SwampCTF 2024 - Writeups
This is a writeup for all forensics and OSINT challenges from SwampCTF 2024. Since SwampCTF released with four other CTFs on the same day, I left the CTF after clearing the two categories since they were way too easy. Hope the authors increase the level of difficulty for veterans like me.
pingpong [Forensics]
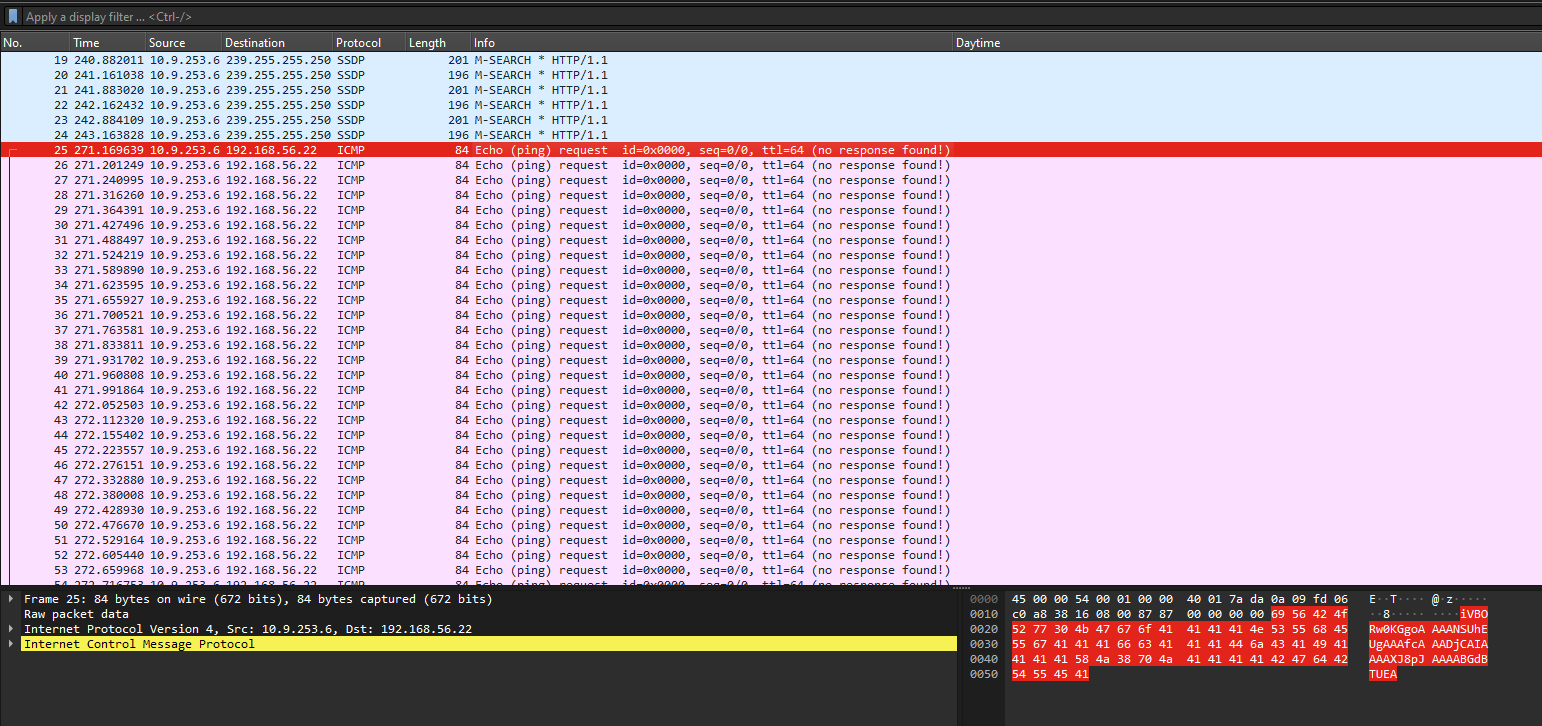
Question: What happened to my traffic??? The pings?!?? They’re taking over!!!! They’re… ping… pong pingpong ping find my pong flag.
