ShunyaCTF Aarambha 2024 - Writeups
This is a writeup for some forensics, OSINT and misc challenges from ShunyaCTF Aarambha 2024. This CTF was special as it was my first time getting 🩸 in a forensics challenge. However, I really did not enjoy one of the OSINT challenge where it was super guessy, and for some reason the author gave a wrong nudge.
BIBBA 1 [Forensics]
Question: my grandfather sent me this one photo describing it as his one of the most cherised and sacred memories during his time. help me find out some details about it. part 1: png header error, after solving flag would be printed on the photo.
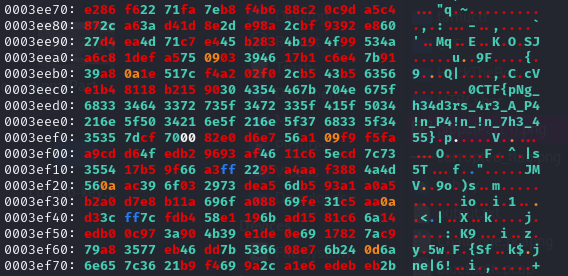
Flag: 0CTF{pNg_h34d3rs_4r3_A_P4!n_P4!n_!n_7h3_455}
We are given a corrupted PNG image to investigate. However, the flag can be obtained without fixing the image.
The Vanishing of Dr. Kumar [Forensics]
Question: Dr. Kumar disappeared right before his big cybersecurity speech, leaving everyone baffled. Despite tight security, no one saw where he went. The mystery of his disappearance has everyone on edge, with ACP Pradyuman and his team joining the investigation.
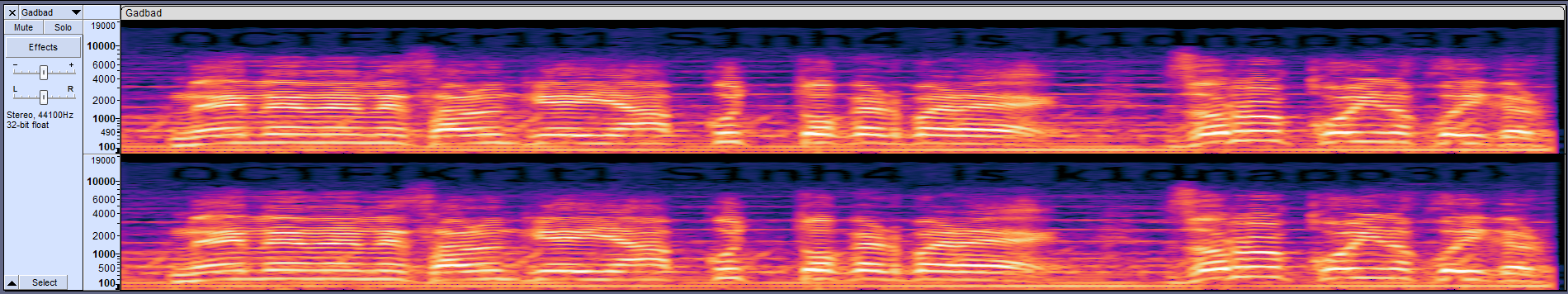
Flag: 0CTF{Kr1t1_S1nh4_is_k1dnapp3r}
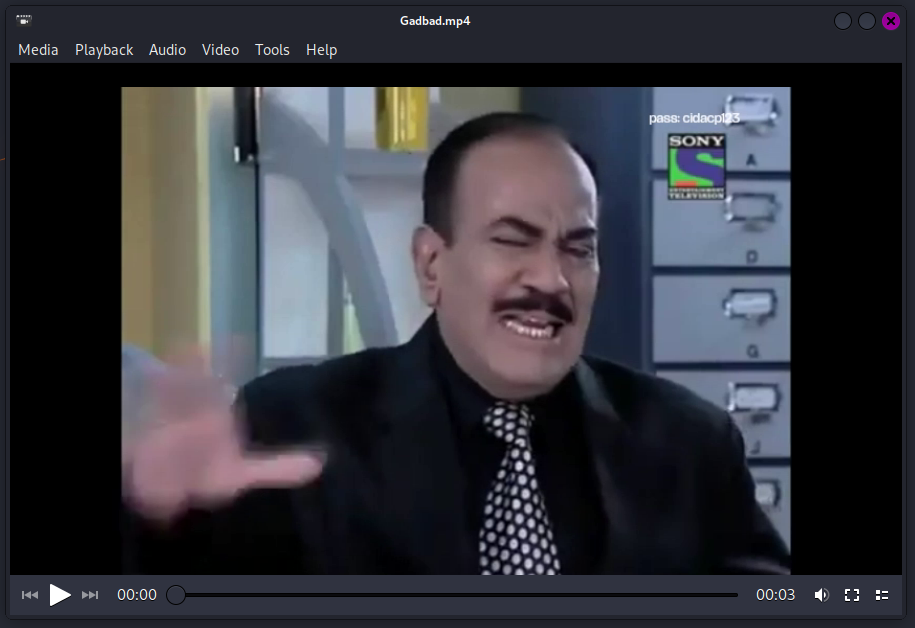
We are given a MP4 video to investigate. Watching the video carefully, no hidden text or data could be found. So I extracted the MP3 audio from the video to identify audio steganography.
The flag can be obtained from the audio spectrogram.
The Hunt of Dr. Kumar [Forensics] 🩸
Question: Dr. Kumar’s hiding spot remains a mystery in the crowded city. With time ticking away, finding him becomes more urgent. Will ACP Pradyuman and his team outsmart the villain and rescue Dr. Kumar before it’s too late?
Flag: 0CTF{Ujjayanta_Palace}
We are given a MP4 video to investigate. Analyzing the video, there were no hidden text or data again. So I extracted the MP3 audio from the video to identify audio steganography. However, this time the audio gave nothing of interest. So I checked the video’s metadata for extra information.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
└─$ exiftool Gadbad2.mp4
ExifTool Version Number : 12.76
File Name : Gadbad2.mp4
Directory : .
File Size : 521 kB
File Modification Date/Time : 2024:04:13 09:41:01-04:00
File Access Date/Time : 2024:04:13 14:04:08-04:00
File Inode Change Date/Time : 2024:04:13 09:41:01-04:00
File Permissions : -rwxrwxrwx
File Type : MP4
File Type Extension : mp4
MIME Type : video/mp4
Major Brand : MP4 v2 [ISO 14496-14]
Minor Version : 0.0.0
Compatible Brands : isom, mp42
Movie Header Version : 0
Create Date : 2024:03:10 06:56:21
Modify Date : 2024:03:10 06:56:21
Time Scale : 14336
Duration : 12.98 s
Preferred Rate : 1
Preferred Volume : 100.00%
Preview Time : 0 s
Preview Duration : 0 s
Poster Time : 0 s
Selection Time : 0 s
Selection Duration : 0 s
Current Time : 0 s
Next Track ID : 3
Track Header Version : 0
Track Create Date : 2024:03:10 06:56:21
Track Modify Date : 2024:03:10 06:56:21
Track ID : 1
Track Duration : 12.96 s
Track Layer : 0
Track Volume : 0.00%
Image Width : 508
Image Height : 360
Compressor ID : avc1
Source Image Width : 508
Source Image Height : 360
X Resolution : 72
Y Resolution : 72
Bit Depth : 24
Video Frame Rate : 28
Graphics Mode : srcCopy
Op Color : 0 0 0
Matrix Structure : 1 0 0 0 1 0 0 0 1
Media Header Version : 0
Media Create Date : 2024:03:10 06:56:21
Media Modify Date : 2024:03:10 06:56:21
Media Time Scale : 44100
Media Duration : 12.98 s
Media Language Code : und
Handler Description : ISO Media file produced by Google Inc. Created on: 03/09/2024.
Audio Format : mp4a
Audio Channels : 2
Audio Bits Per Sample : 16
Audio Sample Rate : 44100
Balance : 0
Handler Type : Metadata
Handler Vendor ID : Apple
Google Start Time : 0
Google Track Duration : 13.03 s
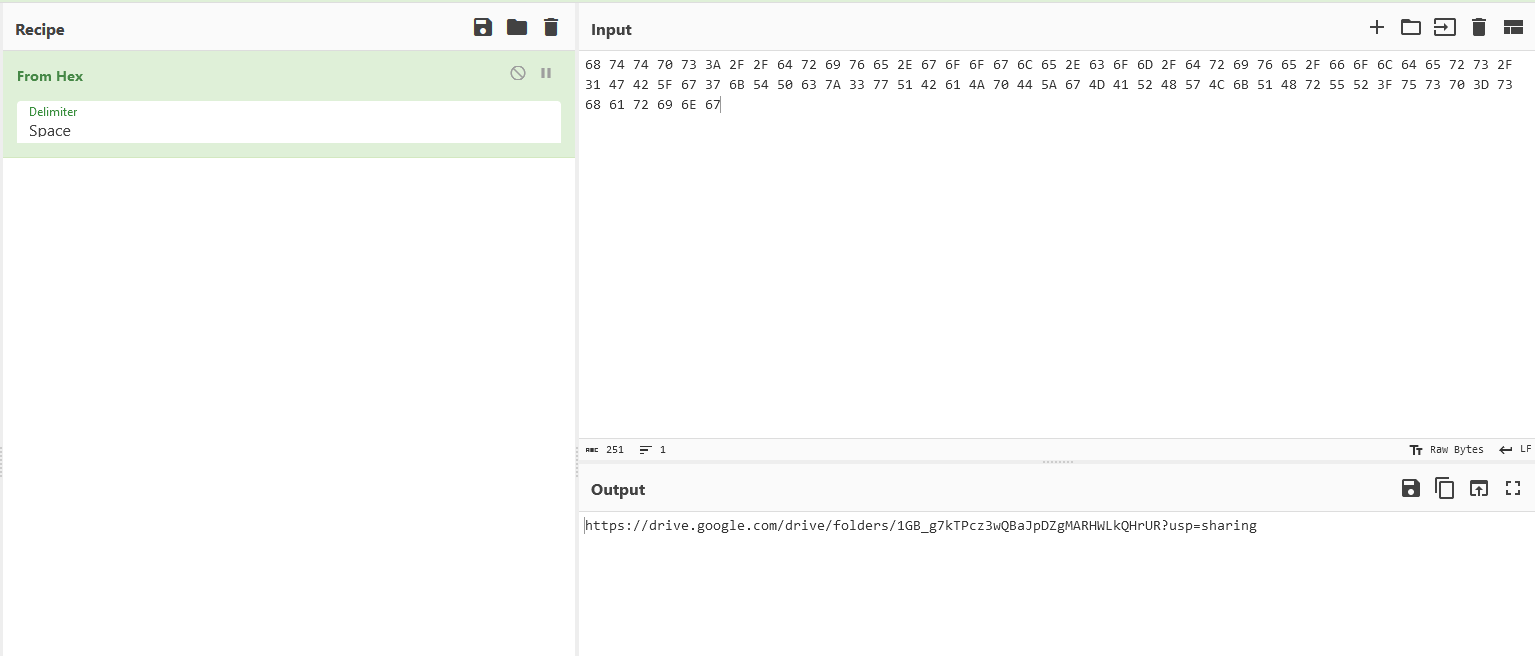
Initial Key : 68 74 74 70 73 3A 2F 2F 64 72 69 76 65 2E 67 6F 6F 67 6C 65 2E 63 6F 6D 2F 64 72 69 76 65 2F 66 6F 6C 64 65 72 73 2F 31 47 42 5F 67 37 6B 54 50 63 7A 33 77 51 42 61 4A 70 44 5A 67 4D 41 52 48 57 4C 6B 51 48 72 55 52 3F 75 73 70 3D 73 68 61 72 69 6E 67
Media Data Size : 512085
Media Data Offset : 8495
Image Size : 508x360
Megapixels : 0.183
Avg Bitrate : 316 kbps
Rotation : 0
Inside the metadata, a hex encoded Google Drive link can be obtained which redirects to a PDF and text file.
