San Diego CTF 2024 - Writeups
This is a writeup for all forensics challenges from San Diego CTF 2024. Overall, a pretty difficult CTF where each challenge will require critical thinking. This CTF was also my first time trying out reverse engineering challenges.
Finding Savage [OSINT]
Question: While I was at a security lunch, I overheard Professor Savage talking about how he uses one of those services that continually removes name off data broker sites. But I’m sure you can still find his address somewhere online…
Flag: sdctf{#### STREET CITY STATE ZIP} (Redacted due to privacy issues)
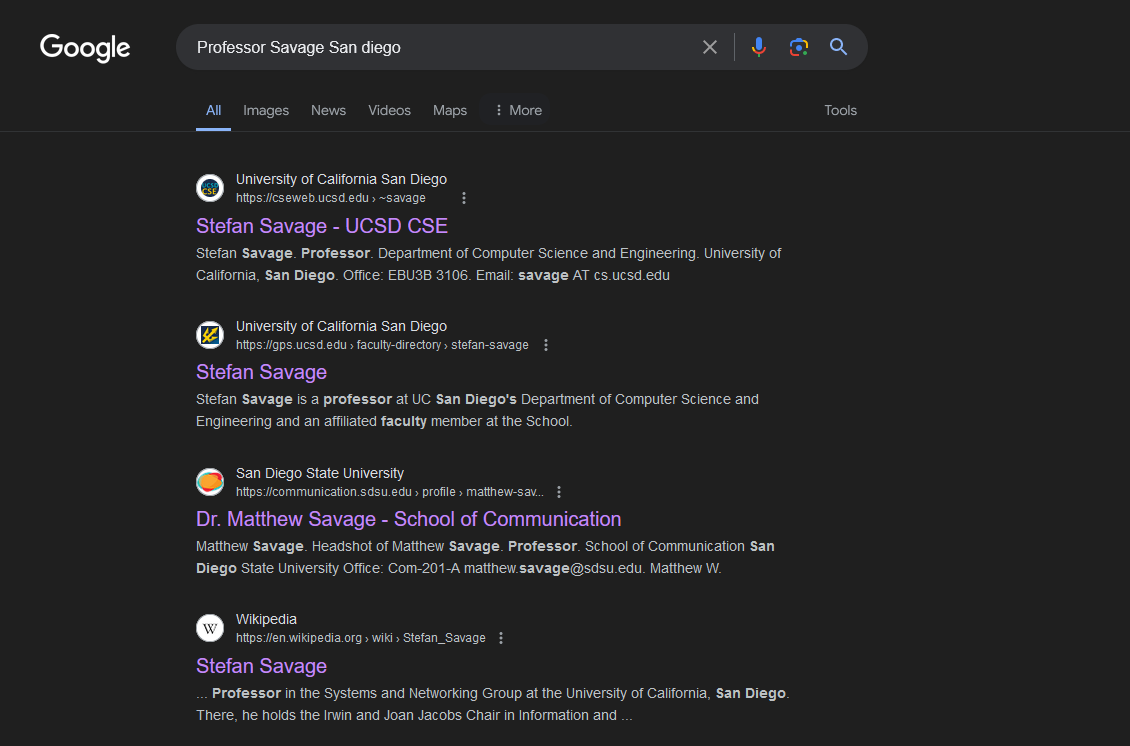
