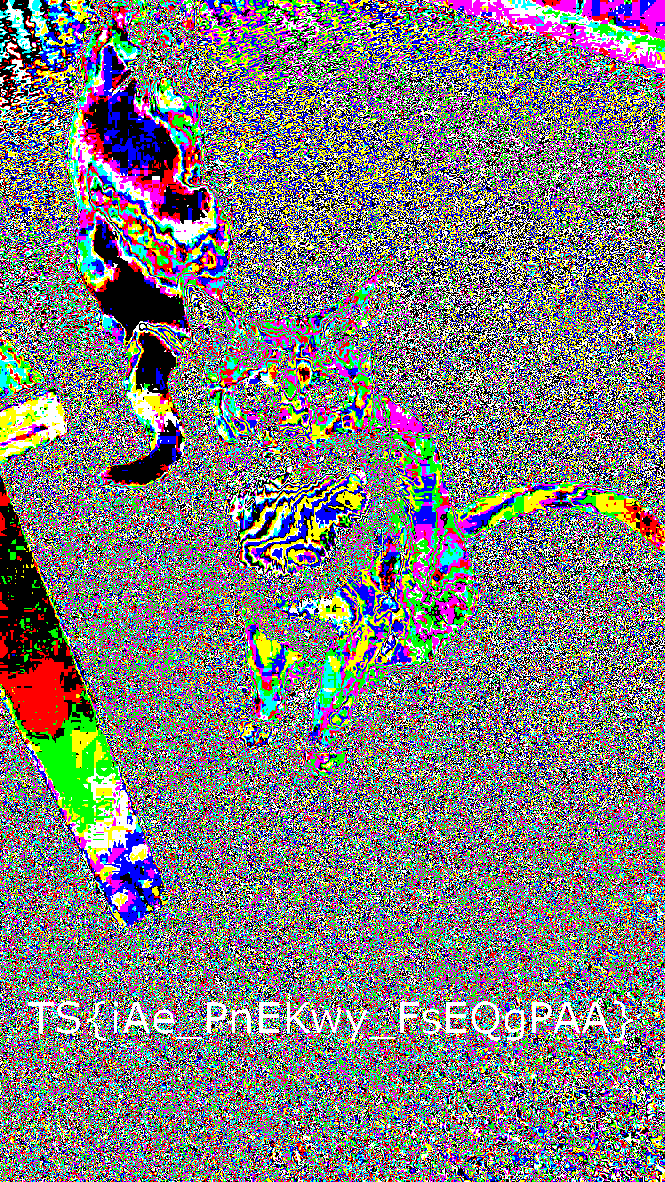RITSEC CTF 2024 - Writeups
This is a writeup for some forensics challenges from RITSEC CTF 2024. I collaborated with my teammate @Blugon to play this CTF together after finishing our internship. Unfortunately, I could not clear the last forensics challenge due to time constraints, but I was still happy that I managed to clear out the rest with ease.
Ransom Note [Forensics]
Question: After the break-in to his lab Anthony found a suspicious new file on his desktop named README.txt. Anthony opened the file and found that it was a ransom demand from whomever stole his invention. Perhaps the contents of the ransom note contain a clue to the attacker’s identity.
