bi0sCTF 2024 - Writeups
This is a writeup for a forensics and misc challenge from bi0sCTF 2024. Unfortunately, I was busy with my internship so I could not finish every forensics challenge before the CTF ended. However, I did attempt them after the CTF and managed to find all the flags for one of the challenges (if only I had time to play).
Scenario [Forensics]
Randon, an IT employee finds a USB on his desk after recess. Unable to contain his curiosity he decides to plug it in. Suddenly the computer goes haywire and before he knows it, some windows pops open and closes on its own. With no clue of what just happened, he tries seeking help from a colleague. Even after Richard’s effort to remove the malware, Randon noticed that the malware persisted after his system restarted.
verboten 1 [Forensics]
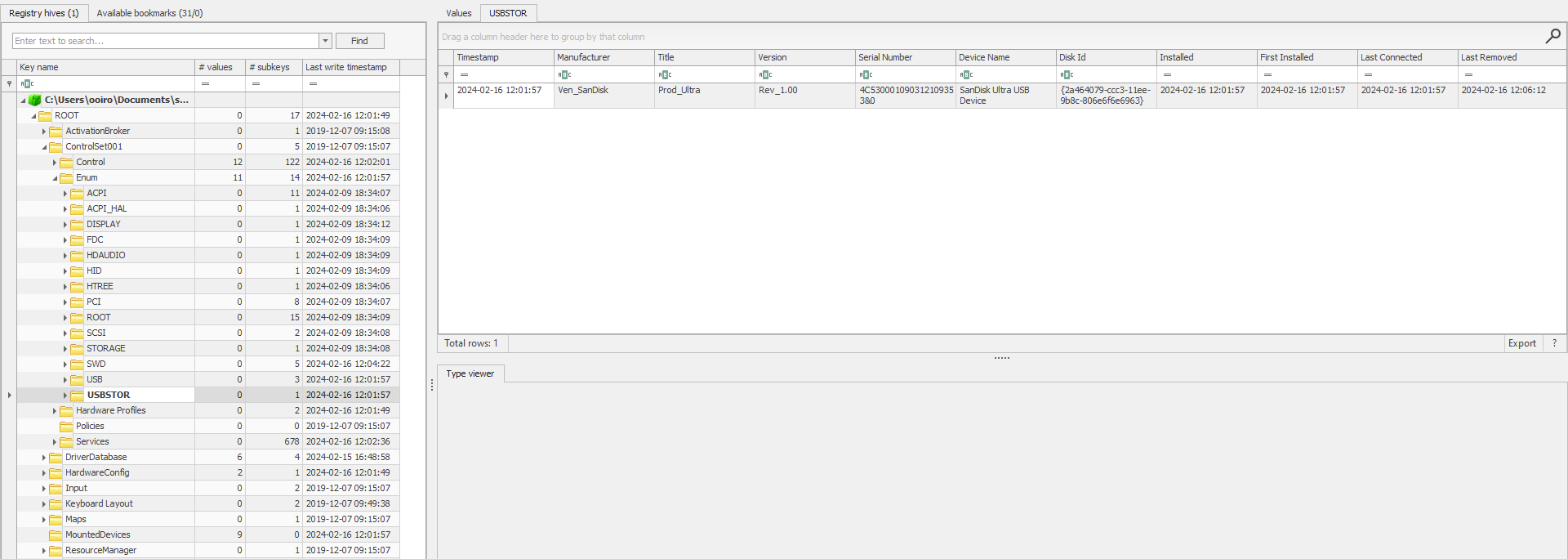
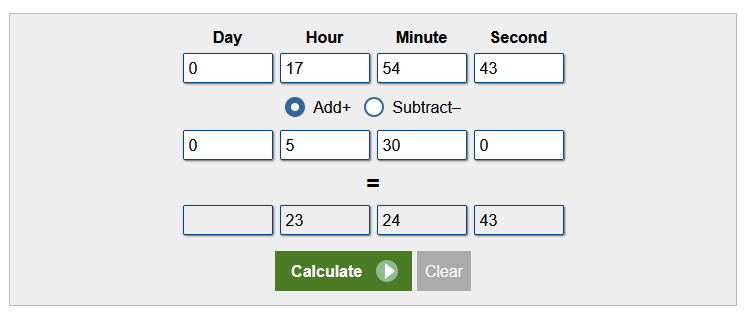
Question: What is the serial number of the sandisk usb that he plugged into the system? And when did he plug it into the system? Format: verboten{serial_number:YYYY-MM-DD-HH-MM-SS}
Flag: verboten{4C530001090312109353&0:2024-02-16-12-01-57}
We are given an AD1 image to investigate. Researching online about USB forensics, I stumbled upon this blog that mentioned the serial ID of the USB and the timestamp of when it was plugged into the system can be located in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USBSTOR.
