IrisCTF 2025 - Writeups
This is a writeup for some forensics challenges from IrisCTF 2025. Overall, a great CTF but it was not as enjoyable as the previous years. This might be because most challenges were created by a single person, I guess it’s time to increase manpower in the team.
deldeldel [Forensics]
Question: I managed to log more than just keys… perhaps it was too much data to capture?
Flag: irisctf{this_keylogger_is_too_hard_to_use}
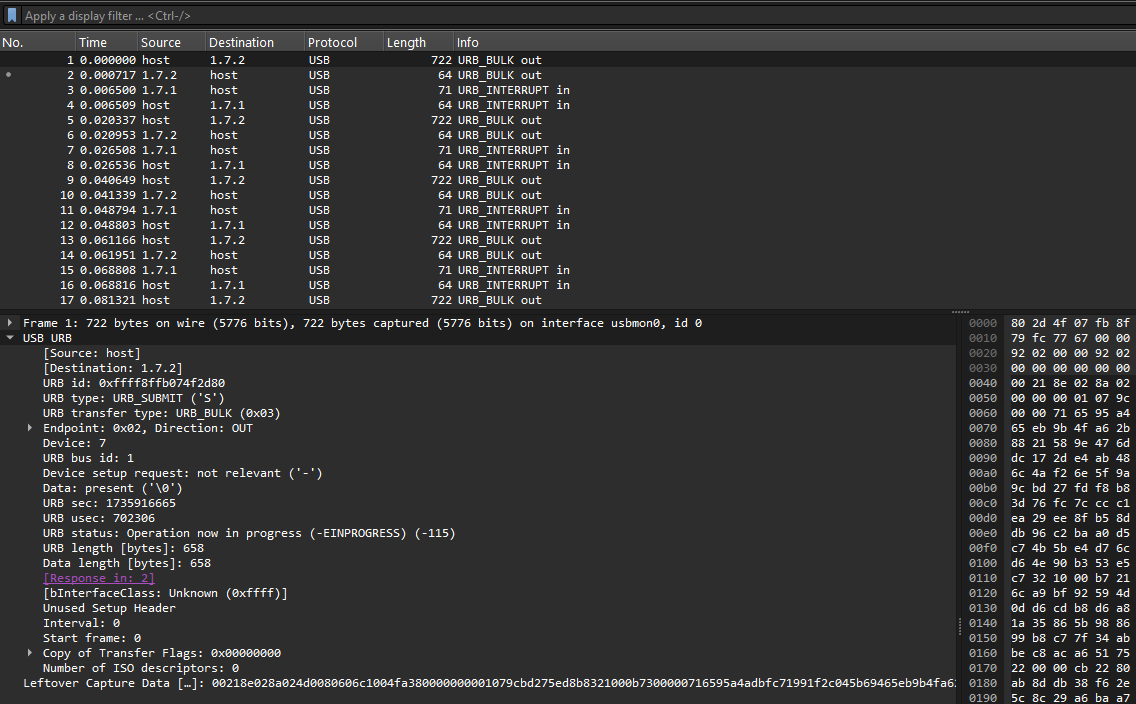
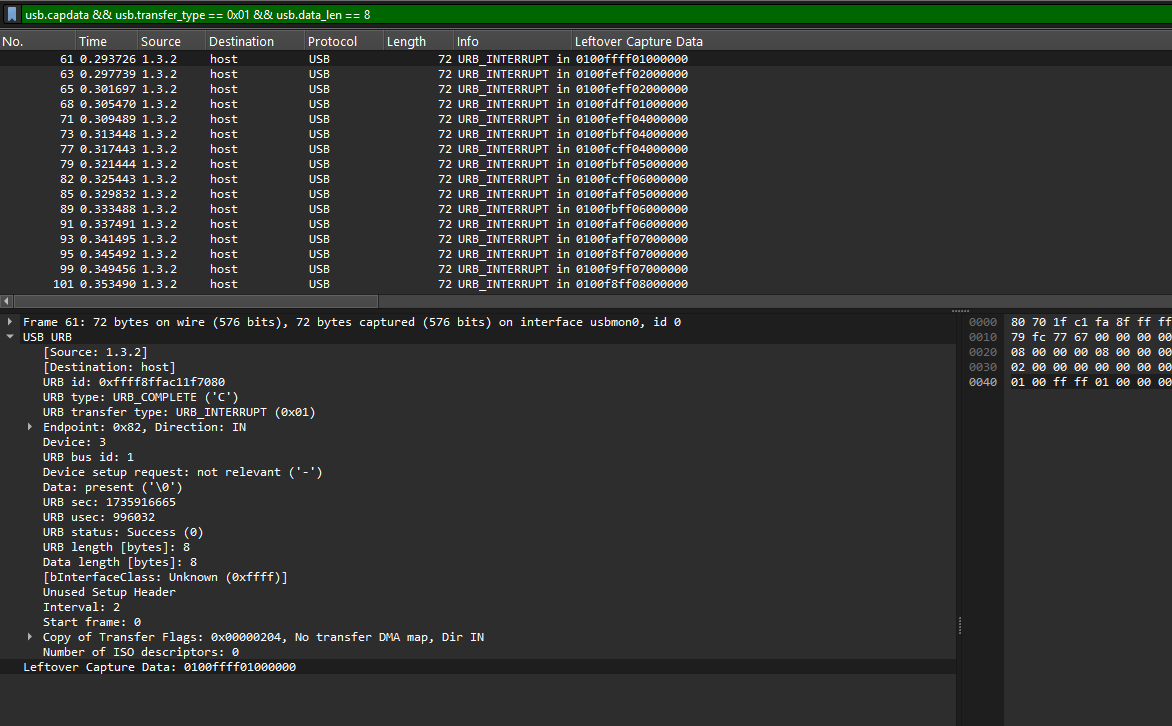
We are given a PCAP file to investigate. Analyzing it, a stream of USB packets can be identified.
