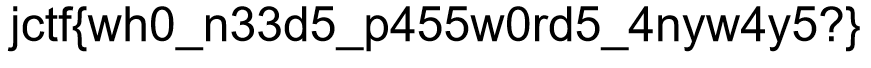JerseyCTF 2024 - Writeups
This is a writeup for some forensics challenges from JerseyCTF 2024. I joined this CTF when it was about to end in like 8 hours, managed to solve almost all the forensics challenges.
substitute-detail-torrent [Forensics]
Question: We’ve been given a file and need to figure out what url it was downloaded from.
Flag: jctf{https://www.NTFS/File/Metadata}
We are given a Windows Imaging Format (WIM) file to investigate. Just strings the file to obtain the flag.
1
2
3
4
5
└─$ strings Blob.wim
MSWIM
This is a testHostUrl:jctf{https://www.NTFS/File/Metadata}
O%{V
O%{V
groovy [Forensics]
Question: You know you’re getting old when you hear the music these kids are putting out and all you think is “no thank you.” Anyway, I’m too old for this or maybe I need some cybernetic ears or something. Maybe you’ll like these groovy tunes.
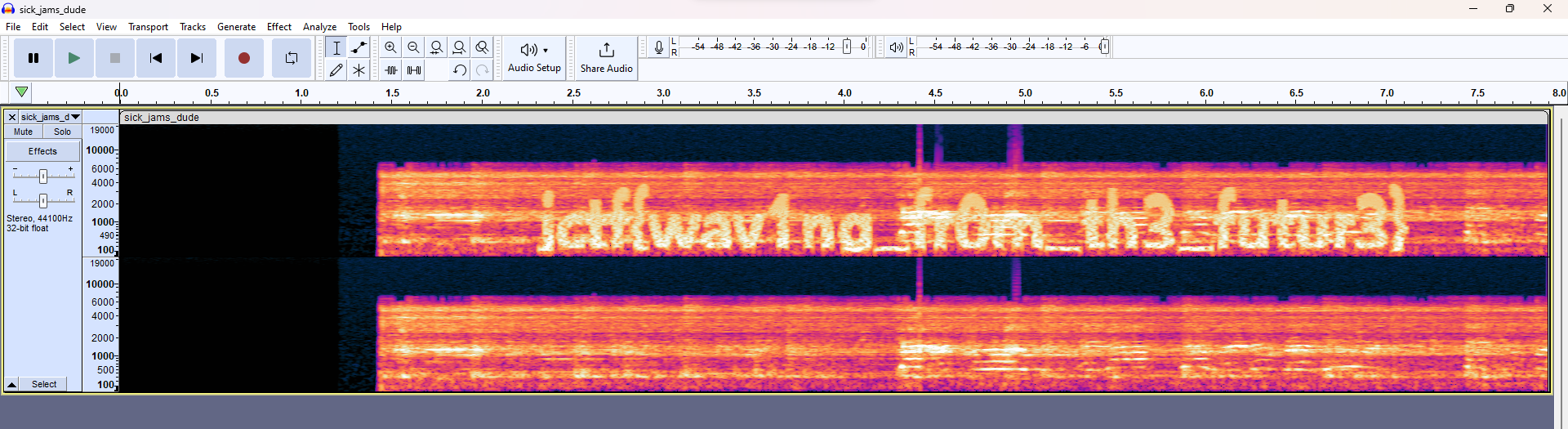
Flag: jctf{wav1ng_fr0m_th3_futur3}
We are given a WAV file to investigate. Just check the audio spectrogram to obtain the flag.
open-notes [Forensics]
Question: A workstatiobn we are examining had some open files at the time of the memory capture. Examine the memory image at open-notes.vmem to find the flag.
Flag: jctf{m3m0ry_f0r3ns1cs_ftw}
We are given a memory dump to investigate. Since the name and hint mentioned about notes/notepad, I dumped the notepad.exe process and the flag can be found.
1
2
3
4
5
6
└─$ strings -e l pid.6168.dmp | grep jctf{
jctf{m3m0ry_f0r3ns1cs_ftw}
jctf{m
jctf{m3m0ry_f0r3ns1cs_ftw
jctf{m3m0ry_f0r3ns1cs
jctf{m3m0ry_f0r3ns1cs_ftw}
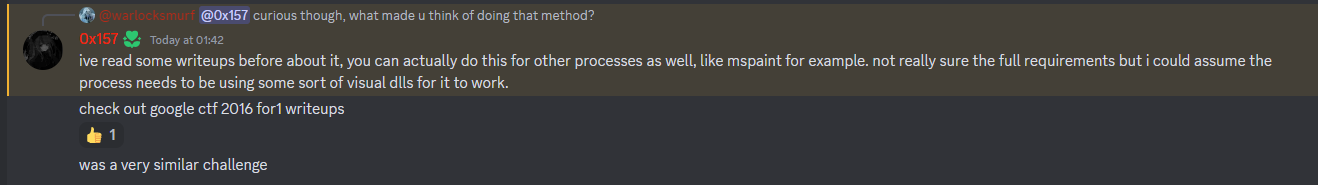
Another interesting method from @0x157 was that most processes can be actually loaded into GIMP as .data to read its content. Blog 1 and Blog 2 talks about his method and it is very interesting.
All-Along-the-Watchtower [Forensics]
Question: Our informant has met back with us at base. He has stolen a file from a suspect who’s starting to show dangerous signs of cyberpsychosis. Aside from his unending lust for bloodshed, our informant noted that the suspect would not shut up about “rats making him crazy” as well as the term “Base FFFF+1” but that’s probably just nonsense. Anyways, can you look beyond the layers of this corrupted file to extract the information that we need?
Flag: jctf{1-4m-50-50rry-f0r-7h15}
We are given a corrupted JPG file. Using binwalk, it was shown that it was actually a zip file with two files within it.
1
2
3
4
5
6
7
└─$ binwalk -e the-panglao-watchtower.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
130313 0x1FD09 Zip archive data, at least v2.0 to extract, compressed size: 1464, uncompressed size: 5958, name: SECRETS/password.txt
131827 0x202F3 Zip archive data, at least v2.0 to extract, compressed size: 834, uncompressed size: 834, name: SECRETS/protected_2.7z
132847 0x206EF End of Zip archive, footer length: 22
Extracting the files, we obtained a password.txt file and another zip file to crack.
1
2
3
4
5
6
7
└─$ tree *
1FD09.zip [error opening dir]
SECRETS
├── password.txt
└── protected_2.7z
1 directory, 3 files
So it was obvious that a dictionary attack was required. Using 7z2john and john, the zip file hash can be obtained for further cracking. The password was jimihendrix123!.
