BYUCTF 2024 - Writeups
This is a writeup for all forensics challenges from BYUCTF 2024. Overall, the forensics challenges were fun but some of them were kinda guessy (and also very laggy thanks to the button). Shoutout to my teammate @ayam for solving two challenges that I was stuck at for so long.
Who Am I [Forensics]
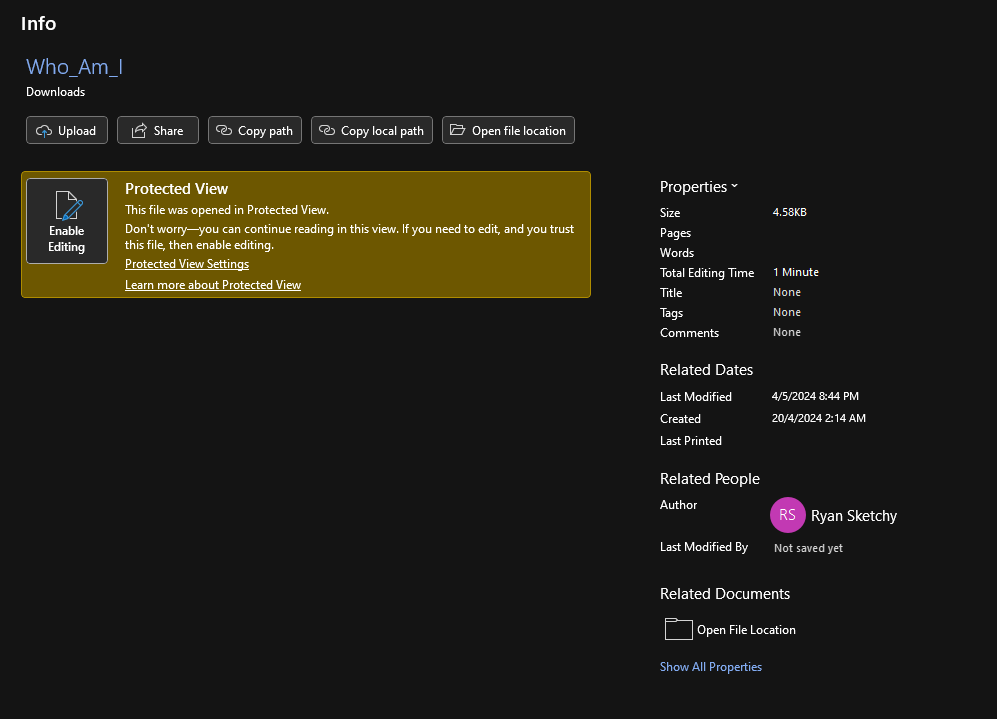
Question: We have a Word file placed on one of our machines by a cyber attacker. Who is the author of the document?
Flag: byuctf{Ryan Sketchy}
We are given a docx file to investigate. Just check the author’s name in the document itself.
Advanced Steak [Forensics]
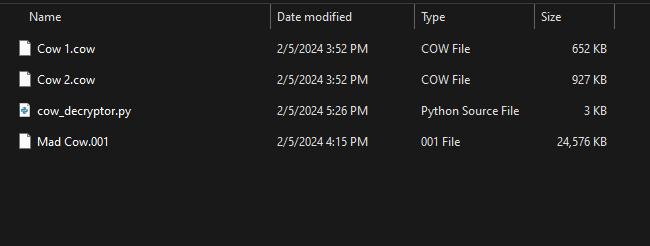
Question: The Mad Cow APT has been responsible for a significant amount of attacks against organizations in the technology, finance, and energy domains. They first started their attacks around 3 years ago, though they have been dormant in the last 2 years. Recently, the APT started to resurface. Field agents were able to conduct a raid against a known Mad Cow hideout. In the process, the agents pulled a flash drive from one of the Mad Cow computers. Unfortunately, it looks like one of the threat actors was able to begin wiping the flash drive with random data before the analyst pulled the drive. The field agent pulled the drive before the wipe was complete, but parts of the drive have been corrupted. Our team has already created a forensic image of the drive: Mad Cow.001. Analysts who studied the Mad Cow APT two years ago are highly confident that the APT is utilizing the same tactics as they have in previous years. One such tactic is communicating through a custom file type. Fortunately, one of analysts built a decryptor for this custom file type. Using this, we can turn any .cow files into a standard PNG. The decryptor does not offer any useful information on finding these files, however. Your job is to find any .cow files on the corrupted flash drive (Mad Cow.001) and pull them from the image file. You can use the two provided .cow files as reference to help understand what the files look like. Then, run any discovered .cow file(s) through the decryptor to determine if there is any useful data. The data will be in the format byuctf{flag}.
