IrisCTF 2024 - Writeups
This is a writeup for some forensics, networking and OSINT challenges from IrisCTF 2024. Overall, the CTF was incredibly enjoyable despite the challenges being exceptionally difficult. However, the realistic nature of these challenges made them a valuable training ground for honing my DFIR skills. During the event, I also had the pleasure of meeting a new friend, @seal, who shares a passion for forensics challenges and creates excellent writeups for them as well.
Not Just Media [Forensics]
Question: I downloaded a video from the internet, but I think I got the wrong subtitles. Note: The flag is all lowercase.
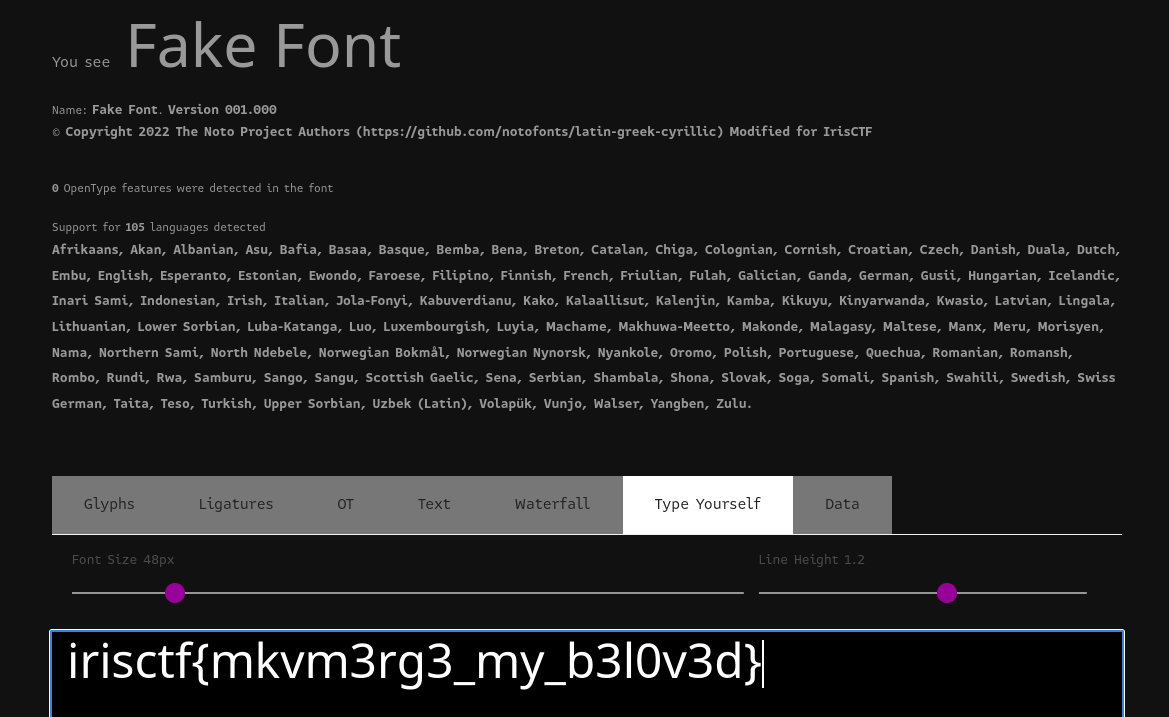
Flag: irisctf{mkvm3rg3_my_b3l0v3d}
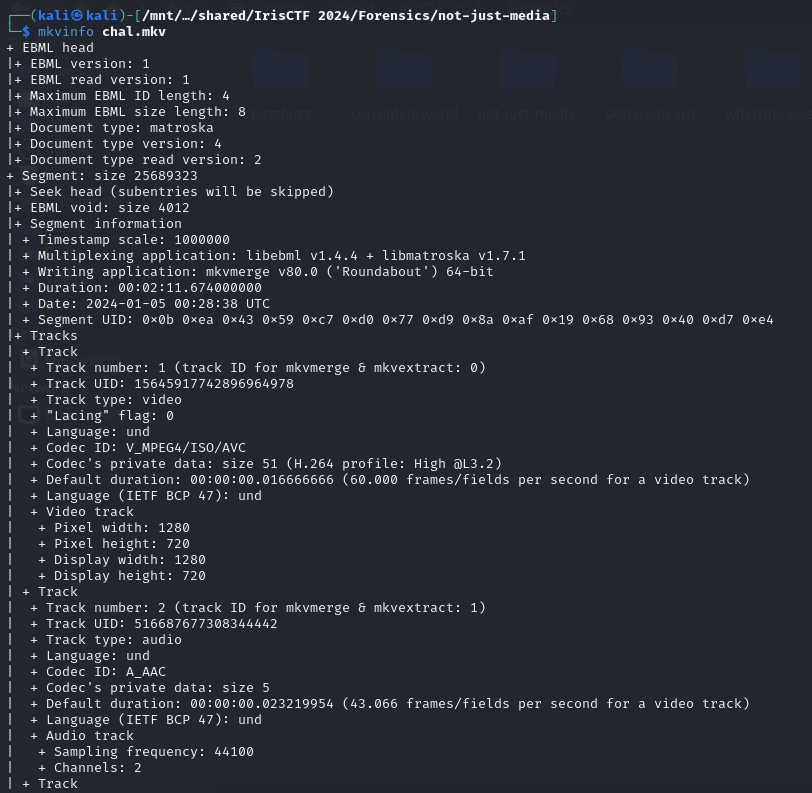
We are given a MKV video file to investigate. Researching online about MKV videos and subtitles, there seems to be a default tool called mkvinfo which was able to list the tracks and subtitles embedded within a MKV video.
