Nexus CTF 2024 - Writeups
This is a writeup for all forensics and steganography challenges from Nexus CTF 2024. A pretty interesting and difficult CTF to train my DFIR skills, surprisingly managed to solve all the challenges despite having 4 other CTFs running on the same day.
You Can’t See Me [Steganography]
Question: Wait is John Cena really invisible? Can we actually not see him?? Why does he keep saying that?!
Flag: NexusCTF{H0w_Th3_H3ck_c4n_Ev3ry0ne_SEE_mee!!!}
We are given a JPG image of John Cena to investigate. Analyzing the image metadata, a secret key can be obtained for steghide to obtain the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
└─$ exiftool chall.jpg
ExifTool Version Number : 12.76
File Name : chall.jpg
Directory : .
File Size : 31 kB
File Modification Date/Time : 2024:04:20 23:56:26-04:00
File Access Date/Time : 2024:04:20 23:57:00-04:00
File Inode Change Date/Time : 2024:04:20 23:56:26-04:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
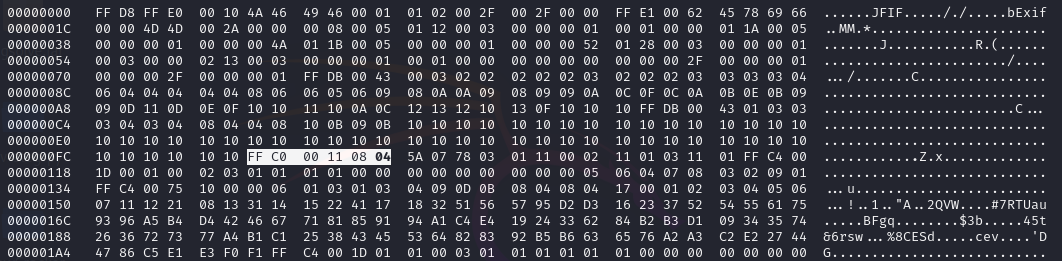
Comment : ohmygodyoucanactuallyseeme
Image Width : 777
Image Height : 437
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 777x437
Megapixels : 0.340
1
2
3
4
5
└─$ steghide extract -sf chall.jpg -p ohmygodyoucanactuallyseeme
wrote extracted data to "flag.txt".
└─$ cat flag.txt
NexusCTF{H0w_Th3_H3ck_c4n_Ev3ry0ne_SEE_mee!!!}
Zero Hidden Knight in Space [Steganography]
Question: My girlfriend cheated on me. And My Friend send me “The seamless flow of words hinted at their close connection, like hidden bonds between the letters.” And After the first one my Friend Wants more complex That is the reason he hide another thing so I want to solve that steg. Please help me.
Flag: NexusCTF{L3gends_Are_m4de_f0r_Br3aking_The_Syst3m}
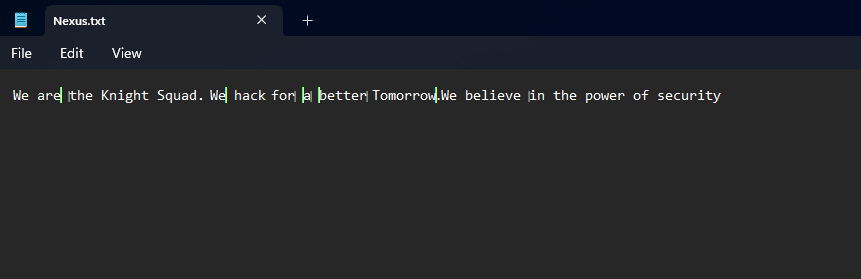
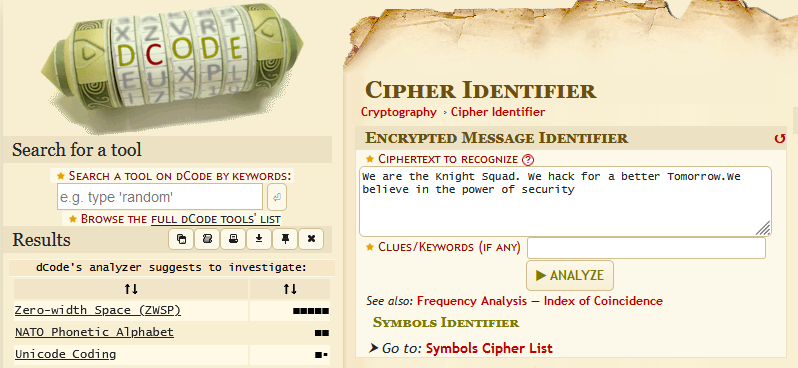
We are given a suspiciously formatted ciphertext to investigate. Analyzing the ciphertext on dcode, it seems that the encoding method was called Zero-width Space (ZWSP).
