GOH CTF 2023 - Writeups
This is a writeup for some forensics and OSINT challenges from Game of Hackers CTF 2023 organized by UniKL MIIT. My university sponsored several students to participate in this CTF and I was fortunate enough to be selected. I teamed up with my friends @Nathan and @Wowiee to compete against students from other Malaysian universities. In the end, we only achieved 13th place out of 30 teams, but it was still a memorable experience that tested our CTF skills and teamwork.
The realm of Eerie Area [Forensics]
Question: In this mysterious realm, a malevolent force is at play. Uncover the hidden malevolence within. Figure out the dark secrets the area holds.
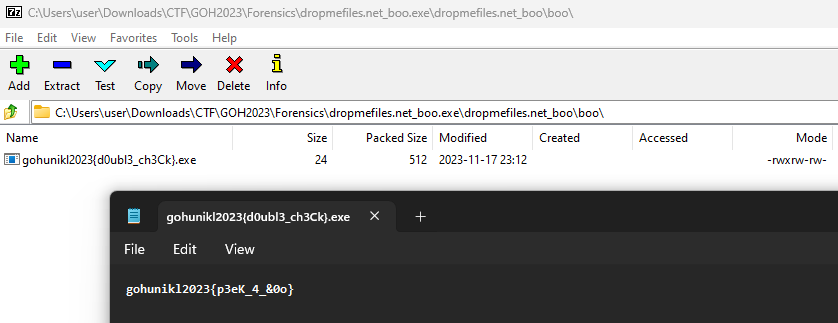
Flag: gohunikl2023{p3ek_4_&0o}
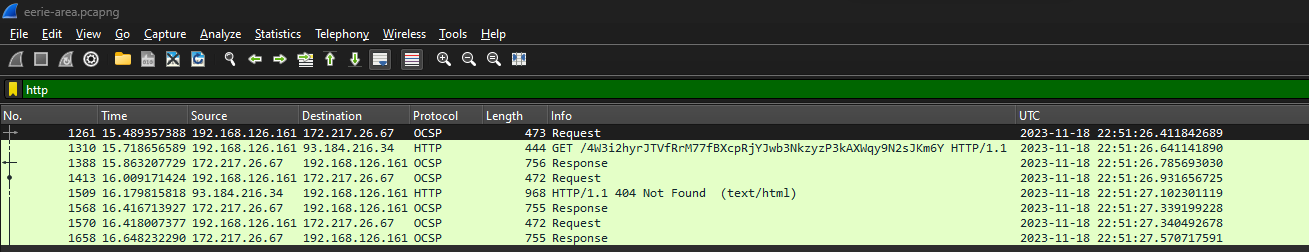
We are given a PCAP file to investigate. Analyzing the HTTP packets, a strange encoded GET request can be identified.
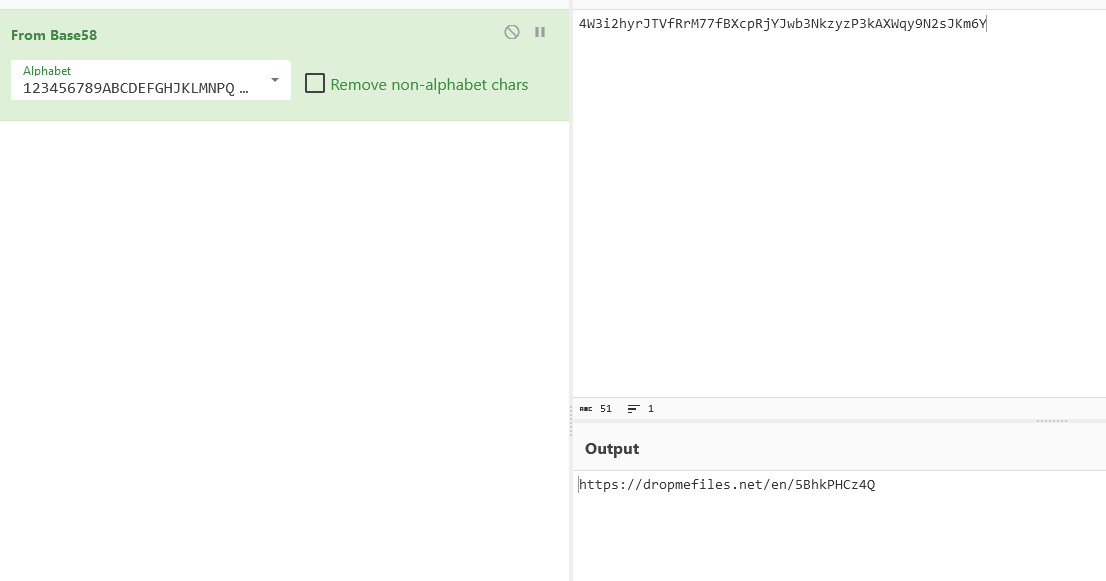
Decoding the URL with Base58 will output another URL that redirects to a file upload website.
