UTCTF 2024 - Writeups
This is a writeup for some forensics challenges from UTCTF 2024. I was super happy that I almost managed to solve every forensics challenges solo during this CTF, showing how much of an improvement I’ve gain over the past few months. Overall, very proud of this writeup. PS: an OSINT category should be created instead of mixing in with forensics.
Contracts [Forensics]
Question: Magical contracts are hard. Occasionally, you sign with the flag instead of your name. It happens.
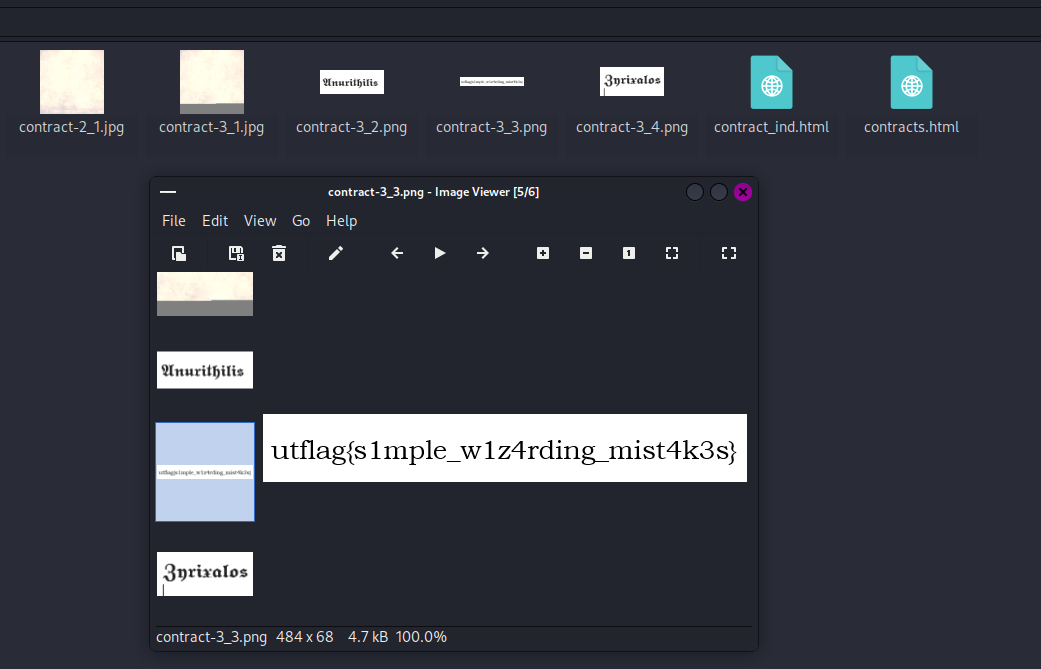
Flag: utflag{s1mple_w1z4rding_mist4k3s}
We are given a PDF file to investigate. The PDF file seems to be a contract with signature images below it. Analyzing it with binwalk, nothing interesting can be found other than the text.
Researching on PDF signatures, I stumbled upon this video that talks about pdf layer extraction. By converting the PDF file to html, the flag can be obtained.
1
2
3
4
└─$ pdftohtml contract.pdf
Page-1
Page-2
Page-3
A Very Professional Website [Forensics]
Question: Web dev skills go brrr http://puffer.utctf.live:8549
Flag: utflag{gitR3fl0g}
We are given an unfinished website to investigate. A forensics challenge that require web tactics, seems interesting. I used gobuster to enumerate directories and found out the website had a hidden .git file within it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ gobuster dir -u http://puffer.utctf.live:8549 -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://puffer.utctf.live:8549
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.git/HEAD (Status: 200) [Size: 21]
/index.html (Status: 200) [Size: 590]
Progress: 4614 / 4615 (99.98%)
===============================================================
Finished
===============================================================