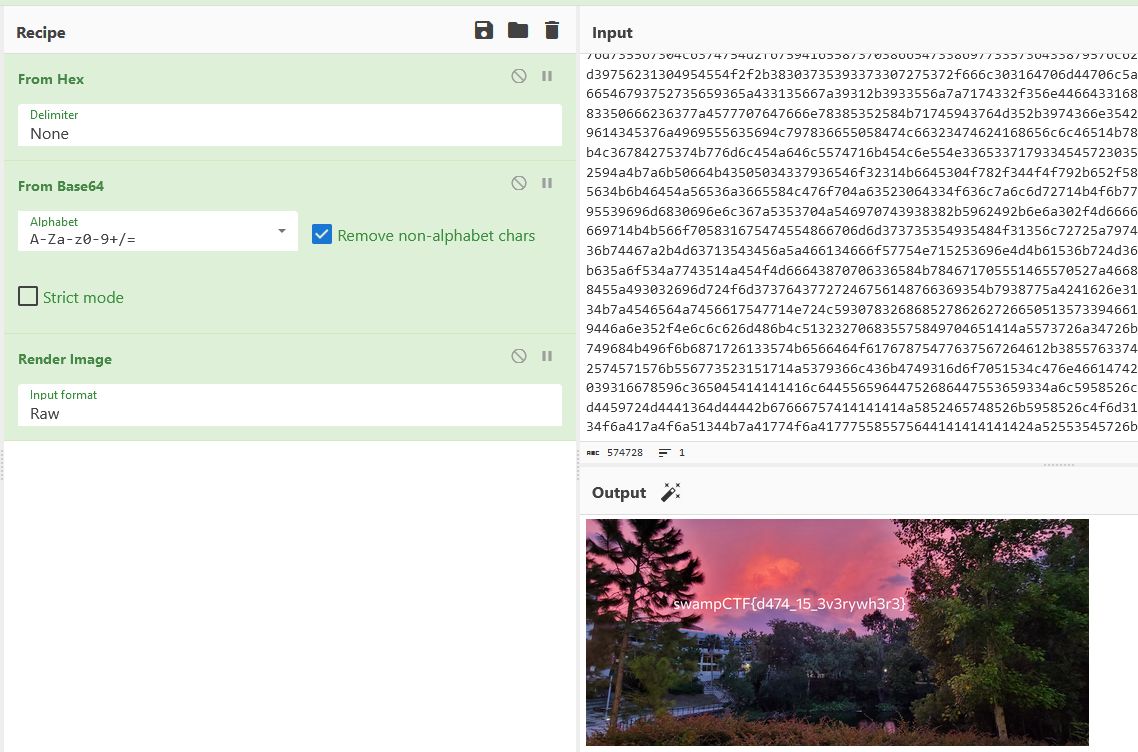
Flag: swampCTF{d474_15_3v3rywh3r3}
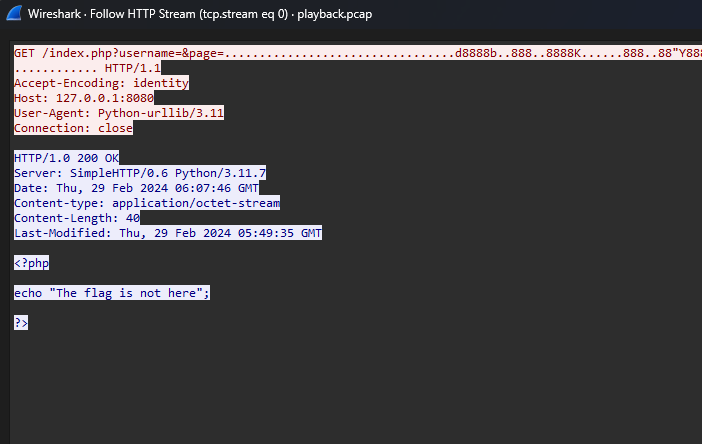
We are given a PCAP file to investigate. Looking at the packets, it seems that the ICMP ping requests are not receiving any responses. However, each ICMP packet had base64 encoded data within them. So I just extracted the encoded data and the flag can be obtained.
1
2
└─$ tshark -r traffic.pcap -Y "icmp.type==8" -T fields -e data | tr -d '\n'
6956424f5277304b47676f414141414e5355684555674141416663414141446a43414941414141584a38704a414141414247644254554541414c4750432f7868425141414143426a53464a4e414142364a6741416749514141506f41414143413641414164544141414f7067414141366d41414146334363756c453841414141426d4a4c523051412f77442f41502b6776616554414141414358424957584d41414173544141414c457745416d707759414141414233524a5455554836414d614552386a504235497a7741416741424a52454655654e7073765865596e5064314876707258357665742f6346734f69394541414a646c496b78536171554e32794a557479695233624b64652b63654c636d39776e63527a3733746878456c66314c6c4955535a45454f77696974775777414c5a672b3837757a4f7a30722f374b2f654d724d35437a4478343873374e547676716539377a6e50656348542f37682f7741415141416768497a786d7436734e75714762686957555737555a30763570667061766c45736c737462423866362b67616e562b5a76462b59643278724a396e41736c746258695943374e6f30746c764c6c616c554c615133543045314c4a684c6d596c4f3064327676786f35344d6f54566443715469436553796154415544654d686d557572693476463565584b3858722b64767a6c57584d784f626534666c3661626c615a4979375078686a684241416742426b327a614545474d7368414141694e5950344678414343455543454b4d73534c4a4d61694e714630643464546730454446317564586c7270536d6131446f79573739672b76666a3843315a336457354a7164455050304e4267667a77575268414b49526751676e4d67424f6543635343454546774949415267516741426f4f436341694541414278777a