picoCTF 2024 - Writeups
This is a writeup for all forensics challenges from picoCTF 2024. Overall, a pretty solid CTF with good forensics challenges where most of them were pretty simple while some required some thinking to solve. The CTF also had a long duration of 7 days so I managed to solve all of the forensics challenges before it ended.
Scan Surprise [Forensics]
Question: I’ve gotten bored of handing out flags as text. Wouldn’t it be cool if they were an image instead? You can download the challenge files here: challenge.zip Additional details will be available after launching your challenge instance.
Flag: picoCTF{p33k_@_b00_a81f0a35}
We are given a QR code to scan. Literally just scan it to obtain the flag.
Verify [Forensics]
Question: People keep trying to trick my players with imitation flags. I want to make sure they get the real thing! I’m going to provide the SHA-256 hash and a decrypt script to help you know that my flags are legitimate. You can download the challenge files here: challenge.zip
Flag: picoCTF{trust_but_verify_00011a60}
We are given a bash script with some data files and a checksum file of 3ad37ed6c5ab81d31e4c94ae611e0adf2e9e3e6bee55804ebc7f386283e366a4. Reading the bash script, it seems that it checks for the valid file according to the checksum given.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
#!/bin/bash
# Check if the user provided a file name as an argument
if [ $# -eq 0 ]; then
echo "Expected usage: decrypt.sh <filename>"
exit 1
fi
# Store the provided filename in a variable
file_name="$1"
# Check if the provided argument is a file and not a folder
if [ ! -f "/home/ctf-player/drop-in/$file_name" ]; then
echo "Error: '$file_name' is not a valid file. Look inside the 'files' folder with 'ls -R'!"
exit 1
fi
# If there's an error reading the file, print an error message
if ! openssl enc -d -aes-256-cbc -pbkdf2 -iter 100000 -salt -in "/home/ctf-player/drop-in/$file_name" -k picoCTF; then
echo "Error: Failed to decrypt '$file_name'. This flag is fake! Keep looking!"
fi
So we just have to find the valid file among the others using the checksum given. Running bash script with the valid file’s name 00011a60, the flag can be obtained.
1
2
└─$ sha256sum * | grep "03b52eabed517324828b9e09cbbf8a7b0911f348f76cf989ba6d51acede6d5d8"
03b52eabed517324828b9e09cbbf8a7b0911f348f76cf989ba6d51acede6d5d8 00011a60
1
2
└─$ ./decrypt.sh 00011a60
picoCTF{trust_but_verify_00011a60}
Mob psycho [Forensics]
Question: Can you handle APKs? Download the android apk here.
Flag: picoCTF{ax8mC0RU6ve_NX85l4ax8mCl_a3eb5ac2}
We are given an APK file to investigate. These APK challenge are always simple, just unzip it and find the flag via strings, grep, find, etc.
1
2
3
4
5
6
7
8
└─$ find . -name 'flag*'
./mobpsycho.apk_FILES/res/color/flag.txt
└─$ cat mobpsycho.apk_FILES/res/color/flag.txt
7069636f4354467b6178386d433052553676655f4e5838356c346178386d436c5f61336562356163327d
└─$ echo 7069636f4354467b6178386d433052553676655f4e5838356c346178386d436c5f61336562356163327d | xxd -r -p
picoCTF{ax8mC0RU6ve_NX85l4ax8mCl_a3eb5ac2}
CanYouSee [Forensics]
Question: How about some hide and seek? Download this file here.