Note: this is not a reverse engineering challenge. The cow_decryptor.py is intentionally missing important data. You do not need to reverse engineer the script in order to find the file(s). This challenge can be solved without examining the cow_decryptor.py file.
Flag: byuctf{incredi-bull}
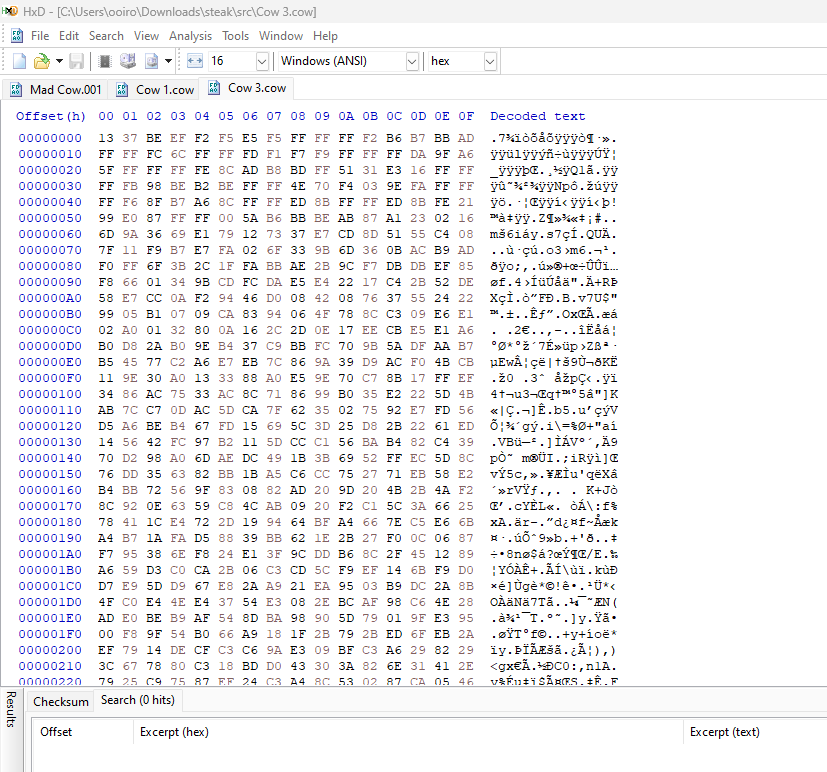
We are given a 001 image, a Python script and two encrypted files to investigate. Reading the scenario, it seems that the .cow files were originally png images before the encryption and the Python script was to help decrypt .cow files for us automatically.
Testing the decryption with Cow 1.cow, the file was able to be decrypted.
1
PS C:\Users\ooiro\Downloads\steak\src> python .\cow_decryptor.py -i '.\Cow 1.cow' -o decrypt1.png
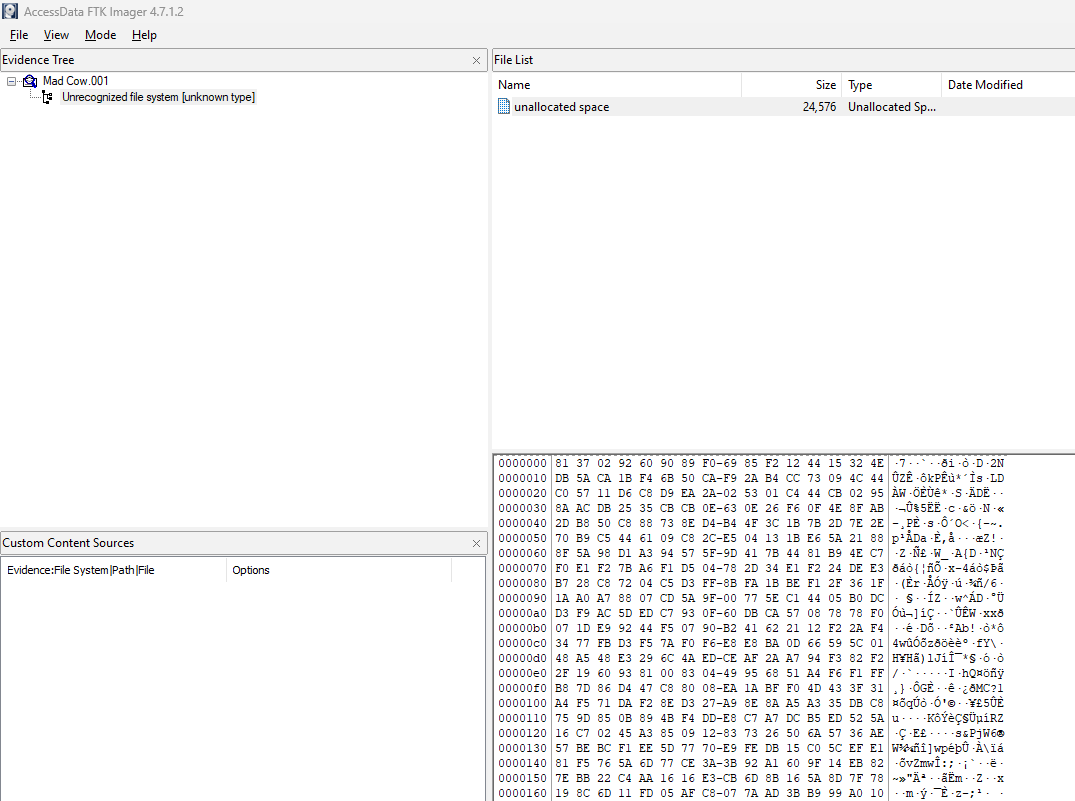
Analyzing the 001 image now, it seems that it was just a huge chunk of data. Again, the scenario mentioned something about having leftover .cow files within the corrupted data.