6a6b5567414d42594c424a6f5032487537394364324d424141414941494341444143494541516351434567685037626841425143434345414e422f755244513356634133633843414441424541515143694441502f316541514541414549494249414151414168414241494241586e777673513454353778787368684f444f482b46664736316e33413057676773416841414375702f6f766b5941774b455148414341674244756272716235373472654f422b6a722b647776313641514743454c68624c6f4141497668714557794f6148734341414545414244366d386f352f2b586467424335463863766e523133517742335478455337754630543544336151684164773935634b79444e37742f39665949494367675141674b4243467950787536322b4765612b772b4251414141416b4941495163654c7676587545536b636f4e2f6553464330382b6448397864653363314c58766e583174704b6672632f643838754c4575416d713135616e313230484b54494444715055336656494f4c4b3276746f567a5135336a6a534d2b734c615459425a4e4a714f786c4b56387070434a4d4f6b716872716943582b3153652f486b667075646e355a4378614e6d752f2b68652f71385843454b43715657654d50724a683778392b2b6d732f4f76487566336e746531705968526264337258785a6e455779455176312f2f3069372f32785035484c6c36662b764870313339383655306d6959696d79674246772b4835536f316a3939354547474d41414264436871697a6f324e685a536d56694375797a446833714c4e6571636979624a6c6d5a795a484b6176564770717164475136467059584f374b3552446979554678534e5558434f4b7971362f6d3144594f6262697a4f353876727369796c5970483744782f4c706e4a2f2b2f3176537171694b557139336e436f45346c456a4b5a524b35615037446f30304e45764362785179732f586c32504a2b4e69476a54392b2b61653262582f71696164336a5737392b6339652b76727a5839365747377434342f4a624e3035646e62396d696e717057654d434f41353154773257694b496f756d55797a6a564e4534497a6835716d4d6454542f346d6e502f5879613639657633564e4973523262455654442b32374b364a465435773561546d576f56764a63474c50356a3148647439564b4b352f34365876462f574b46677044794655434f7850706a7a2f364e444a6f543366506e2f2f31583