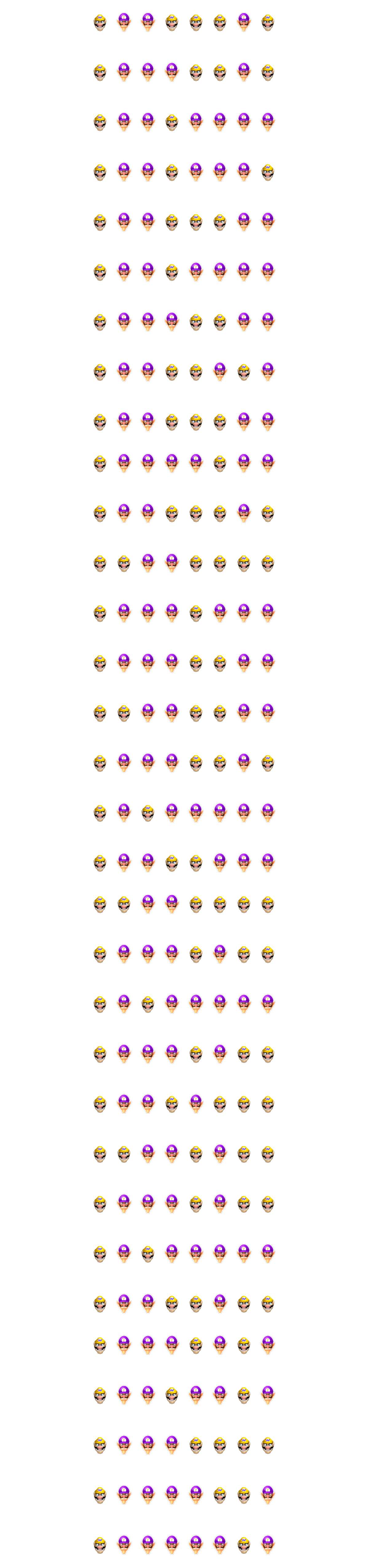BroncoCTF 2024 - Writeups
This is a writeup for some forensics, OSINT, cryptography and misc challenges from BroncoCTF 2024. Although the CTF was aimed at beginners, some of the challenges proved to be quite difficult, featuring unique and well-crafted problems tailored specifically for the forensics category. It was also clear that the organizers have a particular fondness for binary.
Wario Party [Forensics]
Question: Who is the true hero of the Mario Party games you might ask? Look inward and you might find it at the intersection of Mario’s color and the number of brothers.
Flag: bronco{b0ws3r_g0t_th4t_dumpy}
We are given an image to investigate. Reading the description carefully, it mentioned something about Mario’s color (Red) and the number of brothers (2). Using this information, analyzing the image shows that there data encoded in Red 2.
So we can use online tools like StegOnline to extract the hidden data embedded within the image.