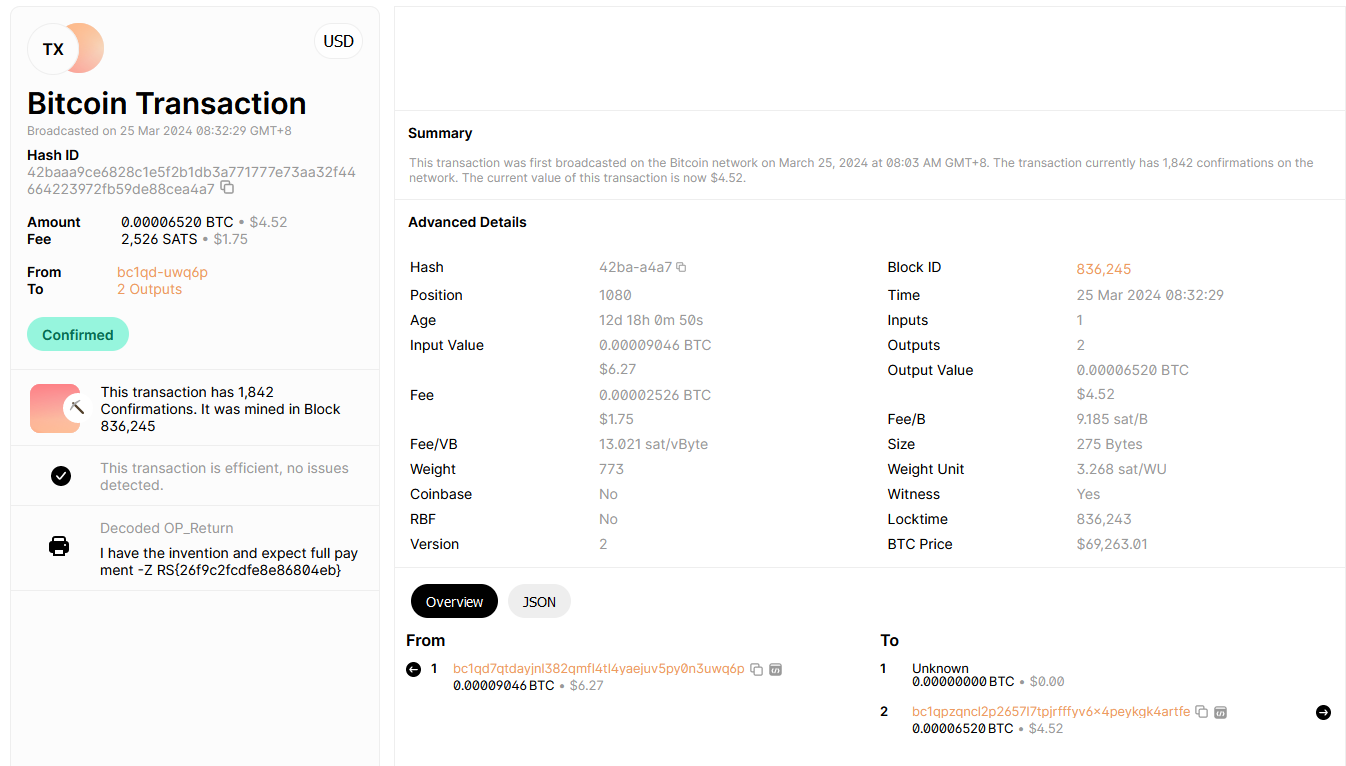
Flag: RS{26f9c2fcdfe8e86804eb}
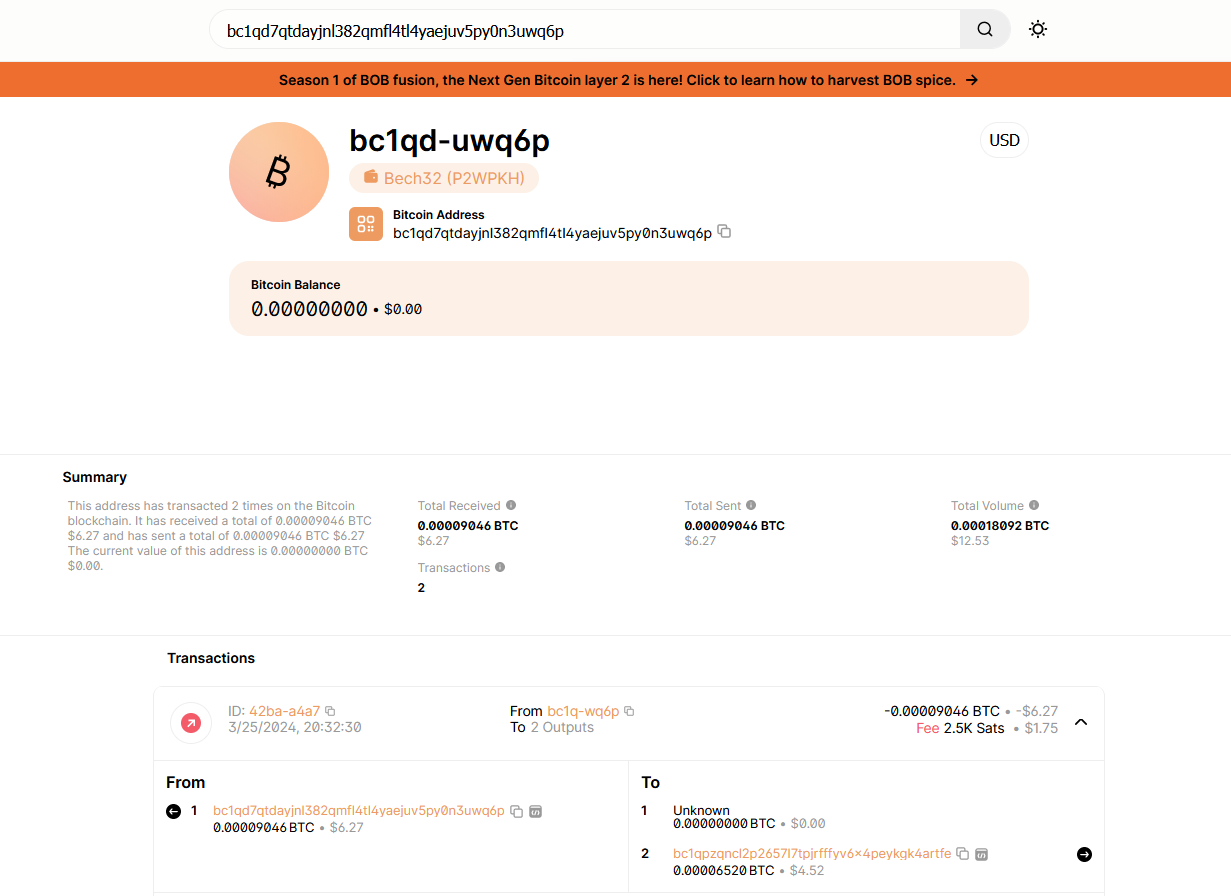
We are given a ransomware note to investigate. Reading it, the victim seems to have fallen for a bitcoin scam, hence I went online to search for the hacker’s bitcoin address to identify his actual account.
1
2
3
4
5
6
7
8
9
10
-----BEGIN BITCOIN SIGNED MESSAGE-----
Your invention has been taken.
If you ever want to see it again send 10 BTC to this address:
bc1qd7qtdayjnl382qmfl4tl4yaejuv5py0n3uwq6p
You have 3 days.
-----BEGIN BITCOIN SIGNATURE-----
H3zAMJyVW2j1+Y7A+w8wflZRUmggR+Sn532ZuAGtGLcxEERvymcPrtnXVkB+0mBqCUAb0AQwyPFJfGxvIeQDPpE=