952596e514f754b4a48526f6331475856395a57713431394a53612b4764662b505539752f643863507239762f6a3266354844536a6256396474662f6232704737652b2b6550764666513172424341414a4551684d4b30624969415244426e584168424b6557635177676478374674477742675756525369435152525a494a6b66435837336b797542344a77686768307a416432774a41534c4b6b617170466e615a705749444f46525a725a684d51574737554c453574775367454e623070414141496c4f7456524968756d785a7a7541414151695441634c6f6e706b524373684950527a4843424a4e774e4d6f34713956716a576254734f326c315a5671765361416f4a7a564c583239575663566c636a456f5a5178786a6c3362314b45494f664d335537475744736b636336466347392b46343442786867436b46555365346533396e66334b70703862586e3634767945724d673162767a77765665717a57704b445964514b4b6c4673346c55574e4d6949513068354947654149414c49414348776b636634414952464d46544872713067614877494c554e536e7755417a44414a4344635839306a6a6e774138674b7444386351415141425168424243414b6b633766505258734549514949497665443353506a34694e4343486d66342f30444143414576632f3367525735434e6261794e6166326e2f314e6b38414b41514564373453414169524336494151412f6f33586342694c3064644245627448383438463764396d7541696149644834506e6f62386a45503754554e52366b51655843434855746a7351415066632b6a457943483274302b4c755a4c4237376f5541425168324762542b31454a3549494c336571415034523148456e726e43344732492b2b6653696a61506878424b41514d6163706f2f30445471416f42467862796778305a3044434f37446a6b4d47646937755a5365565541514754636144614534497978306345525264467554552f2b797631506455694a4b387454736b4b326a4f31635753315536685749344c3333506a782b342b5a7170555367704a663054634f39414473396e646e76762f7a71636e4835774d59394a6a576164694d5453683762636e4275656635766a72386f5a47526135764e48487637644a372f2b31706c7a54563535634f7664786158472b3966665054632f2f76724e6330444744393131647971657074516548527a70485269616d72754e454c5973437771677949706c57516