ISITDTU CTF 2024 (Quals) - Writeups
This is a writeup for an OSINT challenge from ISITDTU CTF 2024 (Quals). Unfortunately, L3ak did not manage to qualify for the final round. But I still did this writeup to showcase an interesting OSINT challenge that we encountered in this CTF.
Two Steps Ahead [OSINT]
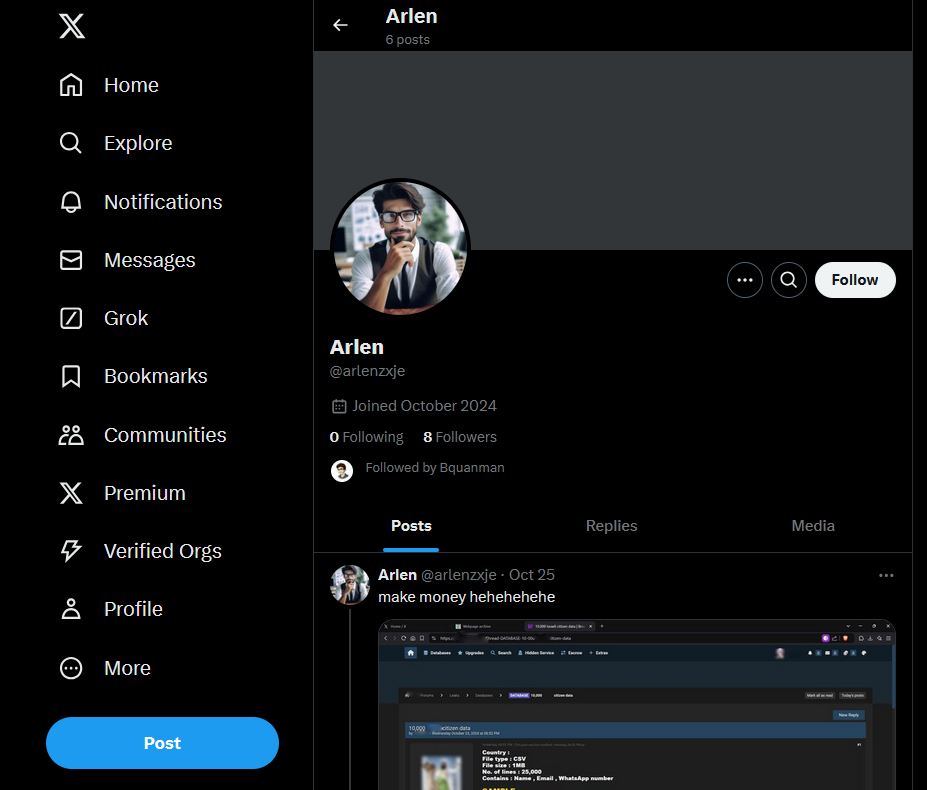
Question: An elusive individual using the alias “arlenzxje” has stolen highly sensitive information from a major company. From our initial investigation, we’ve discovered that he is addicted to social media. Your mission is to track his online footprint and recover the stolen information.