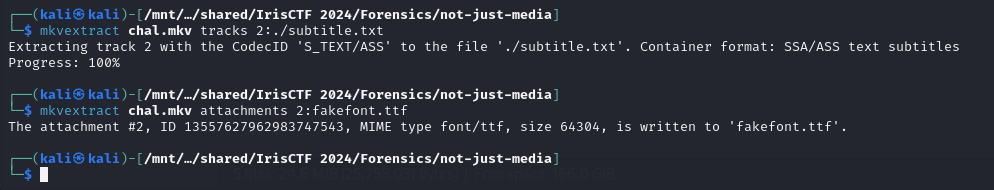
Analyzing the output, the subtitles and a suspicious font file could be extracted from the MKV video.
Combine both files together using fontdrop.io, the flag can be obtained.
skat’s SD card [Forensics]
Question: “Do I love being manager? I love my kids. I love real estate. I love ceramics. I love chocolate. I love computers. I love trains.”
Flag: irisctf{0h_cr4p_ive_left_my_k3ys_out_4nd_ab0ut}
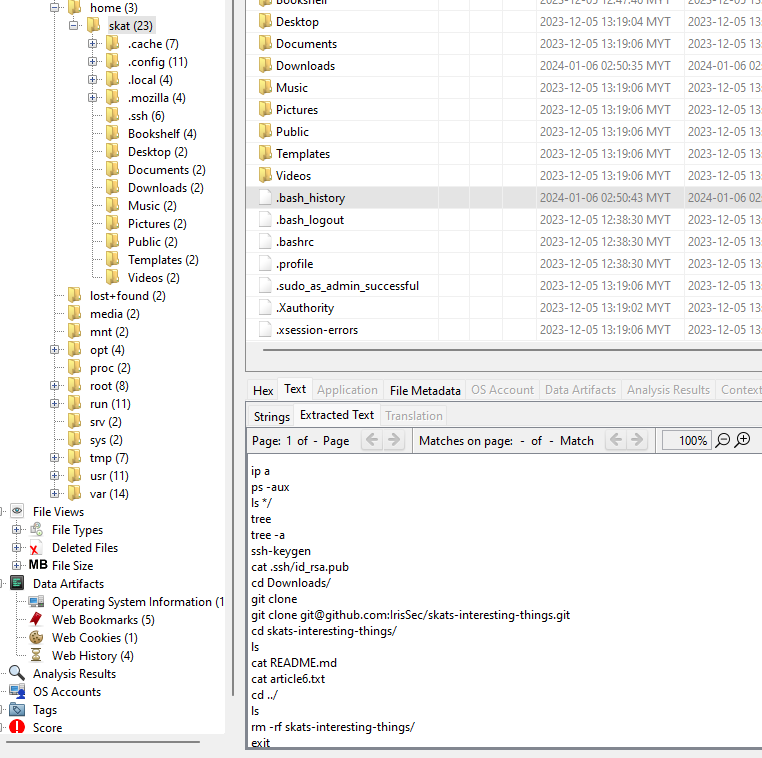
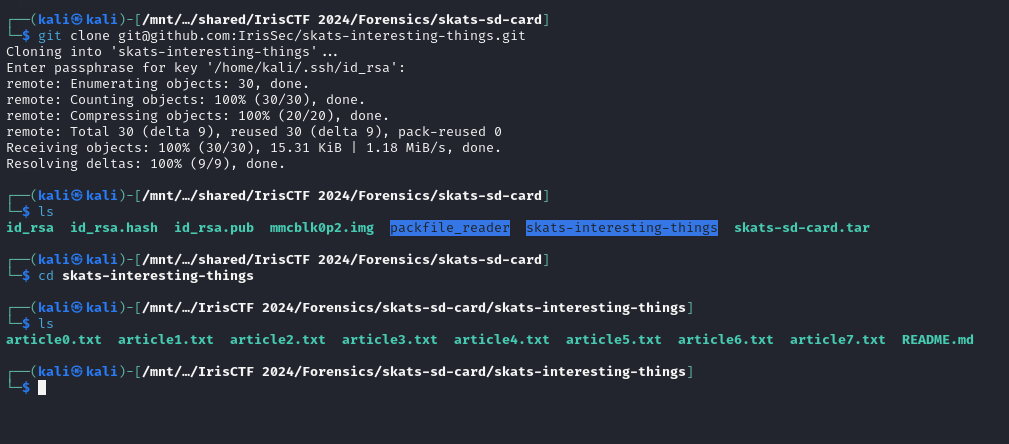
We are given a Linux file system to investigate. Analyzing the user’s bash history, the user seem to have downloaded a repository from GitHub called skats-interesting-things.git.