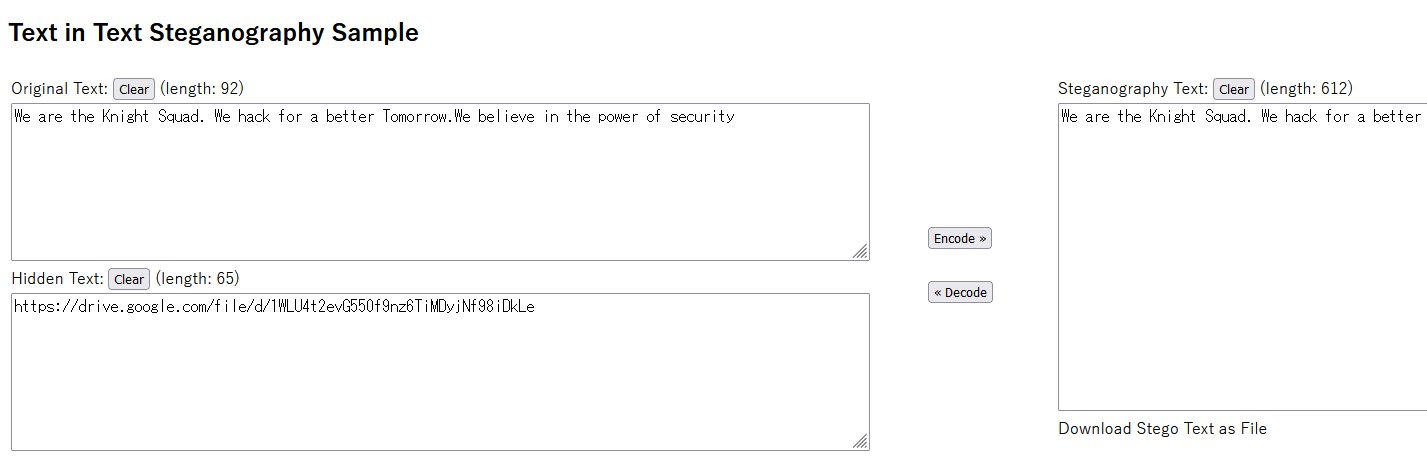
Researching online for decoding tools, I found a website that can decode zero-width characters. The decoded message can be obtained which was a Google Drive link.
Accessing the link was a bmp image where the flag can be obtained.
Blind [Steganography]
Question: i am in front of your nose XD
Flag: NexusCTF{1m463_r351z1n6_15_r34lly_4m4z1n6_5634985bd80}
We are given a Desktop screenshot to investigate. Looking at the bottom right of screenshot, the flag was cut-off due to the height.
So the height has to be adjusted using its hex values. A good reference to learn about jpg/jpeg hex values.
Editing FF C0 00 11 08 03 5A 07 78 to FF C0 00 11 08 04 5A 07 78, the flag can be obtained.
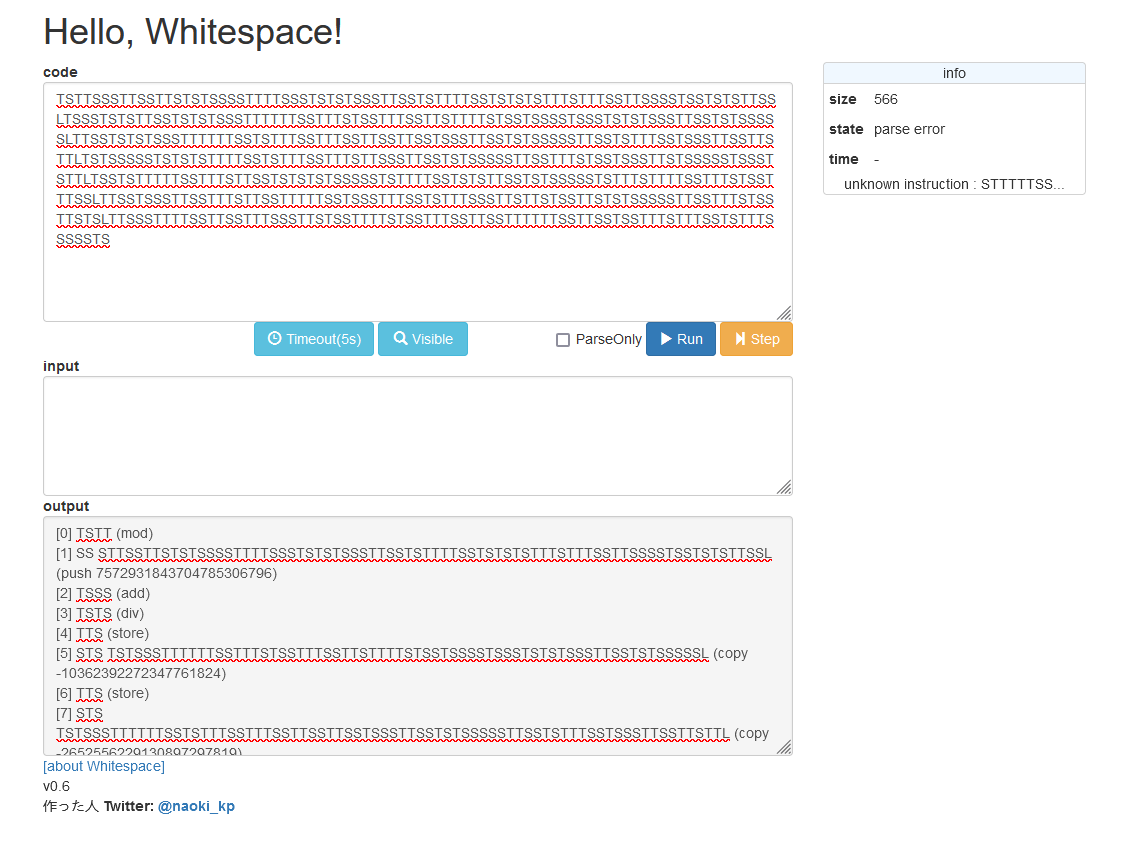
The C.S Dictionary [Steganography]
Question: Are you aware of these terms related to the vast field of Computer Science Engineering??
