BlackHat MEA Qualification CTF 2024 - Writeups
This is a writeup for all forensics challenges from BlackHat MEA Qualification CTF 2024. Despite not getting top 10, we did our best and managed to achieve 30th place out of 900+ teams. Shame there weren’t many forensics challenges to play around.
Artifact [Forensics]
Question: During the investigation of a compromised machine, it was determined that an impersonation tool had been executed. The Digital Forensics and Incident Response (DFIR) team has provided only a specific hive for analysis. Your objective is to identify the name of the executable associated with the impersonation tool and determine the earliest suspected execution time of this executable on the affected machine. Flag format/example: BHFlagY{cmd.exe_29/12/1992_22:33:13}
Flag: BHFlagY{DeadPotato-NET4.exe_09/08/2024_22:42:13}
We were given a SYSTEM hive to investigate. Using regripper, a suspicious executable DeadPotato-NET4.exe can be identified in the user’s Desktop.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
└─$ regripper -r execution -f system | grep -i "Labib"
Parsed Plugins file.
Launching appcertdlls v.20200427
appcertdlls complete.
Launching appcompatcache v.20220921
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\Update\OneDriveSetup.exe 2024-08-07 22:34:51
C:\Users\Labib\Desktop\DeadPotato-NET4.exe 2024-08-09 22:42:13
C:\Users\Labib\Desktop\AppCompatCacheParser.exe 2023-03-07 22:13:00
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\24.151.0728.0003\FileSyncConfig.exe 2024-08-07 22:34:59
C:\Users\Labib\AppData\Local\Temp\{FCBEF861-3B0B-4F55-9E2B-903577AEE8E9}\AccessData_FTK_Imager_4.7.1.exe 2024-08-07 23:07:52
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\OneDrive.exe 2024-08-07 22:35:01
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileSyncConfig.exe 2024-07-16 11:51:33
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\24.126.0623.0001\FileSyncConfig.exe 2024-07-17 12:17:56
C:\Users\Labib\Desktop\AmcacheParser\AmcacheParser.exe 2023-05-21 18:49:06
C:\Users\Labib\Desktop\AppCompatCacheParser\AppCompatCacheParser.exe 2023-03-07 22:13:00
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\21.220.1024.0005\FileSyncConfig.exe 2024-07-16 12:17:17
C:\Users\Labib\AppData\Local\Temp\44634BC6-55D7-44DE-8A4A-E9E9BDFCD912\dismhost.exe 2022-11-05 08:47:00
C:\Users\Labib\AppData\Local\Temp\6F0F4AD9-855E-431E-9F69-447FA4697ABF\dismhost.exe 2022-11-05 08:47:00
C:\Users\Labib\Desktop\AccessData_FTK_Imager_4.7.1.exe 2024-08-07 23:07:52
C:\Users\Labib\AppData\Local\Temp\7731ba34-653f-4425-977c-bed900928f96_AppCompatCacheParser.zip.f96\AppCompatCacheParser.exe 2023-03-07 22:13:00
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\24.151.0728.0003\Microsoft.SharePoint.exe 2024-08-07 22:35:01
C:\Users\Labib\Desktop\AmcacheParser\DeadPotato-NET4.exe 2024-08-09 22:42:13
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe 2024-07-17 12:18:00
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\24.126.0623.0001\Microsoft.SharePoint.exe 2024-07-17 12:17:59
appcompatcache complete.
Launching backuprestore v.20200517
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\21.220.1024.0005\FileCoAuth.exe 2024-07-16 12:17:16
C:\Users\Labib\AppData\Local\Microsoft\OneDrive\24.151.0728.0003\FileCoAuth.exe 2024-08-07 22:34:58
C:\Users\Labib\Desktop\AmcacheParser\8bKpGWGh.exe 2024-08-09 23:05:18
NotFS [Forensics]
Question: Is this a FileSystem? Identify the file and make the necessary adjustments to solve the challenge. Note: The challenge file size is 16GB after extraction.
