osu!gaming CTF 2024 - Writeups
This is a writeup for some forensics, OSINT and osu! challenges from osu!gaming CTF 2024. Pretty impressive for osu! to create a CTF competition out of nowhere with interesting challenges related to their rhythm game. They even have their own CTF category called osu, adding a fun and distinctive twist to the event.
nathan-on-osu [Forensics]
Question: Here’s an old screenshot of chat logs between sahuang and Nathan on hollow’s Windows machine, but a crucial part of the conversation seems to be cropped out… Can you help to recover the flag from the future?
Flag: osu{cr0pp3d_Future_Candy<3}
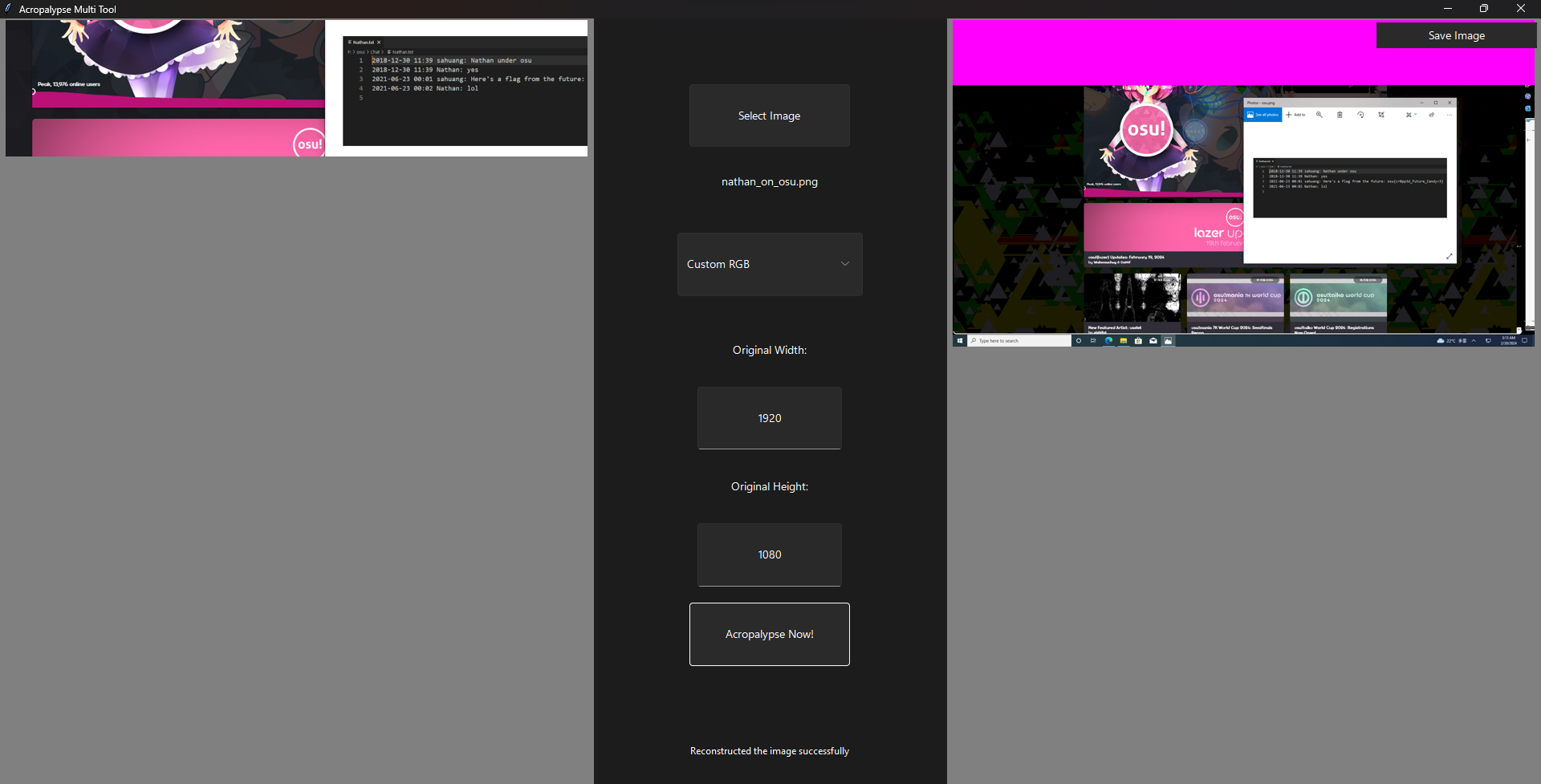
We are given a cropped PNG image to investigate. This seems to be related to the CVE-2023-21036 where cropped images can be easily recovered to view the unaltered version. We can use tools such as Acropalypse to recover the image with the right resolution. However, the web tool did not work for me for some reason. When using the tool and receiving this error, just change the code to from gif_lib import *.
