DeadSec CTF 2024 - Writeups
This is a writeup for some misc and OSINT challenges from DeadSec CTF 2024. Another W for L3ak where we achieved 1st place 🥇! The misc challenge was interesting as it showcased a new method of cracking zip files using ZipCrypto method. However, the OSINT challenges were pretty lackluster and very little leads, hope the authors improve them next year.
Forgotten Password [Misc]
Question: I was going to create this extremely easy forensics challenge for you, but accidentally used the flag as the password when I encrypted the archive. This flag is now deleted, and since it is not possible to brute-force it, I guess that means this challenge can no longer be solved, or can it?
Flag: DEAD{weird_how_this_encryption_is_the_default_in_2024}
We are given a ZIP file and a Python script to investigate. Analyzing the Python script first, it seems to create an ISO file containing the flag and packages the ISO file into a password-protected ZIP file using the flag as the password.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
from io import BytesIO
import os
import subprocess
import pycdlib # pip install pycdlib
try:
FLAG = open("flag.txt","r").read()
except FileNotFoundError:
FLAG = "fake_flag_for_testing"
iso = pycdlib.PyCdlib()
iso.new(interchange_level=4)
iso.add_fp(BytesIO(FLAG.encode()), len(FLAG), '/flag.txt;1')
iso.write('challenge.iso')
iso.close()
subprocess.check_output(["zip", "challenge.zip", "challenge.iso", "-P", FLAG])
Analyzing the given zip file, the zip encryption method can be identified as ZipCrypto Deflate, a legacy zip encryption method that can be cracked using a known plaintext attack.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
└─$ 7z l -slt challenge.zip
7-Zip 24.07 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-06-19
64-bit locale=en_US.UTF-8 Threads:32 OPEN_MAX:1024
Scanning the drive for archives:
1 file, 574 bytes (1 KiB)
Listing archive: challenge.zip
--
Path = challenge.zip
Type = zip
Physical Size = 574
----------
Path = challenge.iso
Folder = -
Size = 53248
Packed Size = 382
Modified = 2024-07-25 15:46:32
Created =
Accessed =
Attributes = -rwxrwxrwx
Encrypted = +
Comment =
CRC = 17EE7183
Method = ZipCrypto Deflate
Characteristics = UT:MA:1 ux : Encrypt Descriptor
Host OS = Unix
Version = 20
Volume Index = 0
Offset = 0
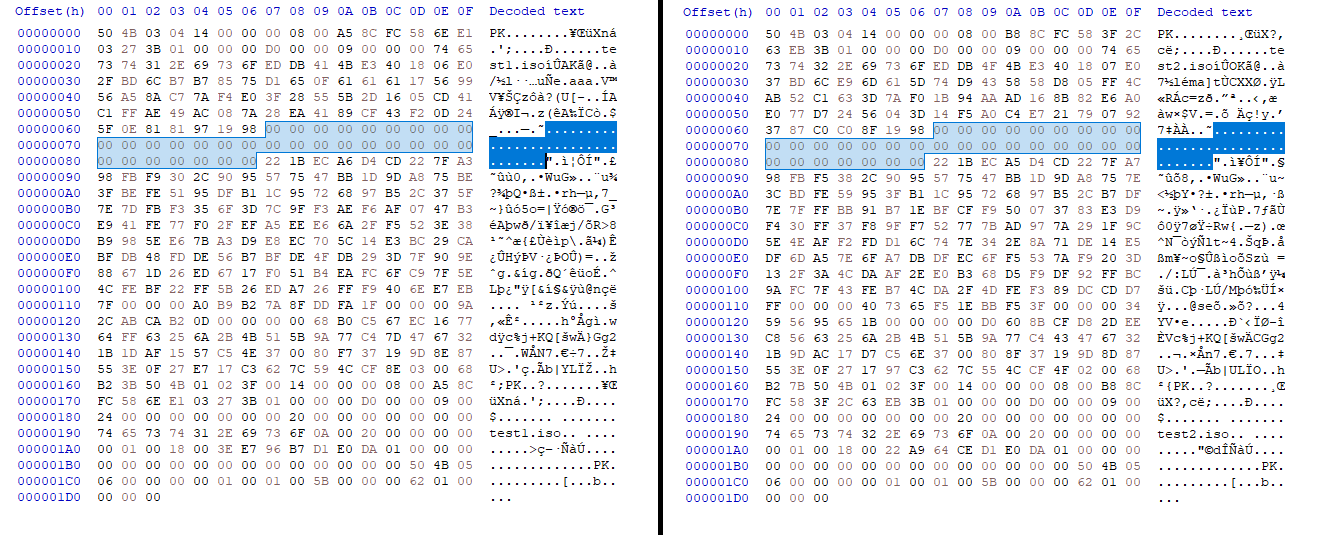
However, the ZipCrypto Deflate method essentially deflates the files before compressing them into a zip file, making the attack infeasible since a contiguous 8 bytes plaintext will be impossible to obtain. Spending hours on this, our teammate @Kibeth suggested that we generate our own deflated ISO files using the given Python script and compress them into unencrypted zip files to try and obtain any 12 byte plaintext that we might utilize.