-----END BITCOIN SIGNATURE-----
Using Blockchain Explorer, the hacker’s bitcoin account can be obtained. Looking at the first transaction, the flag can also be obtained.
Decrypt the Flood [Forensics]
Question: Dive into the digital currents of Decrypt the Flood! Navigate through encrypted waters, uncovering clues hidden within the network flow. Will you decrypt the mystery behind Anthony’s vanished invention, or will it remain lost in the flood?
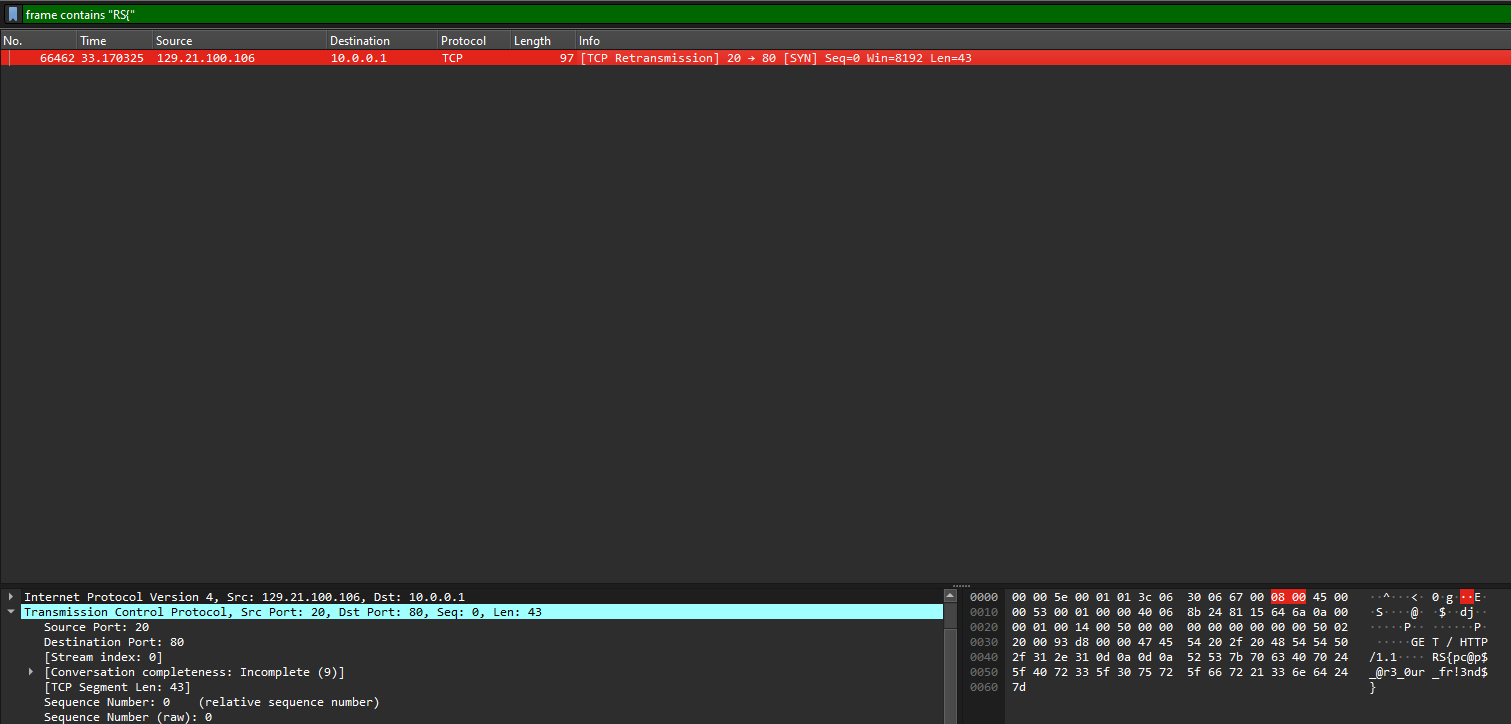
Flag: RS{pc@p$_@r3_0ur_fr!3nd$}
We are given a PCAP to investigate. Several TCP packets can be identified having hidden data in each of them. Filtering the PCAP with the phrase “RS{“, the flag can be obtained.
