Space Heroes CTF 2024 - Writeups
This is a writeup for all forensics challenges from Space Heroes CTF 2024. Participated in this CTF for a quick warm up on forensics, solved all of the challenges in 2 hours. Hope they release more forensics challenges next year because the challenges were way to simple.
Petey the Panther’s Guide to the Galaxy [Forensics]
Question: Petey the Panther has stumbled upon the greatest treasure this side of the Milky Way: a bonafide Hitchhikers Guide to the Galaxy! What kind of secrets does this thing hold?
Flag: shctf{s0_l0ng_4nd_th4nks_f0r_4ll_th3_flags}
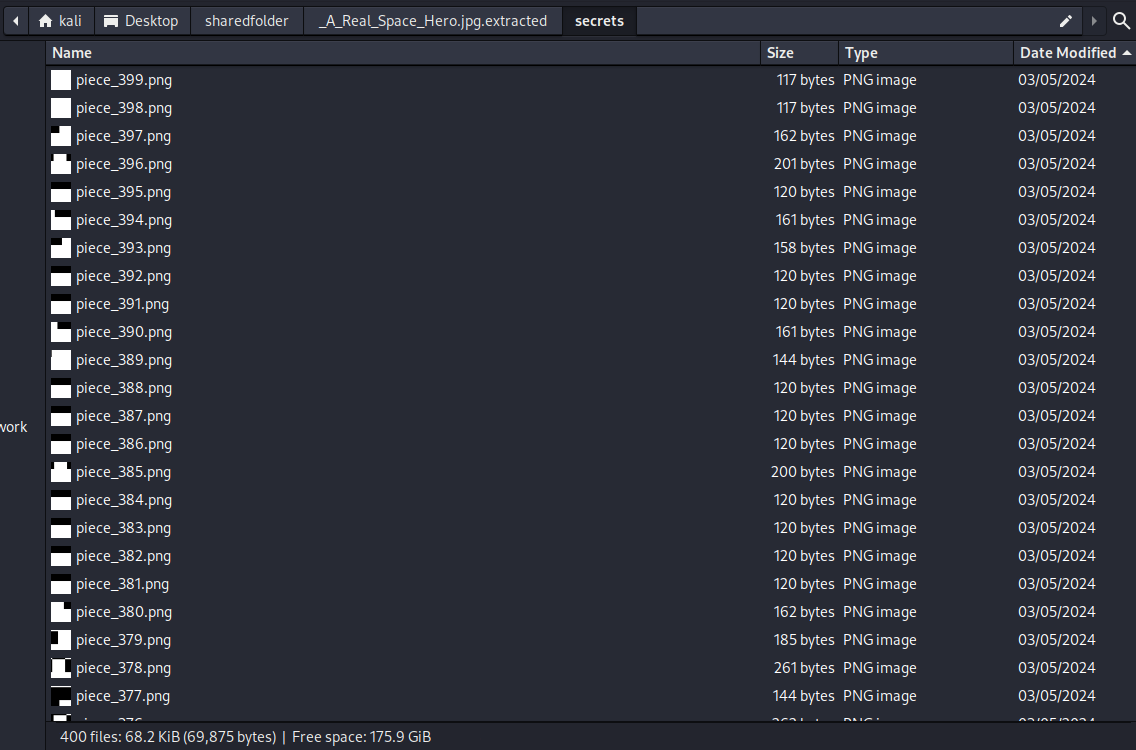
We are given an image to investigate. Analyzing and extracting the files with binwalk, a secret folder can be obtained with several image fragments.
Creating a Python script to merge the pieces automatically, an image can be formed. The merged image was a QR code where the flag can be obtained by scanning it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
from PIL import Image
piece_width, piece_height = 20, 20 # Each piece is 20x20
final_width = piece_width * 20 # 20 pieces in a row
final_height = piece_height * 20
# Create a new blank image to hold the merged pieces
final_image = Image.new('RGBA', (final_width, final_height), (255, 255, 255, 0)) # RGBA mode for transparency
for i in range(400):
piece_path = f"piece_{i}.png" # Assuming the pieces are named piece_0.png, piece_1.png, ..., piece_399.png
piece_image = Image.open(piece_path)
row = i // 20
col = i % 20
x_offset = col * piece_width
y_offset = row * piece_height
final_image.paste(piece_image, (x_offset, y_offset))
final_image.save("merged_image.png")
A Window into Space [Forensics]
Question: I think aliens are testing us again and they they are poking fun at our internet protocols by using them in close proximity to earth. We were able to intercept something but I cant figure out what it is. Take a crack at it for me.