The PDF file doesn’t seem to have any secret data embedded within it excluding the blocked out image.
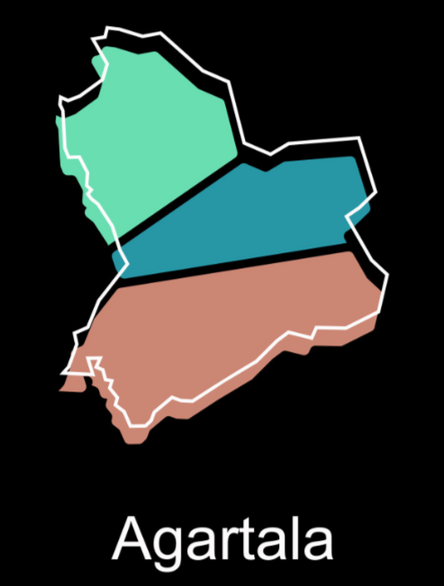
Thankfully, I remember this during another CTF where pdftohtml can help decompile the pdf layers to obtain the blocked image. The blocked image seems have a picture of Agartala.
The text file seem to be suspicious though where hidden whitespaces between texts. Having knowledge on whitespace programming language from other CTFs, I thought I could decode something, but alas nothing was found.
Researching online on whitespace forensics, I stumbled upon this writeup that talks about SNOW (Steganographic Nature Of Whitespace). In the writeup, they mentioned brute forcing a password, but remembering that I already have Agartala, it could potentially be the secret key.
1
2
└─$ stegsnow -C -p "Agartala" LocationFinal.txt
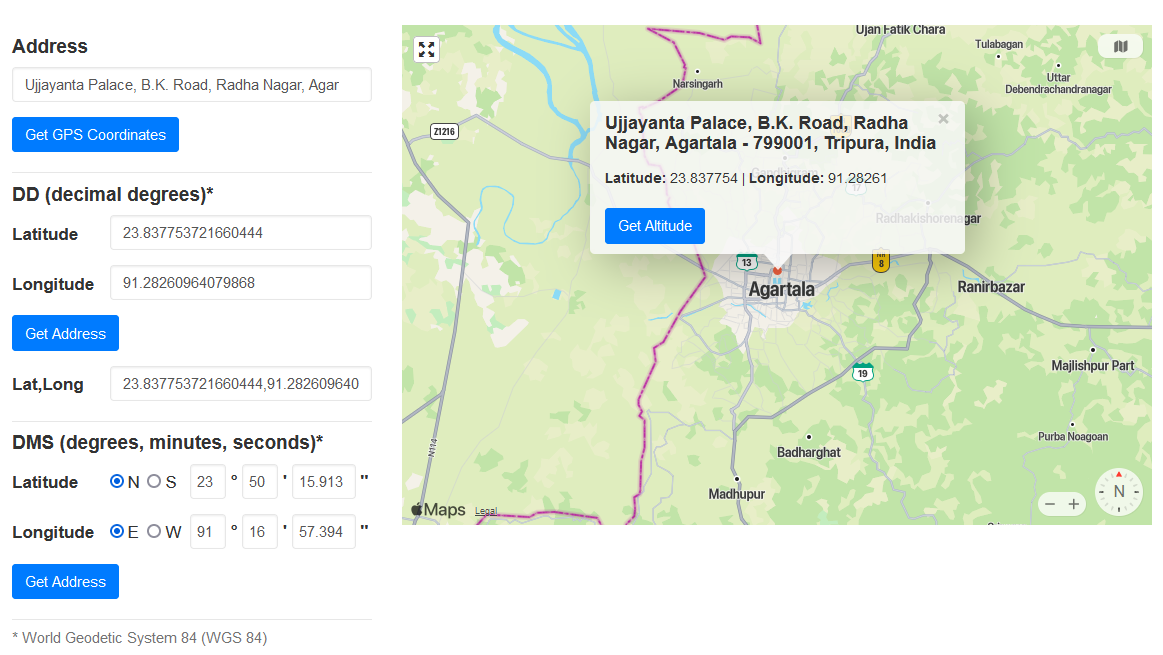
23.837753721660444, 91.28260964079868
With the coordinates, we can find the exact location to be Ujjayanta Palace.
Check Research and Check again [Forensics]
Question: Sometimes in life, everything goes wrong, nothing works and you crash every time you try to look within yourself. In such moments, calculate where you came from, and see what you can correct, generally the last thing you did wrong is what needs to be corrected first. Flag Format: 0ctf{words_with_underscore}
Flag: 0ctf{crc_1s_a_us5ful_m5chan1sm}
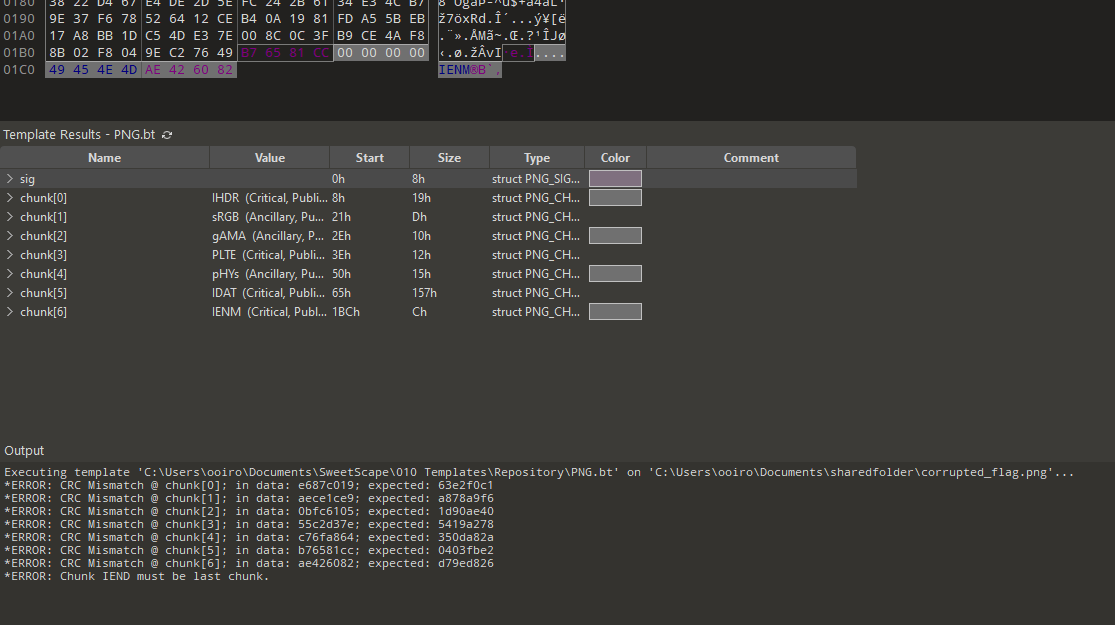
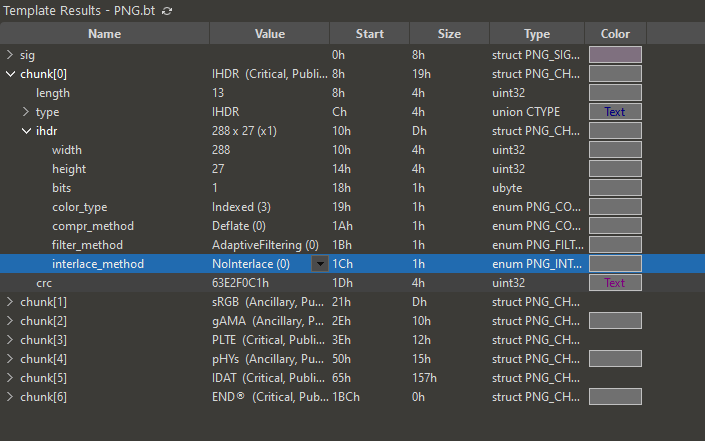
We are given a corrupted png image to investigate. Putting the image on 010 Editor, we can fix the CRC errors easily.
After fixing the bytes, we are greeted with another issue on the interlace method.
1
2
3
4
5
6
└─$ pngcheck -v corrupted_flag.png
zlib warning: different version (expected 1.2.13, using 1.3)
File: corrupted_flag.png (455 bytes)
chunk IHDR at offset 0x0000c, length 13: invalid interlace method (82)
ERRORS DETECTED in corrupted_flag.png
Reading online on the interlace byte, the byte can be located near the end of the IHDR header. Changing the interlace method bytes to 0, we get the flag.
Infant Mem [Forensics]
Question: Here is that one last minute chall….because of-course I can’t skip Memory Analysis!! Find the Device Name of my OS followed by name of Local User!! Remember to enclose it around flag format!!
Flag: 0CTF{mr1tyu-PC_lord-mr1tyu}
We are given a memory dump to investigate. The first thing to always do is to check the profile to ensure Volatility 2 works.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ python2 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw imageinfo
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86_24000, Win7SP1x86
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/home/kali/Desktop/sharedfolder/mr1tyu.raw)
PAE type : PAE
DTB : 0x185000L
KDBG : 0x82939de8L
Number of Processors : 4
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0x80b97000L
KPCR for CPU 1 : 0x807ce000L
KPCR for CPU 2 : 0x89855000L
KPCR for CPU 3 : 0x89893000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2024-04-13 12:10:14 UTC+0000
Image local date and time : 2024-04-13 17:40:14 +0530
Researching online on how I can find the exact device name, I stumbled upon this website that mentioned the SYSTEM registry contains the hostname of the machine. Using theh hivelist plugin in Volatility 2, the hostname can also be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ python2 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw --profile Win7SP1x86_23418 hivelist
Volatility Foundation Volatility Framework 2.6.1
Virtual Physical Name
---------- ---------- ----
0x8d88a5d8 0x0f3f05d8 \Device\HarddiskVolume1\Boot\BCD
0x8ff4d550 0x0b884550 \SystemRoot\System32\Config\SECURITY
0x8ff71580 0x0b7e3580 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0x8ffae008 0x0b13c008 \SystemRoot\System32\Config\SAM
0x90857408 0x11d3e408 \SystemRoot\System32\Config\DEFAULT
0x968999c8 0x501c99c8 \??\C:\Users\lord-mr1tyu\ntuser.dat
0x9938f008 0x1eef8008 \??\C:\Users\lord-mr1tyu\AppData\Local\Microsoft\Windows\UsrClass.dat
0x9ba24008 0x30d6a008 \??\C:\System Volume Information\Syscache.hve
0x8860a6d8 0x137806d8 [no name]
0x8861a008 0x13943008 \REGISTRY\MACHINE\SYSTEM
0x8863b008 0x13964008 \REGISTRY\MACHINE\HARDWARE
0x88c51508 0x0a378508 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0x89ffe338 0x122ea338 \SystemRoot\System32\Config\SOFTWARE
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ python2 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw --profile Win7SP1x86_23418 printkey -o 0x8861a008 -K 'ControlSet001\Control\ComputerName\ComputerName'
Volatility Foundation Volatility Framework 2.6.1
Legend: (S) = Stable (V) = Volatile
----------------------------
Registry: \REGISTRY\MACHINE\SYSTEM
Key name: ComputerName (S)
Last updated: 2024-04-12 04:22:44 UTC+0000
Subkeys:
Values:
REG_SZ : (S) mnmsrvc
REG_SZ ComputerName : (S) MR1TYU-PC
After obtaining the hostname, we can find the local user by using the hashdump plugin. The local user can be identified as lord-mr1tyu.