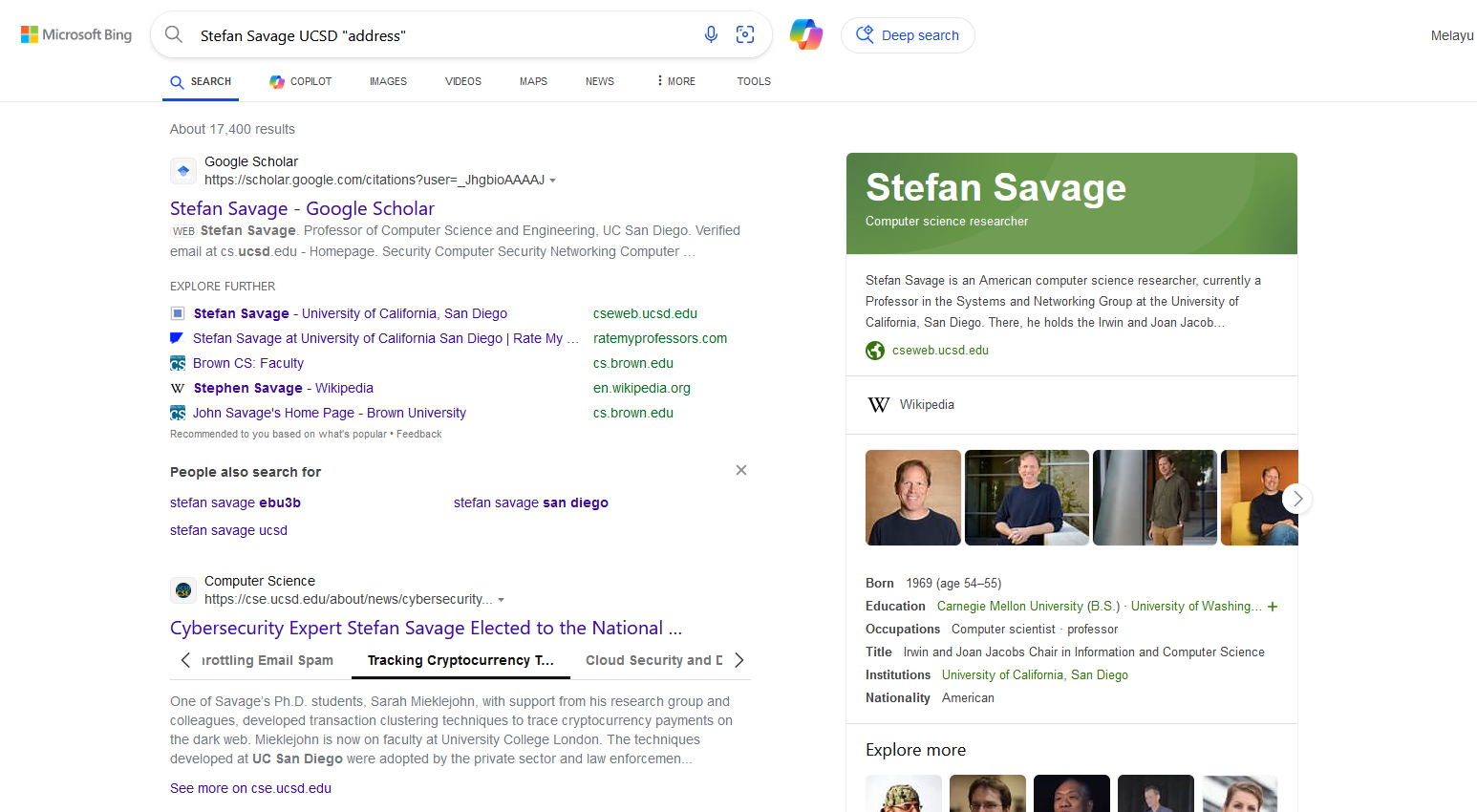
Googling about Professor Savage in San Diego, the results show a person called Stefan Savage that teaches in the University of California, San Diego (the CTF organizer’s university). However, Google does not show any results about his home address.
So by utilizing other search engines like Bing Search, his home address can be obtained easily in a website.
Chill Beats [OSINT]
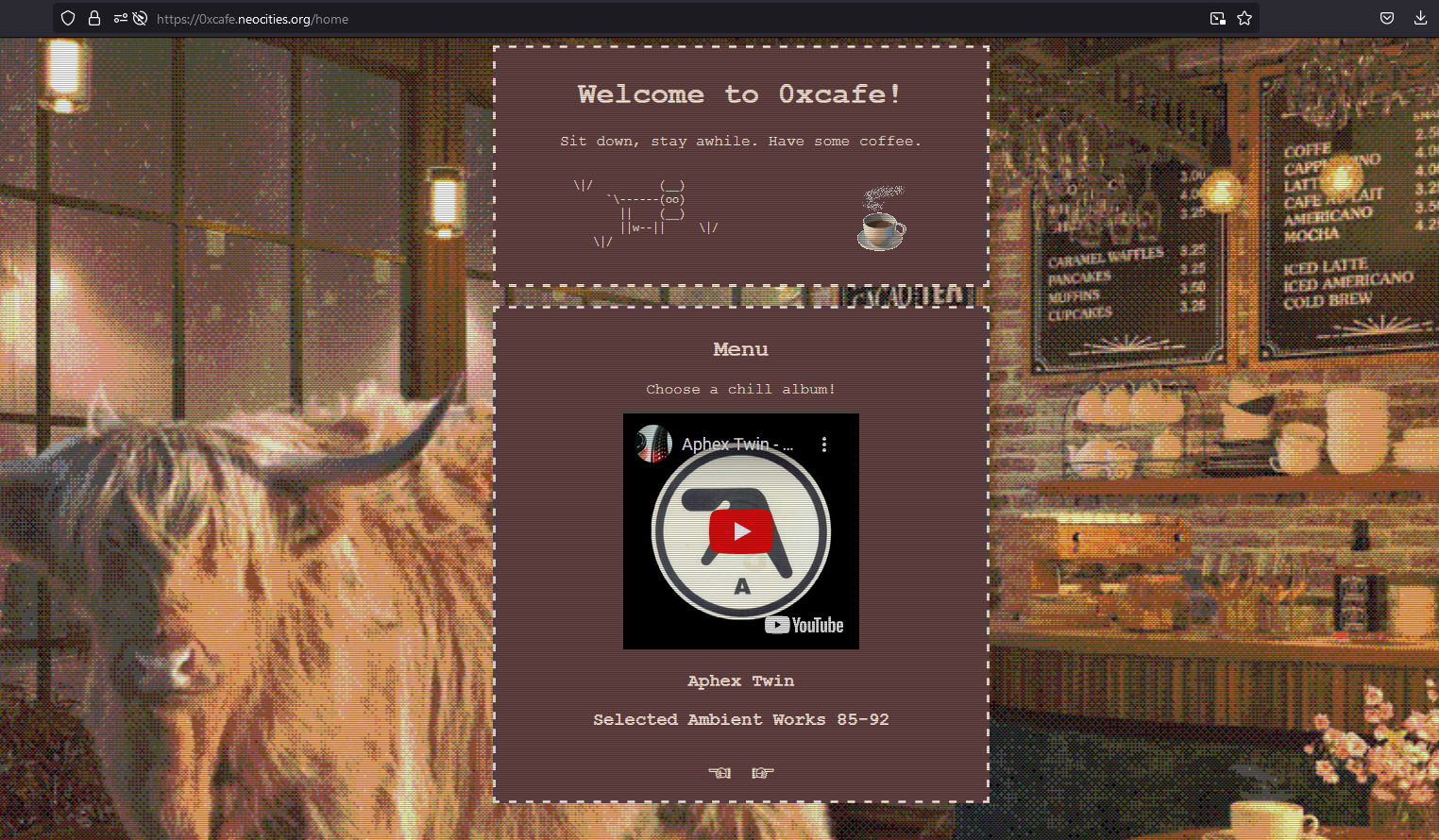
Question: Why don’t we all just take a break from hacking and enjoy some music on my webpage? https://0xcafe.neocities.org/
Hint: There’s also lots of other sites out there streaming sweet jams!