Flag: shctf{1_sh0uld_try_h1d1ng_1n_th3_ch3cksum_n3xt_t1me_0817}
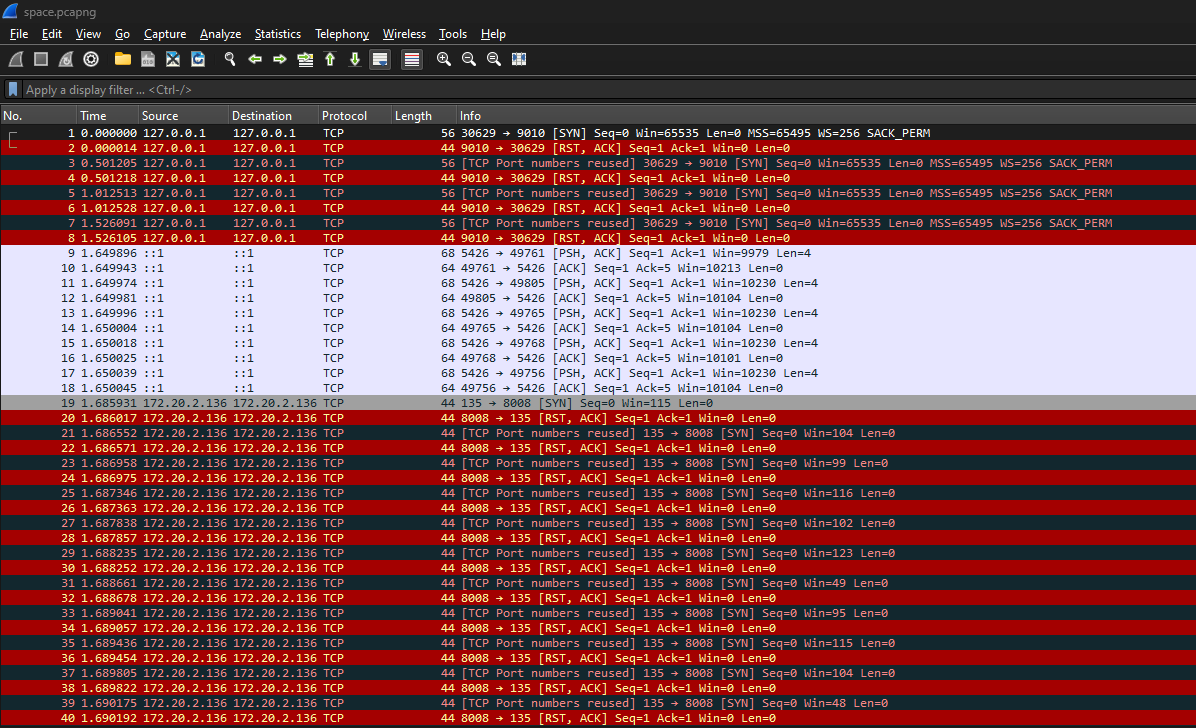
We are given a PCAP to investigate. Analyzing it, several TCP packets can be found being sent from port 8008 to port 135.
