Incognito 5.0 CTF 2024 - Writeups
This is a writeup for all OSINT and cryptography challenges from Incognito 5.0 CTF 2024. A quick CTF to practice my OSINT and cryptography skills. Overall, I was very impressed with their OSINT challenges, they allowed me learn new set of OSINT tools.
Don’t panic [OSINT]
Question: One of our agent was able to get the username “GlitchyBagel42”, you know what’s next 🤷
Flag: ictf{p1x3L_hUnT3R_My5t3ry}
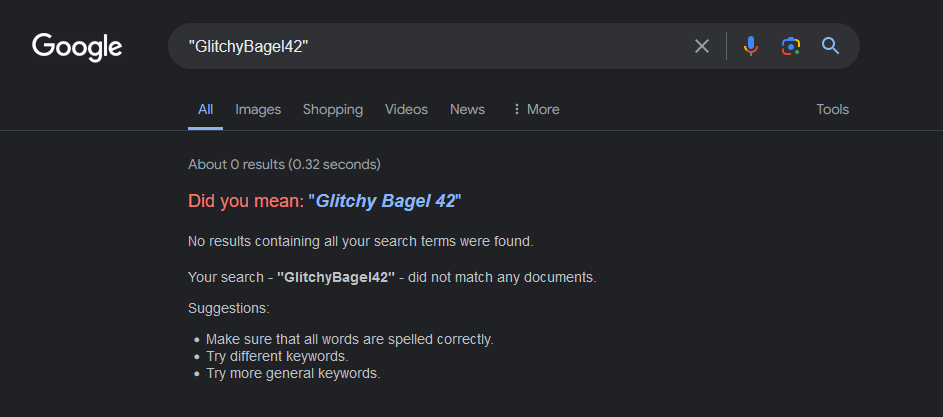
We are tasked to retrieve information on the user GlitchyBagel42. I used this online username lookup tool to search up a username on different platforms, however, there seems to be 0 results on Google.
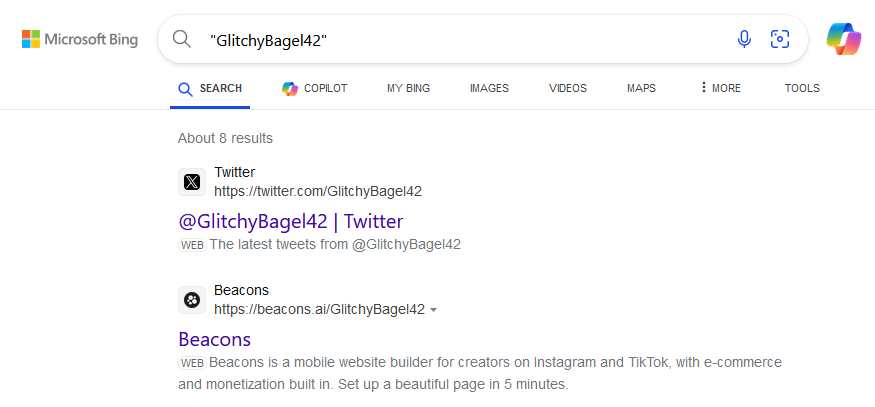
Checking the results of Bing, a Twitter account can be found associated with the specific username.