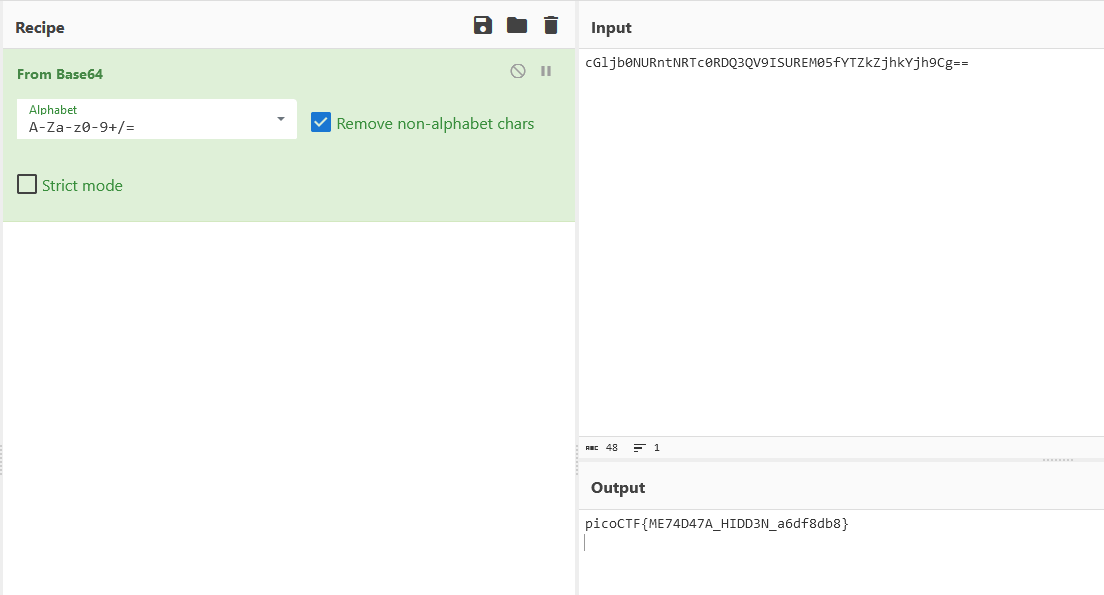
Flag: picoCTF{ME74D47A_HIDD3N_a6df8db8}
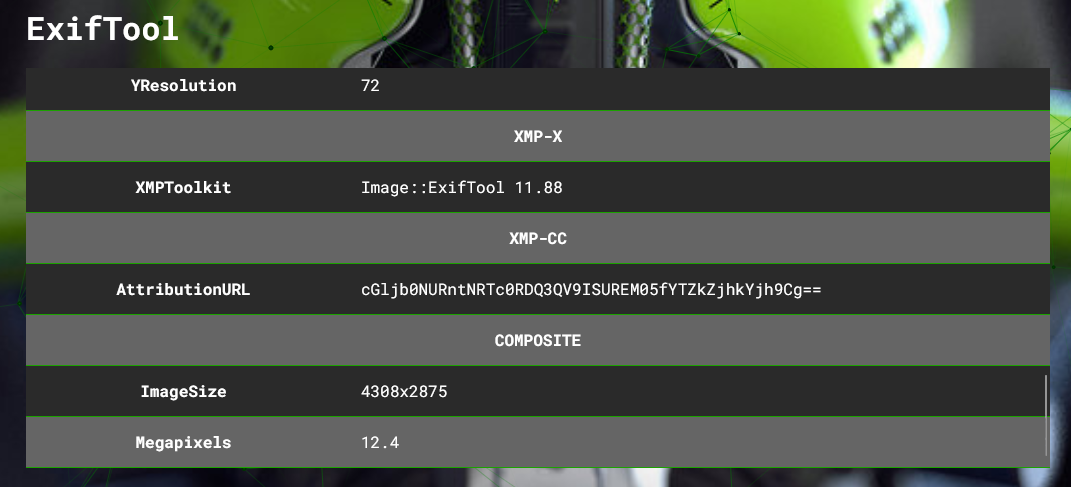
We are given a image to investigate. The encoded flag can be found within its metadata.
Secret of the Polyglot [Forensics]
Question: The Network Operations Center (NOC) of your local institution picked up a suspicious file, they’re getting conflicting information on what type of file it is. They’ve brought you in as an external expert to examine the file. Can you extract all the information from this strange file? Download the suspicious file here.