Flag: NexusCTF{L3gends_Are_m4de_f0r_Br3aking_The_Syst3m}
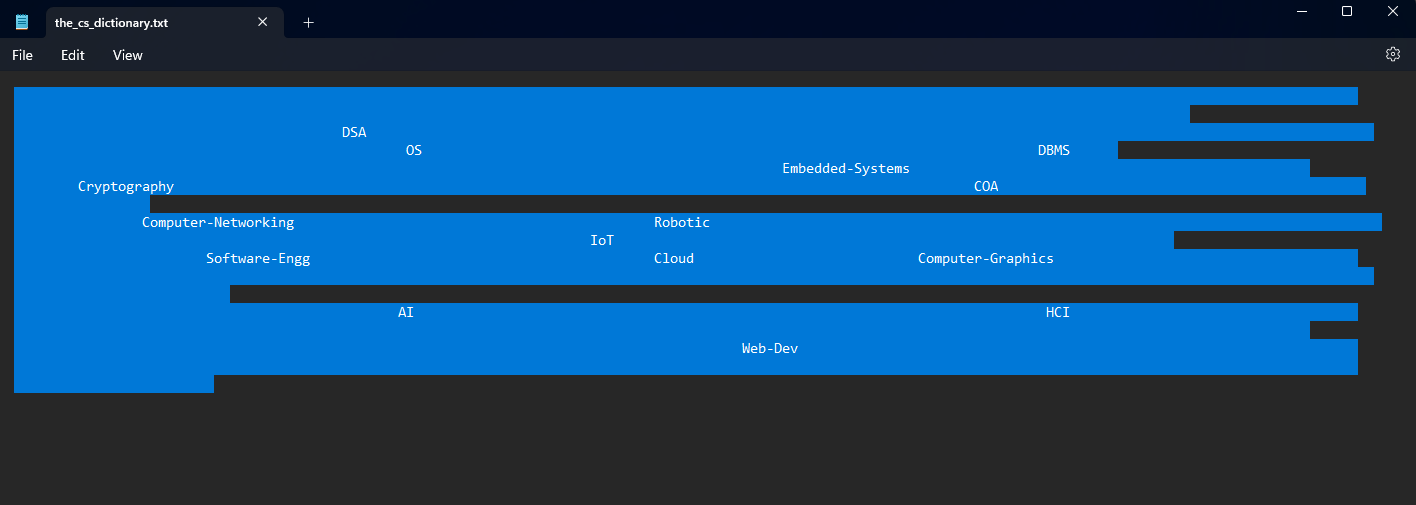
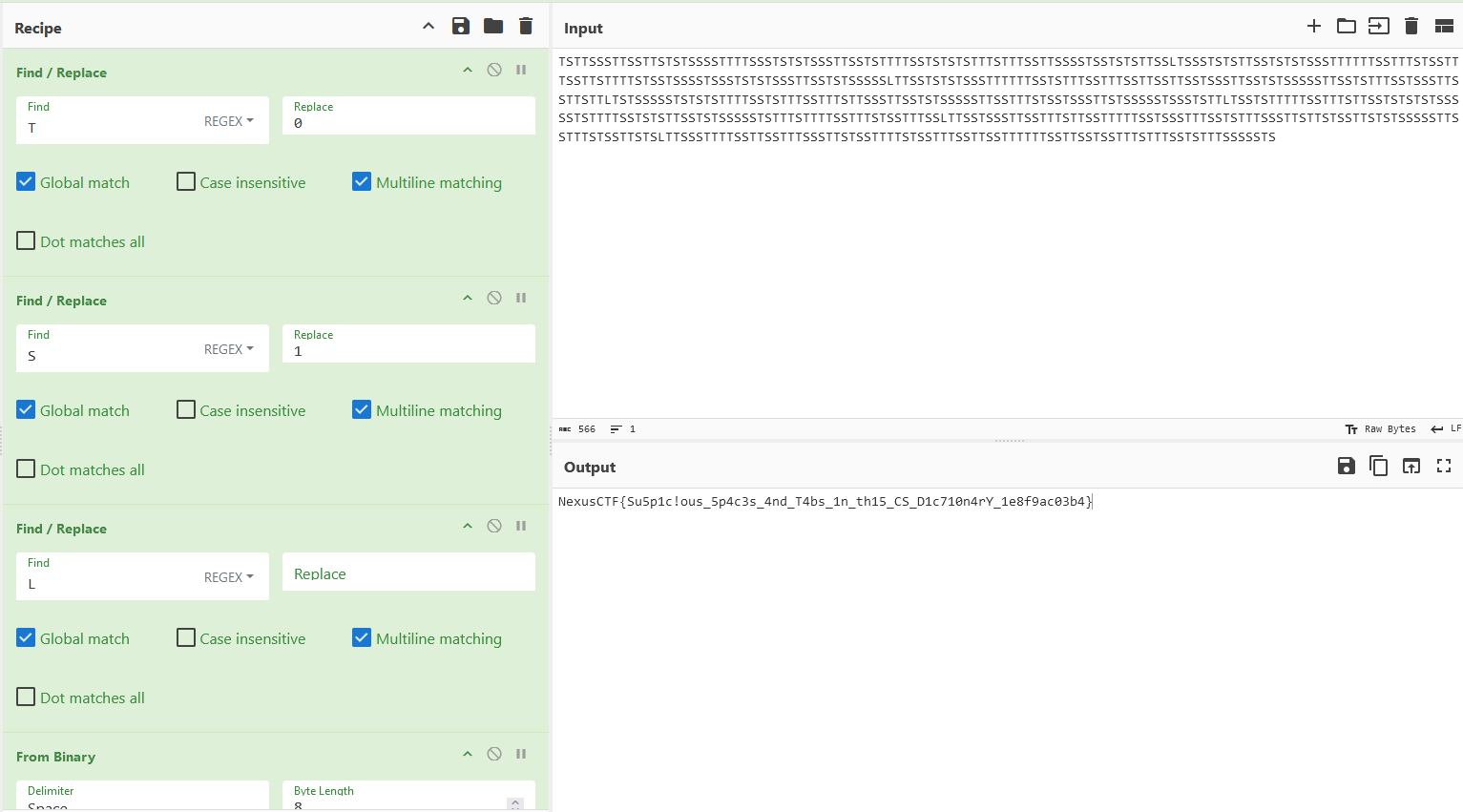
We are given a suspiciously spaced ciphertext to investigate. This time it was obvious that the encoding method used here was Whitespace programming/SNOW.
However, it seems the hidden data was not in the whitespaces after all.
After some research, I used this website to find the tabs and spaces.
Looking at the tabs and spaces, it seems to form a binary string. Replacing tabs = 0 and spaces = 1, the flag can be obtained.
