reading the log files, it seems that the flag was broken up into pieces with bogus text between them. The flag can be obtained manually from the bogus logs.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
1971-11-24 06:22:08.531691 - ATT - Boeing 727
V
i
1971-11-24 07:31:08.531691 - HWR - Boeing 727
s
1971-11-24 06:22:08.531691 - ATT - Boeing 727
1971-11-24 07:31:08.531691 - HWR - Boeing 727
h
1971-11-24 06:22:08.531691 - ATT - Boeing 727
1971-11-24 06:22:08.531691 - ATT - Boeing 727
1971-11-24 06:22:08.531691 - ATT - Boeing 727
1971-11-24 07:31:08.531691 - HWR - Boeing 727
w
1971-11-24 07:31:08.531691 - HWR - Boeing 727
1971-11-24 06:22:08.531691 - ATT - Boeing 727
1971-11-24 06:22:08.531691 - ATT - Boeing 727
1971-11-24 07:31:08.531691 - HWR - Boeing 727
1971-11-24 07:31:08.531691 - HWR - Boeing 727
1971-11-24 07:31:08.531691 - HWR - Boeing 727
1971-11-24 06:22:08.531691 - ATT - Boeing 727
a
---SNIP---
Secret Code [Steganography]
Question: Akshay has a letter for you and need your help.
Flag: VishwaCTF{th15_15_4_5up3r_53cr3t_c0d3_u53_1t_w153ly_4nd_d0nt_5h4re_1t_w1th_4ny0ne}
The question gave us a JPG file and text file to investigate. The text file seem to be be a letter from Akshay.
1
2
3
4
5
6
7
8
9
10
11
To,
VishwaCTF'24 Participant
I am Akshay, an ex employee at a Tech firm. Over all the years, I have been trading Cypto currencies and made a lot of money doing that. Now I want to withdraw my money, but I'll be charged a huge tax for the transaction in my country.
I got to know that you are a nice person and also your country doesn't charge any tax so I need your help.
I want you to withdraw the money and hand over to me. But I feel some hackers are spying on my internet activity, so I am sharing this file with you. Get the password and withdraw it before the hackers have the access to my account.
Your friend,
Akshay
Analyzing the JPG file, a ZIP file seems to be embedded within it.
1
2
3
4
5
6
7
8
└─$ binwalk -e confidential.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
116247 0x1C617 Zip archive data, at least v2.0 to extract, compressed size: 72486, uncompressed size: 72530, name: 5ecr3t_c0de.zip
188778 0x2E16A Zip archive data, at least v2.0 to extract, compressed size: 170, uncompressed size: 263, name: helper.txt
189177 0x2E2F9 End of Zip archive, footer length: 22
Extracting the ZIP file, another password-protected ZIP file and a text file containing a hint can be obtained. The hint mentioned something about the password being 6 digit numbers.
1
2
3
Hey buddy, I'm really sorry if this takes long for you to get the password. But it's a matter of $10,000,000 so I can't risk it out.
"I really can't remember the password for zip. All I can remember is it was a 6 digit number. Hope you can figure it out easily"
So I created a script to generated a wordlist with 6 digit numbers and used John the Ripper to crack it.
1
2
3
4
5
6
7
8
$ zip2john 5ecr3t_c0de.zip > secret.hash
$ john --wordlist=sixdigits.txt secret.hash
$ john --show secret.hash
5ecr3t_c0de.zip/5ecr3t_c0de.txt:945621:5ecr3t_c0de.txt:5ecr3t_c0de.zip:5ecr3t_c0de.zip
5ecr3t_c0de.zip/info.txt:945621:info.txt:5ecr3t_c0de.zip:5ecr3t_c0de.zip
2 password hashes cracked, 0 left
Extracting the ZIP file, two text files can be obtained. One of them was random numbers while the other had another hint. The hint mentioned something about the numbers being related to the given image (confidential.jpg).
1
What are these random numbers? Is it related to the given image? Maybe you should find it out by yourself
Analyzing the numbers, they seem to either be (x,y) coordinates or pixels.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(443, 1096)
(444, 1096)
(445, 1096)
(3220, 1096)
(3221, 1096)
(38, 1097)
(39, 1097)
(43, 1097)
(80, 1097)
(81, 1097)
(83, 1097)
(93, 1097)
(95, 1097)
---SNIP---
I used ChatGPT to generate a script that will color a white pixel on a blank image which easily reveals the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
from PIL import Image
def read_coordinates(file_path):
with open(file_path, 'r') as f:
lines = f.readlines()
coordinates = []
for line in lines:
x, y = line.replace('(', '').replace(')', '').split(',')
coordinates.append((int(x), int(y)))
return coordinates
def draw_white_pixels(image_path, coordinates, output_path):
img = Image.open(image_path)
for coord in coordinates:
img.putpixel(coord, (255, 255, 255)) # RGB value for white
img.save(output_path)
image_path = '/confidential.jpg'
file_path = '/5ecr3t_c0de.txt'
output_path = 'output_image.png'
coordinates = read_coordinates(file_path)
draw_white_pixels(image_path, coordinates, output_path)
print(f"Image with white pixels at the given coordinates has been saved as {output_path}.")