Curiosity Helped the Cat [Forensics]
Question: In the relentless pursuit to reclaim Anthony’s stolen invention, we’ve meticulously sifted through the digital ether, finding a PNG file adorned with whimsical felines. Suspicions now converge upon Alex, a shadowy figure lurking within the depths of cyberspace, his motives shrouded in secrecy.
Flag: RS{tHe_HaCKer_TeRMiNAL}
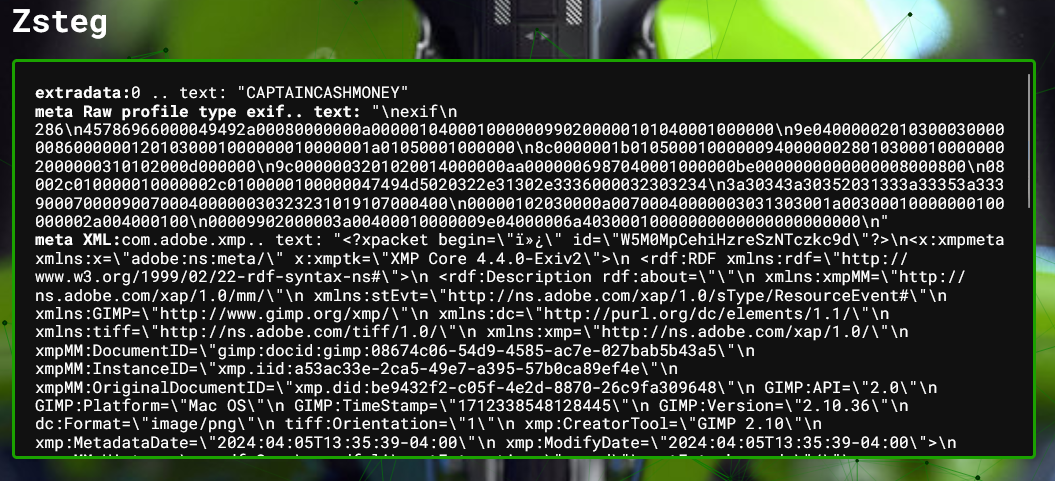
We are given an image to investigate. Looking at the zsteg results, there seems to be a string embedded within the image bits, specifically CAPTAINCASHMONEY.