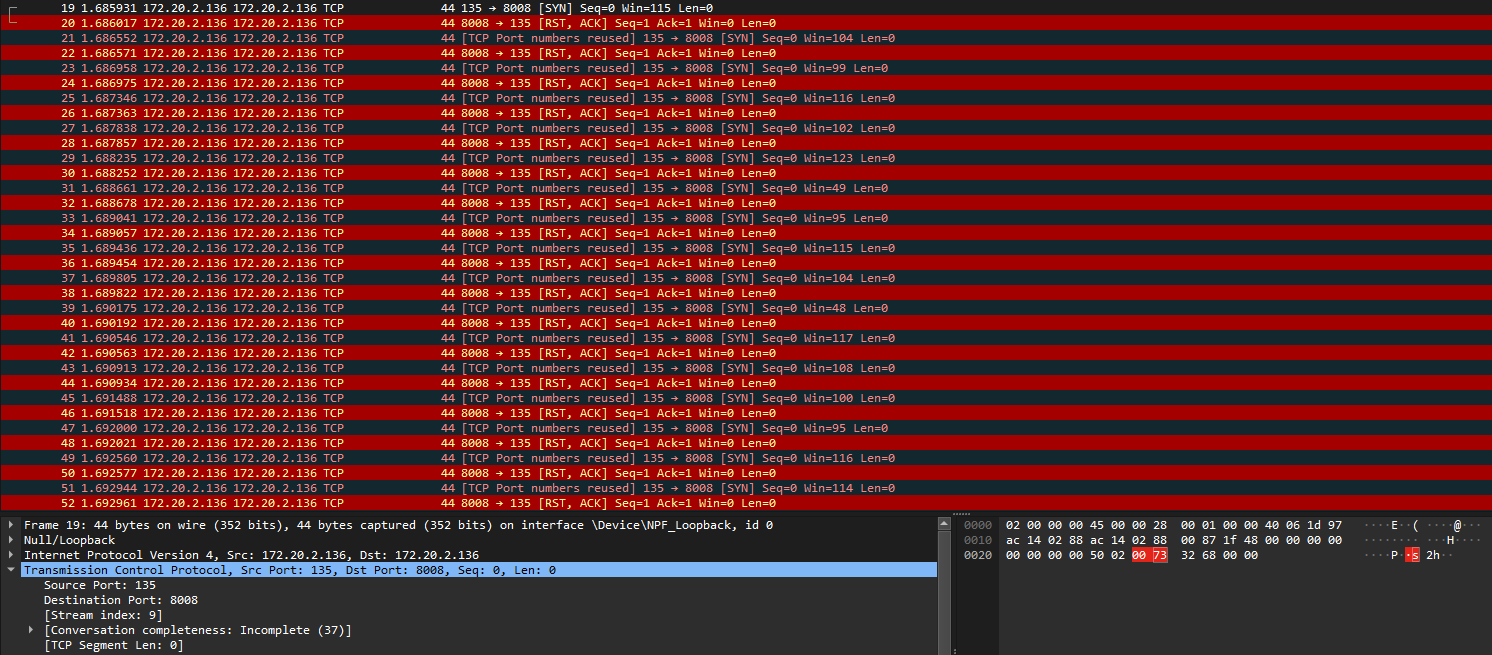
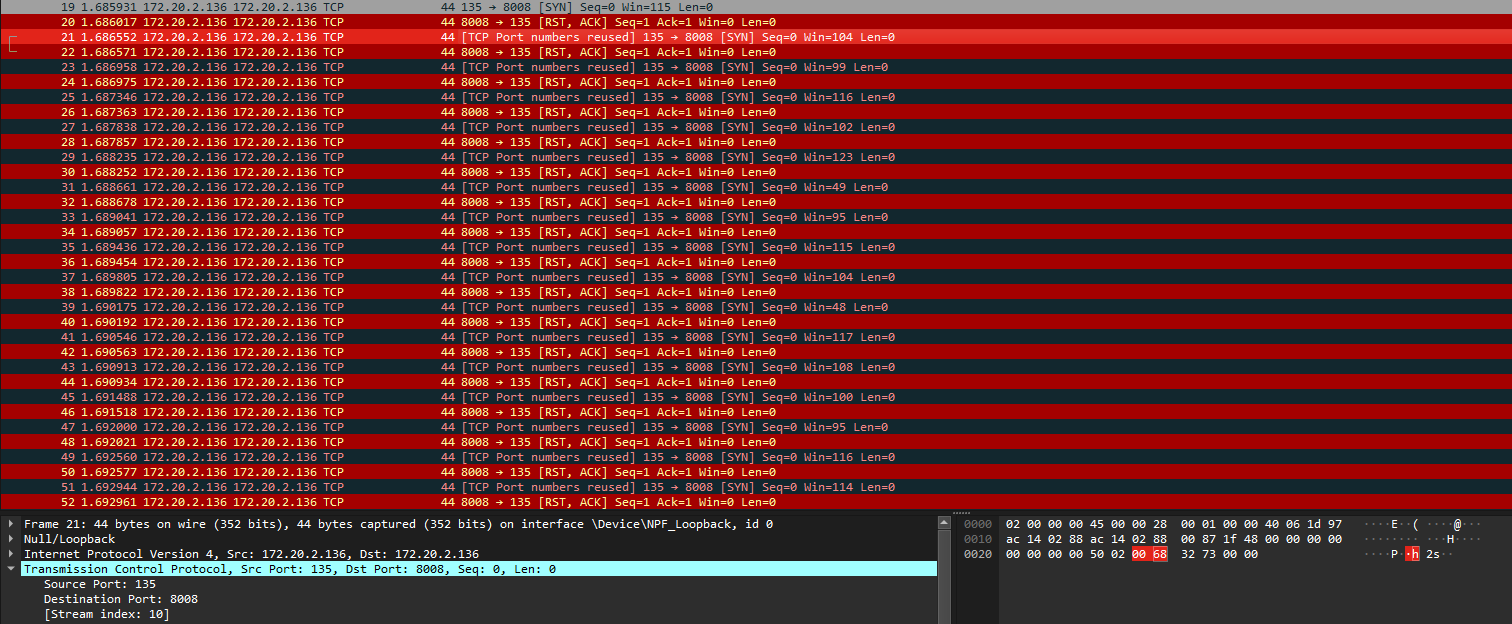
This challenge was similar to other CTFs that I have played where duplicated TCP packets will usually have hidden data within them. Looking at the first 5 SYN packets, it seems that the only difference between them was the letter in the data. The screenshots below shows the data difference between the first and the second SYN packet, notice how the highlighted letters were changing