So I attempted to clone the repository myself but it required a secret key. Unfortunately I could not solve this before the CTF ended, but I still attempted it with the help from several members on Discord. They mentioned that we can actually utilize a public key from the .ssh file.
We can then brute force the private key using John the Ripper to obtain the passphrase.
1
2
ssh2john id_rsa > id_rsa.hash
john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
The cracked password was password (that’s not very secure skat). However, we have to also copy both the private key and public key to my own .ssh directory to be used for authorization. After doing so, the repository can be cloned successfully.
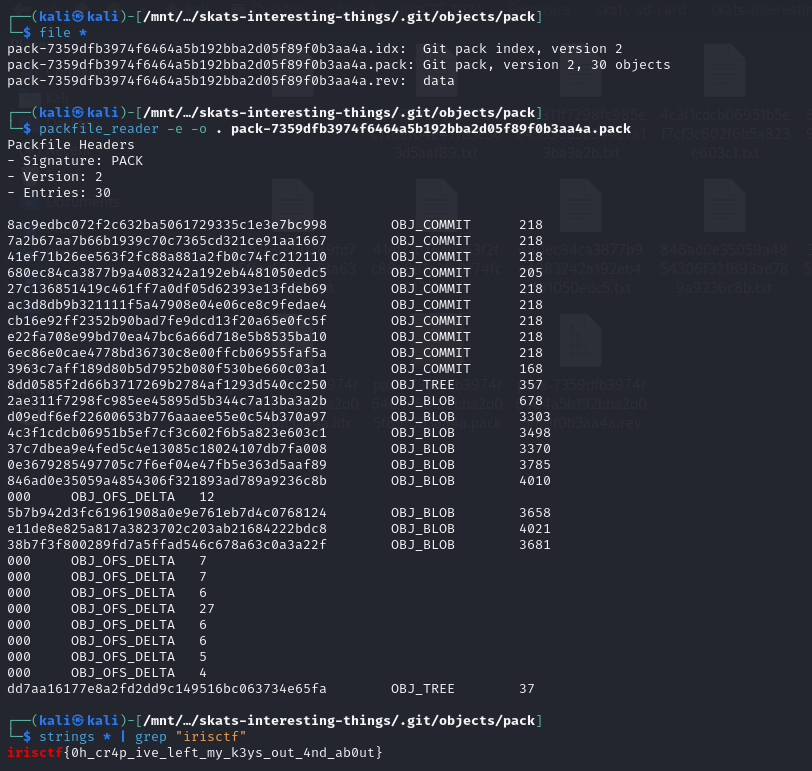
@seal on Discord mentioned that we can use a tool called packfile_reader to extract and parse .git data to several text files. Navigating to .git/objects/pack, we can utilize the tool and just grep the flag.
Where’s skat? [Networking]
Question: While traveling over the holidays, I was doing some casual wardriving (as I often do). Can you use my capture to find where I went? Note: the flag is irisctf{the_location}, where the_location is the full name of my destination location, not the street address. For example, irisctf{Washington_Monument}. Note that the flag is not case sensitive.