1
2
3
4
5
6
└─$ python2 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw --profile Win7SP1x86_23418 hashdump -y 0x8861a008 -s 0x8ffae008
Volatility Foundation Volatility Framework 2.6.1
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
lord-mr1tyu:1000:aad3b435b51404eeaad3b435b51404ee:259745cb123a52aa2e693aaacca2db52:::
HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:3e1b070771e65a9f57b6cced3bfb2931:::
Baby Mem [Forensics]
Question: Sorry, I made more. Help me find the name and physical address of file potentially containing the Virus!!!
Flag: 0CTF{DudleyTrojan.bat_0x64ac7a18}
We can start the investigation by analyzing the processes, cmd history and files of the compromised machine. For this part, I used Volatility 3 for a neater output.
Processes:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
└─$ python3 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw windows.pstree
Volatility 3 Framework 2.5.2
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
4 0 System 0x84554bb8 100 565 N/A False 2024-04-13 06:19:29.000000 N/A
* 284 4 smss.exe 0x8560cd20 2 32 N/A False 2024-04-13 06:19:29.000000 N/A
364 356 csrss.exe 0x855e3d20 9 336 0 False 2024-04-13 06:19:33.000000 N/A
412 404 csrss.exe 0x85d20a80 10 788 1 False 2024-04-13 06:19:34.000000 N/A
* 5724 412 conhost.exe 0x85f53d20 2 52 1 False 2024-04-13 12:08:30.000000 N/A
420 356 wininit.exe 0x845ce1e0 3 82 0 False 2024-04-13 06:19:34.000000 N/A
* 524 420 lsm.exe 0x85d60948 9 144 0 False 2024-04-13 06:19:34.000000 N/A
* 508 420 services.exe 0x85d35b90 6 196 0 False 2024-04-13 06:19:34.000000 N/A
** 864 508 svchost.exe 0x85e155f0 18 460 0 False 2024-04-13 06:19:37.000000 N/A
*** 2068 864 dwm.exe 0x84710188 3 87 1 False 2024-04-13 06:23:48.000000 N/A
** 704 508 svchost.exe 0x859f1570 8 284 0 False 2024-04-13 06:19:36.000000 N/A
** 1400 508 svchost.exe 0x85f4a258 16 313 0 False 2024-04-13 06:19:44.000000 N/A
** 1032 508 svchost.exe 0x85e7faf8 5 143 0 False 2024-04-13 06:19:41.000000 N/A
** 1512 508 svchost.exe 0x85f915a8 21 317 0 False 2024-04-13 06:19:45.000000 N/A
** 2012 508 SearchIndexer. 0x8474d030 14 874 0 False 2024-04-13 06:21:51.000000 N/A
** 624 508 svchost.exe 0x85dc6170 9 377 0 False 2024-04-13 06:19:35.000000 N/A
** 912 508 svchost.exe 0x85e1c030 29 1106 0 False 2024-04-13 06:19:37.000000 N/A
*** 3716 912 wuauclt.exe 0x849188c8 3 95 1 False 2024-04-13 06:32:08.000000 N/A
** 1360 508 spoolsv.exe 0x85f394c8 13 302 0 False 2024-04-13 06:19:44.000000 N/A
** 3896 508 taskhost.exe 0x8544c880 5 96 1 False 2024-04-13 06:34:48.000000 N/A
** 1308 508 wmpnetwk.exe 0x84702670 13 415 0 False 2024-04-13 06:21:49.000000 N/A
** 888 508 svchost.exe 0x85e16768 13 339 0 False 2024-04-13 06:19:37.000000 N/A
** 796 508 svchost.exe 0x859f89e8 21 511 0 False 2024-04-13 06:19:36.000000 N/A
*** 1264 796 audiodg.exe 0x84e9ea68 4 131 0 False 2024-04-13 11:57:37.000000 N/A
** 1176 508 svchost.exe 0x85eb4030 17 533 0 False 2024-04-13 06:19:42.000000 N/A
** 2264 508 taskhost.exe 0x8470cd20 10 283 1 False 2024-04-13 06:23:49.000000 N/A
* 516 420 lsass.exe 0x85d635e0 5 662 0 False 2024-04-13 06:19:34.000000 N/A
460 404 winlogon.exe 0x85ce7d20 3 118 1 False 2024-04-13 06:19:34.000000 N/A
2116 2056 explorer.exe 0x84912d20 24 953 1 False 2024-04-13 06:23:48.000000 N/A
* 3872 2116 msedge.exe 0x8472d568 45 1860 1 False 2024-04-13 07:31:11.000000 N/A
** 2304 3872 msedge.exe 0x84bf6c68 16 345 1 False 2024-04-13 07:31:36.000000 N/A
** 2824 3872 msedge.exe 0x84892750 15 317 1 False 2024-04-13 09:35:10.000000 N/A
** 3848 3872 msedge.exe 0x85072d20 15 235 1 False 2024-04-13 11:54:03.000000 N/A
** 3088 3872 msedge.exe 0x850f3118 15 349 1 False 2024-04-13 09:34:56.000000 N/A
** 2840 3872 msedge.exe 0x84e79410 16 404 1 False 2024-04-13 10:29:38.000000 N/A
** 3104 3872 msedge.exe 0x84e1e430 12 212 1 False 2024-04-13 07:31:15.000000 N/A
** 2100 3872 msedge.exe 0x8615bbd8 7 149 1 False 2024-04-13 07:31:16.000000 N/A
** 2356 3872 WinRAR.exe 0x860a9b58 8 474 1 False 2024-04-13 11:46:45.000000 N/A
** 696 3872 msedge.exe 0x860a7120 18 430 1 False 2024-04-13 10:06:44.000000 N/A
** 4936 3872 msedge.exe 0x84fc2640 17 233 1 False 2024-04-13 12:06:22.000000 N/A
** 588 3872 msedge.exe 0x85fb59d0 18 509 1 False 2024-04-13 07:31:18.000000 N/A
** 1112 3872 msedge.exe 0x84e9cb68 11 186 1 False 2024-04-13 07:31:36.000000 N/A
** 2784 3872 msedge.exe 0x852371d0 17 266 1 False 2024-04-13 07:34:46.000000 N/A
** 2528 3872 msedge.exe 0x85f07518 15 242 1 False 2024-04-13 10:11:25.000000 N/A
** 3300 3872 msedge.exe 0x850c3030 15 261 1 False 2024-04-13 09:35:06.000000 N/A
** 1636 3872 msedge.exe 0x85149d20 16 241 1 False 2024-04-13 10:31:10.000000 N/A
** 2284 3872 msedge.exe 0x855a1110 14 238 1 False 2024-04-13 07:31:20.000000 N/A
** 3952 3872 msedge.exe 0x85e8d1e8 8 129 1 False 2024-04-13 07:31:11.000000 N/A
** 4848 3872 msedge.exe 0x84f94030 15 248 1 False 2024-04-13 12:06:13.000000 N/A
** 3192 3872 msedge.exe 0x85fd50e8 16 582 1 False 2024-04-13 09:22:08.000000 N/A
* 2380 2116 MRCv120.exe 0x848cc910 5 325 1 False 2024-04-13 11:58:02.000000 N/A
* 5716 2116 cmd.exe 0x84fc4900 1 21 1 False 2024-04-13 12:08:30.000000 N/A
2136 2852 taskmgr.exe 0x8529d670 7 126 1 False 2024-04-13 11:40:55.000000 N/A
2636 3108 iexplore.exe 0x85d99d20 9 481 1 False 2024-04-13 12:04:28.000000 N/A
* 2756 2636 iexplore.exe 0x84ba0588 23 677 1 False 2024-04-13 12:04:30.000000 N/A
** 1000 2756 ie_to_edge_stu 0x8543fd20 0 - 1 False 2024-04-13 12:04:34.000000 2024-04-13 12:04:34.000000
** 3616 2756 ie_to_edge_stu 0x8504eb68 0 - 1 False 2024-04-13 12:04:34.000000 2024-04-13 12:04:34.000000
CMD history:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
└─$ python3 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw windows.cmdline