433374a45676f6f775351687a486268713662706f7550304d41554e7352416a44474f6a4e64582f334372353338384a516b5359663348697975727a614d47714f556332685978757a533346713570736871574e4d55444a4d6b394f43422b39343566306f67775778714f3434697939786858656e63357348527a6b7a756433376c31772b4e62692b6135512f477a78545743786576584a49787a6d5579647838364f7467336b4d746b53395831737a637666502f646e3677306c697436735734324f525141414d656d3349335743446f4f64527848434f
Notoriously Tricky Login Mess (Part 1) [Forensics]
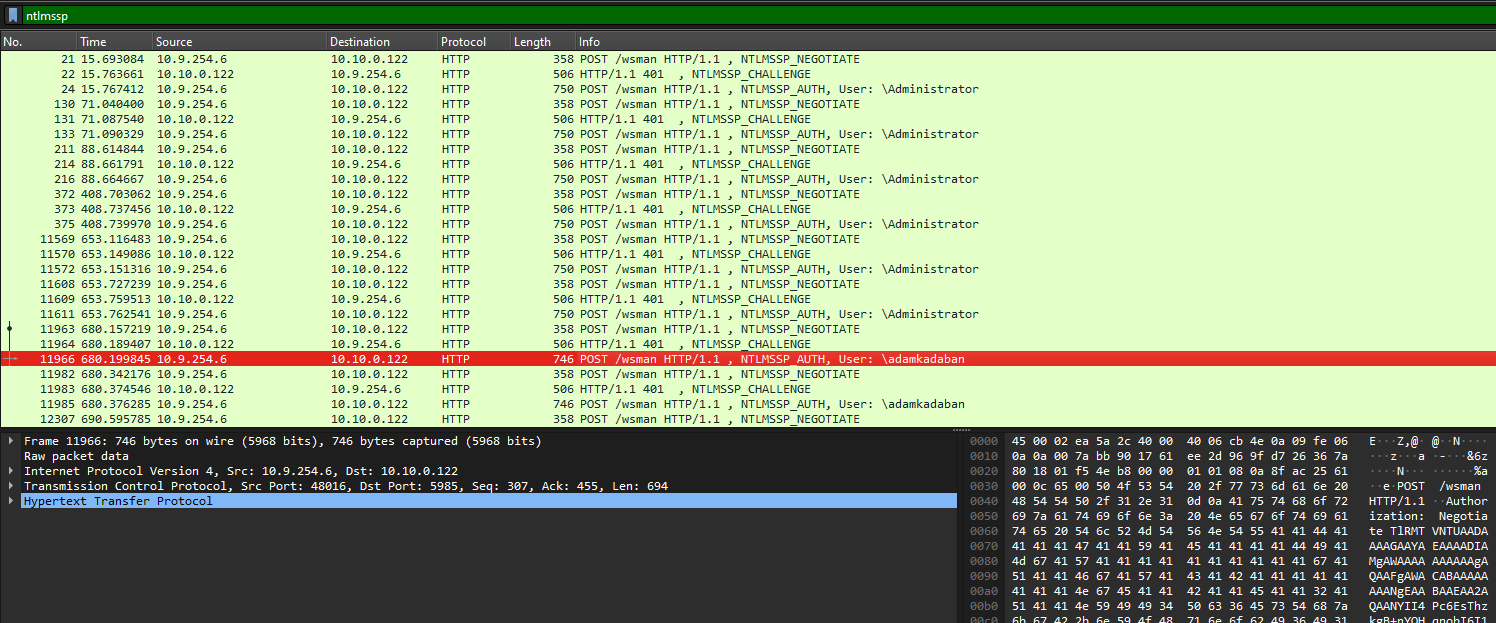
Question: We found out a user account has been compromised on our network. We took a packet capture of the time that we believe the remote login happened. Can you find out what the username of the compromised account is? Flag format: swampCTF{username}
Flag: swampCTF{adamkadaban}
We are given a pcap file to investigate. Looking at the packets, it seems that the attack is slightly similar to this blog. I just filtered the NTLMSSP packets and the username can be found.
New C2 Channel? [Forensics]
Question: Sometimes you can exfiltrate data with more than just plain text. Can you figure out how the attacker smuggled out the flag on our network?
Flag: swampCTF{w3lc0m3_70_7h3_l4nd_0f_7h3_pc4p}
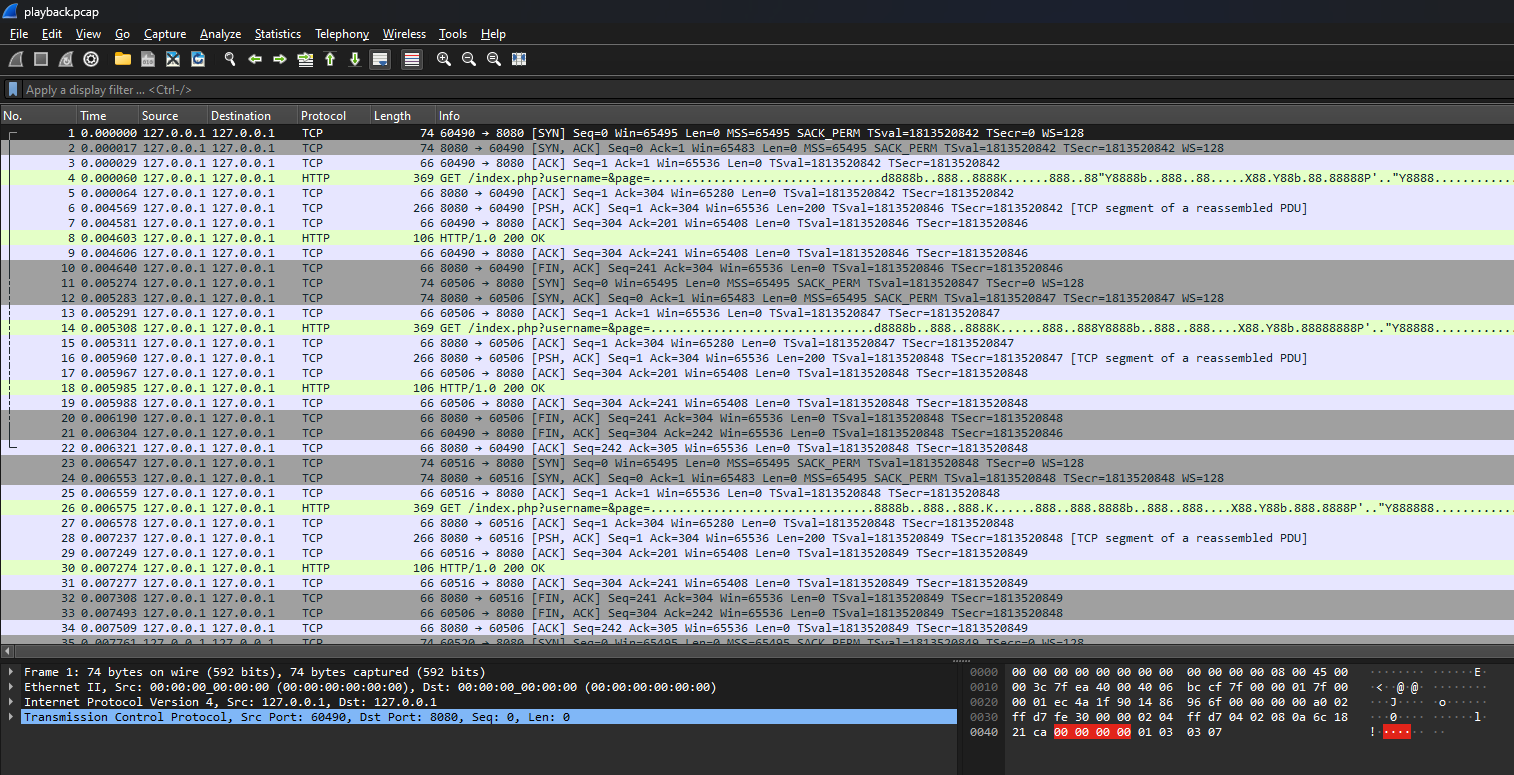
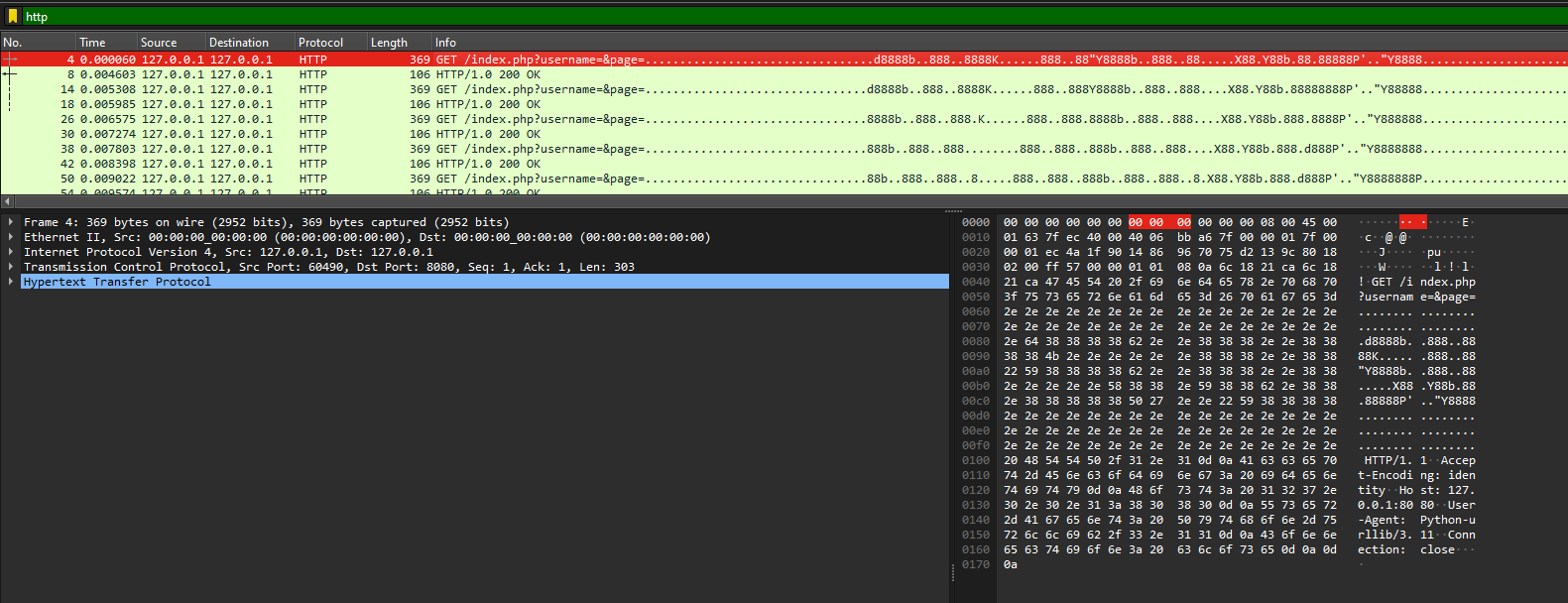
We are given a pcap file to investigate. Looking at the packets, there seem to be a repeated set of HTTP and TCP packets being sent across.
Filtering by HTTP packets, the URL seems to be replicating something related to the flag. Checking the HTTP streams, nothing of interest can be found.
After an hour of searching, I realized that I was just overthinking it. Looking at the packet data on the bottom right pane, a letter ‘S’ can be found. So it was obvious that the URLs were replicating the flag.
