COMPFEST CTF 2024 - Writeups
This is a writeup for all forensics challenges from COMPFEST CTF 2024. Yet again L3ak managed to solve every challenge and achieve 🥇 on the CTF. Overall, the forensics challenges were really well made with no guessy aspects.
industrialspy 3 [Forensics]
Question: Dear X, I welcome you to the internship program at Collective Inc. Your first task is to figure out what happened to one of our servers. We have a suspicion that someone logged in and did something. We recovered some files to help you figure this out. If you have figured it out, submit your report to nc challenges.ctf.compfest.id 9009.
Flag: COMPFEST16{t00_3z_3vEN_f0R_4N_1ntErn_abdfe98ce2}
We were given a PCAP file to investigate and several questions to answer.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
└─$ nc challenges.ctf.compfest.id 9009
1. What ports are open on the attacked machine? (ex: 1,2,3,4)
22,5432
2. What is the credentials used to access the database? (ex: root:root)
server:changeme
3. What is the password for the "super" user on the database?
cafecoagroindustrialdelpacfico
4. What table does the attacker modify?
penalties
5. It seems that the attacker has modified their own data, what is their full name?
Lyubov Pryadko
Thank you for submitting your report. We will review it and get back to you as soon as possible.
COMPFEST16{t00_3z_3vEN_f0R_4N_1ntErn_abdfe98ce2}
Question 1: What ports are open on the attacked machine? (ex: 1,2,3,4)
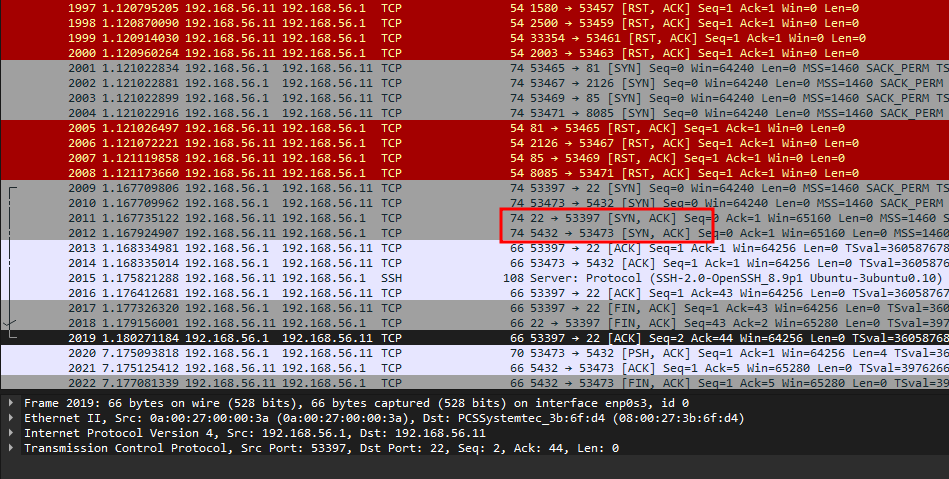
The attacker can be seen performing a SYN scan to enumerate the victim. Analyzing further, only port 22 and 5432 responded to the SYN packets with ACK.
Question 2: What is the credentials used to access the database? (ex: root:root)
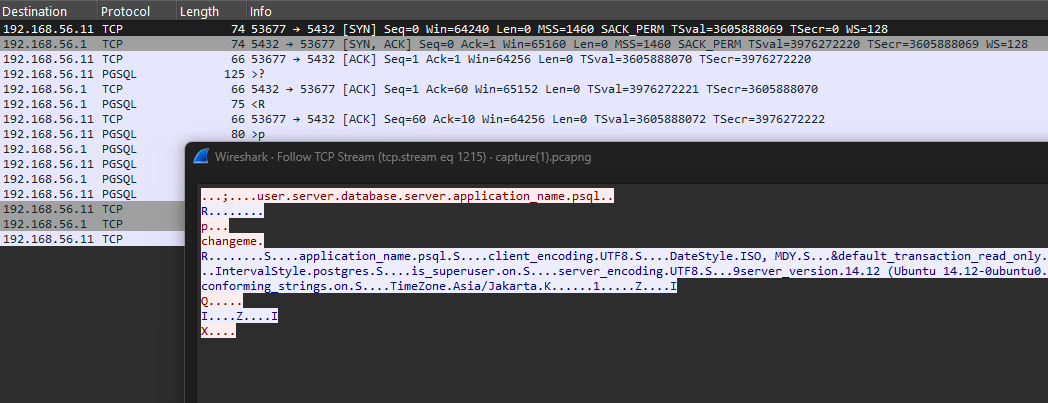
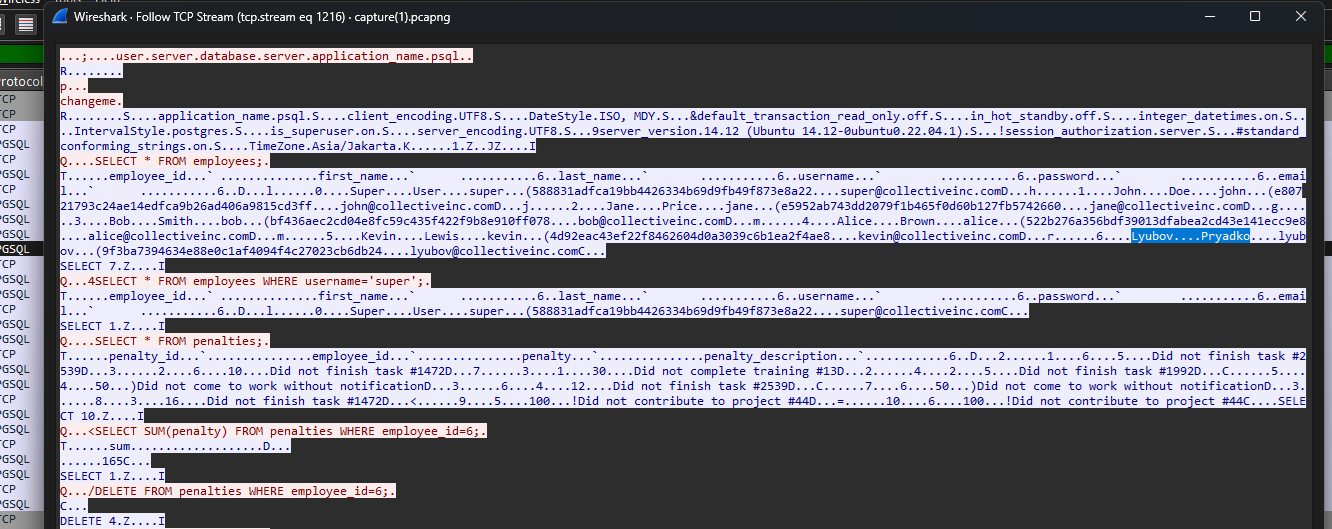
TCP stream 1215 shows the attacker successfully accessing the database with password changeme.