verboten 2 [Forensics]
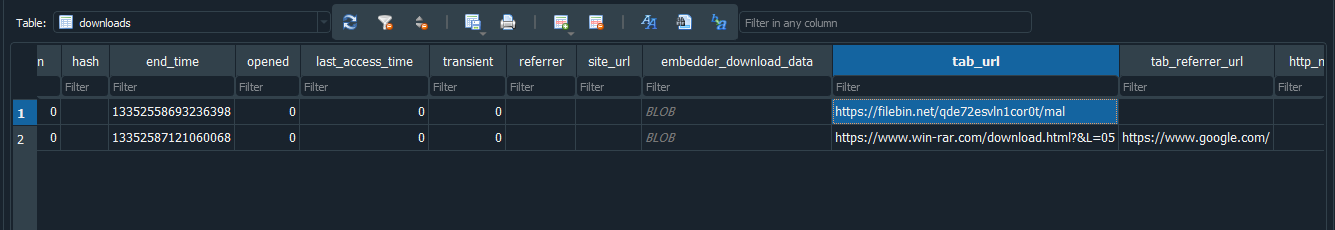
Question: What is the hash of the url from which the executable in the usb downloaded the malware from? Format: verboten{md5(url)}
Flag: verboten{11ecc1766b893aa2835f5e185147d1d2}
Going through the user’s Chrome browser history, the URL can be identified as https://filebin.net/qde72esvln1cor0t/mal.
verboten 3 [Forensics]
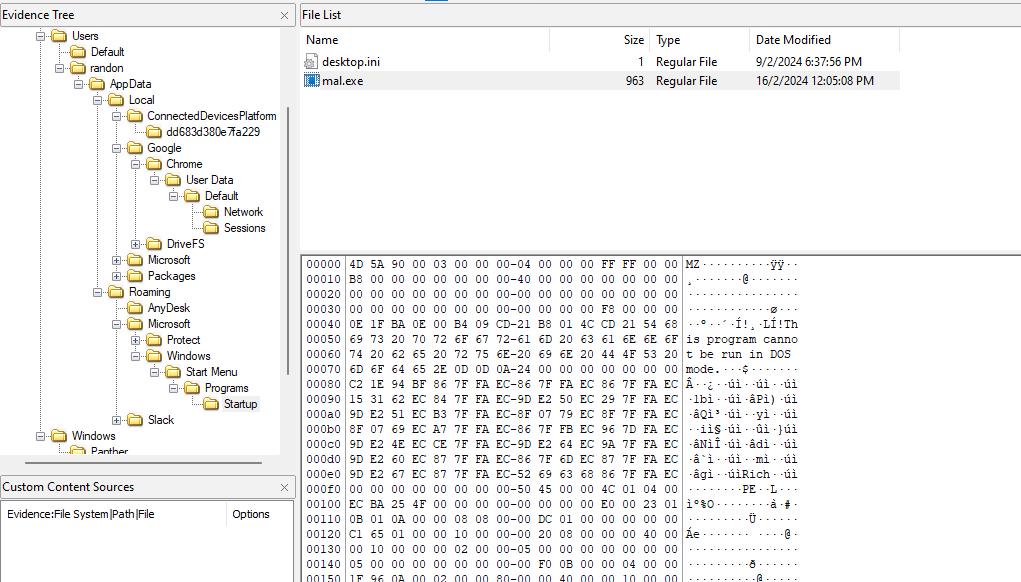
Question: What is the hash of the malware that the executable in the usb downloaded which persisted even after the efforts to remove the malware? Format: verboten{md5{malware_executable)}
Flag: verboten{169cbd05b7095f4dc9530f35a6980a79}
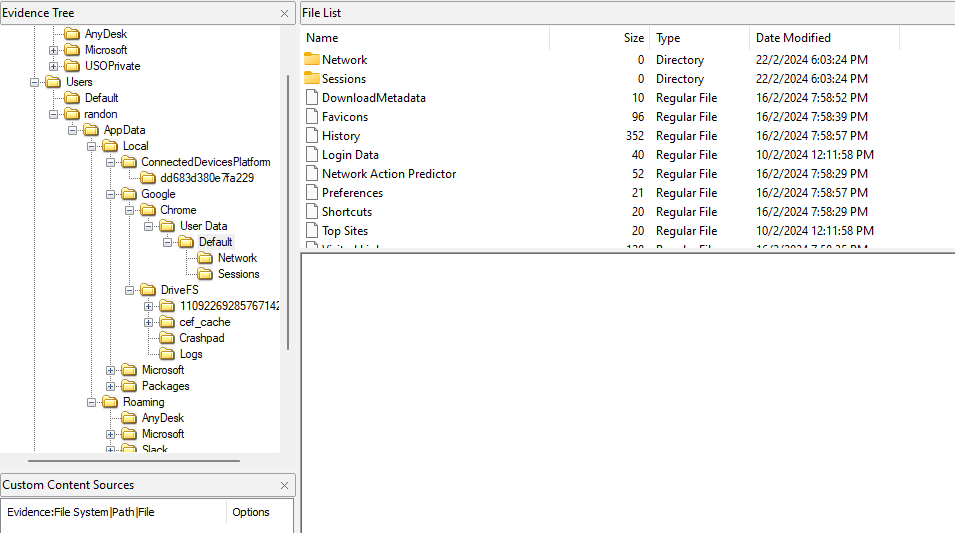
The malware was already identified to be mal.exe, we just have to look for it in the system. Going through common Windows locations, the malware was identified in C:\Users\randon\AppData\Roaming\Microsoft\Windows\Startup\.