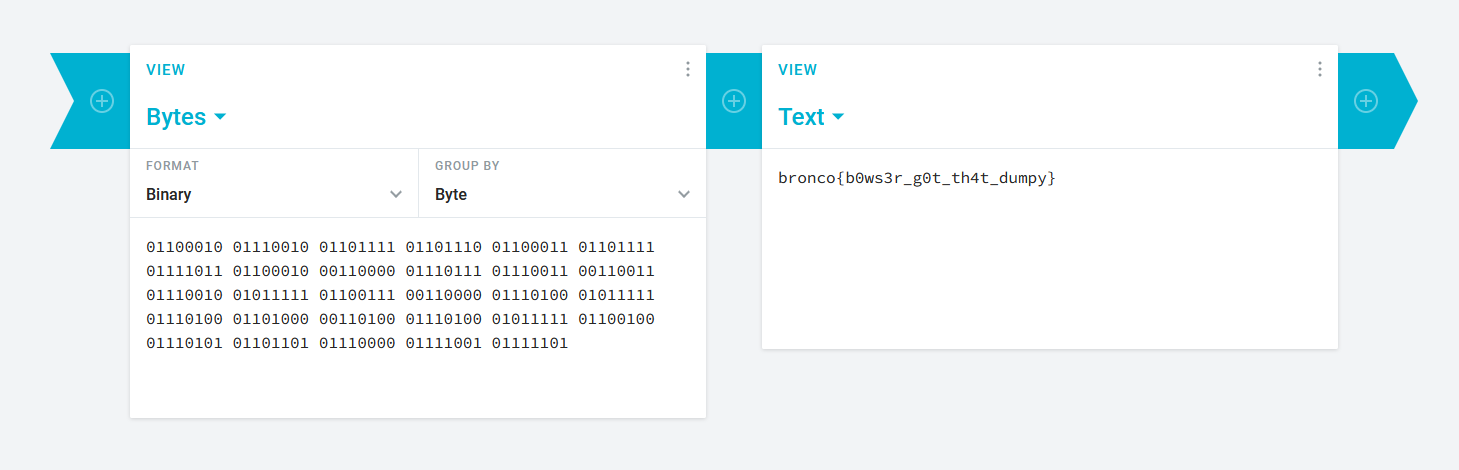
The extracted data seems to be an image of another puzzle with Wario and Waluigi. Analyzing the image, it seems that it is a binary string where Wario=0 and Waluigi=1. Converting the binary to ASCII, the flag can be obtained.
Boom [Forensics]
Question: With all these talks of arbitration, things are tense here around the office. I feel like people are going to explode at any moment. I gotta watch where I step before I accidentally bring something up and uncover something I didn’t want to.
Hint: Look into Minesweeper and hex
Flag: bronco{bo0m!}
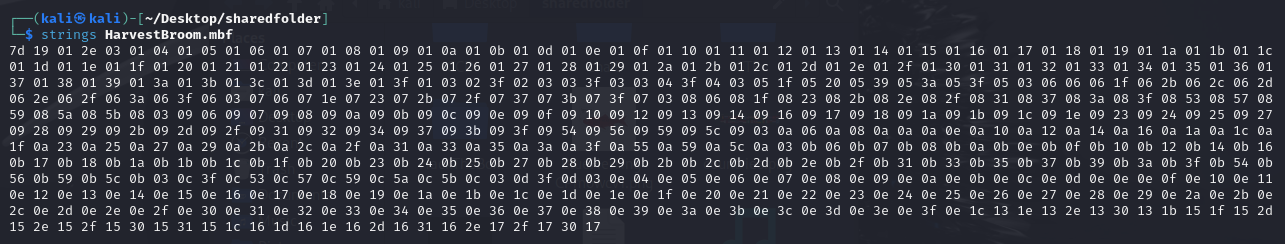
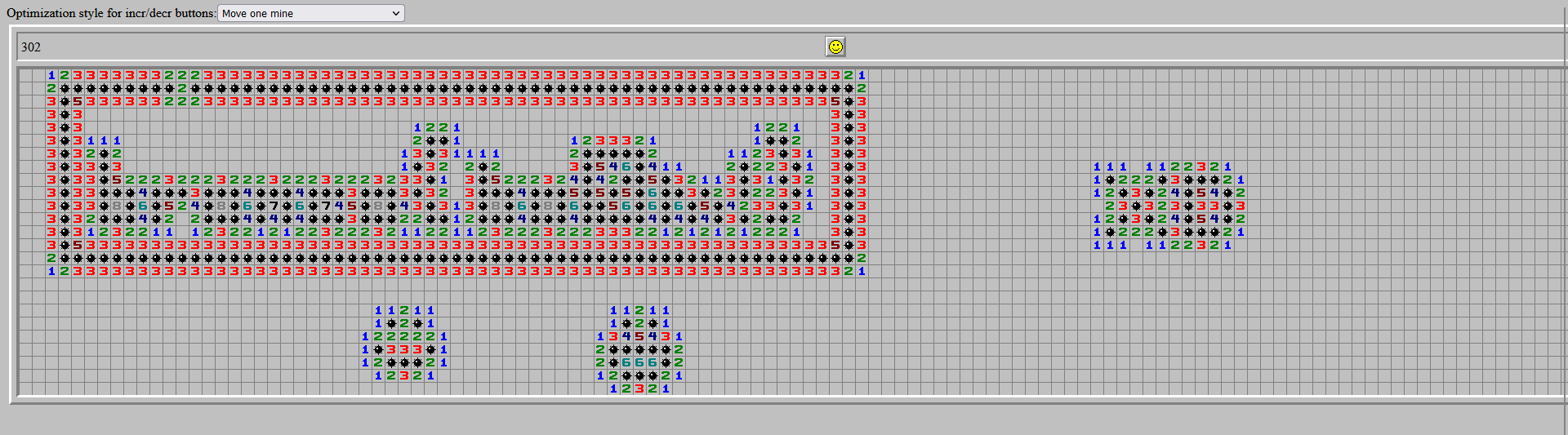
We are given a Minesweeper board file to investigate. Analyzing the file content, several hex data can be identified.