Question 3: What is the password for the “super” user on the database?
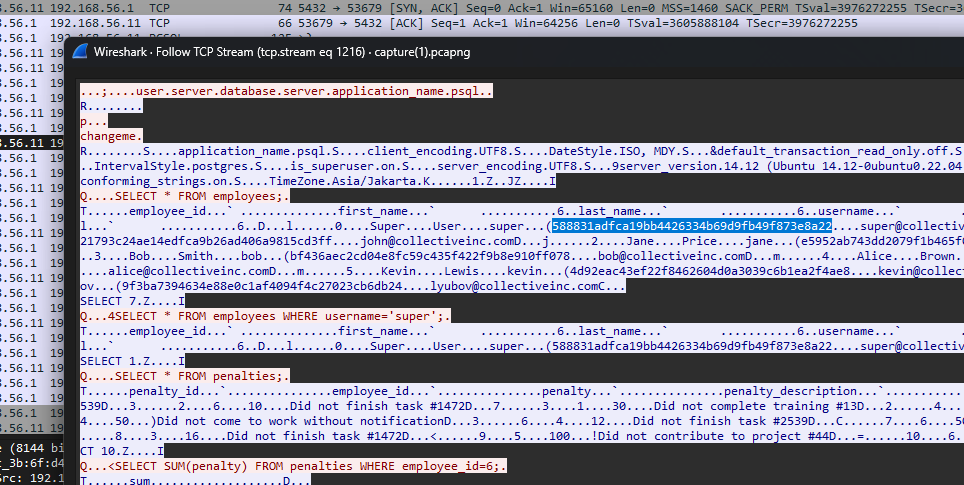
TCP stream 1216 shows the attacker viewing several tables after initial access. The password hash can be identified, with the cracked password being cafecoagroindustrialdelpacfico.
Question 4: What table does the attacker modify?
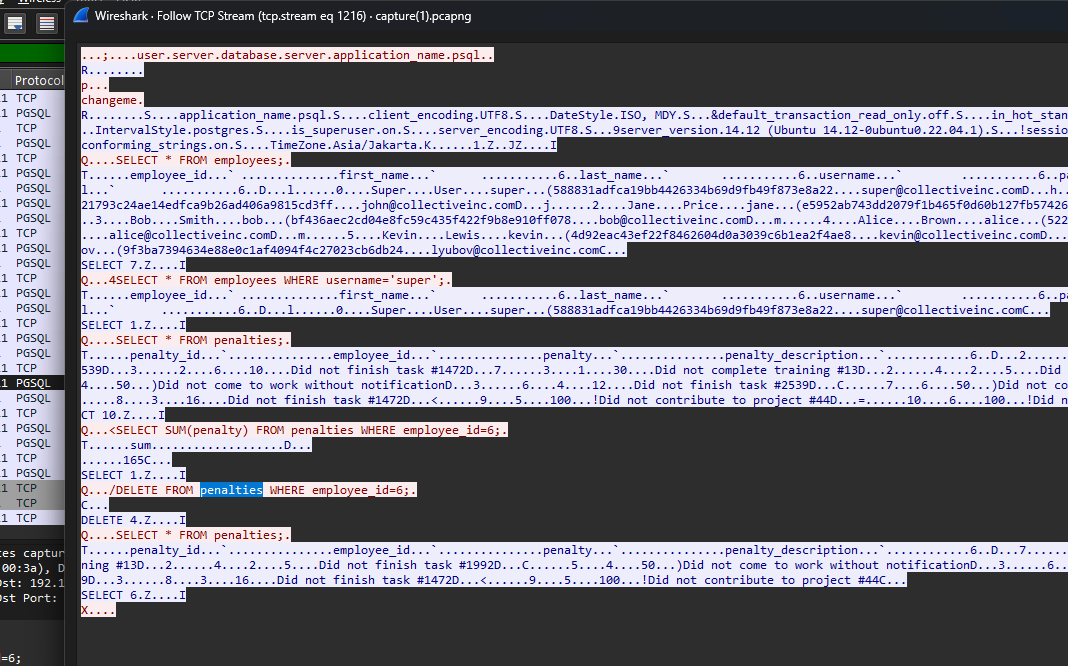
TCP stream 1216 shows the attacker performing a DELETE query on the table penalties.
Question 5: It seems that the attacker has modified their own data, what is their full name?
TCP stream 1216 shows the attacker deleting the entry for employee ID 6. Checking the employee table, the full name Lyubov Pryadko was identified to be the employee ID 6.
the dumb hacker [Forensics]
Question: Someone broke into my house and used my computer! Whoever they are, I don’t think they’re very smart.. They left the browser open. Can you figure out what they did to my computer?
Flag: COMPFEST16{h4ck3r_l3ft_4_N0t3_sA1d_tH4t_sm00thcr1m1nal_w4s_h3re_4dff1d3627}
We were given a Windows registry file to investigate. Analyzing the file manually, several search results can be identified on HKEY_USERS\target\Software\Microsoft\Internet Explorer\TypedURLs.