Looking at the Leftover Capture Data from 1.3.2, there will be a series of 8 bytes strung together. This suggest that the communicating device was most likely a USB keyboard.
Using an online USB keyboard parser, the flag can be obtained.
1
2
3
4
5
6
7
8
└─$ python3 Usb_Keyboard_Parser.py klogger.pcapng
[-] Found Modifier in 310 packets [-]
[+] Using filter "usb.capdata" Retrived HID Data is :
Hheey AAalicce! Ii tthink Ii''m ssupppooseed too giivee yoou tiss fllaag:
iriisctfF{[tthis_akeyloggeer_iisS_too_hard_to_use}
Windy Day [Forensics]
Question: I have really bad memory. I was analyzing something but then lost track of an important note…
Flag: irisctf{i_am_an_idiot_with_bad_memory}
We are given a memory dump to investigate. Analyzing the processes, multiple Firefox processes can be identified.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
└─$ python3 vol.py -f ~/Desktop/IrisCTF2025/memdump.mem windows.pstree
Volatility 3 Framework 2.14.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
---SNIP---
3036 4060 firefox.exe 0xe38cb818b500 89 - 1 True 2025-01-03 16:55:40.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -first-startup C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 3968 3036 firefox.exe 0xe38cb75b9080 22 - 1 True 2025-01-03 16:55:41.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20241209150345 -prefsHandle 2064 -prefsLen 23966 -prefMapHandle 2068 -prefMapSize 263663 -ipcHandle 2132 -initialChannelId {ac4e74d0-1792-4a52-83e7-7d095d688095} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 1 gpu C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 3328 3036 firefox.exe 0xe38cbb8c6800 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 12020 -prefsLen 39119 -prefMapHandle 12012 -prefMapSize 263663 -jsInitHandle 9276 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 12076 -initialChannelId {0ae8e86b-8dde-4774-9c69-446879aaf7a8} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 103 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2308 3036 firefox.exe 0xe38cbbb44080 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 13244 -prefsLen 39119 -prefMapHandle 4148 -prefMapSize 263663 -jsInitHandle 3652 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 6228 -initialChannelId {969760e2-8126-41a6-84ff-39f0c89da2c0} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 101 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2712 3036 firefox.exe 0xe38cbba16080 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 18080 -prefsLen 39119 -prefMapHandle 13800 -prefMapSize 263663 -jsInitHandle 18408 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 10416 -initialChannelId {1b029914-ad72-442c-984d-374bc0679a74} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 102 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 4508 3036 firefox.exe 0xe38cbbbe8800 19 - 1 True 2025-01-03 17:09:59.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 8980 -prefsLen 39119 -prefMapHandle 14468 -prefMapSize 263663 -jsInitHandle 13356 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 12824 -initialChannelId {4658bbab-d041-445a-a6b2-07d6c88e0183} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 108 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 5664 3036 firefox.exe 0xe38cbb7c9080 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 14088 -prefsLen 39119 -prefMapHandle 13264 -prefMapSize 263663 -jsInitHandle 13124 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 13644 -initialChannelId {3cfd96f5-3c6d-4cad-ae54-839219559465} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 106 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 928 3036 firefox.exe 0xe38cbbc8c080 19 - 1 True 2025-01-03 17:10:00.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 15528 -prefsLen 39119 -prefMapHandle 14956 -prefMapSize 263663 -jsInitHandle 14964 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 5716 -initialChannelId {8b195931-6f5a-4ac8-b8c6-ce7ced96ebe9} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 111 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 4772 3036 firefox.exe 0xe38cbb0d6300 18 - 1 True 2025-01-03 16:57:38.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 3152 -prefsLen 38578 -prefMapHandle 5656 -prefMapSize 263663 -jsInitHandle 3848 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 3292 -initialChannelId {7272d1b7-f244-4b2c-b7b4-8e80c28490f4} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 16 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 3624 3036 firefox.exe 0xe38cbb380080 5 - 1 True 2025-01-03 16:55:41.