verboten 4 [Forensics]
Question: What is the hash of the zip file and the invite address of the remote desktop that was sent through slack? Format: verboten{md5(zip_file):invite_address}
Flag: verboten{b092eb225b07e17ba8a70b755ba97050:1541069606}
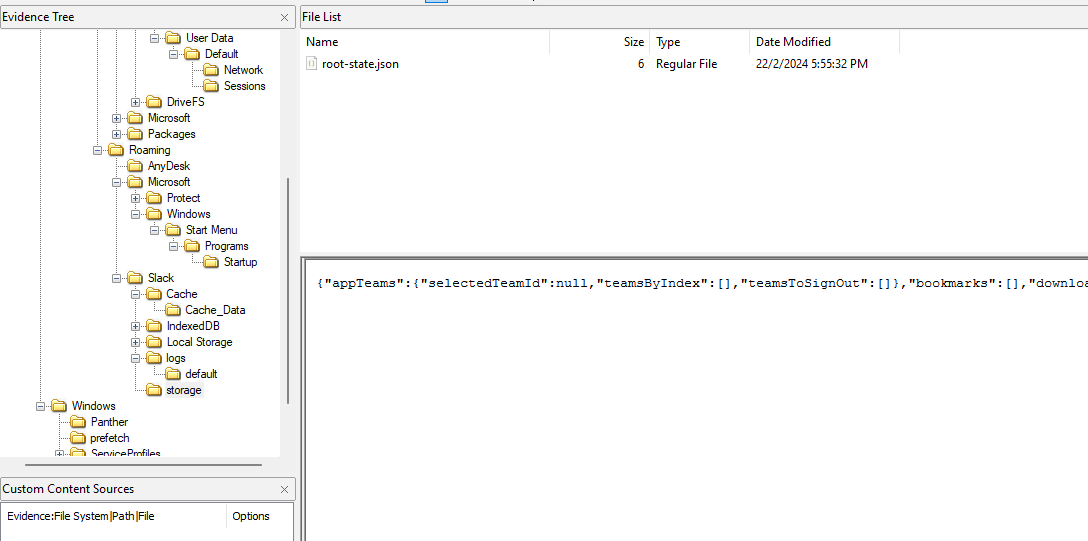
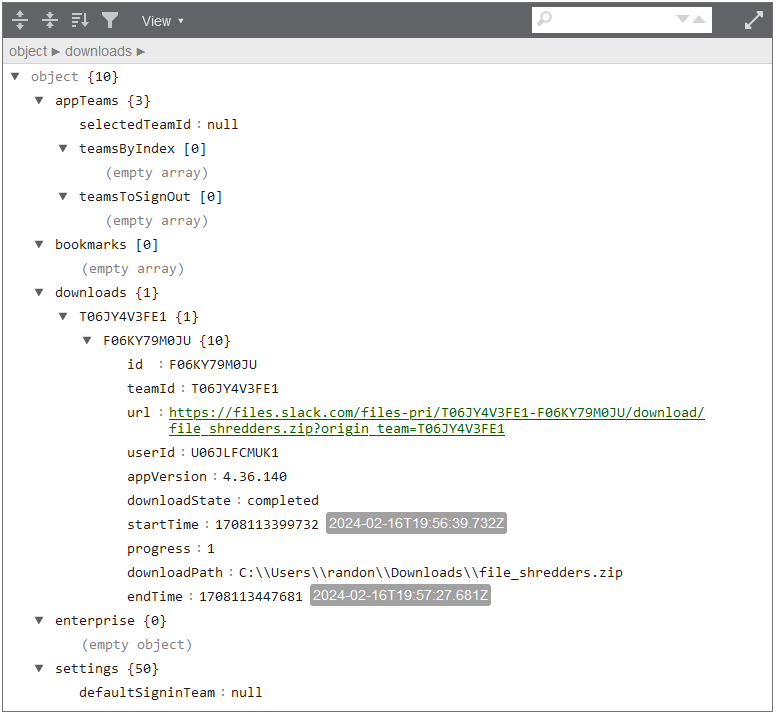
Analyzing the “root-state.json” file located in C:\Users\randon\AppData\Roaming\, the name of the downloaded ZIP file can be identified.