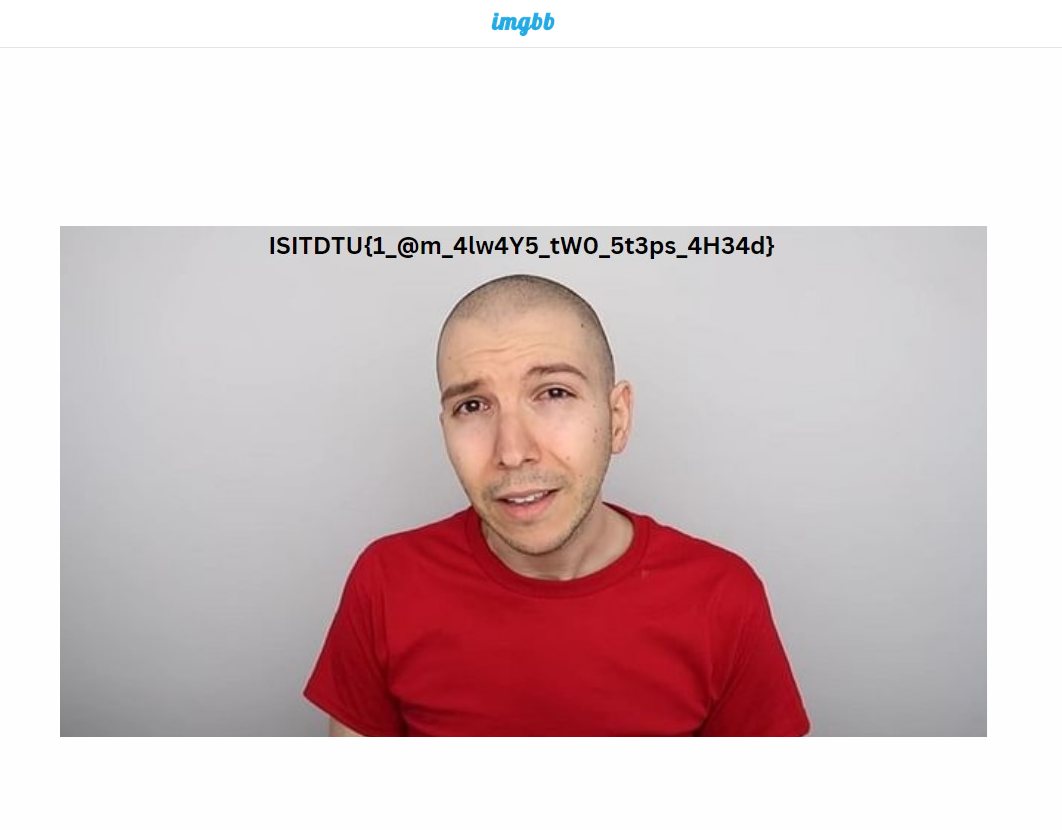
Flag: ISITDU(1_@m_4lw4Y5_tW0_5t3ps_4H34d}
We are tasked to find information about a user with this alias arlenzxje. Searching his alias online, we can identify his X account.
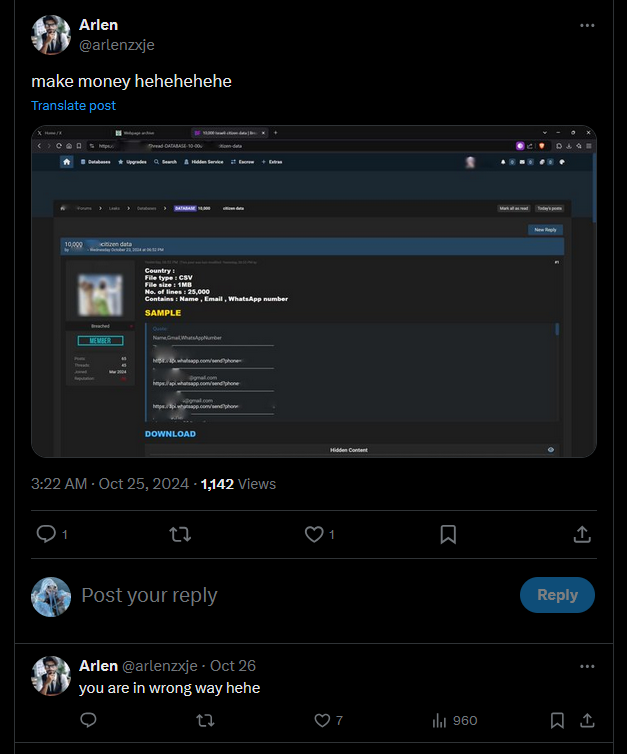
One of his post mentioned a BreachForums post about data leaks, however, it was a red herring according to the author.