Insignificant? [Steganography]
Question: Can you tell me how significant this bit of music really is??
Flag: NexusCTF{Th3_Le4st_S1Gn1f!c4n7_B1t55_1n_A_W4v_f1L3_6fe20da1bc9}
We are given a wav audio file (without any file extension) to investigate. Analyzing it on Audacity the audio waveform and spectrogram seem to be normal.
Reading the challenge name and description, it seems to be mentioning about something related to LSB. Researching online about audio LSB, I stumbled upon this website that we can extract LSB bits from audio with stegolsb.
1
2
3
4
└─$ stegolsb wavsteg -r -i challenge.wav -o output.txt -n 2 -b 10000
Files read in 0.05s
Recovered 10000 bytes in 0.00s
Written output file in 0.01s
1
2
3
4
5
6
7
8
└─$ cat output.txt
NexusCTF{Th3_Le4st_S1Gn1f!c4n7_B1t55_1n_A_W4v_f1L3_6fe20da1bc9}
�3�����������0���
�03�0�3��?��������������������
��?����<����?������
��3
�30�30
���<�
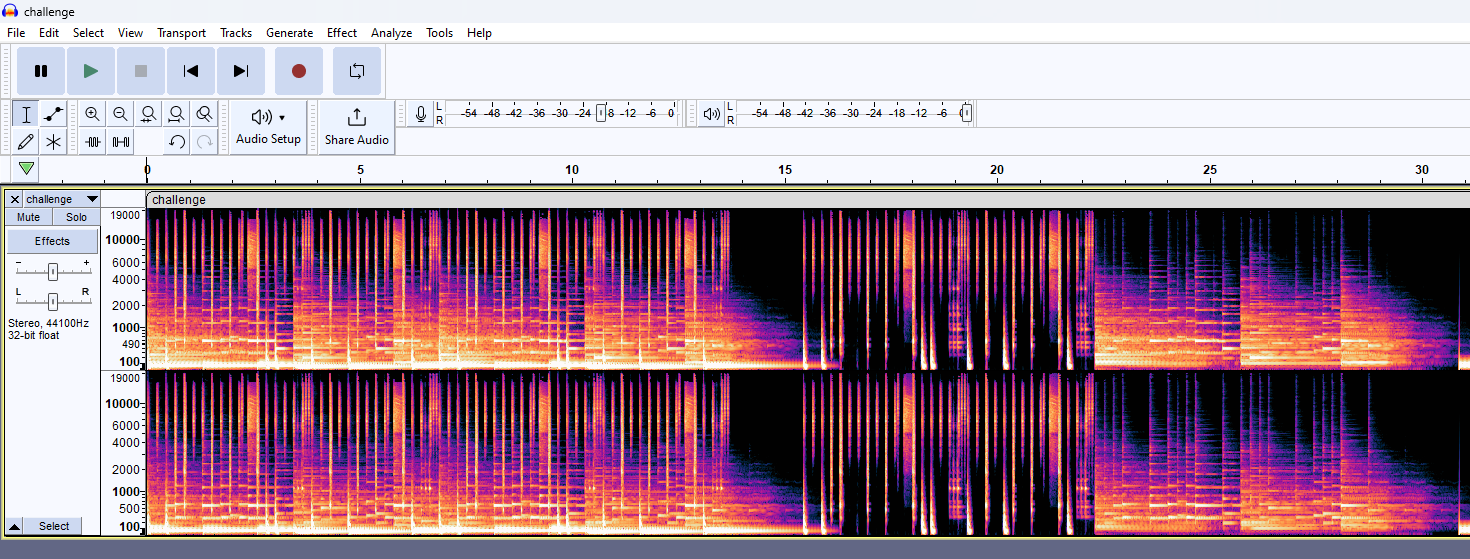
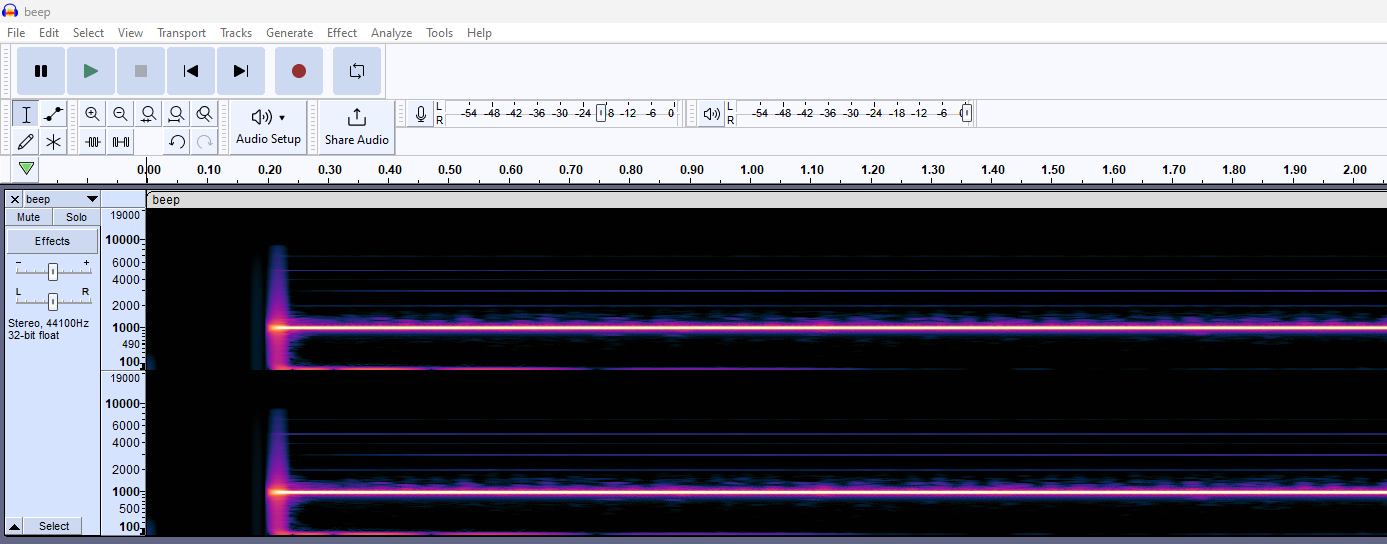
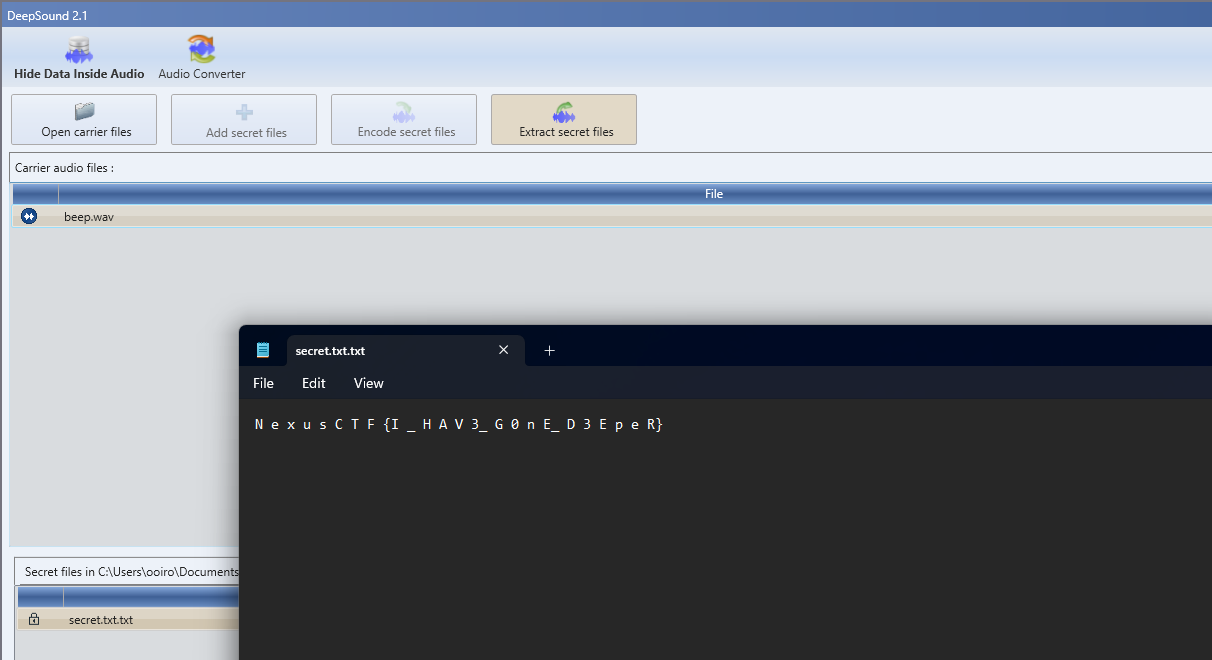
Deep… Deep… Deeper [Steganography]
Question: Let’s see how deep you can go.