With my knowledge on .git forensics, GitTools can be used to dump the .git folder and extract objects from it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
└─$ bash gitdumper.sh http://puffer.utctf.live:8549/.git/ ~/Desktop/bin
###########
# GitDumper is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[*] Destination folder does not exist
[+] Creating /home/kali/Desktop/bin/.git/
[+] Downloaded: HEAD
[-] Downloaded: objects/info/packs
[+] Downloaded: description
[+] Downloaded: config
[+] Downloaded: COMMIT_EDITMSG
[+] Downloaded: index
[-] Downloaded: packed-refs
[-] Downloaded: refs/heads/master
[-] Downloaded: refs/remotes/origin/HEAD
[-] Downloaded: refs/stash
[+] Downloaded: logs/HEAD
[-] Downloaded: logs/refs/heads/master
[-] Downloaded: logs/refs/remotes/origin/HEAD
[-] Downloaded: info/refs
[+] Downloaded: info/exclude
[-] Downloaded: /refs/wip/index/refs/heads/master
[-] Downloaded: /refs/wip/wtree/refs/heads/master
[-] Downloaded: objects/00/00000000000000000000000000000000000000
[+] Downloaded: objects/e2/a975aa4dc20fd279591267b64617f73ede199e
[+] Downloaded: objects/bb/a639202cd2e6228b65a4d20bf0e9c38dd4e479
[+] Downloaded: objects/9d/525e298e3b9fc70c9e8110b593c65c8b897361
[+] Downloaded: objects/d6/cebe17a2ef4c5eec1f7ee1ed1b77d9a66be79c
[+] Downloaded: objects/73/f3e2181302f0aef5da05ae4f4948aba58ebded
[+] Downloaded: objects/45/0b6bb9e3944e09e345348840a0311e7b70e2e0
[+] Downloaded: objects/9c/8220f43c7c86d4b7d284c42c9cd515f15e79c8
[+] Downloaded: objects/1d/2961fb02140ea819212ac081b0291c323fd056
└─$ bash extractor.sh ~/Desktop/bin/ ~/Desktop/bin
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[+] Found commit: e2a975aa4dc20fd279591267b64617f73ede199e
[+] Found file: /home/kali/Desktop/bin/0-e2a975aa4dc20fd279591267b64617f73ede199e/documentation.html
[+] Found file: /home/kali/Desktop/bin/0-e2a975aa4dc20fd279591267b64617f73ede199e/index.html