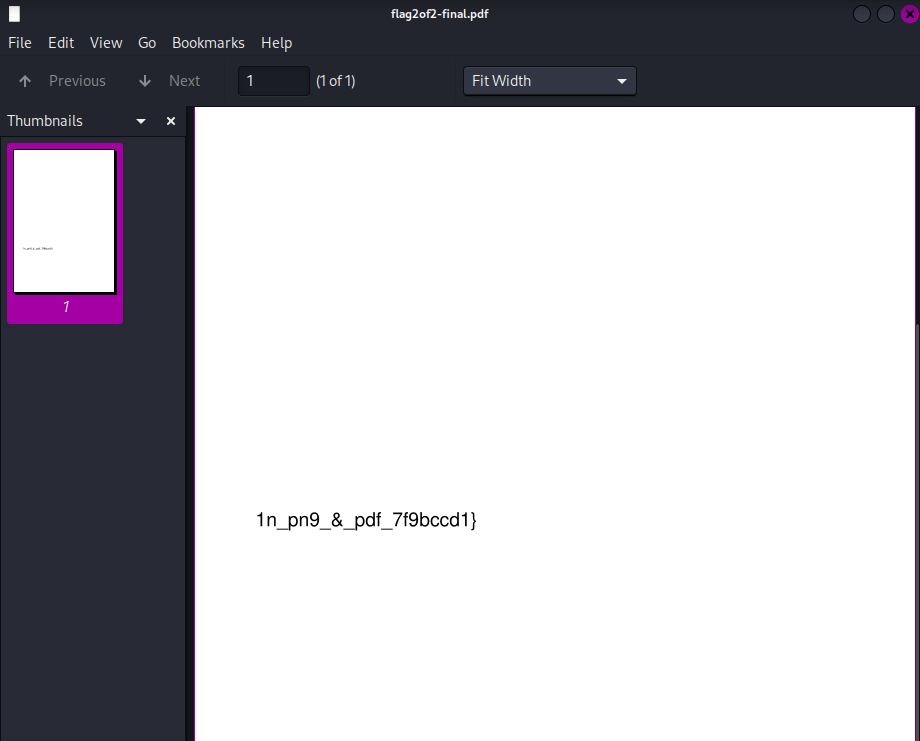
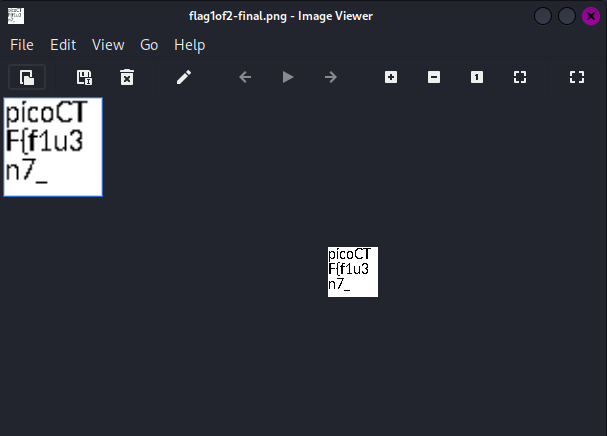
Flag: picoCTF{f1u3n7_1n_pn9_&_pdf_7f9bccd1}
We are given a PDF file to investigate. Inside it, a part of the flag can be obtained.
However, it seems that it was actually a PNG image instead. Changing the file extension, the other part of the flag can be obtained.
1
2
└─$ file flag2of2-final.pdf
flag2of2-final.pdf: PNG image data, 50 x 50, 8-bit/color RGBA, non-interlaced
Blast from the past [Forensics]
Question: The judge for these pictures is a real fan of antiques. Can you age this photo to the specifications? Set the timestamps on this picture to 1970:01:01 00:00:00.001+00:00 with as much precision as possible for each timestamp. In this example, +00:00 is a timezone adjustment. Any timezone is acceptable as long as the time is equivalent. As an example, this timestamp is acceptable as well: 1969:12:31 19:00:00.001-05:00. For timestamps without a timezone adjustment, put them in GMT time (+00:00). The checker program provides the timestamp needed for each. Use this picture. Additional details will be available after launching your challenge instance.