1
2
3
4
5
6
7
└─$ 7z2john protected_2.7z > hash
$7z$2$19$0$$16$07996b1663ef7ae9a7ae82e70359f808$2151154755$688$683$c7b1b14608b52685963c5e8a3254c5dd9edbded6e2bfd586b98f6555455607e516c5e710e3302061c1278efd81cbefccef79f78a4cbbc05c81299ff88741372c64380759b0e5b9e06968dc5c0ee69e7e592729ad2f2ed7e20727845f244395a0b864db750b919695ff29f95ed1bb864d767f38c32ee896d0741819e941c3f59f0cfe972e7487bb0b7a3c68282c6f42179f0650580f9cc7c3d6272be71bbdc002ad6a93cd91b9b092357b85a8de31ee10764f8742880e1410bbe49420737e653d4c96fb8b66a13344e24c290dafa189cc764151cfe771b517088fdc11e14d7aa5bb5fafd2f7ee38aa2dabb2143d926f17150d285b5671f7e4d4fdc053ba6ac15b93f3ec3f231b4832a19324ff28a621ad8ebe1ccc445bac1fb3dc56e246a333ad672731558e5a852e3bb1b565684c5521c3fd3c19e93f73a0d814abaad490cba3cfc74783334b772b6fd2a01f3a5d094dde614e0df90def5e4f2ecea6cfb24e9ddec2d1248687a2acfabf53fc7b03eab41c2a7d640041ba8d84f69269e7938cc80011f5d6a8d87b043384d32c0fbda880e00067fea1f9524baf912cba4ca2a0558588a23cfd8eba2cd17031ed296399834cefa7f47d8c4aaa0391b2b391af88cfd75297d8d1530cd8c5ab3d981dc736c745f9ff4ab6457b512447b54b1fd98793b551af22ef20d5406ad7054a7733000f8800adb733379ecf87cf15401dd7d9576ae20b5cf3b29f195f55345d209b6cf1efc7d7ed4e4d3529d230ccacfabedeb24e99b86935eaf2880eaa9e8e481845581181c8b0ecb07a8b6f47bf24569a0699c4c443a1618a1fdd821cb635d4a0e989ec7af4712eaa6541b7c3f28087b3ab5bceffc3da9b54982225136a1961877657fb58b0e127c641e34cb14ff2a95328bf44918e768bbbb7e25f2a3162507497162dd07faeffb6b70019c56b75f19b1bc08780c88f8e5b3c2aeeeaebec0b38d9eb$720$00
└─$ john --wordlist=password.txt hash
└─$ john --show hash
?:jimihendrix123!
Cracking the zip file, we are given another text file with weird text. Researching online, I stumbled upon this blog that mentioned the decoding technique was Base65536 (no joke). Decoding it gives us the flag.
1
2
└─$ cat secret_plans.txt
啉鹷ꍬ鴠𔑡啥𒁴鰠𓉥𓈠驨啭ꍡ捬褠驨𒄠ꍯ顩慥𓈠驨𒄠ꍯ𓉩顩险𓅮唬鵴啥魯鹦鹣ꍡ啳𒁴捯褠驨啹鹷ꍬ𒄠𖥡售絔𖥥𔔠腩啬ꍡ啬陰捹簠饯ꔠ啹驨饡鴠𓁵𓅴售鵔𓅩鸠啳𓉩鸠𐙳𓈧鸠捴縠ꔧ鰠鹯鱮𓈠啯陲𒅭鱡啥鵴𒁲鱵啨鵴啥𓉳驲𓉥啳驮𓉸𔔠驥捫褠鹨啳𒁲𓍧啥繁鴠𓅡ꔠ饡啥驭鰠𐙯啥陭捤砠靹𓁥𓅰项𒁨鹳啳𓅩𐘠啯除𐙭ꄠꉯ捥縠啴鹷ꍬ霠啥𓁣𠁡捹縠ꔧ頠陲𖥺售𓁃𠁡瑹縠𔔠𓅡頠陲𖥺𒀠顮捥褠驨啹𒁬ꉣ饥ꔠ啥𐙩阠𓀠𒁯慭阠𓀠靵驢啲𒁲ꕯ售啁𓍲面𓁥𓀠𒁯啭鹷鵴𓀠𓉡捳蜠𓉡啳陭驫ꔠ啥𓁣𠁡捹𓁃𠁡瑹砠陲𖥺唿啉陷啳𓁣𠁡啹𐙯驣䄮褊驨啹𓍰啴驭鸠啮啡𒁲ꕯ䄮瘊𓀠靵驢啲𒁲ꕯ䄮瘊𓀠靵驢啲𒁲ꕯ𔔠𓉩啨陲𓅴䄮褊驨啹𓍰啴驭鸠啮啡𓍲面𓁥𓀠𒁯啭鹷鵴𓀠靵驢啲陲𓅴䄮蜊靵驢啲陲𓅴唿啉陨驴𓀠靵驢啲陲𓅴䄮褊驨啹陭驫ꔠ啥𓁣𠁡捹㸍𓁃𠁡瑹縠𔔠𓅡頠陲𖥺𒀠顮捥㸍鵔𖥥𒄠𓉵ꔠ啥𐙩阠𓀠𒁯𦡭𢲀䄮砊陲𖥺唿啉陷啳𓁣𠁡啹𐙯驣䄮褊驨啹𓍰啴驭鸠啮啡𒁲ꕯ䄮瘊𓀠靵驢啲𒁲ꕯ䄮瘊𓀠靵驢啲𒁲ꕯ𔔠𓉩啨陲𓅴䄮褊驨啹𓍰啴驭鸠啮啡𓍲面𓁥𓀠𒁯啭鹷鵴𓀠靵驢啲陲𓅴䄮蜊靵驢啲陲𓅴唿啉陨驴𓀠靵驢啲陲𓅴䄮褊驨啹陭驫ꔠ啥𓁣𠁡捹㸍𓁃𠁡瑹縠𔔠𓅡頠陲𖥺𒀠顮捥㸍鵔𖥥𒄠𓉵ꔠ啥𐙩阠𓀠𒁯𦡭𢲀售㸍㸍㸍顪魴晻椭扭攵樭𓀰𖥲鬭𓀰氭晨𠌵
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
I will have to get them all. The police, the politicians, the officials too. They will pay. THey wiLl all pay. God my head hurts. This is it isn't it. I'm going to rampage through the streets next week. This rogue AI has made me gone mad. Cyberpsychosis is no damn joke. It will be crazy. I'm crazy. Crazy? I was crazy once. They locked me in a room, a rubber room. A rubber room with rats. Rats make me crazy.Crazy? Crazy? I was crazy once.
They put me in a room.
A rubber room.
A rubber room with rats.
They put me in a rubber room with rubber rats.
Rubber rats? I hate rubber rats.
They make me crazy.
Crazy? I was crazy once.
They put me in a room….
Crazy? I was crazy once.
They put me in a room.
A rubber room.
A rubber room with rats.
They put me in a rubber room with rubber rats.
Rubber rats? I hate rubber rats.
They make me crazy.
Crazy? I was crazy once.
They put me in a room….
jctf{1-4m-50-50rry-f0r-7h15}
living-on-the-edge [Forensics]
Question: A workstation we are examing had a browser open at the time of the acquisition. Examine the memory image living-on-the-edge.vmem to find the flag.
Flag: jctf{3dg3_0f_y0ur_s3at}
We are given a memory dump to investigate. Since the name and hint mentioned about Microsoft Edge, I dumped the msedge.exe process and the flag can be found.
1
2
3
4
5
└─$ strings -e l pid.5344.dmp | grep jctf{
https://www.jerseyctf.com/?flag=jctf{3dg3_0f_y0ur_s3at}
https://www.jerseyctf.com/?flag=jctf{3dg3_0f_y0ur_s3at}#Resources
https://www.jerseyctf.com/?flag=jctf{3dg3_0f_y0ur_s3at}
---SNIP---
rescue-mission [Forensics]
Question: Linux really lets you do anything… when messing around with my new install, I managed to delete my bootloader! Now I can’t get in when I had an important file on my desktop… at least I virtualized it, maybe you can get the data out of it?