1
2
3
4
PS C:\Users\ooiro\Desktop\Acropalypse-Multi-Tool-1.0.0> python gui.py
Traceback (most recent call last):
File "C:\Users\ooiro\Desktop\Acropalypse-Multi-Tool-1.0.0\gui.py", line 15, in <module>
from gif_lib import acropalypse_gif
So I went ahead and used Acropalypse-Multi-Tool instead. Running the tool with the appropriate width and height, the flag can be obtained.
volatile-map [Forensics]
Question: Hey osu! players, our SOC team was informed that a group of spies from Mai Corp is trying to sabotage our infrastructure via their secret map in osu!. We were able to break into their rendezvous, but they noticed we were stealing their data and they corrupted them in time. Fortunately, we managed to acquire a full memory dump from one of their machines. Can you help us investigate what they were trying to do?
Flag: osu{hide_n_seeeeeeeeeek}
We are given a memory dump to investigate. Analyzing the processes, a suspicious process osu!.exe seem to be running notepad.exe for some reason (kinda sus).
1
2
3
4
5
6
7
8
9
└─$ python3 vol.py -f ~/Desktop/sharedfolder/osu/memory.dmp windows.pstree
Volatility 3 Framework 2.5.2
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
---SNIP---
*** 2272 4556 osu!.exe 0xca8603f1f080 34 - 1 True 2024-03-01 13:41:15.000000 N/A
**** 7928 2272 notepad.exe 0xca8604d4d340 3 - 1 True 2024-03-01 13:42:17.000000 N/A
**** 6188 2272 notepad.exe 0xca8604d77340 3 - 1 True 2024-03-01 13:42:38.000000 N/A
Check for suspicious commands using cmdline, Notepad does indeed have an executed command that seem to have a hex and base64 encoded string.
1
2
3
└─$ python3 vol.py -f ~/Desktop/sharedfolder/osu/memory.dmp windows.cmdline
...
7928 notepad.exe "C:\Windows\System32\notepad.exe" C:\Users\Administrator\AppData\Local\osu!\Songs\beatmap-638448119315467561-ambient-relaxing-music-for-you-15969\osu{ - 686964655f6e (sahuang) [X3NlZWVlZWVlZWVla30=].osu
After decoding them, the flag can be obtained.
1
2
└─$ (echo "686964655f6e" | xxd -r -p) && (echo "X3NlZWVlZWVlZWVla30=" | base64 -d)
hide_n_seeeeeeeeeek}
kfc-with-who? [OSINT]
Question: “KFC with @Who?” Of course you should know this meme as an average osu player - even ppy posted about it last year. Check out where the legendary osu! KFC guy streams, and find the flag there.
Flag: osu{mastery_in_terrible_rage-inducing_chokes}
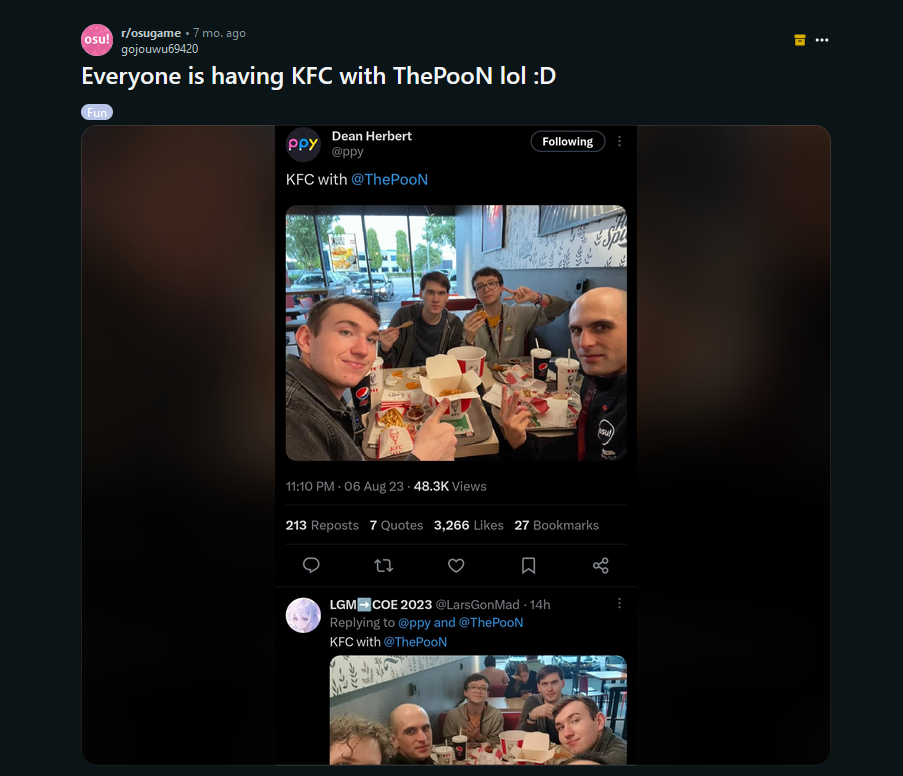
We are tasked to identify a osu! streamer. Googling about osu! and KFC, a Reddit post can be identified that mentioned something about osu! players having KFC with a streamer called ThePooN.