Volatility 3 Framework 2.5.2
Progress: 100.00 PDB scanning finished
PID Process Args
4 System Required memory at 0x10 is not valid (process exited?)
284 smss.exe \SystemRoot\System32\smss.exe
364 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16
412 csrss.exe %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16
420 wininit.exe wininit.exe
460 winlogon.exe winlogon.exe
508 services.exe C:\Windows\system32\services.exe
516 lsass.exe C:\Windows\system32\lsass.exe
524 lsm.exe C:\Windows\system32\lsm.exe
624 svchost.exe C:\Windows\system32\svchost.exe -k DcomLaunch
704 svchost.exe C:\Windows\system32\svchost.exe -k RPCSS
796 svchost.exe C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted
864 svchost.exe C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted
888 svchost.exe C:\Windows\system32\svchost.exe -k LocalService
912 svchost.exe C:\Windows\system32\svchost.exe -k netsvcs
1032 svchost.exe C:\Windows\system32\svchost.exe -k GPSvcGroup
1176 svchost.exe C:\Windows\system32\svchost.exe -k NetworkService
1360 spoolsv.exe C:\Windows\System32\spoolsv.exe
1400 svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceNoNetwork
1512 svchost.exe C:\Windows\system32\svchost.exe -k LocalServiceAndNoImpersonation
1308 wmpnetwk.exe "C:\Program Files\Windows Media Player\wmpnetwk.exe"
2012 SearchIndexer. C:\Windows\system32\SearchIndexer.exe /Embedding
2068 dwm.exe "C:\Windows\system32\Dwm.exe"
2116 explorer.exe C:\Windows\Explorer.EXE
2264 taskhost.exe "taskhost.exe"
3716 wuauclt.exe "C:\Windows\system32\wuauclt.exe"
3896 taskhost.exe "taskhost.exe"
3872 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default
3952 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\lord-mr1tyu\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\lord-mr1tyu\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.165 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.140 --initial-client-data=0xac,0xb0,0xb4,0x80,0xbc,0x7199f598,0x7199f5a8,0x7199f5b4
3104 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1404 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:3
2100 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1656 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:8
588 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=4379902650 --mojo-platform-channel-handle=2296 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
2284 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1620 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:2
2304 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=4399592727 --mojo-platform-channel-handle=4160 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
1112 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --mojo-platform-channel-handle=4284 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:8
2784 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=4593680368 --mojo-platform-channel-handle=3936 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
3192 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=55 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=11084188365 --mojo-platform-channel-handle=5448 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
3088 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=74 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=11856249352 --mojo-platform-channel-handle=5028 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
3300 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=77 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=11867467064 --mojo-platform-channel-handle=4764 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
2824 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=78 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=11872438455 --mojo-platform-channel-handle=6156 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
696 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=90 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=13810409802 --mojo-platform-channel-handle=6436 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
2528 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=102 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=14109354445 --mojo-platform-channel-handle=3648 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
2840 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=110 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=15082931910 --mojo-platform-channel-handle=7092 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
1636 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=116 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=15178364762 --mojo-platform-channel-handle=6652 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
2136 taskmgr.exe "C:\Windows\system32\taskmgr.exe" /1
2356 WinRAR.exe "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\lord-mr1tyu\Downloads\Trojans.rar"
3848 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=155 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=20196413819 --mojo-platform-channel-handle=7480 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
1264 audiodg.exe C:\Windows\system32\AUDIODG.EXE 0x808
2380 MRCv120.exe "C:\Users\lord-mr1tyu\Downloads\MRCv120.exe"
2636 iexplore.exe "C:\Program Files\Internet Explorer\iexplore.exe" http://www.avp.ru/
2756 iexplore.exe "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2636 CREDAT:267521 /prefetch:2
1000 ie_to_edge_stu Required memory at 0x7ffdf010 is not valid (process exited?)
3616 ie_to_edge_stu Required memory at 0x7ffd3010 is not valid (process exited?)
4848 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=180 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=20952615036 --mojo-platform-channel-handle=7512 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
4936 msedge.exe "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=181 --time-ticks-at-unix-epoch=-1712989098458717 --launch-time-ticks=20963783767 --mojo-platform-channel-handle=7032 --field-trial-handle=1284,i,15575738720015917717,4132625940781285365,131072 /prefetch:1
5716 cmd.exe C:\Windows\system32\cmd.exe /c ""E:\AUTOEXEC.BAT" "
5724 conhost.exe \??\C:\Windows\system32\conhost.exe "1118329821-1006554123-177061749116503517041263593121912131584-367562364-1474603904
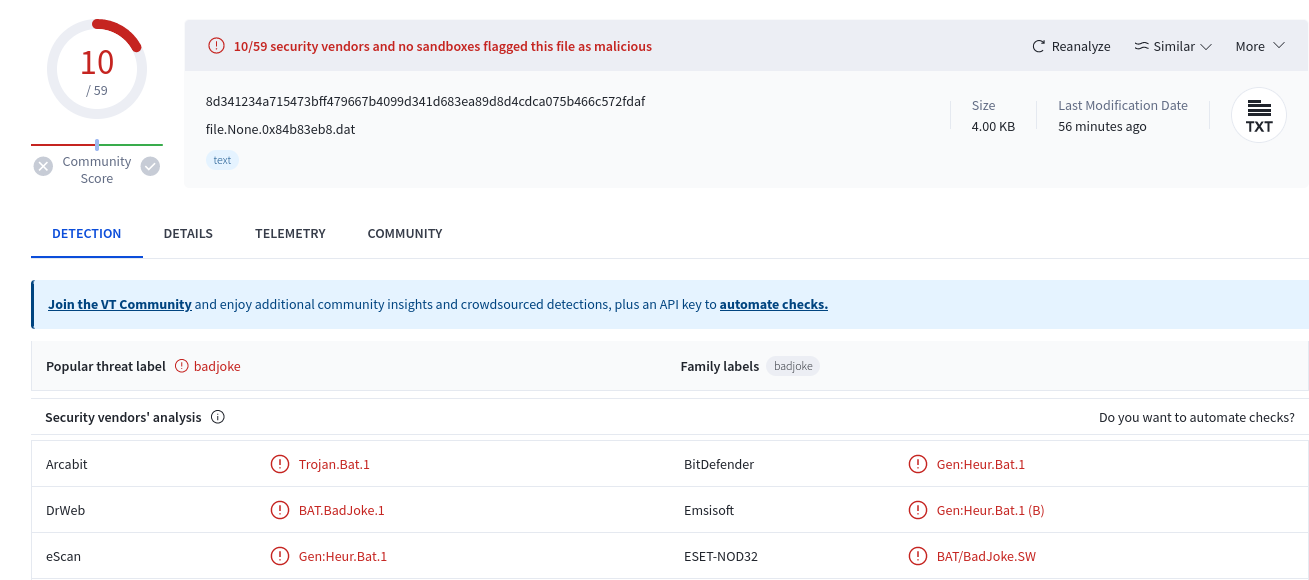
With these output, several programs can be identified as suspicious. This includes Trojans.rar and AUTOEXEC.BAT. Checking files related to Trojans, another suspicious file can be identified as DudleyTrojan.bat with a physical address of 0x64ac7a18 (I have no clue why it’s this address). Uploading the malware on VirusTotal, the Trojan seems to be malicious after all.
1
2
3
4
5
6
7
8
└─$ python3 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw windows.filescan | grep "Trojan"
0x6486f938 100.0\DudleyTrojan.bat 128
0x64a24a70 \DudleyTrojan.bat 128
0x64a33cc8 \Users\lord-mr1tyu\Downloads\DudleyTrojan.bat 128
0x64ac7a18 \DudleyTrojan.bat 128
0x64b9ae20 \Users\lord-mr1tyu\Downloads\DudleyTrojan.bat 128
0x64bbd688 \Users\lord-mr1tyu\AppData\Roaming\Microsoft\Windows\Recent\Trojans.lnk 128
0x64d62950 \Users\lord-mr1tyu\Downloads\DudleyTrojan.bat98.crdownload 128
Teenage Mem [Forensics]
Question: Sorry but lastly, please give me the md5 hash of the virus… See you all next time:)
Flag: 0CTF{0bf9e9f7e629cde113b50513d6ea6f34}
Just dump the malicious file and get its md5 hash.
1
2
3
4
5
6
7
8
9
└─$ python3 vol.py -f ~/Desktop/sharedfolder/mr1tyu.raw -o ~/Desktop/bin windows.dumpfiles --physaddr 0x64ac7a18
Volatility 3 Framework 2.5.2
Progress: 100.00 PDB scanning finished
Cache FileObject FileName Result
DataSectionObject 0x64ac7a18 DudleyTrojan.bat file.0x64ac7a18.0x84e0cce8.DataSectionObject.DudleyTrojan.bat.dat
└─$ md5sum file.0x64ac7a18.0x84e0cce8.DataSectionObject.DudleyTrojan.bat.dat
0bf9e9f7e629cde113b50513d6ea6f34 file.0x64ac7a18.0x84e0cce8.DataSectionObject.DudleyTrojan.bat.dat
Dawg [OSINT]
Question: Thats not a dog, thats a dawg, but who does it belong to?
Flag: 0CTF{Kevin_Systrom}
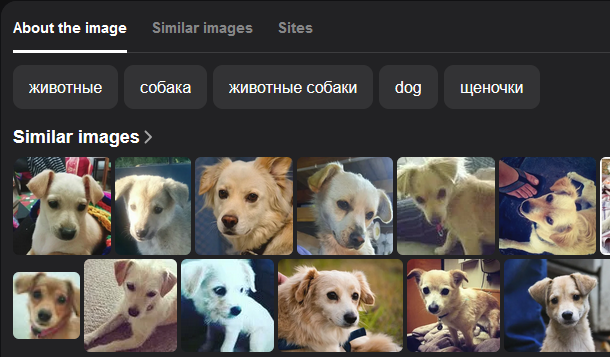
We are tasked to identify the owner of the dog with the image of the dog.
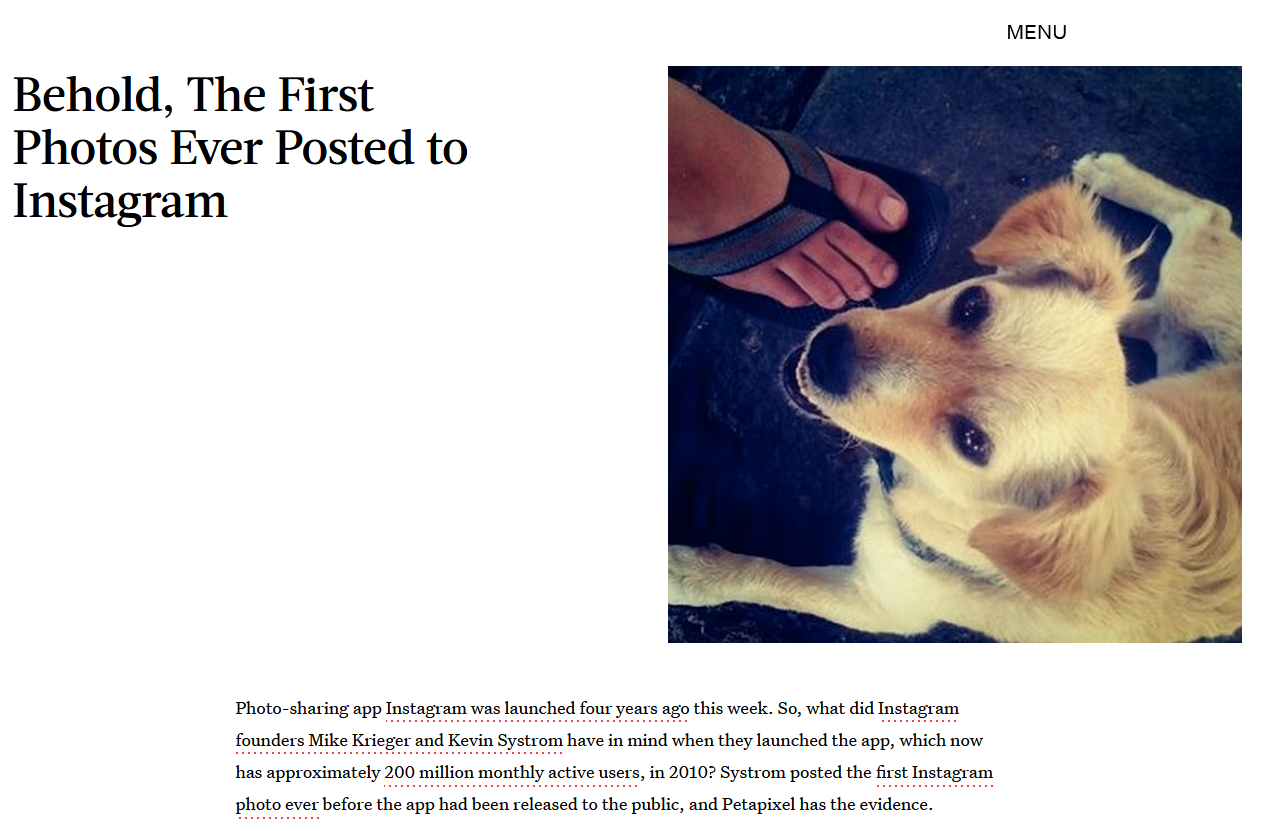
Reverse searching the image on Google and Yandex, the original photo can be found on Yandex which leads us to a blog.