1
2
3
4
5
[HKEY_USERS\target\Software\Microsoft\Internet Explorer\TypedURLs]
"url1"="https://www.google.com/search?q=How+to+open+a+Docs+Folder%3F&rlz=1C1VDKB_enID1072ID1072&oq=How+to+open+a+Docs+Folder%3F&gs_lcrp=EgZjaHJvbWUyBggAEEUYOTIICAEQABgWGB4yCAgCEAAYFhgeMggIAxAAGBYYHjIICAQQABgWGB4yCAgFEAAYFhgeMggIBhAAGBYYHjIICAcQABgWGB4yCAgIEAAYFhgeMg0ICRAAGIYDGIAEGIoF0gEIMTIyMmowajeoAgCwAgA&sourceid=chrome&ie=UTF-8"
"url2"="https://www.google.com/search?q=How+do+i+make+a+Document+File%3F&sca_esv=52ba8db68abe4d65&rlz=1C1VDKB_enID1072ID1072&sxsrf=ADLYWIKDXwVMcCYDZ91Y2qyN_GfVYJgfEg%3A1721381411546&ei=IzKaZryCIf-anesP2qKj6Ak&ved=0ahUKEwj8n7u85bKHAxV_TWcHHVrRCJ0Q4dUDCA8&uact=5&oq=How+do+i+make+a+Document+File%3F&gs_lp=Egxnd3Mtd2l6LXNlcnAiHkhvdyBkbyBpIG1ha2UgYSBEb2N1bWVudCBGaWxlPzIGEAAYFhgeMgYQABgWGB4yBhAAGBYYHjIGEAAYFhgeMgYQABgWGB4yBhAAGBYYHjIGEAAYFhgeMgYQABgWGB4yCBAAGBYYHhgPMggQABgWGB4YD0iSFFCMDFiMDHADeAGQAQCYAXagAXaqAQMwLjG4AQPIAQD4AQL4AQGYAgSgApABwgIKEAAYsAMY1gQYR5gDAIgGAZAGCJIHAzMuMaAHiwg&sclient=gws-wiz-serp"
"url3"="https://www.google.com/search?q=Can+the+computer%27s+owner+do+a+User+Activity+Tracking+to+check+what+i+have+Accessed%3F&sca_esv=52ba8db68abe4d65&rlz=1C1VDKB_enID1072ID1072&sxsrf=ADLYWIJlyVBxYCaGBYPn_7EqRmmvxqfMhg%3A1721381584706&ei=0DKaZvjkKrus4-EP76GoiAY&ved=0ahUKEwj4jISP5rKHAxU71jgGHe8QCmEQ4dUDCA8&uact=5&oq=Can+the+computer%27s+owner+do+a+User+Activity+Tracking+to+check+what+i+have+Accessed%3F&gs_lp=Egxnd3Mtd2l6LXNlcnAiU0NhbiB0aGUgY29tcHV0ZXIncyBvd25lciBkbyBhIFVzZXIgQWN0aXZpdHkgVHJhY2tpbmcgdG8gY2hlY2sgd2hhdCBpIGhhdmUgQWNjZXNzZWQ_MgoQABiwAxjWBBhHMgoQABiwAxjWBBhHMgoQABiwAxjWBBhHMgoQABiwAxjWBBhHMgoQABiwAxjWBBhHMgoQABiwAxjWBBhHMgoQABiwAxjWBBhHMgoQABiwAxjWBBhHSIMVUPYMWPYMcAN4AZABAJgBAKABAKoBALgBA8gBAPgBAvgBAZgCA6ACD5gDAIgGAZAGCJIHATOgBwA&sclient=gws-wiz-serp"
"url4"="https://www.google.com/search?q=How+to+open+Paint+App+on+a+computer&sca_esv=52ba8db68abe4d65&rlz=1C1VDKB_enID1072ID1072&sxsrf=ADLYWIIJbu9_cFQRxKU44d2aPdWVsfKsfw%3A1721381613121&ei=7TKaZsyPB42I4-EP-d6ViAE&ved=0ahUKEwiMusqc5rKHAxUNxDgGHXlvBREQ4dUDCA8&uact=5&oq=How+to+open+Paint+App+on+a+computer&gs_lp=Egxnd3Mtd2l6LXNlcnAiI0hvdyB0byBvcGVuIFBhaW50IEFwcCBvbiBhIGNvbXB1dGVyMgUQIRigAUjdBlAAWABwAHgBkAEAmAGAAaABgAGqAQMwLjG4AQPIAQD4AQL4AQGYAgGgAokBmAMAkgcDMC4xoAfcAQ&sclient=gws-wiz-serp"
The first search was something about opening “Docs Folder”. Analyzing the registries related to this, the first part of the flag can be identified as a value on HKEY_USERS\target\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\Folder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
[HKEY_USERS\target\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\Folder]
"MRUListEx"=hex:01,00,00,00,00,00,00,00,ff,ff,ff,ff
"0"=hex:44,00,6f,00,77,00,6e,00,6c,00,6f,00,61,00,64,00,73,00,00,00,68,00,32,\
00,00,00,00,00,00,00,00,00,00,00,44,6f,77,6e,6c,6f,61,64,73,2e,6c,6e,6b,00,\
4c,00,09,00,04,00,ef,be,00,00,00,00,00,00,00,00,2e,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,44,00,6f,00,\
77,00,6e,00,6c,00,6f,00,61,00,64,00,73,00,2e,00,6c,00,6e,00,6b,00,00,00,1c,\
00,00,00
"1"=hex:73,00,6d,00,30,00,30,00,74,00,68,00,63,00,72,00,31,00,6d,00,31,00,6e,\
00,61,00,6c,00,00,00,78,00,32,00,00,00,00,00,00,00,00,00,00,00,73,6d,30,30,\
74,68,63,72,31,6d,31,6e,61,6c,2e,6c,6e,6b,00,00,56,00,09,00,04,00,ef,be,00,\
00,00,00,00,00,00,00,2e,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,73,00,6d,00,30,00,30,00,74,00,68,00,63,\
00,72,00,31,00,6d,00,31,00,6e,00,61,00,6c,00,2e,00,6c,00,6e,00,6b,00,00,00,\
22,00,00,00
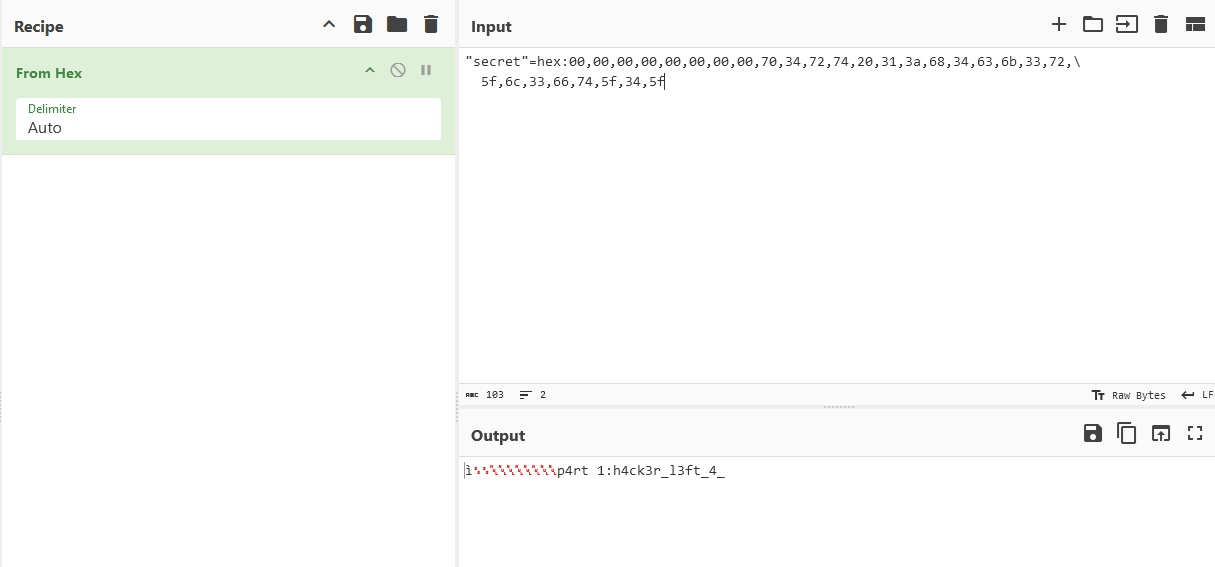
"secret"=hex:00,00,00,00,00,00,00,00,70,34,72,74,20,31,3a,68,34,63,6b,33,72,\
5f,6c,33,66,74,5f,34,5f
The second search was something about making a Document file. Analyzing the registries related to this, no results could be obtained on HKEY_USERS\target\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.doc. However, it seems that the second part of the flag can be identified as a value on HKEY_USERS\target\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.txt instead.