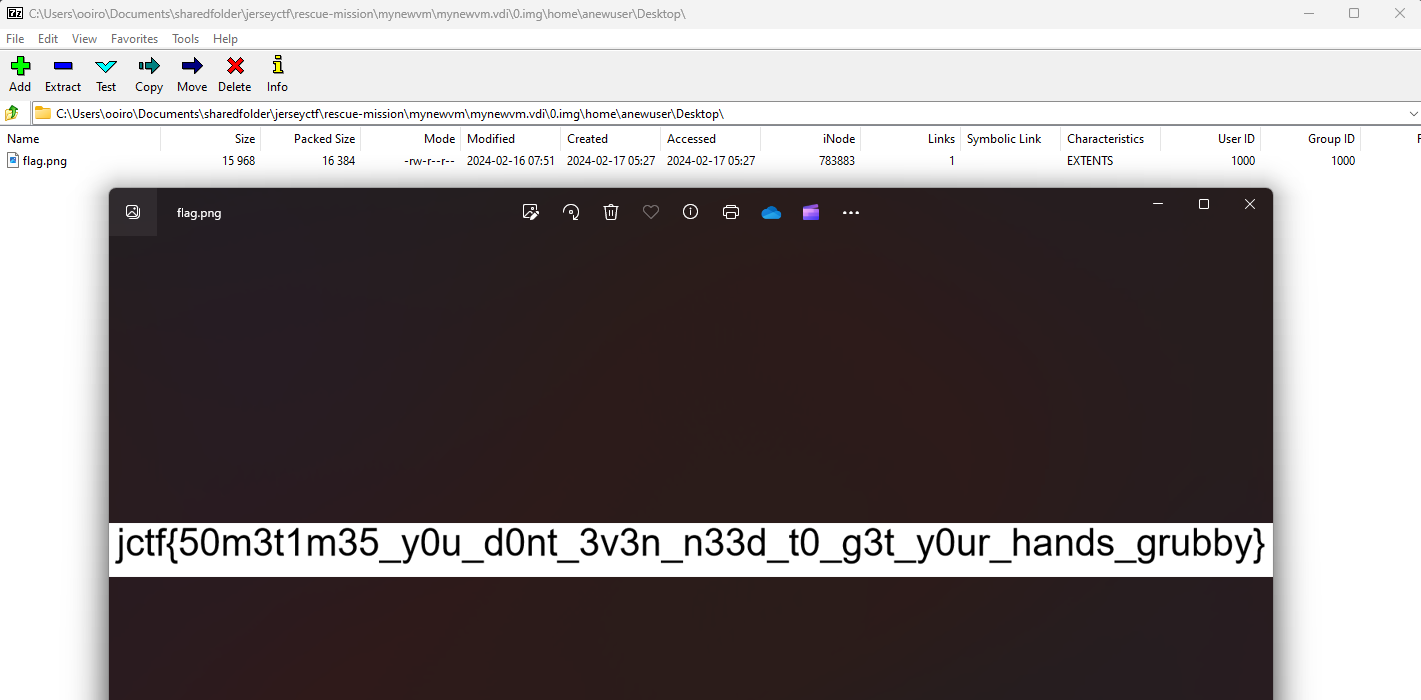
Flag: jctf{50m3t1m35_y0u_d0nt_3v3n_n33d_t0_g3t_y0ur_hands_grubby}
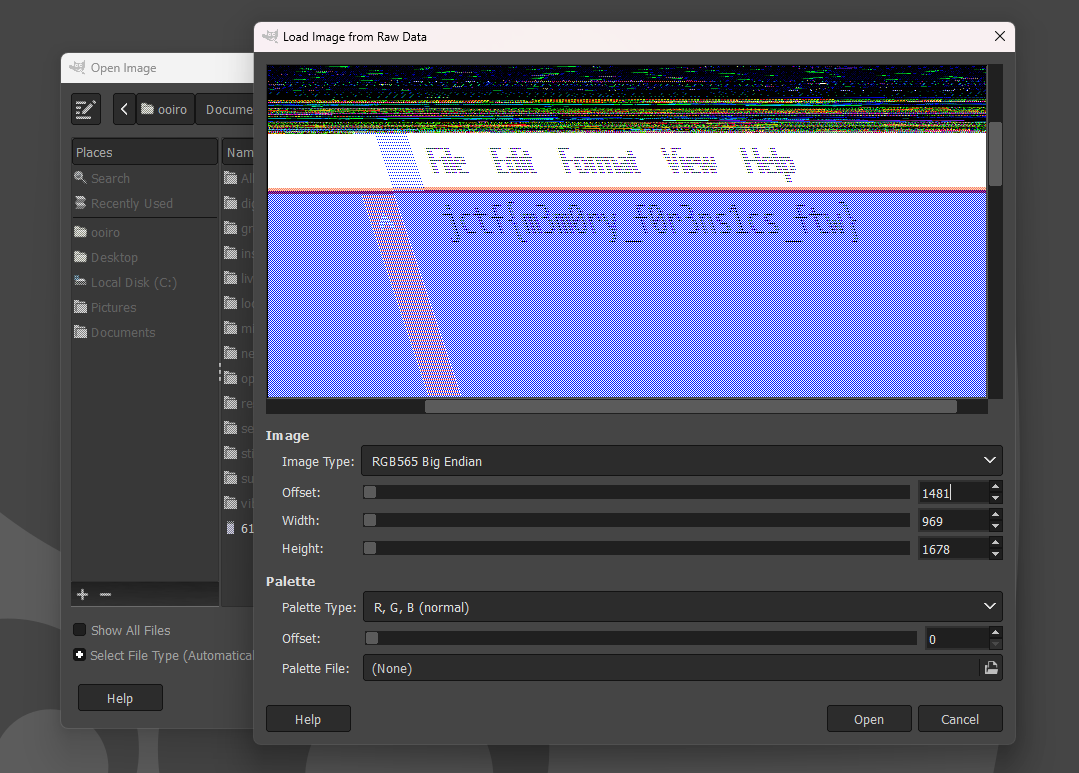
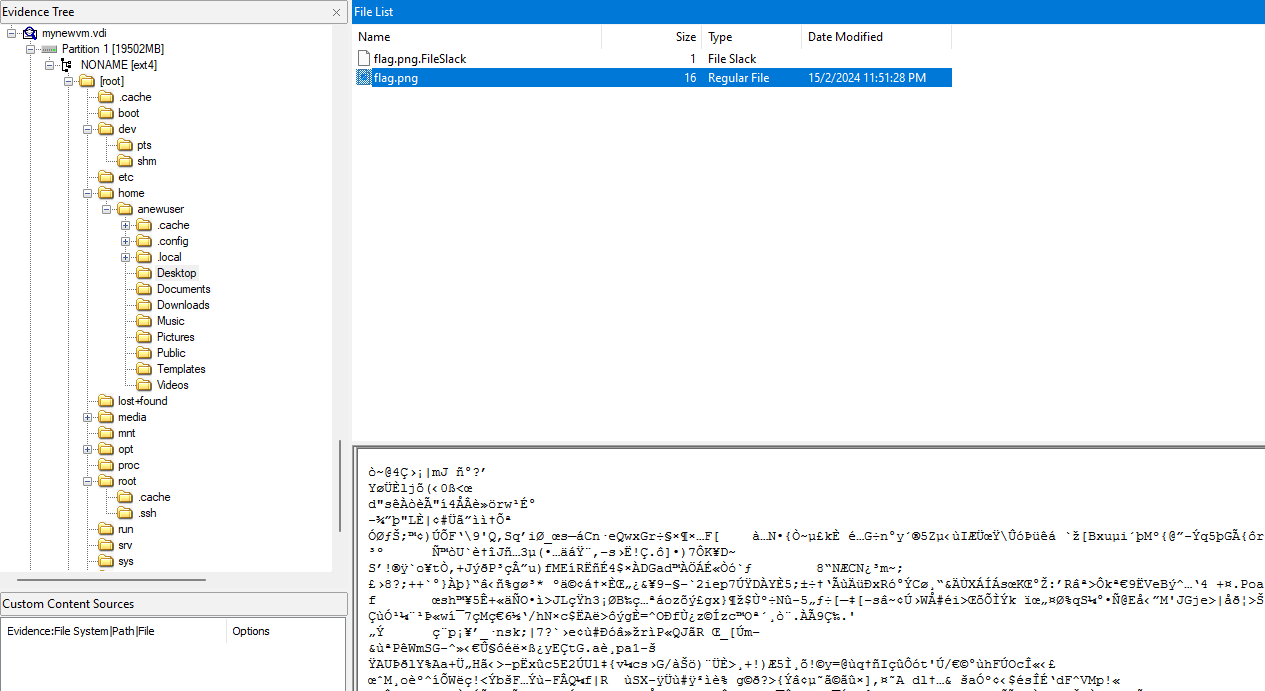
We are given a VDI file to investigate. Reading the question, it seems that the flag is probably located in the user’s Desktop. Using FTK Imager, I found the flag image but it was broken/corrupted. Spending 2 hours on how I can recover its content using the slack space, I gave up and tried using 7zip to analyze it for fun. Unexpectedly, it worked..