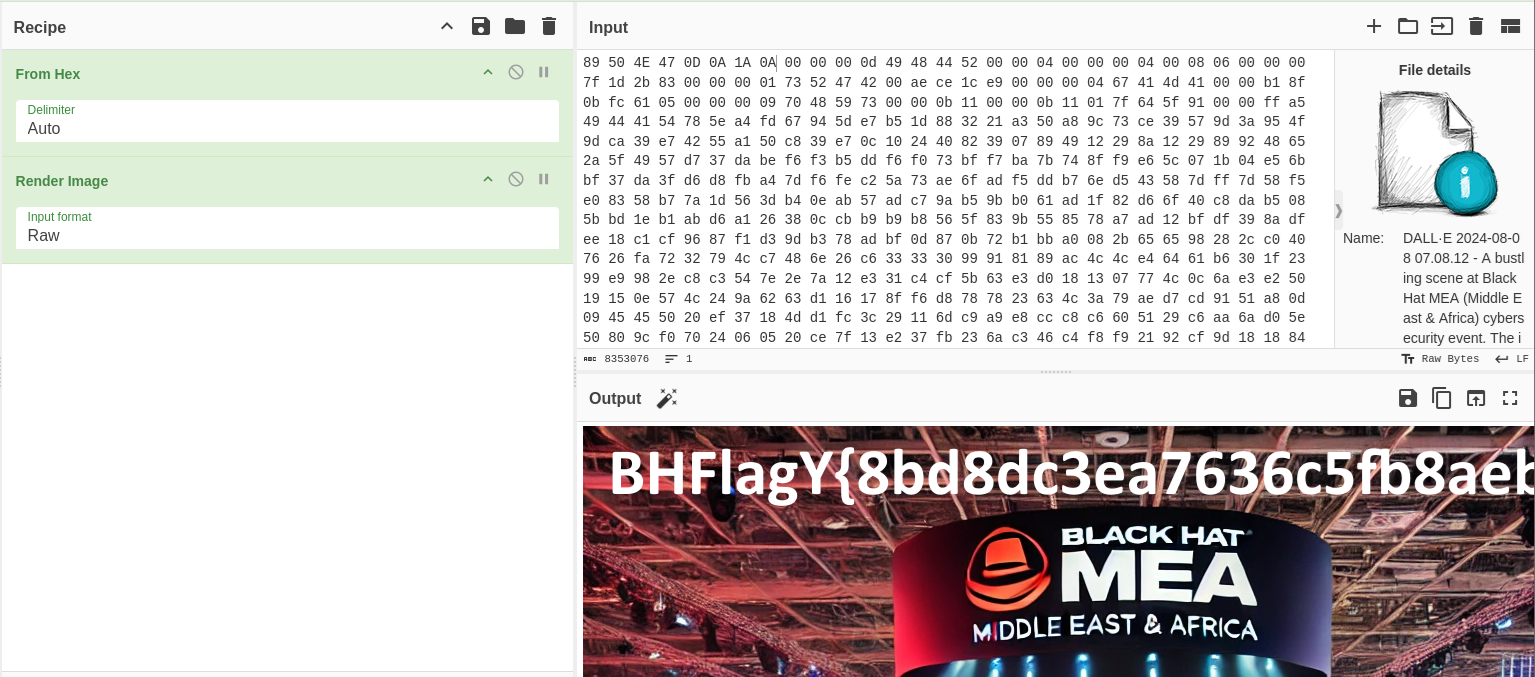
Flag: BHFlagY{8bd8dc3ea7636c5fb8aeb}
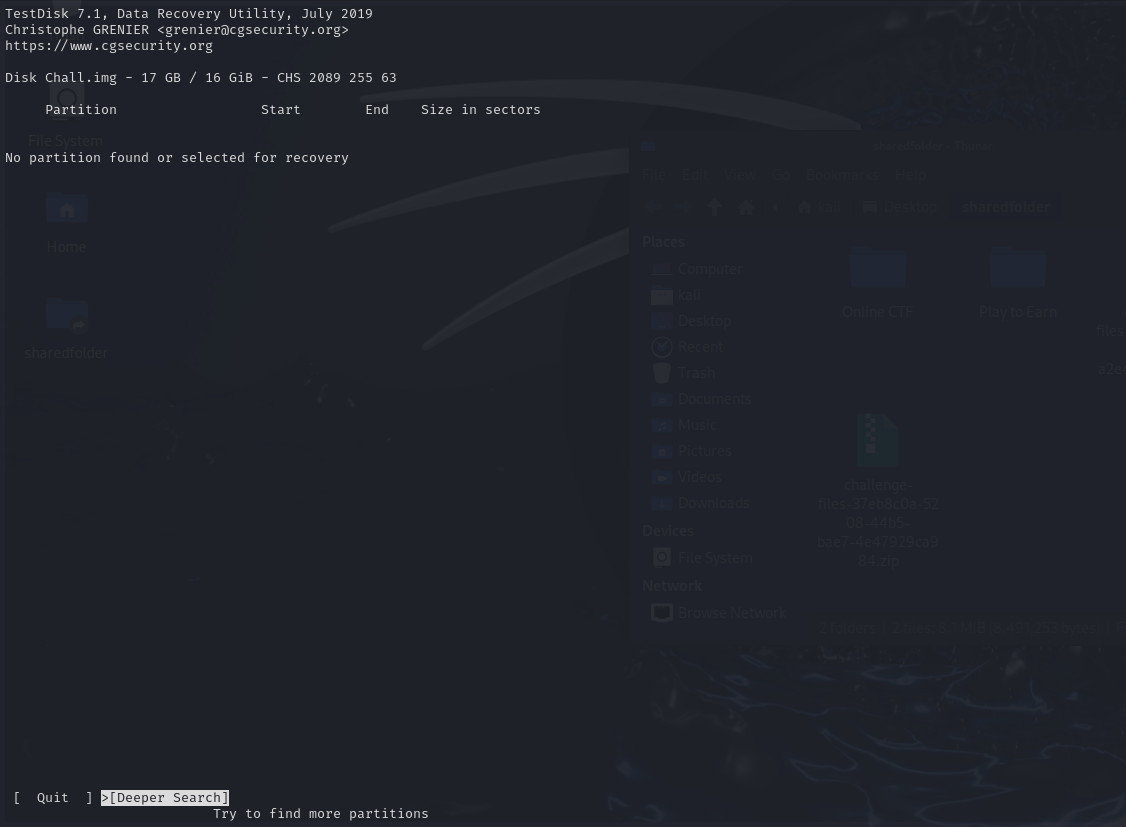
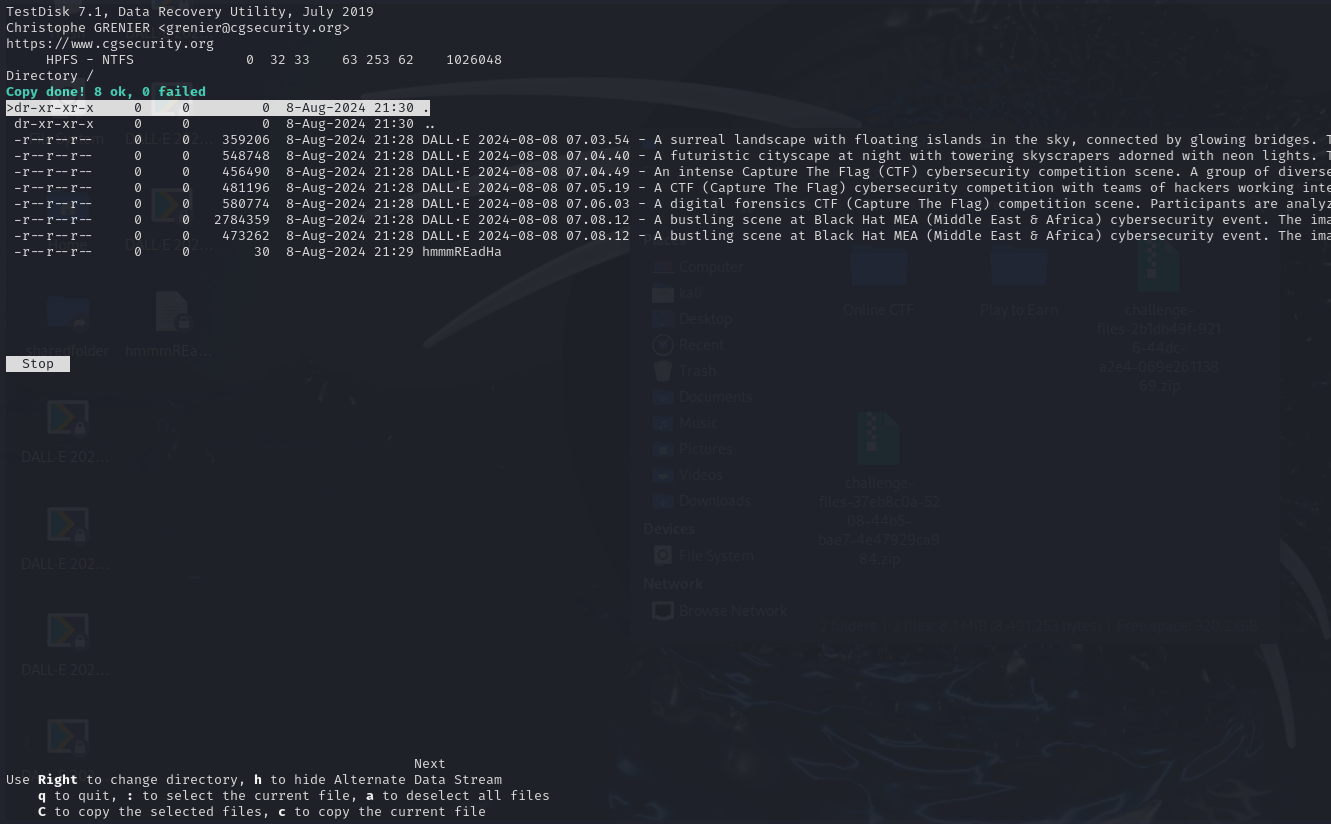
We were given a disk image to investigate. However, it seems that the NTFS header was missing from the disk image. One easy method to solve this challenge was to utilising testdisk with “Deeper Search” to extract the files within the disk image.
Analyzing the extracted files, an odd PNG image can be identified with a broken header.
1
2
3
4
5
6
7
8
9
└─$ file *
DALL·E 2024-08-08 07.03.54 - A surreal landscape with floating islands in the sky, connected by glowing bridges. The islands have lush greenery and ancient ruins on them. Below, a.webp: RIFF (little-endian) data, Web/P image, VP8 encoding, 1024x1024, Scaling: [none]x[none], YUV color, decoders should clamp