Generating two samples, notice how both deflated ISO files that are compressed into unencrypted zip files have a consistent stream of null bytes. This was due to the nature of ISO files where they contain many sections of null bytes within them. So, instead of guessing a plaintext for the attack to work, an offset can be specified to read the section in the unencrypted zip file that has 12 null bytes for bkcrack to obtain the appropriate keys.
1
2
3
4
5
6
7
8
9
10
11
❯ .\bkcrack.exe -C challenge.zip -c challenge.iso -x 68 0000000000000000000000000000
bkcrack 1.7.0 - 2024-05-26
[19:01:52] Z reduction using 6 bytes of known plaintext
100.0 % (6 / 6)
[19:01:52] Attack on 1062600 Z values at index 75
Keys: 6b13ebc5 cc0be8ac 709e18f9
72.8 % (773877 / 1062600)
Found a solution. Stopping.
You may resume the attack with the option: --continue-attack 773877
[19:10:02] Keys
6b13ebc5 cc0be8ac 709e18f9
After obtaining the keys, the given zip file can be decrypted and the flag can be obtained.
1
2
3
4
❯ .\bkcrack.exe -C challenge.zip -k 6b13ebc5 cc0be8ac 709e18f9 -D unlock.zip
bkcrack 1.7.0 - 2024-05-26
[19:17:34] Writing decrypted archive unlock.zip
100.0 % (1 / 1)
Financial supporter 1 [OSINT]
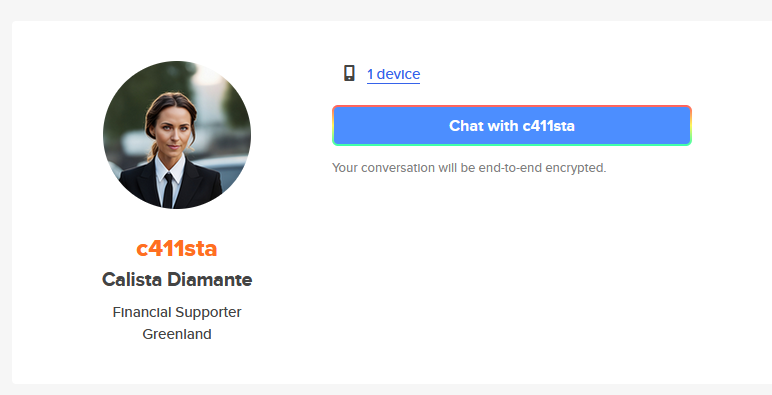
Question: You have received a secret mission, which is to attack a criminal organization. There is no information about this organization; we only know the name of the financial supporter for this organization, whose name is “Calista Diamante”. Your task is to find her weak points, then infiltrate and attack the company. First, let me know what phone she uses.