locked-out [Forensics]
Question: I made this zip folder a while ago and I can’t remember the password! I know I made it a very secure password, so wordlists won’t help… can you open this folder without the password?
Flag: jctf{wh0_n33d5_p455w0rd5_4nyw4y5?}
We are given a password-protected zip file that has a text file of the flag and a SVG file. Remembering a CTF I’ve played previously, this relates to the plaintext attack since the content within the zip was compressed using the Store method. Reading the description, I was right, however, there is a twist. See, most blogs will mention SVG headers to have <?xml version="1.0". However, according to Mozilla, SVG headers can also have this <svg version="1.1" as the header too.
1
2
3
4
5
6
└─$ unzip -Z -l locked-out.zip
Archive: locked-out.zip
Zip file size: 173982 bytes, number of entries: 2
-rw-a-- 6.3 fat 10528 Bx 10540 stor 24-Feb-19 18:19 flag.png
-rw-a-- 6.3 fat 163138 Bx 163150 stor 24-Feb-19 19:34 nokeynoprob.svg
2 files, 173666 bytes uncompressed, 173666 bytes compressed: 0.0%
So the plaintext we were required to use was actually <svg version="1.1", not the usual <?xml version="1.0". I asked the author on this and he agreed it’s true, he wanted players to actually understand the attack rather than copy pasting codes from README.md (LMAO).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
└─$ echo -n '<svg version="1.1"' > out
└─$ ./bkcrack -C ~/Desktop/sharedfolder/jerseyctf/locked-out/locked-out.zip -c nokeynoprob.svg -p out