DALL·E 2024-08-08 07.04.40 - A futuristic cityscape at night with towering skyscrapers adorned with neon lights. The streets are bustling with people and advanced vehicles, and th.webp: RIFF (little-endian) data, Web/P image, VP8 encoding, 1024x1024, Scaling: [none]x[none], YUV color, decoders should clamp
DALL·E 2024-08-08 07.04.49 - An intense Capture The Flag (CTF) cybersecurity competition scene. A group of diverse hackers are working on laptops, surrounded by multiple monitors .webp: RIFF (little-endian) data, Web/P image, VP8 encoding, 1024x1024, Scaling: [none]x[none], YUV color, decoders should clamp
DALL·E 2024-08-08 07.05.19 - A CTF (Capture The Flag) cybersecurity competition with teams of hackers working intensely on various challenges. The scene includes multiple tables w.webp: RIFF (little-endian) data, Web/P image, VP8 encoding, 1024x1024, Scaling: [none]x[none], YUV color, decoders should clamp
DALL·E 2024-08-08 07.06.03 - A digital forensics CTF (Capture The Flag) competition scene. Participants are analyzing various digital artifacts such as memory dumps, network traff.webp: RIFF (little-endian) data, Web/P image, VP8 encoding, 1024x1024, Scaling: [none]x[none], YUV color, decoders should clamp
DALL·E 2024-08-08 07.08.12 - A bustling scene at Black Hat MEA (Middle East & Africa) cybersecurity event. The image includes a large exhibition hall filled with booths from vario.png: data
DALL·E 2024-08-08 07.08.12 - A bustling scene at Black Hat MEA (Middle East & Africa) cybersecurity event. The image includes a large exhibition hall filled with booths from vario.webp: RIFF (little-endian) data, Web/P image, VP8 encoding, 1024x1024, Scaling: [none]x[none], YUV color, decoders should clamp
hmmmREadHa: ASCII text
Fixing the PNG header will output the flag.