Researching online about this file type, I came across MZRG which allows players to load custom Minesweeper boards. The flag can be identified after loading the Minesweeper board.
Mystery Sound [Forensics]
Question: This transmission supposedly contains a secret flag, but I can’t decode it because of some interference. Can you help?
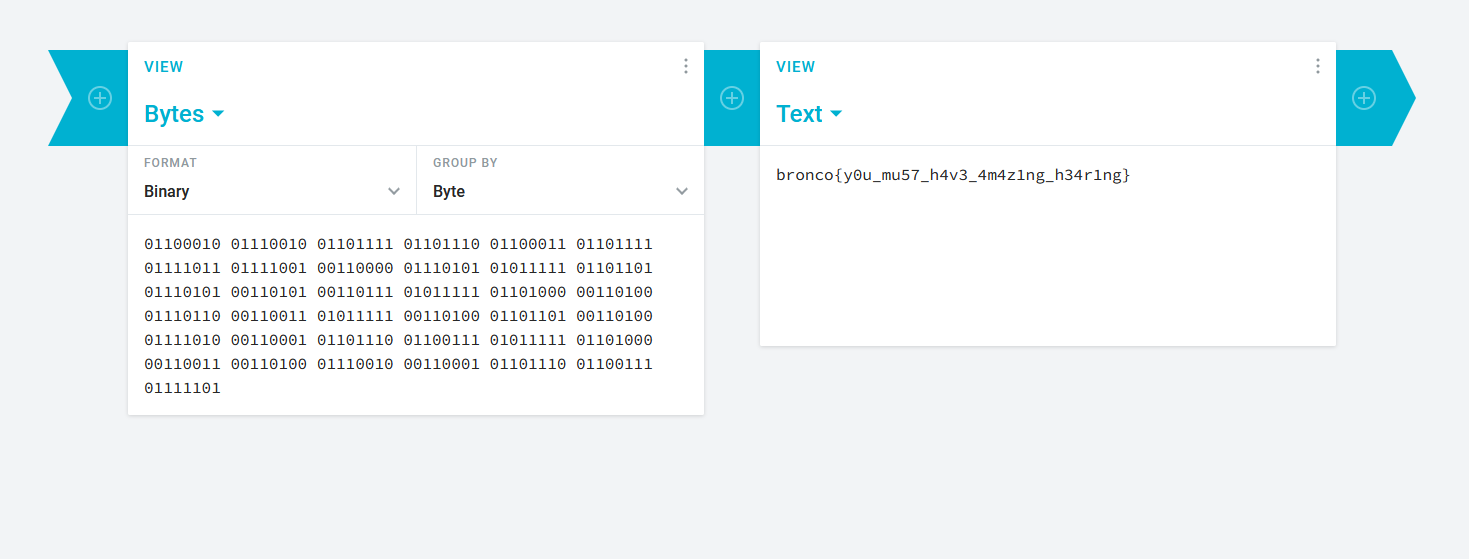
Flag: bronco{y0u_mu57_h4v3_4m4z1ng_h34r1ng}
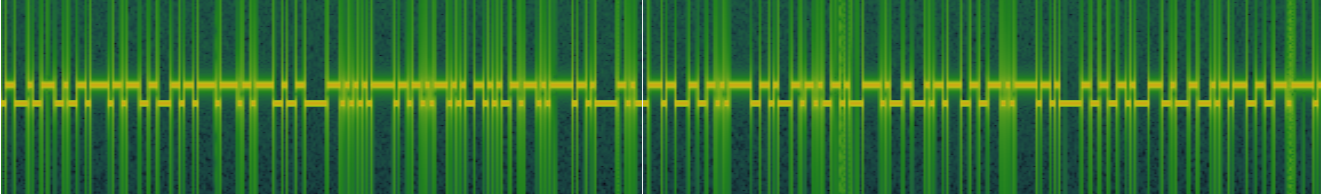
We are given a WAV audio file to investigate. Analyzing the audio spectrogram, a long sequence of digital waves can be identified.