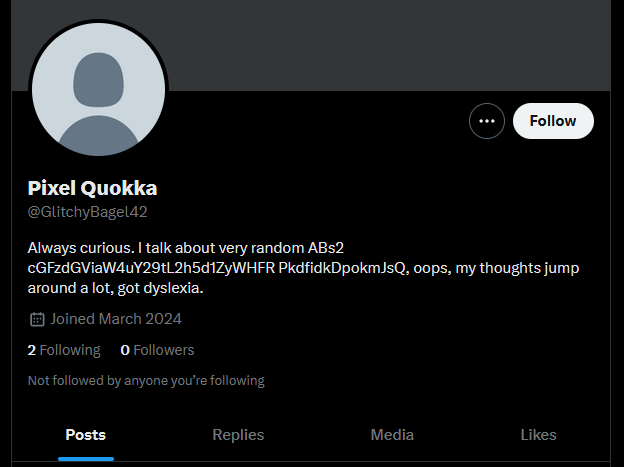
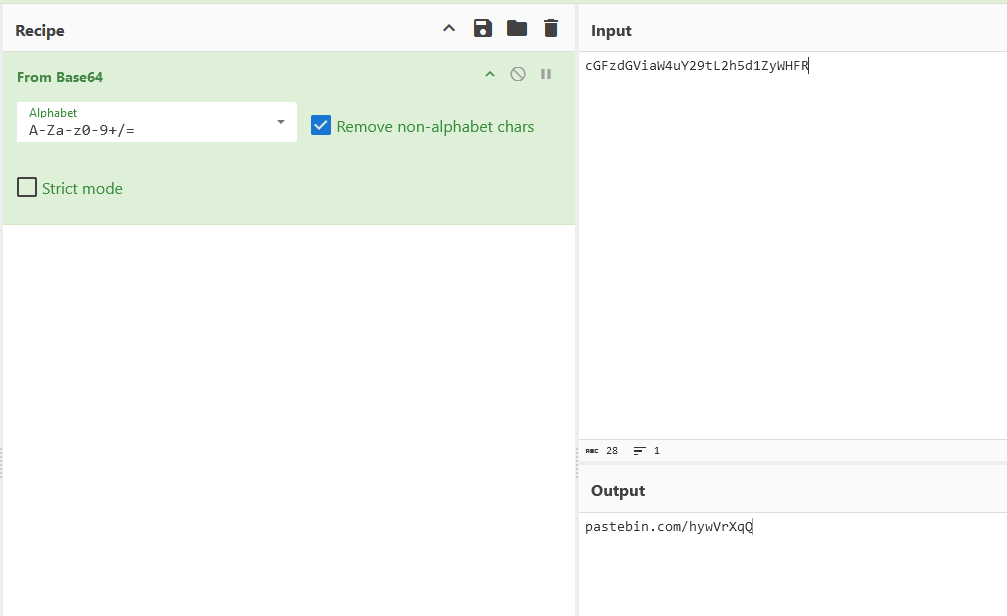
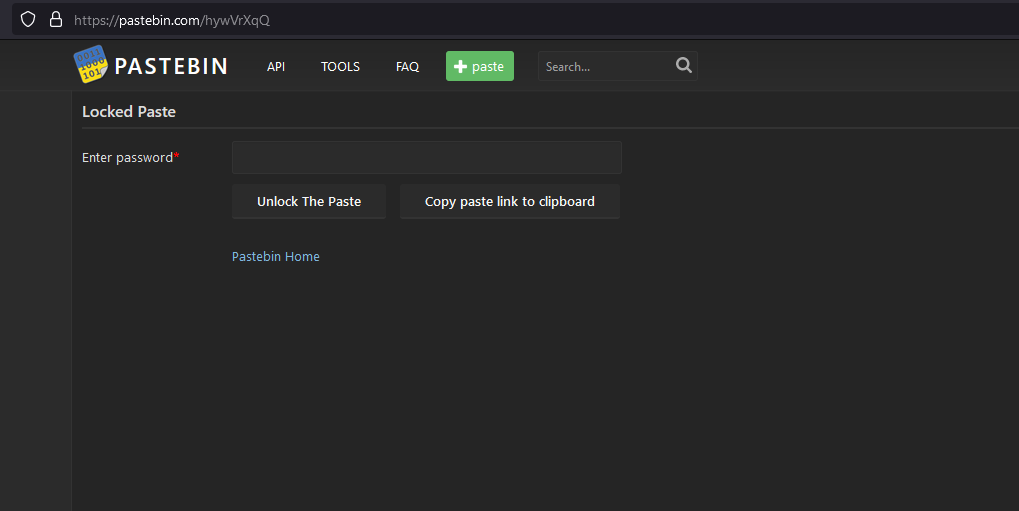
Analyzing the Twitter account, the first clue that can be obtained was the encoded text on the account’s bio. Decoding it provides a Pastebin URL.
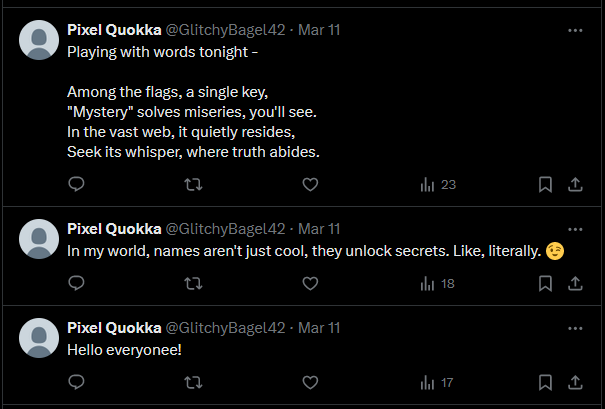
However, the Pastebin data seems to be password-protected. Finding more information on getting the password, several other clues can be obtained from the account’s tweets. It mentioned something about names unlocking secrets. This highly suggests that Pixel Quokka was the password for the Pastebin data.