Flag: picoCTF{71m3_7r4v311ng_p1c7ur3_72ecb15c}
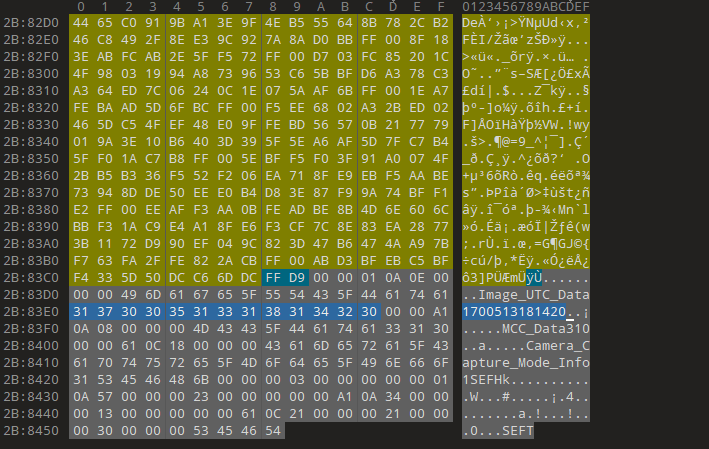
We are given an image to modify. According to the question, we are required to modify every timestamp in the image to 1970:01:01 00:00:00.001+00:00. Using a simple exiftool command, I can modify most of the metadata entries. However, one of the entries still had issues, specifically the Samsung: TimeStamp entry.
1
exiftool "-AllDates=1970:01:01 00:00:00.001" "-SubSecCreateDate=1970:01:01 00:00:00.001" "-SubSecDateTimeOriginal=1970:01:01 00:00:00.001" "-SubSecModifyDate=1970:01:01 00:00:00.001" original.jpg
After some thinking, I tried manually editing the hex value of the image to modify that specific metadata. The timestamp is written in Epoch Time, so I have to modify 1700513181420 to 0000000000001.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
└─$ nc mimas.picoctf.net 62478
MD5 of your picture:
412331ca77b633d2529dc0e0ab5ad6eb test.out
Checking tag 1/7
Looking at IFD0: ModifyDate
Looking for '1970:01:01 00:00:00'
Found: 1970:01:01 00:00:00
Great job, you got that one!
Checking tag 2/7
Looking at ExifIFD: DateTimeOriginal
Looking for '1970:01:01 00:00:00'
Found: 1970:01:01 00:00:00
Great job, you got that one!
Checking tag 3/7
Looking at ExifIFD: CreateDate
Looking for '1970:01:01 00:00:00'
Found: 1970:01:01 00:00:00
Great job, you got that one!
Checking tag 4/7
Looking at Composite: SubSecCreateDate
Looking for '1970:01:01 00:00:00.001'
Found: 1970:01:01 00:00:00.001
Great job, you got that one!
Checking tag 5/7
Looking at Composite: SubSecDateTimeOriginal
Looking for '1970:01:01 00:00:00.001'
Found: 1970:01:01 00:00:00.001
Great job, you got that one!
Checking tag 6/7
Looking at Composite: SubSecModifyDate
Looking for '1970:01:01 00:00:00.001'
Found: 1970:01:01 00:00:00.001
Great job, you got that one!
Checking tag 7/7
Timezones do not have to match, as long as it's the equivalent time.
Looking at Samsung: TimeStamp
Looking for '1970:01:01 00:00:00.001+00:00'
Found: 1970:01:01 00:00:00.001+00:00
Great job, you got that one!
endianness-v2 [Forensics]
Question: Here’s a file that was recovered from a 32-bits system that organized the bytes a weird way. We’re not even sure what type of file it is. Download it here and see what you can get out of it.