Unfortunately, this was not the flag, so I assumed this string was a key for decoding purposes later. Doing some research on how I can extract more data, my friend @knight_ gave a nudge on using additional features from zsteg. Checking out the extra features, I stumbled upon this blog that mentions zsteg-mask.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
└─$ zsteg-mask cats.png -d cats_masks
[.] cats_masks/cats.mask_00000001.png .. 318257 bytes
[.] cats_masks/cats.mask_00000011.png .. 606547 bytes
[.] cats_masks/cats.mask_00000111.png .. 836690 bytes
[.] cats_masks/cats.mask_00001111.png .. 1036516 bytes
[.] cats_masks/cats.mask_00000010.png .. 381239 bytes
[.] cats_masks/cats.mask_00000100.png .. 372400 bytes
[.] cats_masks/cats.mask_00001000.png .. 326386 bytes
[.] cats_masks/cats.mask_00010000.png .. 245715 bytes
[.] cats_masks/cats.mask_00100000.png .. 173651 bytes
[.] cats_masks/cats.mask_01000000.png .. 106949 bytes
[.] cats_masks/cats.mask_10000000.png .. 8483 bytes
[.] cats_masks/cats.mask_r00000001.png .. 158301 bytes
[.] cats_masks/cats.mask_r00000011.png .. 291698 bytes
[.] cats_masks/cats.mask_r00000111.png .. 416533 bytes
[.] cats_masks/cats.mask_r00001111.png .. 517876 bytes
[.] cats_masks/cats.mask_r00000010.png .. 156512 bytes
[.] cats_masks/cats.mask_r00000100.png .. 152313 bytes
[.] cats_masks/cats.mask_r00001000.png .. 141895 bytes
[.] cats_masks/cats.mask_r00010000.png .. 117899 bytes
[.] cats_masks/cats.mask_r00100000.png .. 79932 bytes
[.] cats_masks/cats.mask_r01000000.png .. 50386 bytes
[.] cats_masks/cats.mask_r10000000.png .. 9298 bytes
[.] cats_masks/cats.mask_g00000001.png .. 158503 bytes
[.] cats_masks/cats.mask_g00000011.png .. 292378 bytes
[.] cats_masks/cats.mask_g00000111.png .. 416199 bytes
[.] cats_masks/cats.mask_g00001111.png .. 516955 bytes
[.] cats_masks/cats.mask_g00000010.png .. 156314 bytes
[.] cats_masks/cats.mask_g00000100.png .. 151123 bytes
[.] cats_masks/cats.mask_g00001000.png .. 141008 bytes