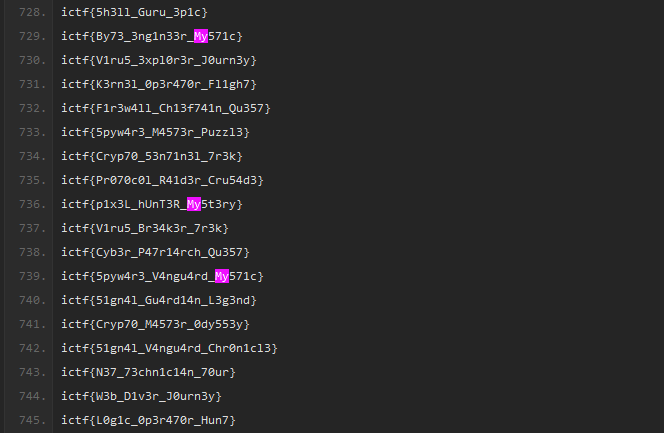
Unsurprisingly, the password was indeed correct and the Pastebin data can be obtained for further analysis. Inside the Pastebin data was several variations of the flag. Checking the tweets again, one of them mentioned something about the word Mystery being able solve miseries. This suggests that the flag had the word Mystery but obfuscated in some way.
Filtering the lines with ‘My’, the only flag that has the word My5t3ry can be obtained.
Email Tracker [OSINT]
Question: Our team discovered the user behind “bbburn216@gmail.com”, enjoys badminton with a friend who shared a secret in their coding activities. We’re eager to uncover what it is.
Flag: ictf{L0v3_F0r_C0d3_Vi4_M41L}
We are given a Gmail account to investigate. Using GHunt, details about a specific Google account can be extracted if a Gmail account was provided to the tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
└─$ ghunt email bbburn216@gmail.com
.d8888b. 888 888 888
d88P Y88b 888 888 888
888 888 888 888 888
888 8888888888 888 888 88888b. 888888
888 88888 888 888 888 888 888 "88b 888
888 888 888 888 888 888 888 888 888
Y88b d88P 888 888 Y88b 888 888 888 Y88b.
"Y8888P88 888 888 "Y88888 888 888 "Y888 v2
By: mxrch (🐦 @mxrchreborn)
Support my work on GitHub Sponsors ! 💖
> GHunt 2.1.6 (BlackHat Edition) <
🎉 You are up to date !
[+] Stored session loaded !
[+] Authenticated !
[!] You have this person in these containers :
- Profile
- Contact
🙋 Google Account data
[-] Default profile picture
[-] Default cover picture
Last profile edit : 2024/03/30 11:31:42 (UTC)
Email : bbburn216@gmail.com
Gaia ID : 104752872827702401548
User types :
- GOOGLE_USER (The user is a Google user.)
📞 Google Chat Extended Data
Entity Type : PERSON
Customer ID : Not found.
🌐 Google Plus Extended Data
Entreprise User : False
🎮 Play Games data
[+] New token for playgames has been generated
[-] No player profile found.
🗺 Maps data
Profile page : https://www.google.com/maps/contrib/104752872827702401548/reviews
[Statistics]
Reviews : 1
[Reviews]
[+] Average rating : 5/5
[-] No costs data.
Target's locations preferences :
🏨 Generic [1]
- Badminton court (1)
[+] Probable location (confidence => Very low) :
- ?, India
🗓 Calendar data
[-] No public Google Calendar.