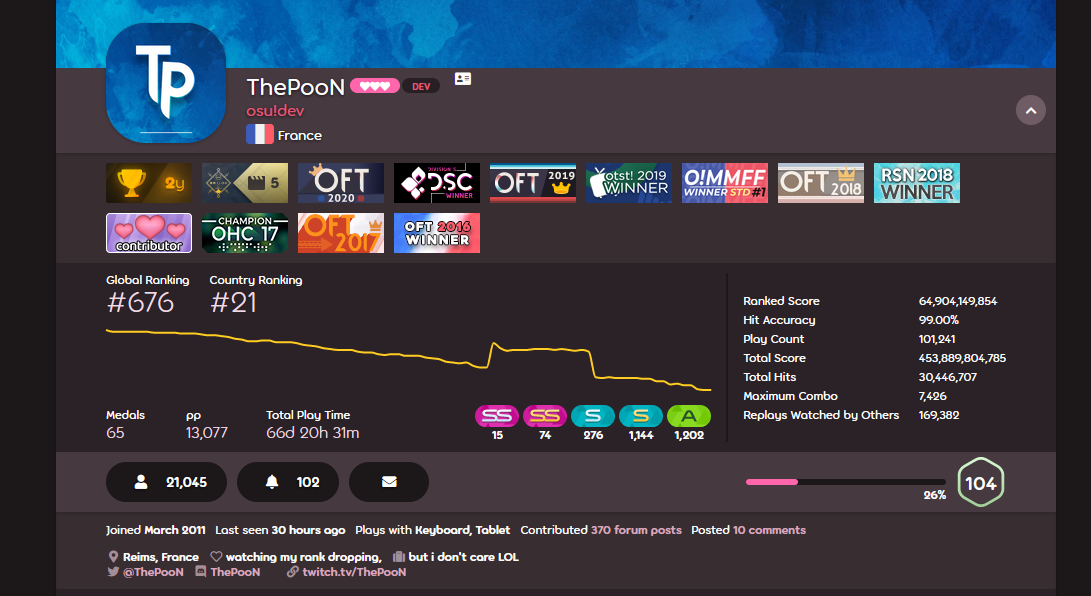
Finding his profile on the osu! website, his Twitch channel was linked on his bio, making the search easier.
On the About page on his Twitch channel, the flag can be found.
when-you-see-it [OSINT]
Question: My friend is so obsessed with osu! that he refused to play any CTF! Today he came to me and sent me this weird GIF, can you understand what he is trying to tell me?
Flag: osu{@nd_wh3n_y0u_fuxx1n_cL1ck3d_nd_c_1T!!!}
We are tasked to identify the person pointing at his monitor given the GIF file. Reverse searching the GIF, we find that the person was known as Aireu.
Using binwalk on the GIF, a hidden ZIP file can be extracted.
1
2
3
4
5
6
7
8
9
└─$ binwalk -e challenge.gif
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 GIF image data, version "89a", 498 x 373
3410748 0x340B3C Zip archive data, at least v1.0 to extract, name: secret/
3410813 0x340B7D Zip archive data, encrypted at least v2.0 to extract, compressed size: 201, uncompressed size: 230, name: secret/confidential
3411107 0x340CA3 Zip archive data, encrypted at least v2.0 to extract, compressed size: 2821, uncompressed size: 317388, name: secret/secret.wav
3414272 0x341900 End of Zip archive, footer length: 22
However, the ZIP file was password-protected. Hence, I randomly tried Aireu as the password and it worked. The zip file contains a WAV audio file and text file which gives the first part of the flag. The text file also had a hint to locate the second part.