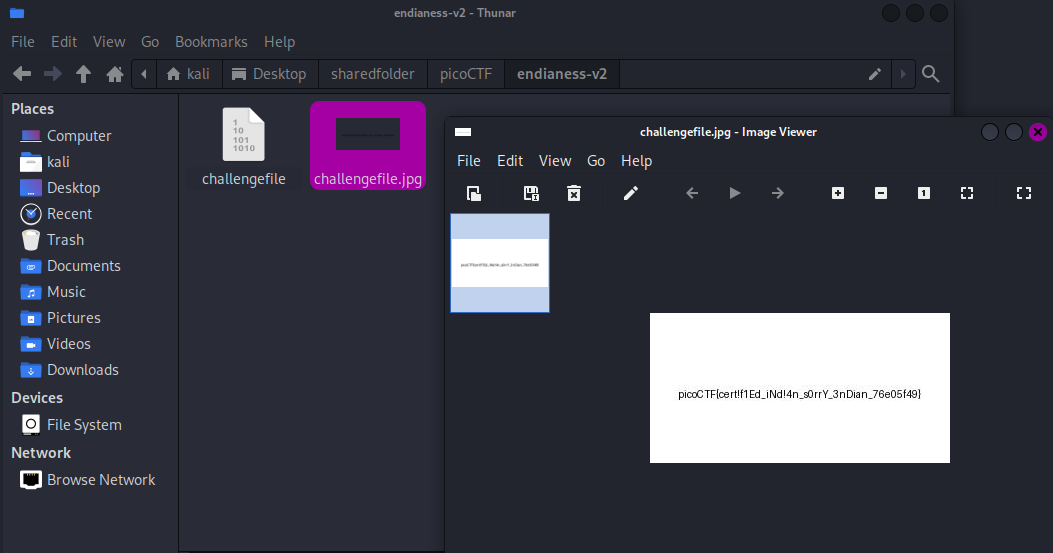
Flag: picoCTF{cert!f1Ed_iNd!4n_s0rrY_3nDian_76e05f49}
We are given a file to investigate. Checking its hex values, it seem that each byte was reversed just like big endian and little endian.
1
2
3
4
5
6
7
8
9
10
11
└─$ xxd challengefile | head
00000000: e0ff d8ff 464a 1000 0100 4649 0100 0001 ....FJ....FI....
00000010: 0000 0100 4300 dbff 0606 0800 0805 0607 ....C...........
00000020: 0907 0707 0c0a 0809 0b0c 0d14 1219 0c0b ................
00000030: 1d14 0f13 1d1e 1f1a 201c 1c1a 2027 2e24 ........ ... '.$
00000040: 1c23 2c22 2937 281c 3431 302c 271f 3434 .#,")7(.410,'.44
00000050: 3238 3d39 3433 2e3c 00db ff32 0909 0143 28=943.<...2...C
00000060: 0c0b 0c09 180d 0d18 211c 2132 3232 3232 ........!.!22222
00000070: 3232 3232 3232 3232 3232 3232 3232 3232 2222222222222222
00000080: 3232 3232 3232 3232 3232 3232 3232 3232 2222222222222222
00000090: 3232 3232 3232 3232 3232 3232 c0ff 3232 222222222222..22
Researching online about converting a file from little endian to big endian, I stumbled upon this forum that has a single command to convert the bytes.
1
hexdump -v -e '1/4 "%08x"' -e '"\n"' challengefile | xxd -r -p > challengefile.jpg
Dear Diary [Forensics]
Question: If you can find the flag on this disk image, we can close the case for good!Download the disk image here.