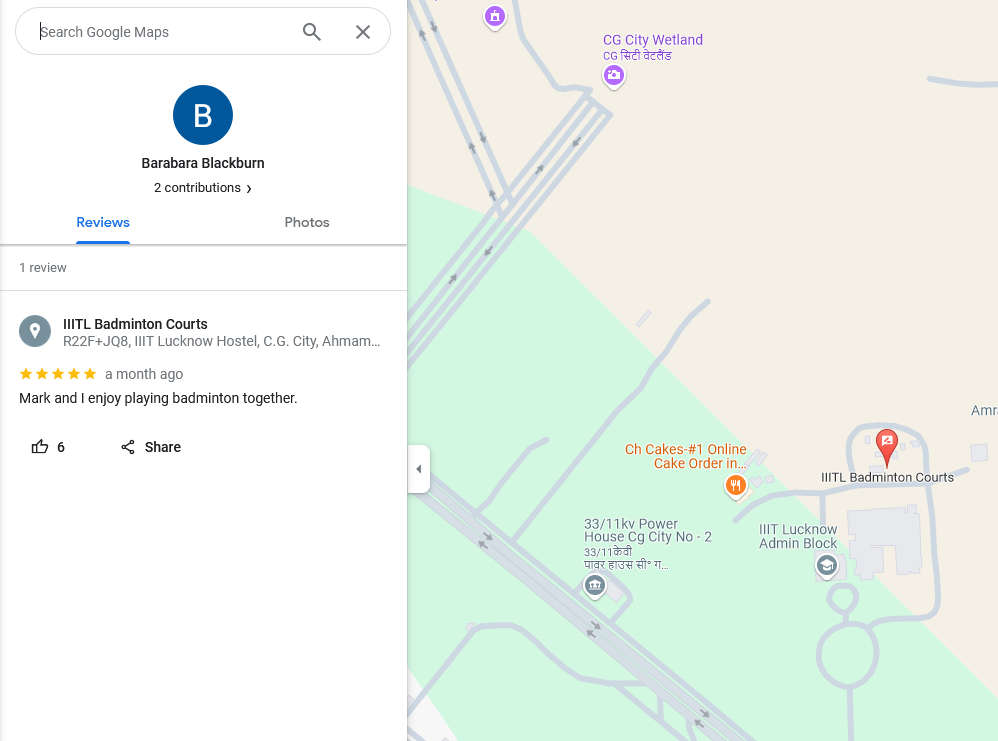
The output shows that the user has left a review on Google maps. Analyzing the review, it seems that Barabara Blackburn (the user) was playing badminton with his friend Mark.
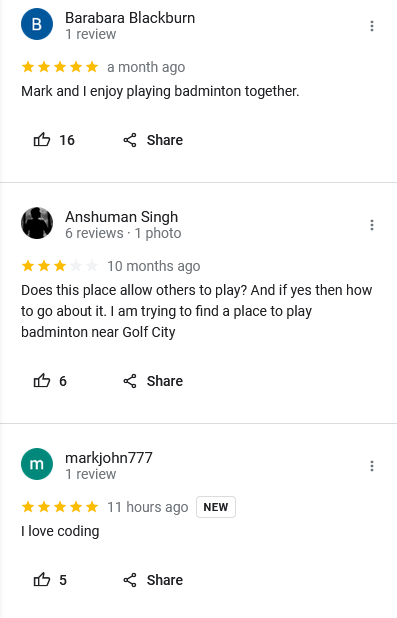
Spending countless hours on finding Barabara Blackburn on different social platforms, nothing of interest can be found. However, when checking the reviews of the location, a review from Mark can be found.