After manually inserting each bit and decoding them (had to repeat 6 times rip my eyes), the flag can be obtained.
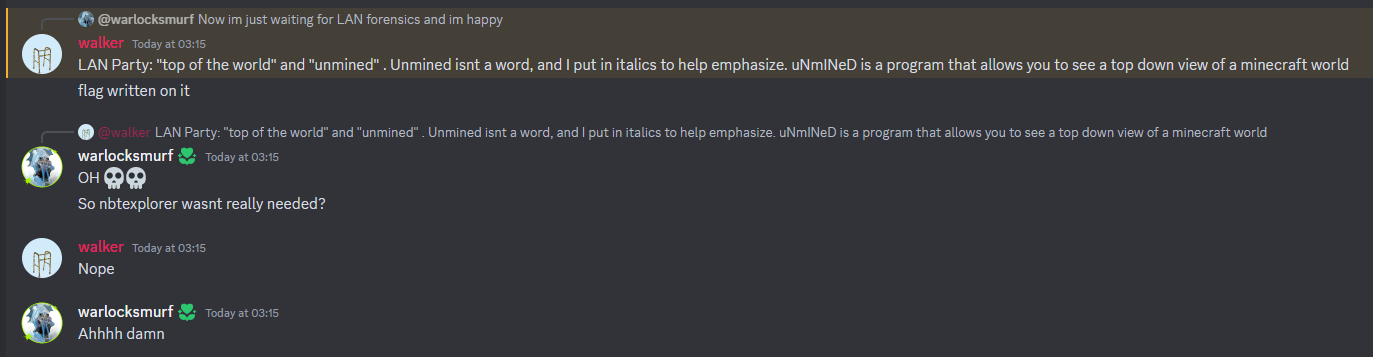
LAN Party [Forensics]
Question: My friend is SO MEAN! He changed my password on my home router and hid it in this Minecraft world. He even unmined the chunk I dug out…what a jerk. Ugh, now I am just here at the top of the world rather than at bedrock mining diamonds.
Flag: bronco{b1rd's_Ey3_View}
we are given Minecraft files to investigate. Unfortunately I could not solve this before the CTF ended, but I still attempted it with the help from the author. Since it was Minecraft forensics, I assume we had to analyze the chunk position in NBTExplorer to uncover hidden values. However, the author mentioned that another specific tool can be used to get the flag directly.
By using uNmINeD to get a top down view of any Minecraft world, the flag can be obtained.