Notoriously Tricky Login Mess (Part 2) [Forensics]
Question: Great job finding the username! We want to find out the password of the account now to see how it was so easily breached. Can you help? Flag format: swampCTF{password}
Flag: swampCTF{emilyyoudontknowmypassword}
We are given the same PCAP from a previous challenge to investigate. Doing some research online about NTLMSSP and HTTP-SPNEGO-session-encrypted, I was stuck on this challenge for awhile. Thankfully, a friend of mine @0x157 gave a small but effective nudge for me. Basically, the challenge was not related to the encrypted data at all, instead it was just NTLM hash cracking. Reading on how this works in NTLMSSP, I stumbled upon this video that teaches the method to dump NTLM hashes from a PCAP. Basically, I have to forge the NTLM hash myself using the data from NTLMSSP_CHALLENGE and NTLMSSP_AUTH.
The final hash should look like this:
1
adamkadaban:::9860ff77ebae7c49:427e62eb532e7cf982af3a23fb5aa4b2:010100000000000000a205e9c266da01e7973bcb0507f9230000000002001e0045004300320041004d0041005a002d00450033003300530047004c00380001001e0045004300320041004d0041005a002d00450033003300530047004c00380004001e0045004300320041004d0041005a002d00450033003300530047004c00380003001e0045004300320041004d0041005a002d00450033003300530047004c003800070008001998a3e4c266da010000000000000000
Crack the hash and the flag can be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
└─$
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 5.0+debian Linux, None+Asserts, RELOC, SPIR, LLVM 16.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz, 1436/2937 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
Cracking performance lower than expected?
* Append -O to the commandline.
This lowers the maximum supported password/salt length (usually down to 32).
* Append -w 3 to the commandline.
This can cause your screen to lag.
* Append -S to the commandline.
This has a drastic speed impact but can be better for specific attacks.
Typical scenarios are a small wordlist but a large ruleset.
* Update your backend API runtime / driver the right way:
https://hashcat.net/faq/wrongdriver
* Create more work items to make use of your parallelization power:
https://hashcat.net/faq/morework
ADAMKADABAN:::9860ff77ebae7c49:427e62eb532e7cf982af3a23fb5aa4b2:010100000000000000a205e9c266da01e7973bcb0507f9230000000002001e0045004300320041004d0041005a002d00450033003300530047004c00380001001e0045004300320041004d0041005a002d00450033003300530047004c00380004001e0045004300320041004d0041005a002d00450033003300530047004c00380003001e0045004300320041004d0041005a002d00450033003300530047004c003800070008001998a3e4c266da010000000000000000:emilyyoudontknowmypassword
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: ADAMKADABAN:::9860ff77ebae7c49:427e62eb532e7cf982af...000000
Time.Started.....: Sat Apr 6 07:36:29 2024 (17 secs)
Time.Estimated...: Sat Apr 6 07:36:46 2024 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 505.2 kH/s (0.70ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 8328192/14344385 (58.06%)
Rejected.........: 0/8328192 (0.00%)
Restore.Point....: 8327680/14344385 (58.06%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: eminem6575 -> emilywin
Hardware.Mon.#1..: Util: 50%
Started: Sat Apr 6 07:36:06 2024
Stopped: Sat Apr 6 07:36:48 2024
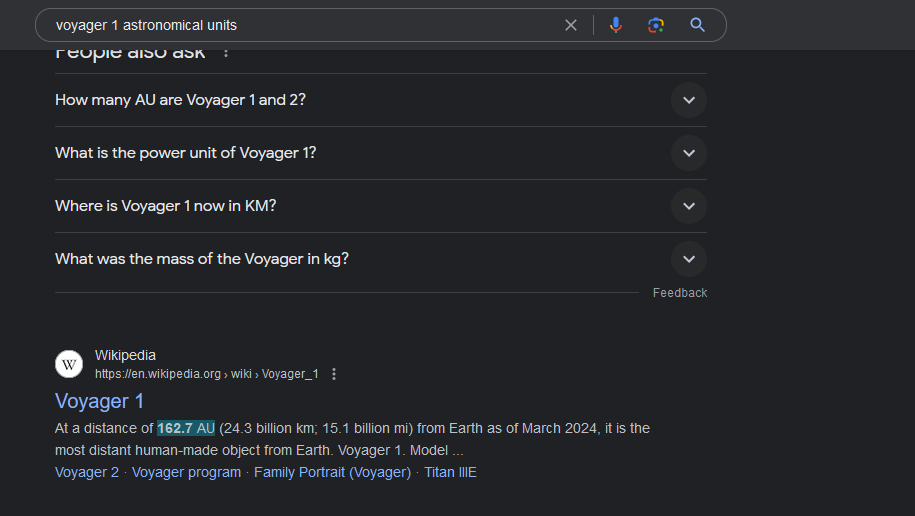
Lost in Space [OSINT]
Question: I think OSINT challenges are stupid! If they aren’t, prove it! How far away is this? Don’t bother giving me the unit, there’s only one that you should be using in space anyways (use Astronomical Units). The flag entry is extremely forgiving just make sure you get the integer for distance right.