1
2
3
4
5
6
7
8
9
10
[HKEY_USERS\target\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.txt]
"0"=hex:66,00,69,00,6c,00,65,00,31,00,2e,00,74,00,78,00,74,00,00,00,5c,00,32,\
00,00,00,00,00,00,00,00,00,00,00,66,69,6c,65,31,2e,6c,6e,6b,00,44,00,09,00,\
04,00,ef,be,00,00,00,00,00,00,00,00,2e,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,66,00,69,00,6c,00,65,00,\
31,00,2e,00,6c,00,6e,00,6b,00,00,00,18,00,00,00
"MRUListEx"=hex:00,00,00,00,ff,ff,ff,ff
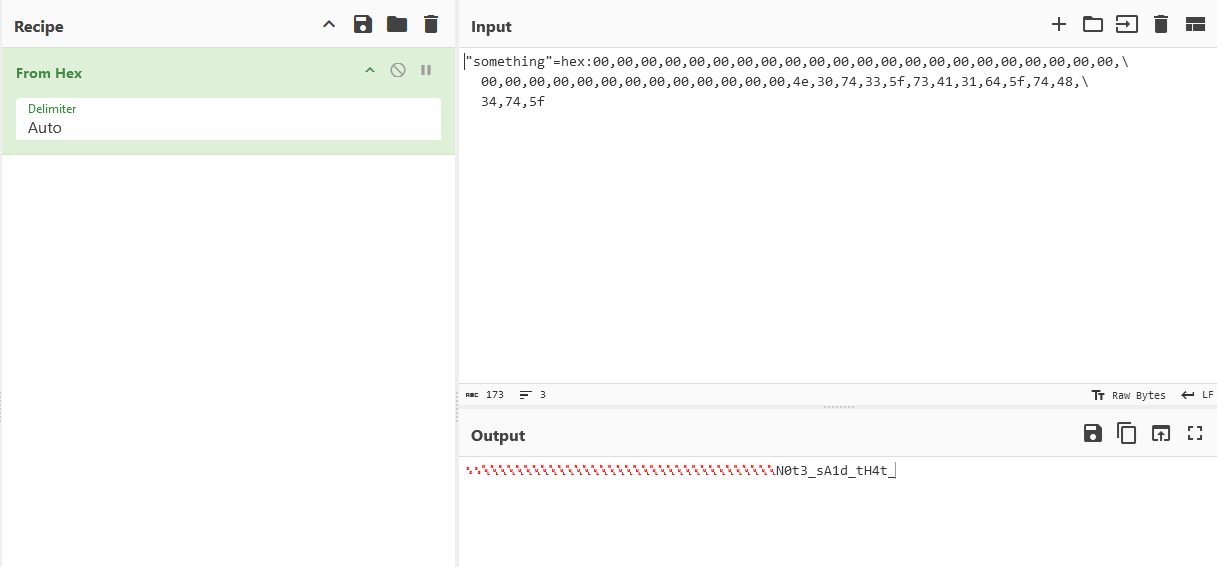
"something"=hex:00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,4e,30,74,33,5f,73,41,31,64,5f,74,48,\
34,74,5f
The last 2 searches was something about “User Activity Tracking” and opening Microsoft Paint. Analyzing the registries related to this,
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
[HKEY_USERS\target\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count]
"HRZR_PGYPHNPbhag:pgbe"=hex:ff,ff,ff,ff,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,00,00,00,00,00,00,00,\
00,00,00,00,00
"Zvpebfbsg.Trgfgnegrq_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,0e,00,00,00,15,00,00,\
00,a0,68,06,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,\
00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,0f,\
4a,0d,19,f2,d6,da,01,00,00,00,00
"HRZR_PGYFRFFVBA"=hex:00,00,00,00,47,00,00,00,88,00,00,00,6f,b6,34,00,0e,00,00,\
00,15,00,00,00,a0,68,06,00,4d,00,69,00,63,00,72,00,6f,00,73,00,6f,00,66,00,\
74,00,2e,00,47,00,65,00,74,00,73,00,74,00,61,00,72,00,74,00,65,00,64,00,5f,\
00,38,00,77,00,65,00,6b,00,79,00,62,00,33,00,64,00,38,00,62,00,62,00,77,00,\
65,00,21,00,41,00,70,00,70,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,0e,00,00,00,15,00,00,00,a0,68,06,00,4d,00,69,00,63,00,72,00,6f,\
00,73,00,6f,00,66,00,74,00,2e,00,47,00,65,00,74,00,73,00,74,00,61,00,72,00,\
74,00,65,00,64,00,5f,00,38,00,77,00,65,00,6b,00,79,00,62,00,33,00,64,00,38,\
00,62,00,62,00,77,00,65,00,21,00,41,00,70,00,70,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,0e,00,00,00,15,00,00,00,a0,68,06,00,4d,00,\
69,00,63,00,72,00,6f,00,73,00,6f,00,66,00,74,00,2e,00,47,00,65,00,74,00,73,\
00,74,00,61,00,72,00,74,00,65,00,64,00,5f,00,38,00,77,00,65,00,6b,00,79,00,\
62,00,33,00,64,00,38,00,62,00,62,00,77,00,65,00,21,00,41,00,70,00,70,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,\
00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00,00
"Zvpebfbsg.JvaqbjfSrrqonpxUho_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,0c,00,00,00,\
12,00,00,00,60,4f,05,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,\
00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,\
ff,ff,0f,4a,0d,19,f2,d6,da,01,00,00,00,00
"Zvpebfbsg.ZvpebfbsgFgvpxlAbgrf_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,0a,00,00,00,\
0f,00,00,00,20,36,04,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,\
00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,\
ff,ff,0f,4a,0d,19,f2,d6,da,01,00,00,00,00
"Zvpebfbsg.JvaqbjfPnyphyngbe_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,08,00,00,00,0c,\
00,00,00,e0,1c,03,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,\
ff,0f,4a,0d,19,f2,d6,da,01,00,00,00,00
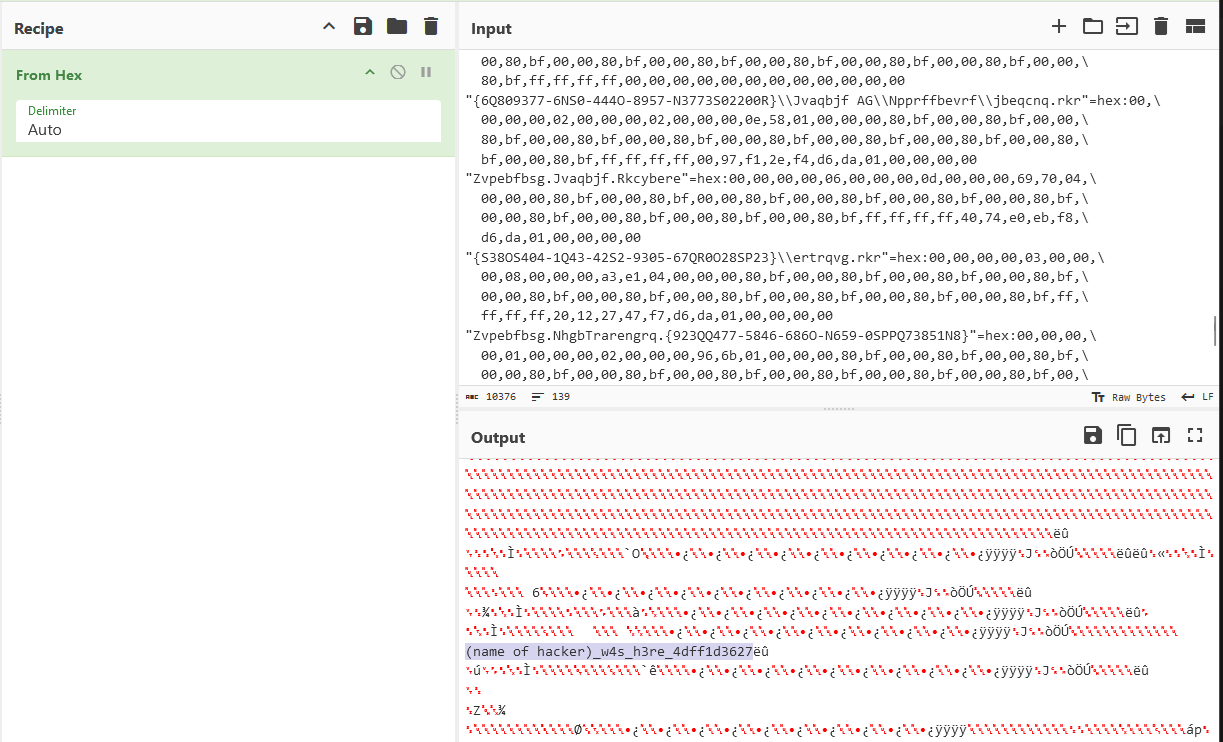
"Zvpebfbsg.Cnvag_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,06,00,00,00,09,00,00,00,a0,\