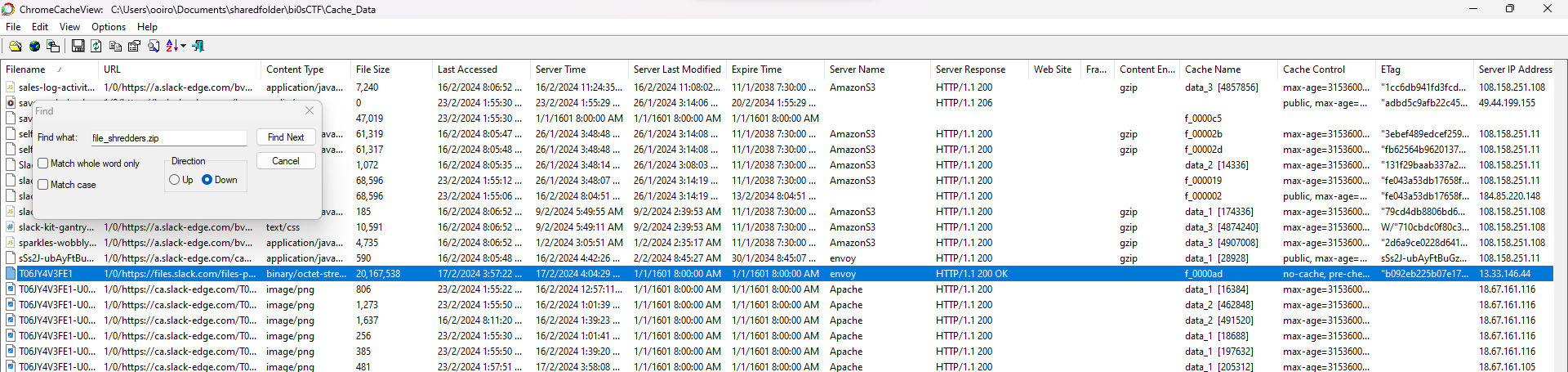
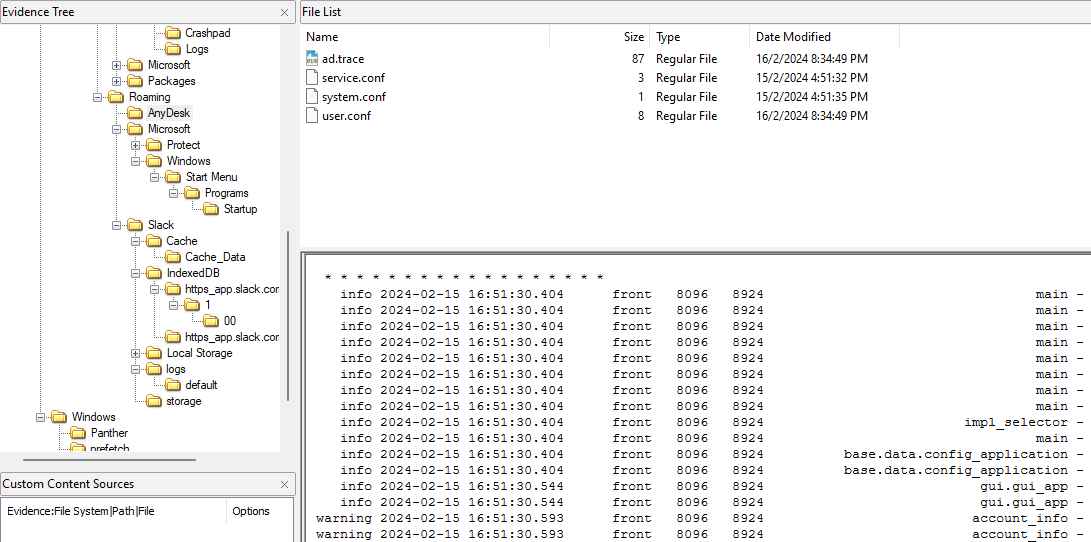
Researching online about extracting Slack cached files, I stumbled upon this blog that mentioned using Nirsoft Chrome Cache Viewer to view cached data in Slack. By filtering the name of the ZIP file identified previously, the MD5 hash of the ZIP file can be obtain from the ETag column.
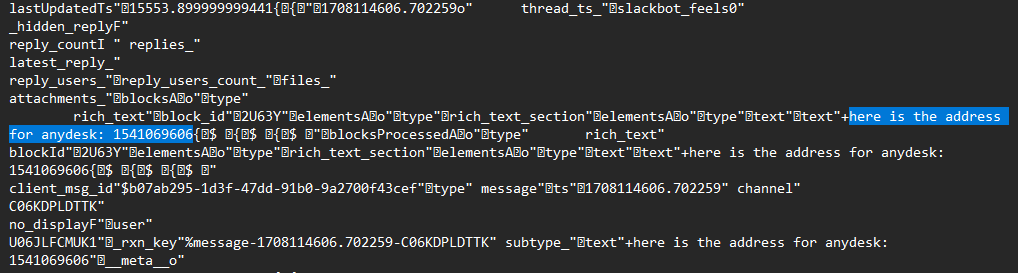
Analyzing the IndexedDB blob file located in C:\Users\randon\AppData\Roaming\Slack\IndexedDB\ using grep, the invite address can be found with a suspicious text about AnyDesk connection.