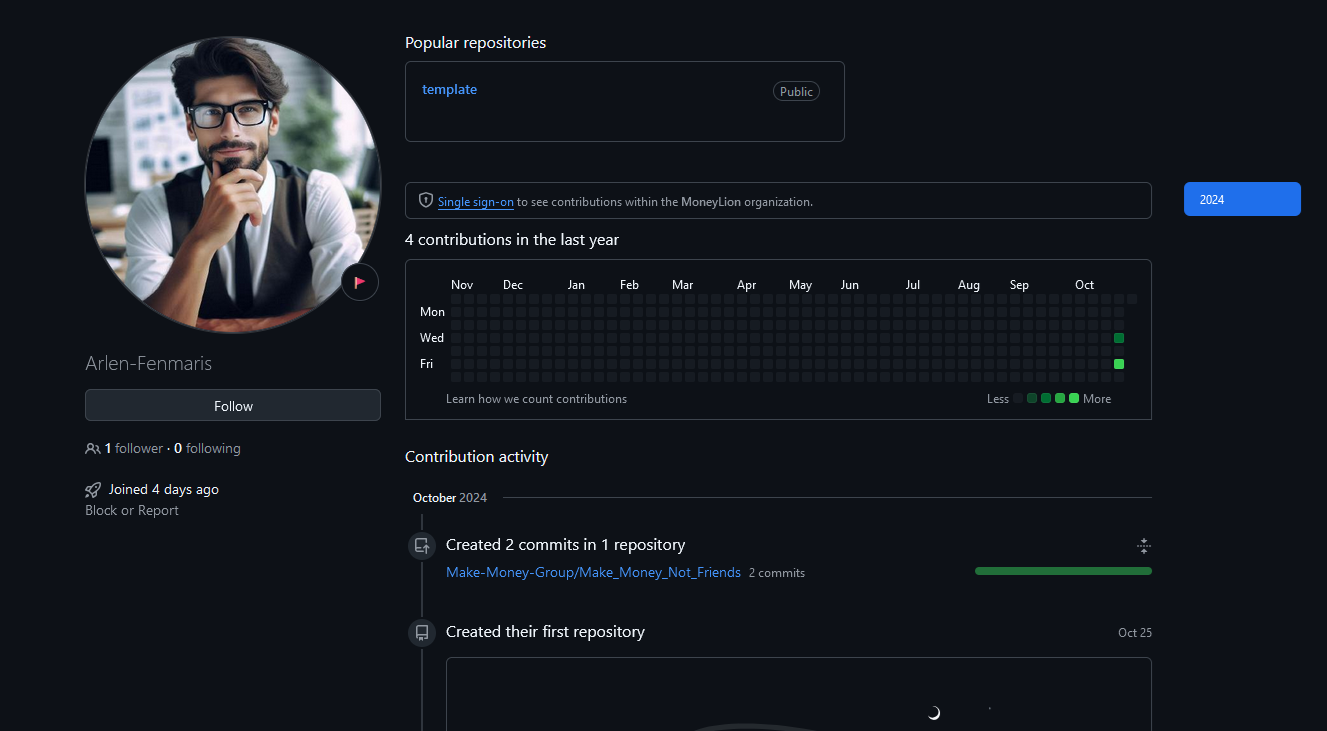
Searching his alias online further, we can identify his GitHub account.
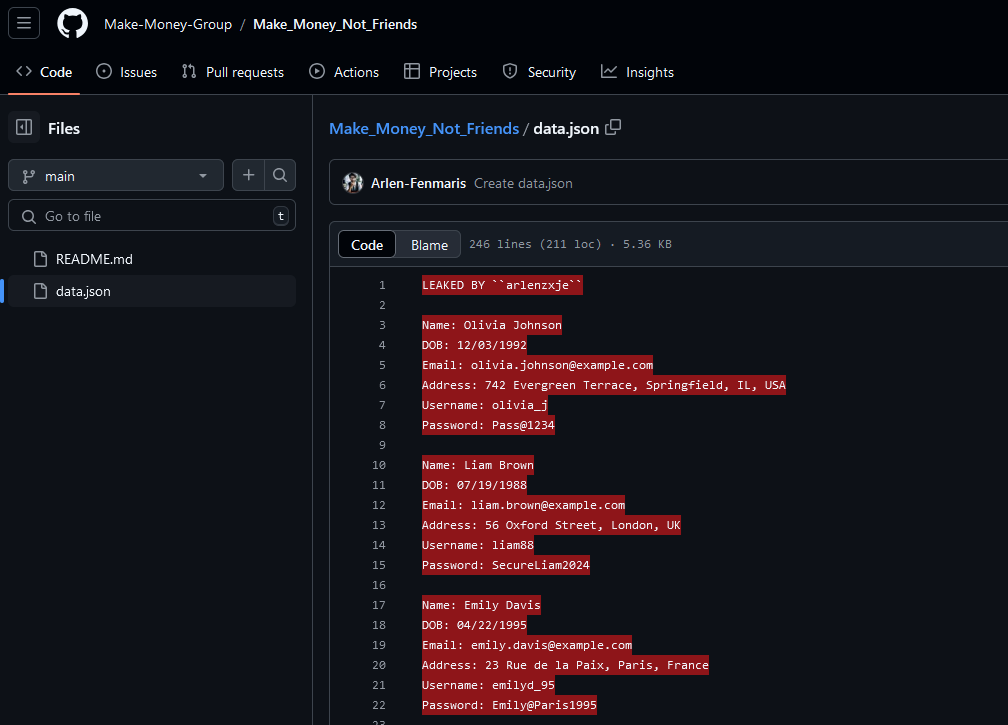
Looking at his commits, we can see a repository Make_Money_Not_Friends was modified. Checking the commit history, it seems to be a leaked public database. However, there were no signs of the flag.