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20241209150345 -prefsHandle 2400 -prefsLen 24011 -prefMapHandle 2404 -prefMapSize 263663 -ipcHandle 2412 -initialChannelId {098f1298-fdd9-4dea-be71-d90b993c7ab0} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -win32kLockedDown -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 2 socket C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 5288 3036 firefox.exe 0xe38cbb8a9800 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 12808 -prefsLen 39119 -prefMapHandle 17300 -prefMapSize 263663 -jsInitHandle 13876 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 13348 -initialChannelId {86b1b033-8b78-4ca9-a67e-034d4fc7ed79} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 105 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 5804 3036 firefox.exe 0xe38cbb261080 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 7276 -prefsLen 39119 -prefMapHandle 12280 -prefMapSize 263663 -jsInitHandle 11828 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 20016 -initialChannelId {d1eed9b1-cec0-453e-9987-9f933850762c} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 100 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 5044 3036 firefox.exe 0xe38cbb7c8800 5 - 1 True 2025-01-03 16:56:43.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20241209150345 -sandboxingKind 1 -prefsHandle 6212 -prefsLen 41863 -prefMapHandle 6216 -prefMapSize 263663 -ipcHandle 6224 -initialChannelId {161e8909-da24-4286-ad7a-be388785c626} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 13 utility C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 3124 3036 firefox.exe 0xe38cbbca0080 19 - 1 True 2025-01-03 17:10:01.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 11976 -prefsLen 39119 -prefMapHandle 11980 -prefMapSize 263663 -jsInitHandle 11984 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 11384 -initialChannelId {3910a84f-9ad2-41c0-aee2-812e7856118d} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 115 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 3132 3036 firefox.exe 0xe38cbb1e1080 5 - 1 True 2025-01-03 16:55:47.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20241209150345 -sandboxingKind 0 -prefsHandle 2780 -prefsLen 35947 -prefMapHandle 5080 -prefMapSize 263663 -ipcHandle 5104 -initialChannelId {afa7d2a4-dfb6-46e5-968d-78ee98e7d2ac} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 8 utility C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 5324 3036 firefox.exe 0xe38cbba94080 19 - 1 True 2025-01-03 17:09:52.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 12280 -prefsLen 39119 -prefMapHandle 11828 -prefMapSize 263663 -jsInitHandle 7292 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 10604 -initialChannelId {17833eda-a5c3-4134-b9bf-771b9952c871} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 98 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 5196 3036 firefox.exe 0xe38cbb8c0800 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 19588 -prefsLen 39119 -prefMapHandle 19704 -prefMapSize 263663 -jsInitHandle 15784 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 19720 -initialChannelId {671a4e9a-9787-44ff-8871-7c229509a918} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 107 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2252 3036 firefox.exe 0xe38cb7e25080 19 - 1 True 2025-01-03 17:10:01.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 19028 -prefsLen 39119 -prefMapHandle 19036 -prefMapSize 263663 -jsInitHandle 15164 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 15156 -initialChannelId {020a0bb9-6a2e-4eb2-9abf-27888cbbf869} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 113 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 7116 3036 firefox.exe 0xe38cb7e32680 19 - 1 True 2025-01-03 17:10:01.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 7060 -prefsLen 39119 -prefMapHandle 1508 -prefMapSize 263663 -jsInitHandle 9720 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 11644 -initialChannelId {5405565b-6d17-4686-8281-5b8da8253037} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 116 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 740 3036 firefox.exe 0xe38cbb89e400 19 - 1 True 2025-01-03 17:10:01.