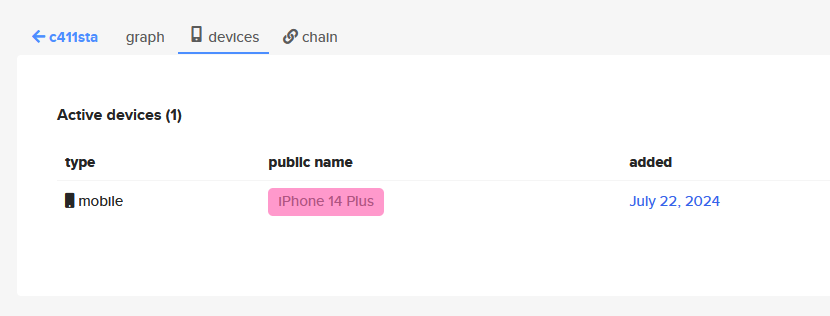
Flag: dead{iphone_14_plus}
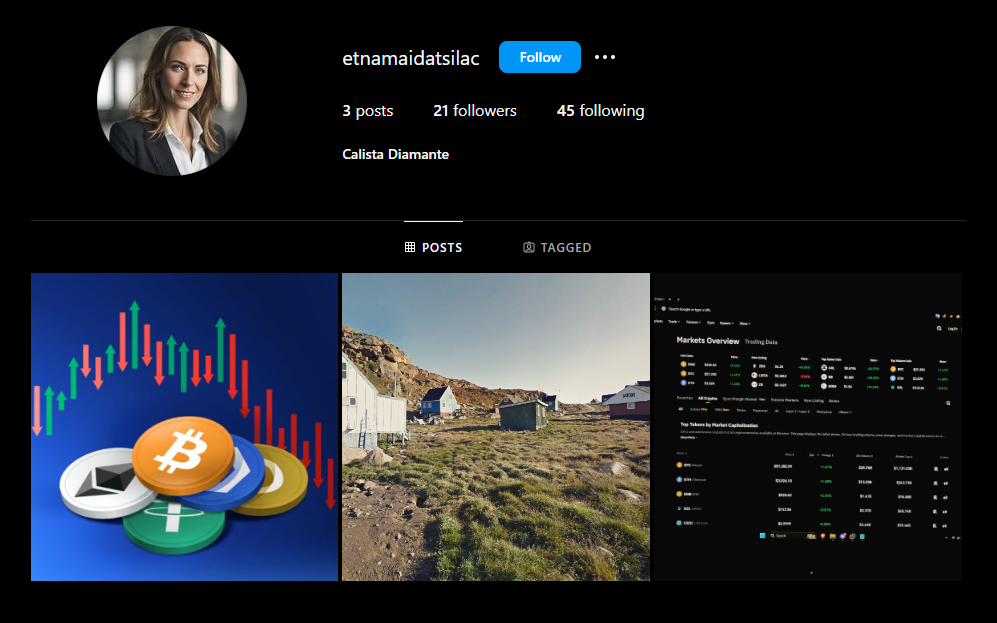
We are tasked to locate a criminal organization given the name of the financial supporter for this organization Calista Diamante. The user can be identified on Instagram, with a post having a hashtag that could be useful for the search.
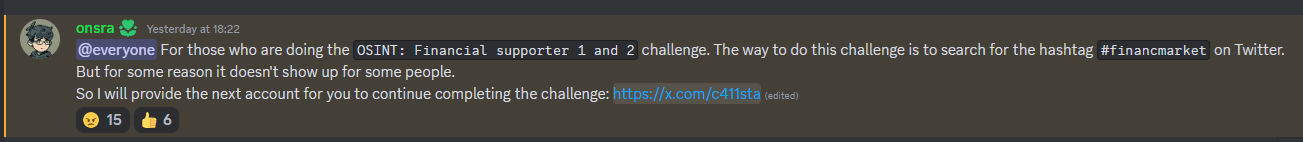
However, the hashtag could not give any results on X. After a few hours, the author gave us the X account saying that the challenge was broken (bruh).