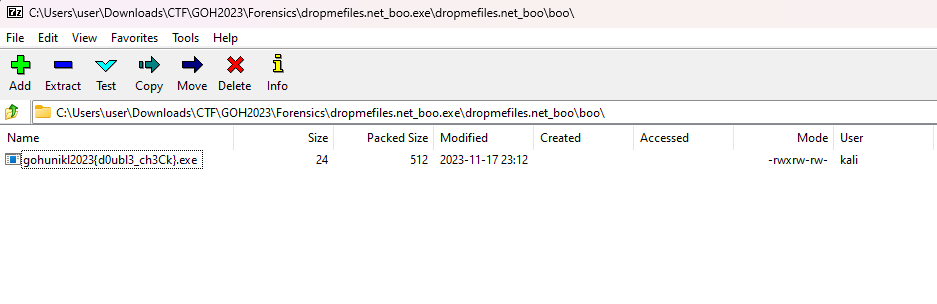
In the website, a file called dropmefiles.net_boo.exe could be downloaded. However, it was discovered that the file was actually a ZIP file rather than an executable file.
1
2
└─$ file dropmefiles.net_boo.exe
dropmefiles.net_boo.exe: gzip compressed data, from Unix, original size modulo 2^32 10240
Navigating the ZIP file, the flag can be obtained within a hidden file embedded into another file.
However, the flag was actually a bait…The real flag can be obtained from the file content instead.
Find Me [OSINT]
Question:
Flag: gounikl2023{Y0u_F0und_M3}
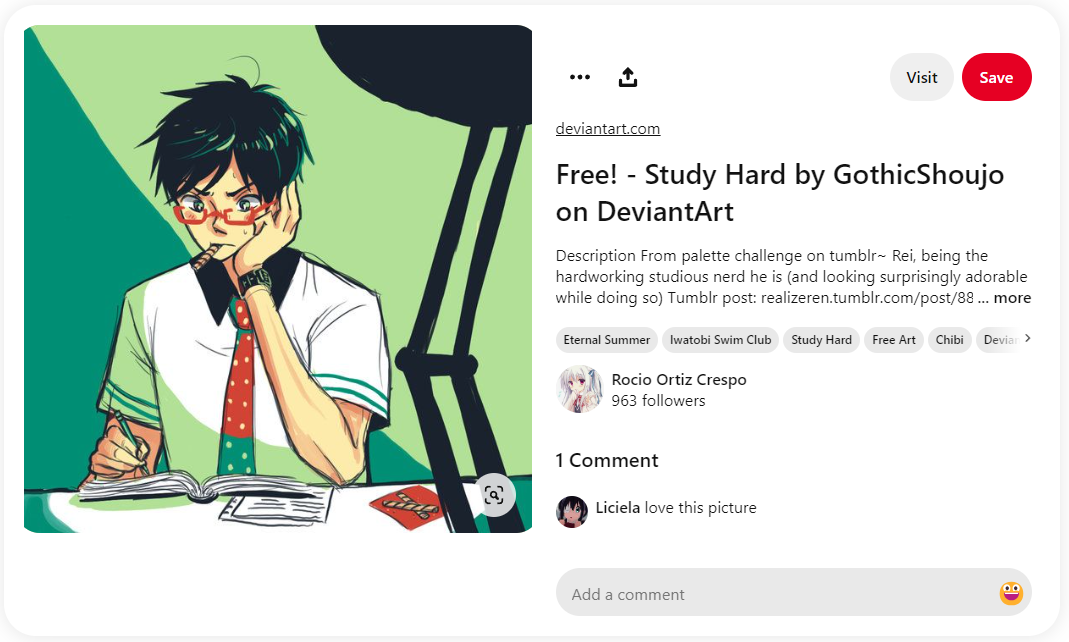
We are tasked to investigate a person given an anime picture. Reverse searching the anime picture, one of the results was a Pinterest post.