Flag: swampCTF{162.7}
We are tasked to identify the distance of a satellite. Reverse searching the image, the name of the satellite can be identified as Voyager 1.
Googling about Voyager 1, the flag can be obtained in the Wikipedia page.
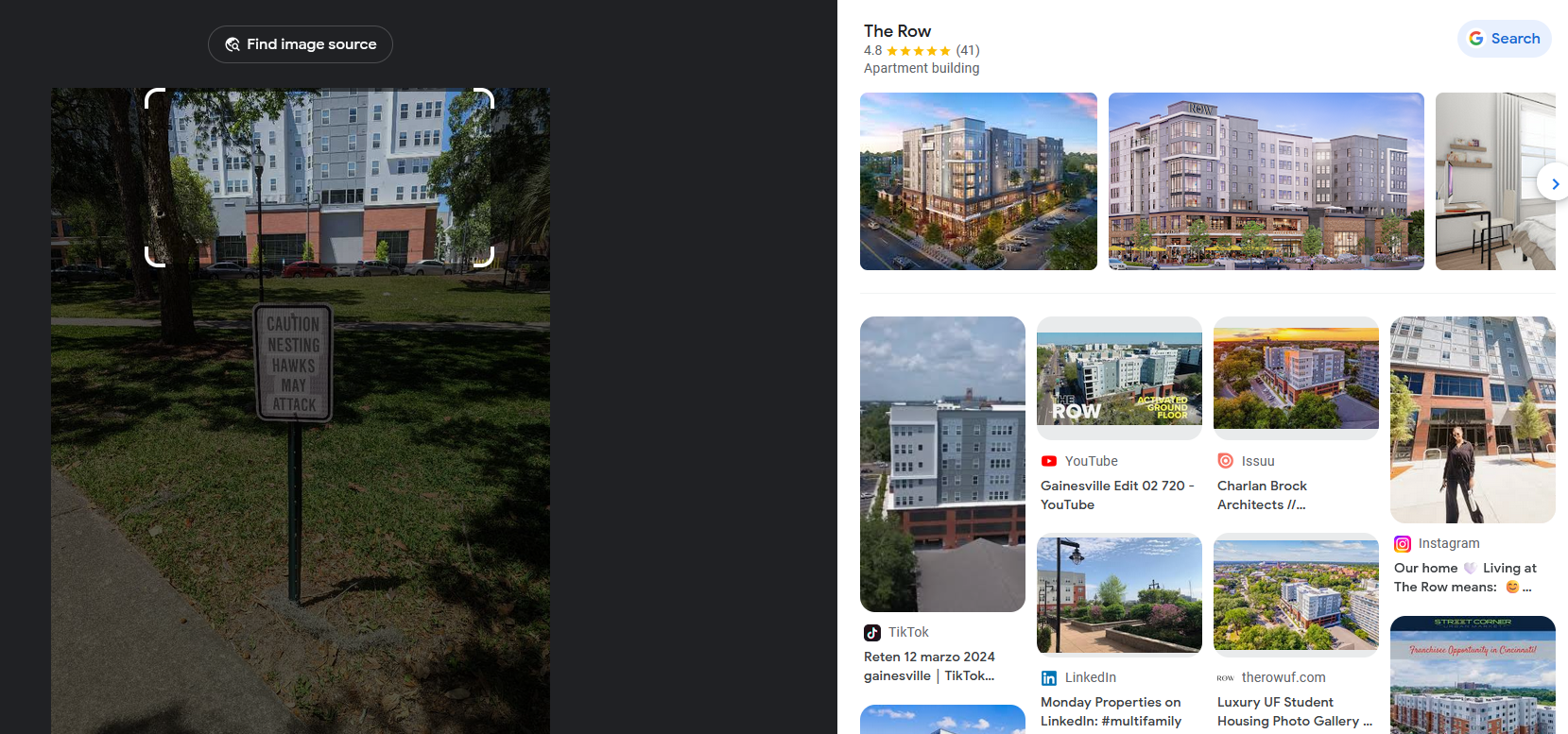
Aerial Attack [OSINT]
Question: Find where this photo was taken! Make sure to keep your eyes out for the hawks though! The flag is the truncated coordinate of this location to the hundredths. Ex: (xx.xx, xx.xx)
Flag: swampCTF{29.65,-82.33}
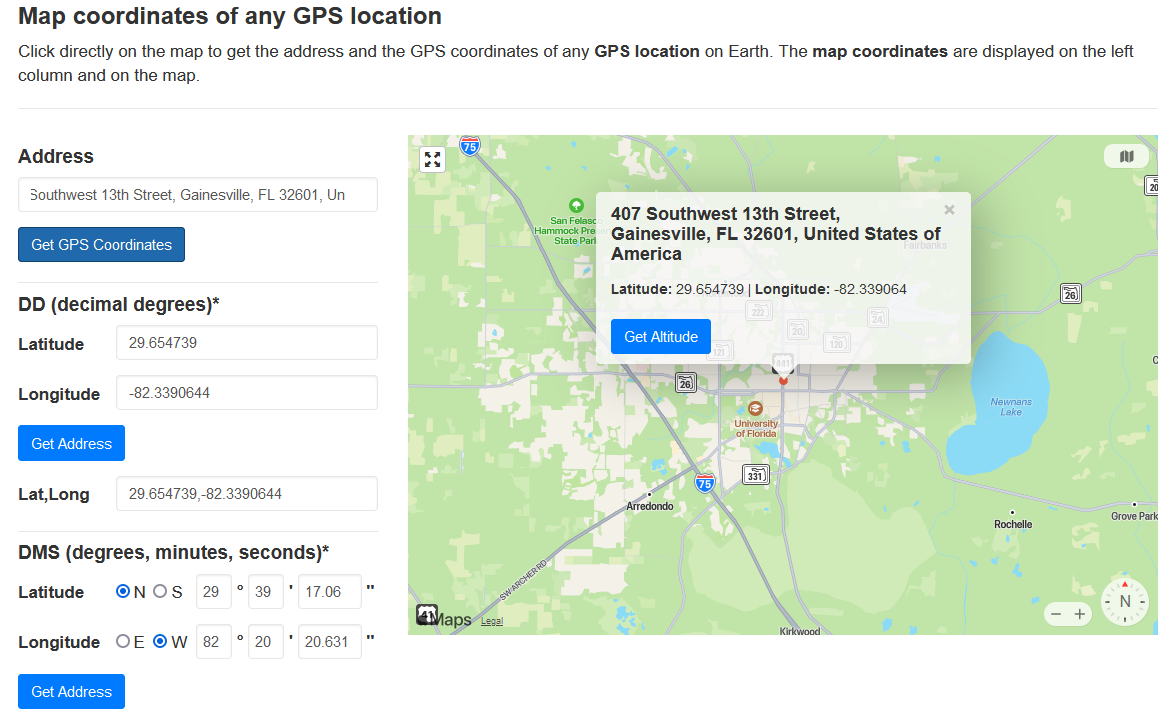
We are tasked to locate the coordinates of a specific campus or a park.
Reverse searching the image, it seems that the building behind the signboard was called The Row.
Retrieving the address of The Row, the coordinates can be found.
Hidden Snack Stop [OSINT]