Flag: picoCTF{1_533_n4m35_80d24b30}
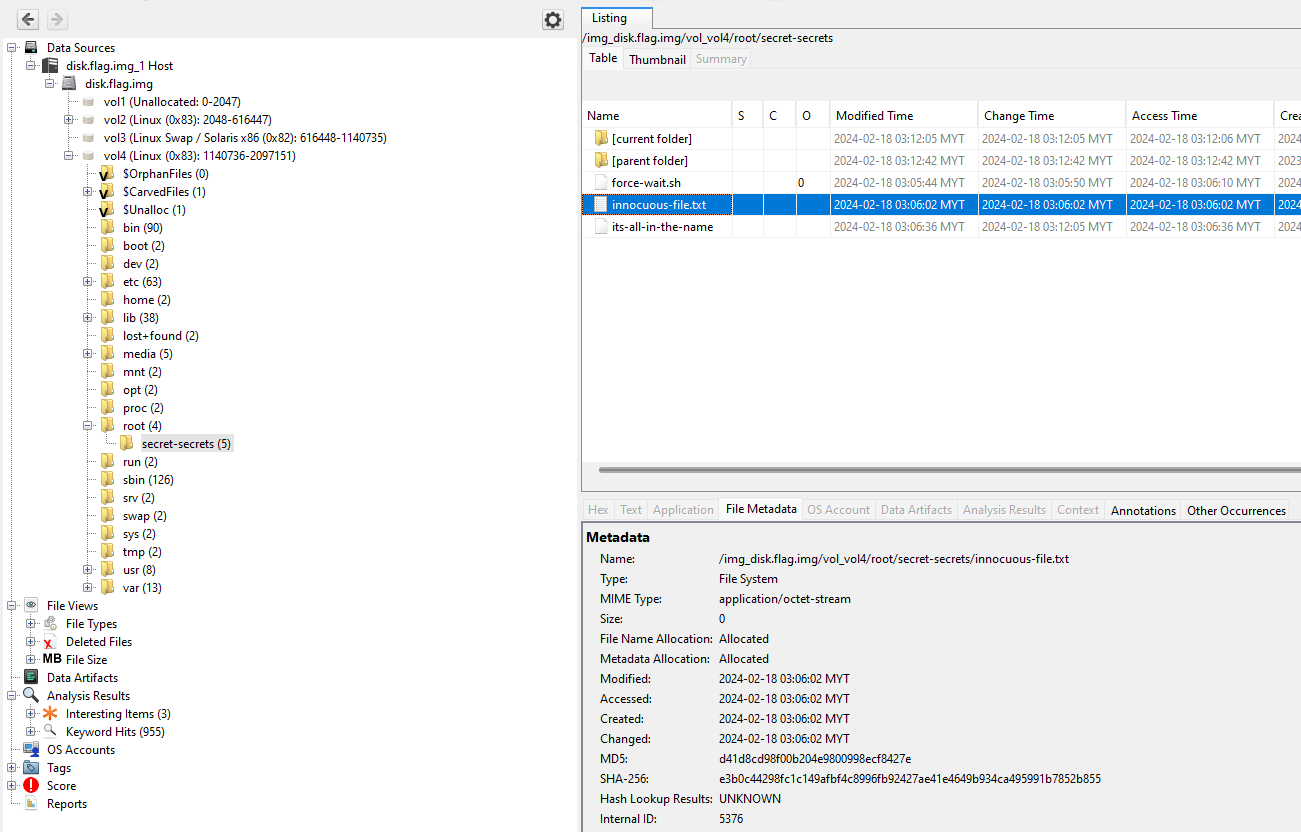
We are given a disk image to investigate. Opening it on Autopsy, a suspicious text file can be found on the root directory. However, it seems that the text file is deleted or shredded so the data can not be retrieved.