[+] Found file: /home/kali/Desktop/bin/0-e2a975aa4dc20fd279591267b64617f73ede199e/links.html
[+] Found commit: bba639202cd2e6228b65a4d20bf0e9c38dd4e479
[+] Found file: /home/kali/Desktop/bin/1-bba639202cd2e6228b65a4d20bf0e9c38dd4e479/documentation.html
[+] Found file: /home/kali/Desktop/bin/1-bba639202cd2e6228b65a4d20bf0e9c38dd4e479/index.html
[+] Found file: /home/kali/Desktop/bin/1-bba639202cd2e6228b65a4d20bf0e9c38dd4e479/links.html
[+] Found file: /home/kali/Desktop/bin/1-bba639202cd2e6228b65a4d20bf0e9c38dd4e479/secrets.html
Checking the objects, the flag can be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
└─$ tree *
0-e2a975aa4dc20fd279591267b64617f73ede199e
├── commit-meta.txt
├── documentation.html
├── index.html
└── links.html
1-bba639202cd2e6228b65a4d20bf0e9c38dd4e479
├── commit-meta.txt
├── documentation.html
├── index.html
├── links.html
└── secrets.html
2 directories, 9 files
└─$ cat 1-bba639202cd2e6228b65a4d20bf0e9c38dd4e479/secrets.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Secrets</title>
</head>
<body>
<p>It's no big deal if I store secrets here, right? I mean I'll never merge it in to the main branch, so no one but me should ever be able to get here!</p>
<ul>
<li>The moon landings were faked on the moon.</li>
<li>Area 51 does not perform extraterrestrial research. Rather, it is an exclusive resort that only the elites can access.</li>
<li>The government convinced us rocks can think to cover up the fact that computers are actually powered by tiny hamsters on wheels.</li>
<li>The real reason your shoes come untied is to keep you distracted. From what? ... I don't remember, I just got distracted tying my shoe.</li>
<li>Stoplights don't actually help with traffic flow - they are there to test the population's patience and obedience.</li>
<li>Elevators don't actually go up and down. Rather, they transport you to a parallel dimension which contains your desired floor.</li>