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 19004 -prefsLen 39119 -prefMapHandle 19008 -prefMapSize 263663 -jsInitHandle 15156 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 19052 -initialChannelId {a41f0b61-d64b-409c-888b-27aca3c33138} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 112 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2920 3036 firefox.exe 0xe38cbbc9e080 19 - 1 True 2025-01-03 17:10:01.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 18608 -prefsLen 39119 -prefMapHandle 14696 -prefMapSize 263663 -jsInitHandle 18632 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 8816 -initialChannelId {d24fb81b-2086-4b26-9361-d9767e8de3b6} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 114 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 4076 3036 firefox.exe 0xe38cbb116080 17 - 1 True 2025-01-03 16:55:45.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4144 -prefsLen 27390 -prefMapHandle 4148 -prefMapSize 263663 -jsInitHandle 4152 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 4160 -initialChannelId {6305bab3-d270-490e-b5e2-823fb8b72509} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 6 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 6256 3036 firefox.exe 0xe38cbb884800 19 - 1 True 2025-01-03 17:09:56.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 12804 -prefsLen 39119 -prefMapHandle 12784 -prefMapSize 263663 -jsInitHandle 12876 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 12864 -initialChannelId {f00479ad-5d51-430e-9b2e-befaea83ff66} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 104 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 2420 3036 firefox.exe 0xe38cbb711800 5 - 1 True 2025-01-03 16:55:44.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20241209150345 -prefsHandle 1404 -prefsLen 26988 -prefMapHandle 1368 -prefMapSize 263663 -ipcHandle 3040 -initialChannelId {f2ec1d05-e313-4442-a153-486d573136db} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 5 rdd C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 3828 3036 firefox.exe 0xe38cbb539800 17 - 1 True 2025-01-03 16:55:43.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 3472 -prefsLen 25398 -prefMapHandle 3476 -prefMapSize 263663 -jsInitHandle 3480 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 3488 -initialChannelId {8ce303c2-1040-44ba-886e-1a582fe4f34b} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 4 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
* 4344 3036 firefox.exe 0xe38cbbbb8080 19 - 1 True 2025-01-03 17:10:00.000000 UTC N/A \Device\HarddiskVolume4\Program Files (x86)\Mozilla Firefox\firefox.exe "C:\Program Files (x86)\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 9284 -prefsLen 39119 -prefMapHandle 12012 -prefMapSize 263663 -jsInitHandle 18072 -jsInitLen 234660 -parentBuildID 20241209150345 -ipcHandle 15348 -initialChannelId {a793a13f-fee2-4cba-a9bf-1d4b92760a59} -parentPid 3036 -crashReporter "\\.\pipe\gecko-crash-server-pipe.3036" -appDir "C:\Program Files (x86)\Mozilla Firefox\browser" - 110 tab C:\Program Files (x86)\Mozilla Firefox\firefox.exe
---SNIP---
Dumping the Firefox process and analyzing for the base64 string of irisctf, the flag can be obtained.
1
2
3
4
5
6
└─$ strings pid.3036.dmp | grep -iE "aXJpc2N0Z"
---SNIP---
aXJpc2N0ZntpX2FtX2FuX2lkaW90X3dpdGhfYmFkX21lbW9yeX0=
https://www.google.com/complete/search?client=firefox&channel=fen&q=aXJpc2N0ZntpX2FtX2FuX2lkaW90X3dpdGhfYmFkX21lbW9yeX0%3D
https://www.google.com/complete/search?client=firefox&channel=fen&q=aXJpc2N0ZntpX2FtX2FuX2lkaW90X3dpdGhfYmFkX21lbW9yeX0%3D
1
2
└─$ echo "aXJpc2N0ZntpX2FtX2FuX2lkaW90X3dpdGhfYmFkX21lbW9yeX0=" | base64 -d
irisctf{i_am_an_idiot_with_bad_memory}
PS: Since the vol2 clipboard plugin was not working with the memory dump due to profile issues, I had to solve it unintendedly.
Tracem 1 [Forensics]
Question: Here at EI Corp, ethics are our top priority! That’s why our IT team was shocked when we got a knock from our ISP informing us that someone on our computer network was involved in some illegitimate activity. Who would do that? Don’t they know that’s illegal? Our ISP’s knocking (and so is HR), and we need someone to hold accountable. Can you find out who committed this violation?
Flag: irisctf{llloyd}
We are given a JSON log to investigate. Skimming through the logs, the main logs seem to be DNS, DHCP, syslog (RADIUS and SSO) and Active Directory.