Reading online about retrieving deleted and shredded files, I found this writeup that talks about a similar challenge created by picoCTF too. Just follow the steps in the writeup but instead of a single text file, we find out that the text file was broken up into pieces.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ strings -t d disk.flag.img | grep -iE "innocuous-file.txt"
600033336 innocuous-file.txt
728730680 innocuous-file.txt
728743992 innocuous-file.txt
728752184 innocuous-file.txt
728758328 innocuous-file.txt
728767544 innocuous-file.txt
728776760 innocuous-file.txt
728785976 innocuous-file.txt
728792120 innocuous-file.txt
728801336 innocuous-file.txt
728807480 innocuous-file.txt
728816696 innocuous-file.txt
728825912 innocuous-file.txt
728832056 innocuous-file.txt
So I can create a simple Python script to do the offset calculations automatically.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
import subprocess
inno_offsets = [600033336, 728730680, 728743992, 728752184, 728758328, 728767544, 728776760, 728785976, 728792120, 728801336, 728807480, 728816696, 728825912, 728832056]
offsets_minus = [(offset - 584056832) / 1024 for offset in inno_offsets]
results = []
print(offsets_minus)
for offset in offsets_minus:
cmd = f"ifind -f ext4 -o 0001140736 -d {int(offset)} ./disk.flag.img"
result = subprocess.run(cmd, shell=True, capture_output=True, text=True)
results.append(result.stdout)
print(results)
With the offsets, the flag parts can be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
└─$ icat -f ext4 -o 1140736 disk.flag.img 8 | hexdump -C | grep inno -A 5 -B 5
001f87a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
001f8800 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
001f8810 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
001f8820 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
001f8830 34 07 00 00 c4 03 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
001f8840 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
001f8850 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
001f8bf0 00 00 00 00 00 00 00 00 0c 00 00 de ee 60 49 0d |.............`I.|
001f8c00 ff a1 00 00 0c 00 00 00 5d 03 d1 65 70 79 73 65 |........]..epyse|
--
001fbba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
001fbc00 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
001fbc10 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
001fbc20 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
001fbc30 34 07 00 00 1c 00 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
001fbc40 73 2d 66 69 6c 65 2e 74 78 74 00 00 35 07 00 00 |s-file.txt..5...|
001fbc50 a8 03 11 01 6f 72 69 67 69 6e 61 6c 2d 66 69 6c |....original-fil|
001fbc60 65 6e 61 6d 65 00 00 00 00 00 00 00 00 00 00 00 |ename...........|
001fbc70 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
--
001fdba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
001fdc00 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
001fdc10 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
001fdc20 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
001fdc30 34 07 00 00 38 00 12 01 69 6e 6e 6f 63 75 6f 75 |4...8...innocuou|
001fdc40 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
001fdc50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
001fdc60 00 00 00 00 00 00 00 00 35 07 00 00 8c 03 03 01 |........5.......|
001fdc70 70 69 63 00 00 00 00 00 00 00 00 00 00 00 00 00 |pic.............|
001fdc80 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
--
001ff3a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
001ff400 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
001ff410 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
001ff420 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
001ff430 34 07 00 00 1c 00 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
001ff440 73 2d 66 69 6c 65 2e 74 78 74 00 00 35 07 00 00 |s-file.txt..5...|
001ff450 a8 03 03 01 6f 43 54 00 00 00 00 00 00 00 00 00 |....oCT.........|
001ff460 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
001ff7f0 00 00 00 00 00 00 00 00 0c 00 00 de 37 f9 23 19 |............7.#.|
--
002017a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00201800 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
00201810 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
00201820 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
00201830 34 07 00 00 28 00 12 01 69 6e 6e 6f 63 75 6f 75 |4...(...innocuou|
00201840 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
00201850 00 00 00 00 00 00 00 00 35 07 00 00 9c 03 03 01 |........5.......|
00201860 46 7b 31 00 00 00 00 00 00 00 00 00 00 00 00 00 |F{1.............|
00201870 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
--
00203ba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00203c00 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