from each SYN packet. Following along the SYN packets, the flag can be obtained.
Space Frisbee [Forensics]
Question: We’ve recorded an U.F.O. near our location and it seems they are trying to communicate with us. The second half of the audio intelligible, can you discover what they’re trying to say?
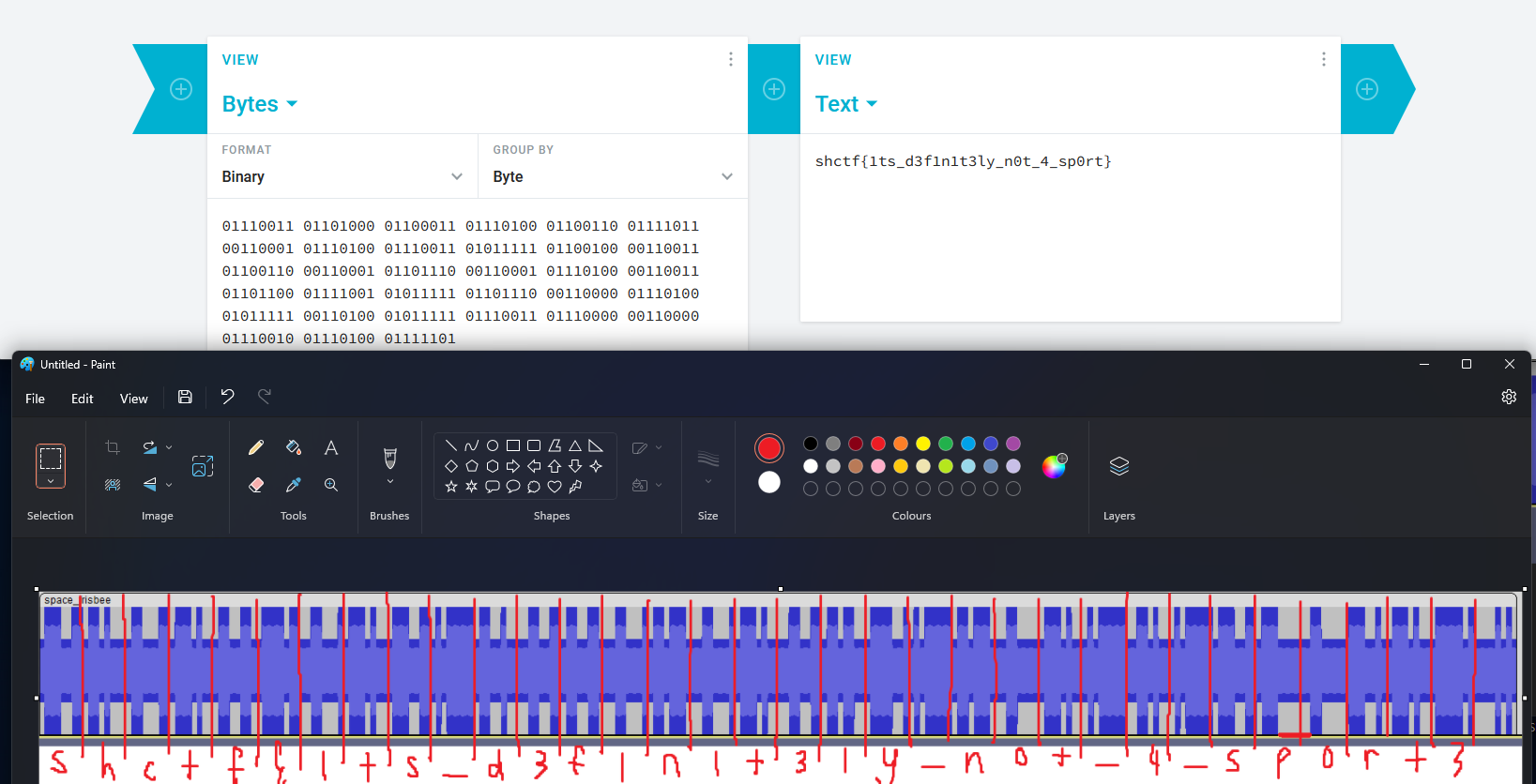
Flag: shctf{1ts_d3f1n1t3ly_n0t_4_sp0rt}
We are given a wav audio to investigate. Analyzing it on Audacity, the audio spectrogram seems to not show anything suspicious.