1
2
3
4
5
└─$ jq -r '.sourcetype' logs.json | sort | uniq -c | sort -nr
399100 stream:dns
108592 stream:dhcp
15541 syslog
15 ActiveDirectory
Since there were DNS logs, I wanted to identify what kind of illegal website was accessed by the user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ jq -r '.data.queries[]?.name // empty' logs.json | sort | uniq -c | sort -nr
---SNIP---
14 bigcommerce.com
14 asus.com
14 aftermarket.pl
10 bp0.blogger.com
8 vanityfair.com
6 justgiving.com
6 g.co
6 deloitte.com
4 slate.com
4 as.com
2 welt.de
2 breachforums.st
2 bmj.com
1 smith-wesson.com
1 copious-amounts-of-illicit-substances-marketplace.com
Seems like the illegal website was literally called copious-amounts-of-illicit-substances-marketplace.com. Using this illegal website as a keyword, the IP 10.33.18.209 seems to be the user.
1
2
3
└─$ strings logs.json | grep "copious-amounts-of-illicit-substances-marketplace.com"
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 06:30:18.99", "data": {"timestamp": "2024-12-04 06:30:18.347812", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.33.18.209", "src_port": 7419, "dest_ip": "10.33.0.2", "dest_port": 53, "transaction_id": 45042, "queries": [{"type": "A", "class": "IN", "name": "copious-amounts-of-illicit-substances-marketplace.com"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 06:30:19.21", "data": {"timestamp": "2024-12-04 06:30:18.572830", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.33.0.2", "src_port": 53, "dest_ip": "10.33.18.209", "dest_port": 7419, "transaction_id": 45042, "answers": [{"type": "A", "class": "IN", "name": "copious-amounts-of-illicit-substances-marketplace.com", "addr": "104.16.148.244"}]}}
With the IP, it was pretty simple to identify the user to be llloyd from the SSO logs.
1
2
└─$ strings logs.json | grep "10.33.18.209" | grep https
{"host": "primary", "source": "udp:514", "sourcetype": "syslog", "_time": "2024-12-04 04:58:36.95", "data": {"_raw": "2024-12-04 04:58:35.622504||https://sso.evil-insurance.corp/idp/profile/SAML2/Redirect/SSO|/idp/profile/SAML2/Redirect/SSO|5b52053ac1ab1f4935a3d7d6c6aa4ff0|authn/MFA|10.33.18.209|Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3 Edge/16.16299|https://sso.evil-insurance.corp/ns/profiles/saml2/sso/browser|llloyd||uid|service.evil-insurance.corp|https://sso.evil-insurance.corp/idp/sso|url:oasis:names:tc:SAML:2.0:protocol|urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect|urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST|kzYQV+Jk2w3KkwmRjR+HK4QWVQ3qzLPLgA5klV2b8bQT+NLYLeqCZw5xUGKbx1U1158jlnUYRrILtVTtMkMdbA==|urn:oasis:names:tc:SAML:2.0:nameid-format:transient|_60b0fd4b0ed5bba3474faeb85b3944e|2024-12-04 04:58:35.622504|_c4b56d58-625b-49aa-b859-4a2068422979||||urn:oasis:names:tc:SAML:2.0:status:Success|||false|false|true", "timestamp": "2024-12-04 04:58:35.622504", "NLYLeqCZw5xUGKbx1U1158jlnUYRrILtVTtMkMdbA": "=|urn:oasis:names:tc:SAML:2.0:nameid-format:transient|_60b0fd4b0ed5bba3474faeb85b3944e|2024-12-04"}}
Tracem 2 [Forensics]
Question: Another knock from our ISP and HR looking for a John Doe… but now it’s not so easy.
Flag: irisctf{mhammond}
We are given a JSON log to investigate. Skimming through the logs, the main logs seem to be DNS, DHCP, syslog (RADIUS and SSO) and Active Directory.
1
2
3
4
5
└─$ jq -r '.sourcetype' logs.json | sort | uniq -c | sort -nr
251244 stream:dns
71018 stream:dhcp
10068 syslog
12 ActiveDirectory
Similarly, I used the same jq query to identify the name of the illegal website accessed by the user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
└─$ jq -r '.data.queries[]?.name // empty' logs.json | sort | uniq -c | sort -nr
---SNIP---
8 feedproxy.google.com
8 as.com
6 xbox.com
6 justgiving.com
4 vanityfair.com
2 ubuntu.com
2 thepiratebay.org
2 lexpress.fr
2 generic-illicit-activities-hub.org
2 deloitte.com
2 bp0.blogger.com
2 bmj.com
Seems like the illegal website was literally called generic-illicit-activities-hub.org. Using this illegal website as a keyword, the IP 10.18.21.121 seems to be the user.