Wiki Wiki Wiki [OSINT]
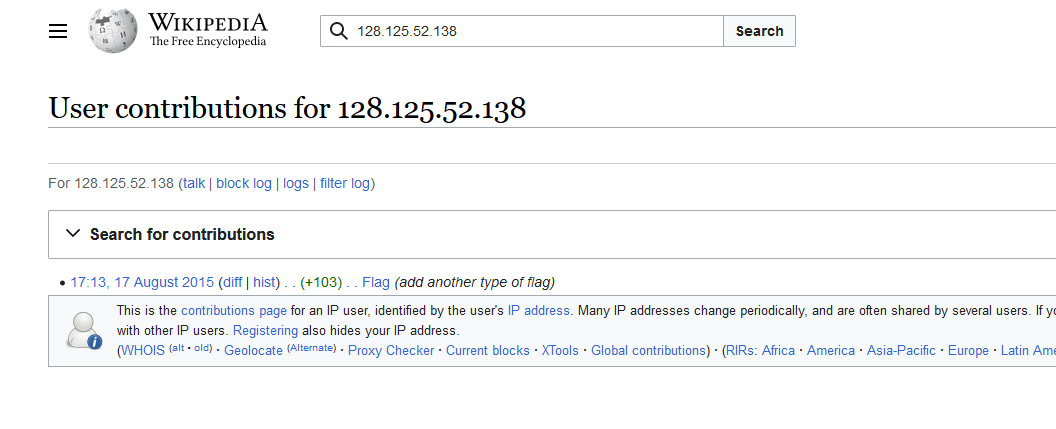
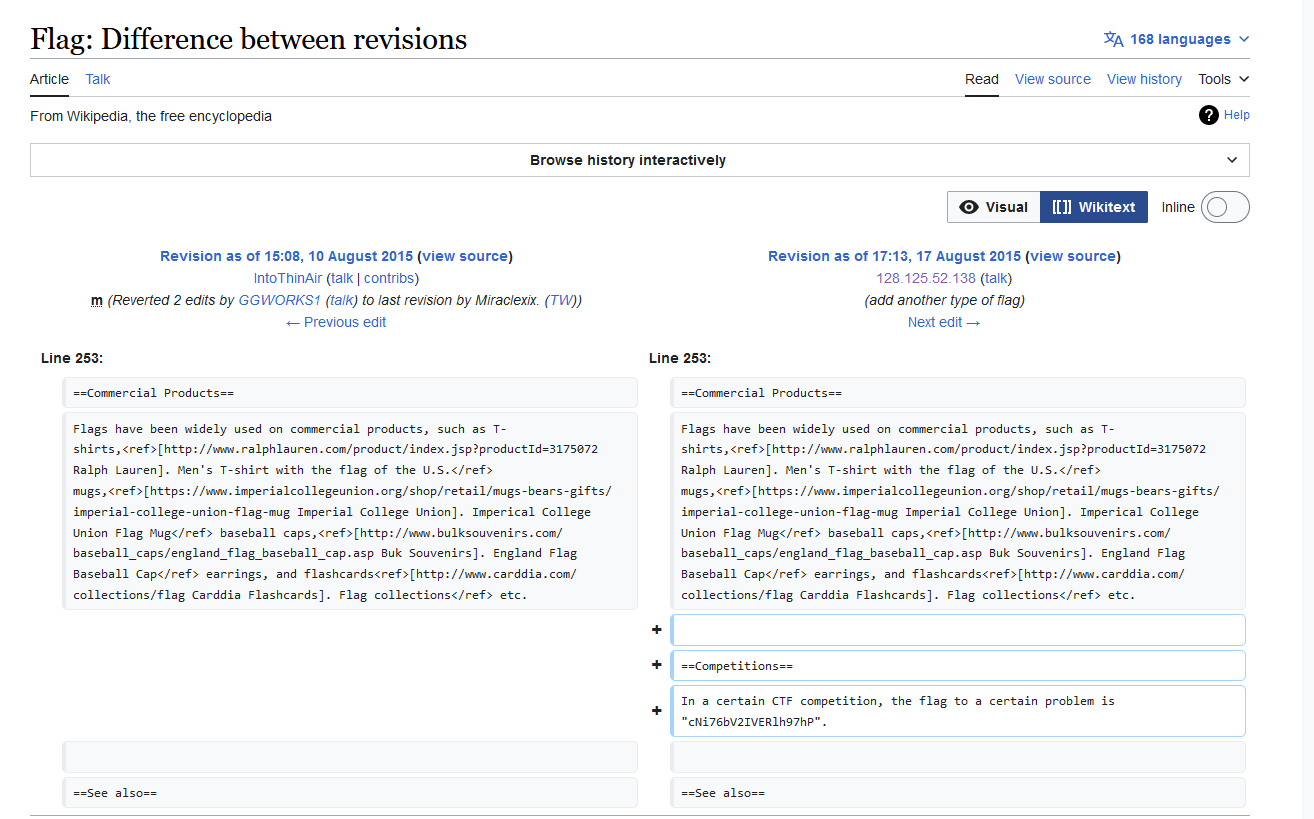
Question: Not much to go off here, but it’s all you need: Wikipedia and 128.125.52.138. The flag is not in the typical format, but wrap it in bronco{} before submitting. You will know when you find it.