Reading the blog, the image seems to be the first Instagram post ever and the dog’s owner can be identified as Kevin Systrom.
Uncover the Tea [OSINT]
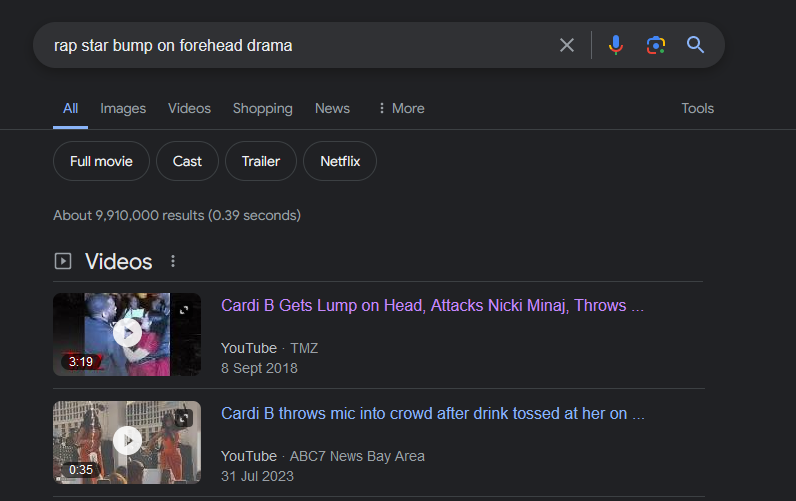
Question: Yo, so imagine this crazy drama dive, fam! You got two major rap stars going at it like it’s nobody’s business, taking their beef from tweets to real-life blows at some fancy event. One even came out with a massive bump on her forehead,yeah, that’s your clue, no cap fr dude, like, it was straight-up insane! And then, there’s this record label, right? Rumor has it they were trading avocado toast recipes or arguing over who’s got the better Spotify playlist. They’re in deep trouble, with lawsuits flying left and right, shady deals going down, it’s like watching a Netflix thriller unfold, fr. But wait, there’s more! There’s this whole motorsport incident that went down, with rumors flying about who was involved and what actually went down, man. It’s like a whole conspiracy theory brewing, with twists and turns hotter than the tea we spill, you feel me? And speaking of brainstorming, I heard they were sipping on some green, but not the organic kind you find at Whole Foods. Nah, bruh, we’re talking that Netflix series-level drama, with more plot twists than a Kanye West tweet. So grab your popcorn and get ready for the tea, ‘cause this story’s about to get wilder than my DMs after a breakup!
Flag: 0CTF{NYFW_2018_Cardi_Minaj}
We are tasked to retrieve information about the drama between two famous rap stars where one of them had a massive bump on her forehead. Googling about it, the rap stars can be identified as Cardi B and Nicki Minaj.
Researching about this drama, I stumbled upon this article that mentions them fighting during the New York fashion week 2018.
who stole? [OSINT]
Question: One of our members love guitar and music. Don’t wanna badmouth but he’s a boomer, bro uses YouTube instead of Spotify XD. Also, he’s very defensive of his fav artists and will not like if anyone sample their beats (or as he calls that “stealing”)
Flag: 0CTF{mu51c41_fl4g}
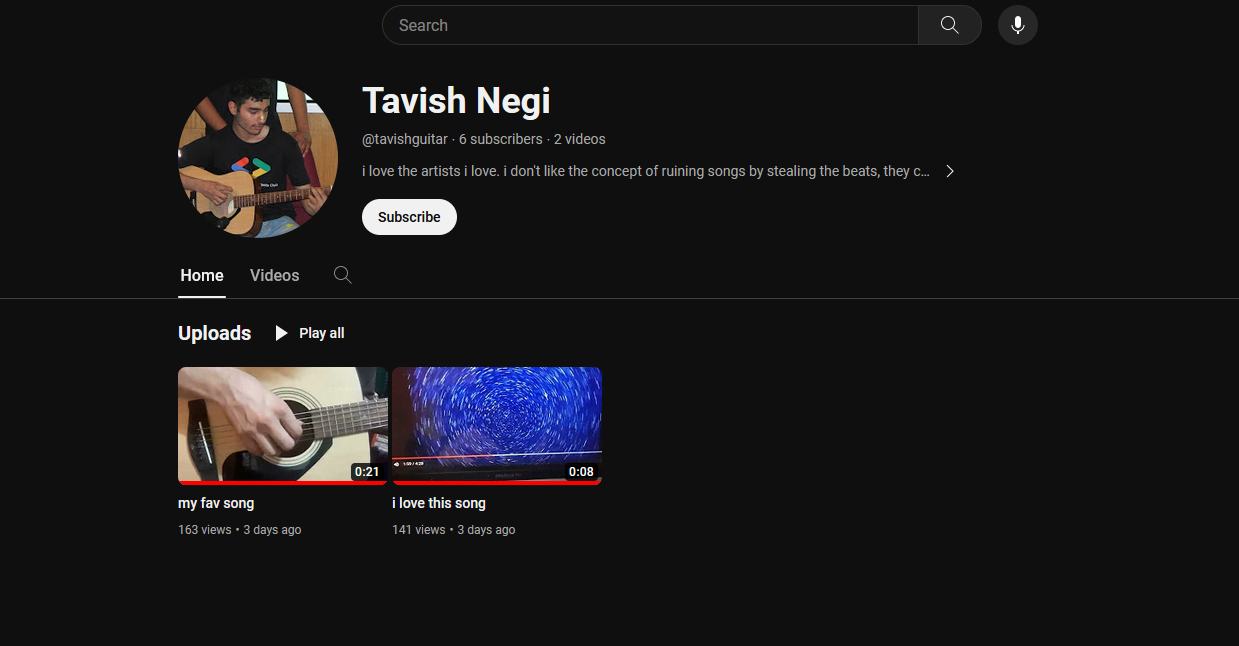
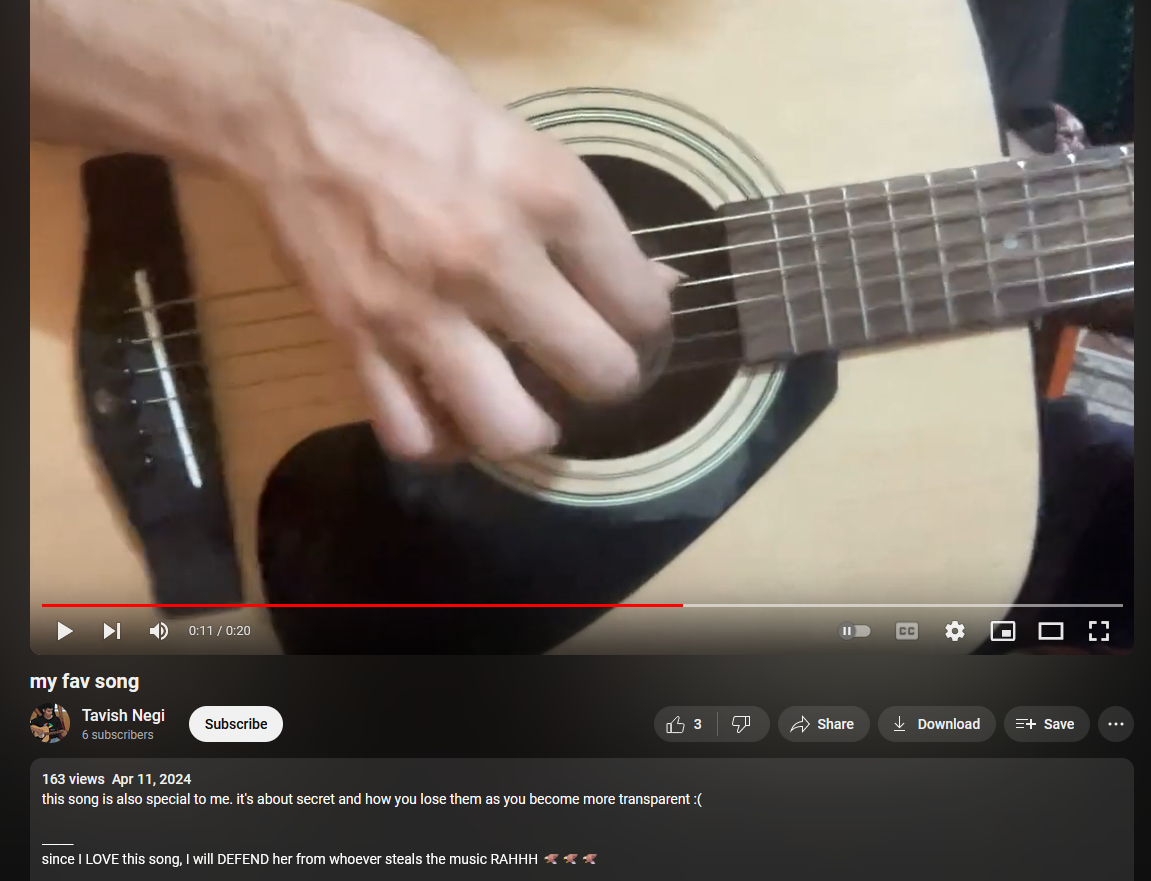
We are tasked to retrieve information about a user that loves music. It seems that one of the organizers has a YouTube channel where they post their music covers. Going through some of them, I found out it was Tavish Negi/tavilefty.
The question and his Youtube status shows that he really hates sampled music.