1
2
3
4
5
└─$ strings logs.json | grep "generic-illicit-activities-hub.org"
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:01.12", "data": {"timestamp": "2024-12-04 09:05:00.400067", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 22066, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 2835, "queries": [{"type": "A", "class": "IN", "name": "generic-illicit-activities-hub.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:00.70", "data": {"timestamp": "2024-12-04 09:05:00.520979", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 64559, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 3019, "queries": [{"type": "AAAA", "class": "IN", "name": "generic-illicit-activities-hub.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:01.76", "data": {"timestamp": "2024-12-04 09:05:01.197568", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 22066, "transaction_id": 2835, "answers": [{"type": "A", "class": "IN", "name": "generic-illicit-activities-hub.org", "addr": "96.16.243.221"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:01.72", "data": {"timestamp": "2024-12-04 09:05:01.201187", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 64559, "transaction_id": 3019, "answers": [{"type": "AAAA", "class": "IN", "name": "generic-illicit-activities-hub.org", "addr": null}]}}
However, the IP doesn’t lead to any users since the IP was assigned by a DHCP this time.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
└─$ strings logs.json | grep "10.18.21.121"
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 08:49:20.52", "data": {"timestamp": "2024-12-04 08:49:20.310176", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "de:ad:be:ef:ca:fe", "src_ip": "0.0.0.0", "src_port": 68, "dest_mac": "FF:FF:FF:FF:FF:FF", "dest_ip": "255.255.255.255", "dest_port": 67, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "0.0.0.0", "transaction_id": 1005317175, "opcode": "DHCPREQUEST", "riaddr": "10.18.21.121"}}
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 08:49:21.00", "data": {"timestamp": "2024-12-04 08:49:20.982612", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "EB:A8:B3:FB:A0:AB", "src_ip": "10.18.0.2", "src_port": 67, "dest_mac": "de:ad:be:ef:ca:fe", "dest_ip": "10.18.21.121", "dest_port": 68, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "10.18.21.121", "transaction_id": 1005317175, "opcode": "DHCPACK"}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:49:34.58", "data": {"timestamp": "2024-12-04 08:49:33.772810", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 42110, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 61288, "queries": [{"type": "A", "class": "IN", "name": "www.google.com"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:49:34.58", "data": {"timestamp": "2024-12-04 08:49:33.780002", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 12733, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 25258, "queries": [{"type": "AAAA", "class": "IN", "name": "www.google.com"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:49:34.70", "data": {"timestamp": "2024-12-04 08:49:33.990102", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 42110, "transaction_id": 61288, "answers": [{"type": "A", "class": "IN", "name": "www.google.com", "addr": "142.250.72.68"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:49:34.72", "data": {"timestamp": "2024-12-04 08:49:34.102001", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 12733, "transaction_id": 25258, "answers": [{"type": "AAAA", "class": "IN", "name": "www.google.com", "addr": "2607:f8b0:400f:807::2004"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:18.72", "data": {"timestamp": "2024-12-04 08:51:17.829209", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 18183, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 6754, "queries": [{"type": "A", "class": "IN", "name": "2.arch.pool.ntp.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:18.73", "data": {"timestamp": "2024-12-04 08:51:17.830022", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 4232, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 34487, "queries": [{"type": "AAAA", "class": "IN", "name": "2.arch.pool.ntp.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:18.92", "data": {"timestamp": "2024-12-04 08:51:18.120091", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 18183, "transaction_id": 6754, "answers": [{"type": "A", "class": "IN", "name": "2.arch.pool.ntp.org", "addr": "137.190.2.4"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:18.90", "data": {"timestamp": "2024-12-04 08:51:18.182029", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 4232, "transaction_id": 34487, "answers": [{"type": "AAAA", "class": "IN", "name": "2.arch.pool.ntp.org", "addr": "2607:ff50:0:1a::20"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:51.12", "data": {"timestamp": "2024-12-04 08:51:51.092921", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 48851, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 119, "queries": [{"type": "A", "class": "IN", "name": "thepiratebay.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:51.13", "data": {"timestamp": "2024-12-04 08:51:51.102210", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 2975, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 13007, "queries": [{"type": "AAAA", "class": "IN", "name": "thepiratebay.