[.] cats_masks/cats.mask_g00010000.png .. 115847 bytes
[.] cats_masks/cats.mask_g00100000.png .. 80148 bytes
[.] cats_masks/cats.mask_g01000000.png .. 54539 bytes
[.] cats_masks/cats.mask_g10000000.png .. 8969 bytes
[.] cats_masks/cats.mask_b00000001.png .. 153898 bytes
[.] cats_masks/cats.mask_b00000011.png .. 291224 bytes
[.] cats_masks/cats.mask_b00000111.png .. 417350 bytes
[.] cats_masks/cats.mask_b00001111.png .. 518611 bytes
[.] cats_masks/cats.mask_b00000010.png .. 152362 bytes
[.] cats_masks/cats.mask_b00000100.png .. 148125 bytes
[.] cats_masks/cats.mask_b00001000.png .. 138048 bytes
[.] cats_masks/cats.mask_b00010000.png .. 113318 bytes
[.] cats_masks/cats.mask_b00100000.png .. 74690 bytes
[.] cats_masks/cats.mask_b01000000.png .. 40419 bytes
[.] cats_masks/cats.mask_b10000000.png .. 8825 bytes
[.] cats_masks/cats.mask_a00000001.png .. 6273 bytes
[.] cats_masks/cats.mask_a00000011.png .. 7149 bytes
[.] cats_masks/cats.mask_a00000111.png .. 7481 bytes
[.] cats_masks/cats.mask_a00001111.png .. 7483 bytes
[.] cats_masks/cats.mask_a00000010.png .. 6102 bytes
[.] cats_masks/cats.mask_a00000100.png .. 6266 bytes
[.] cats_masks/cats.mask_a00001000.png .. all pixels = #<ZPNG::Color #ffffff>
[.] cats_masks/cats.mask_a00010000.png .. all pixels = #<ZPNG::Color #ffffff>
[.] cats_masks/cats.mask_a00100000.png .. all pixels = #<ZPNG::Color #ffffff>
[.] cats_masks/cats.mask_a01000000.png .. all pixels = #<ZPNG::Color #ffffff>
[.] cats_masks/cats.mask_a10000000.png .. all pixels = #<ZPNG::Color #ffffff>
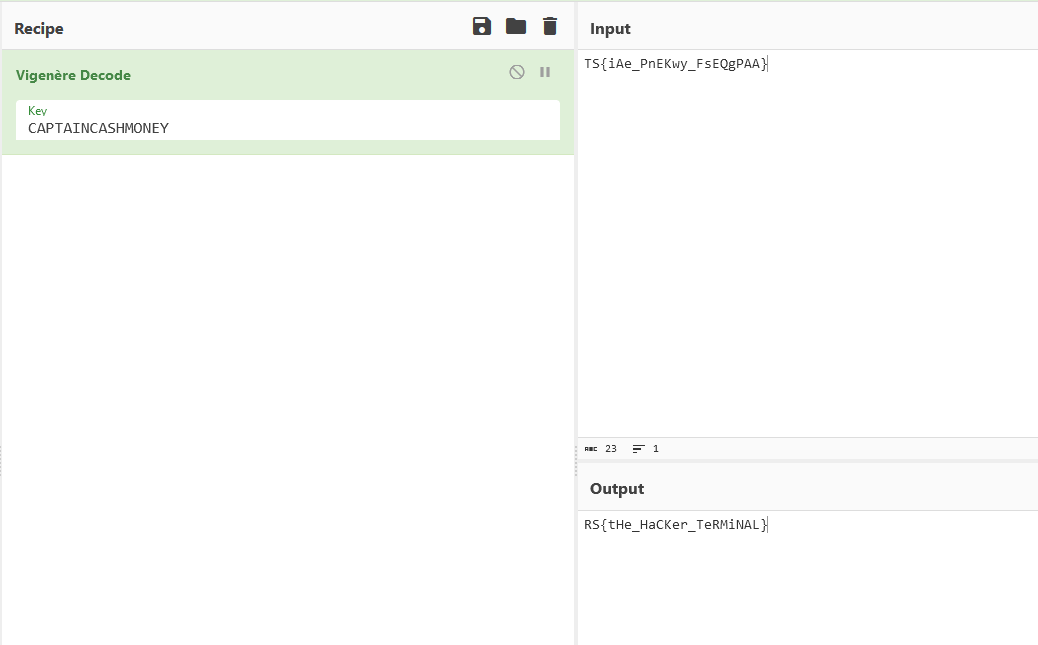
The encoded flag can be obtained as TS{iAe_PnEKwy_FsEQgPAA}. Since we have the encoded flag and a key, I opted for Vignere cipher and it successfully decoded the flag.
Wacky Flags [Forensics]
Question: We were reviewing network traffic around the time that the invention was stolen. We think there’s a thing or two off. Can you help us?
Hint: Before we “reserve” our seats. We need to append a “01” to our tickets.