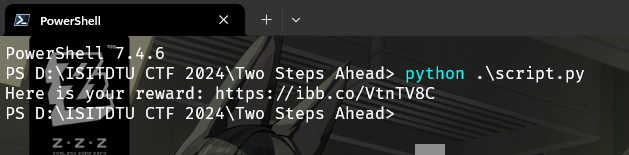
Going through his public gist, there was a script called script.py that was just performing XOR to generate a URL to a Rick Roll video.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
def xor_encrypt_decrypt(data, key):
if isinstance(data, str):
data = data.encode('utf-8')
if isinstance(key, str):
key = key.encode('utf-8')
decrypted_data = bytearray()
key_length = len(key)
for i in range(len(data)):
decrypted_data.append(data[i] ^ key[i % key_length])
return decrypted_data
# Example usage
encrypted = b'\x00\x15\x06\x14\x18_VG\x08\x10\x06E\x06\x16G7\x06\n?3A+'
key = "hardkey"
decoded = xor_encrypt_decrypt(encrypted, key)
print(f"Here is your reward: {decoded.decode('utf-8')}")
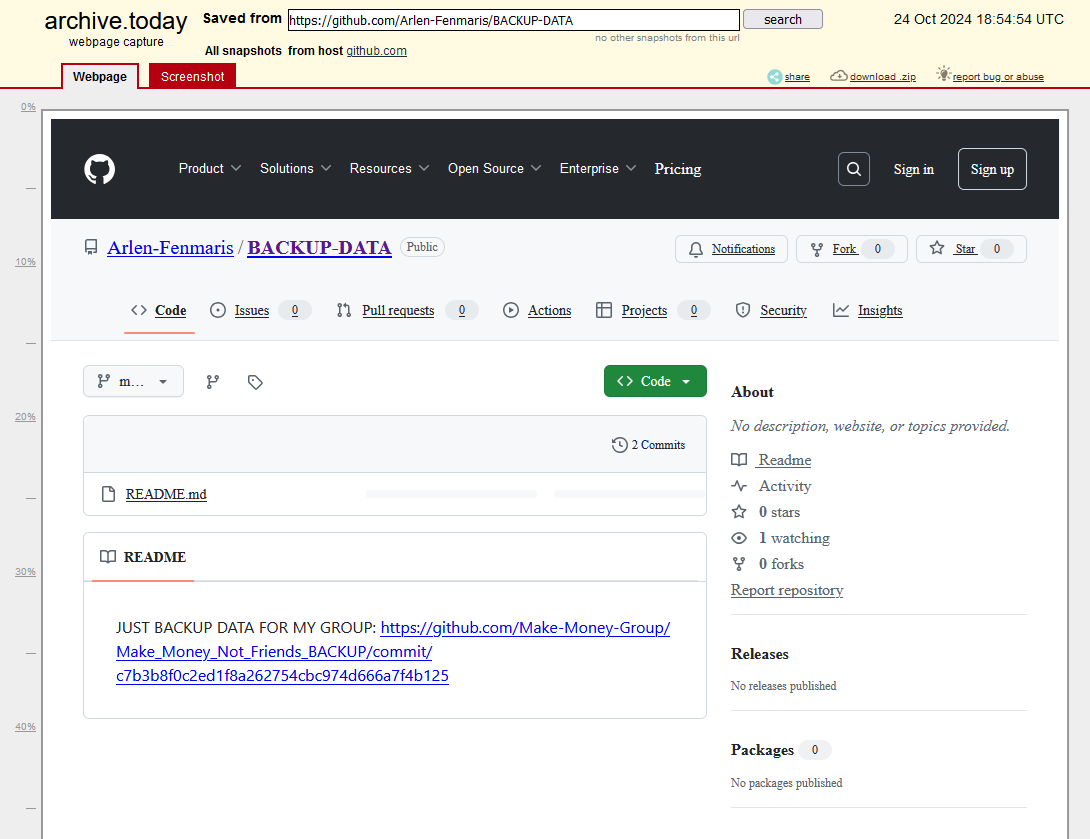
After a few hours, I managed to find something interesting in the previous repository using archive.ph.