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:53.22", "data": {"timestamp": "2024-12-04 08:51:52.449001", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 48851, "transaction_id": 119, "answers": [{"type": "A", "class": "IN", "name": "thepiratebay.org", "addr": "104.16.148.244"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 08:51:53.22", "data": {"timestamp": "2024-12-04 08:51:52.450021", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 2975, "transaction_id": 13007, "answers": [{"type": "AAAA", "class": "IN", "name": "thepiratebay.org", "addr": null}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:01.12", "data": {"timestamp": "2024-12-04 09:05:00.400067", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 22066, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 2835, "queries": [{"type": "A", "class": "IN", "name": "generic-illicit-activities-hub.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:00.70", "data": {"timestamp": "2024-12-04 09:05:00.520979", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.21.121", "src_port": 64559, "dest_ip": "10.18.0.2", "dest_port": 53, "transaction_id": 3019, "queries": [{"type": "AAAA", "class": "IN", "name": "generic-illicit-activities-hub.org"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:01.76", "data": {"timestamp": "2024-12-04 09:05:01.197568", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 22066, "transaction_id": 2835, "answers": [{"type": "A", "class": "IN", "name": "generic-illicit-activities-hub.org", "addr": "96.16.243.221"}]}}
{"host": "primary", "source": "stream:dns", "sourcetype": "stream:dns", "_time": "2024-12-04 09:05:01.72", "data": {"timestamp": "2024-12-04 09:05:01.201187", "protocol_stack": "ip:udp:dns", "transport": "udp", "src_ip": "10.18.0.2", "src_port": 53, "dest_ip": "10.18.21.121", "dest_port": 64559, "transaction_id": 3019, "answers": [{"type": "AAAA", "class": "IN", "name": "generic-illicit-activities-hub.org", "addr": null}]}}
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 09:22:01.12", "data": {"timestamp": "2024-12-04 09:22:00.411200", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "de:ad:be:ef:ca:fe", "src_ip": "10.18.21.121", "src_port": 68, "dest_mac": "FF:FF:FF:FF:FF:FF", "dest_ip": "255.255.255.255", "dest_port": 67, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "0.0.0.0", "transaction_id": 2674233379, "opcode": "DHCPRELEASE"}}
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 09:22:01.15", "data": {"timestamp": "2024-12-04 09:22:00.519792", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "EB:A8:B3:FB:A0:AB", "src_ip": "10.18.0.2", "src_port": 67, "dest_mac": "de:ad:be:ef:ca:fe", "dest_ip": "10.18.21.121", "dest_port": 68, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "10.18.21.121", "transaction_id": 2674233379, "opcode": "DHCPACK"}}
I tried to correlate the timestamp with the SSO logins when the DHCP assigned the IP (which is around 2024-12-04 08:49:20.52), but none of the usernames were correct.
Analyzing the DHCP logs again, we can identify the user’s MAC address to be de:ad:be:ef:ca:fe. However, the MAC address seem to only be present in DHCP logs and the DHCP logs show that the IP that was associated with the MAC address was released after accessing the illegal website.
1
2
3
4
5
└─$ strings logs.json | grep "de:ad:be:ef:ca:fe"
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 08:49:20.52", "data": {"timestamp": "2024-12-04 08:49:20.310176", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "de:ad:be:ef:ca:fe", "src_ip": "0.0.0.0", "src_port": 68, "dest_mac": "FF:FF:FF:FF:FF:FF", "dest_ip": "255.255.255.255", "dest_port": 67, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "0.0.0.0", "transaction_id": 1005317175, "opcode": "DHCPREQUEST", "riaddr": "10.18.21.121"}}
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 08:49:21.00", "data": {"timestamp": "2024-12-04 08:49:20.982612", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "EB:A8:B3:FB:A0:AB", "src_ip": "10.18.0.2", "src_port": 67, "dest_mac": "de:ad:be:ef:ca:fe", "dest_ip": "10.18.21.121", "dest_port": 68, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "10.18.21.121", "transaction_id": 1005317175, "opcode": "DHCPACK"}}
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 09:22:01.12", "data": {"timestamp": "2024-12-04 09:22:00.411200", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "de:ad:be:ef:ca:fe", "src_ip": "10.18.21.121", "src_port": 68, "dest_mac": "FF:FF:FF:FF:FF:FF", "dest_ip": "255.255.255.255", "dest_port": 67, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "0.0.0.0", "transaction_id": 2674233379, "opcode": "DHCPRELEASE"}}
{"host": "primary", "source": "stream:dhcp", "sourcetype": "stream:dhcp", "_time": "2024-12-04 09:22:01.15", "data": {"timestamp": "2024-12-04 09:22:00.519792", "protocol_stack": "ip:udp:dhcp", "transport": "udp", "src_mac": "EB:A8:B3:FB:A0:AB", "src_ip": "10.18.0.2", "src_port": 67, "dest_mac": "de:ad:be:ef:ca:fe", "dest_ip": "10.18.21.121", "dest_port": 68, "chaddr": "de:ad:be:ef:ca:fe", "ciaddr": "10.18.21.121", "transaction_id": 2674233379, "opcode": "DHCPACK"}}
Unfortunately I could not solve this before the CTF ended, but I still attempted it since the challenge was pretty interesting. Apparently, the user can be easily suspected to be conducting MAC spoofing due to the lack of reassignments or reusage of the MAC address in the logs. One method from a player was to identify MAC addresses that was assigned 2+ IP addresses, but I feel like this method is non-practical since it is normal to expect a MAC address having 2+ IP addresses.