Hint 2: We have some reservations about Tony’s Contraption but Please don’t share them with anyone. (Author forgot to send this 💀)
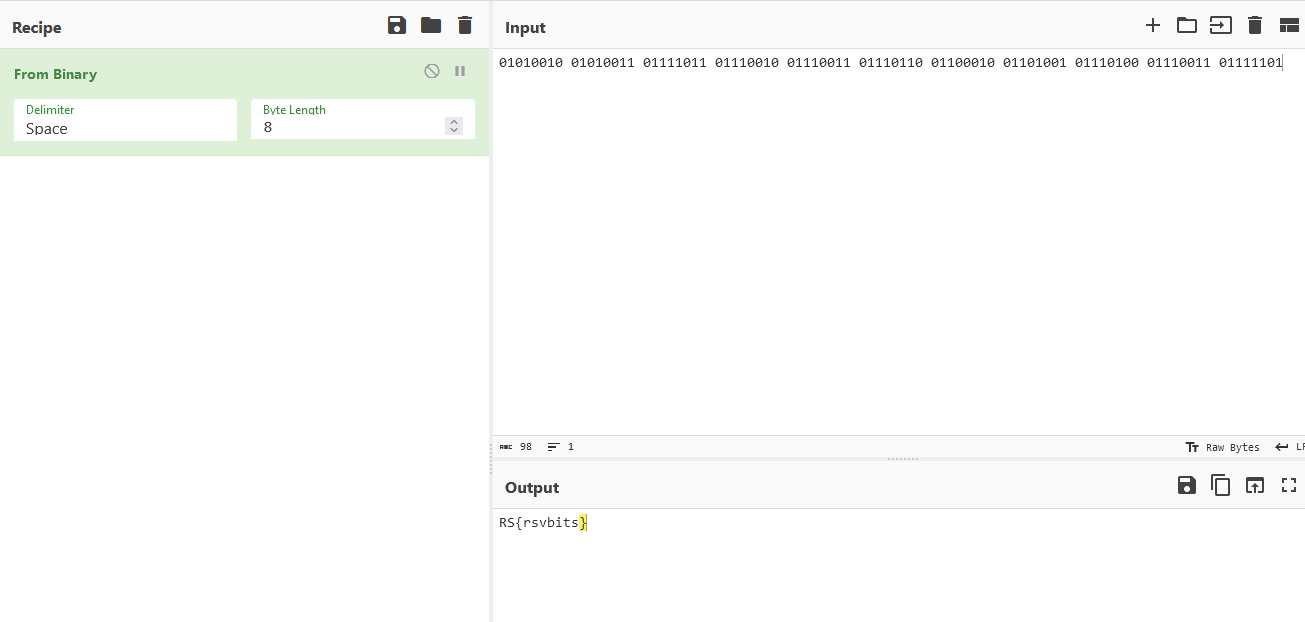
Flag: RS{rsvbits}
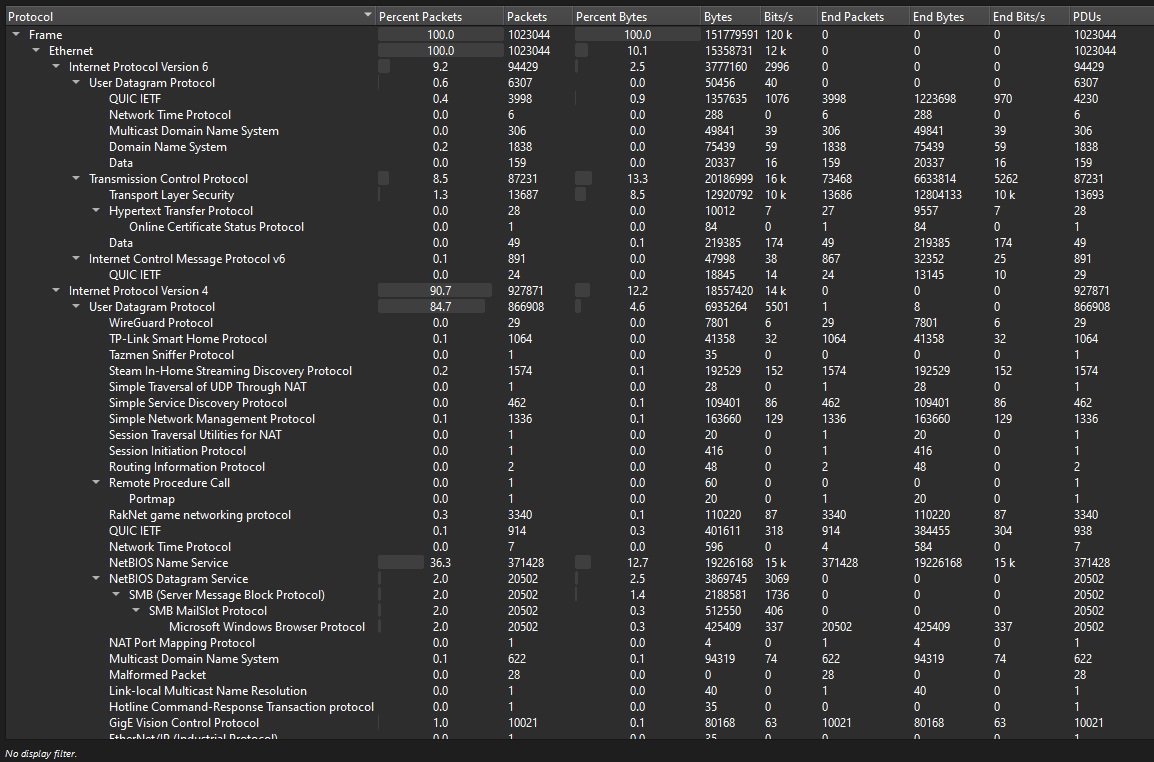
We are given a PCAP to investigate. The PCAP had alot of packets with various protocols, so the search will be super difficult. Unfortunately, I could not solve this before the CTF ended, but I wanted to solve the last challenge so I attempted it again.