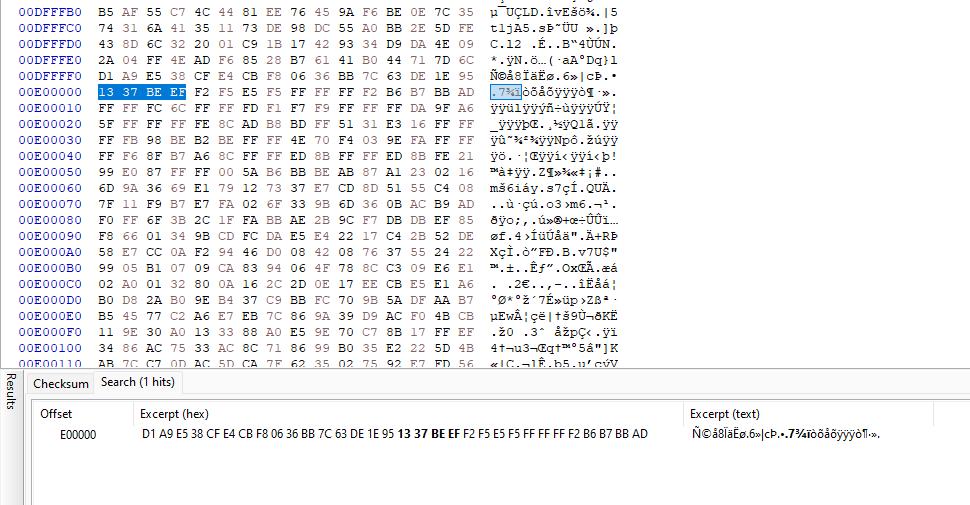
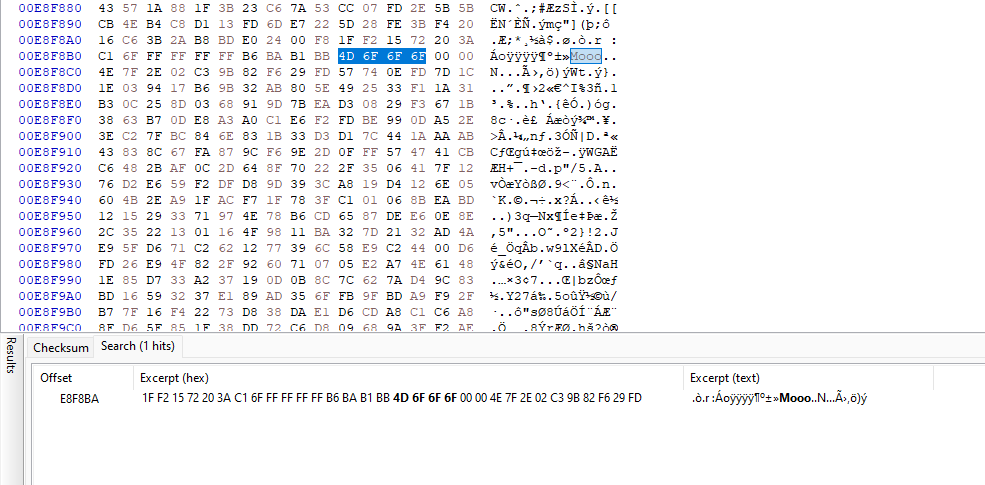
Remembering about a carving challenge from Dreamhack, I analyzed the hexdump of the 001 file with HxD and searched for the header values of .cow files. By filtering for 13 37 BE EF (header) and 4D 6F 6F 6F (tail), the entire .cow file can be located easily.