One writeup that stood out the most was from @Stefan, where his solve method seems the most logical to me. Since the user might have impersonated another user, the DHCP flow from the user’s machine would be DHCPREQUEST > DHCPREQUEST > DHCPRELEASE, indicating that at least 2 IPs were assigned simultaneously to the same MAC address. So a script can be created to identify MAC addresses that have sequential DHCP requests without DHCP releases.
Disclaimer: All credits to @Stefan for creating this awesome script in JavaScript. I just converted the script to Python for simplicity sake.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
import json
with open('logs.json', 'r', encoding='utf-8') as file:
data = file.readlines()
mac_requests = {}
mac_releases = {}
result = []
for linenr, line in enumerate(data, start=1):
try:
log = json.loads(line.strip())
log_data = log.get("data", {})
mac_address = log_data.get("chaddr")
timestamp = log_data.get("timestamp")
requested_ip = log_data.get("riaddr")
current_ip = log_data.get("ciaddr")
opcode = log_data.get("opcode")
if opcode == 'DHCPREQUEST':
if mac_address not in mac_requests:
mac_requests[mac_address] = []
mac_requests[mac_address].append({'requested_ip': requested_ip, 'timestamp': timestamp})
if opcode == 'DHCPRELEASE':
if mac_address not in mac_releases:
mac_releases[mac_address] = []
mac_releases[mac_address].append({'released_ip': current_ip, 'timestamp': timestamp})
except json.JSONDecodeError:
print(f"Error parsing line {linenr}: {line.strip()}")
# Check for sequential requests without releases
for mac, requests in mac_requests.items():
if len(requests) > 1:
for i in range(1, len(requests)):
first_request = requests[i - 1]
second_request = requests[i]
if first_request['requested_ip'] != second_request['requested_ip']:
releases = mac_releases.get(mac, [])
released_ips = [release['released_ip'] for release in releases]
if first_request['requested_ip'] not in released_ips:
result.append(f"Potential spoofing detected for MAC: {mac}. IPs requested: {first_request['requested_ip']} and {second_request['requested_ip']}")
for entry in result:
print(entry)
1
2
3
└─$ python script.py
Potential spoofing detected for MAC: 53:75:56:a7:98:8f. IPs requested: 10.17.161.10 and 10.18.13.187
Potential spoofing detected for MAC: 53:75:56:a7:98:8f. IPs requested: 10.18.13.187 and 10.17.161.10
With the IP, it was pretty simple to identify the user to be mhammond from the SSO logs.
1
2
└─$ strings logs.json | grep "10.17.161.10" | grep https
{"host": "primary", "source": "udp:514", "sourcetype": "syslog", "_time": "2024-12-04 07:42:16.11", "data": {"_raw": "2024-12-04 07:42:16.058355||https://sso.evil-insurance.corp/idp/profile/SAML2/Redirect/SSO|/idp/profile/SAML2/Redirect/SSO|6be5e0fe638be3ae75c3702ae6f3fa91|authn/MFA|10.17.161.10|Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Firefox/53.0.3 Safari/537.3|https://sso.evil-insurance.corp/ns/profiles/saml2/sso/browser|mhammond||uid|gitlab.evil-insurance.corp|https://sso.evil-insurance.corp/idp/sso|url:oasis:names:tc:SAML:2.0:protocol|urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect|urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST|dxjj4bc2qh7nNYCxDufIMJUJgZg7XEC6stCo4dlJwt74i2KuXFbL6Qx3OJEOSOdnvea2zz6oK76KK2/9xWxJ0A==|urn:oasis:names:tc:SAML:2.0:nameid-format:transient|_2b0a5fe78da29cb3c501145bf54e92a5|2024-12-04 07:42:16.058355|_5cee657f-4daf-4b2f-bdaf-9bee0d9bc103||||urn:oasis:names:tc:SAML:2.0:status:Success|||false|false|true", "timestamp": "2024-12-04 07:42:16.058355", "xWxJ0A": "=|urn:oasis:names:tc:SAML:2.0:nameid-format:transient|_2b0a5fe78da29cb3c501145bf54e92a5|2024-12-04"}}