1
2
3
4
5
6
7
8
9
10
11
12
13
HIGHLY CONFIDENTIAL
<REDACTED>
I have stored extremely important files here and in another place.
Find it at "osu_game_/[0-9]+/".
As a reward, here is the first part of the flag: `osu{@nd_`
Yours,
Team Osu!Gaming
</REDACTED>
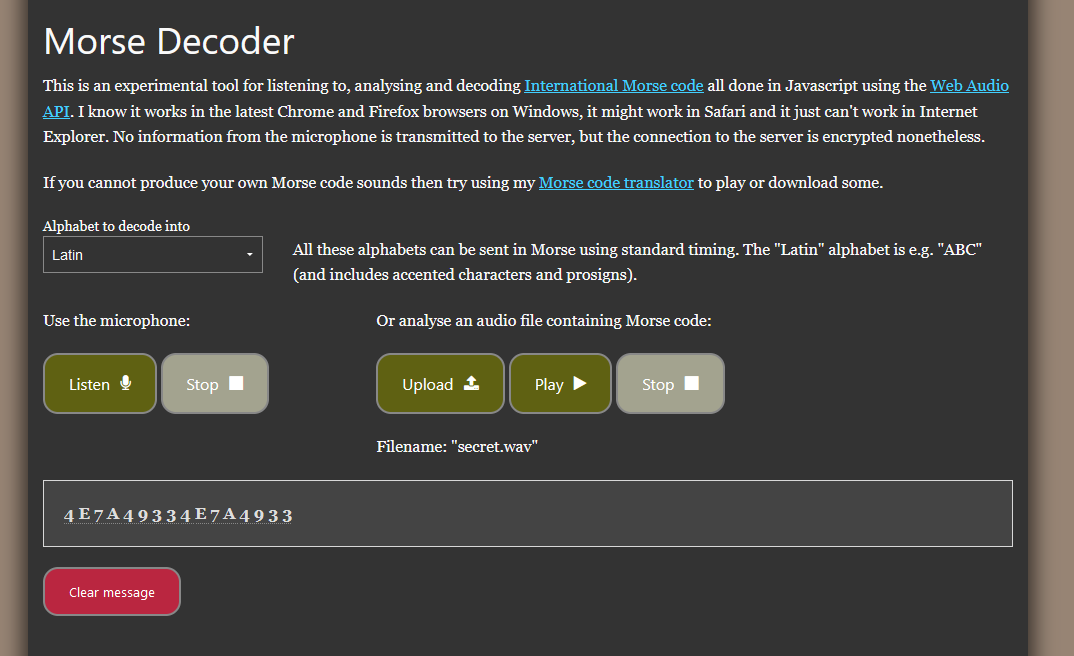
Listening to the WAV audio, it seems to be Morse code with a hidden message.
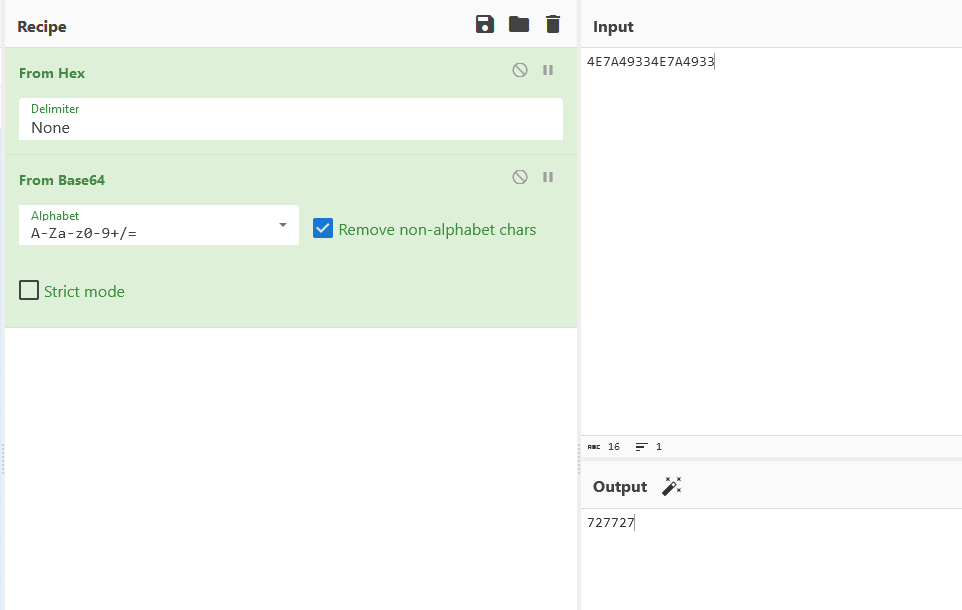
I went ahead and further decoded the hidden message on CyberChef and found this number. Yes I play osu! back in the days and I know of the 727 meme. So I assumed 727727 might be required to find the second part of the flag.