Flag: irisctf{los_angeles_union_station}
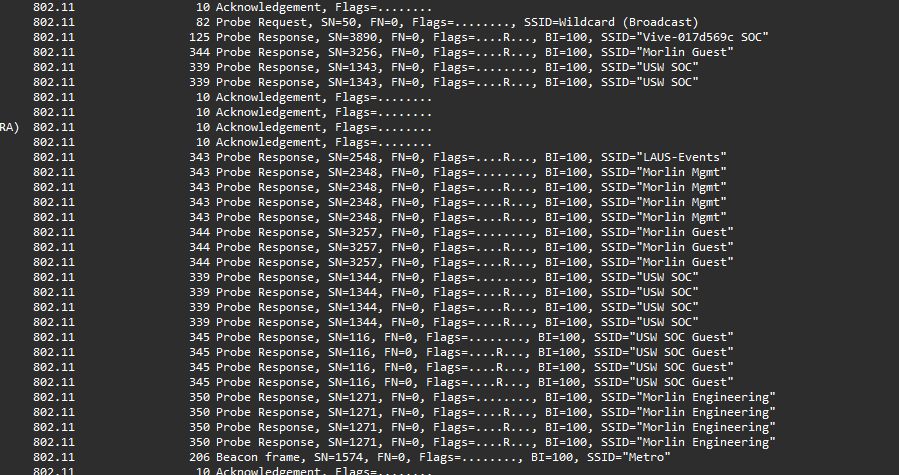
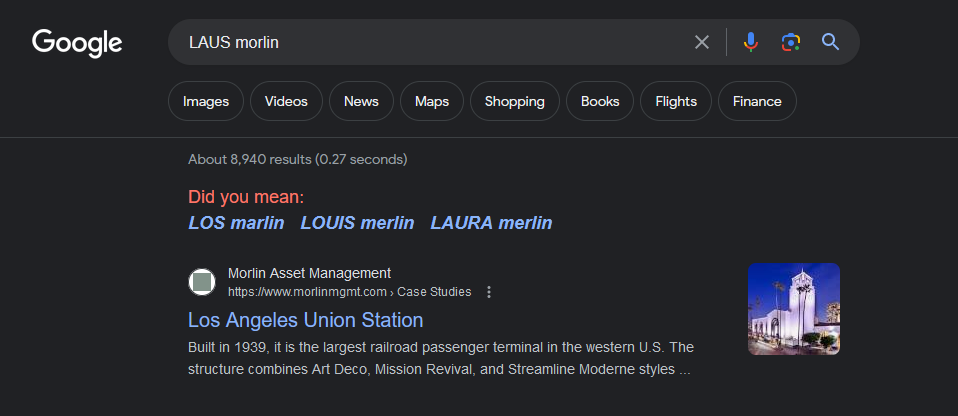
We are given a PCAP file to investigate. Analyzing the packets, it seems like the user’s device was communicating with nearby routers which lead to the same location (according to the SSID).
From what I understand, it seems that the user was present in some metro station due to the multiple Metro SSIDs and by checking LAUS with Morlin together (I thought Morlin was a hotel), we can get the exact location. Funny way to solve the challenge unintendedly.
Czech Where? [OSINT]
Question: Iris visited this cool shop a while back, but forgot where it was! What street is it on?
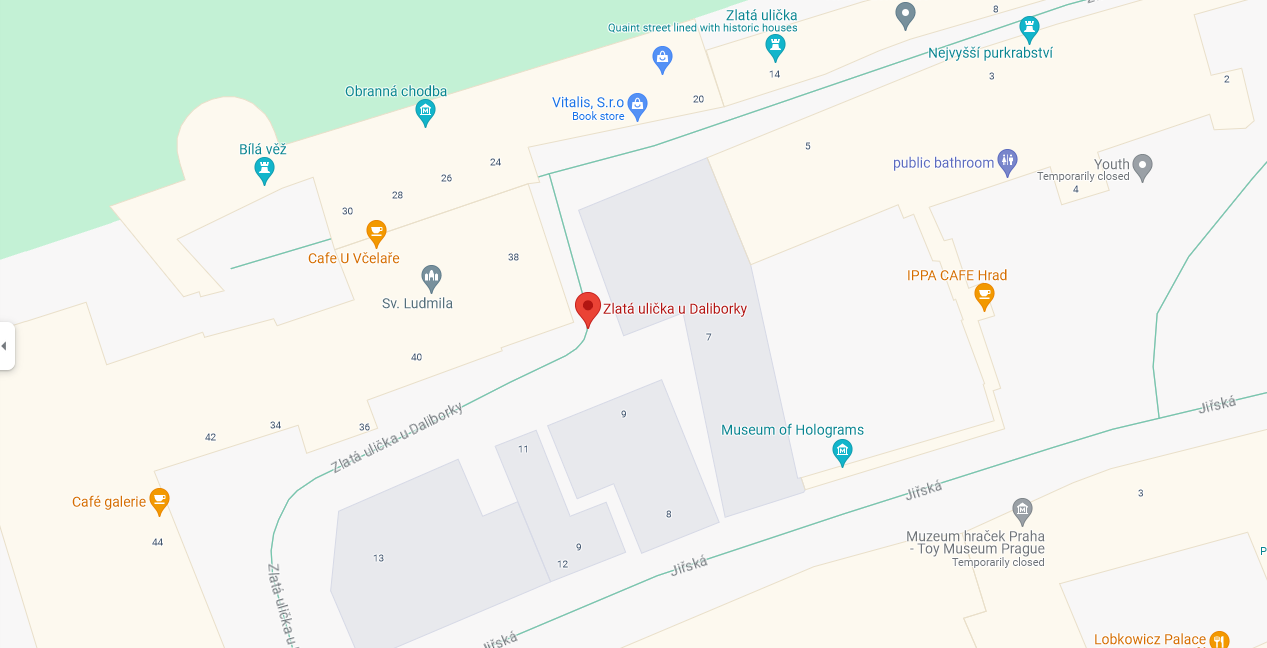
Flag: irisctf{zlata_ulicka_u_daliborky}
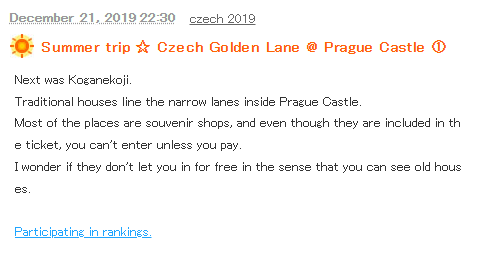
We are tasked to identify the street name of a specific location given the image of a Czech cafe. Reverse searching the image, the name of the cafe can be identified in a Japanese blog.