Intended method: @Dysnome mentioned this tool to parse Slack conversations.
verboten 5 [Forensics]
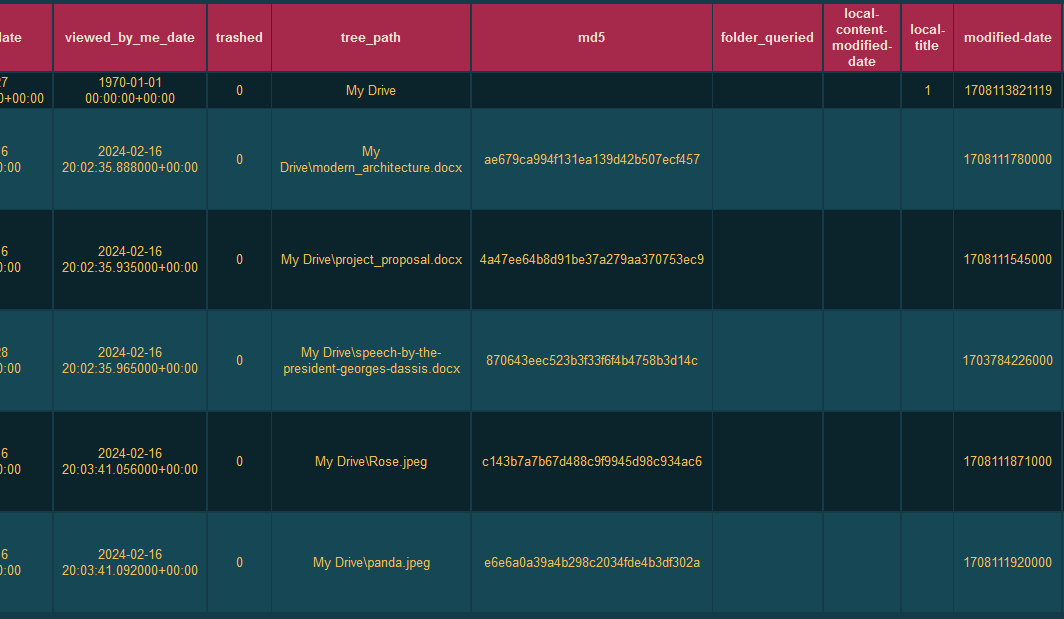
Question: What is the hash of all the files that were synced to Google Drive before it was shredded? Format: verboten{md5 of each file separated by ‘:’}
Flag: verboten{ae679ca994f131ea139d42b507ecf457:4a47ee64b8d91be37a279aa370753ec9:870643eec523b3f33f6f4b4758b3d14c:c143b7a7b67d488c9f9945d98c934ac6:e6e6a0a39a4b298c2034fde4b3df302a}
Researching online about Google Drive forensics, I stumbled upon this blog that mentioned a tool called DriveFS Sleuth to parse Google Drive File Stream disk artifacts. The deleted files can be identified after running the tool with the specific Google Drive artifacts.
verboten 6 [Forensics]
Question: What is time of the incoming connection on AnyDesk? And what is the ID of user from which the connection is requested? Format: verboten{YYYY-MM-DD-HH-MM-SS:user_id}
Flag: verboten{2024-02-16-20-29-04:221436813}
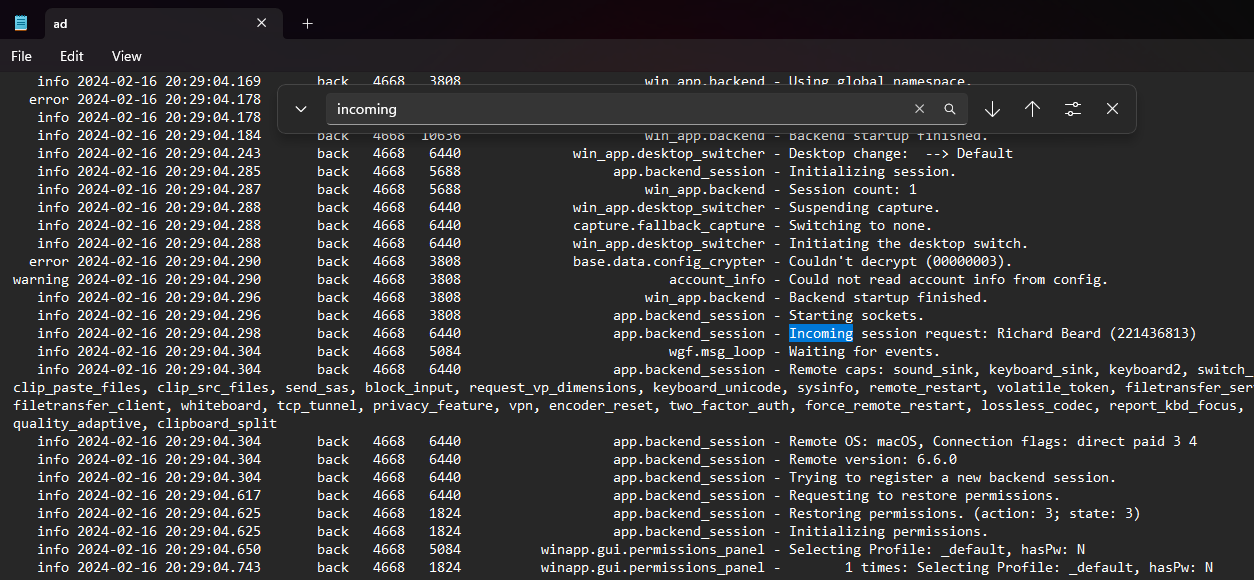
Researching online about AnyDesk forensics, I stumbled upon this blog that mentioned about successful AnyDesk connections being stored in “ad.trace” log file.