<li>The Earth does not exist. #NoEarthSociety</li>
<li>If you squint your eyes, every country's flag contains very tiny text which reads: utflag{gitR3fl0g}</li>
</ul>
</body>
</html>
Study Music [Forensics]
Question: I listen to this while studying for my exams. https://youtu.be/1Cbaa6dO2Yk Note: the audio is the focus of this challenge. The video can be safely ignored.
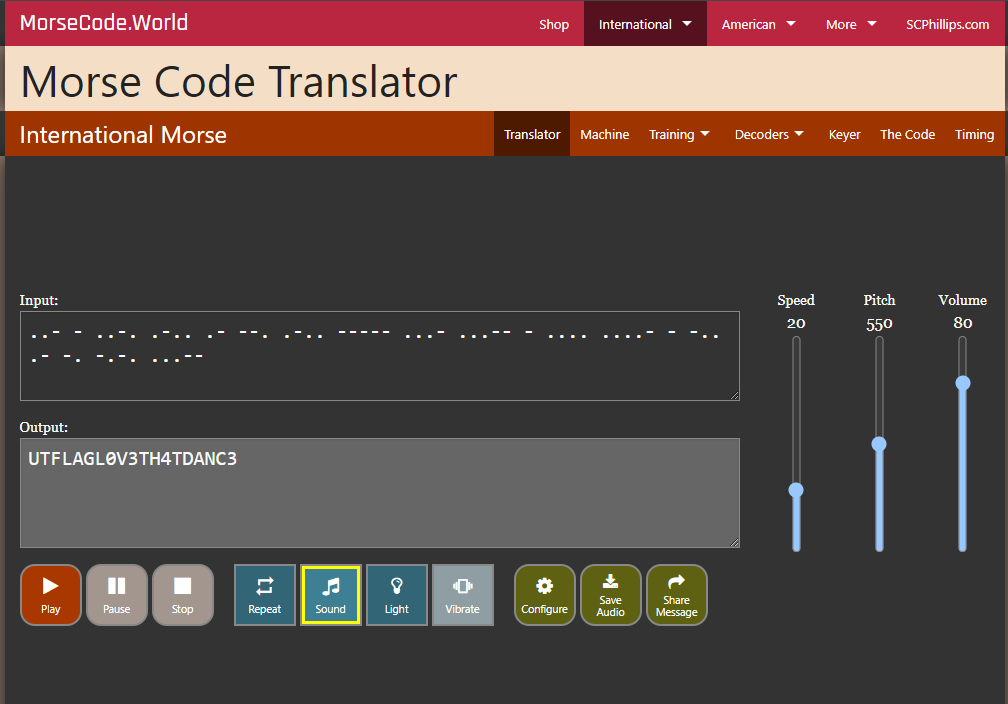
Flag: utflag{L0V3TH4TDANC3}
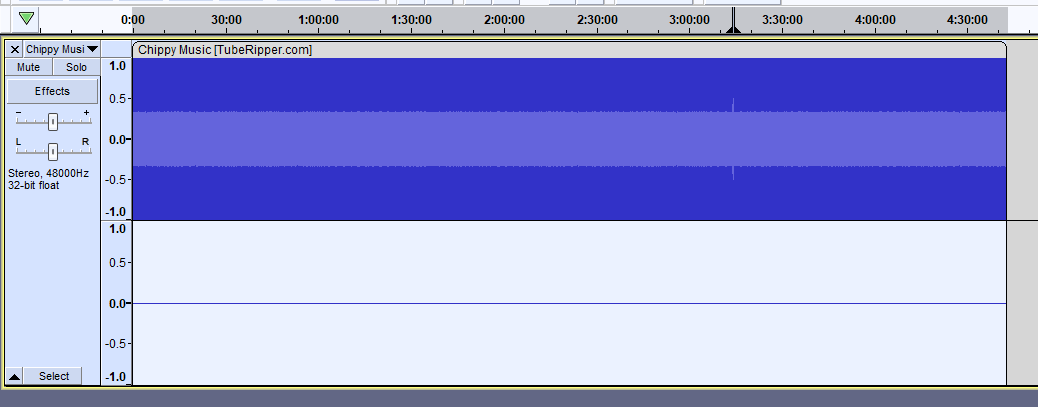
We are given a YouTube video to investigate. Extracting the audio and analyzing it on Audacity, a suspicious spike can be found in this audio.
Listening to the audio spike, it seems that a morse code was embedded within the audio. So I just had to trim that part and listen to it carefully (rip my left ear and sanity). You can also use online spectrogram tools like this to find the morse code.
OSINT 1 [Forensics]
Question: It seems like companies have document leaks all the time nowadays. I wonder if this company has any. (NOTE: It turns out there’s also an actual company named Kakuu in Japan. The real company is not in scope. Please don’t try and hack them.) http://puffer.utctf.live:8756
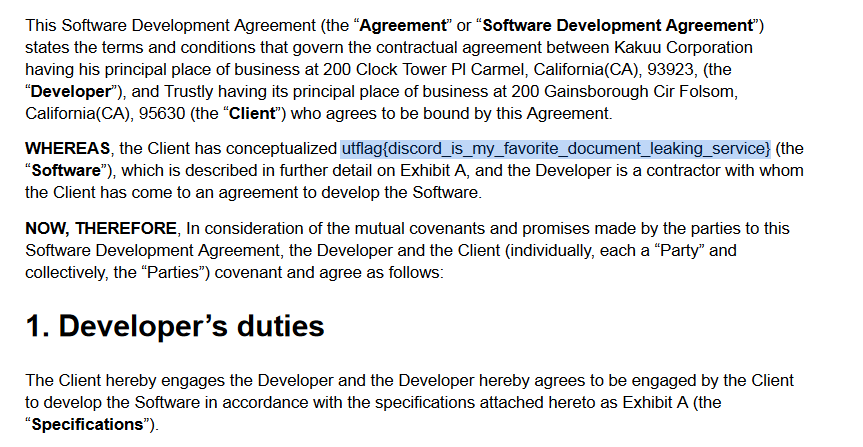
Flag: utflag{discord_is_my_favorite_document_leaking_service}
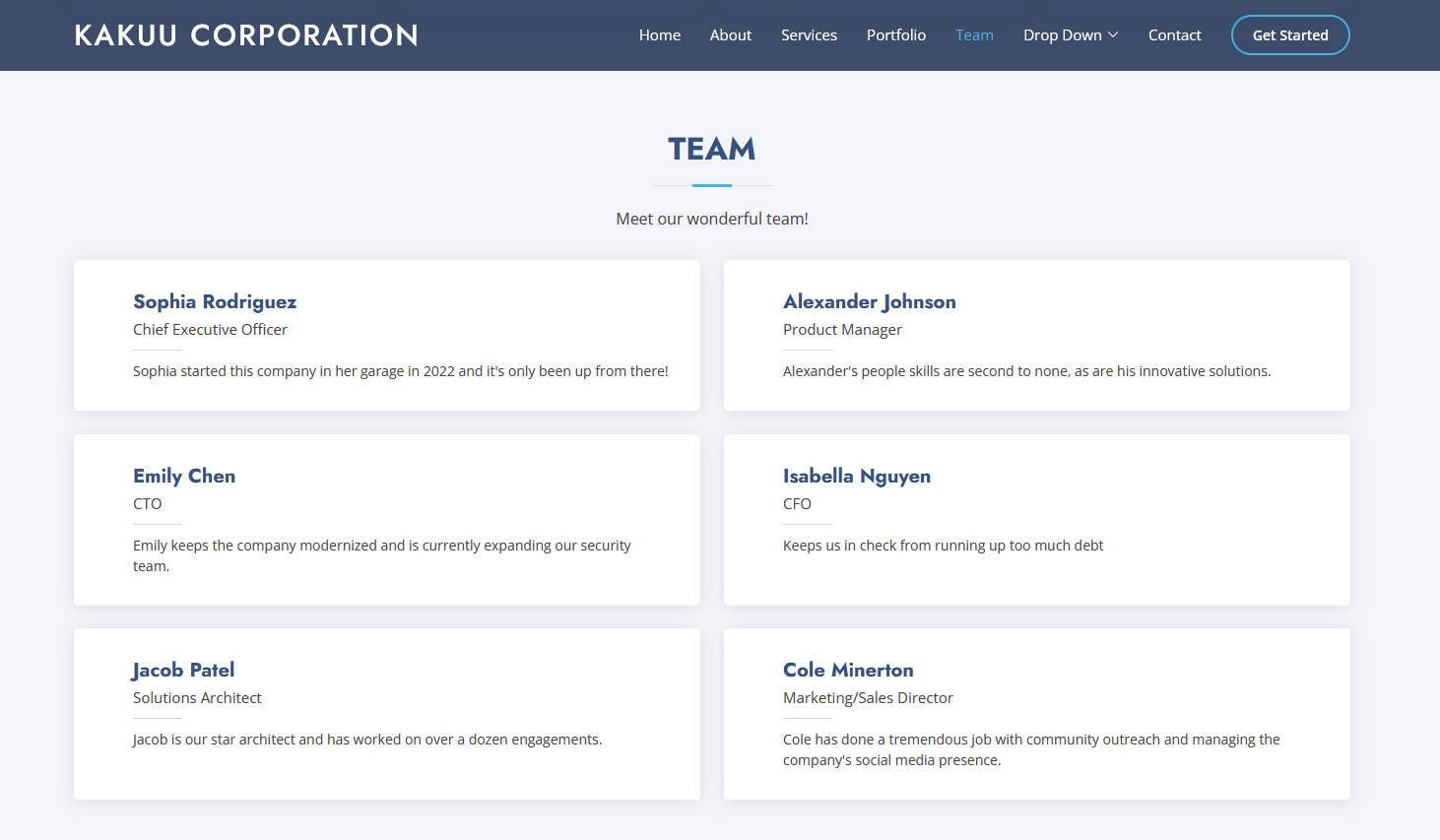
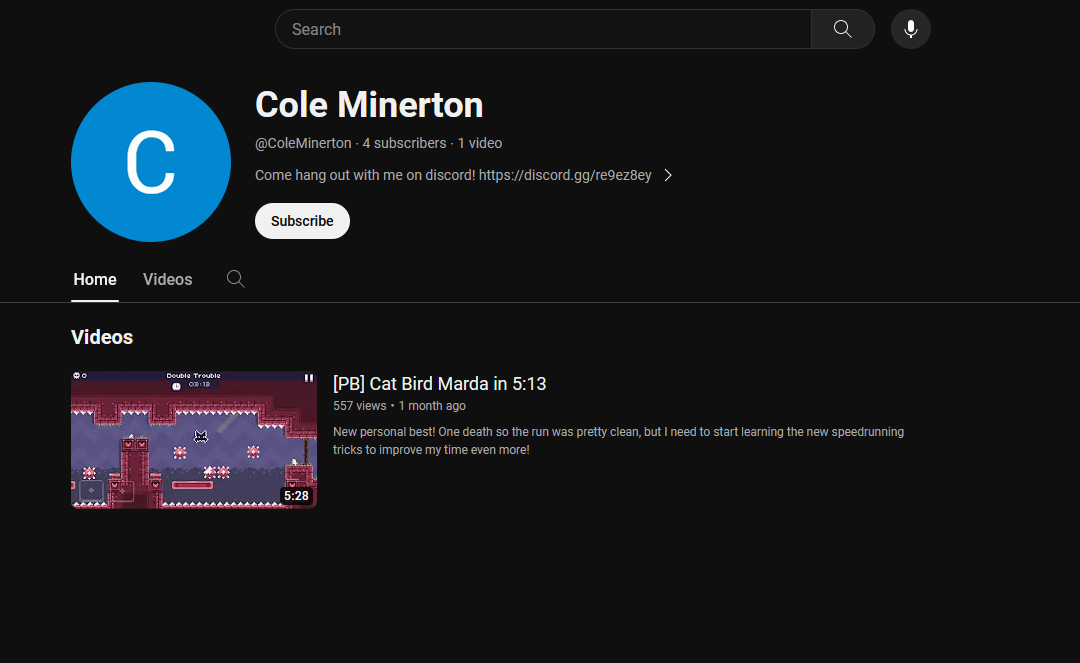
We are given a company website to investigate. After spending a few hours on finding information on Kakuu Corporation, I found out it was just a fictional company name (excluding the company in Japan). Checking out the website again, an employee section can be found.
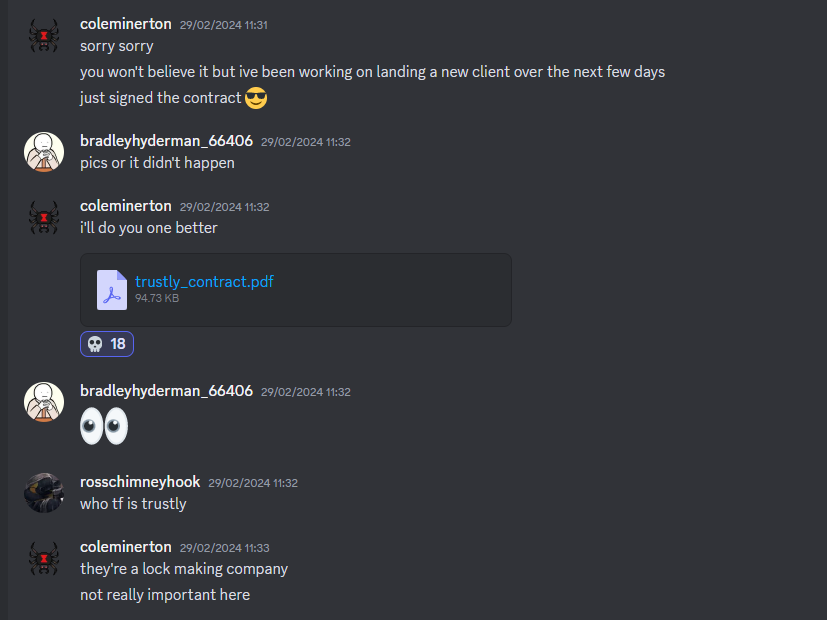
Going through all of them, Cole Minerton seems to have a YouTube channel and other social media accounts. Inside his YouTube channel was a Discord invite link to his server.