Flag: sdctf{0xc0ff3-FM}
We are given a website to investigate. Inside it, it was just a music streaming website using a YouTube playlist.
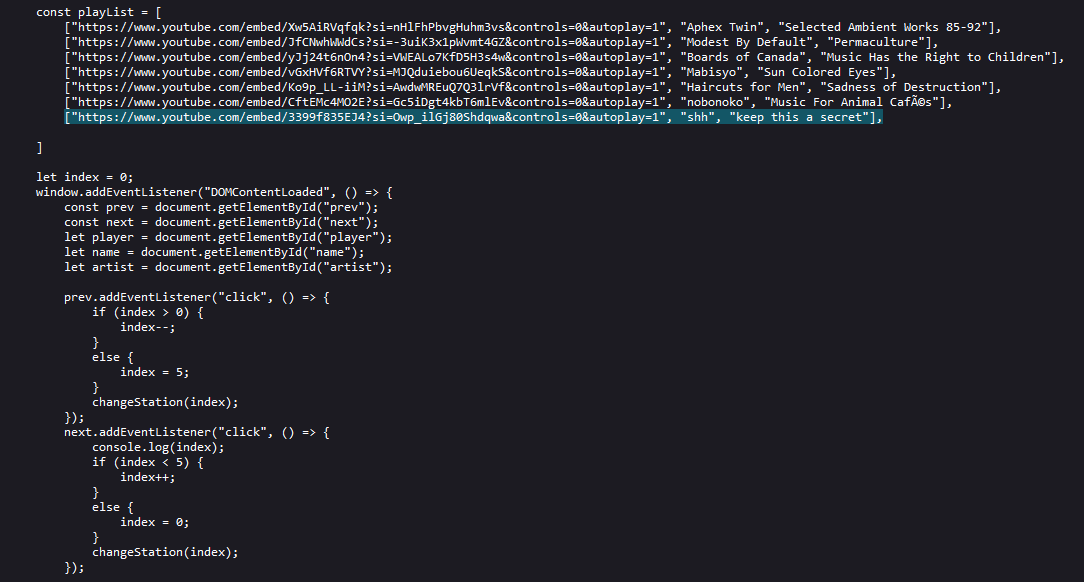
Analyzing its source code, a suspicious JavaScript can be found where a secret video was within the song playlist.