Carving the data chunk from E00000 to E8F8BA, the third .cow file can be obtained and decrypted.
The Worst Challenge Ever [Forensics]
Question: Hello there! Don’t click on it
Flag: byuctf{wh4ts_4_nu11_byt3_4nyw4ys}
We are given a weird text file to investigate. PS: DON’T CLICK THE WEIRD BUTTON OR YOUR BROWSER WILL CRASH! Analyzing it, it seems like it was just a normal text.
1
2
└─$ cat justterrible.txt
hello, theregeneral kenobi
However, opening it on Notepad shows that there were hidden data in between the words.
1
敨汬Ɐ琠敨敲 Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā Ā 朁湥牥污欠湥扯
Analyzing the hexdump, it seems that the hidden data were 00 and 01 bytes.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
└─$ xxd justterrible.txt
00000000: 6865 6c6c 6f2c 2074 6865 7265 0000 0000 hello, there....
00000010: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000040: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000050: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000060: 0000 0000 0000 0000 0000 0000 0000 0100 ................
00000070: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000080: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000090: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000000a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000000b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000000c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000000d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000000e0: 0000 0000 0000 0000 0100 0000 0000 0000 ................
000000f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000100: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000110: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000120: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000130: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000140: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000150: 0000 0000 0000 0000 0000 0000 0000 0100 ................
00000160: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000170: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000180: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000190: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000001a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000001b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000001c0: 0000 0100 0000 0000 0000 0000 0000 0000 ................
000001d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000001f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000200: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000210: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000220: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000230: 0000 0000 0000 0001 0000 0000 0000 0000 ................
00000240: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000250: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000260: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000270: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000280: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000290: 0000 0000 0000 0000 0000 0000 0000 0100 ................
000002a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000002b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000002c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000002d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000002e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000002f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000300: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000310: 0000 0000 0000 0000 0000 0100 0000 0000 ................
00000320: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000330: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000340: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000350: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000360: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000370: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000380: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000390: 0000 0100 0000 0000 0000 0000 0000 0000 ................
000003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000003b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000003c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000003d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000003e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000003f0: 0000 0000 0000 0000 0000 0001 0000 0000 ................
00000400: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000410: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000420: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000430: 0100 0000 0000 0000 0000 0000 0000 0000 ................
00000440: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000450: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000460: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000470: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000480: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000490: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000004a0: 0000 0000 0001 0000 0000 0000 0000 0000 ................
000004b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000004c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000004d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000004e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000004f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000500: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000510: 0000 0000 0000 0000 0001 0000 0000 0000 ................
00000520: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000530: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000540: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000550: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000560: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000570: 0000 0000 0000 0000 0001 0000 0000 0000 ................
00000580: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000590: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000005a0: 0000 0000 0000 0000 0000 0000 0000 0100 ................
000005b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000005c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000005d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000005e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000005f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000600: 0000 0000 0000 0000 0000 0000 0000 0100 ................
00000610: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000620: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000630: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000640: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000650: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000660: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000670: 0000 0000 0000 0000 0000 0000 0001 0000 ................
00000680: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000690: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000006a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000006b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000006c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000006d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000006e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000006f0: 0000 0001 0000 0000 0000 0000 0000 0000 ................
00000700: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000710: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000720: 0000 0000 0001 0000 0000 0000 0000 0000 ................
00000730: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000740: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000750: 0000 0000 0000 0001 0000 0000 0000 0000 ................
00000760: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000770: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000780: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000790: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000007a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000007b0: 0000 0000 0000 0001 0000 0000 0000 0000 ................
000007c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000007d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000007e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000007f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000800: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000810: 0000 0000 0000 0000 0000 0100 0000 0000 ................
00000820: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000830: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000840: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000850: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000860: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000870: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000880: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000890: 0000 0000 0100 0000 0000 0000 0000 0000 ................
000008a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000008b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000008c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000008d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000008e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000008f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000900: 0000 0000 0000 0000 0001 0000 0000 0000 ................
00000910: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000920: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000930: 0000 0000 0000 0000 0000 0000 0001 0000 ................
00000940: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000950: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000960: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000970: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000980: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000990: 0000 0000 0000 0000 0000 0000 0001 0000 ................
000009a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000009b0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000009c0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000009d0: 0000 0100 0000 0000 0000 0000 0000 0000 ................
000009e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
000009f0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a00: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a10: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a20: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a30: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a40: 0001 0000 0000 0000 0000 0000 0000 0000 ................
00000a50: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a60: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a70: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a80: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000a90: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000aa0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000ab0: 0000 0000 0000 0000 0000 0001 0000 0000 ................