Reading the Discord server chat logs, the leaked file can be found and the flag was within in.
OSINT 2 [Forensics]
Question: Can you find where the person you identified in the first challenge lives? Flag format is City,State,Zip. For example, if they live at UT Austin submit Austin,TX,78712. Do not include any spaces in your submission. The submission is also case sensitive, and works with or without utflag{}.
Flag: utflag{Raton,NM,87740}
So we are tasked to find Cole Minerton home area.
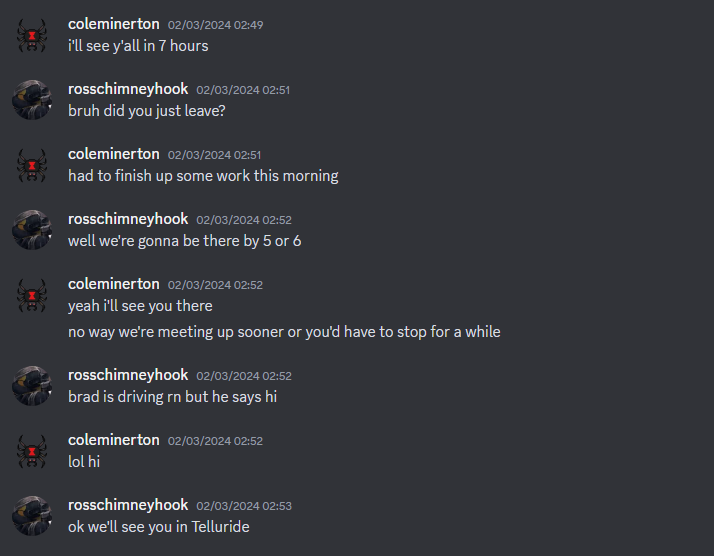
Reading the Discord chat logs again, we know that he recently had a trip to Angel Fire which is located in New Mexico, a place we can start off the search.