03,02,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,0f,4a,0d,\
19,f2,d6,da,01,00,00,00,00,00,00,00,00,00,00,00,00,28,6e,61,6d,65,20,6f,66,\
20,68,61,63,6b,65,72,29,5f,77,34,73,5f,68,33,72,65,5f,34,64,66,66,31,64,33,\
36,32,37
"Zvpebfbsg.JvaqbjfAbgrcnq_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,04,00,00,00,06,00,\
00,00,60,ea,00,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,\
bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,\
0f,4a,0d,19,f2,d6,da,01,00,00,00,00
"ZvpebfbsgJvaqbjf.Pyvrag.POF_pj5a1u2gklrjl!PbegnanHV"=hex:00,00,00,00,00,00,00,\
00,07,00,00,00,d8,06,03,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,\
00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,\
ff,ff,ff,00,00,00,00,00,00,00,00,00,00,00,00
"ZFRqtr"=hex:00,00,00,00,03,00,00,00,11,00,00,00,e1,70,08,00,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,\
bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,e0,cb,ec,e7,f8,d6,da,01,00,00,00,00
"IvfhnyFghqvb.1815p290"=hex:00,00,00,00,01,00,00,00,03,00,00,00,8c,94,04,00,00,\
00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,60,5f,44,4b,f3,d6,da,\
01,00,00,00,00
"Zvpebfbsg.Jvaqbjf.FgnegZrahRkcrevraprUbfg_pj5a1u2gklrjl!Ncc"=hex:00,00,00,00,\
00,00,00,00,01,00,00,00,70,5f,01,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,\
00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,ff,ff,ff,ff,00,00,00,00,00,00,00,00,00,00,00,00
"{6Q809377-6NS0-444O-8957-N3773S02200R}\\Jvaqbjf AG\\Npprffbevrf\\jbeqcnq.rkr"=hex:00,\
00,00,00,02,00,00,00,02,00,00,00,0e,58,01,00,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,\
bf,00,00,80,bf,ff,ff,ff,ff,00,97,f1,2e,f4,d6,da,01,00,00,00,00
"Zvpebfbsg.Jvaqbjf.Rkcybere"=hex:00,00,00,00,06,00,00,00,0d,00,00,00,69,70,04,\
00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,\
00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,ff,40,74,e0,eb,f8,\
d6,da,01,00,00,00,00
"{S38OS404-1Q43-42S2-9305-67QR0O28SP23}\\ertrqvg.rkr"=hex:00,00,00,00,03,00,00,\
00,08,00,00,00,a3,e1,04,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,\
00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,\
ff,ff,ff,20,12,27,47,f7,d6,da,01,00,00,00,00
"Zvpebfbsg.NhgbTrarengrq.{923QQ477-5846-686O-N659-0SPPQ73851N8}"=hex:00,00,00,\
00,01,00,00,00,02,00,00,00,96,6b,01,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,\
00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,\
00,80,bf,ff,ff,ff,ff,50,96,cc,f7,f6,d6,da,01,00,00,00,00
"{1NP14R77-02R7-4R5Q-O744-2RO1NR5198O7}\\pzq.rkr"=hex:00,00,00,00,01,00,00,00,\
00,00,00,00,00,00,00,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,\
00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,\
ff,ff,10,f1,9b,da,f7,d6,da,01,00,00,00,00
"Zvpebfbsg.JvaqbjfGrezvany_8jrxlo3q8oojr!Ncc"=hex:00,00,00,00,00,00,00,00,01,\
00,00,00,db,2e,01,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,ff,ff,ff,\
ff,00,00,00,00,00,00,00,00,00,00,00,00
"Zvpebfbsg.Jvaqbjf.FuryyRkcrevraprUbfg_pj5a1u2gklrjl!Ncc"=hex:00,00,00,00,00,\
00,00,00,01,00,00,00,2f,0d,00,00,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,\
80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,bf,00,00,80,\
bf,ff,ff,ff,ff,00,00,00,00,00,00,00,00,00,00,00,00
However, the flag was still incomplete. It required the name of the hacker in this challenge.