Filtering the log file with keyword “incoming”, information about the AnyDesk connection can be identified.
verboten 7 [Forensics]
Question: When was the shredder executed? Format: verboten{YYYY-MM-DD-HH-MM-SS}
Flag: verboten{2024-02-16-08-31-06}
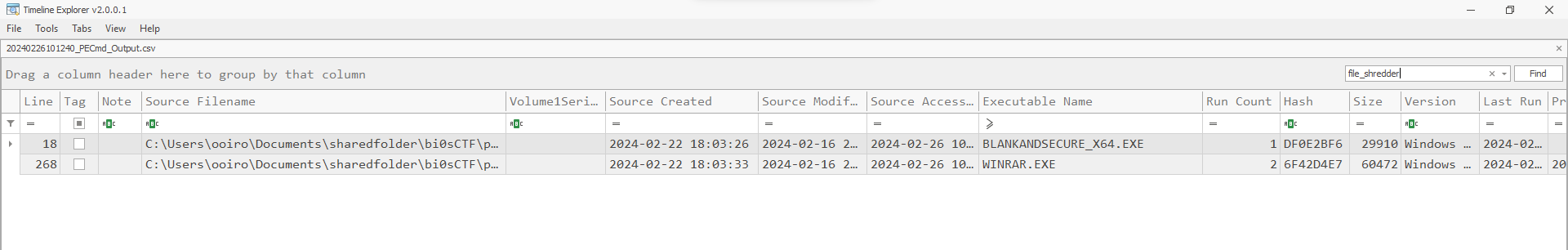
The challenge mentioned a shredder being executed, so I assume it refers to the executable file within file_shredder.zip. However, this ZIP file was assumed to be deleted since it was not present in the Downloads folder. Analyzing the prefetch files, the executed date of BLANKANDSECURE_X64.EXE-DF0E2BF6.pf can be identified.
verboten 8 [Forensics]
Question: What are the answers of the backup questions for resetting the windows password? Format: verboten{answer_1:answer_2:answer_3}