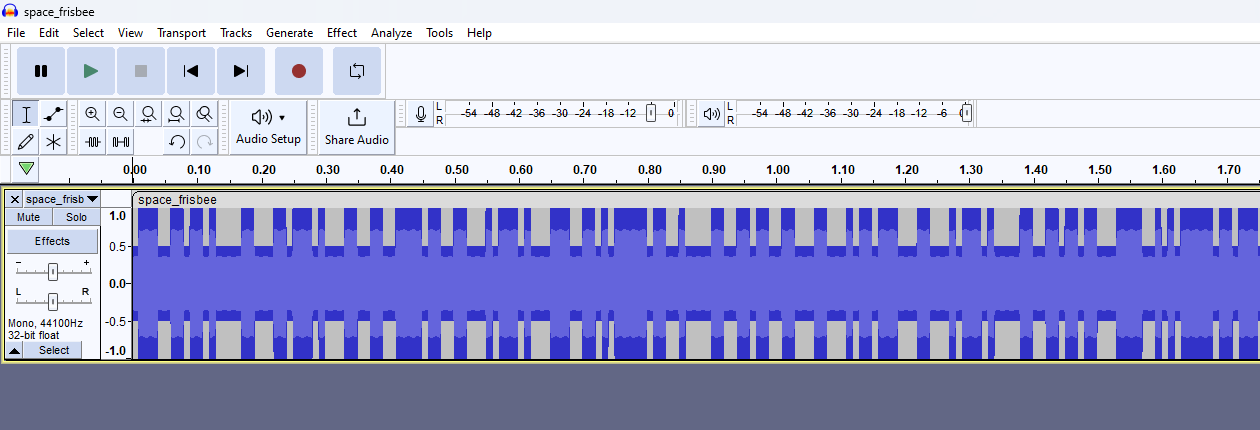
However, the audio waveform seems to be forming a pattern of some sorts. Again, I have played other CTFs where the flag can sometimes be embedded into the audio waveform, specifically encoding it with binary string.
Manually calculating the binary string, the flag can be obtained. There is definitely an easier way to automatically calculate the binary string but I suck at coding so.