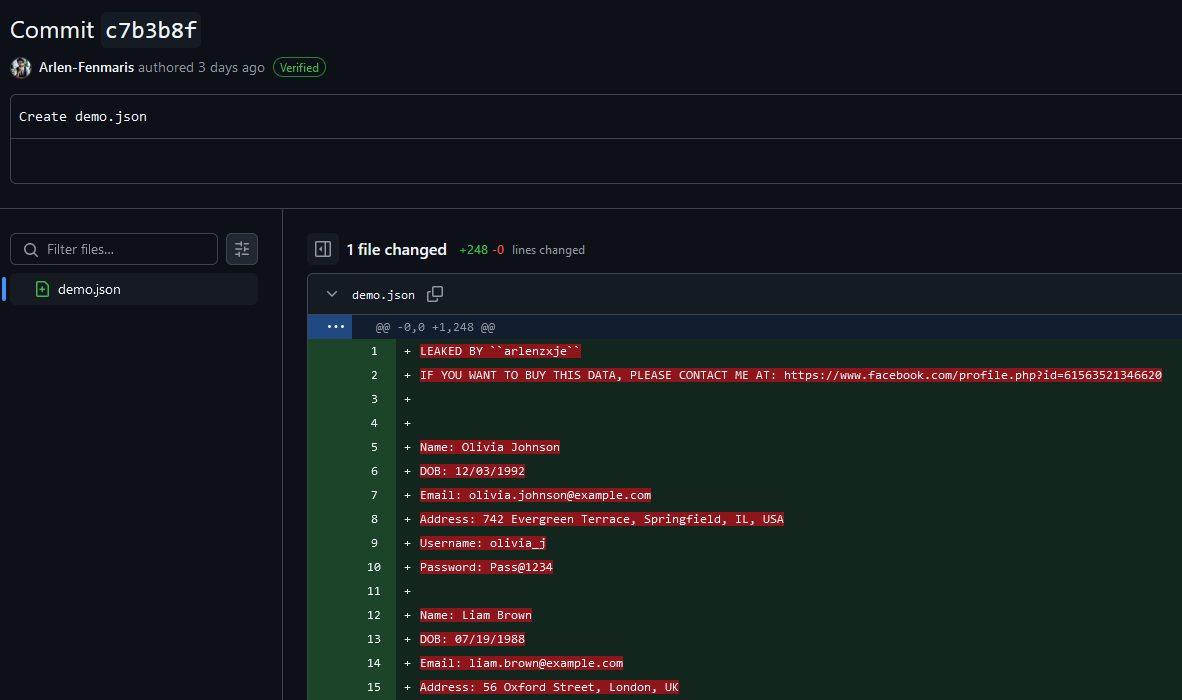
The archive snapshot shows another link that redirects to a hidden commit. Inside the hidden commit was a line that mentioned his Facebook profile.