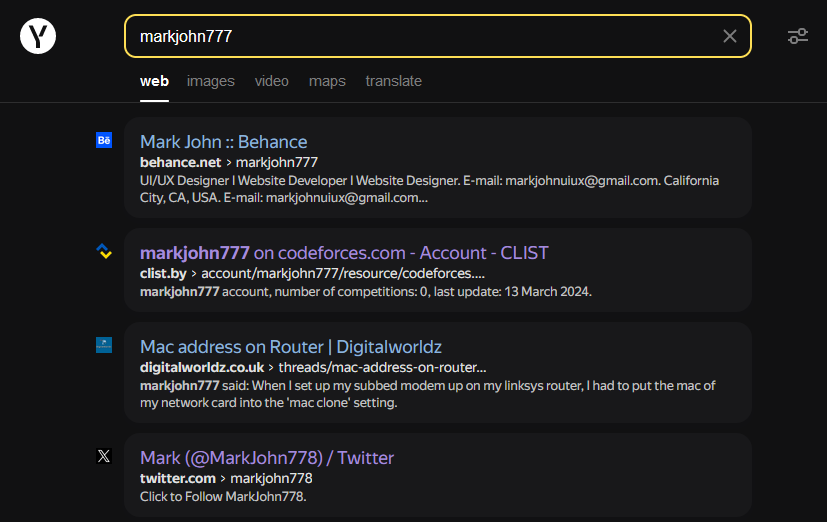
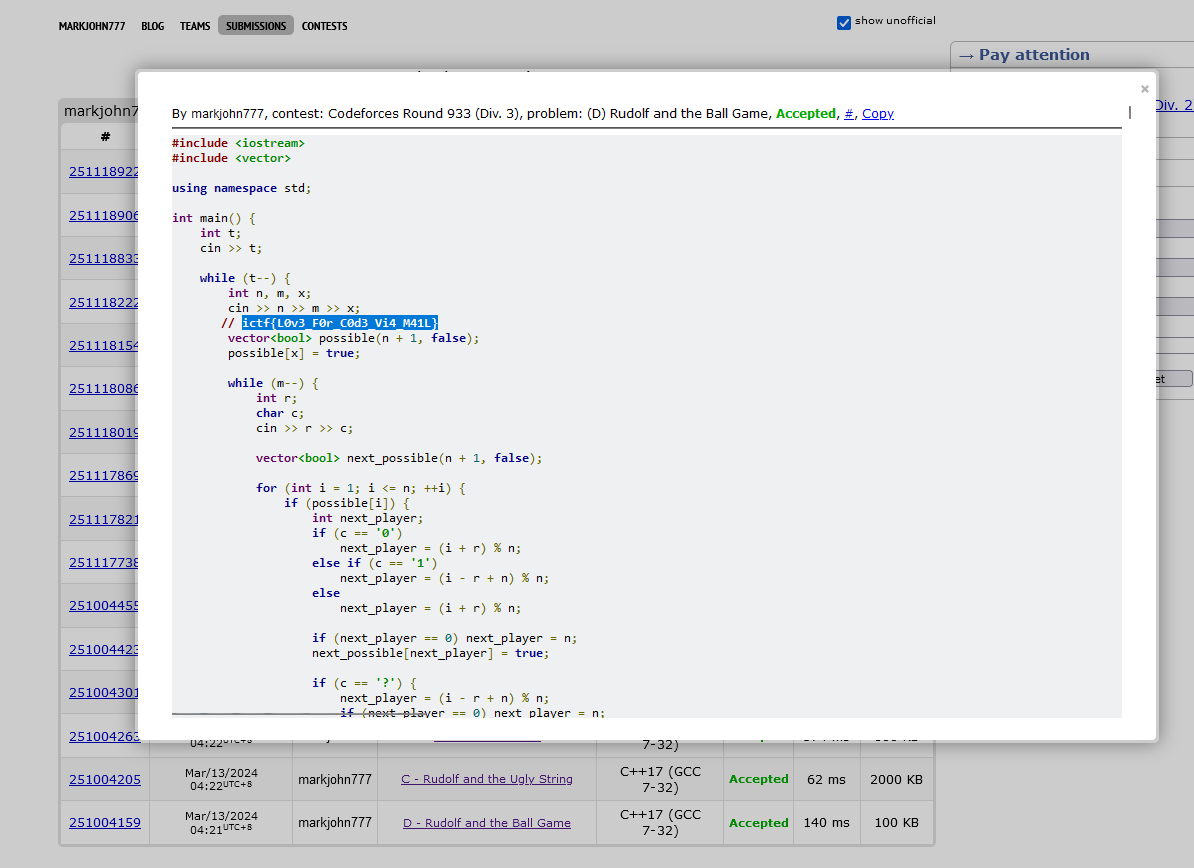
Now we have another username markjohn777 to investigate, we can use the similar online username lookup tool to search up his username on different platforms. Google and Bing seems to show his social media accounts that were either deactivated or deleted already. However, checking out Yandex, his CodeForce account can be found.
The description also mentioned something about Mark leaving a secret during his coding sessions. Hence, the flag was bound to be inside his CodeForce account. Analyzing his code submissions, the last submission with ID 251004159 has the flag.