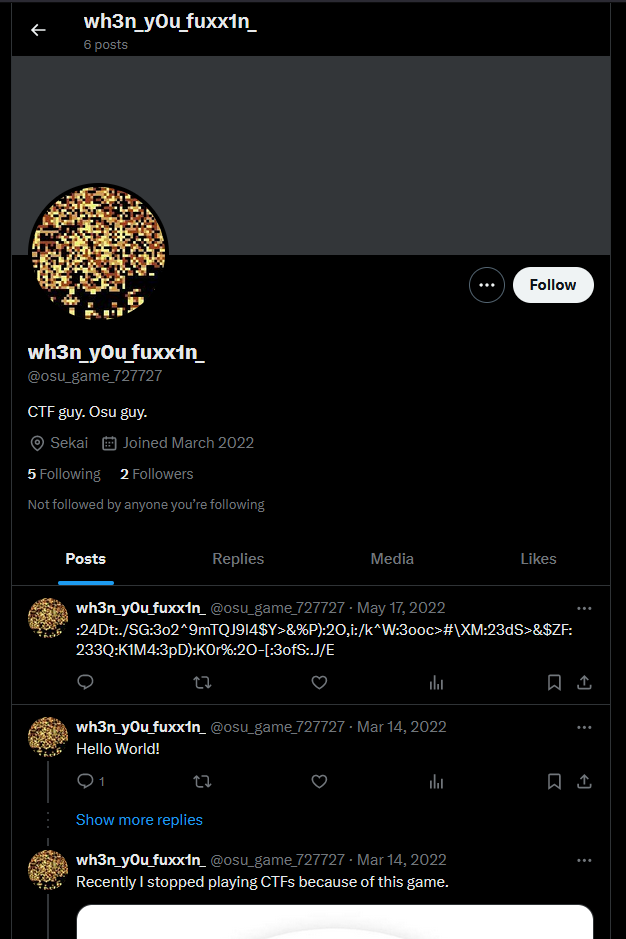
Reading the text file hint again, it mentioned finding the second part of the flag at osu_game_/[0-9]+/. I assume this is a regex where the full string is osu_game_727727. But this was not the flag. At this point I was stuck, but my teammate @Zer01 found out it was a Twitter username all along. The display name of the Twitter account is the second part of the flag.
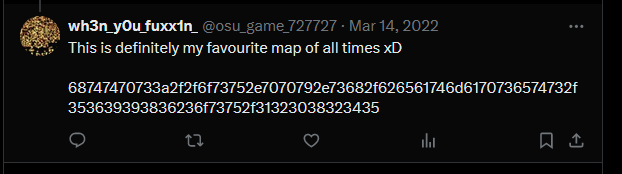
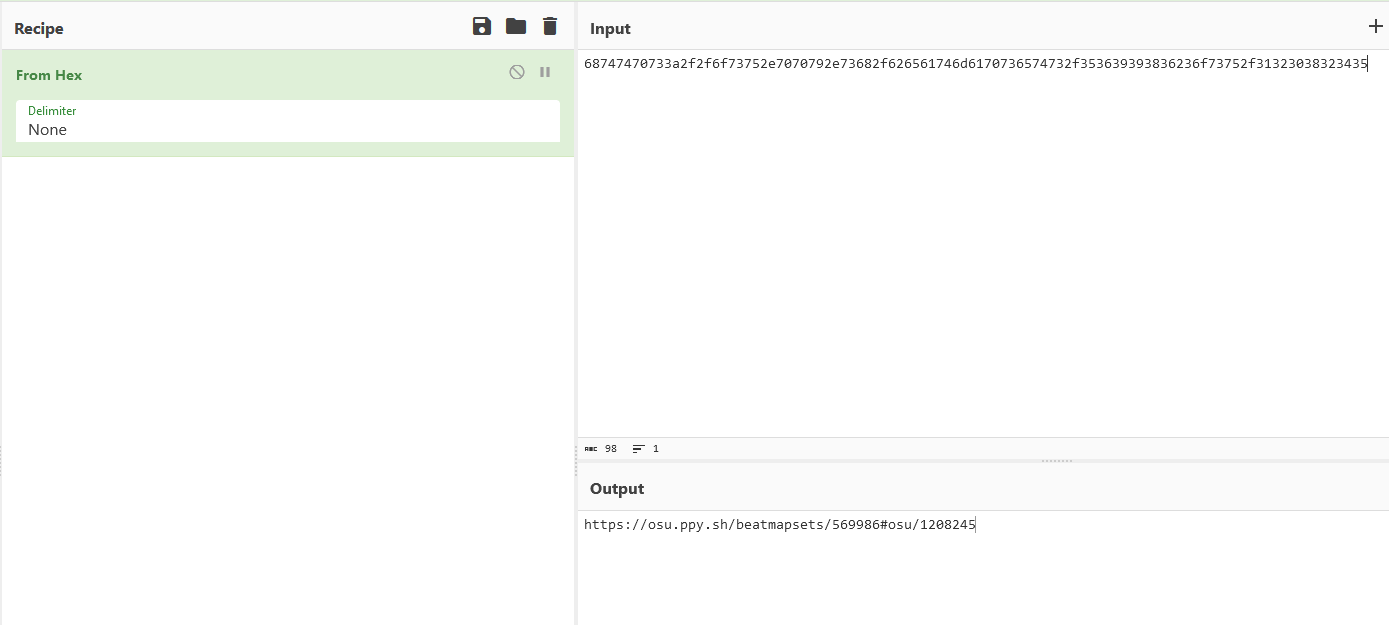
Now to find the third part of the flag, the first link leads us to a Rick Roll video. However, something interesting related to his favourite beatmap can be identified from his other post.
Decoding the hex string will provide a URL to his favourite beatmap (ClariS the goat).