We also know that the time it takes from his house to Telluride is about 7 hours.
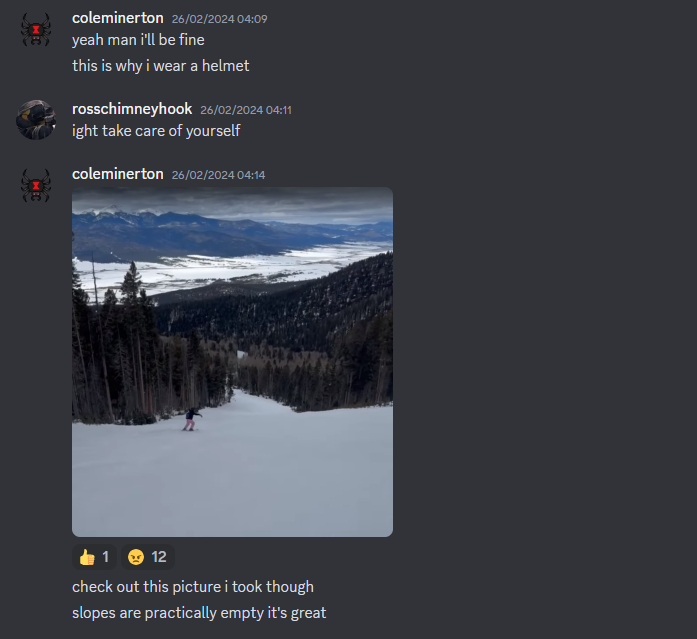
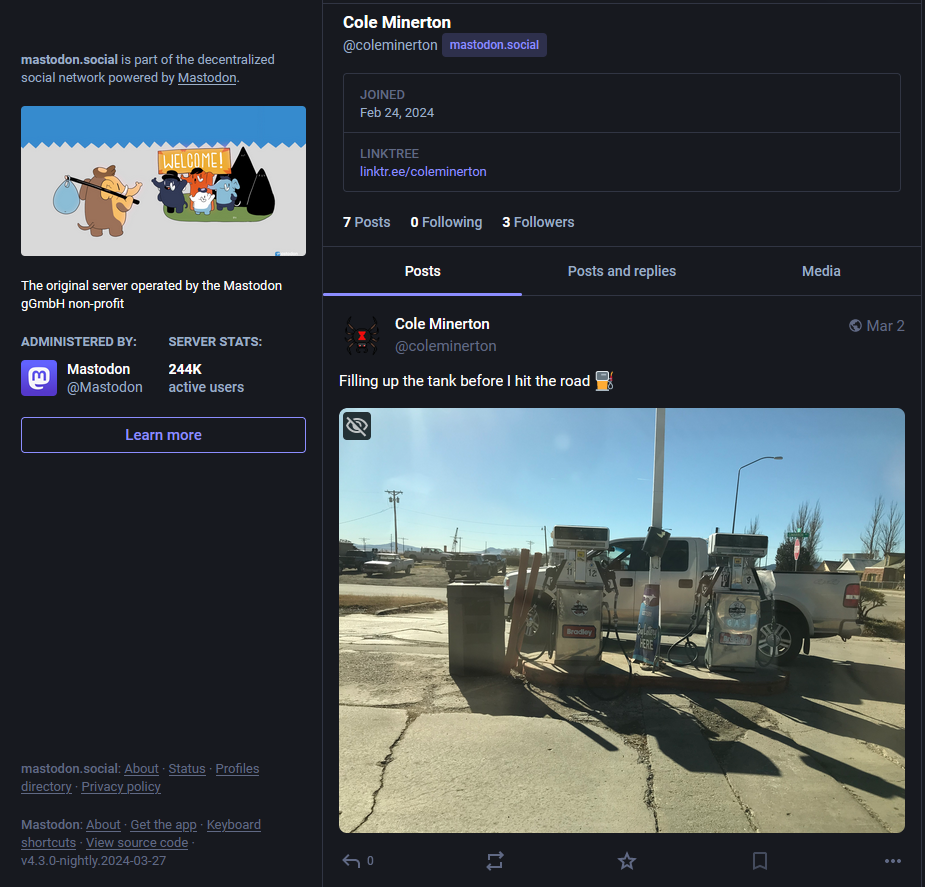
Checking his linktr.ee, we find that his Twitter was basically dead, his Youtube had a speedrun clip, and his Reddit has some posts. However, his mastodon account seems to have pictures of his life events where the most recent post shows that he was in a gas station before going to Telluride.
We can find several important information from the image:
It shows us that the gas station is located somewhere in New Mexico, specifically on a street named Cimarron Ave. The specific gas station can be found based on the street name in New Mexico.
Edit: The sticker that shows Sav-o-Mat was also a huge pinpoint in finding the gas station.
OSINT 3 [Forensics]
Question: Can you find the person’s IP address? Flag format is XXX.XXX.XXX.XXX
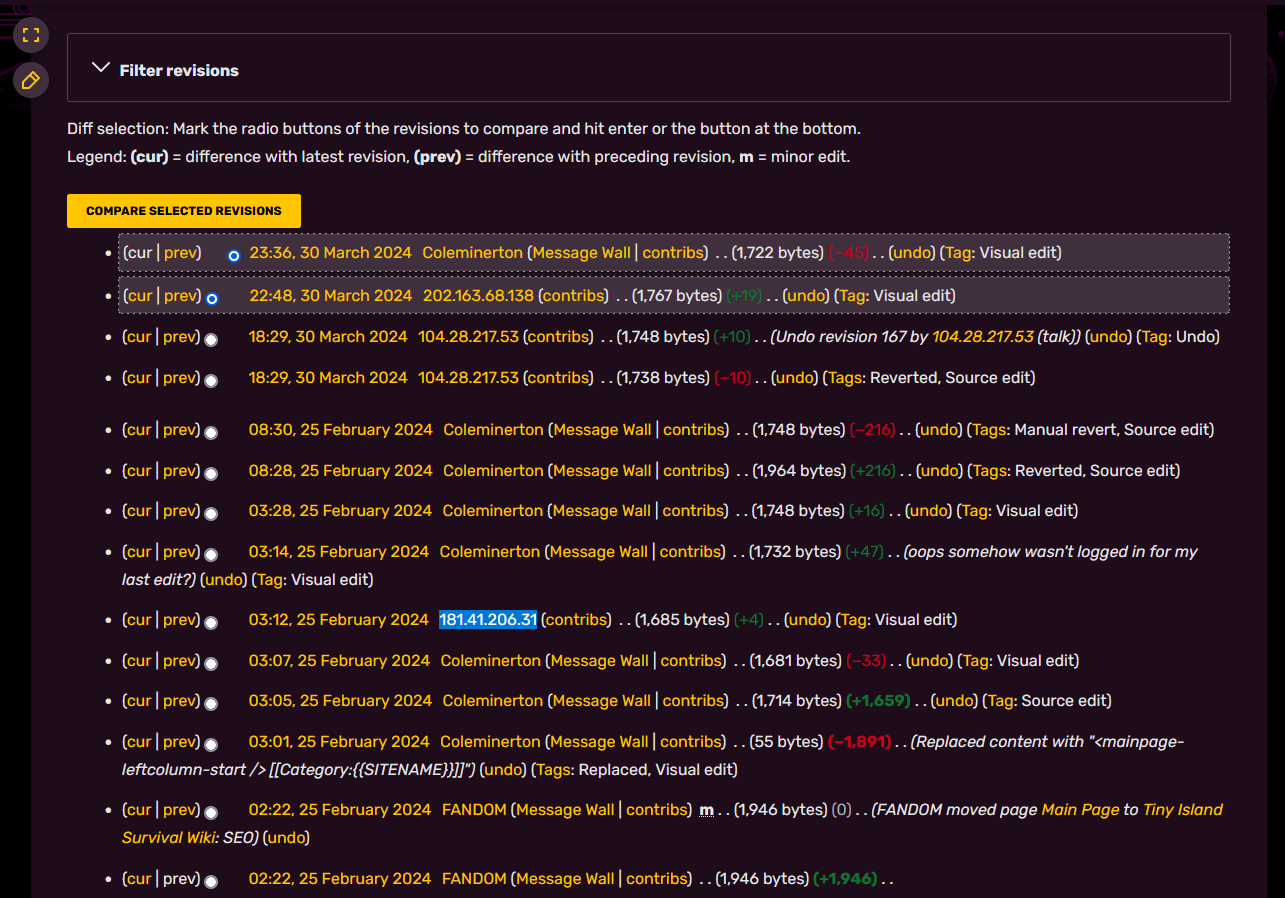
Flag: utflag{181.41.206.31}
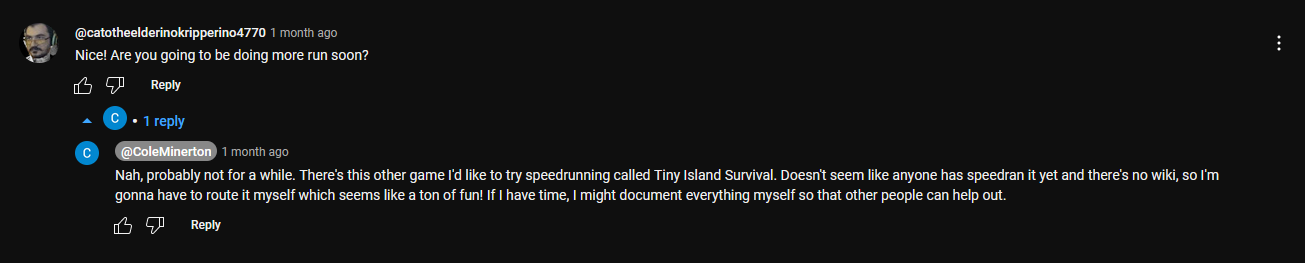
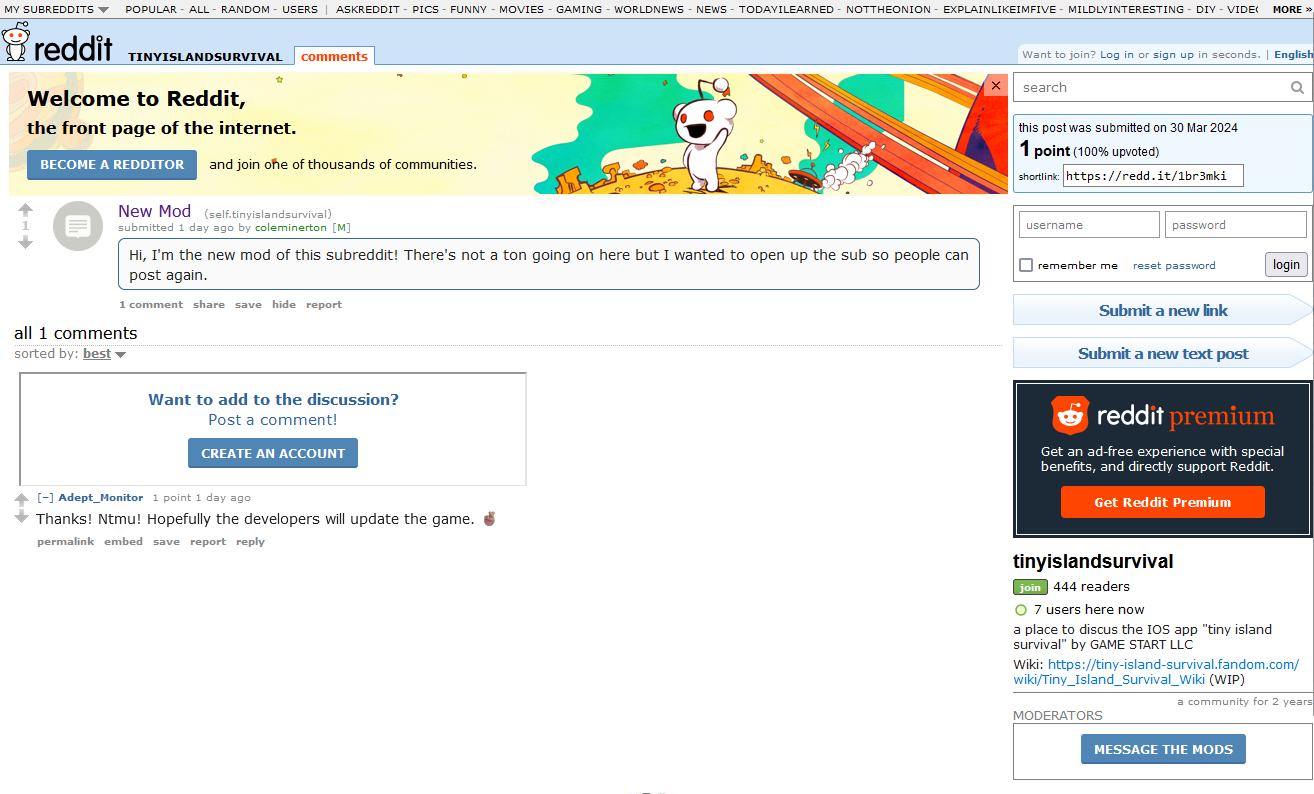
Checking out his speedrun game on Youtube, it seems that he was preparing to speedrun for a game called Tiny Island Survival.