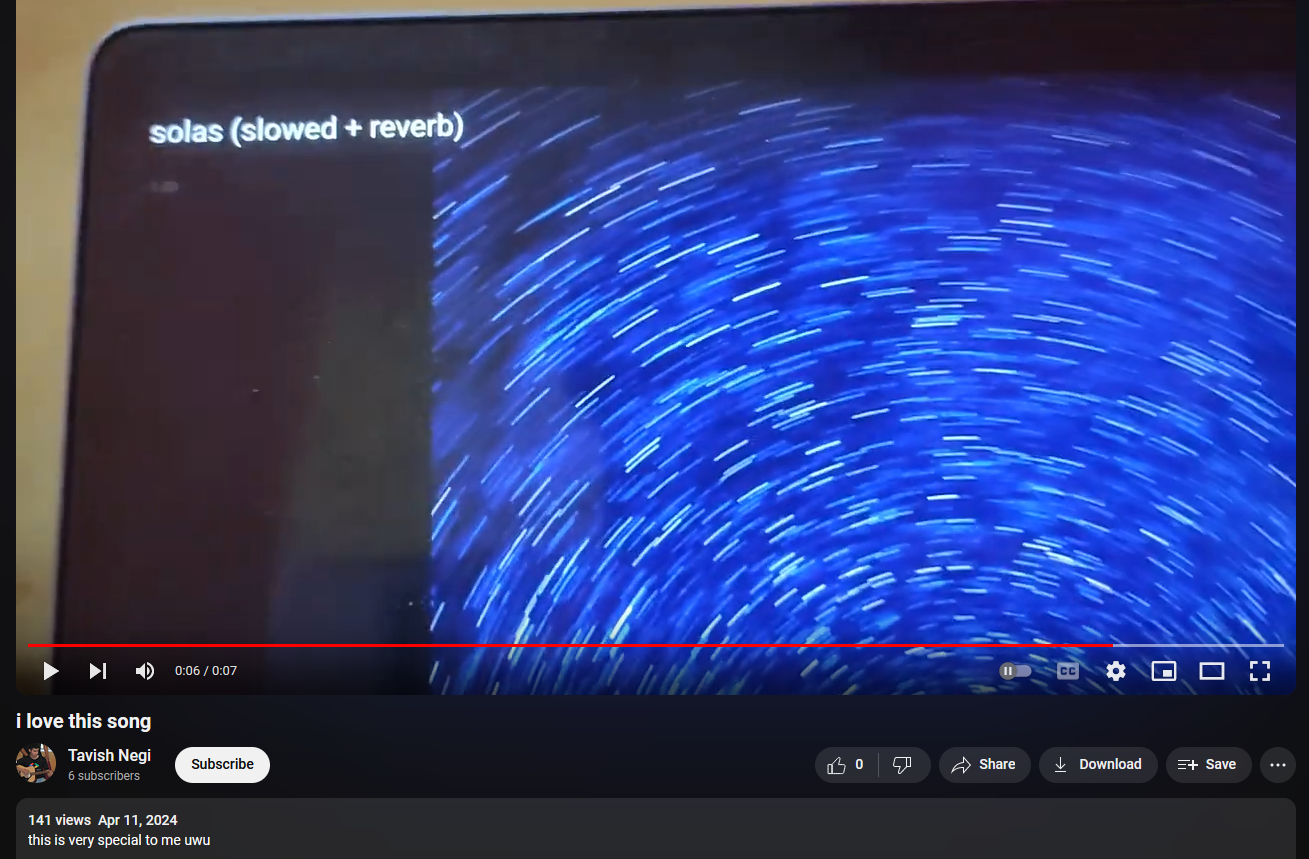
Going through his videos, both of them feature a different song. One of them was solas (slowed+reverb) as shown in the video.
However, his second video was him playing a cover music using his guitar. Initially I thought it was the same song, which made me fall into a rabbithole. But reading the video description, it seems that it was a cover for another song.
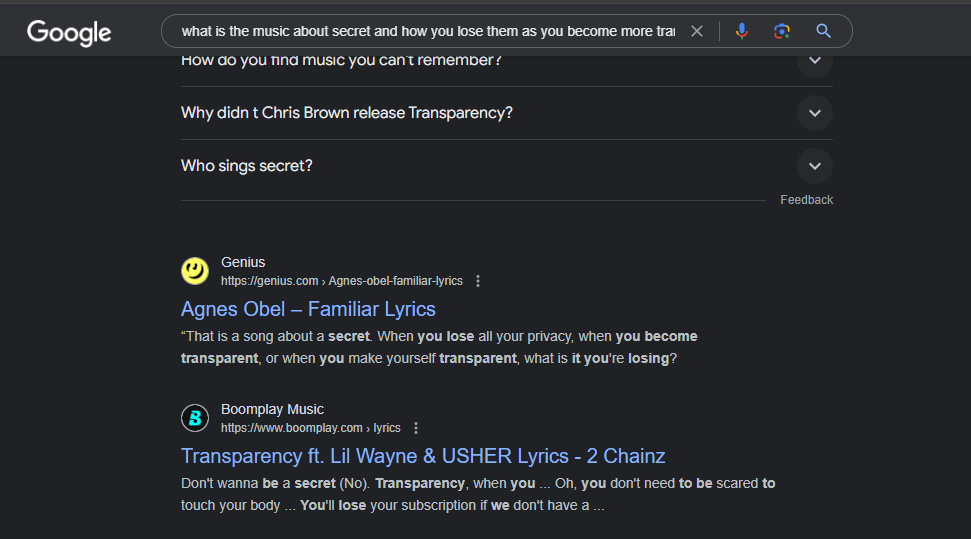
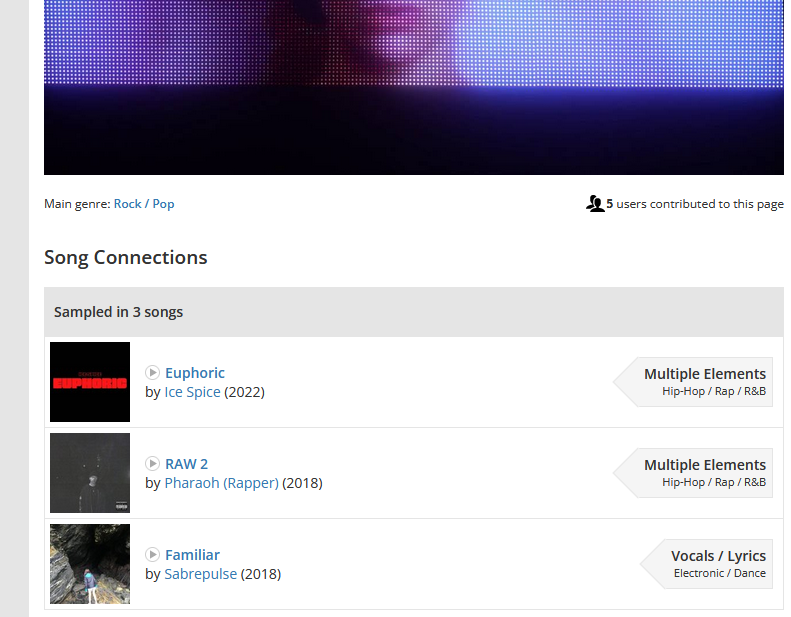
Googling the description about the song, we stumbled upon the music Agnes Obel – Familiar that seems to also talk about secrets and how losing them make us transparent. Checking the music on WhoSampledIt, we can see that the music was sampled in 3 different videos.
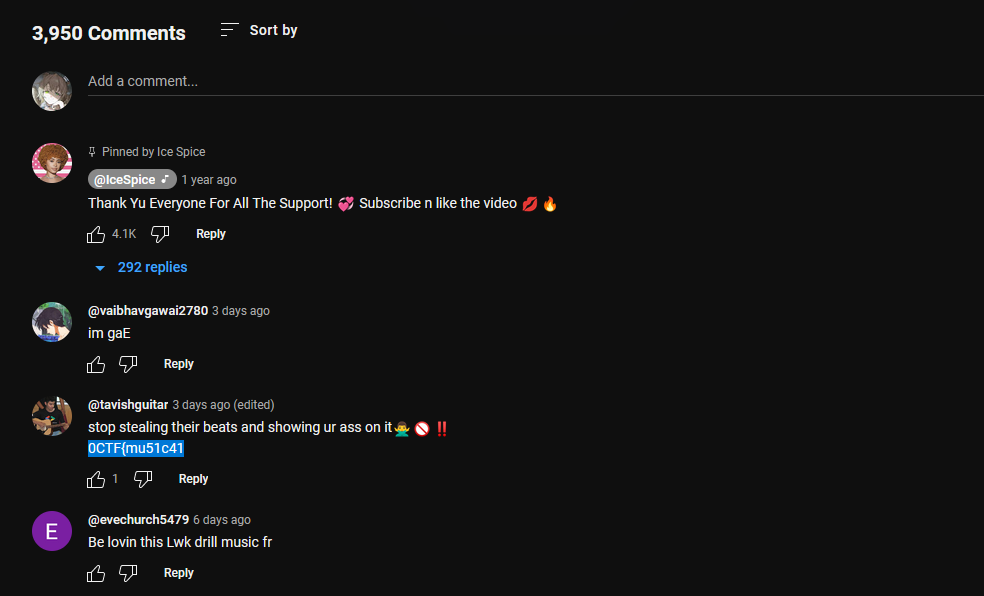
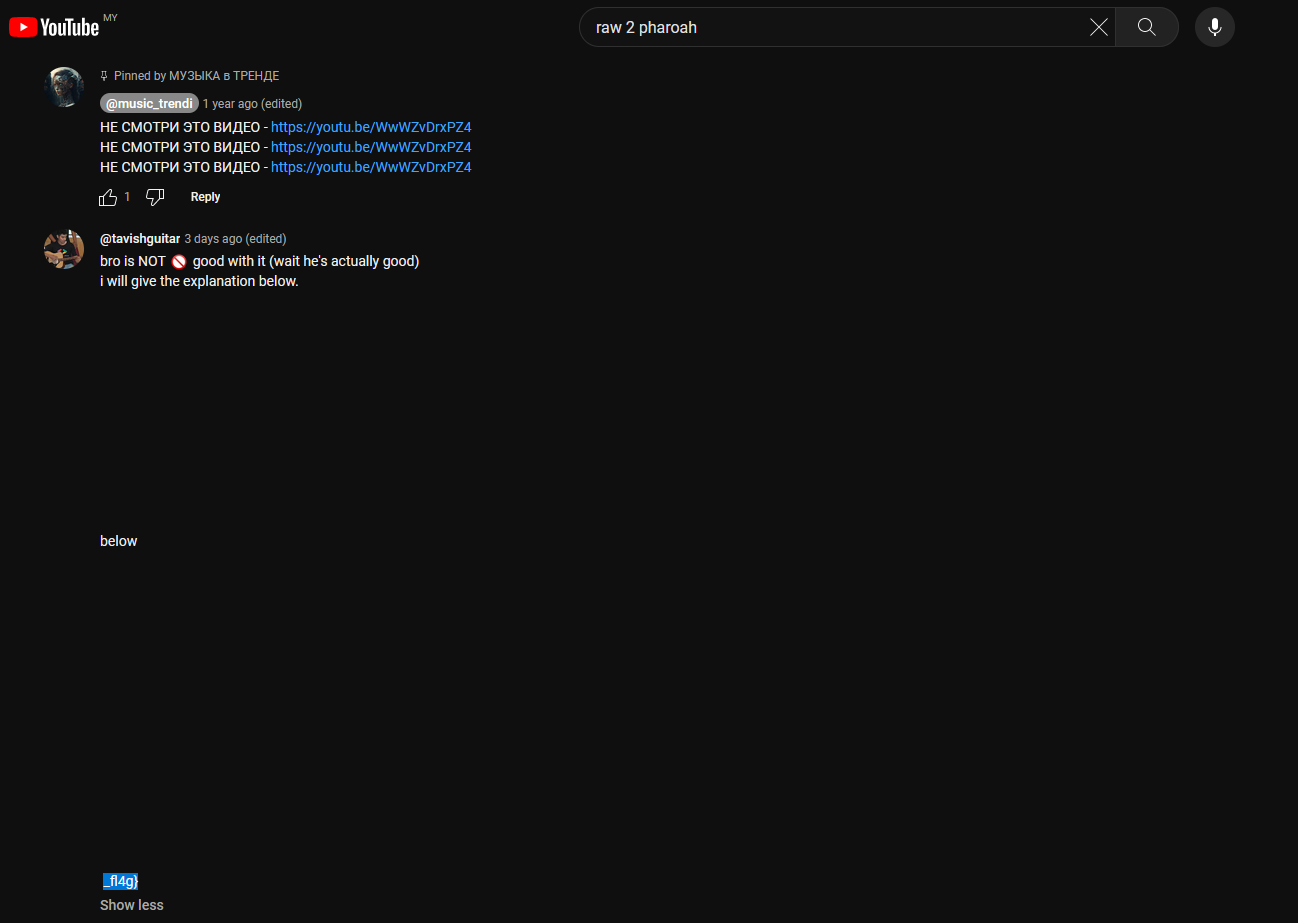
The first part of the flag can be obtained in the comments section of the music video from Ice Spice.