00000ac0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000ad0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000ae0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000af0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b00: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b10: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b20: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b30: 0000 0001 0000 0000 0000 0000 0000 0000 ................
00000b40: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b50: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b60: 0000 0000 0000 0000 0100 0000 0000 0000 ................
00000b70: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b80: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000b90: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000ba0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000bb0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000bc0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000bd0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000be0: 0000 0100 0000 0000 0000 0000 0000 0000 ................
00000bf0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c00: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c10: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c20: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c30: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c40: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c50: 0000 0000 0000 0100 0000 0000 0000 0000 ................
00000c60: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c70: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c80: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000c90: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000ca0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000cb0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000cc0: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000cd0: 0000 0000 0167 656e 6572 616c 206b 656e .....general ken
00000ce0: 6f62 69 obi
At this point, I was stuck and was baffled that so many people were able to solve this instead of the other “harder” challenges later on. Thankfully, my teammate was able to solve it pretty quick too. He mentioned that we can actually just split the 00 bytes with each 01 byte, calculate the 00 bytes length and then just convert the length values to ASCII. So with a script I made with the help from ChatGPT, the flag can be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
def find_00_sequences(hexdump):
sequences = []
current_sequence = []
for byte in hexdump:
if byte == 0x00:
current_sequence.append(byte)
elif byte == 0x01:
if current_sequence:
sequences.append(current_sequence)
current_sequence = []
else:
if current_sequence:
sequences.append(current_sequence)
current_sequence = []
if current_sequence:
sequences.append(current_sequence)
return sequences
def calculate_and_convert(sequences):
lengths = [len(sequence) for sequence in sequences]
ascii_chars = ''.join(chr(length) for length in lengths)
return lengths, ascii_chars
with open("justterrible.txt", "rb") as file:
hexdump = file.read()
# Convert hexdump to list of bytes, skipping non-00/01 values
hexdump_bytes = [byte for byte in hexdump if byte in (0x00, 0x01)]
# Find sequences of 00 bytes separated by 01 bytes
sequences = find_00_sequences(hexdump_bytes)
# Calculate the length of each sequence of 00 bytes and convert to ASCII characters
lengths, ascii_chars = calculate_and_convert(sequences)
print("Lengths of each sequence of 00 bytes:", lengths)
print("Lengths converted to ASCII characters:", ascii_chars)
1
2
3
└─$ python script.py
Lengths of each sequence of 00 bytes: [98, 121, 117, 99, 116, 102, 123, 119, 104, 52, 116, 115, 95, 52, 95, 110, 117, 49, 49, 95, 98, 121, 116, 51, 95, 52, 110, 121, 119, 52, 121, 115, 125]
Lengths converted to ASCII characters: byuctf{wh4ts_4_nu11_byt3_4nyw4ys}
Did Nobody See? [Forensics]
Question: We recently obtained a triage image from a Windows laptop belonging to a suspected ransomware operator. The suspect used several anti-forensic techniques and managed to erase any form of web history. We suspect that we may be able to use data from DNS servers as evidence to tie the suspect to the operation. Unfortunately, the suspect was using a VPN. Can you find any DNS servers used during the VPN connection? The answer will be in the form of byuctf{ip.address} (there may be multiple answers, any valid IP address for the DNS server will work for the answer).
Flag: byuctf{162.252.172.57}
We are given triaged Windows artifacts to investigate. Reading the scenario, it seems that I should be looking for VPN connections to identify the specific DNS servers.