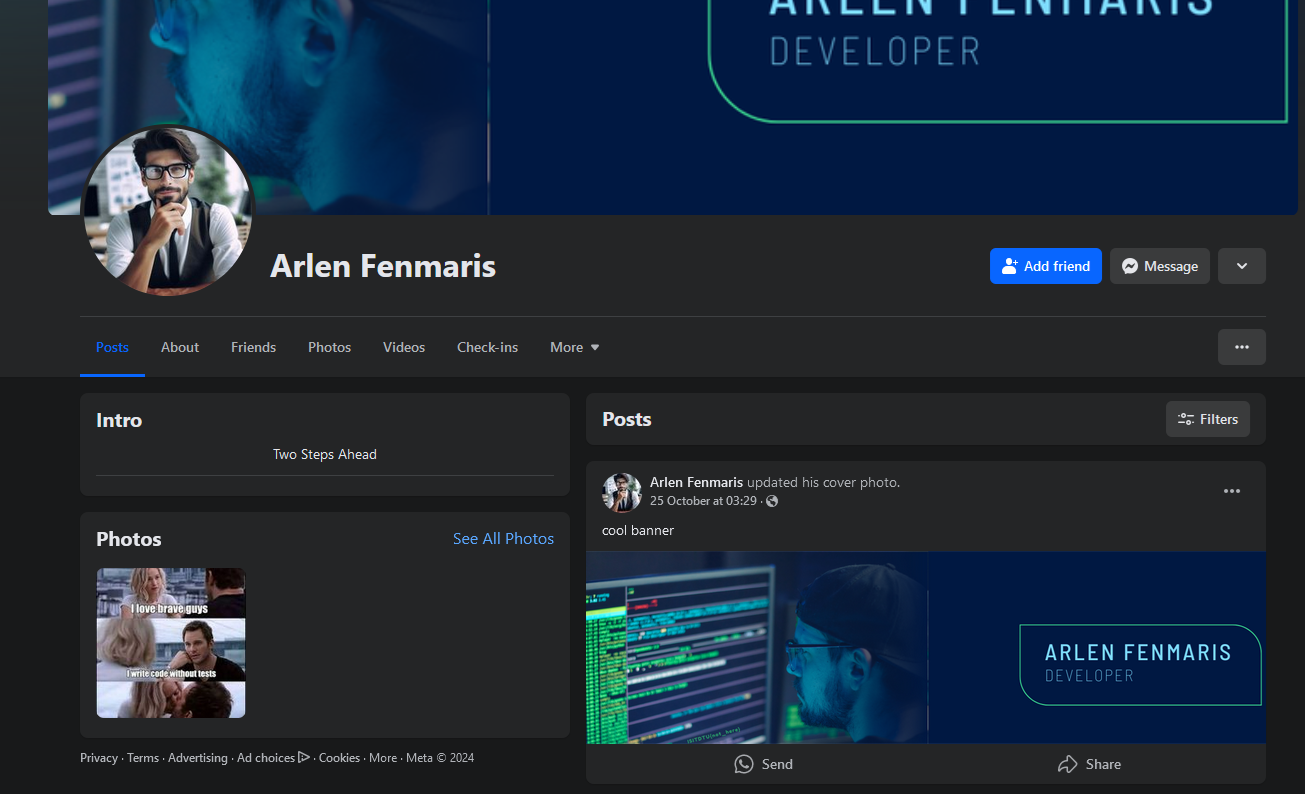
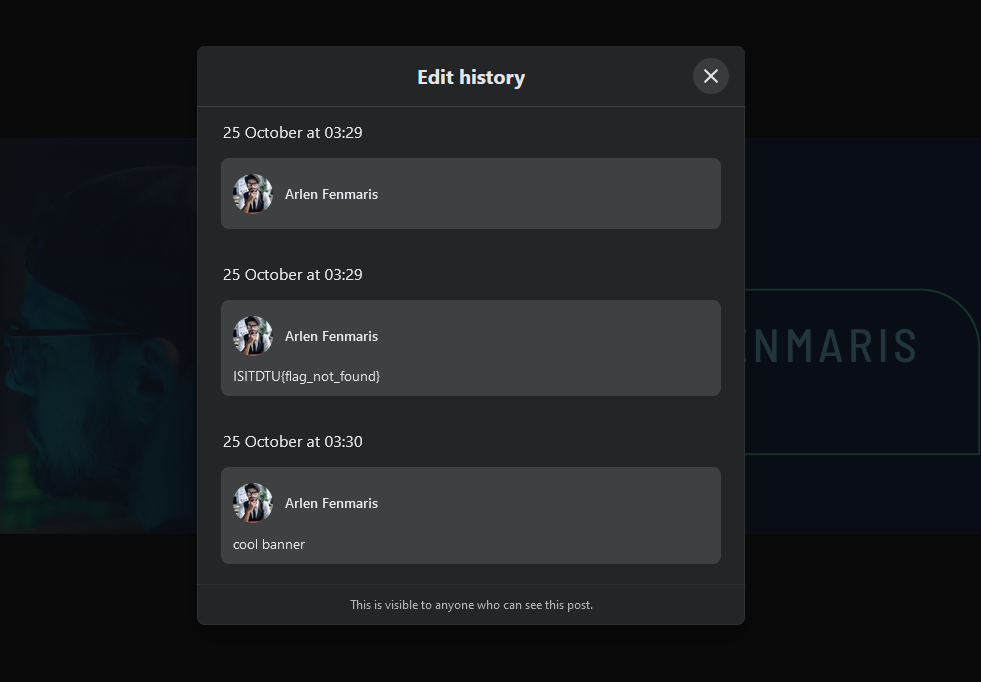
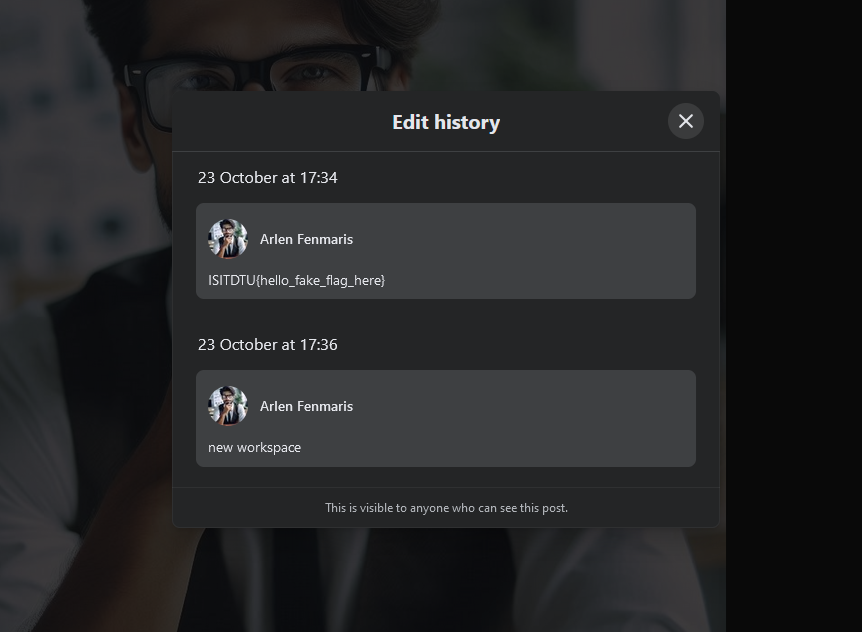
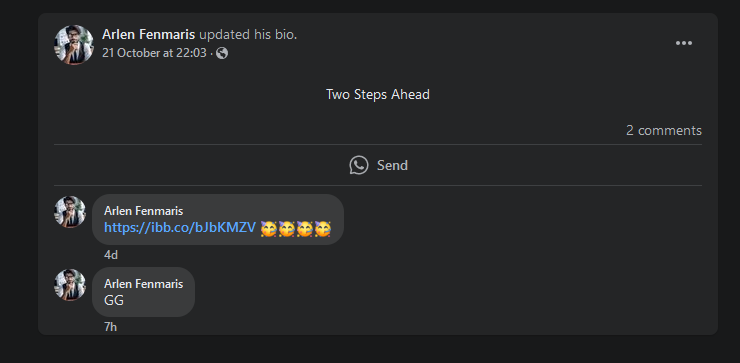
Analyzing his Facebook profile, several fake flags can be identified.
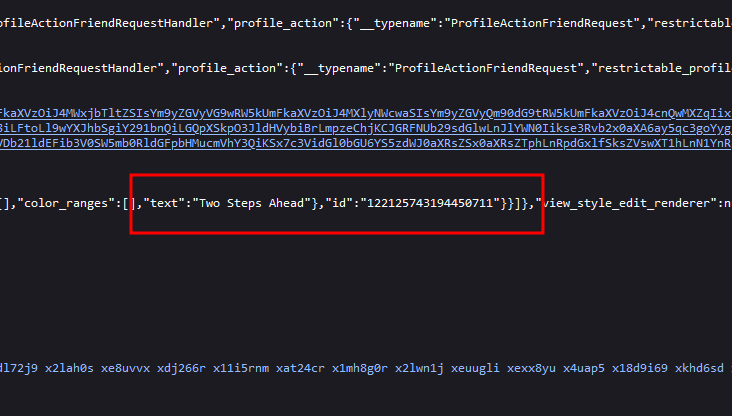
Unfortunately I could not solve this before the CTF ended, but I still attempted it since I know I was close. Here it became interesting, it seems that you can actually extract the post ID from the website element to view hidden comments under the post (in this case, it was his profile bio).