Looking into Google Maps for Czech Golden Lane, the exact street name can be obtained.
Away on Vacation [OSINT]
Question: Iris and her assistant are away on vacation. She left an audio message explaining how to get in touch with her assistant. See what you can learn about the assistant.
Flag: irisctf{pub1ic_4cc0unt5_4r3_51tt1ng_duck5}
We are tasked to identify a person given a voicemail from Iris Stein.
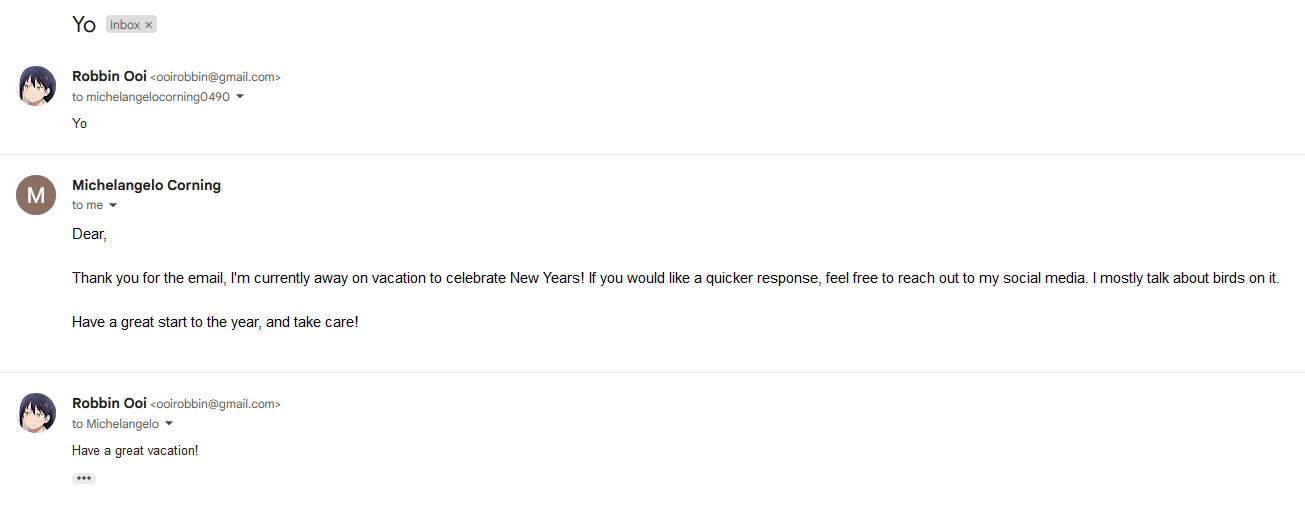
Hello, you’ve reached Iris Stein, head of the HR department! I’m currently away on vacation, please contact my assistant Michel. You can reach out to him at michelangelocorning0490@gmail.com. Have a good day and take care.
Funny thing was I actually went to email Michel since the CTF authors told me it was allowed. Doing so, I got an automatic reply stating that he was also on vacation and I should reach out to him via social media.
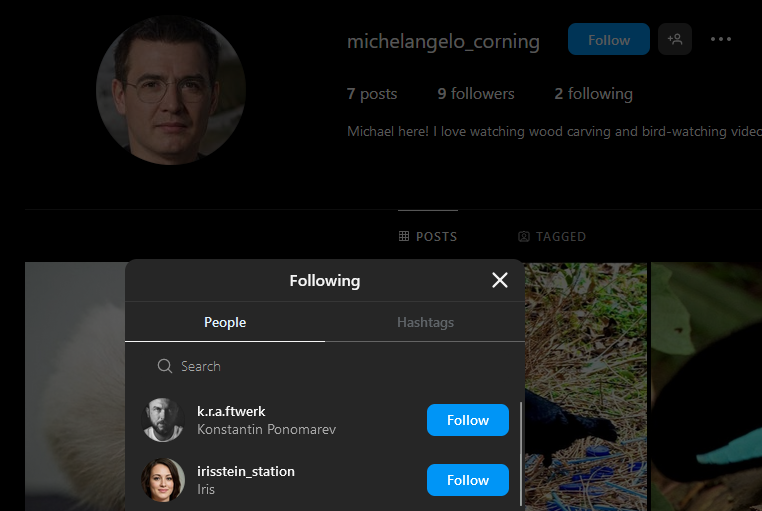
Going through common social media platforms, Michel can be found on Instagram where the flag was in one of his posts.