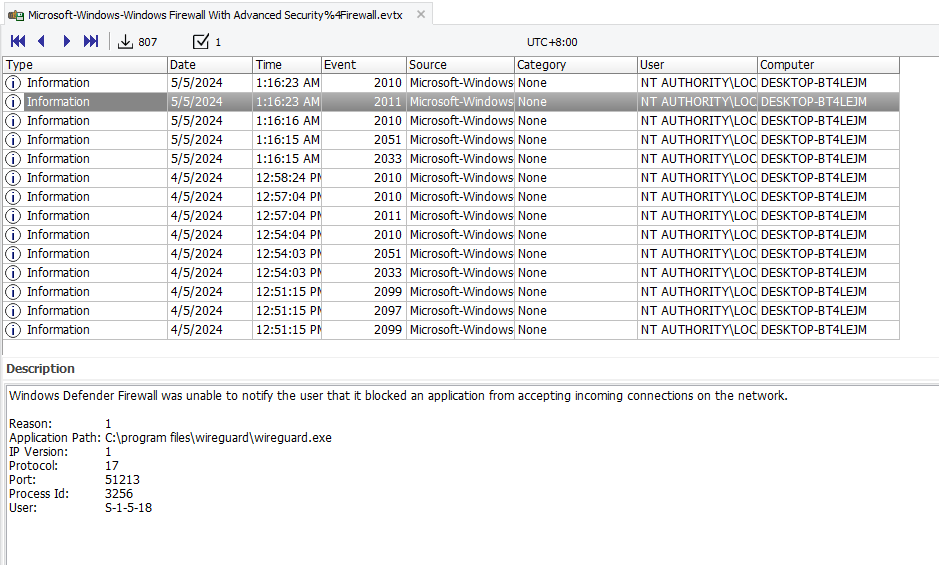
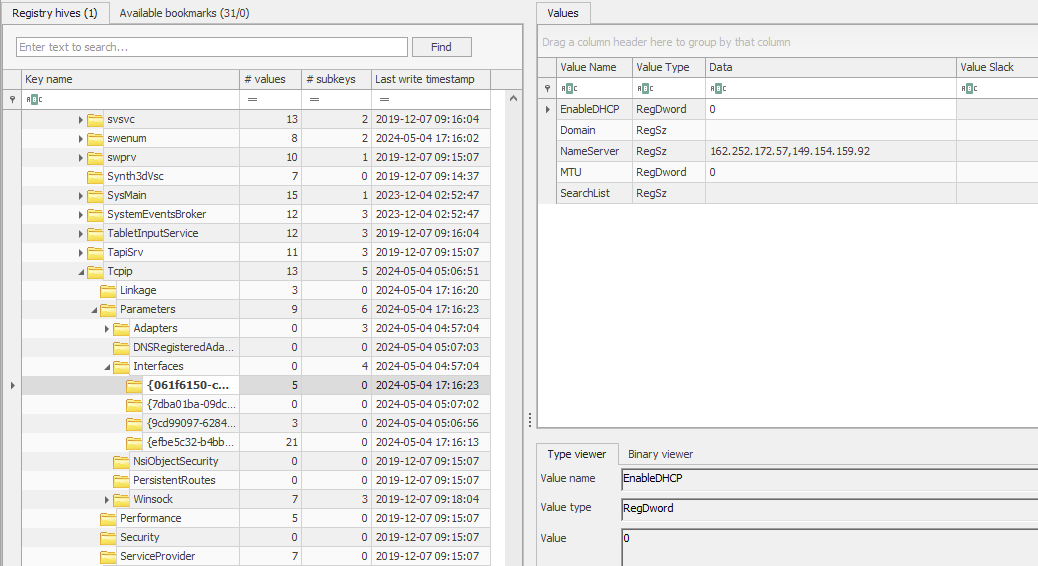
Checking the event logs first, nothing interesting can be found except for the VPN program name found in Microsoft-Windows-Windows Firewall With Advanced Security%4Firewall.evtx.
However, we still have other Windows artifacts to investigate. So by researching online about which registry hive stores network information, I stumbled upon this blog that mentioned HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces. Analyzing the SYSTEM hive, the IP addresses can be found.
Not again! I’ve been BitLockered out of my own computer! [Forensics]
Question: Install Bitlocker they said… it will protect your data they said… Well, now I don’t have access to any of my data because I forgot my password… again! Can you find my FVEK keys? I managed to capture my RAM so they should be in there.
Flag: byuctf{91c75f658705c36090f03779cacb056179e16316ee4af1e90d0f84e090b88d8b_91d4cceb5bf238cb3cb96367314773f5_968052b6b247b32f6cfecce39749785f}
We are given a memory dump to investigate. Researching online about FVEK keys, I stumbled upon this post that talks about a Volatility plugin which extracts bitlocker keys from a memory dump. So by importing the plugin to Volatility 2 via /volatility/volatility/plugins/, the keys can be obtained easily. PS: the image scan will take at least 20-30 minutes so be patient.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
└─$ python2 vol.py -f ~/Desktop/shared/20240327.mem kdbgscan
Volatility Foundation Volatility Framework 2.6.1
**************************************************
Instantiating KDBG using: Unnamed AS Win10x64_19041 (6.4.19041 64bit)
Offset (V) : 0xf8034da00b20
Offset (P) : 0x3000b20
KdCopyDataBlock (V) : 0xf8034d310c08
Block encoded : Yes
Wait never : 0x51ed0a240de2adce
Wait always : 0xe2ab5001d0ab800d
KDBG owner tag check : True
Profile suggestion (KDBGHeader): Win10x64_19041
Service Pack (CmNtCSDVersion) : 0
Build string (NtBuildLab) : 19041.1.amd64fre.vb_release.1912
PsActiveProcessHead : 0xfffff8034da1e130 (129 processes)
PsLoadedModuleList : 0xfffff8034da2a770 (156 modules)
KernelBase : 0xfffff8034ce00000 (Matches MZ: True)
Major (OptionalHeader) : 10
Minor (OptionalHeader) : 0
KPCR : 0xfffff80347d79000 (CPU 0)
KPCR : 0xffffb000e37a0000 (CPU 1)
KPCR : 0xffffb000e31e6000 (CPU 2)
└─$ python2 vol.py -f ~/Desktop/shared/20240327.mem bitlocker --profile=Win10x64_19041
Volatility Foundation Volatility Framework 2.6.1
Address : 0x868fe9d93b10
Cipher : AES-256
FVEK : 91c75f658705c36090f03779cacb056179e16316ee4af1e90d0f84e090b88d8b
Address : 0x868fee591a10
Cipher : AES-128
FVEK : 91d4cceb5bf238cb3cb96367314773f5