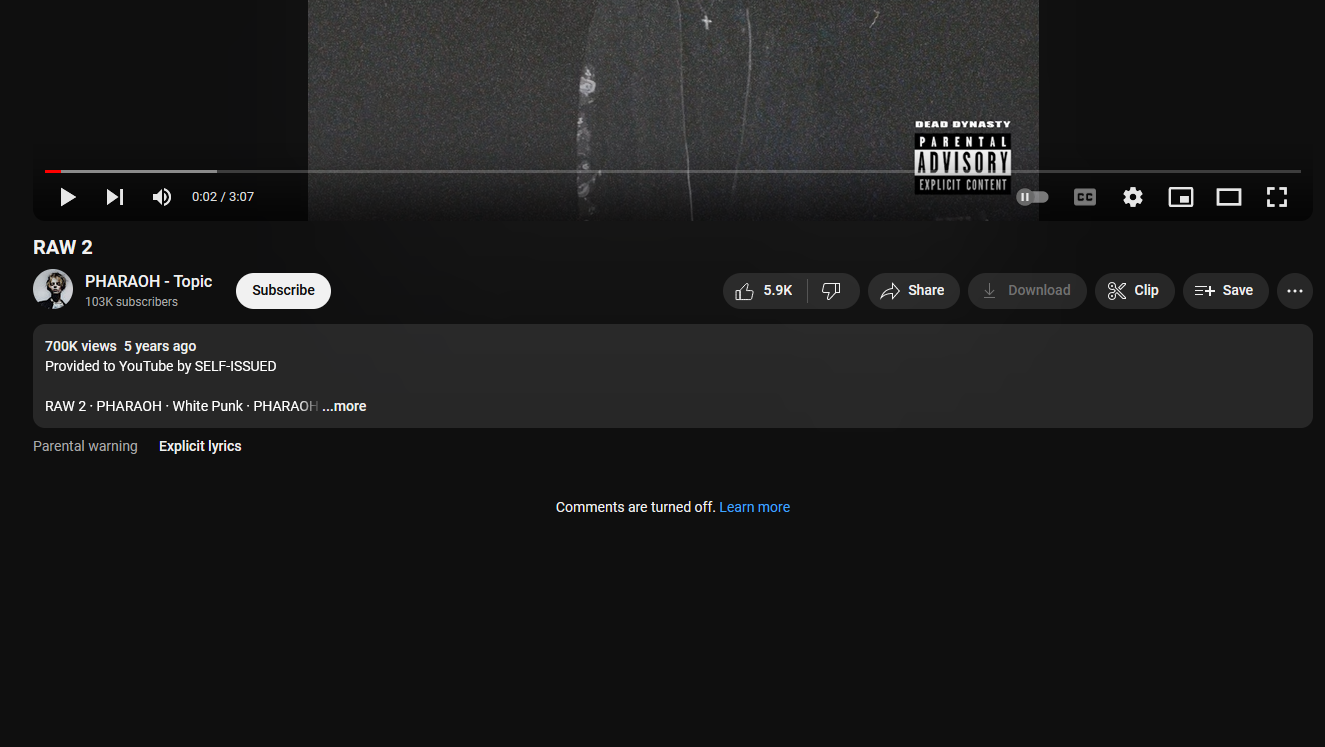
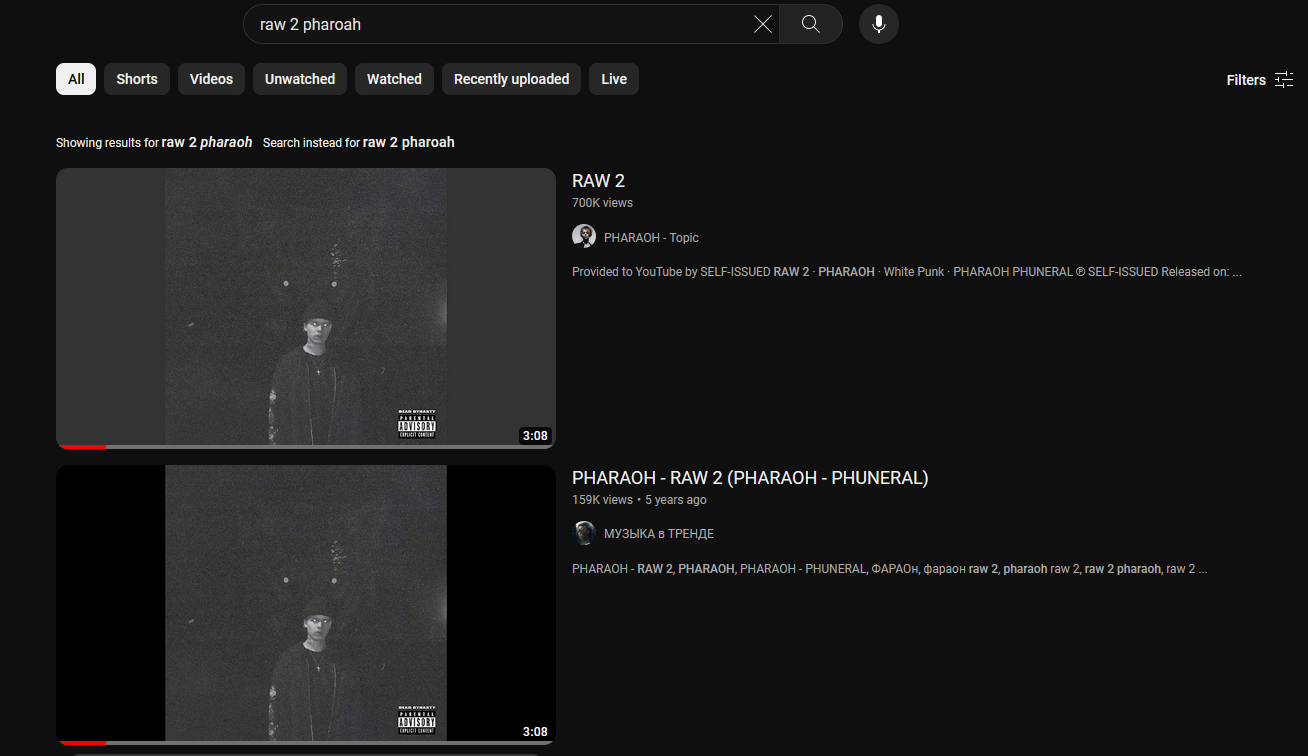
So I assumed the second flag is from one of the three videos again. However, the second music from PHAROAH had no comments enabled.
Searching up PHAROAH on Youtube, the second video seems to have comments enabled where the second flag can be obtained.
Gumm Ho Gaya Hu [Misc]
Question: Hello, my friends, this is yo boi Snip3R straight outta P-town, here we go another web challenge from me, saw your rants and thought of creating an EZPZ challenge for ya’ll (maybe). So here you go, solve this ez web based chall currently introduced to misc section COZ WHY NOT. Mai jo guum hogaya hu inn aankho me jaan, Don’t you know bout mah love, ye an bewafa, Tere fizao me mai khoya reheta hu, Sab dil ki baate, tujhi se meri jaan (that was just rubbish nothing related to the challenge ~ maybe) A bit to describe, you ain’t getting da whole flag in a single go, so keep hunting like my sweet little child. 💋
Flag: 0CTF{50m371m35_17_0nly_l00k5_d1ff1cul7_bu7_15n7_4c7u4lly}
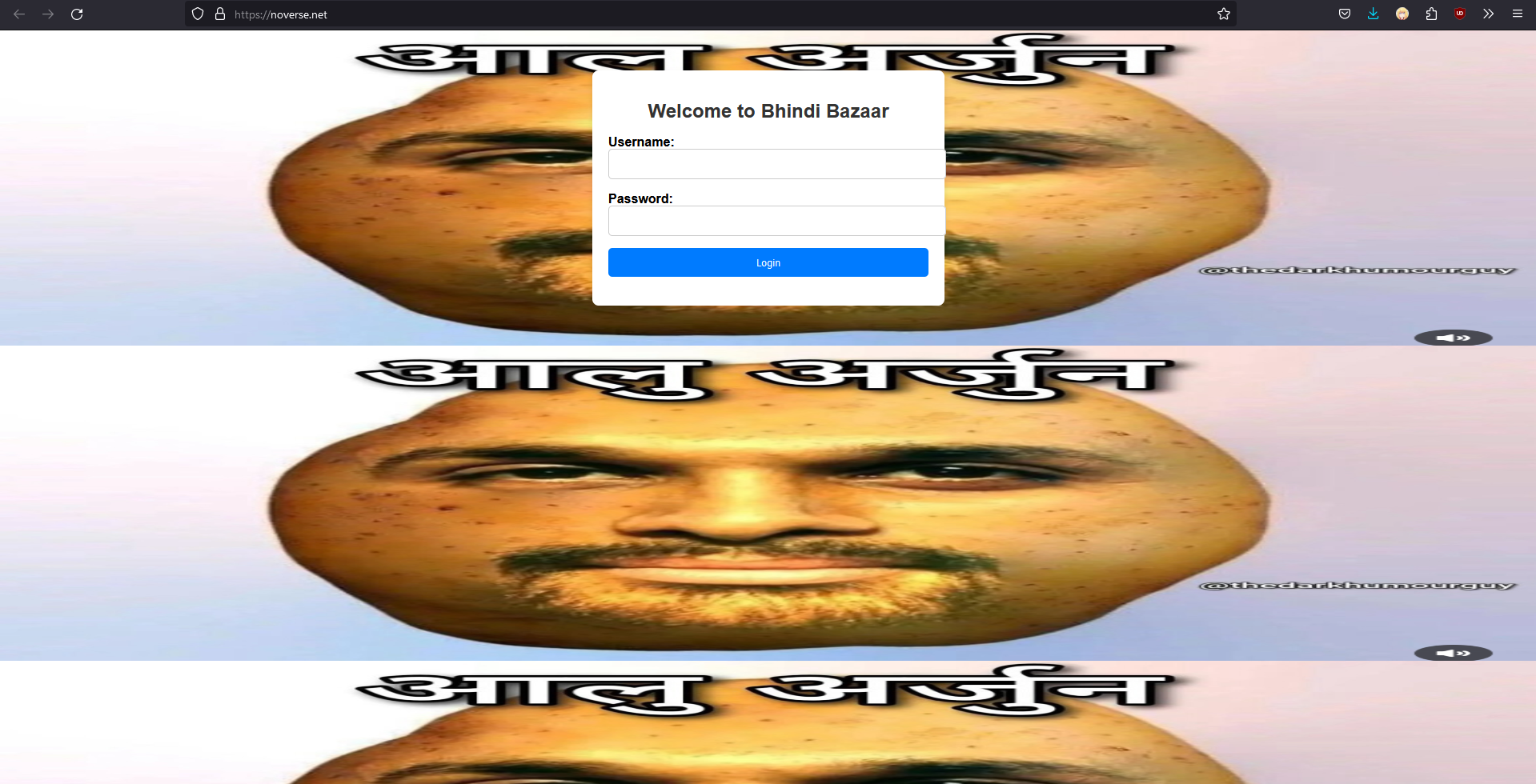
We are given a website to investigate.