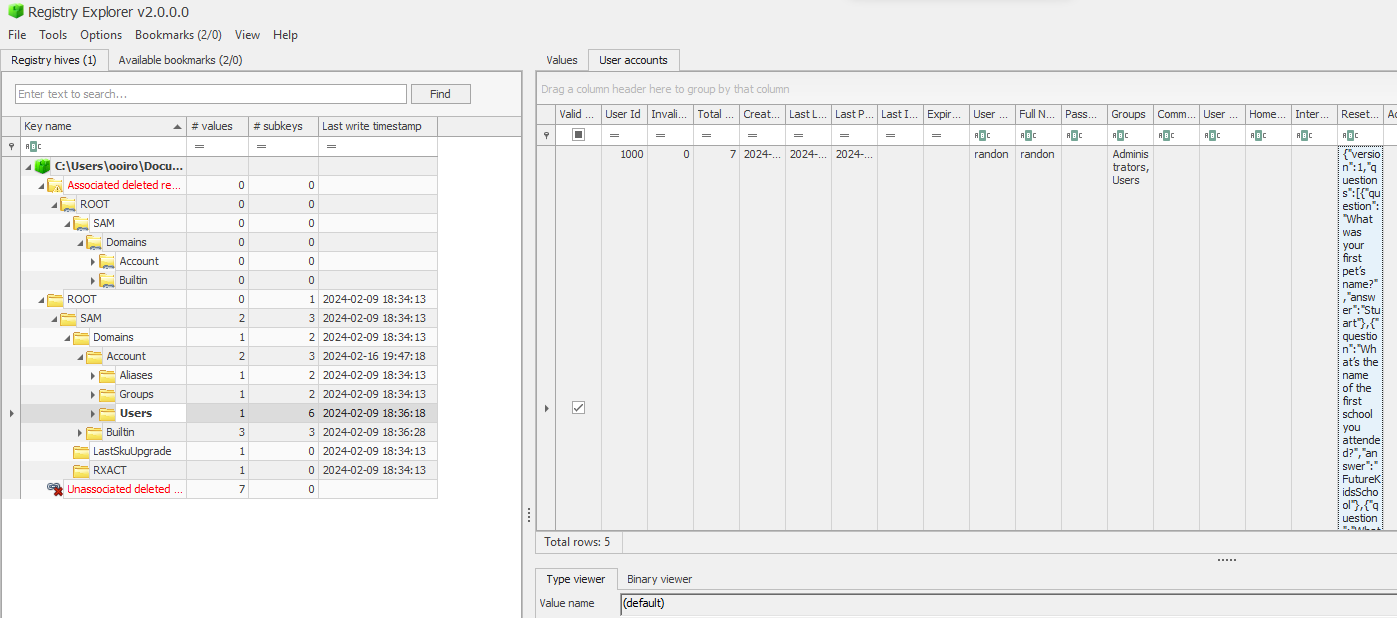
Flag: verboten{Stuart:FutureKidsSchool:Howard}
Analyzing the SAM registry hive, the answers for the backup questions can be identified.
verboten 9 [Forensics]
Question: What is the single use code that he copied into the clipboard and when did he copy it? Format: verboten{single_use_code:YYYY-MM-DD-HH-MM-SS}
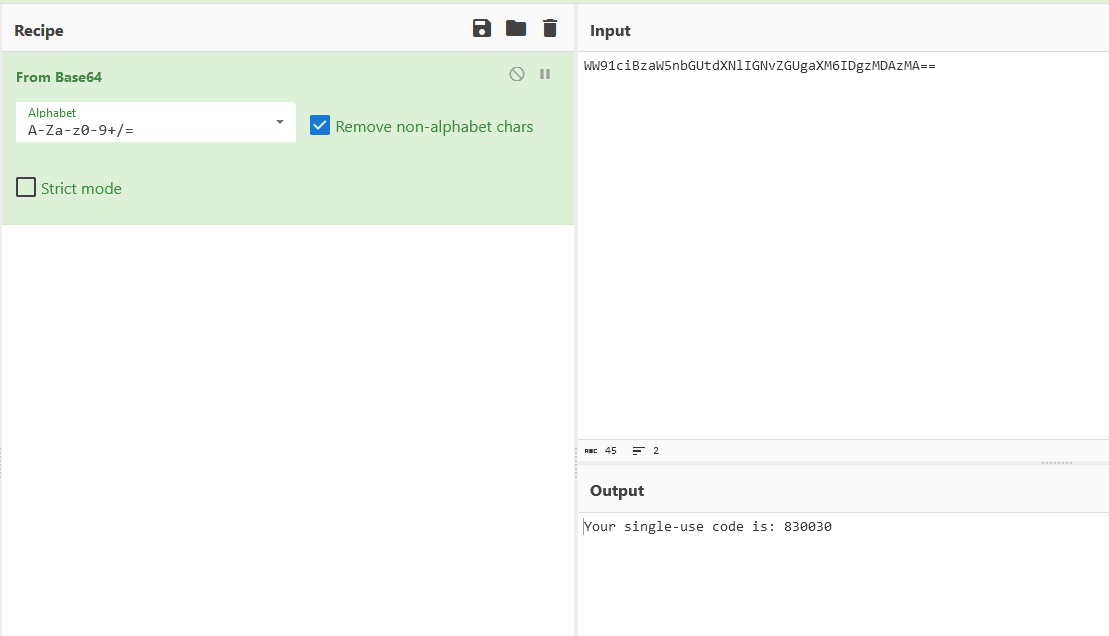
Flag: verboten{830030:2024-02-16-23-24-43}
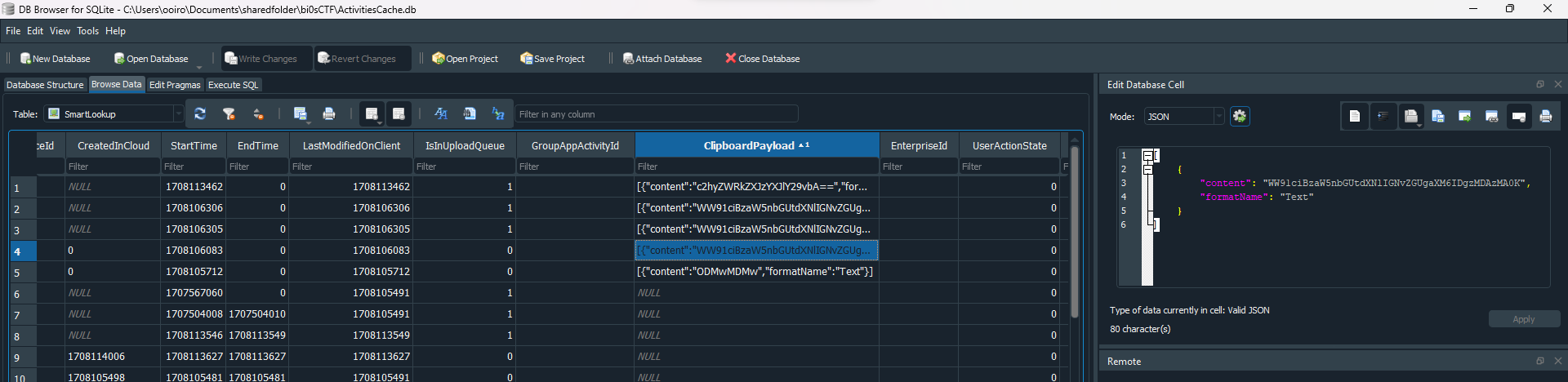
Researching online about Clipboard history, I stumbled upon this blog that mentioned about the “ActivitiesCache.db” file located in \Users\randon\AppData\Local\ConnectedDevicesPlatform\dd683d380e7fa229\. The “ClipboardPayload” column shows the clipboard content.