Clicking the dropboxes will provide the third flag part.
sanity-check-1 [osu]
Question: My first map in 2024: Gawr Gura - Kyoufuu All Back Mapped for osu!gaming CTF 2024. Please play/watch the top diff with video on! To osu! players: CTF is a competition where participants attempt to find text strings, called “flags”, which are secretly hidden in purposefully-vulnerable programs or websites. The strings can be in plain text, images, encoded/encrypted, etc. In sanity-check-1, checkout map metadata and submit the flag you found. Remember flag is always in format osu{…} unless otherwise specified.
Flag: osu{welc0me_2_osu!!}
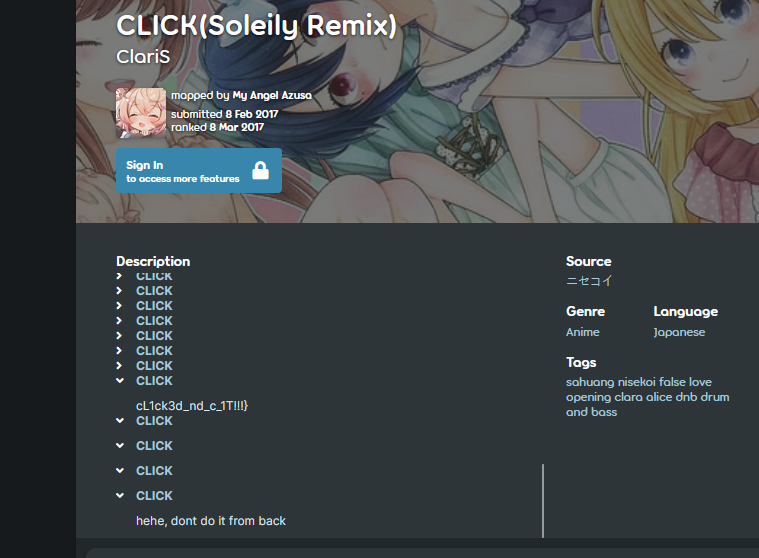
We are given beatmap link to investigate. The flag is in the tags.