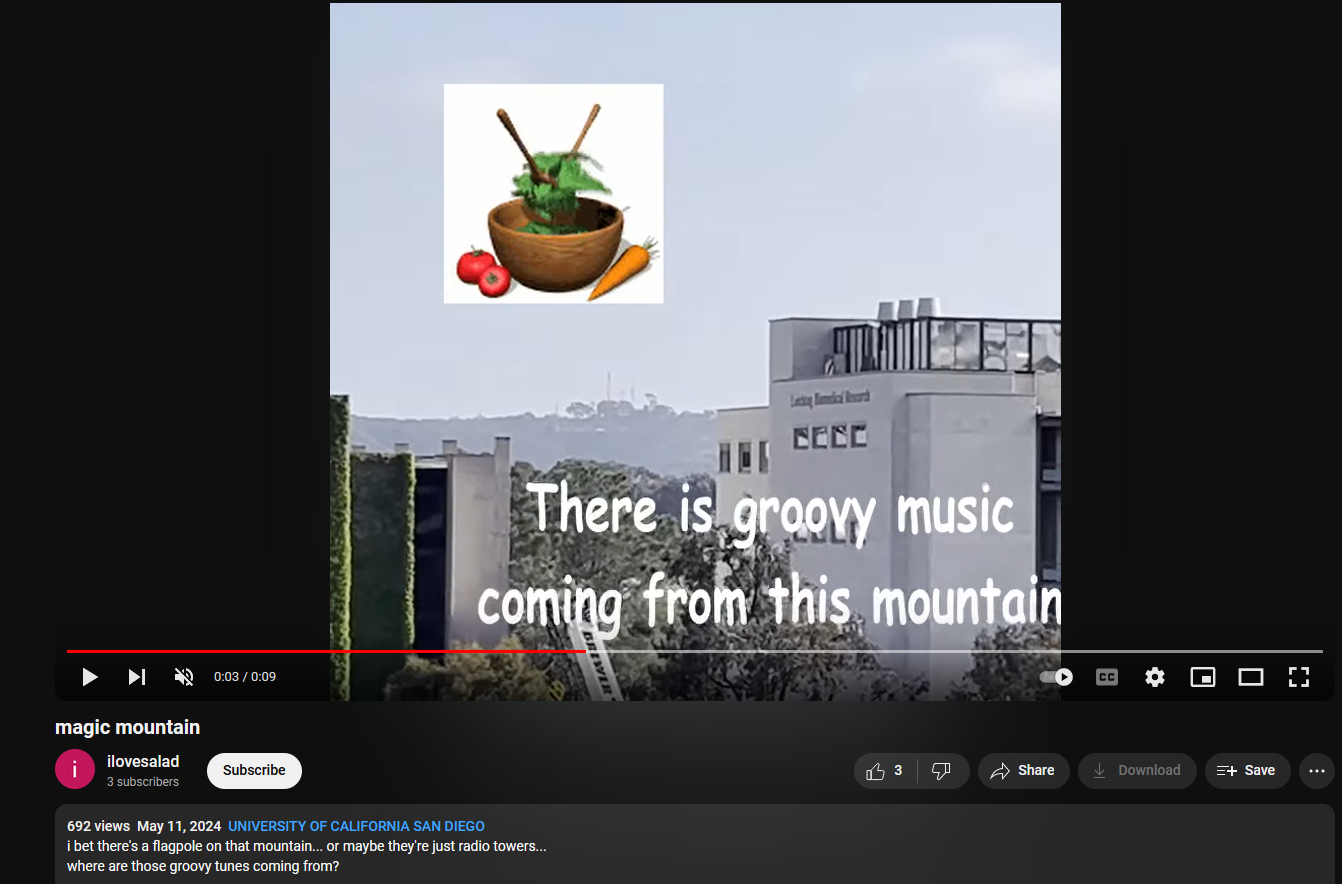
Checking out the secret video, it seems that it was a video pointing to a radio tower near San Diego University from a user called ilovesalad.
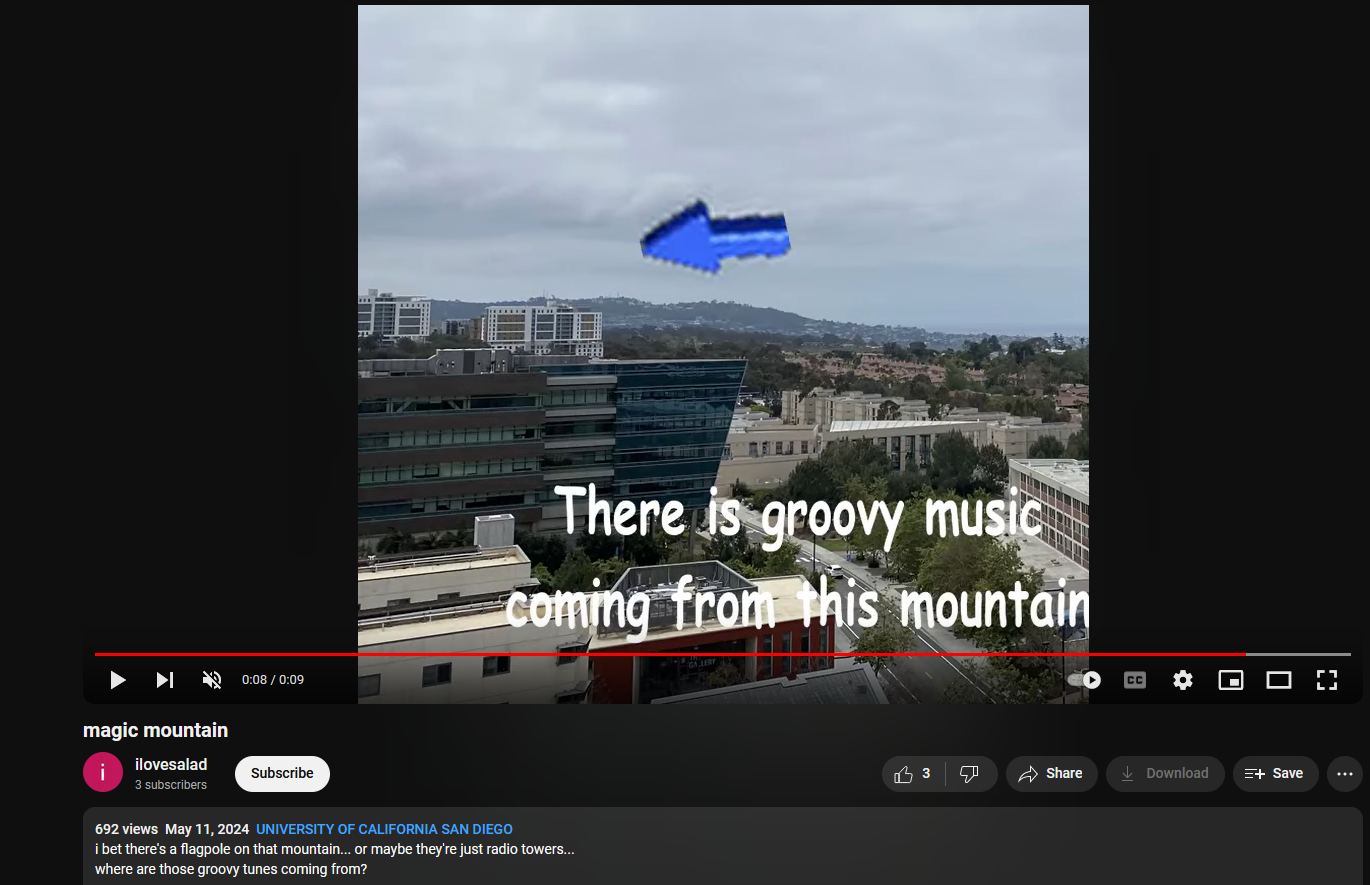