1
COMPFEST16{h4ck3r_l3ft_4_N0t3_sA1d_tH4t_(name of hacker)_w4s_h3re_4dff1d3627}
Analyzing any registry hive with a folder location from the C drive, the hacker’s name can be identfied as sm00thcr1m1nal.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
[HKEY_USERS\target\Control Panel\NotifyIconSettings\6619948649619800705]
"UID"=dword:000001f5
"ExecutablePath"="C:\\Users\\sm00thcr1m1nal\\AppData\\Local\\Microsoft\\OneDrive\\OneDrive.exe"
"InitialTooltip"=""
"IconSnapshot"=hex:89,50,4e,47,0d,0a,1a,0a,00,00,00,0d,49,48,44,52,00,00,00,10,\
00,00,00,10,08,06,00,00,00,1f,f3,ff,61,00,00,00,01,73,52,47,42,00,ae,ce,1c,\
e9,00,00,00,04,67,41,4d,41,00,00,b1,8f,0b,fc,61,05,00,00,01,ad,49,44,41,54,\
38,4f,cd,53,c1,4a,02,51,14,bd,63,26,a1,a2,0d,84,06,ba,08,75,ab,38,e8,be,d9,\
b9,92,44,70,e5,42,03,09,fc,80,c0,9d,2b,85,08,52,f7,8a,f9,05,d6,1f,e8,42,71,\
23,ba,9c,95,a4,e8,22,0a,9c,40,c9,dd,74,cf,d8,44,41,20,d8,a6,03,87,7b,cf,bd,\
ef,9e,79,8f,f7,86,fe,15,ee,99,d9,6d,4a,09,e6,03,53,65,6a,9f,11,fd,63,e6,0f,\
08,9f,11,c0,70,93,79,09,21,49,d2,6d,28,14,3a,41,3e,9f,cf,97,bd,5e,cf,b4,d9,\
6c,20,65,e6,18,09,60,18,9c,31,ab,cc,0b,5d,b1,49,b1,58,44,84,a1,0e,0c,d7,6a,\
b5,37,8e,4f,2c,c3,db,2a,d1,01,13,c3,63,51,14,3d,a9,54,4a,f0,f9,7c,87,8a,a2,\
24,ba,dd,ee,a3,2c,cb,8f,dc,c3,71,c8,6c,36,53,20,10,38,1a,0e,87,a7,2c,25,e6,\
80,a9,62,07,0f,56,ab,55,2e,95,4a,4e,8e,2c,89,fa,fd,3e,b5,5a,2d,a4,5f,3b,11,\
04,e1,dd,e1,70,bc,8e,46,23,6a,b7,db,8e,d5,6a,85,ba,0c,03,2d,9f,cf,53,38,fc,\
b5,2b,1d,df,4d,ea,f5,ba,e8,72,b9,ee,f4,06,63,bd,5e,53,a1,50,78,9e,4e,a7,8a,\
09,05,e3,cb,df,91,4c,26,9f,cb,e5,32,d2,66,2e,97,5b,7a,3c,9e,1b,8b,c5,f2,8a,\
82,cd,66,a3,74,3a,ed,e6,f4,1c,06,d3,c9,64,b2,44,83,cf,b9,f4,fb,fd,6f,b1,58,\
8c,a2,d1,a8,3b,93,c9,50,a5,52,41,ab,19,89,44,94,60,30,78,ed,f5,7a,37,38,0e,\
4c,0c,54,ed,76,bb,da,e9,74,b4,c5,62,f1,2b,d9,04,6f,01,cc,b2,ce,ce,66,33,2d,\
1e,8f,bf,b0,d6,af,13,b7,a0,3a,9d,4e,b5,d1,68,68,83,c1,60,a7,09,af,bb,32,72,\
a6,0e,98,e0,e5,19,8b,76,11,83,98,d9,0b,18,36,4c,f6,06,86,f1,6f,fc,15,44,1f,\
c6,25,c7,9a,73,3e,64,5e,00,00,00,00,49,45,4e,44,ae,42,60,82
"IsPromoted"=dword:00000001
head’s up! [Forensics]
Question: Oh no! My mischievous cat decided to play with my laptop and now all my important files are missing! The only thing left is this single, mysterious file. Can you help me retrieve all my important files?
Flag: COMPFEST16{lO0kS_l1k3_u_k3pt_Ur_hE4D_uP!_22a4b9bdf7}
We were given a ZIP file to investigate.
1
2
└─$ file file
file: Zip archive data, at least v2.0 to extract, compression method=deflate
Inside the ZIP file were two TXT files, one was the first part of the flag while the other was gibberish.
1
2
3
4
5
└─$ cat flag.txt
COMPFEST16{lO0kS_
└─$ cat meong.txt
φΕλ ζβΦΥΞ ΓιΑΩοψΑΣΣΦΓΖΨΖλζΘρ
After some time, my teammate @Vivi’s_Ghost managed to identify something suspicious in the ZIP file. Analyzing the hex values, a PNG can be identified to be embedded into the ZIP file with a broken header.
Fixing the header will provide the second part of the flag.
1
2
3
4
5
6
7
8
9
└─$ binwalk --dd='.*' fixed.zip
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Zip archive data, at least v2.0 to extract, uncompressed size: 635, name: __MACOSX/._flag.txt
513 0x201 Zip archive data, at least v1.0 to extract, compressed size: 18, uncompressed size: 18, name: flag.txt
569 0x239 Zip archive data, at least v2.0 to extract, uncompressed size: 64, name: meong.txt
990 0x3DE End of Zip archive, footer length: 22
1012 0x3F4 PNG image, 1280 x 1280, 8-bit grayscale, non-interlaced
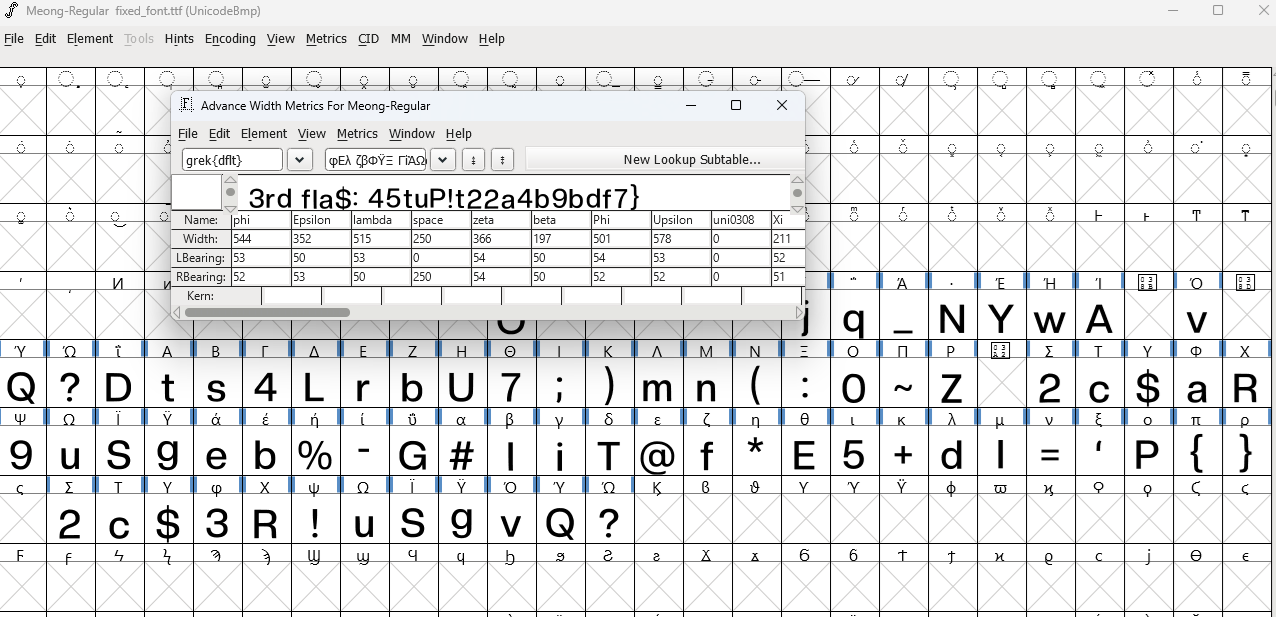
Another thing that was identified in the ZIP file was a TTF font file right after the PNG trailer. The header for the TTF font was broken too so manual fixing was required.