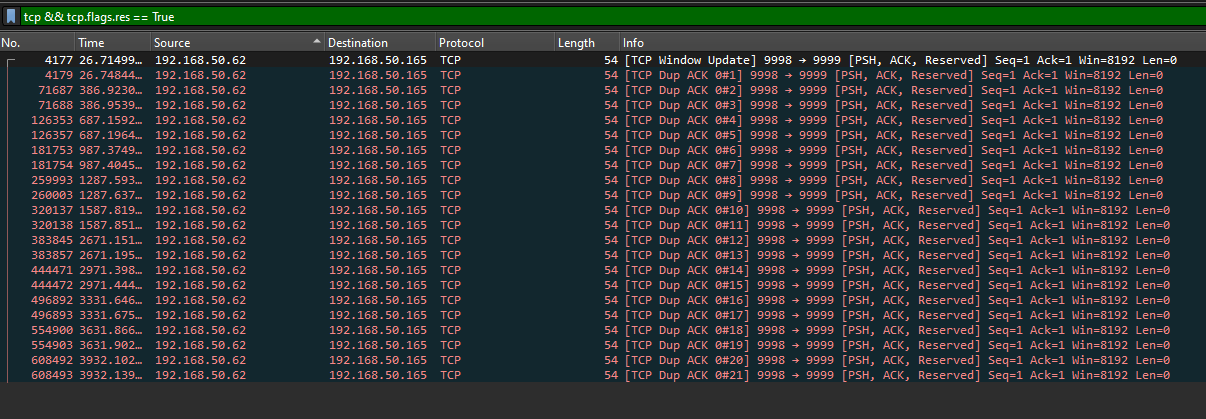
Thankfully, the authors decided to give hints after having 0 solves in the challenge. The hint was something about reserve and 01 bits. The second hint was not given during the CTF but it was hinting that we should be focusing on TCP.
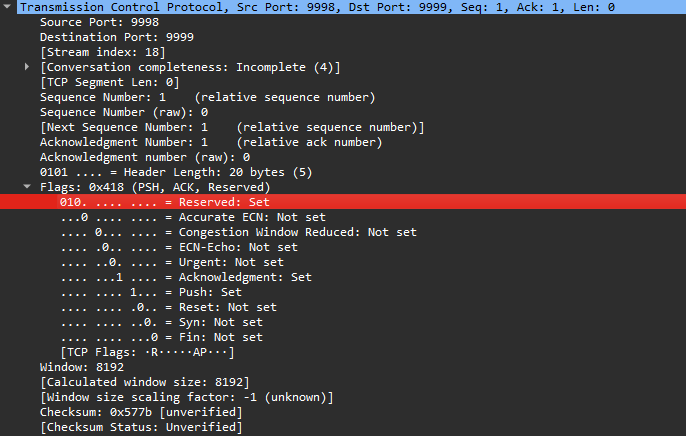
With the hints, the CTF was way easier than I expected it to be. Basically, we know that TCP packets have a Reserved Header on them. So by filtering the pcap with TCP packet’s reserved header set to True, several duplicate ACK packets can be found sent in pairs with a 5-7 minute pause in between them.
Each of the packets had a 3-bit reserved header on them. Remembering about the first hint on prepending 01 bits to the front of the the two paired packets, a binary string can be formed and the flag can be obtained.