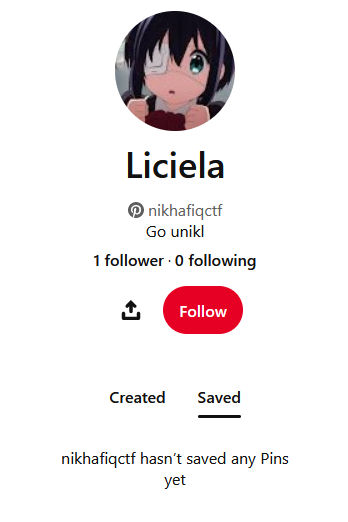
There was a user Liciela that liked the image. Checking the user’s profile, he was identified to be associated with UniKL, meaning we are on the right track.
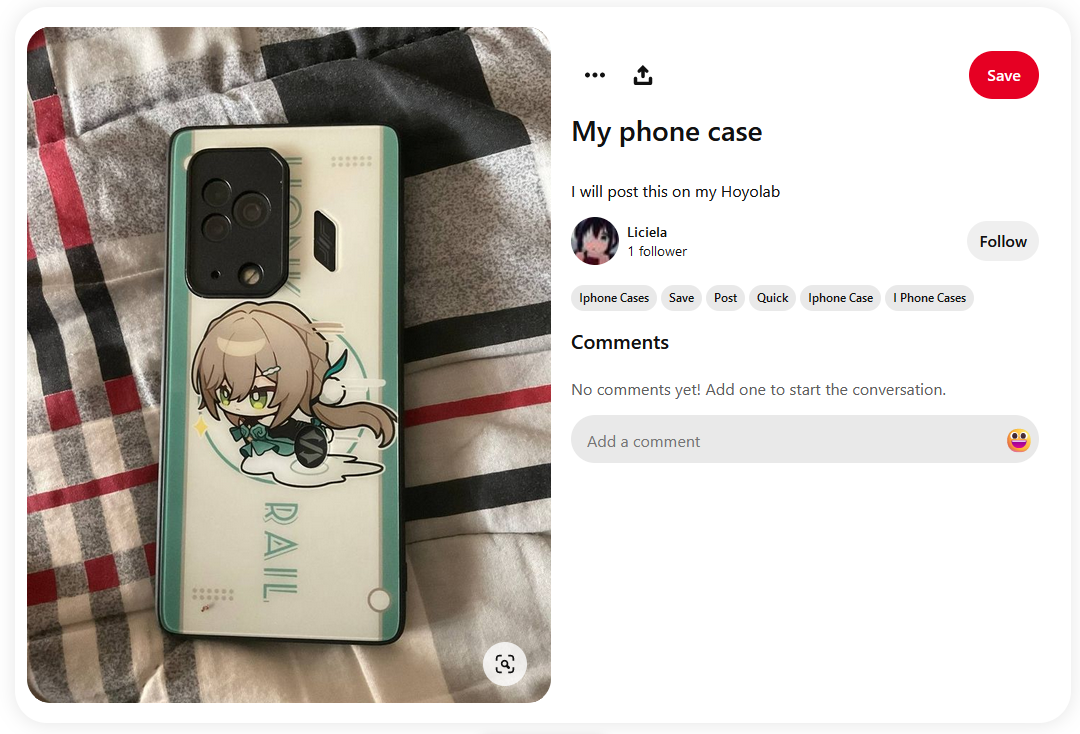
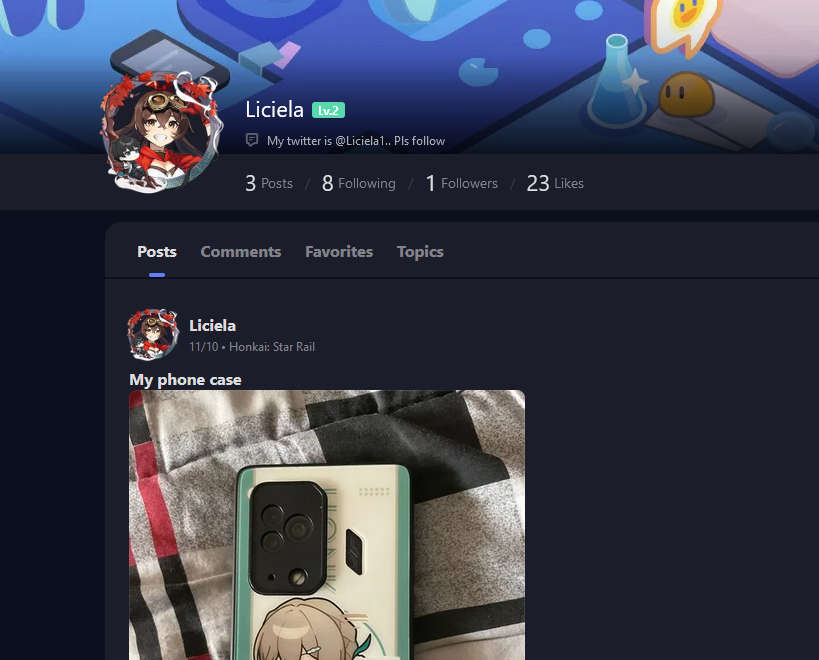
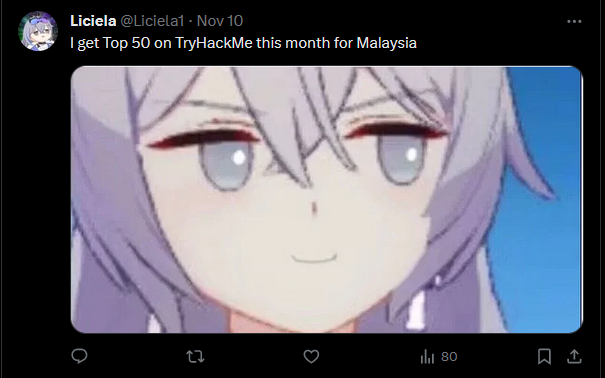
Going to one of his post, we see that he also had a Hoyolab account which I assumed he used the similar name.
Checking his Hoyolab account, his Twitter account can be identified on his account bio. At this point, I was prepared to dive into a deep rabbit hole.
Going to one of his tweets, the user mentioned that he was Top 50 in Malaysia on TryHackMe.