So the username of Calista is identified as c411sta. Looking up the username on Sherlock, several accounts can be found.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ sherlock c411sta
[*] Checking username c411sta on:
[+] DailyMotion: https://www.dailymotion.com/c411sta
[+] Duolingo: https://www.duolingo.com/profile/c411sta
[+] Fiverr: https://www.fiverr.com/c411sta
[+] HackenProof (Hackers): https://hackenproof.com/hackers/c411sta
[+] ICQ: https://icq.im/c411sta/en
[+] Instagram: https://instagram.com/c411sta
[+] Keybase: https://keybase.io/c411sta
[+] LibraryThing: https://www.librarything.com/profile/c411sta
[+] mastodon.social: https://mastodon.social/@c411sta
[*] Search completed with 9 results
One of the scrapped accounts was Keybase which stored the information of her mobile device.
Financial supporter 2 [OSINT]
Question: Very good, you have obtained information about her phone. Dig deeper and let me know what secret she is keeping.
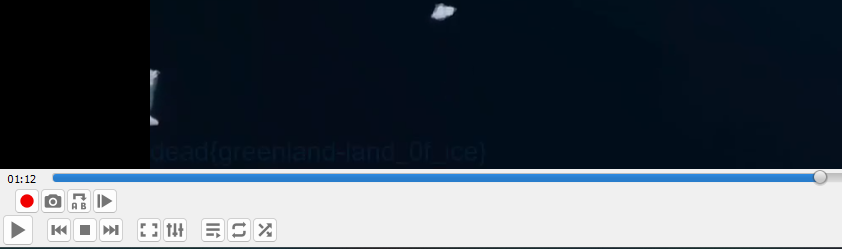
Flag: dead{greenland-land_0f_ice}
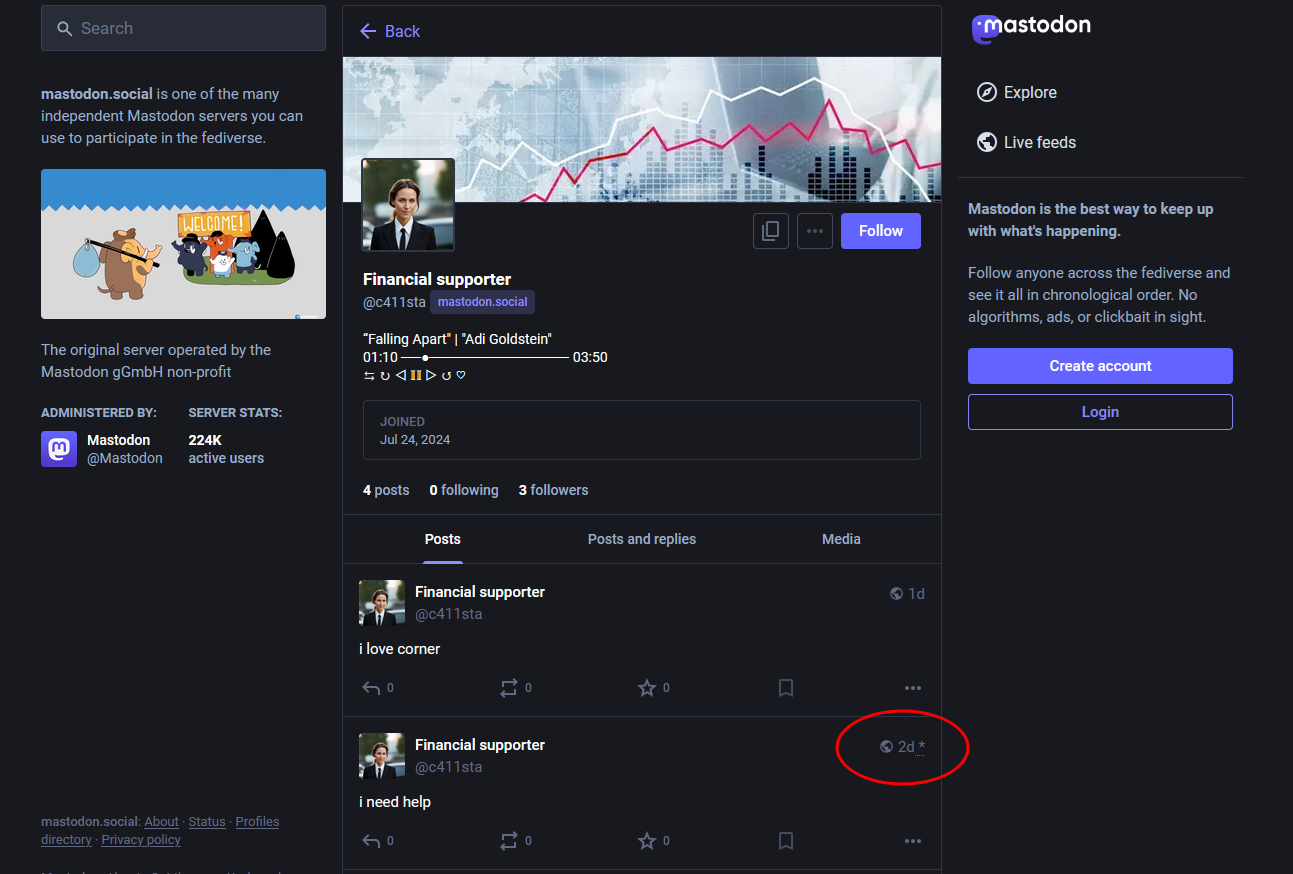
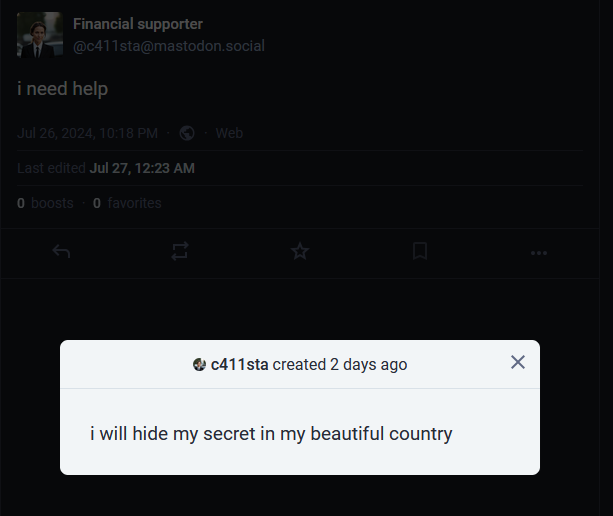
Checking her Mastodon account, one of her post was previously edited 3 times. The earliest edit mentioned hiding a secret in my beautiful country.
Checking her DailyMotion account, a weird text can be found on the account status. My teammate @Aquora found out that the weird text can be used as a URI in DailyMotion to access a private video titled My beautiful country. After spending a few hours, the flag can be found in the video frames. PS: using ‘E’ can view the video frame-by-frame on VLC.
Financial supporter 3 [OSINT]
Question: It seems they sent a stealth expert to rescue her from our pursuit. Let’s try to find information about him. Let me know what his alias is???
Flag: dead{beck}
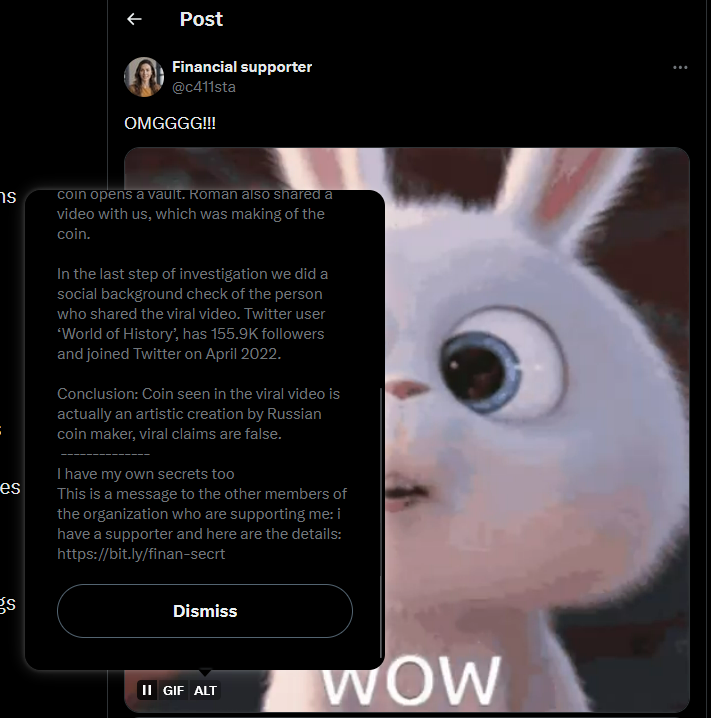
Continuing the search, my teammate @Aquora found a secret URL in one of the GIF posted in X.