00203c10 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
00203c20 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
00203c30 34 07 00 00 1c 00 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
00203c40 73 2d 66 69 6c 65 2e 74 78 74 00 00 35 07 00 00 |s-file.txt..5...|
00203c50 a8 03 03 01 5f 35 33 00 00 00 00 00 00 00 00 00 |...._53.........|
00203c60 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00203ff0 00 00 00 00 00 00 00 00 0c 00 00 de de 63 9f 5e |.............c.^|
--
00205fa0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00206000 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
00206010 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
00206020 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
00206030 34 07 00 00 28 00 12 01 69 6e 6e 6f 63 75 6f 75 |4...(...innocuou|
00206040 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
00206050 00 00 00 00 00 00 00 00 35 07 00 00 9c 03 03 01 |........5.......|
00206060 33 5f 6e 00 00 00 00 00 00 00 00 00 00 00 00 00 |3_n.............|
00206070 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
--
002077a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00207800 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
00207810 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
00207820 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
00207830 34 07 00 00 1c 00 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
00207840 73 2d 66 69 6c 65 2e 74 78 74 00 00 35 07 00 00 |s-file.txt..5...|
00207850 a8 03 03 01 34 6d 33 00 00 00 00 00 00 00 00 00 |....4m3.........|
00207860 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00207bf0 00 00 00 00 00 00 00 00 0c 00 00 de ce 7c 1a 9f |.............|..|
--
00209ba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00209c00 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
00209c10 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
00209c20 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
00209c30 34 07 00 00 28 00 12 01 69 6e 6e 6f 63 75 6f 75 |4...(...innocuou|
00209c40 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
00209c50 00 00 00 00 00 00 00 00 35 07 00 00 9c 03 03 01 |........5.......|
00209c60 35 5f 38 00 00 00 00 00 00 00 00 00 00 00 00 00 |5_8.............|
00209c70 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
--
0020b3a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
0020b400 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
0020b410 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
0020b420 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
0020b430 34 07 00 00 1c 00 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
0020b440 73 2d 66 69 6c 65 2e 74 78 74 00 00 35 07 00 00 |s-file.txt..5...|
0020b450 a8 03 03 01 30 64 32 00 00 00 00 00 00 00 00 00 |....0d2.........|
0020b460 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
0020b7f0 00 00 00 00 00 00 00 00 0c 00 00 de 27 f8 3b ac |............'.;.|
--
0020d7a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
0020d800 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
0020d810 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
0020d820 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
0020d830 34 07 00 00 28 00 12 01 69 6e 6e 6f 63 75 6f 75 |4...(...innocuou|
0020d840 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
0020d850 00 00 00 00 00 00 00 00 35 07 00 00 9c 03 03 01 |........5.......|
0020d860 34 62 33 00 00 00 00 00 00 00 00 00 00 00 00 00 |4b3.............|
0020d870 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
--
0020fba0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
0020fc00 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
0020fc10 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
0020fc20 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
0020fc30 34 07 00 00 1c 00 12 01 69 6e 6e 6f 63 75 6f 75 |4.......innocuou|
0020fc40 73 2d 66 69 6c 65 2e 74 78 74 00 00 35 07 00 00 |s-file.txt..5...|
0020fc50 a8 03 02 01 30 7d 00 00 00 00 00 00 00 00 00 00 |....0}..........|
0020fc60 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
0020fff0 00 00 00 00 00 00 00 00 0c 00 00 de 31 a0 13 22 |............1.."|
--
002113a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00211400 32 07 00 00 0c 00 01 02 2e 00 00 00 cc 00 00 00 |2...............|
00211410 0c 00 02 02 2e 2e 00 00 33 07 00 00 18 00 0d 01 |........3.......|
00211420 66 6f 72 63 65 2d 77 61 69 74 2e 73 68 00 00 00 |force-wait.sh...|
00211430 34 07 00 00 28 00 12 01 69 6e 6e 6f 63 75 6f 75 |4...(...innocuou|
00211440 73 2d 66 69 6c 65 2e 74 78 74 00 00 00 00 00 00 |s-file.txt......|
00211450 00 00 00 00 00 00 00 00 35 07 00 00 9c 03 13 01 |........5.......|
00211460 69 74 73 2d 61 6c 6c 2d 69 6e 2d 74 68 65 2d 6e |its-all-in-the-n|
00211470 61 6d 65 00 00 00 00 00 00 00 00 00 00 00 00 00 |ame.............|
00211480 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|