Flag: bronco{cNi76bV2IVERlh97hP}
Just search the IP address on Wikipedia. The flag can be obtained from the latest changelog.
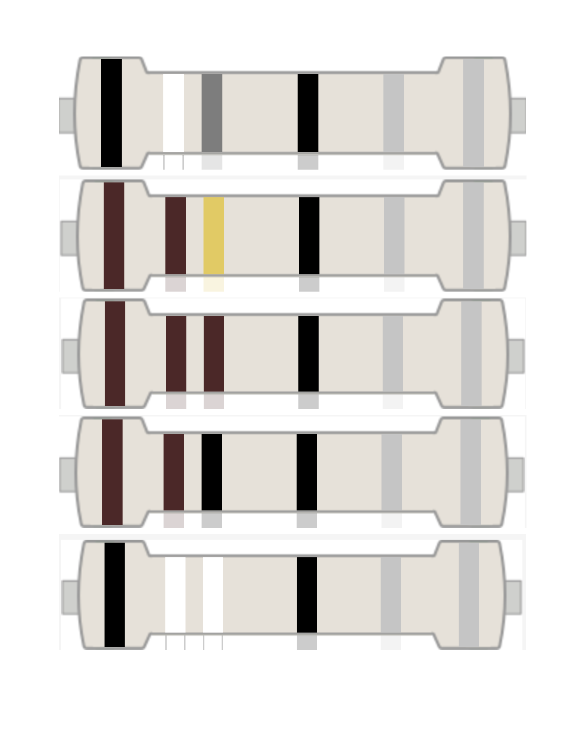
Electrical Engineering [Cryptography]
Question: I hate electrical engineering
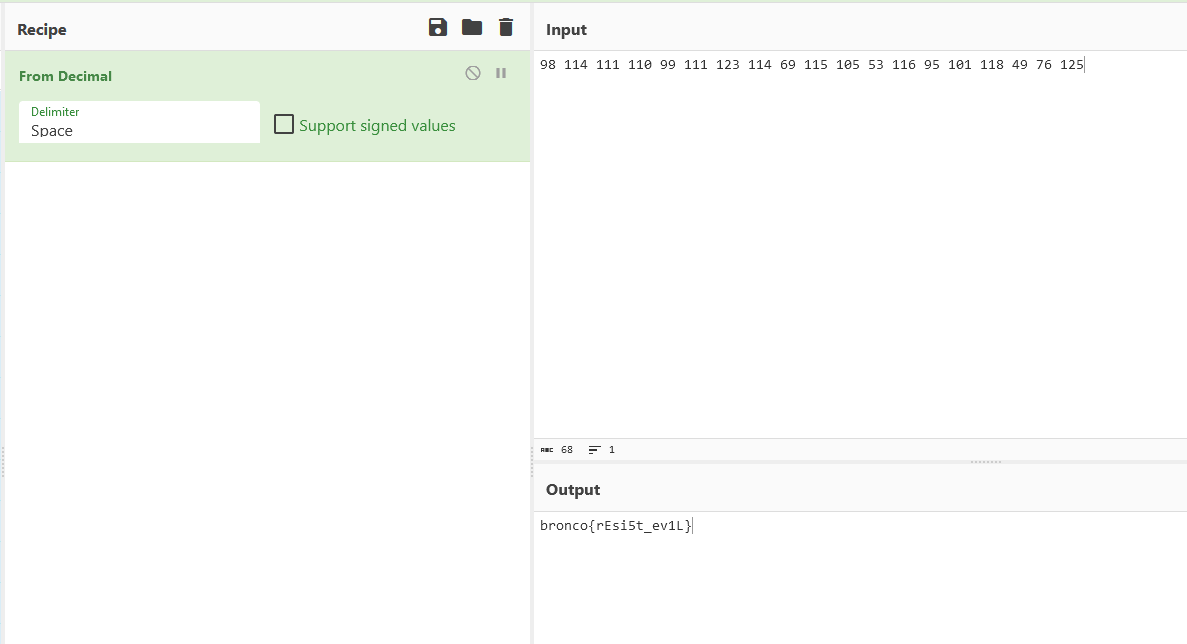
Flag: bronco{rEsi5t_ev1L}
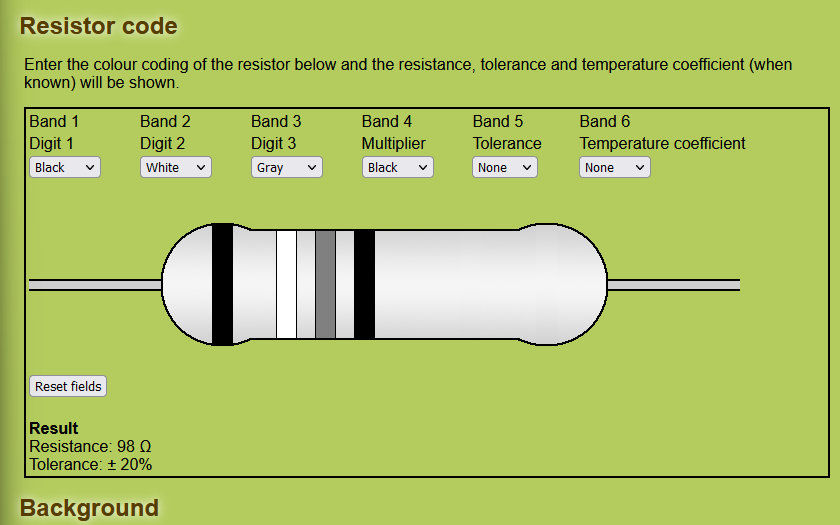
We are given a PDF file to investigate. The PDF had several 6-band resistors that seem to be the flag.
Using this online tool to automatically calculate the Ω values for each resistor, the combined values can be decoded into the flag. Thanks @eror__404 for the sanity check.
Oh, Danny [Cryptography]
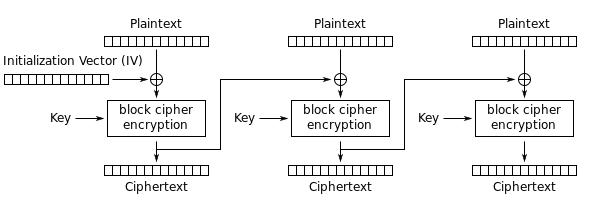
Question: When using AES in CBC mode, Danny has a habit of leaving messages in his initialization vectors. Can you find his secret message?
1
2
3
4
key = 73757065725f6b65795f73747265616d
pt1 = 4163636f7264696e6720746f20616c6c
pt2 = 206b6e6f776e206c617773206f662061
ct2 = 817ed4df4521cc2d6e746c45a834aa2d
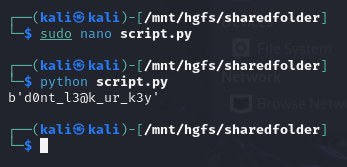
Flag: bronco{d0nt_l3@k_ur_k3y}
We are given an AES key, plaintext and ciphertext to investigate. Since the challenge mentioned that the encryption method was CBC, we can essentially reverse the process to obtain the IV.