Easy [Cryptography]
Question: Delve into binary operations, where math meets magic
Flag: ictf{X0R_Br0ught_Y0u_H3r3?}
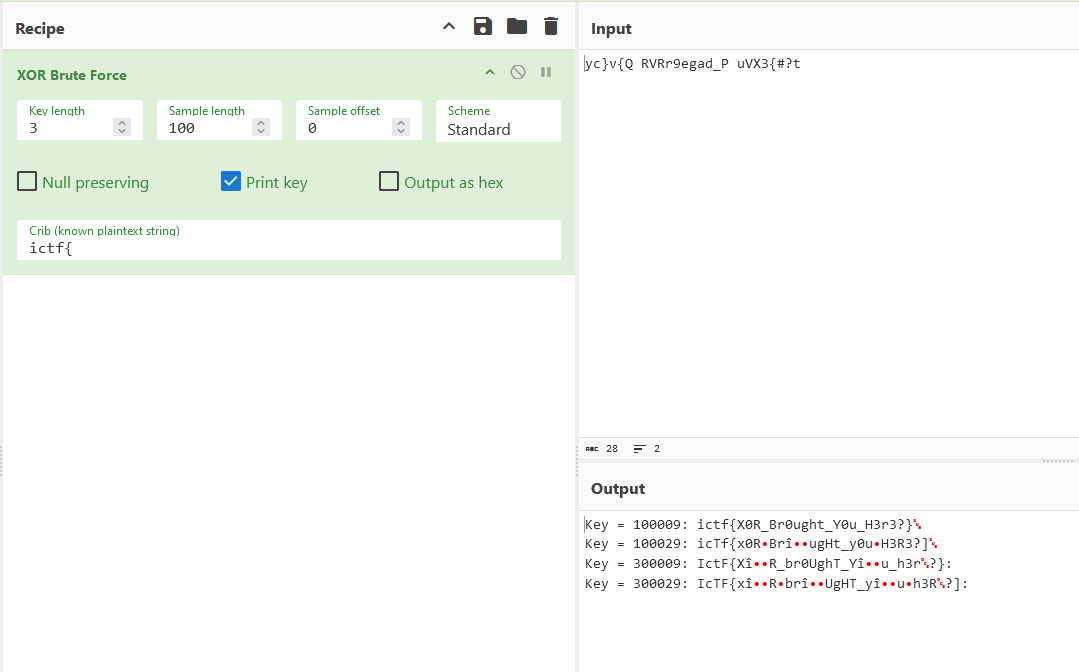
We are given an encoded text to investigate. The description mentioned something about binary operations, this highly suggests XOR. Since a XOR key was not provided, brute forcing the ciphertext easily provides the flag.
Di Dah [Cryptography]
Question: Beneath flickering lights, echoes play their games, In voltage’s fluctuations, telegraph’s silent claims.
Flag: ictf{M0rs3_4nd_D1D@h_Wh1z3r3r}
We are given an encoded text to investigate. Just by looking at the text, it seems like it was related to morse code.
1
dah-di-di-di-dit dah-dah-dah-dah-dit dah-di-di-di-dit di-di-di-dah-dah dah-dah-di-di-dit di-di-di-di-dah dah-di-di-di-dit dah-di-di-di-dit dah-dah-di-di-dit dah-di-di-dit di-di-di-di-dah dah-di-dit di-di-di-dah-dah dah-dah-dah-dah-dah dah-dah-di-di-dit di-di-dah-dah-dah dah-dah-di-di-dit di-di-di-dah-dah di-di-di-dah-dah di-di-di-dah-dah di-di-di-di-dit di-di-dah-dit di-di-di-dah-dah di-di-di-di-dah dah-di-di-di-dit dit dah-di-di-di-dit di-di-di-di-dah di-di-di-di-dit di-di-dah-dit di-di-di-di-dah di-di-di-di-dah di-di-di-dah-dah di-dah-dah-dah-dah di-di-di-di-dah di-di-di-di-dah di-di-di-di-dah dah-dah-dah-dah-dah dah-di-di-di-dit dah-dah-dah-di-dit di-di-di-di-dit di-di-dah-dit di-di-di-di-dit dah-dah-di-di-dit dah-di-di-di-dit dah-dah-dah-di-dit di-di-di-dah-dah di-dah-dah-dah-dah dah-dah-di-di-dit di-dah di-di-di-dah-dah di-di-di-dah-dah dah-dah-di-di-dit di-di-dah-dah-dah di-di-di-dah-dah di-di-di-dah-dah dah-dah-di-di-dit di-di-dah-dah-dah dah-dah-di-di-dit dah-di-dit dah-dah-dah-dah-dah di-dah
Searching online about dah-di-dit, a morse code manual can be found to help translate the morse code manually. Mapping the morse code with the ASCII characters, a hex encoded string can be obtained which was the flag.