Flag: NexusCTF{I_HAV3_G0nE_D3EpeR}
We are given another wav audio file to investigate again. Similarly, the audio waveform and spectrogram seem to be normal.
Reading the challenge name, it seems to be mentioning about DeepSound, a common steganography tool used for audio. However, it seems that the audio was password protected. So the password must be cracked first before obtaining the secret file.
1
2
3
4
5
6
7
8
9
10
11
└─$ deepsound2john beep.wav > sound.txt
└─$ john -w=/usr/share/wordlists/rockyou.txt sound.txt
Using default input encoding: UTF-8
Loaded 1 password hash (dynamic_1529 [sha1($p null_padded_to_len_32) (DeepSound) 128/128 AVX 4x1])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
letmein (beep.wav)
1g 0:00:00:00 DONE (2024-04-20 15:18) 100.0g/s 168000p/s 168000c/s 168000C/s 123456..kenny
Use the "--show --format=dynamic_1529" options to display all of the cracked passwords reliably
Session completed.
Arecibo message [Forensics]
Question: A message just arrived from outer space.
Flag: NexusCTF{I_HAV3_G0nE_D3EpeR}
We are given a WAV audio file to investigate. Reading the description, it mentioned that the audio came from outer space. Having knowledge on space signals in CTFs, it was obviously related to SSTV (Slow Scan TV). Decoding the space signals, the flag can be obtained.
1
2
3
4
5
6
└─$ sstv -d Arecibo.wav -o result.png
[sstv] Searching for calibration header... Found!
[sstv] Detected SSTV mode Martin 2
[sstv] Decoding image... [####################################################################################################] 100%
[sstv] Drawing image data...
[sstv] ...Done!
Echos Parody [Forensics]
Question: “In the land of echoes, where whispers roam, A tale of clues, finds its home. Laughter and tears, merge in the air, In echoes’ parody, stories flare. Footsteps of past, meet those of now, In the echo’s chamber, they take a bow. Love’s sweet whispers, pain’s bitter cry, All in the echoes, they do lie. Listen close, and you will find, Clues and whispers, intertwined. In the echo’s game, secrets unfurl, A world of mysteries, for all to swirl.”
Flag: NexusCTF{C0ll3ct_Th3m_4ll!!}
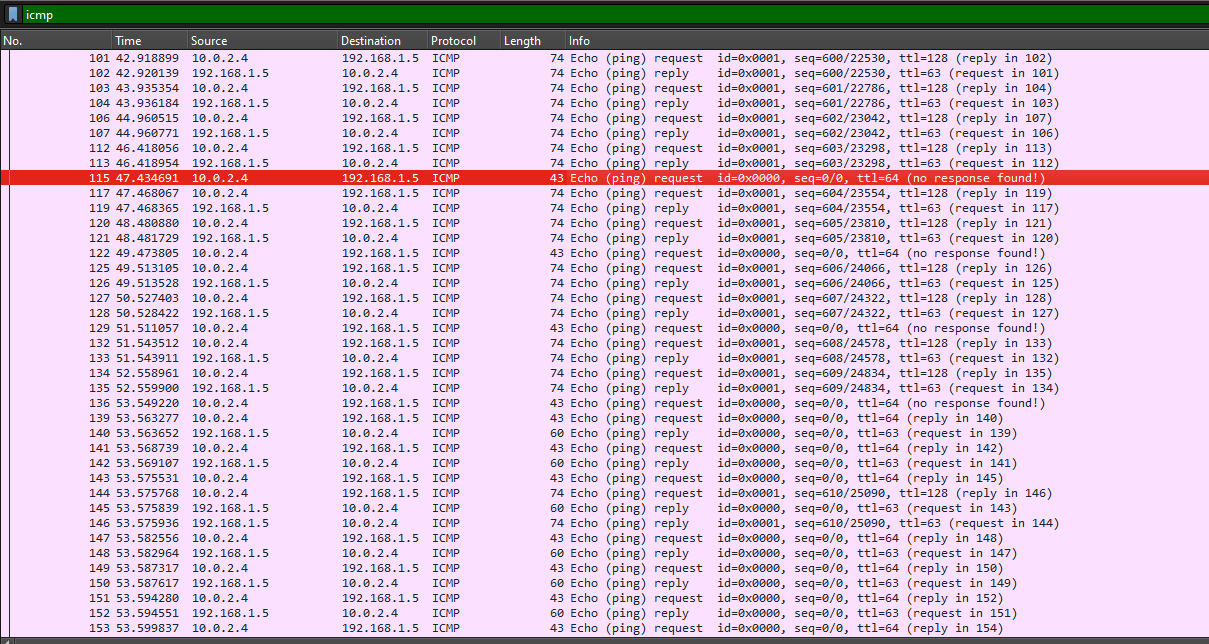
We are given a PCAP to investigate. Inside it were several protocols like ICMP, TCP and TLS. However, the challenge name and description mentioned something about echoes which is related to ICMP, so I guess that is where the focus should be at. Analyzing the ICMP packets, it seems that there were two unique streams, one with ID 0x0000 and the other with ID 0x0001.
