MapnaCTF 2024 - Writeups
This is a writeup for some forensics challenges from MapnaCTF 2024. This was my first CTF with my current team M53 and I managed to solve some forensic challenges with the help from my M53 teammates. Overall, the CTF was pretty hard and I can see why since it was organized by ASIS CTF (played their CTF before, too hard for me).
PLC I 🤖 [Forensics]
Question: The MAPNA CERT team has identified an intrusion into the plant’s PLCs, discovering a covert message transferred to the PLC. Can you uncover this secret message?
Flag: MAPNA{y0U_sHOuLd_4lW4yS__CaR3__PaADd1n9!!}
We are given a PCAP file to investigate. Analyzing the packets, some Ethernet packets seem to have suspicious trailer paddings. Going through all the packets, the flag can be obtained from their trailer.
1
2
3
4
5
6
1: MAPNA{y
2: 0U_sHOu
3: Ld_4lW4
4: yS__CaR
5: 3__PaAD
6: d1n9!!}
Tampered [Forensics]
Question: Our MAPNA flags repository was compromised, with attackers introducing one invalid flag. Can you identify the counterfeit flag?
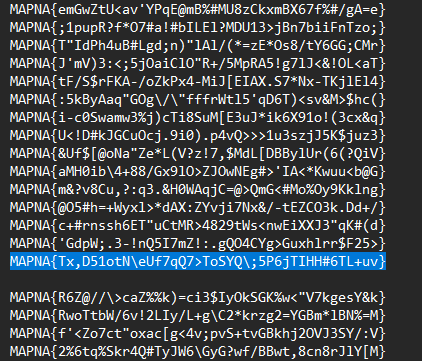
Flag: MAPNA{Tx,D51otN\\eUf7qQ7>ToSYQ\\;5P6jTIHH#6TL+uv}
We are given a text file to investigate. Just find the outlier flag from the fake flags.
Credits to @Stoffe for this hilarious meme
XXG [Forensics]
Question: Welcome to the Forensics XXG challenge! Our investigator stumbled upon a mysterious file. Can you uncover the hidden message?
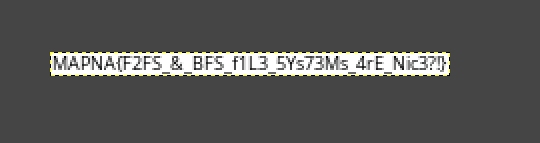
Flag: MAPNA{F2FS_&_BFS_f1L3_5Ys73Ms_4rE_Nic3?!}
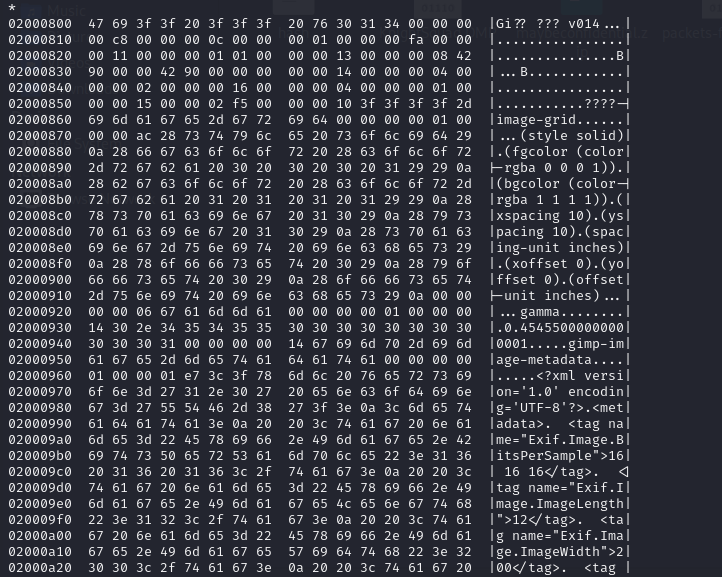
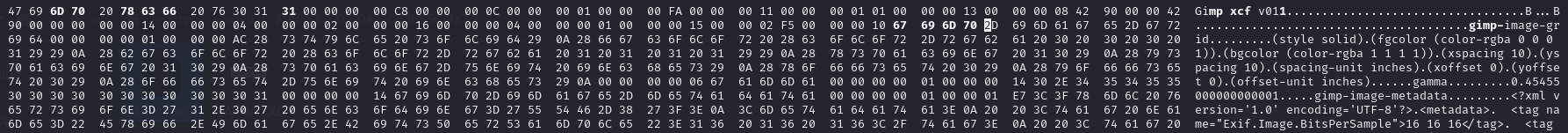
We are given a XXG file to investigate. Unfortunately I could not solve this before the CTF ended, but I still attempted it with the help from @Crazyman. Analyzing the hex data of the file, we can find a hidden image file embedded within it. It is at the very bottom so we have to first extract the specific part and edit some header values.
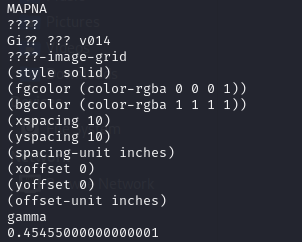
Looking at the broken header, it seems that it closely resembles a GIMP header:
Researching online about GIMP v014, it seems like XCF file was indeed from GIMP. Since we know its an XCF file now, we can study its headers and fix them.
After fixing it, the flag can be viewed GIMP.