Marathon [Cryptography]
Question: How long you can go?
Flag: ictf{D3c0d3_4ll_7h3_W@y}
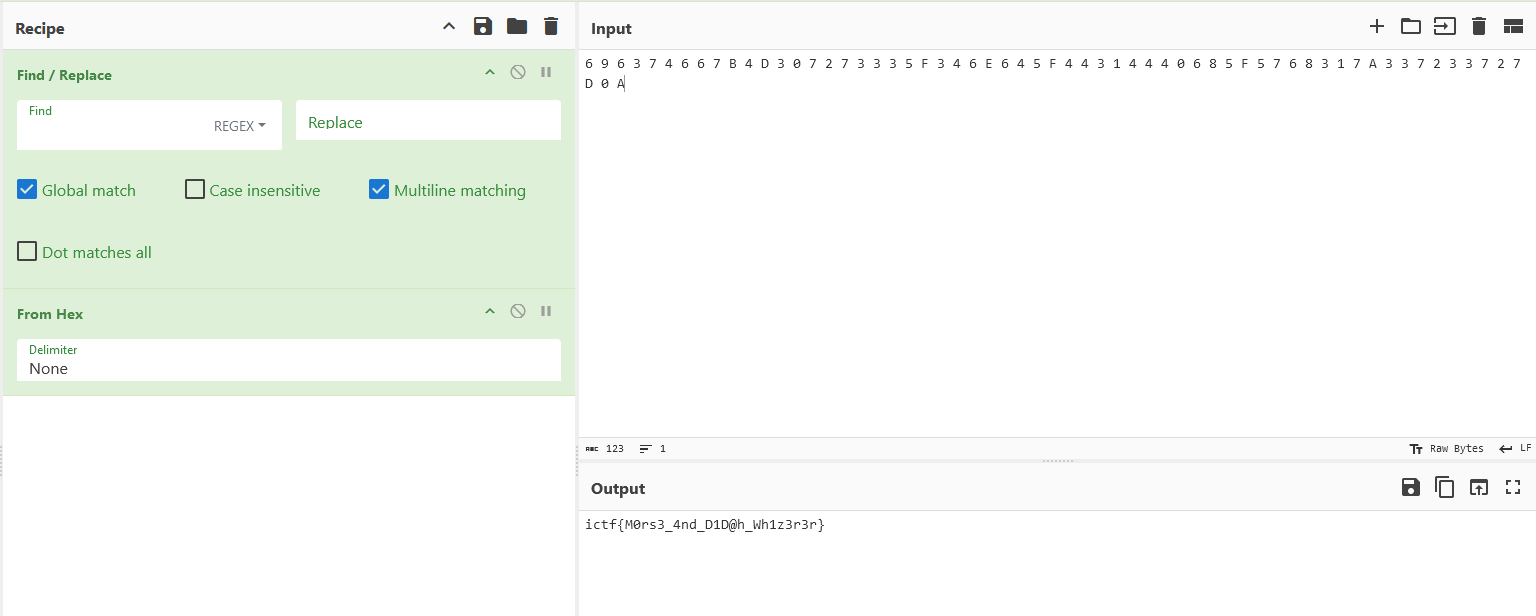
We are given an encoded text to investigate. No joke, the flag can be directly obtained after decoding with various methods.
1
3430203633203639203538203664203763203334203731203366203362203562203731203262203332203366203231203366203564203662203362203365203538203635203330203435203634203739203239203236203530203634203566203363203333203331203532203564203530203265203634203239203533203632203539203535203763203634203632203462203362203533203731203261203733203333203563203430203436203435203461203238203262203466203733203434203539203533203634203663203536203331203334203233203539203565203233203365203537203535203634203438203261203362203635203336203363203634203464203664203666203436203332203236203431203238203436203338203737203533203363203263203461203335203737203239203535203663203463203665203233203333203732203361203236203363203364203436203764203331203731203233203331203530203562203538203439203532203438203366203539203330203632203331203738203261203530203361203231203631203734203536203537203535203637203362203264203531203365203533203633203334203430203733203762203565203639203263203365203439203737203430203236203736203331203639203733203330203665203334203436203536203363203239203337203631203633203339203566203439203265203265203764203432
The whole decoding process using CyberChef