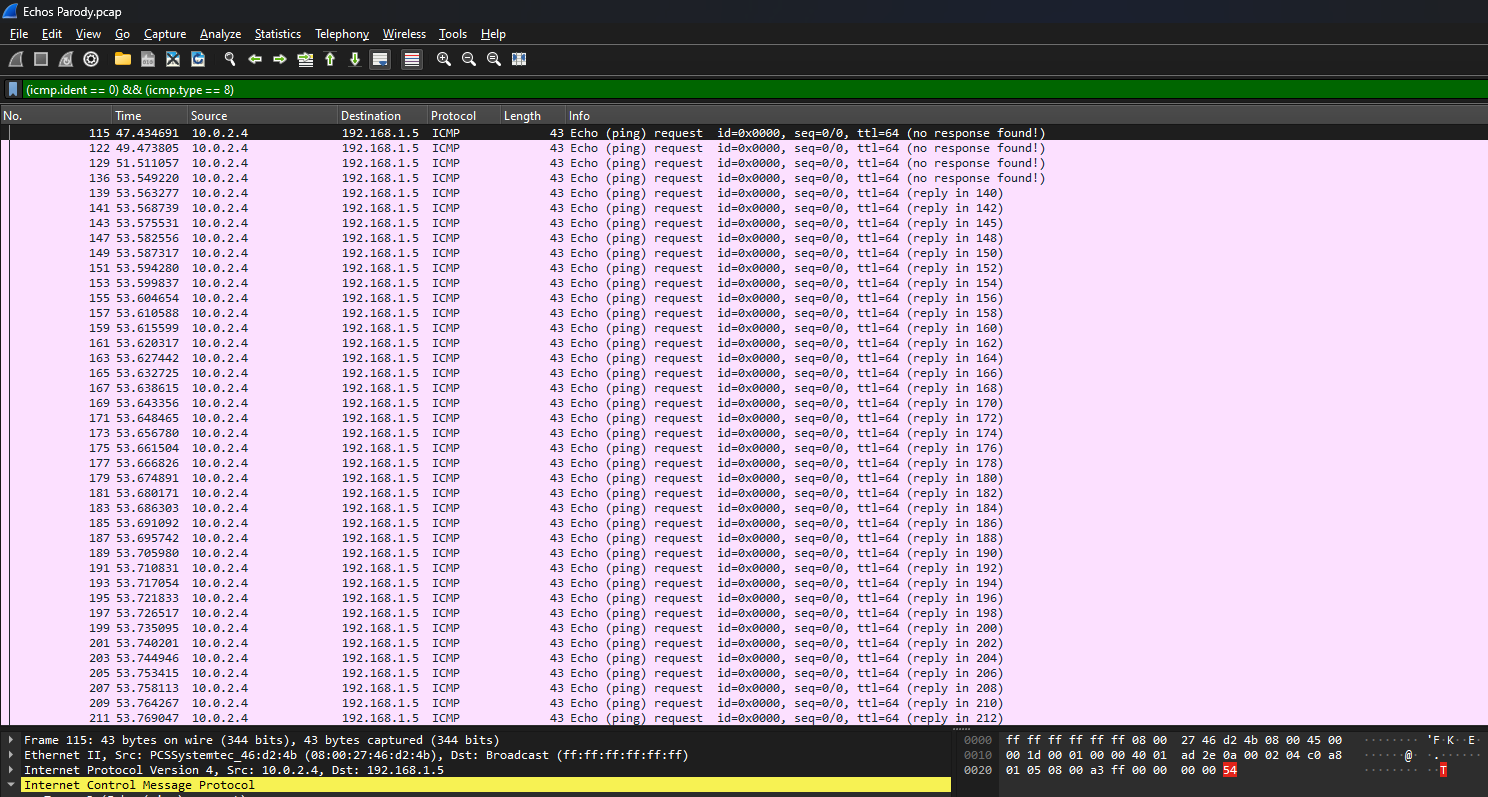
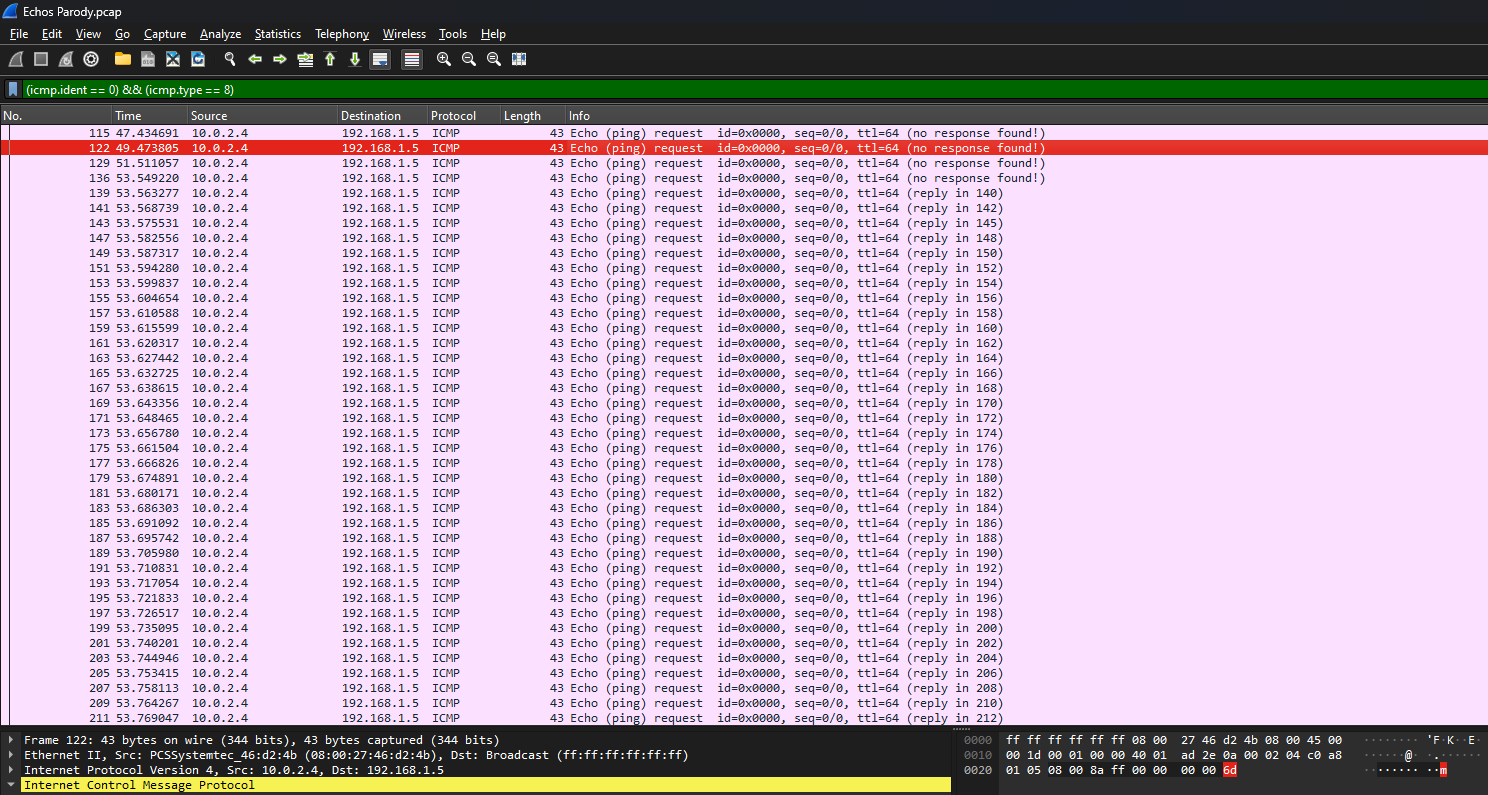
It is common to find ICMP packets storing hidden data within it’s data bytes. Example are these two starting packets from ID 0x0000, notice how the last character in the data was different.
So by filtering the ICMP packets with ID 0x0000 and request only (to avoid duplicates), an encoded string can be obtained.
1
2
3
4
5
6
7
8
└─$ tshark -Y "icmp.ident == 0 && icmp.type == 8" -T fields -e data.data -r Echos\ Parody.pcap | awk '{ printf "%s", $1 }'
546d563464584e4456455a37517a427362444e6a6446395561444e74587a52736243456866513d3d
└─$ echo "546d563464584e4456455a37517a427362444e6a6446395561444e74587a52736243456866513d3d" | xxd -r -p
TmV4dXNDVEZ7QzBsbDNjdF9UaDNtXzRsbCEhfQ==
└─$ echo "TmV4dXNDVEZ7QzBsbDNjdF9UaDNtXzRsbCEhfQ==" | base64 -d
NexusCTF{C0ll3ct_Th3m_4ll!!}