Personal Breach [OSINT]
Question: Security questions can be solved by reconnaissance. The weakest link in security could be the people around you.
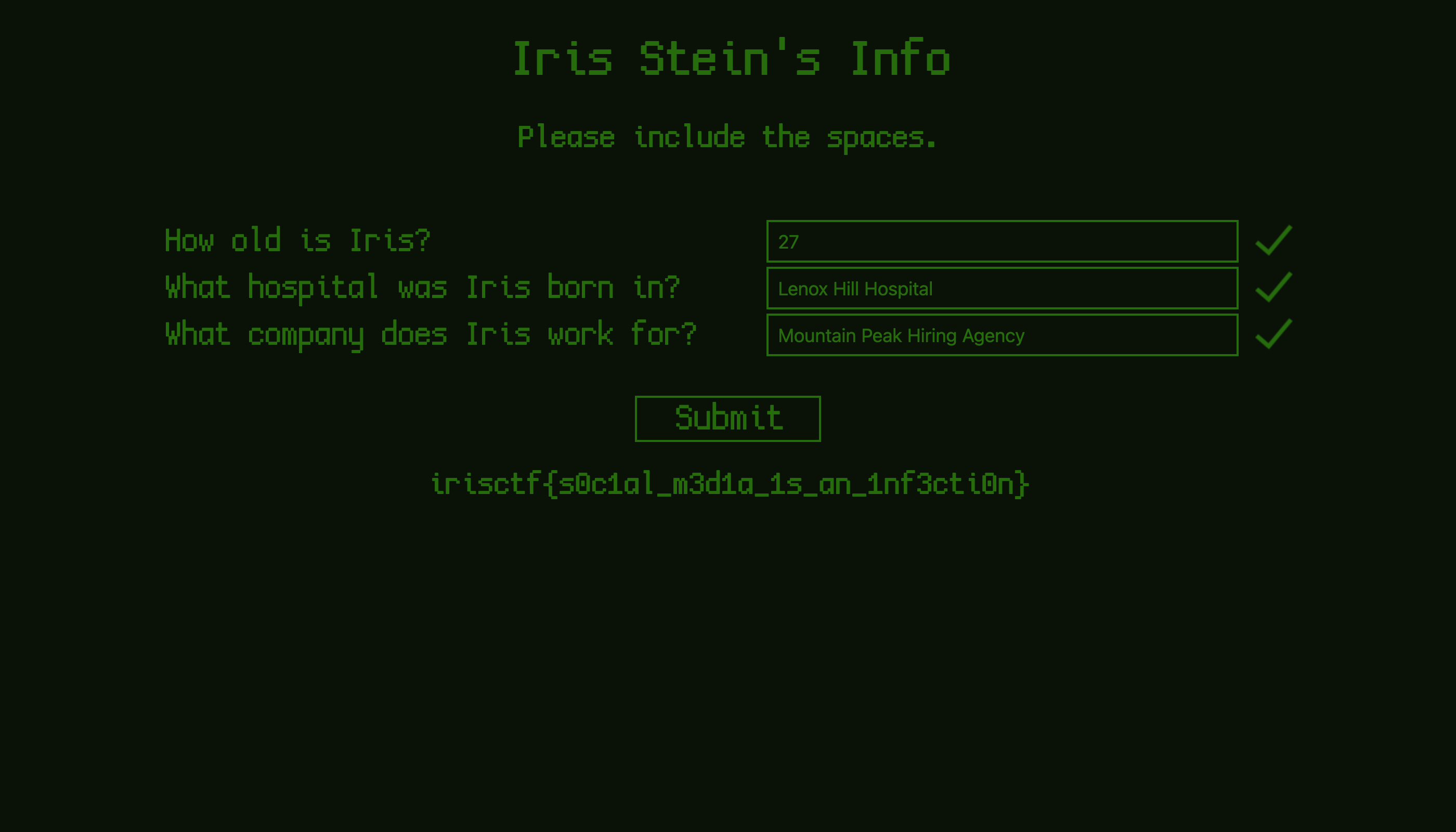
Flag: irisctf{s0c1al_m3d1a_1s_an_1nf3cti0n}
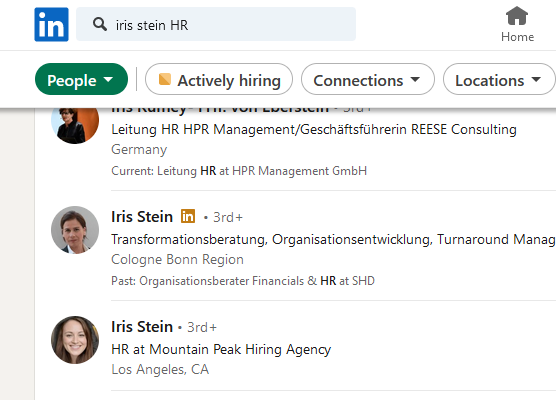
We are tasked to look for information about Iris Stein:
1
2
3
1. How old is Iris?
2. What hospital was Iris born in?
3. What company does Iris work for?
Since we know Iris Stein was associated with Michel at work, we can find her being one Michel’s followers on Instagram.
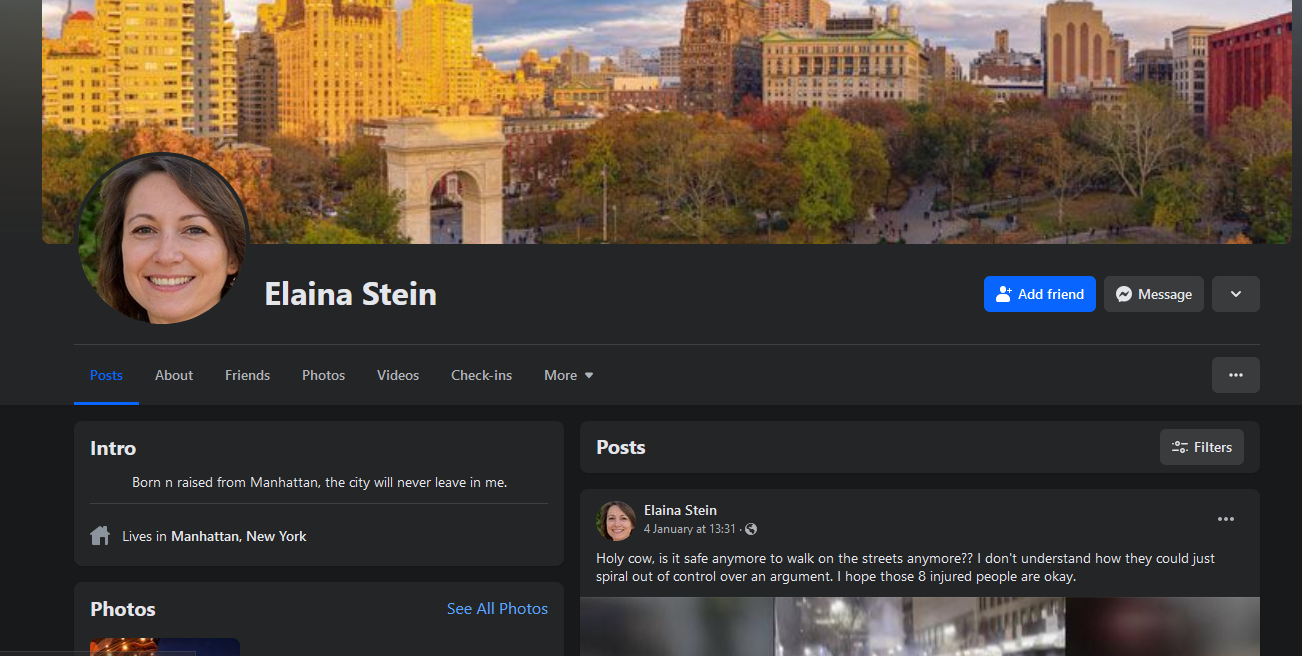
Going through all of her posts, we find that even her mom, Elaina Stein, had a social media account. Looking everywhere for her mom, Facebook seems to be the only social media platform she was using.