smoked [osu]
Question: Imagine getting flag from simply watching a replay…
Flag: osu{smoked_map_fun}
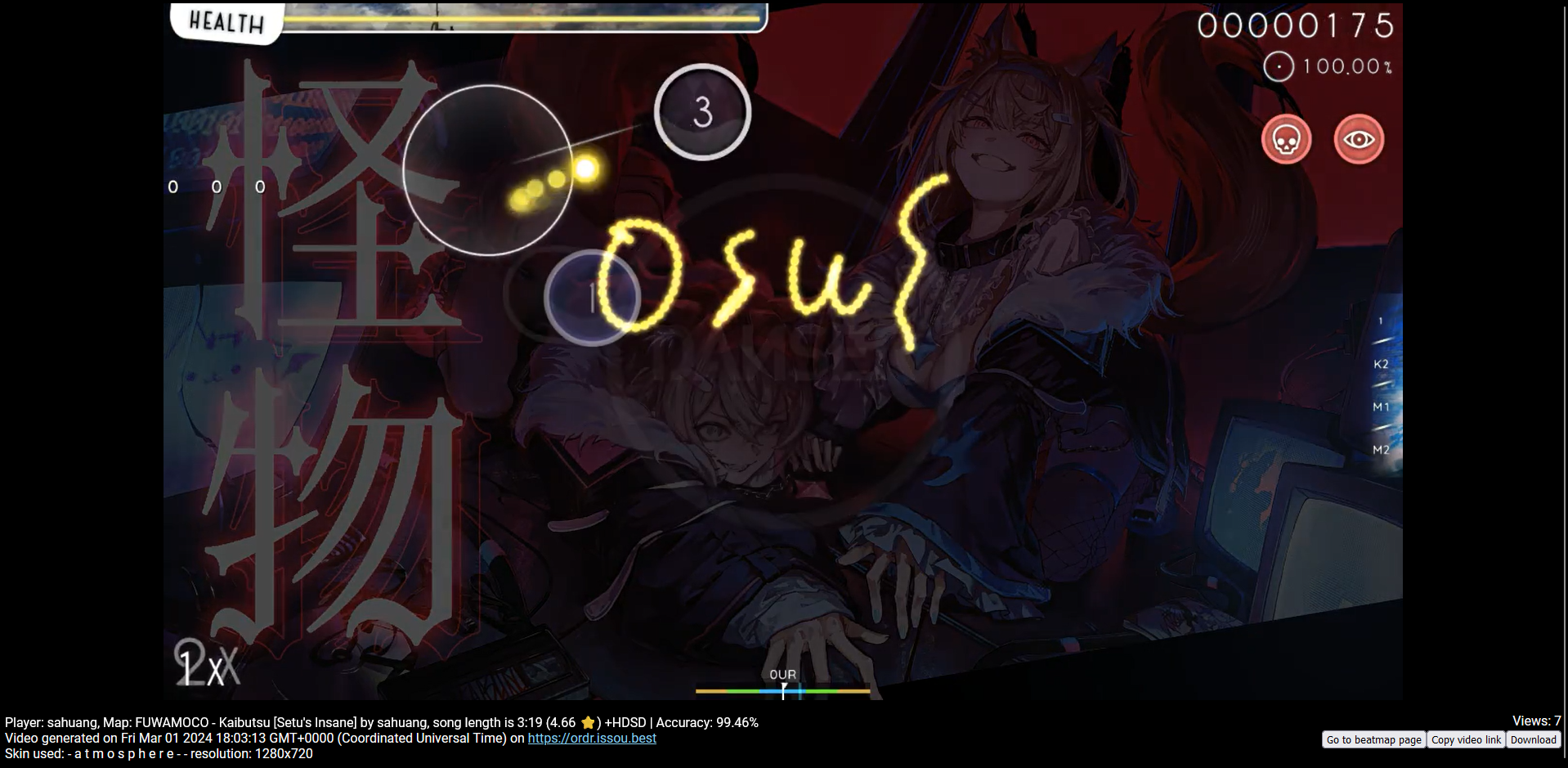
We are given a osu! replay file to investigate. Just enjoy the gameplay and the flag will be drawn in the beatmap.
multi [osu]
Question: Multi is a game mode in osu! for people to play together in a multiplayer lobby. PvP is fun, isn’t it? Join the official CTF lobby osu!gaming CTF 2024 to claim the flag! You are more than welcomed to stay in the lobby for a bit longer and have fun with others. There may or may not be secret prizes for random game winners :D Note: Please behave nicely and follow the rules. Avoid changing lobby name, kicking players, or spamming in chats. Do not spoil the fun for others! Report any misbehaviour to admins.