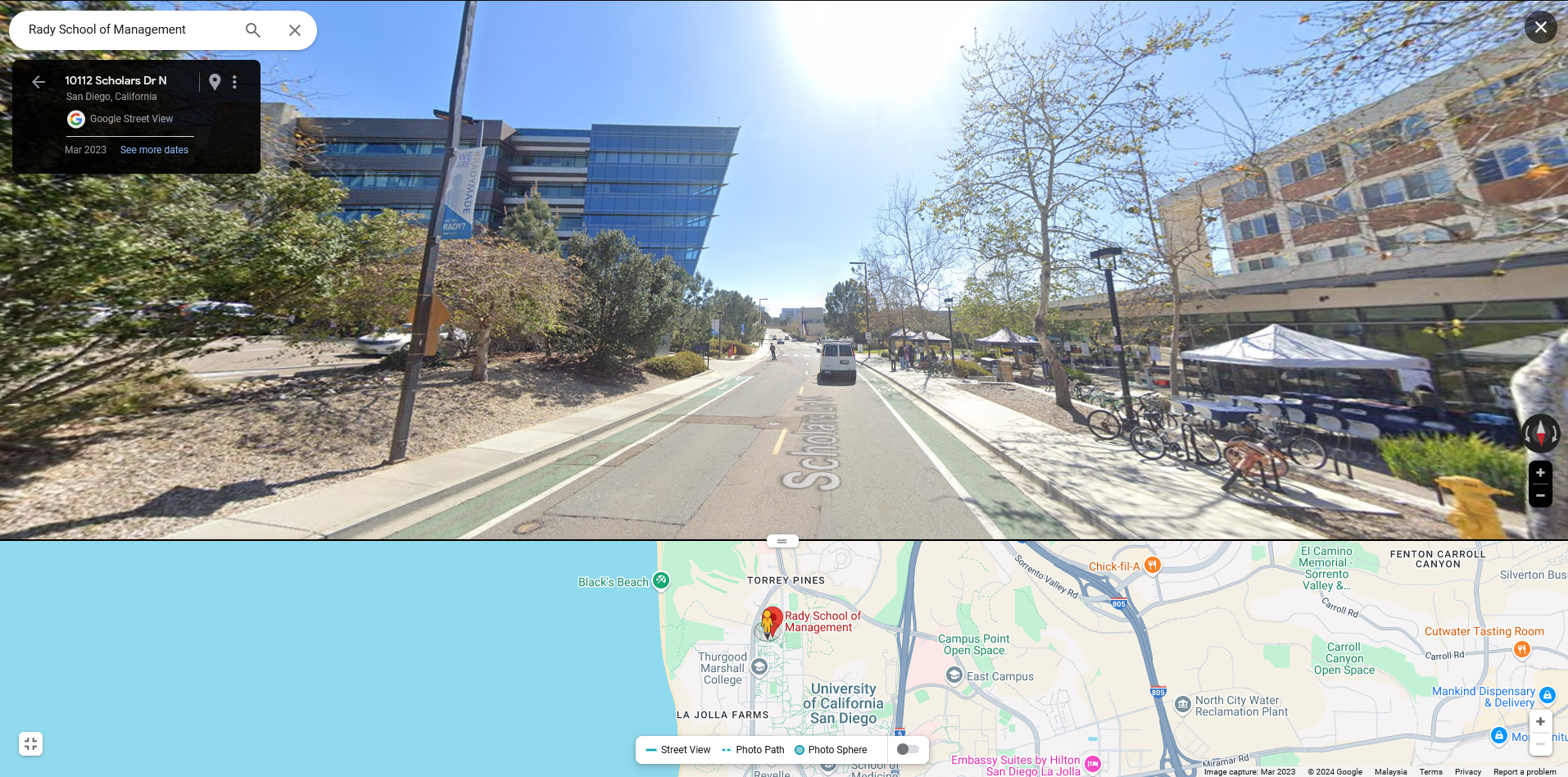
By doing some OSINT, I managed to find the exact location and direction of the building shown in the last seconds of the video. It seems that the mountain was South of the position where I am at judging from the video.