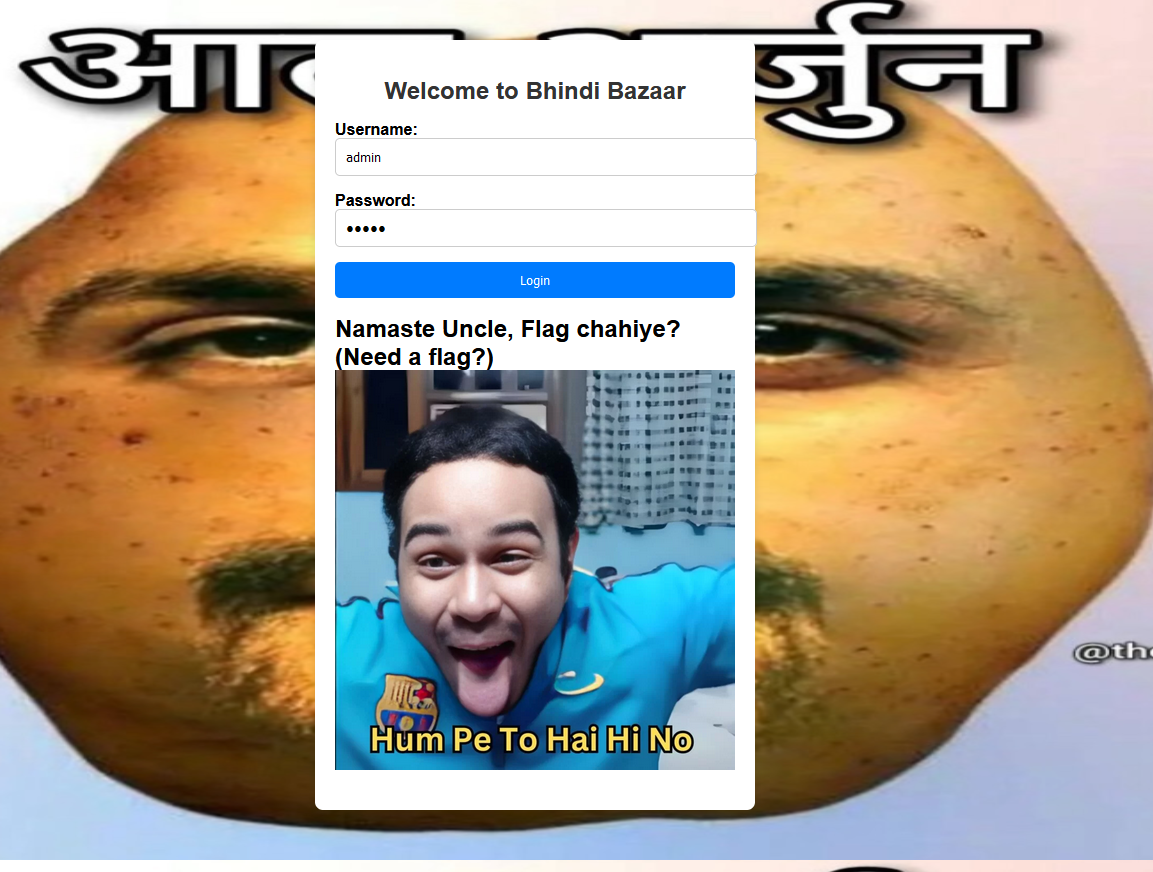
The website had a login form that may be exploitable. Trying the classic admin:admin credentials, it gave a picture that is not related to the challenge at all.
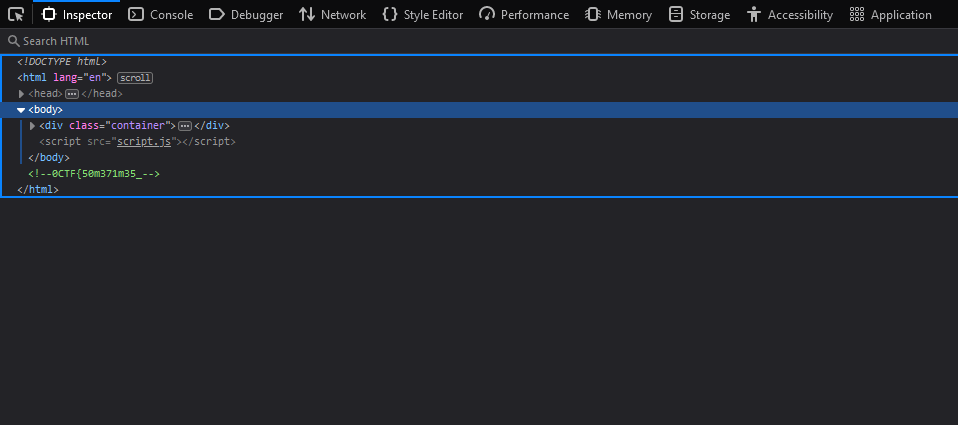
Checking the page source, the first part of the flag can be obtained.
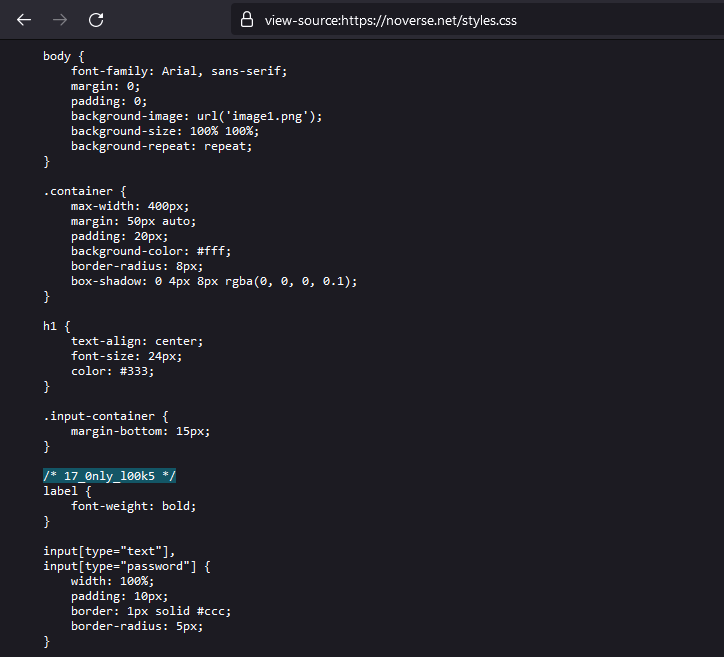
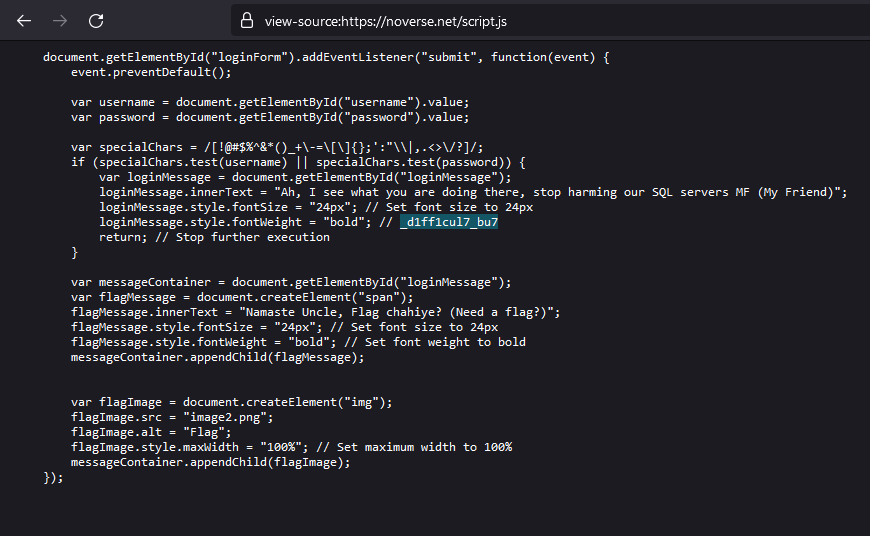
The second and third part of the flag can be obtained in the CSS and Javascript code respectively.
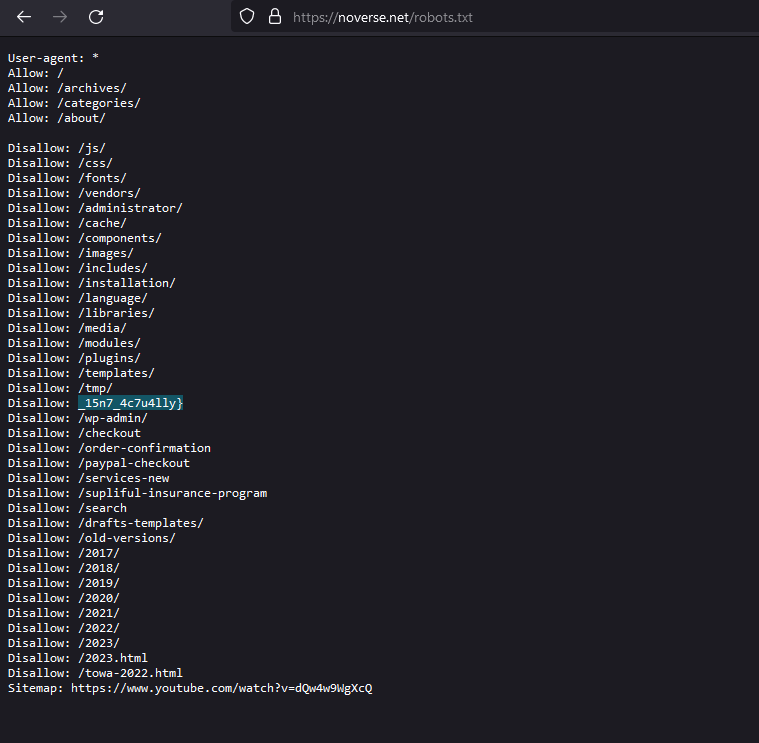
Since we are doing a challenge on a static website, robots.txt might work as it is a very common web technique. Using it, the last part of the flag can be obtained.