bkcrack 1.6.1 - 2024-01-22
[13:27:41] Z reduction using 11 bytes of known plaintext
100.0 % (11 / 11)
[13:27:41] Attack on 575505 Z values at index 6
Keys: 9c9d83e5 7915abee 58998fbc
37.4 % (215500 / 575505)
Found a solution. Stopping.
You may resume the attack with the option: --continue-attack 215500
[13:42:38] Keys
9c9d83e5 7915abee 58998fbc
└─$ ./bkcrack -C ~/Desktop/sharedfolder/jerseyctf/locked-out/locked-out.zip -k 9c9d83e5 7915abee 58998fbc -U cracked.zip jersey
bkcrack 1.6.1 - 2024-01-22
[13:47:59] Writing unlocked archive cracked.zip with password "jersey"
100.0 % (2 / 2)
Wrote unlocked archive.
Cracking the new zip file, we can get the flag.
digital-footprint [Forensics]
Question: One of our agents in the SOC captured some traffic from a suspicious connection on the network. We need you to take a look at the pcap file and see if you can find anything useful. Call it a hunch, but we think the suspect was exchanging information somewhere, but we’re not sure where, or what, or even how.
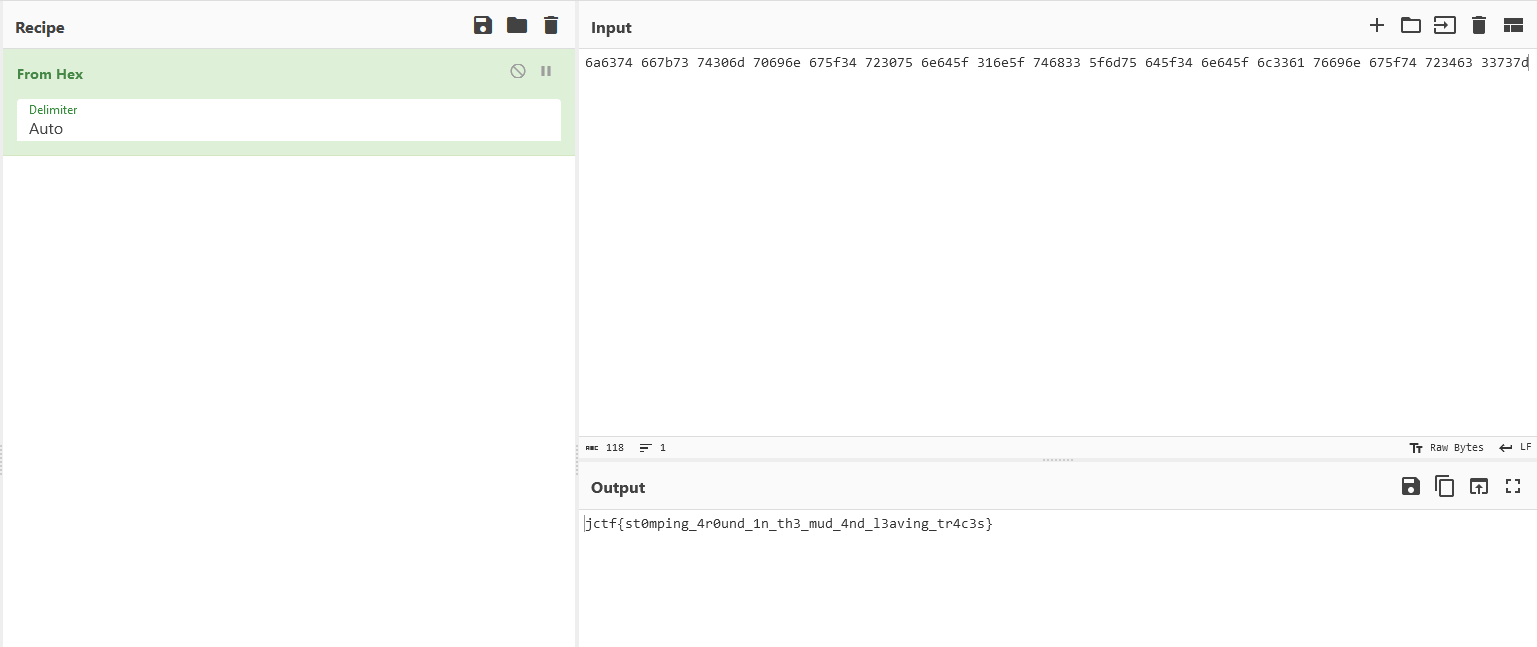
Flag: jctf{st0mping_4r0und_1n_th3_mud_4nd_l3aving_tr4c3s}
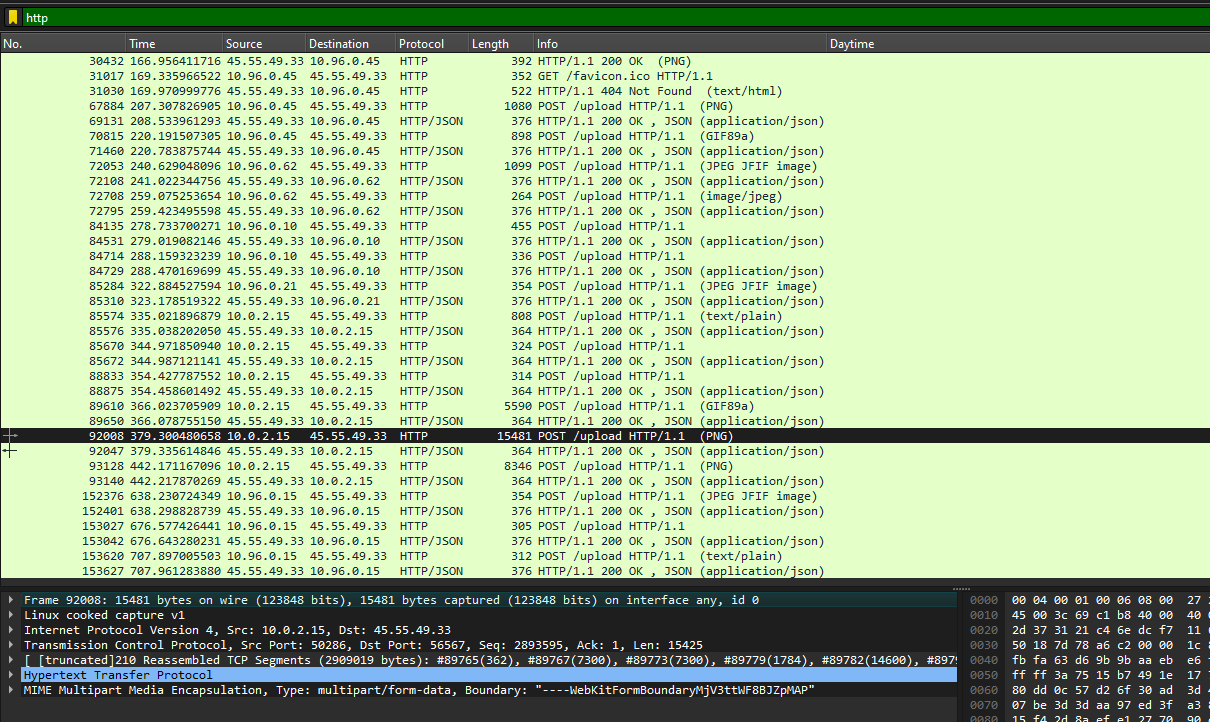
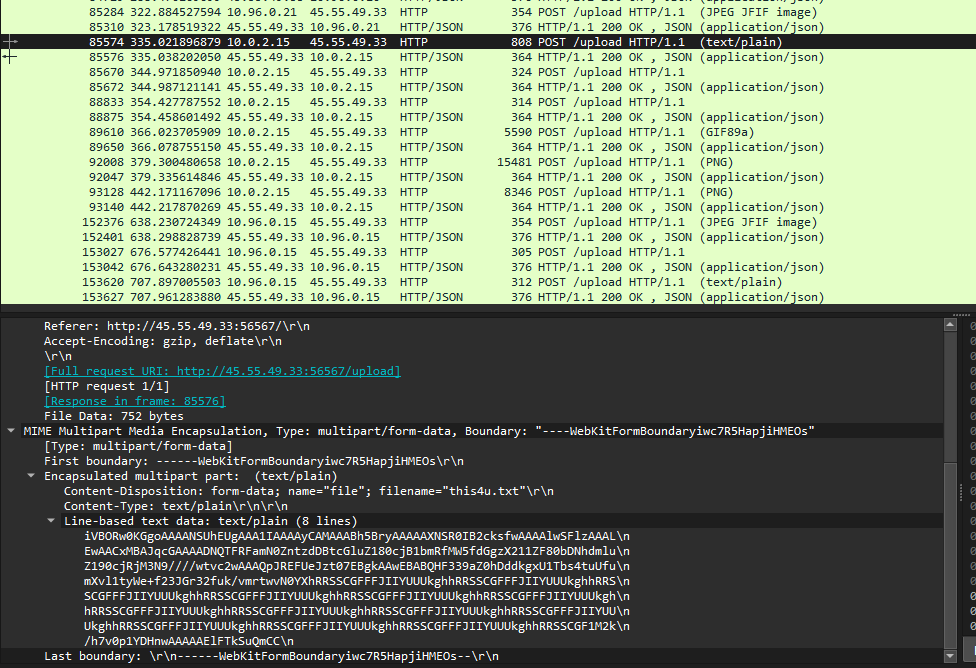
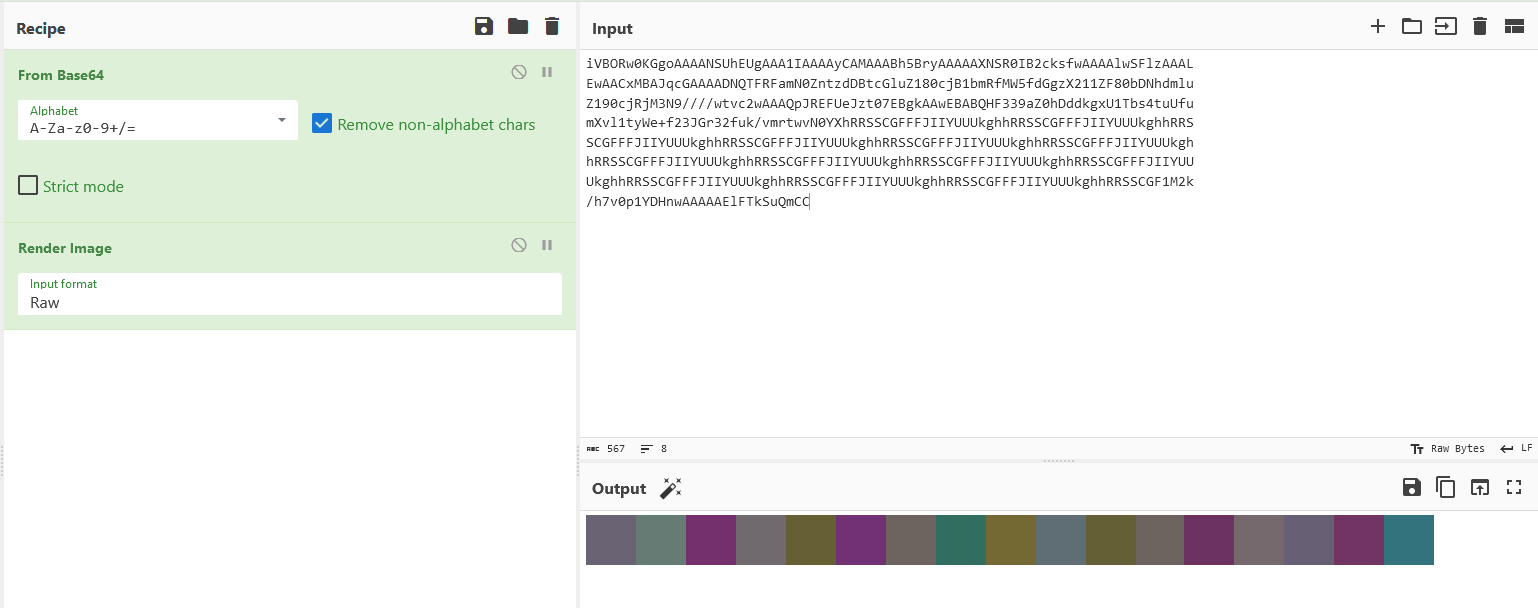
We are given a PCAP file to investigate. There were many packets recorded in the traffic, the one that stands out the most was HTTP since there were several images transmitted within it.