Question: I found this really good chips place, but I don’t want it to be crowded, so I’ve blurred everything. Hahaha! The flag is the address of this location as it’s shown on google maps. Good luck! Do not wrap the address in swampCTF{}
Flag: swampCTF{43 1/2 Broadway St, Asheville, NC 28801, United States}
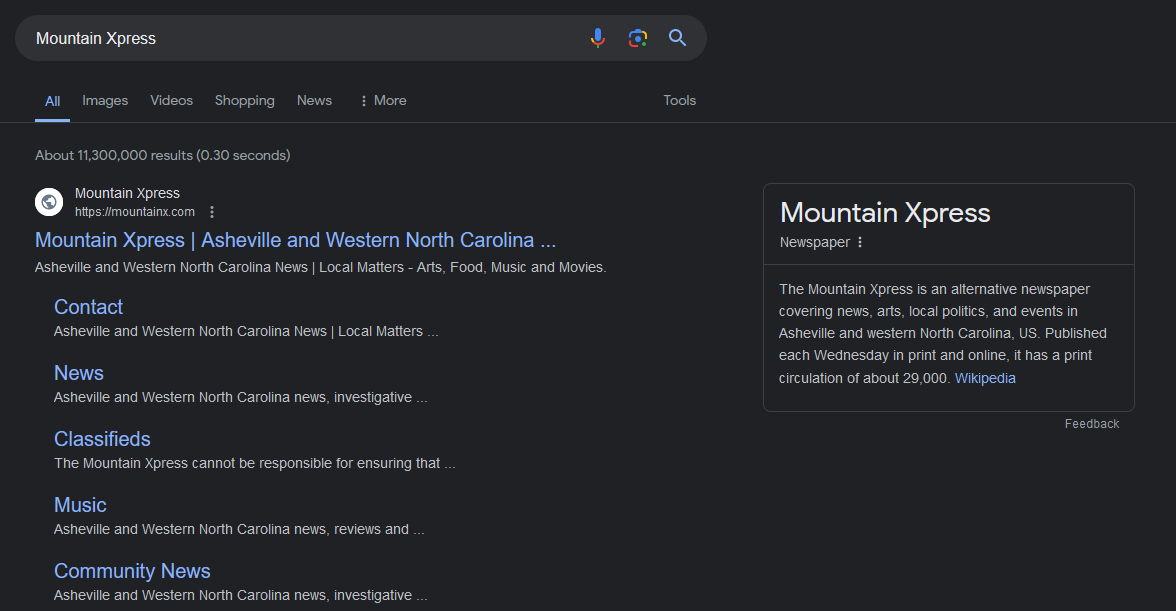
It seems that the image shows a street with several shops near it with their names blurred.
Analyzing the scenary carefully, I can obtain two important information. One was the Mountain Xpress mailbox while the other was Elevation Hotel.
Mountain Xpress tells us that the street is somewhere in Asheville and Western North Carolina.
So by searching for Elevation Hotel in Asheville, the exact location of the hotel can be found.
Looking at the opposite direction, the snack shop location can be found.