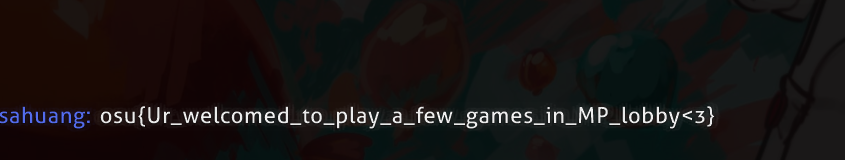
Flag: osu{Ur_welcomed_to_play_a_few_games_in_MP_lobby<3}
I had to reinstall osu! for this lol. Join the Multi lobby and enter !flag to obtain the flag.
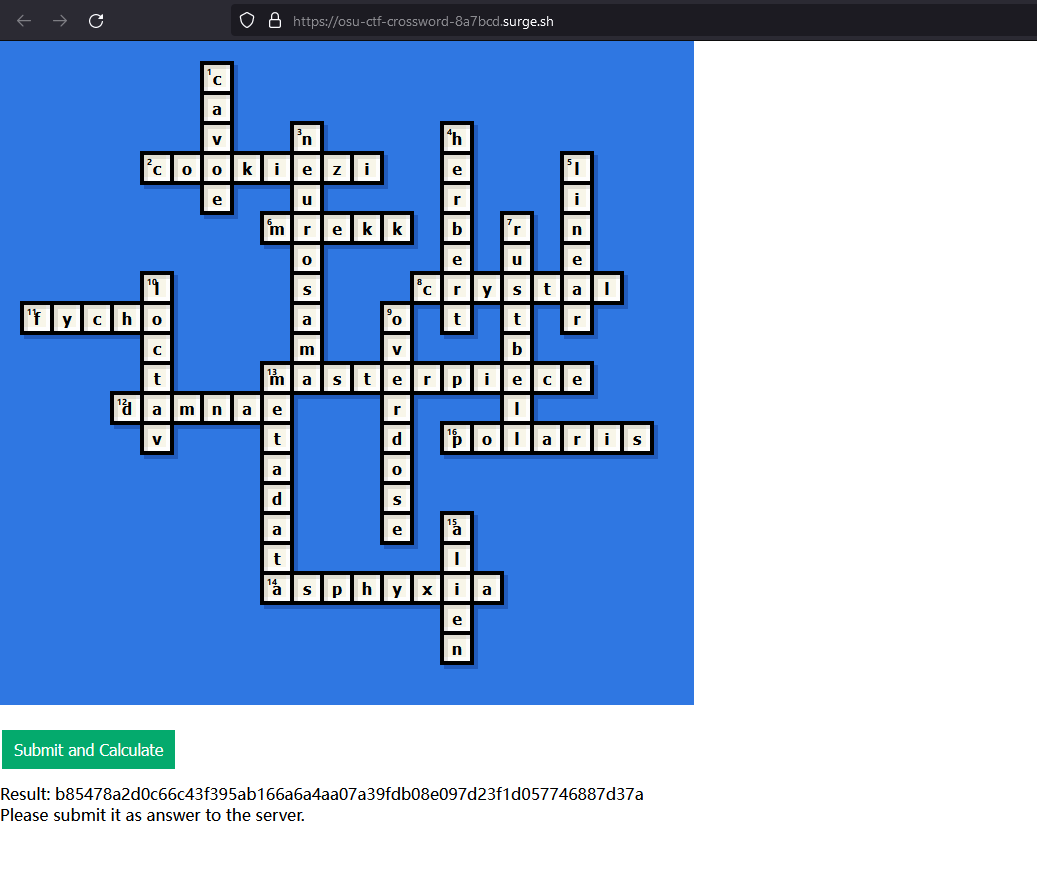
osu!crossword [osu]
Question: Come solve my osu!crossword challenge! Once you completed the puzzle and obtained the hash, submit it to remote server for verification. Note: All characters you enter in crossword should be in lowercase.
Flag: osu{Much_34s13r_Th4n_osu!Trivium_XD}
Just finish the crossword puzzle. PS: ngl the crossword website they made was pretty cool.
1
2
3
└─$ nc chal.osugaming.lol 7270
Submit the hash: b85478a2d0c66c43f395ab166a6a4aa07a39fdb08e097d23f1d057746887d37a
Congrats! Here's your Flag: osu{Much_34s13r_Th4n_osu!Trivium_XD}