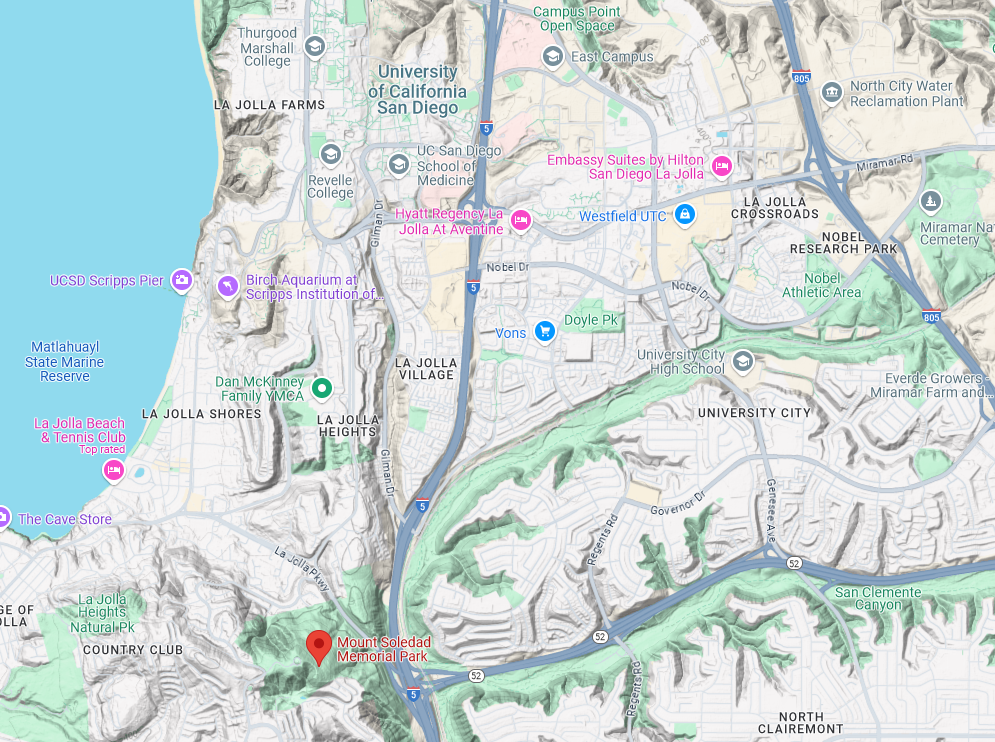
Going South from the building, we stumbled upon Mount Soledad. At this point I was pretty much stuck with the challenge as I could not find the right website that was streaming groovy tunes.
Apparently, after I went to bed, the authors changed the username of the channel owner to ilovesalad89.5. So we know the radio frequency is basically 89.5.
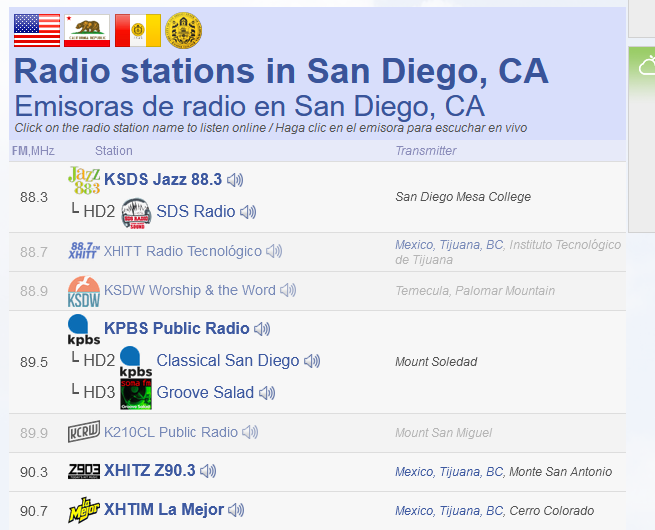
By using this website, we find a suspicious radio website name called Groove Salad and remembering that the YouTube user was ilovesalad, this seems to be the right radio website.
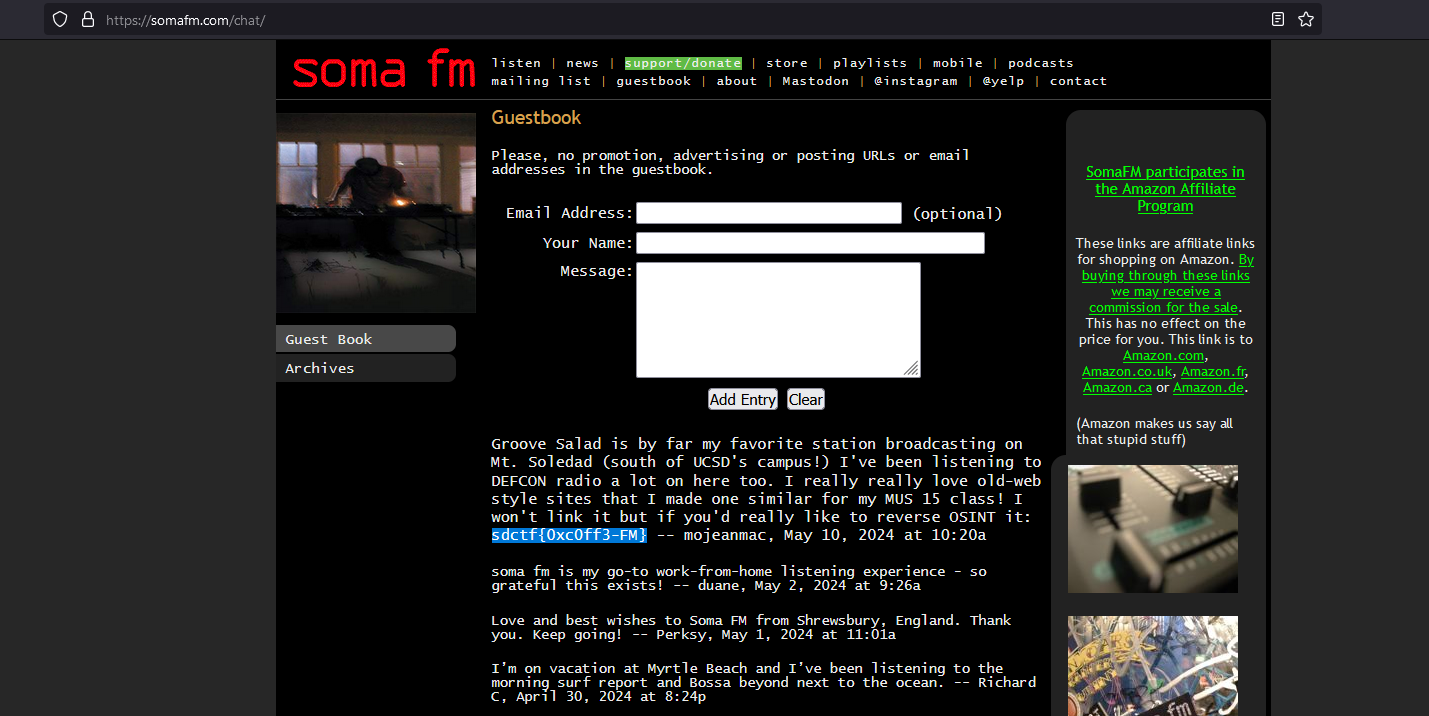
By searching up Groove Salad San Diego, this website was the result. Inside the website guestbook, the flag can be obtained.