Address : 0x868fe988db30
Cipher : AES-128
FVEK : 968052b6b247b32f6cfecce39749785f
Not Sure I’ll Recover From This [Forensics]
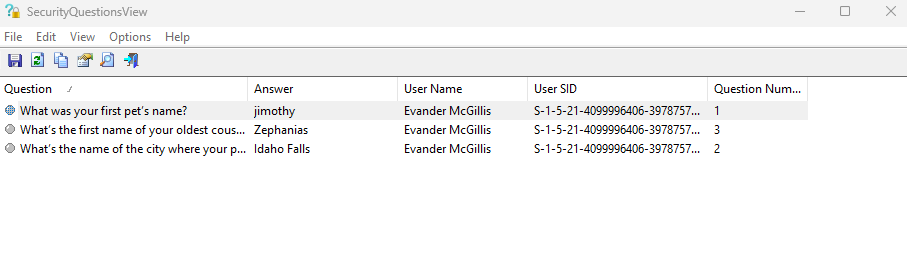
Question: You know, passwords arent easy for person of my age, it’s pretty hard to remember my password, let alone my security questions! I can’t login now, can you help a friend out and recover my security questions so I can login?
Flag: byuctf{jimothy_Idaho Falls_Zephanias}
We are given a virtual machine to investigate. Reading the scenario, it seems that I have to analyze the security questions from a registry hive. However, I already played this kind of forensics challenge before so the process was pretty straightforward.
By extracting the SAM hive from the virtual machine, it can be further analyzed with a Nirsoft tool specifically made to view security questions.
Stardust Whispers [Forensics]
Question: Wrap flag submission with byuctf{}
Flag: byuctf{Amunet_means_the_hidden_one}
We are given a docx file and a PCAP file to investigate. Reading the docx file, it seems that there was a hint given near the end of the paragraph.
1
2
3
4
5
6
7
8
9
--SNIP--
But the path ahead was treacherous. They boarded the Millennium Falcon, piloted by none other than Flash Gordon himself—a swashbuckling hero who had slipped through a cosmic rift. Flash regaled them with tales of Ming the Merciless and Hawkmen, his bravado masking a deeper longing for adventure.
As they neared the Hutt-controlled planet of Tatooine, Leia reminded her friend of the essential component of their plan: “Chani,” she said, “remember the silent language of message packets traveling through the galactic network. It’s our path to infiltrating Jabba’s fortress undetected. The key is 4. If you remember your training, think of the database of exploits and the number 18581.”
Chani nodded, her eyes alight with determination. They would pose as traders, their stillsuits concealing vibroblades. Together they wove a web of deception as they skillfully isolated their target within the bustling cantina’s noise. Finally the trap was set. In a final showdown, they fought side by side—Chani’s crysknife clashing with Jabba’s guards, Leia using the Force to disarm her foes. At long last, the Sapho juice was theirs, though they had to change the final ‘K’ to ‘=’ in order to decipher their mission.
--SNIP--
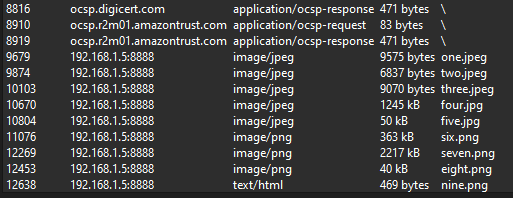
Analyzing the PCAP, there were several ICMP, HTTP and TLS packets being sent in the network. The HTTP object show 9 images that can be exported. With the hint of key is 4, I thought the fourth image must be hiding something. However, there was nothing interesting in the image.