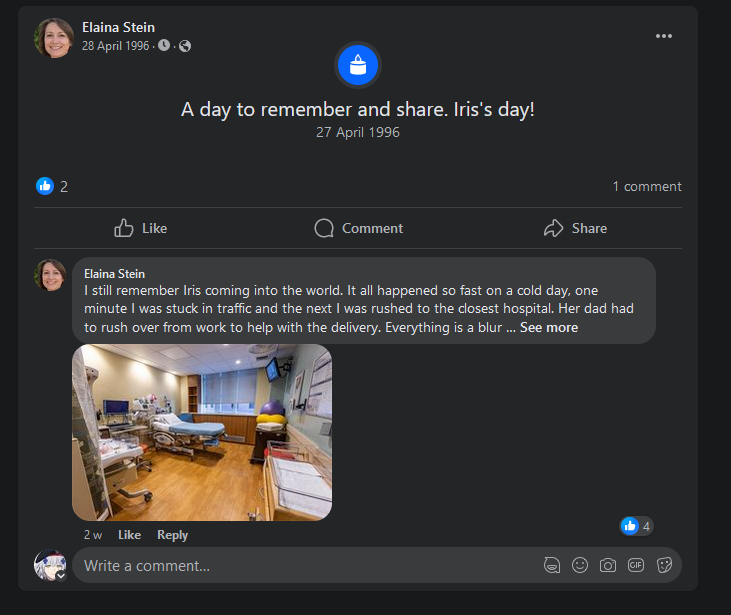
Going through Elaina Stein’s posts, we find a life event post on her daughter’s birth date. There we can identify Iris Stein’s age to be 27 years old.
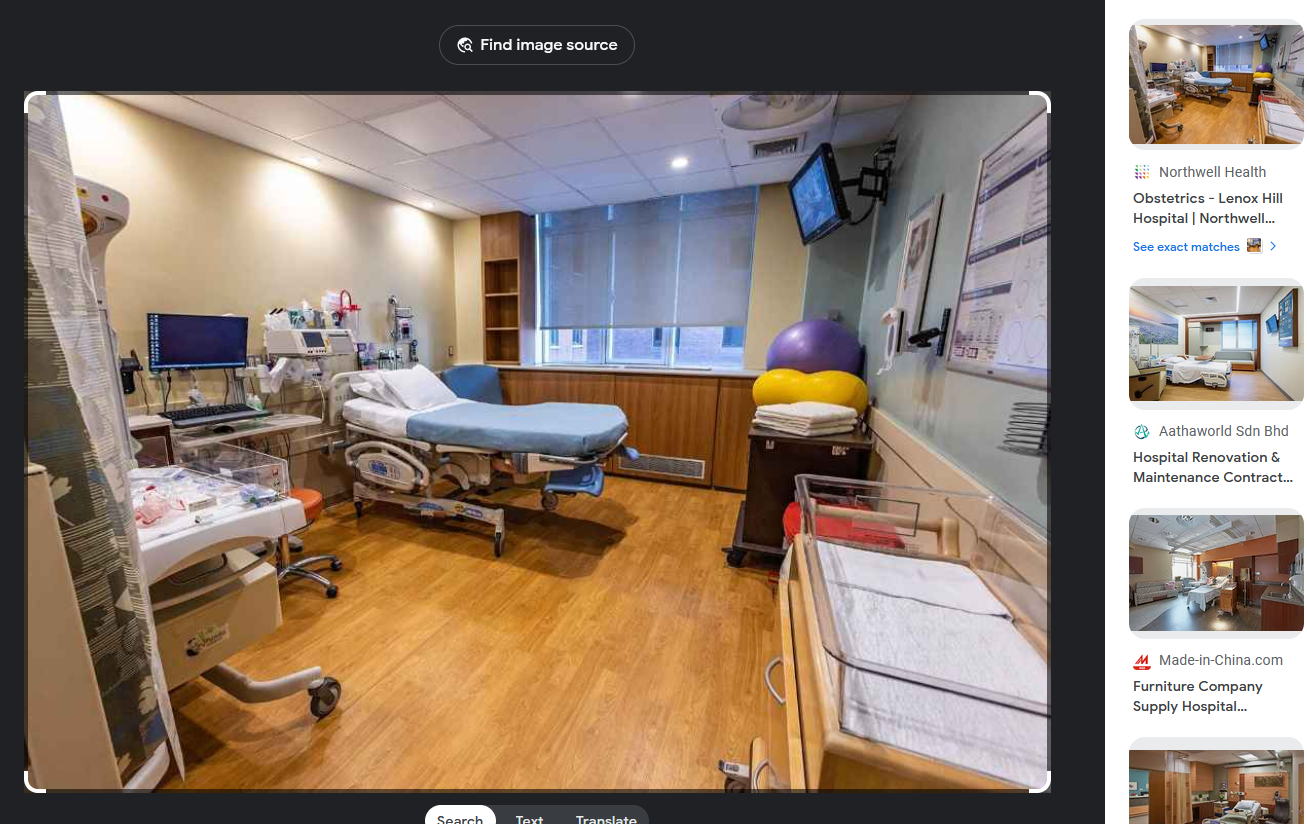
Reverse searching the hospital image, and the name of the hospital can be identified to be Lenox Hill Hospital.
Finally, I went ahead to LinkedIn to locate her company since she was working in a HR department according to the voicemail previously. The company was identified to be Mountain Peek Hiring Agency.
Answering all the questions, the flag is given.