Unfortunately, I could not solve this before the CTF ended. However, I read some writeups on it and it was actually pretty simple. Notice how this particular packet has a long encoded string within it.
Decoding the string gives us a png image with several colors. This is a similar concept to other CTFs I’ve played where color hex codes matter. So just check each hex code and the flag can be obtained.
secret-tunnels [Forensics]
Question: An attacker has accessed the corporate network and is exfiltrating the flag!
Flag: jctf{dn57unn3l1n6}
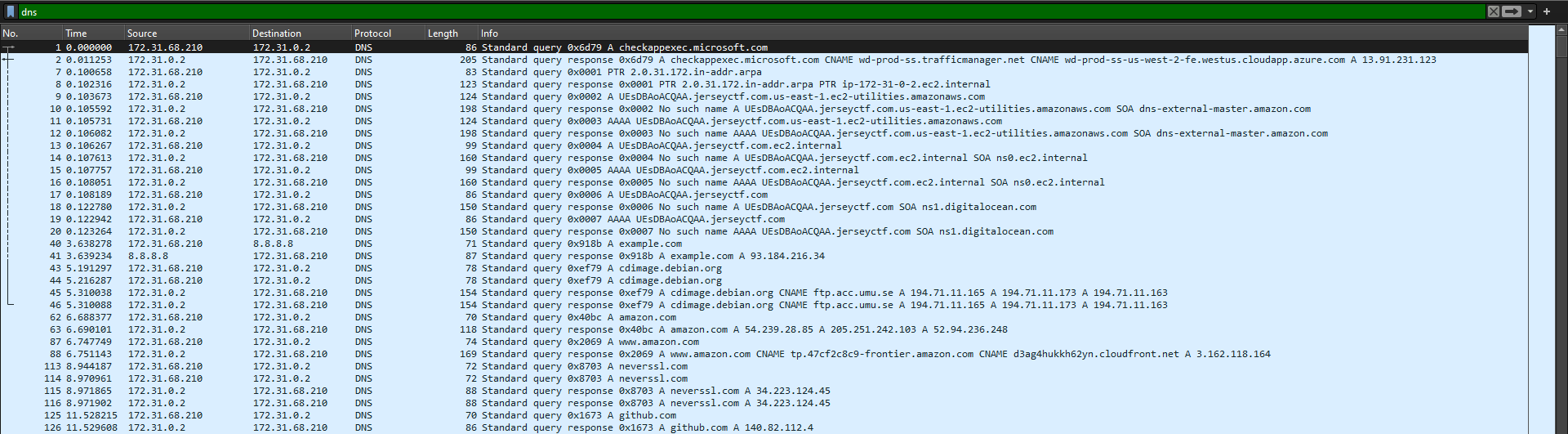
We are given a pcap file to investigate. Several protocols can be found within it like HTTP, DNS and TLS. Spending an hour on this, I noticed the subdomain names were suspicious.
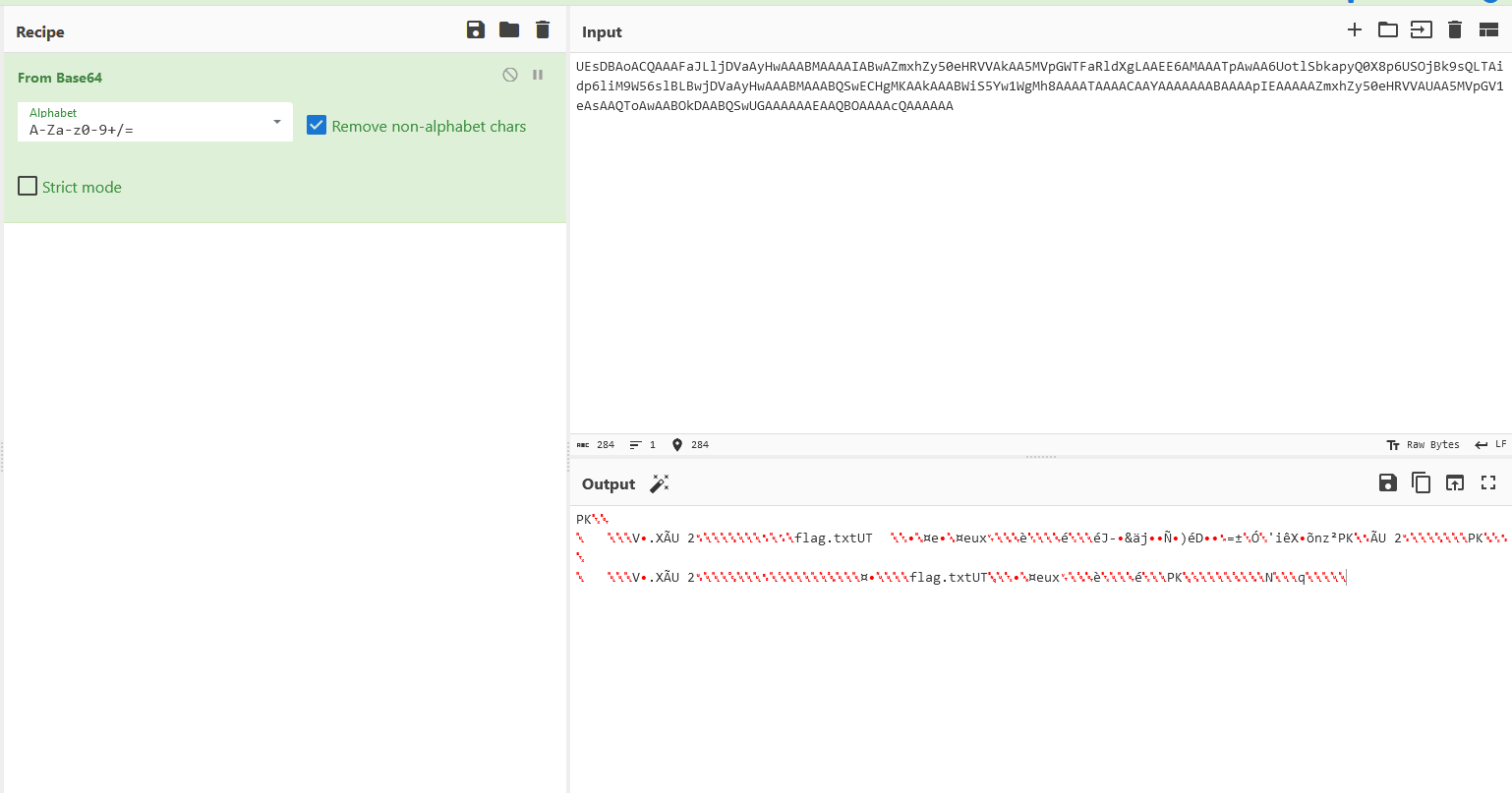
Extracting all the subdomains, we get a zip file (specifically PKZIP).
1
UEsDBAoACQAAAFaJLljDVaAyHwAAABMAAAAIABwAZmxhZy50eHRVVAkAA5MVpGWTFaRldXgLAAEE6AMAAATpAwAA6UotlSbkapyQ0X8p6USOjBk9sQLTAidp6liM9W56slBLBwjDVaAyHwAAABMAAABQSwECHgMKAAkAAABWiS5Yw1WgMh8AAAATAAAACAAYAAAAAAABAAAApIEAAAAAZmxhZy50eHRVVAUAA5MVpGV1eAsAAQToAwAABOkDAABQSwUGAAAAAAEAAQBOAAAAcQAAAAAA
However, the zip file was password protected, so we just have to crack it using john again. The password was njit1220.