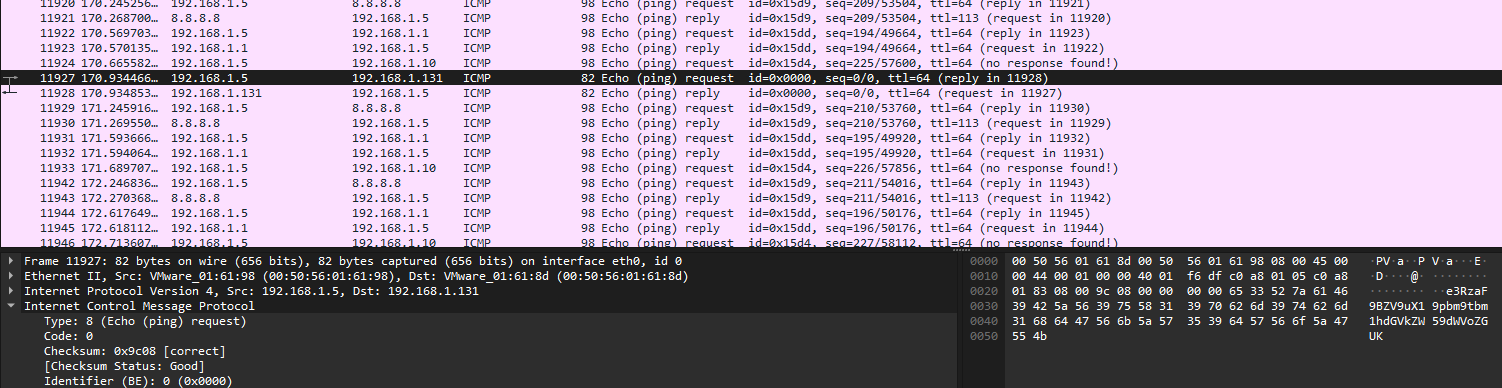
At this point, my teammate managed to solve the whole challenge. It was actually very straightforward, by searching up the exploit ID of 18581 in exploitdb, the exploit is shown to be Covert Channel over ICMP. This suggest that the attacker might be exfiltrating data via the ICMP protocol similar to DNS tunneling. Analyzing the PCAP, an odd ICMP packet can be found which did not fail like the rest.
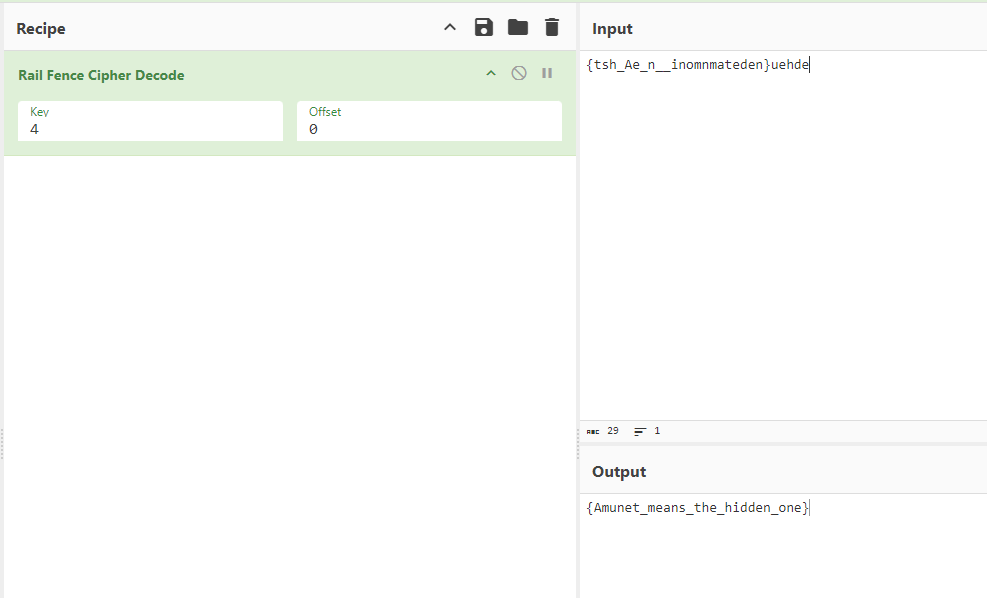
According to the hints again, it mentioned changing K to =. This tells us that the full string should be converted to a base64 encoded string e3RzaF9BZV9uX19pbm9tbm1hdGVkZW59dWVoZGU=. Decoding it gives a broken flag.
1
2
└─$ echo "e3RzaF9BZV9uX19pbm9tbm1hdGVkZW59dWVoZGU=" | base64 -d
{tsh_Ae_n__inomnmateden}uehde
Reading the hints again, we are left with the last hint of key is 4. According to dcode, it suggested Railfence cipher. By decoding the string with rail fence cipher and key 4, the flag can be obtained.