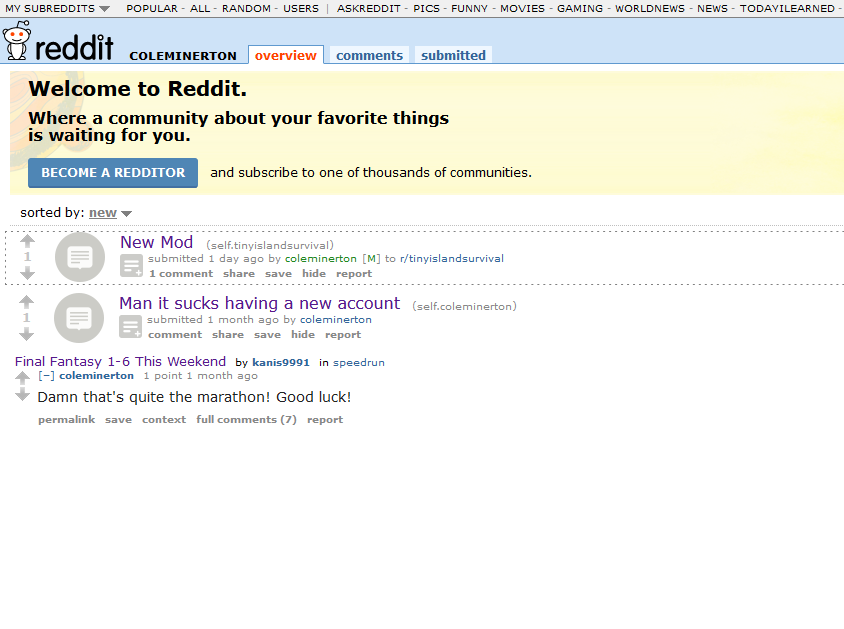
Entering his Reddit account via linktr.ee, it actually leads us to old Reddit for some reason. His most recent Reddit post shows that he became a new moderator in the Tiny Island Survival subreddit.
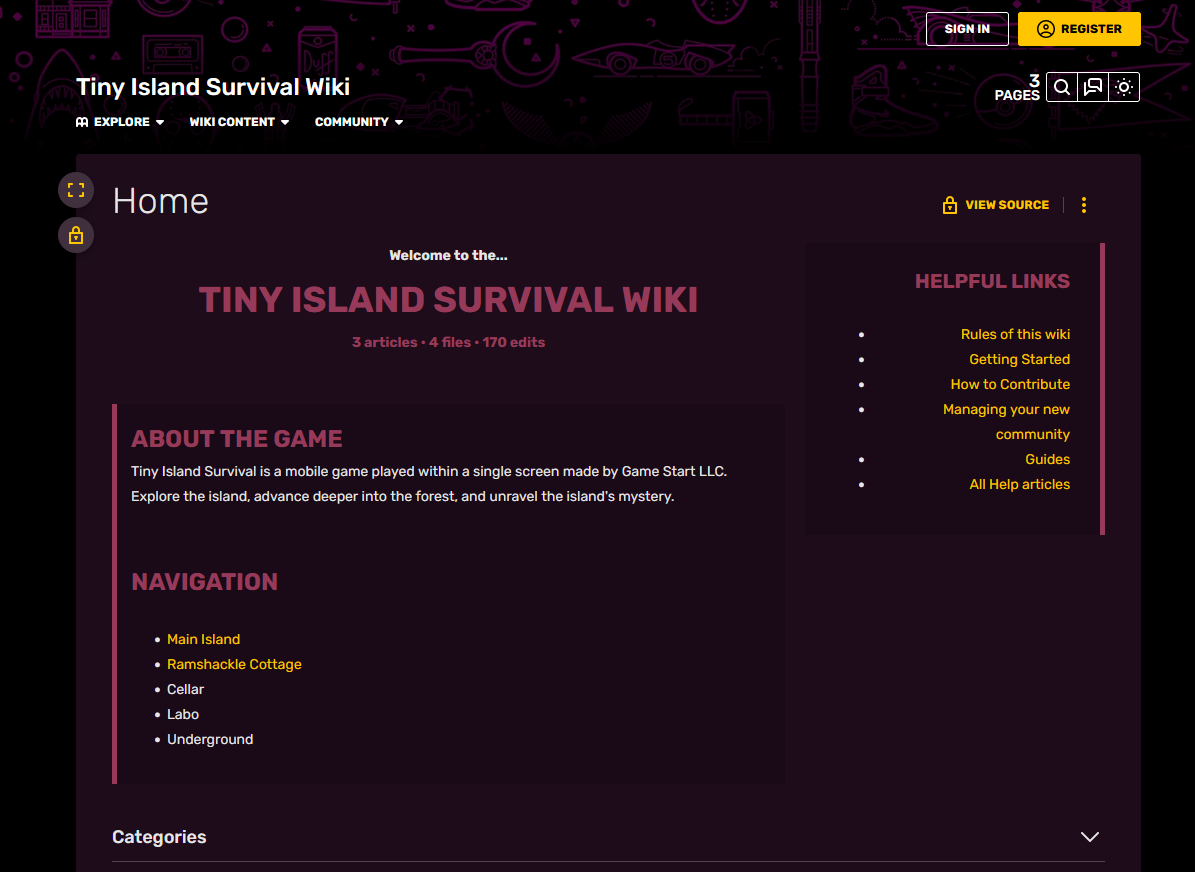
Checking out the post, it seems that a link which leads to a Fandom page of the game can be found at the bottom right of the page.
Fandom works the same way with Wikipedia where public edits are allowed from users. So I checked the edit history of the page and found several IP addresses. One of them was the flag.