1
2
3
4
5
6
7
└─$ zip2john download.zip > hash
$pkzip$1*2*2*0*1f*13*32a055c3*0*42*0*1f*8956*e94a2d9526e46a9c90d17f29e9448e8c193db102d3022769ea588cf56e7ab2*$/pkzip$
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash
└─$ john --show hash
download.zip/flag.txt:njit1220:flag.txt:download.zip::download.zip
Inside the zip file was a text file with the flag.
1
2
└─$ cat flag.txt
jctf{dn57unn3l1n6}
sticky-situation [Forensics]
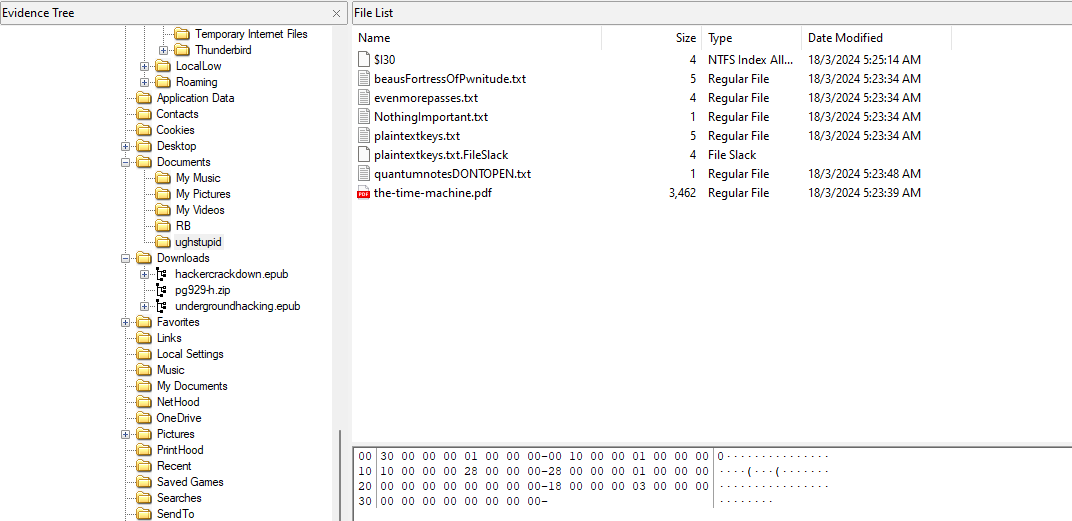
Question: Somebody found this laptop running in the basement of Cullimore - right by the mailroom. Normally we’d just turn it in, but with all of the cyberattacks and cyberpsychosis going on - we’re not about to throw away evidence without examining it first. Examine this ad1, and see if anything sticks out to you. I find it useful to write down my thoughts and findings on whatever I have nearby - paper, sticky notes, etc. Once I have evidence, I put it on a wall or lay it on the table and start connecting the dots. Yes, I’m crazy with strings all over the wall - but it helps! Maybe you’ll find my approach useful, too?
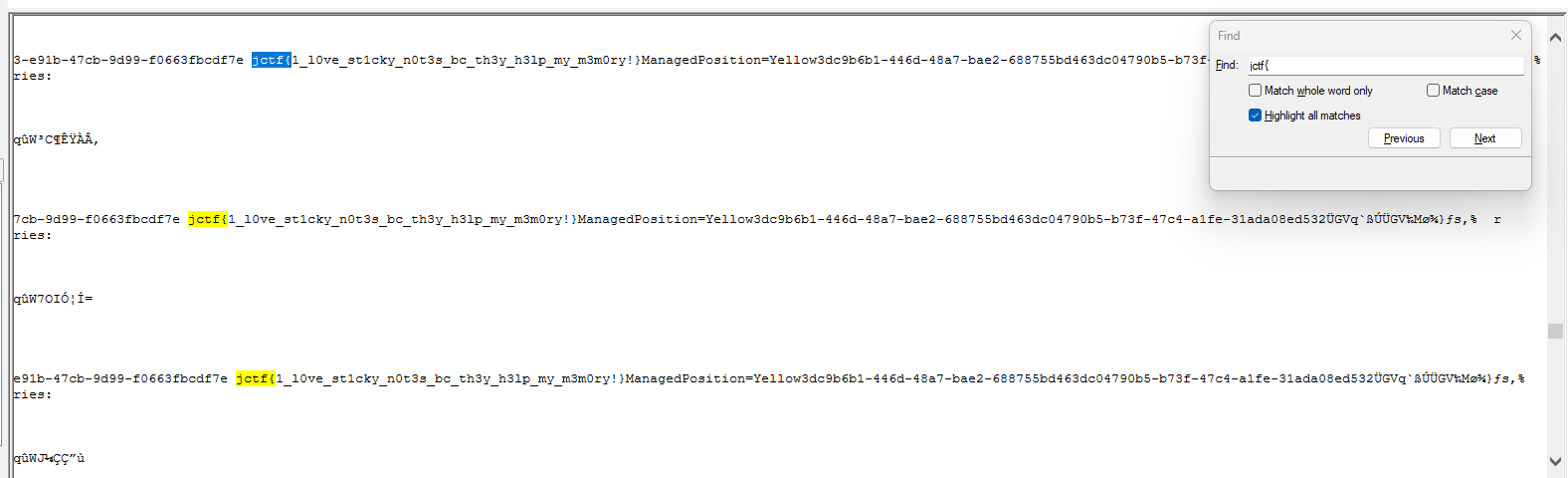
Flag: jctf{1_l0ve_st1cky_n0t3s_bc_th3y_h3lp_my_m3m0ry!}
We are given an AD1 file to investigate. Using FTK Imager, I checked the common folders like Downloads, Documents, Temp and Desktop but only found unrelated files.
Reading the question, it seems that it is related to text files or sticky notes. Reading on Window sticky notes, I stumbled upon this blog that talks about sticky note artifact located in C:\Users\%UserProfile%\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalStat\plum.sqlite. The flag can be found within the artifact.
vibrations [Forensics]
Question: While managing some of our thermal systems, we noticed unusual behavior. We collected the network traffic, see if you can find anything unusual.