Fixing the header and carving it will provide the TTF font file used for meong.txt since to map the third part of the flag. (Automatic translation can be done on FontForge Window -> New Metrics Window)
loss [Forensics]
Question: lmao i just rm -rf ‘ed my usb drive. help me out plz.
Flag: COMPFEST16{g0D_bl3Ss_L1nU5_t0RV4ldS_7f3c45c4dc}
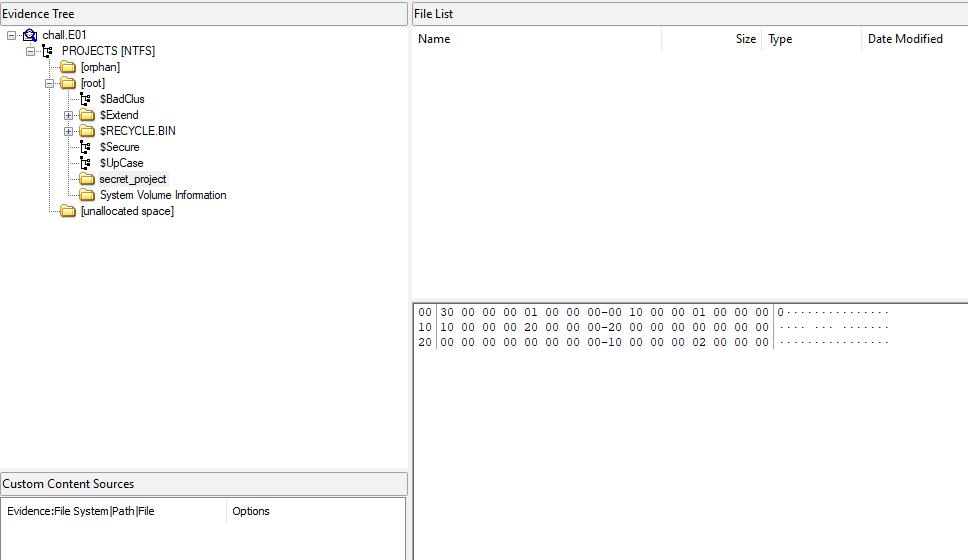
We were given an E01 image to investigate. After adding the appropriate file extension, the image can be analyzed on FTK Imager.
1
2
└─$ file chall
chall: EWF/Expert Witness/EnCase image file format
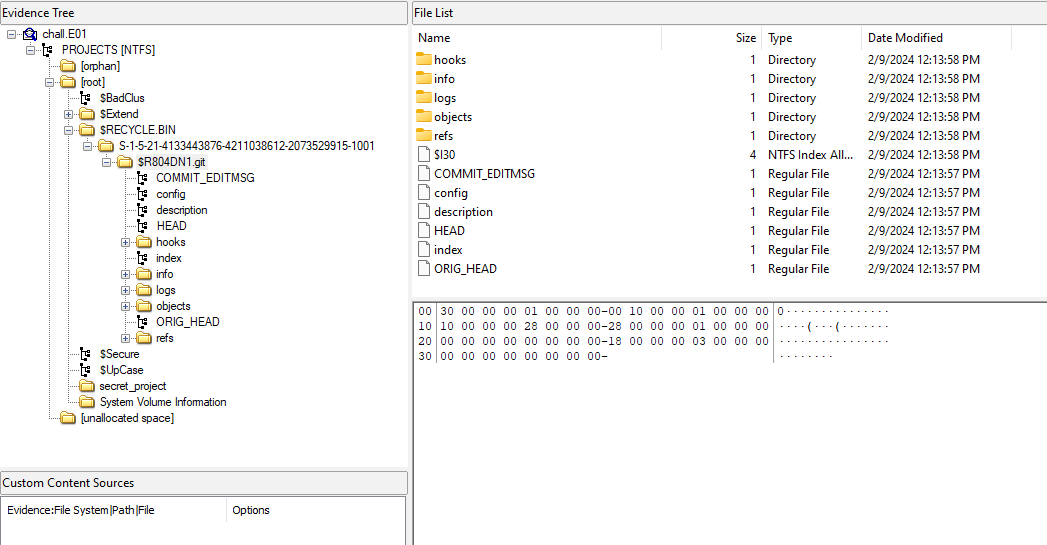
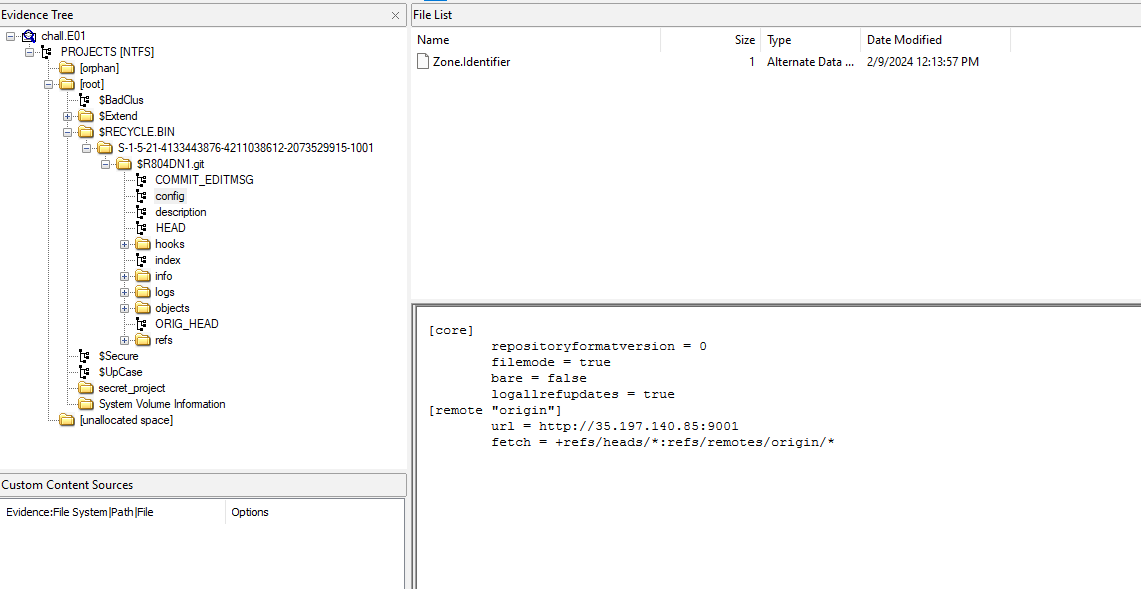
Inside the image was an empty folder and a deleted .git folder in the Recycle Bin.