I generated a Python script to reverse the encryption process and obtain the IV. This script was heavily inspired from @Krauq so credits to him.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
from Crypto.Cipher import AES
from binascii import unhexlify
key = unhexlify("73757065725f6b65795f73747265616d")
ct2 = unhexlify("817ed4df4521cc2d6e746c45a834aa2d")
pt2 = unhexlify("206b6e6f776e206c617773206f662061")
pt1 = unhexlify("4163636f7264696e6720746f20616c6c")
# Decrypt ct2 to get "pt2 XOR ct1"
cipher = AES.new(key, AES.MODE_ECB)
decrypted_ct2 = cipher.decrypt(ct2)
# Calculate ct1
ct1 = bytes(a ^ b for a, b in zip(decrypted_ct2, pt2))
# Decrypt ct1 to get "pt1 XOR IV"
decrypted_ct1 = cipher.decrypt(ct1)
# Calculate IV
iv = bytes(a ^ b for a, b in zip(decrypted_ct1, pt1))
print(iv)
Countries Unite [Misc]
Question: “yoshie” sent me a peculiar message. What could he possibly be trying to say?
Flag: bronco{diveristyequityinclusion}
We are given an image to investigate. The image had several flag emojis, just get the first letter of each country flag and the flag can be obtained.
BroncoCTF Crossword [Misc]
Question: I am really annoyed. I work at Bronco Venture Accelerator and instead of doing work, my boss is just sitting doing a crossword. And drinking lemon juice? WHY! I want to dump it on him and his paper. We need to make MONEY.
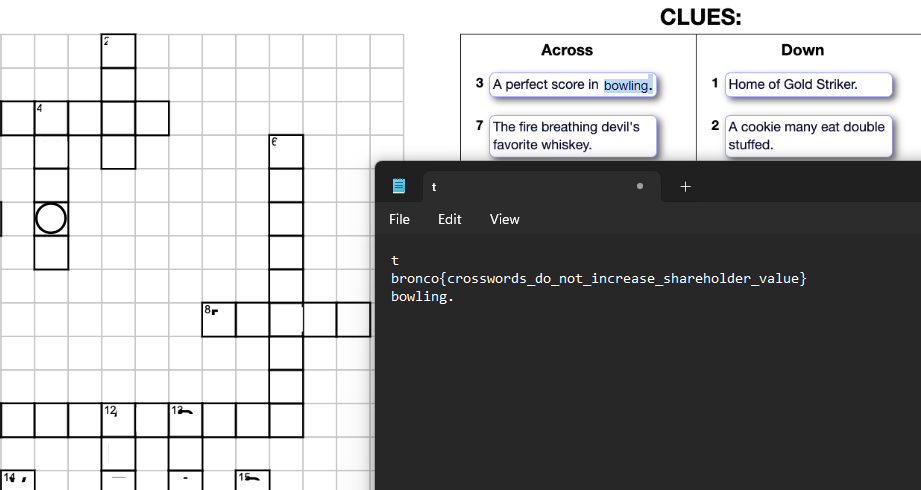
Flag: bronco{crosswords_do_not_increase_shareholder_value}
We are given a PDFF file to investigate. The PDF file was a crossword puzzle with white boxes covering some sections. Initially, I spent an hour doing the crossword puzzle and it lead to no information on the flag. Hence, I had to ask hints from Discord which mentioned something about lemon juice and paper. This obviously means the text “disappeared” as lemon juice on ink produces invisible ink.
Unfortunately I could not solve this before the CTF ended, but I still attempted it with the help from the author. The flag can actually be obtained with a simple CTRL+A (bruh).