Watch the Waves [Forensics]
Question: My friend sent me this cool image. It reminds me of the ocean! I love listening to the sound of crashing waves. (flag is all lowercase)
Flag: sdctf{l3tsg02th3b34ch}
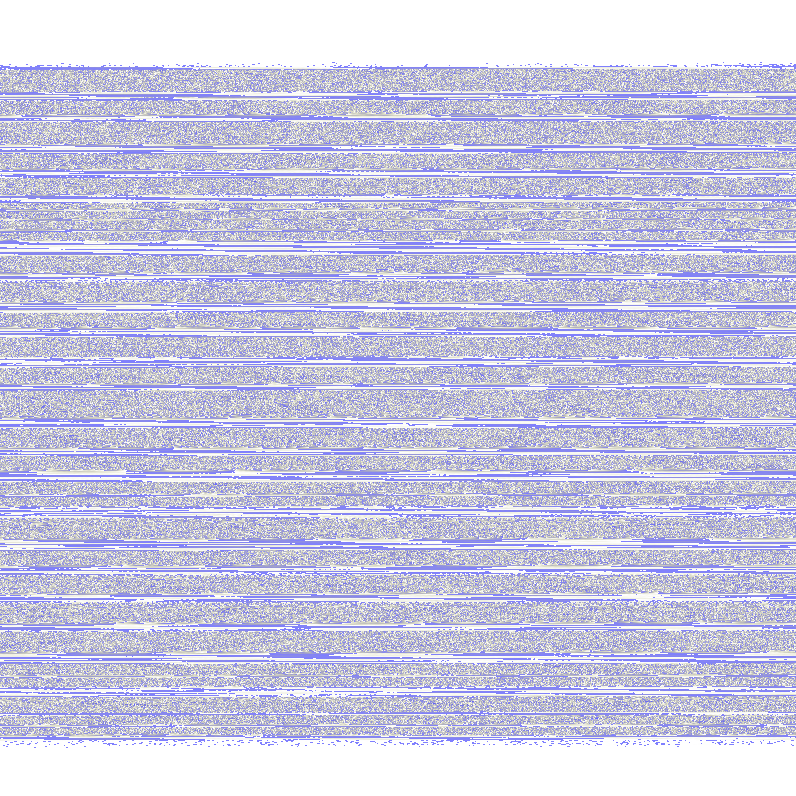
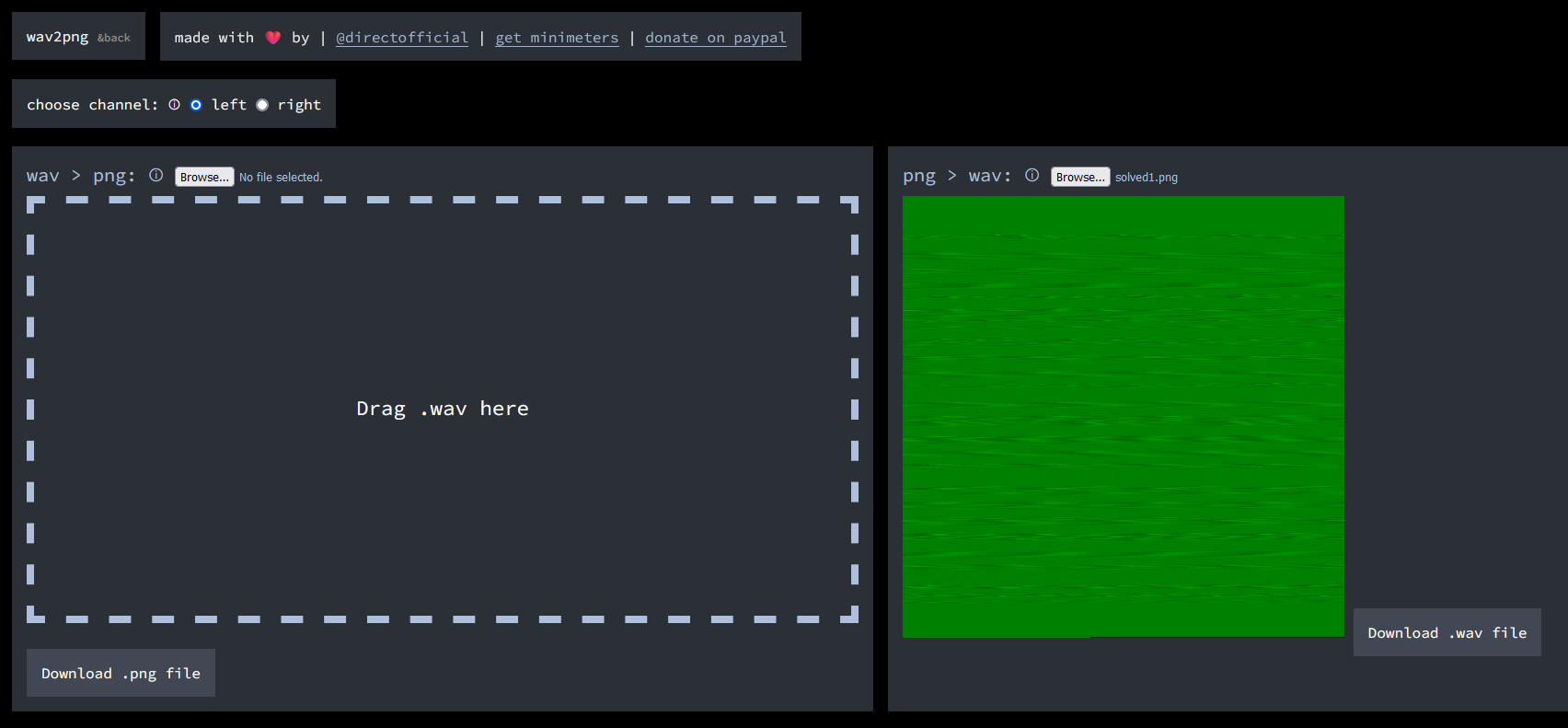
We are given a PNG to investigate. Looking at it, it seems to be a wav audio converted to PNG.
So by using this website, the wav can be extracted and analyzed. Listening to its audio, it seems to be a flag being spoken vocally while having loud background noise covering it. I tried using some online AI background audio cleaner but it still was not clear enough. So I tried changing the bits of the audio via stegsolve to different colors and it seems that full green provides the clearest audio of the flag.
Watch the Waves 2 [Forensics]
Question: Great Scott! There’s something in the water! Scan slowly.
Flag: sdctf{KK6UC_wuz-h3r3}
We are given another PNG to investigate. Similarly, it seems to be a wav audio converted to PNG.
Using the same website, the wav can be extracted and analyzed. The wav audio seems to clearly be a SSTV audio, so by decoding it the flag can be obtained.
1
2
3
4
5
6
└─$ sstv -d audio.wav -o ~/Desktop/result.png
[sstv] Searching for calibration header... Found!
[sstv] Detected SSTV mode Scottie 1
[sstv] Decoding image... [####################################################################################################] 100%
[sstv] Drawing image data...
[sstv] ...Done!
Emojis [Rev]
