Hack A Day CTF 2023 - Writeups
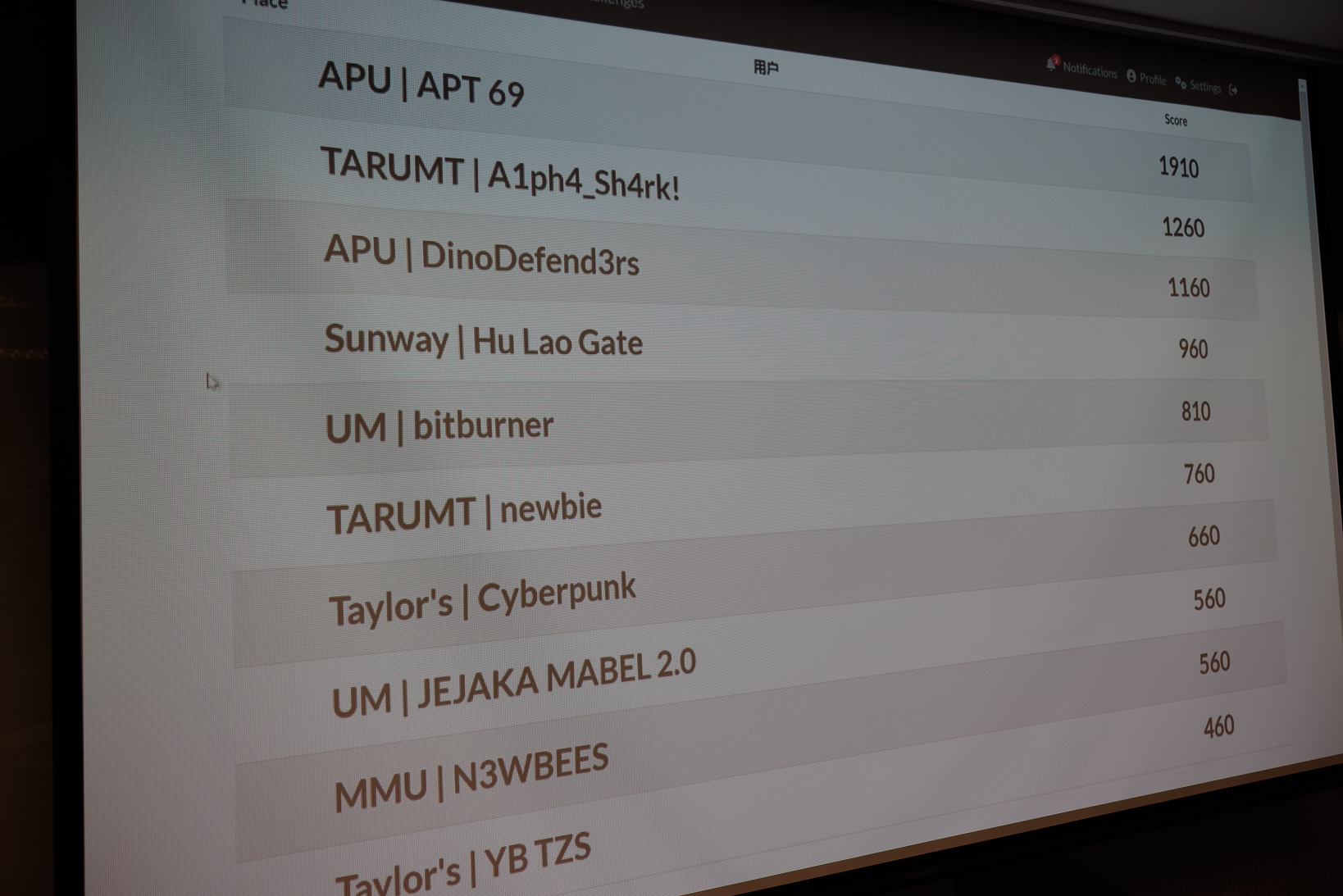
This is a writeup for some OSINT and forensics challenges from Hack A Day CTF 2023 organized by PwC. This was also my first local CTF I’ve participated with my university friends @Shen and @Blugon. In the end we managed to achieve 4th place out of 10 teams locally and 34th out of 60 teams regionally. As my first-ever local CTF experience, this was a huge confidence boost which ignited my passion for DFIR and Threat Hunting.
Disclaimer
Unfortunately, I couldn’t retrieve the files and flags but I still vividly remember how the challenges went down.
OSINT 1 [OSINT]
Question:
Flag:
We are tasked to find information about an insider in a cafe website. The insider was recently known to go incognito to hide from the police, so obviously his profile will not be in the cafe website. I had to use Wayback Machine obtain the flag on the insider’s profile bio.
Threat Hunt 1 [Forensics]
Question:
Flag:
We are given a compromised machine image to investigate. The malware can be found in the user’s Desktop with its name being the flag.
Threat Hunt 2 [Forensics]
Question:
Flag:
Going through the compromised machine, a suspicious file can be found in the Preference folder which seemingly resembles the flag. Later, we found out the flag was encoded with ROT13 due to the file having the word Caesar on the top. Decoding it gives us the flag.