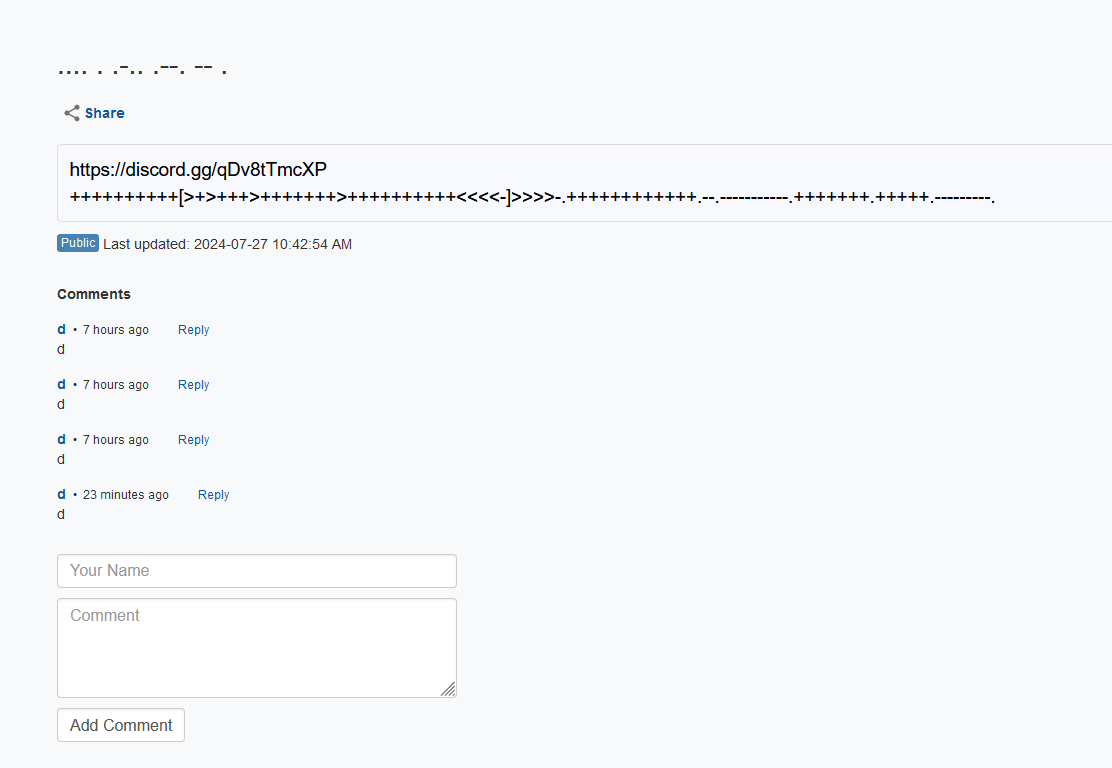
The URL leads us to a page with a Discord server link.
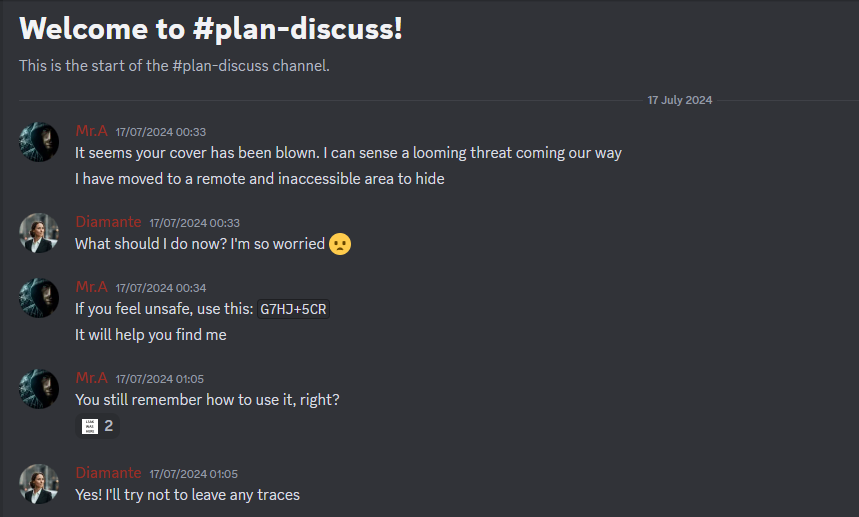
The Discord server had some information about the person.