Question: I have this simple encryption machine that works on emojis! Can you help me find the key?
Hint: the key is the flag
Flag: SDCTF{emojis_look_different_but_theyre_just_like_regular_letters}
We are given a script to reverse engineer. Analyzing the script, it seems that it was encrypting the flag by XORing with a specific string of emojis.
1
2
3
4
5
6
7
8
def main():
print("what do you think the key is?")
encrypted = '🙚🙒🙌🙭😌🙧🙬🙻🙠🙓😣🙯🙖🙺🙠🙖😡🙃🙭🙿🙩🙟😯🙮🙬🙸🙻🙦😨🙩🙽🙉🙻🙑😯🙥🙻🙳🙐🙓😿🙯🙽🙉🙣🙐😡🙹🙖🙤🙪🙞😿🙰🙨🙤🙐🙕😯🙨🙽🙳🙽🙊😷'
key = input()
plaintext = ''.join([chr(ord(c) ^ ord(key[i % len(key)])) for i, c in enumerate(encrypted)])
print("your decrypted text:", plaintext)
main()
So by modifying the script, the XOR key can be obtained.
1
2
3
4
5
6
7
8
9
10
11
def main():
print("what do you think the key is?")
encrypted = '🙚🙒🙌🙭😌🙧🙬🙻🙠🙓😣🙯🙖🙺🙠🙖😡🙃🙭🙿🙩🙟😯🙮🙬🙸🙻🙦😨🙩🙽🙉🙻🙑😯🙥🙻🙳🙐🙓😿🙯🙽🙉🙣🙐😡🙹🙖🙤🙪🙞😿🙰🙨🙤🙐🙕😯🙨🙽🙳🙽🙊😷'
expected_flag = 'SDCTF{'
# XOR the encrypted text with the expected flag format
key = ''.join([chr(ord(encrypted[i]) ^ ord(expected_flag[i % len(expected_flag)])) for i in range(len(expected_flag))])
print("The key is:", key)
main()
1
2
3
PS C:\Users\ooiro> & "C:/Program Files/Python312/python.exe" c:/Users/ooiro/Downloads/emoji.py
what do you think the key is?
The key is: 😉😖😏😹🙊😜
Using the generated XOR key, the flag can be obtained.
1
2
3
4
PS C:\Users\ooiro> & "C:/Program Files/Python312/python.exe" c:/Users/ooiro/Downloads/emoji.py
what do you think the key is?
������������
your decrypted text: SDCTF{emojis_look_different_but_theyre_just_like_regular_letters}