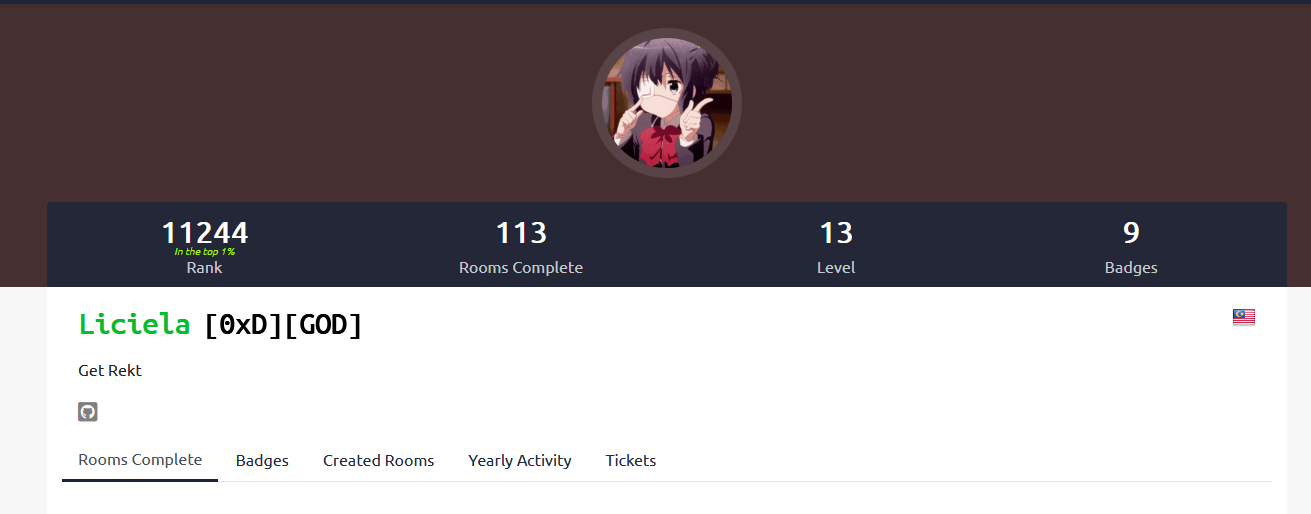
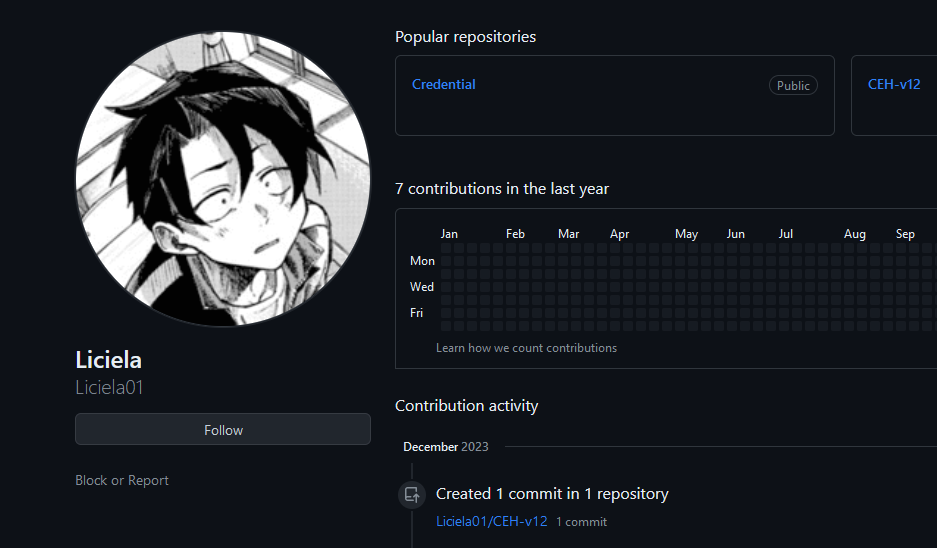
When checking the monthly leaderboards on TryHackMe, we can see that his account was indeed top 1. Inside his TryHackMe account, a GitHub account was linked to it so we can proceed there now.
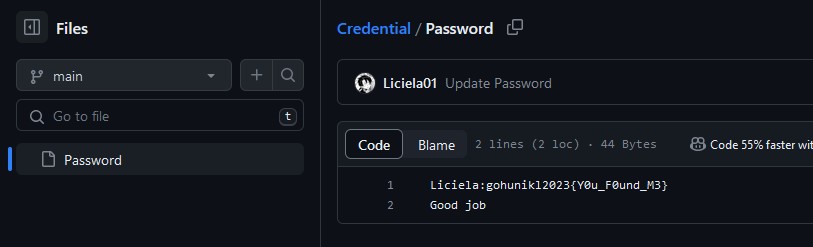
The flag can be obtained in the “Credential” repository.