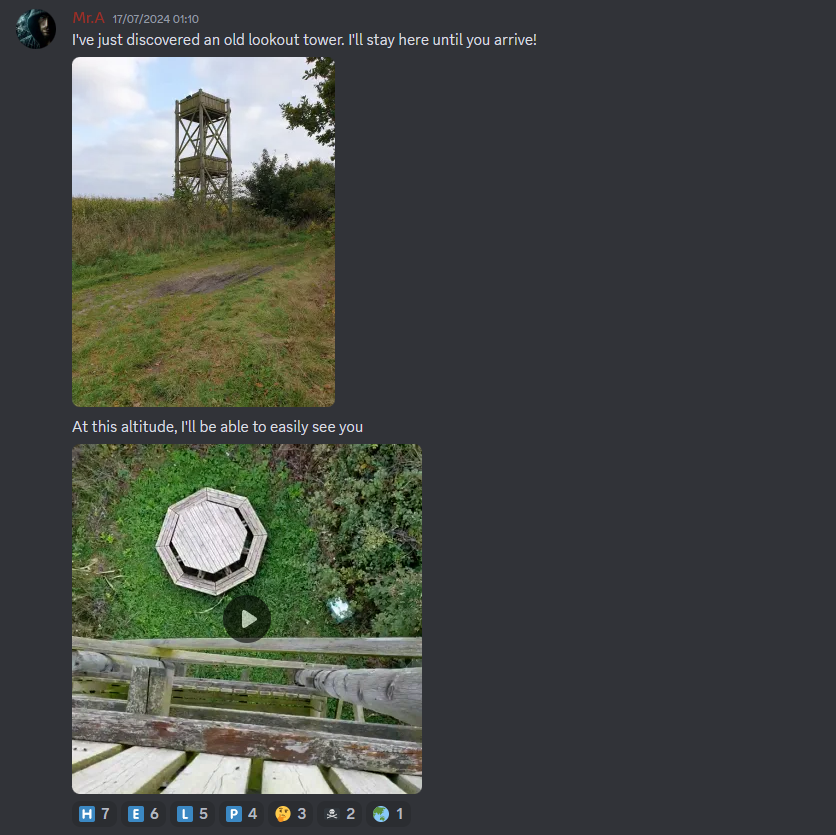
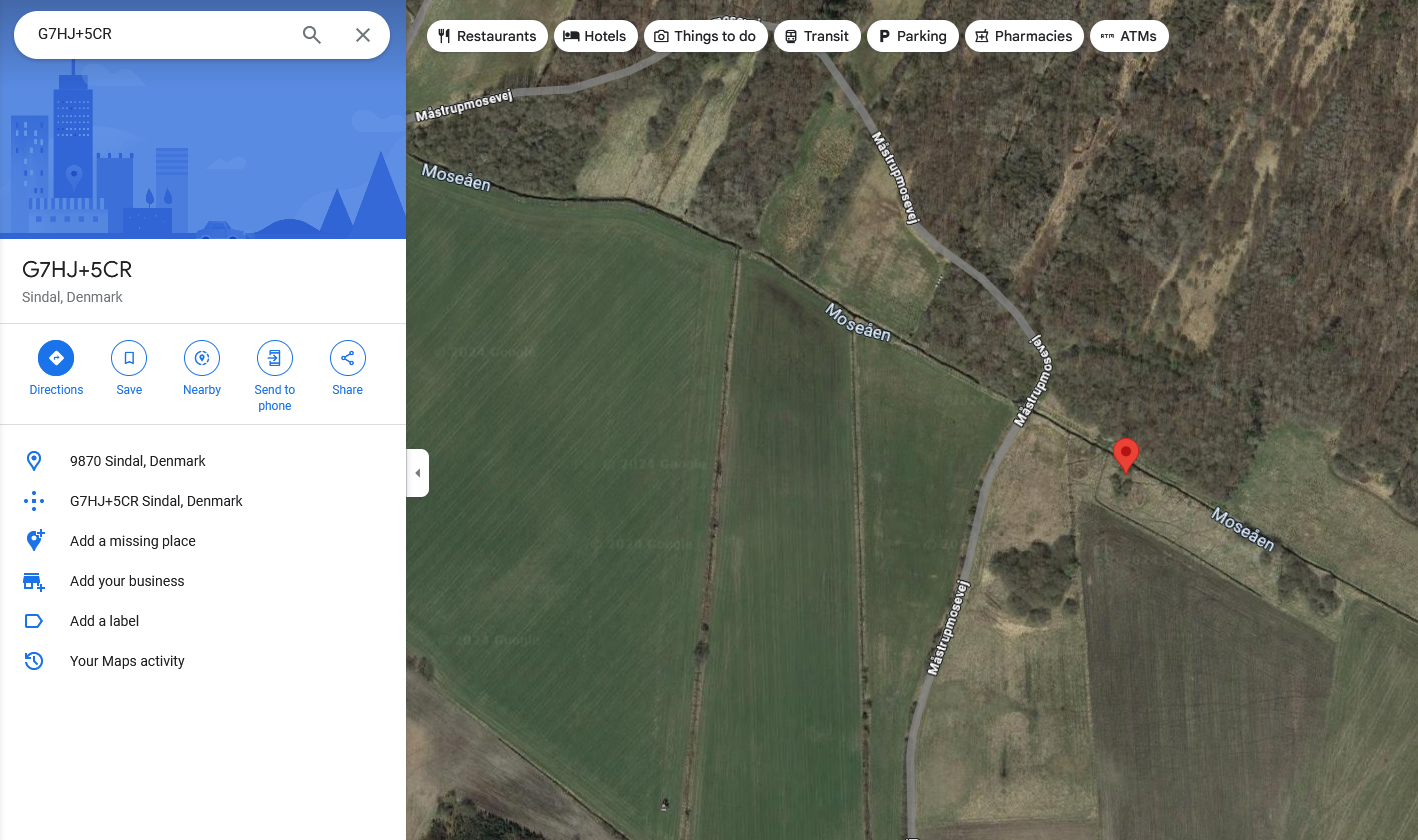
At this point, me and my teammates was super exhausted and did not solve it in time. However, the authors gave the official writeup on it so I will credit it here. Apparently, the image of the watchtower could be reverse searched on Google (does not work consistently). One of the results will lead to this website that mentioned the location to be Måstrup Mose, Porsevej. Using the plus code given G7HJ+5CR, the exact location can be obtained.
The authors also provided hints during the CTF mentioning something about WiFi.
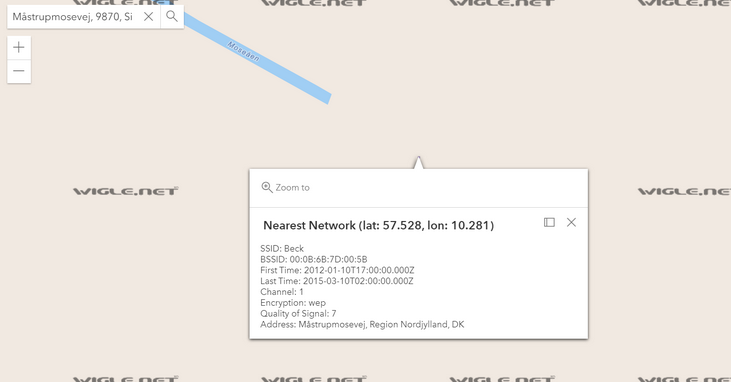
So by utilizing WiFi lookup sites like wigle, the alias can be identified on the SSID.