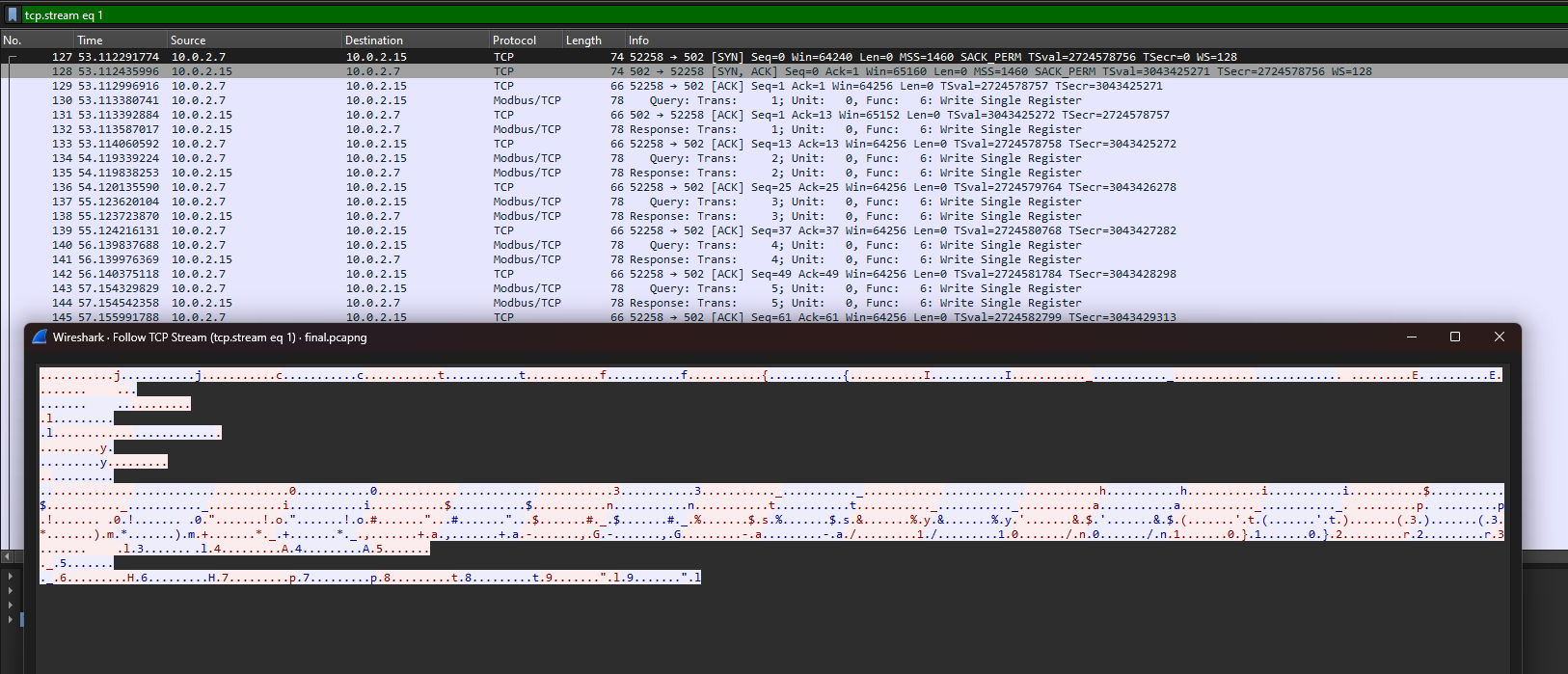
Flag: jctf{I_rEllAy_H0p3_thi$_i$nt_a_p0ol_sy$t3m_aGa1n}
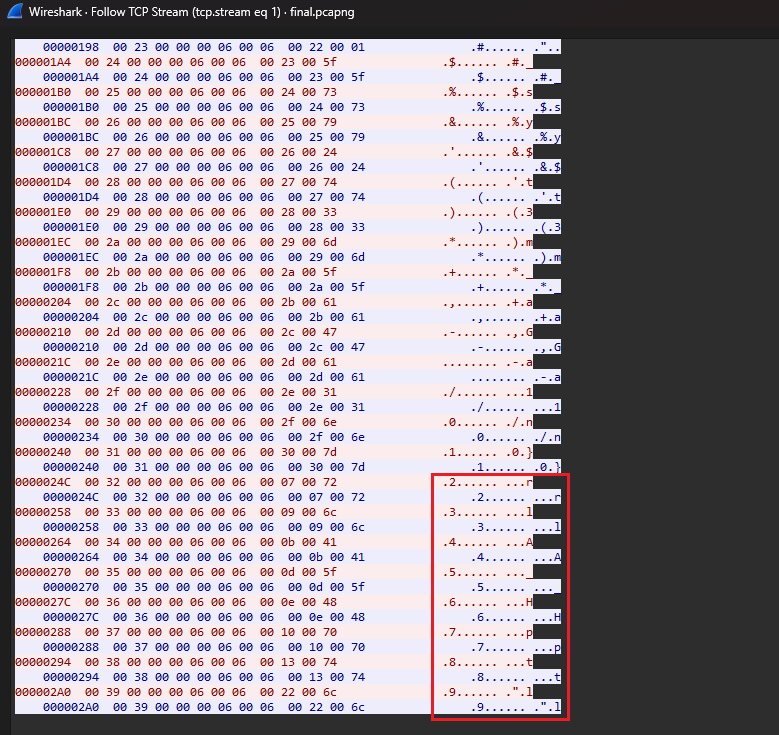
We are given a pcap file to investigate. Inside the pcap, several Modbus packets can be found being transmitted. Checking the TCP stream, the flag can actually be seen broken into several pieces on TCP stream 1.
Unfortunately, I could not solve this before the CTF ended. However, I found out that in between the flag parts were blank spaces. These blank spaces were actually letters from the bottom of the TCP stream. So just place the other letters according to the number. PS: they spelt really wrong.
insecure-creds [Forensics]
Question: Sometimes forensics analysts need to use similar techniques as attackers to complete their investigation.
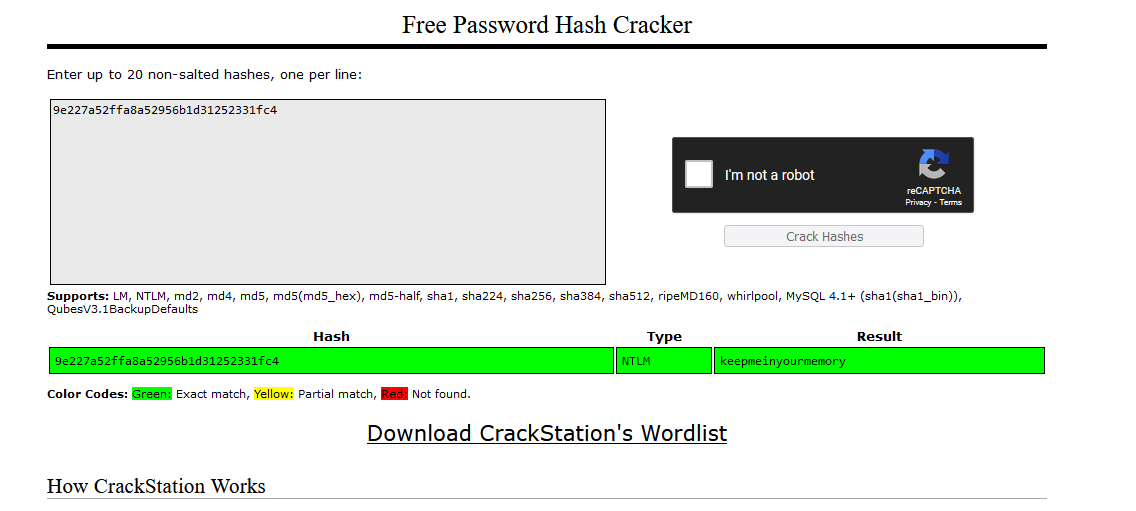
Flag: jctf{keepmeinyourmemory}
We are given a DMP file, specifically a Mini DuMP crash report to investigate. Despite being a hard challenge, I found the flag pretty quickly. Reading the question, it mentions something about credentials. So I read online on cracking DMP files to obtain credentials and stumbled upon this blog and this blog. Basically, we can use a tool called PyPyKatz or mimikatz to dump credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
└─$ pypykatz lsa minidump insecure-creds.DMP
INFO:pypykatz:Parsing file insecure-creds.DMP
FILE: ======== insecure-creds.DMP =======
== LogonSession ==
authentication_id 121929 (1dc49)
session_id 1
username student
domainname DESKTOP-KR3TGUV
logon_server DESKTOP-KR3TGUV
logon_time 2024-02-16T13:00:48.480917+00:00
sid S-1-5-21-1773530256-896341905-2831621244-1000
luid 121929
== MSV ==
Username: student
Domain: .
LM: NA
NT: 9e227a52ffa8a52956b1d31252331fc4
SHA1: 54f1240ef3b3960f3e6bd44aca2f9c83c9898406
DPAPI: 54f1240ef3b3960f3e6bd44aca2f9c83
---SNIP--