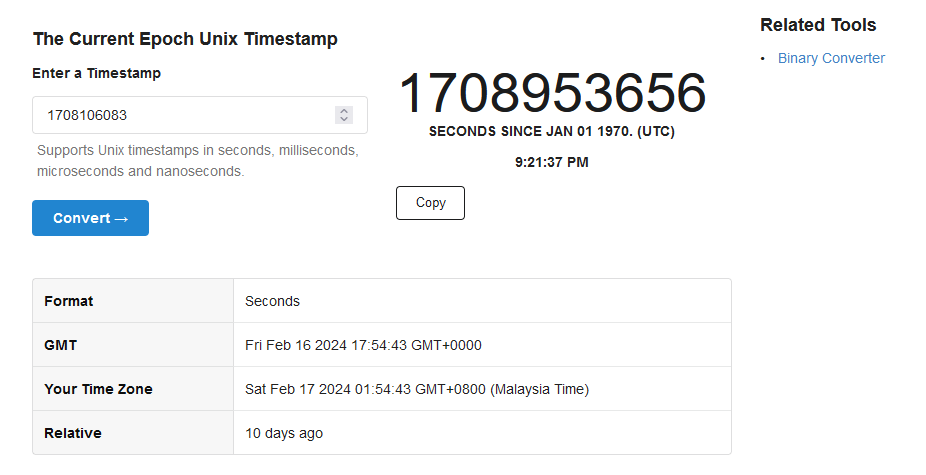
For the epoch time in “LastModifiedOnClient” column, it should be adjusted to IST timezone format as mentioned by the authors. So we can identify the time and convert it to get the real time.
Welcome [Misc]
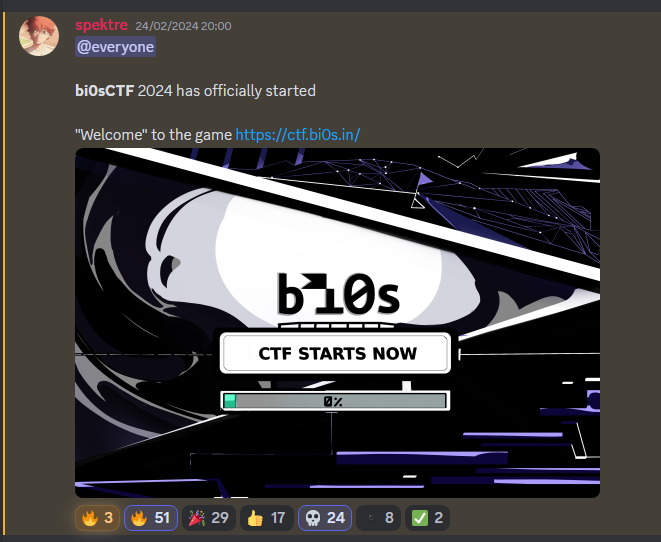
Question: Some things are hidden in plain sight.
Flag: bi0sctf{h1dd3n_1n_pl41n_s1ght}
I know this is just a welcome flag, but I still found it cool how this flag was hidden using Discord. Just copy the text of the announcement post to get the flag embedded within the URL.
1
2
3
4
5
@everyone
**bi0sCTF** 2024 has officially started
"Welcome" to the game https://bi0sctf%7Bh1dd3n_1n_pl41n_s1ght%7D:hehe@ctf.bi0s.in/