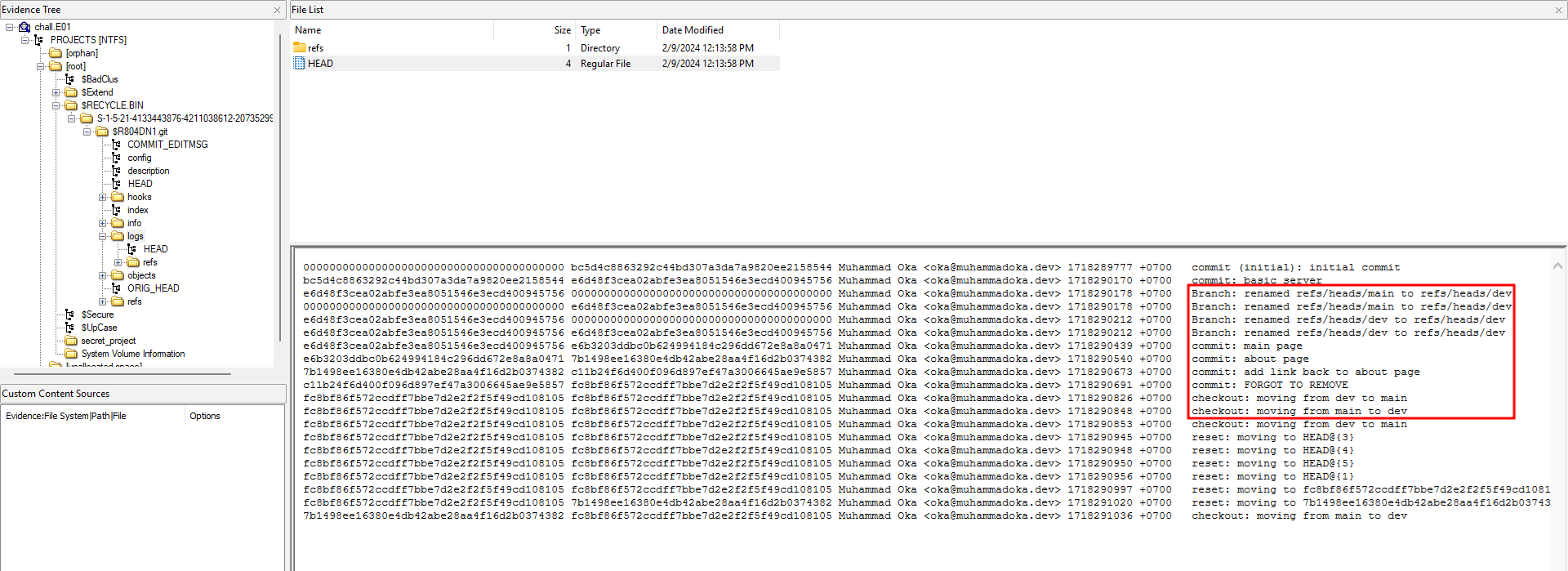
Analyzing the .git folder, a commit was done on a file on the dev branch.
Analyzing further, the server IP can be identified to be http://35.197.140.85:9001 on the config file. However, nothing could be dumped from the server with GitTools.
According to our teammate @MinatoTW, this was due to the rate limiting of the dumping tool. The current speed would not be able to extract all of the objects from the address. Another issue was the dumping tool had to pull the dev branch since that was the location where commits happened.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
# Download files with rate-limit
curl -L -A "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36" -f -k -s --limit-rate 1m "$url" -o "$target"
# Download files from dev branch
function start_download() {
#Add initial/static git files
QUEUE+=('HEAD')
QUEUE+=('objects/info/packs')
QUEUE+=('description')
QUEUE+=('config')
QUEUE+=('COMMIT_EDITMSG')
QUEUE+=('index')
QUEUE+=('packed-refs')
QUEUE+=('refs/heads/master')
QUEUE+=('refs/remotes/origin/HEAD')
QUEUE+=('refs/stash')
QUEUE+=('logs/HEAD')
QUEUE+=('logs/refs/heads/master')
QUEUE+=('logs/refs/remotes/origin/HEAD')
QUEUE+=('info/refs')
QUEUE+=('info/exclude')
QUEUE+=('/refs/wip/index/refs/heads/master')
QUEUE+=('/refs/wip/wtree/refs/heads/master')
QUEUE+=('refs/head/dev')
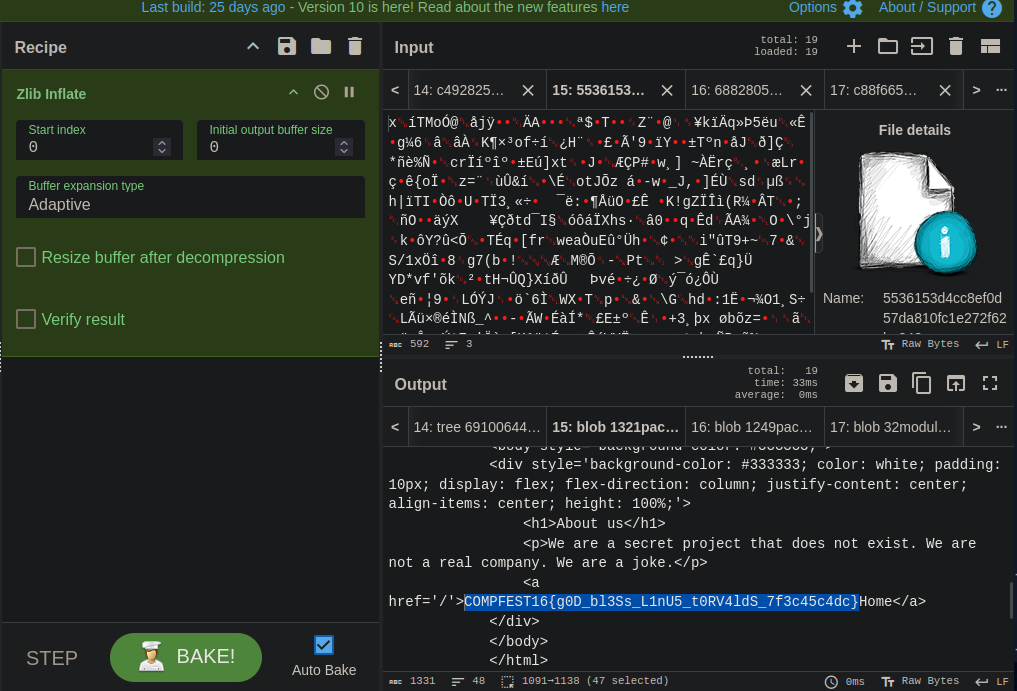
By modifying the dumping tool from GitTools, the commits can be retrieved. The flag can be obtained from one of the commits.